File processing method and device, electronic equipment and storage medium
A file processing and stored technology, applied in the direction of electrical digital data processing, computer security devices, instruments, etc., can solve the problems of easy decryption and leakage of data, low encryption coefficient, etc., and achieve the effect of increasing the difficulty coefficient of decryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
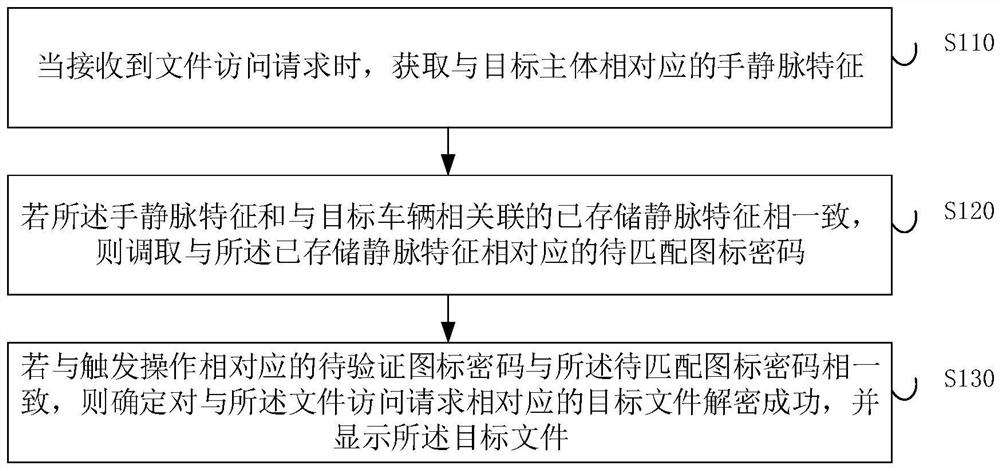
[0029] figure 1 This is a flowchart of a file processing method provided in Embodiment 1 of the present invention. This embodiment is applicable to the situation of data encryption and decryption. The method can be executed by the file processing apparatus in this embodiment of the present invention, and the apparatus can use software and / or hardware. Optionally, it is implemented by an electronic device, and the electronic device may be a mobile terminal, a PC, or a server. The apparatus may be configured in a computing device, and the file processing method provided in this embodiment specifically includes the following steps:
[0030] S110. When a file access request is received, acquire the hand vein feature corresponding to the target subject.
[0031] The file access request includes at least one of access requests for reading, copying, moving, and deleting file data. File data includes, but is not limited to, vehicle video data, basic user data, vehicle driving data, ...
Embodiment 2
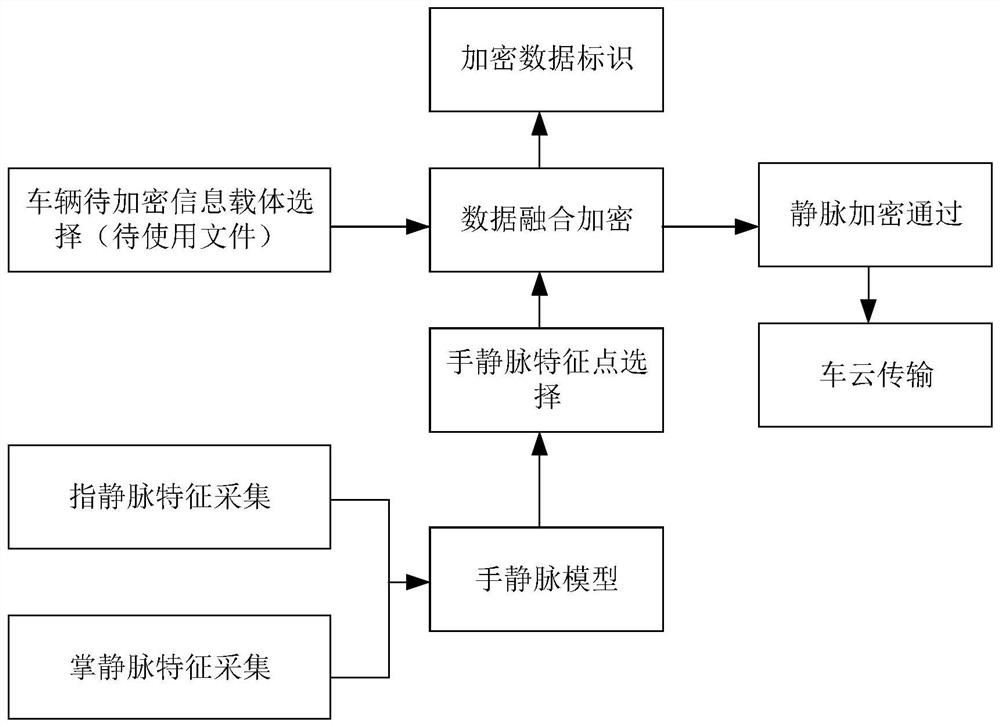
[0062] As an optional embodiment of the above-mentioned embodiment, figure 2 It is a schematic diagram of the file encryption method provided by the second embodiment of the present invention. Specifically, please refer to the following specific content.
