Safe and controllable internet real-name certification mechanism
A real-name authentication, Internet technology, applied in the field of network security, can solve problems such as identity information confidentiality, and achieve the effect of reducing the burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with accompanying drawing and specific embodiment:
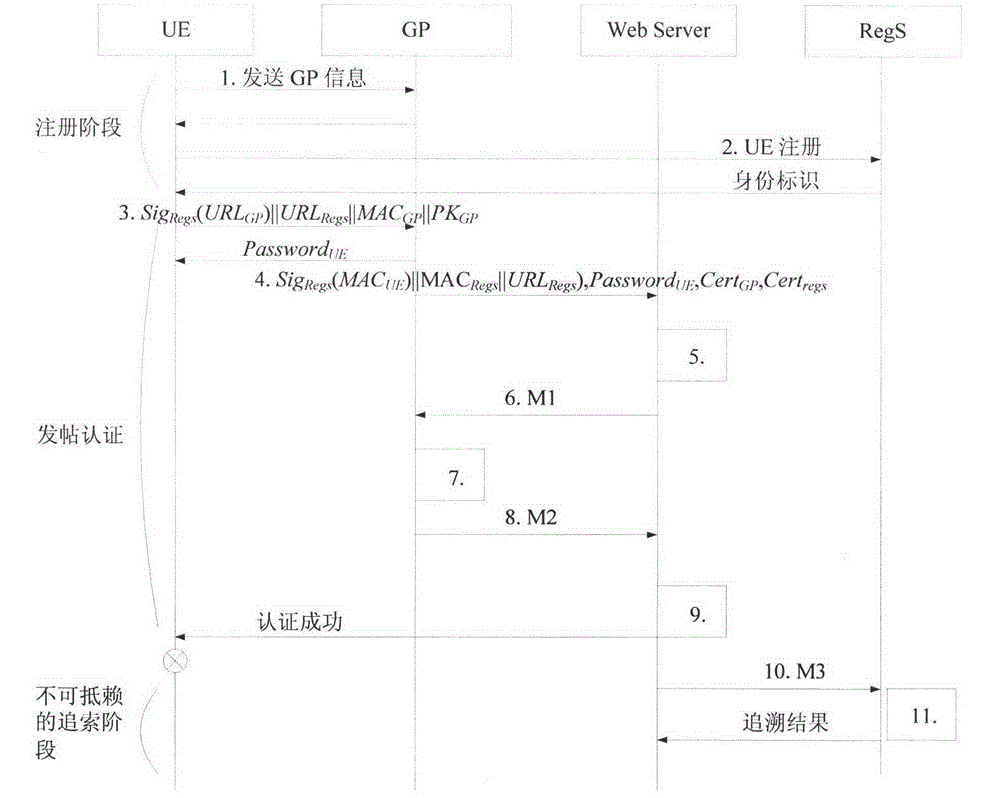
[0025] The present invention mainly includes the processing of three components: a registration stage, a network behavior monitoring stage and a non-repudiation tracing stage. When the UE wants to accept the service provided by the Web Server, the Web Server requires real-name authentication, the UE transmits the identity information to the RegS, and the RegS returns the authentication result of the UE identity information, and encrypts the transmission link to protect the security of the transmitted information. Report the above-mentioned encrypted personal identity information and the above-mentioned real-name authentication result to the above-mentioned website server.
[0026] The implementation steps and signaling interaction of the Internet real-name authentication mechanism are as follows:
[0027] 1. Registration stage
[0028] (1) The UE f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com