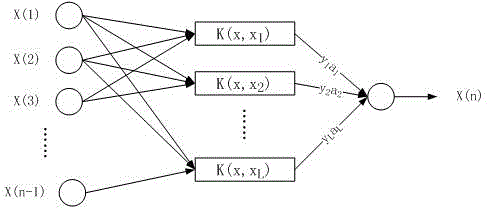
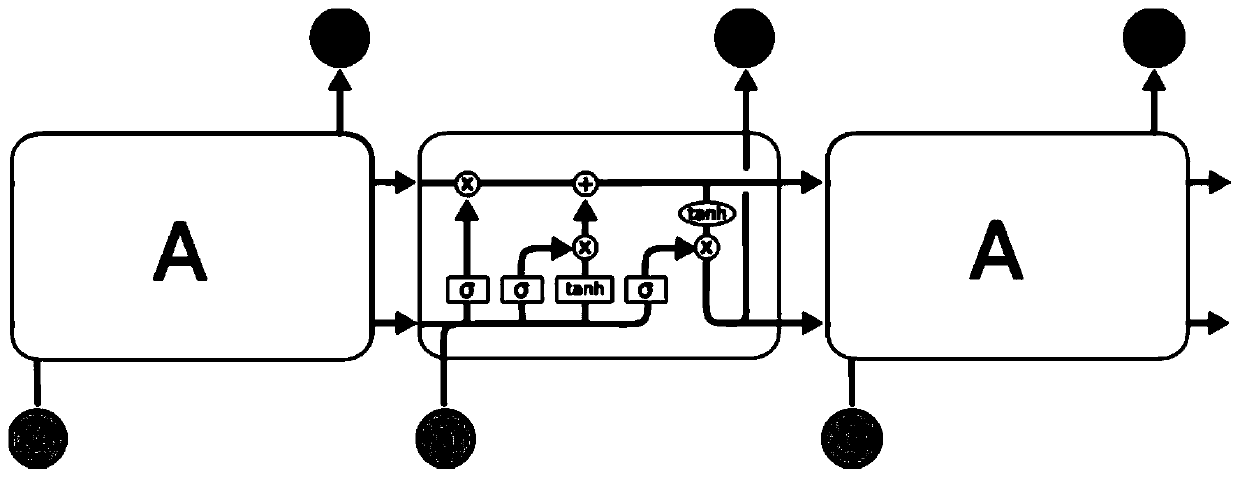
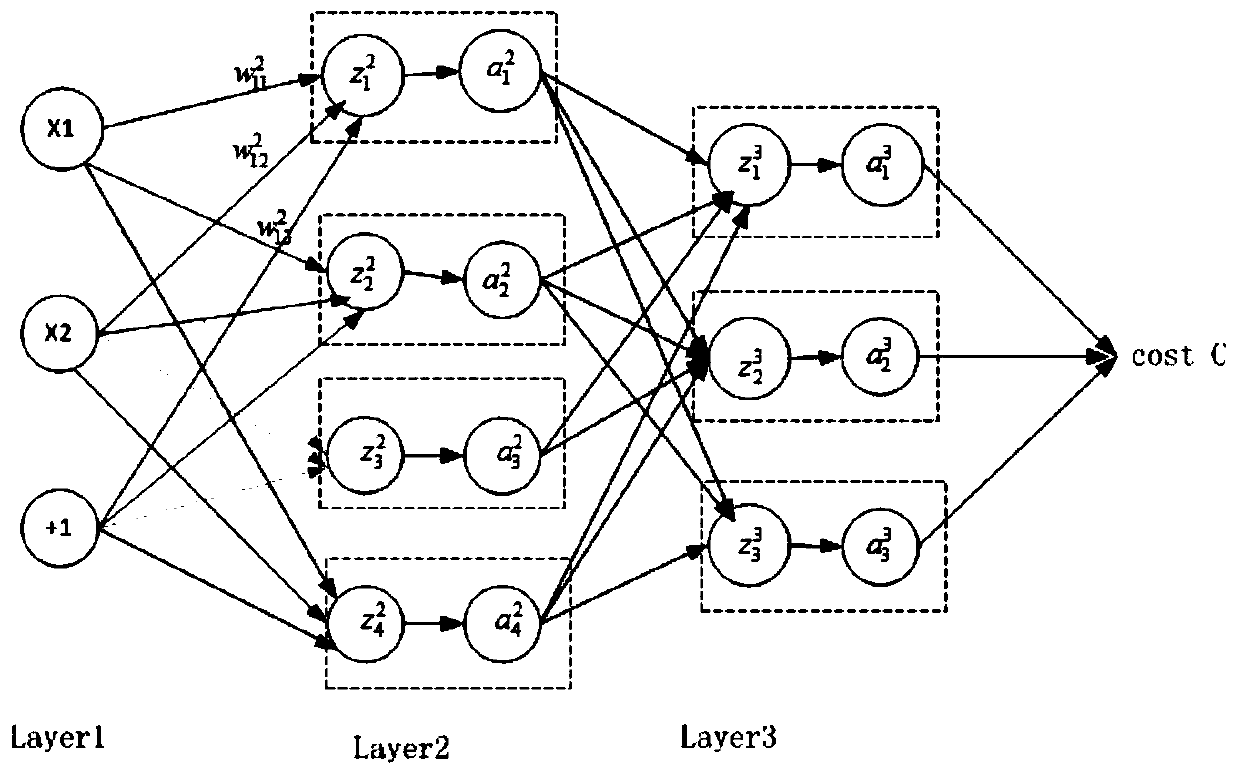
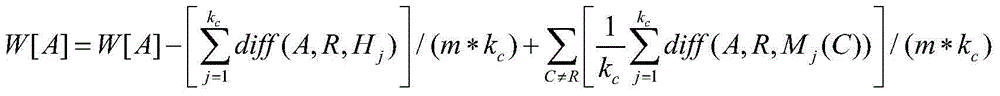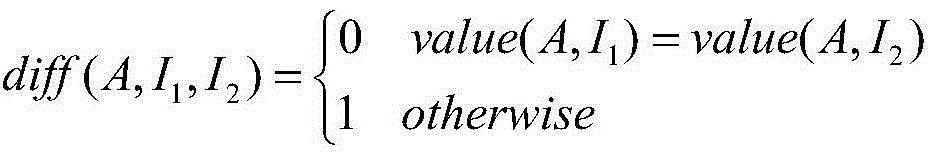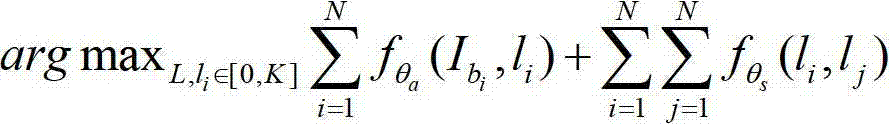Patents
Literature
412 results about "Parameter learning" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Parameter learning. Parameter learning is the process of using data to learn the distributions of a Bayesian network or Dynamic Bayesian network. Bayes Server uses the Expectation Maximization (EM) algorithm to perform maximum likelihood estimation, and supports all of the following: Learning both discrete and continuous distributions.