[0063] see figure 2, the information that needs to be decrypted in the target vehicle can be selected as the to-be-used file based on user requirements, and the to-be-used file includes but is not limited to vehicle-mounted video data, user data, vehicle driving data, and the like. At this time, the user's finger vein feature collection and palm vein feature collection are collected, and each vein feature is input into the hand vein model to generate the first encryption method; at the same time, some or all of the feature points can also be selected in the finger vein feature collection and palm vein feature collection As the second encryption method for the file; the to-be-used file can be encrypted based on the first ...
Embodiment 3
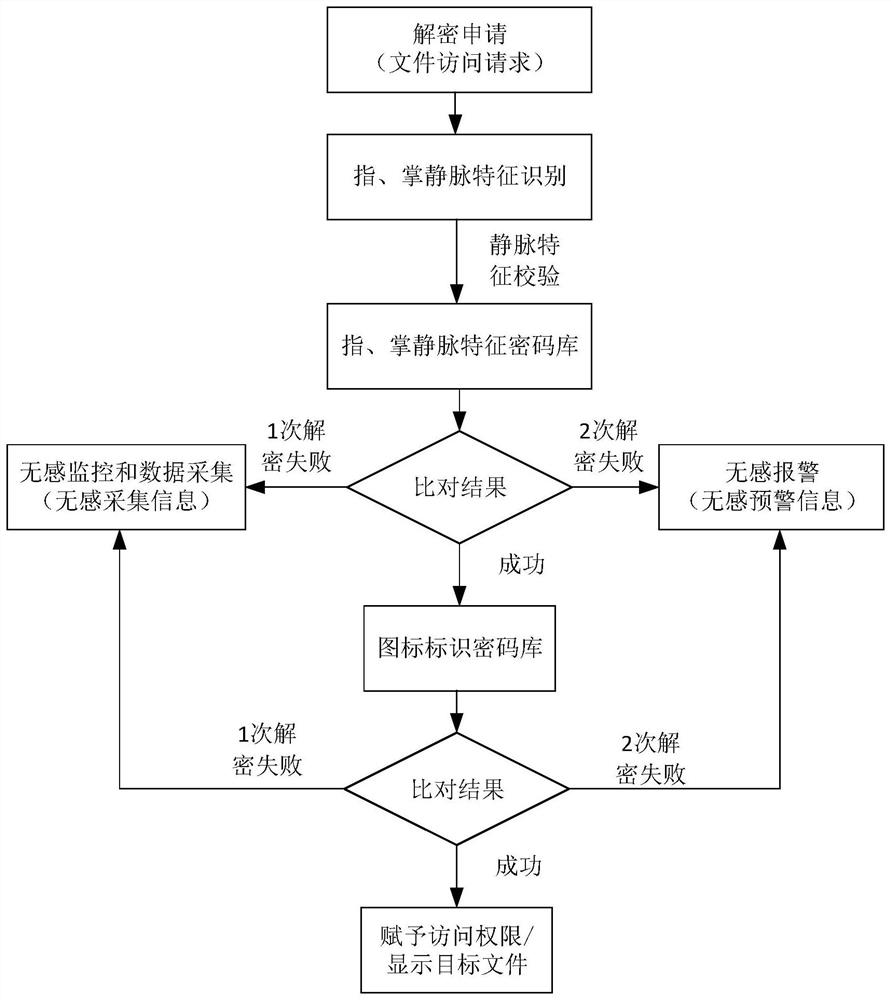
[0067] Figure 5 It is a structural block diagram of a file processing apparatus provided by Embodiment 3 of the present invention. The device includes: a hand vein feature acquisition module 510 , an icon password retrieval module 520 to be matched, and a target file display module 530 .
[0068] Wherein, the hand vein feature acquisition module 510 is configured to acquire hand vein features corresponding to the target subject when a file access request is received, wherein the hand vein features include finger vein features and palm vein features; the icon to be matched The password retrieval module 520 is used to retrieve the icon password to be matched corresponding to the stored vein feature if the hand vein feature is consistent with the stored vein feature associated with the target vehicle; the target file display module 530: If the password of the icon to be verified corresponding to the trigger operation is consistent with the password of the icon to be matched, de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com