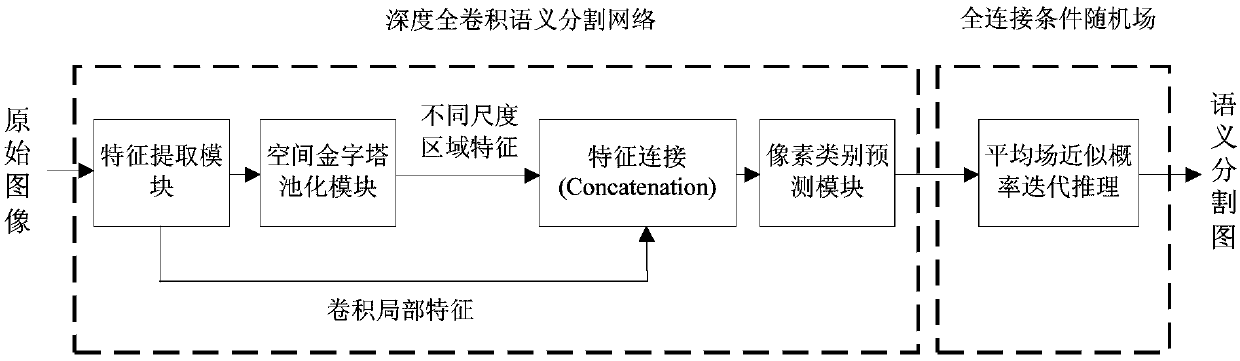
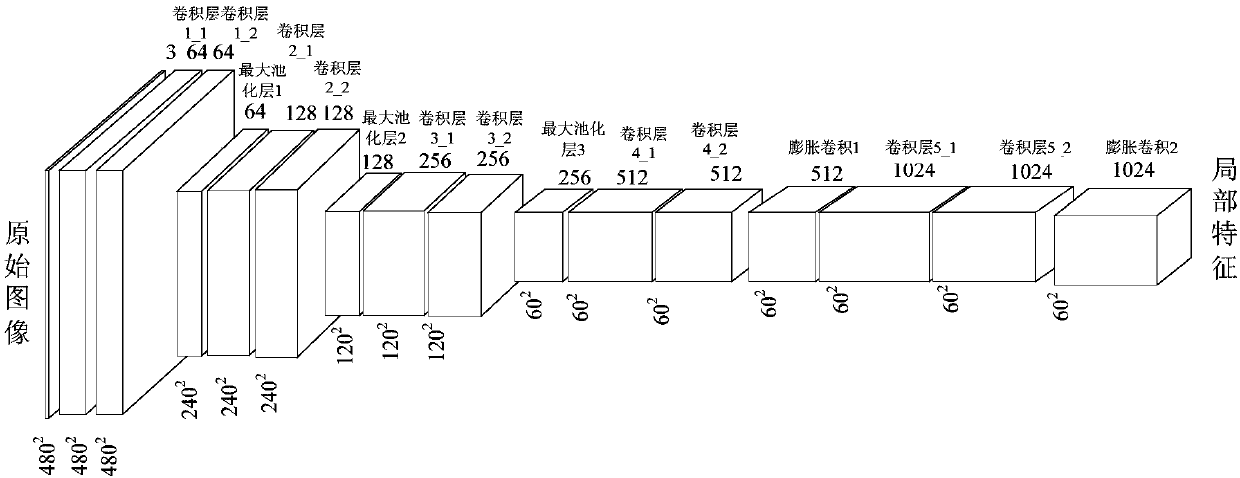
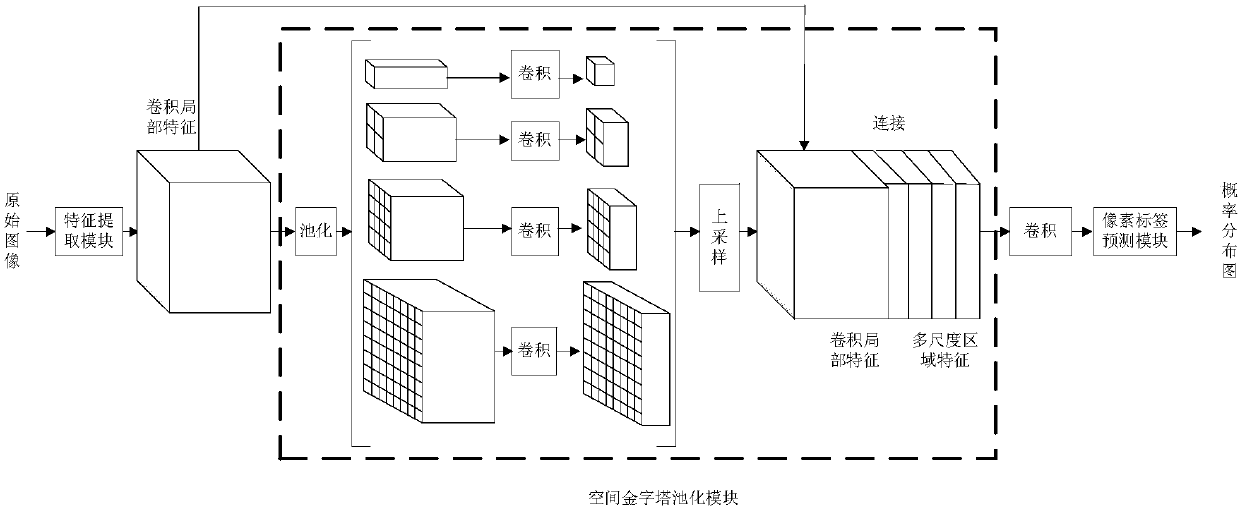
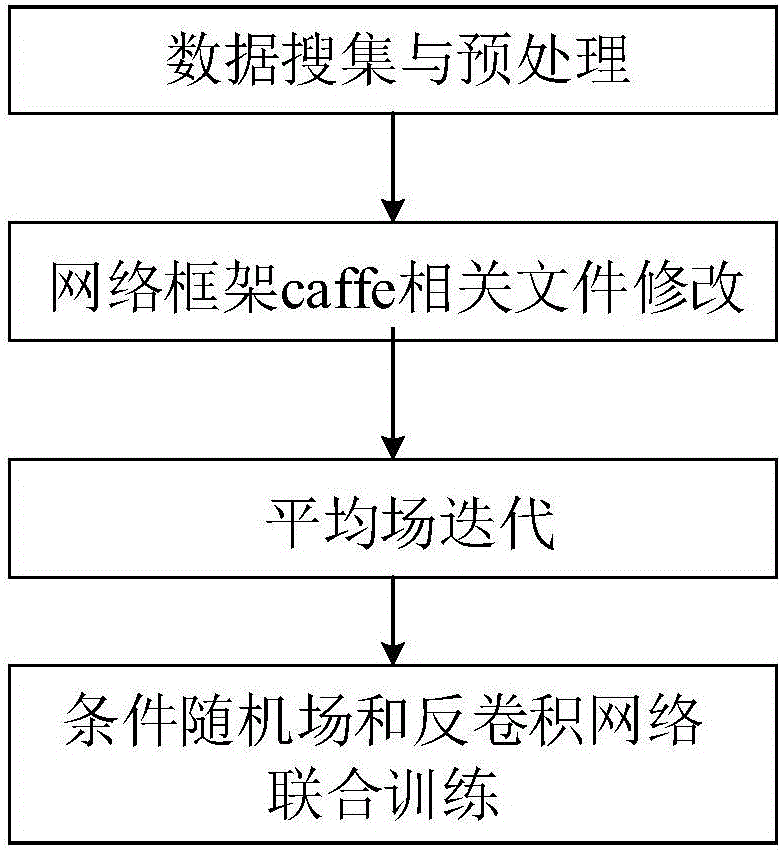
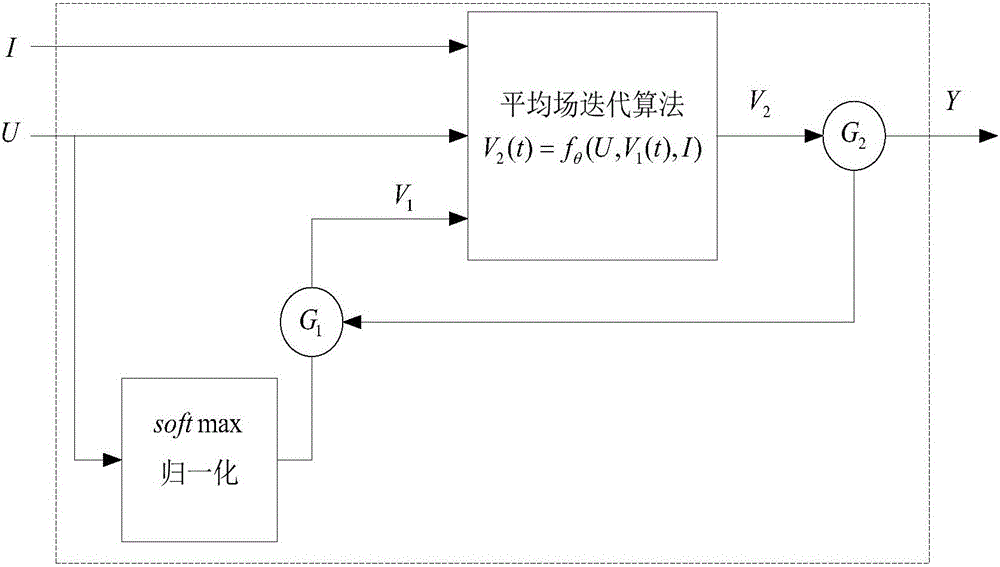
Image semantic division method based on depth full convolution network and condition random field
InactiveCN108062756ADoes not reduce dimensionalityHigh-resolutionImage enhancementImage analysisConditional random fieldImage resolution
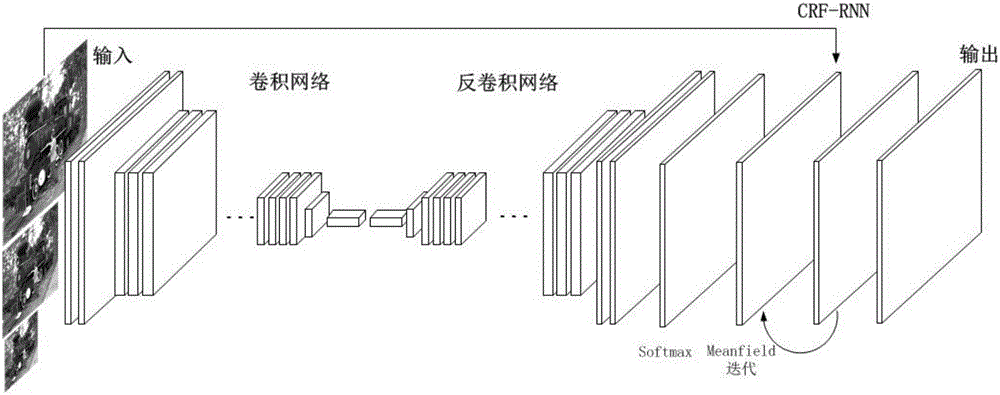
The invention provides an image semantic division method based on a depth full convolution network and a condition random field. The image semantic division method comprises the following steps: establishing a depth full convolution semantic division network model; carrying out structured prediction based on a pixel label of a full connection condition random field, and carrying out model training, parameter learning and image semantic division. According to the image semantic division method provided by the invention, expansion convolution and a spatial pyramid pooling module are introduced into the depth full convolution network, and a label predication pattern output by the depth full convolution network is further revised by utilizing the condition random field; the expansion convolution is used for enlarging a receptive field and ensures that the resolution ratio of a feature pattern is not changed; the spatial pyramid pooling module is used for extracting contextual features of different scale regions from a convolution local feature pattern, and a mutual relation between different objects and connection between the objects and features of regions with different scales are provided for the label predication; the full connection condition random field is used for further optimizing the pixel label according to feature similarity of pixel strength and positions, so that a semantic division pattern with a high resolution ratio, an accurate boundary and good space continuity is generated.
Owner:CHONGQING UNIV OF TECH
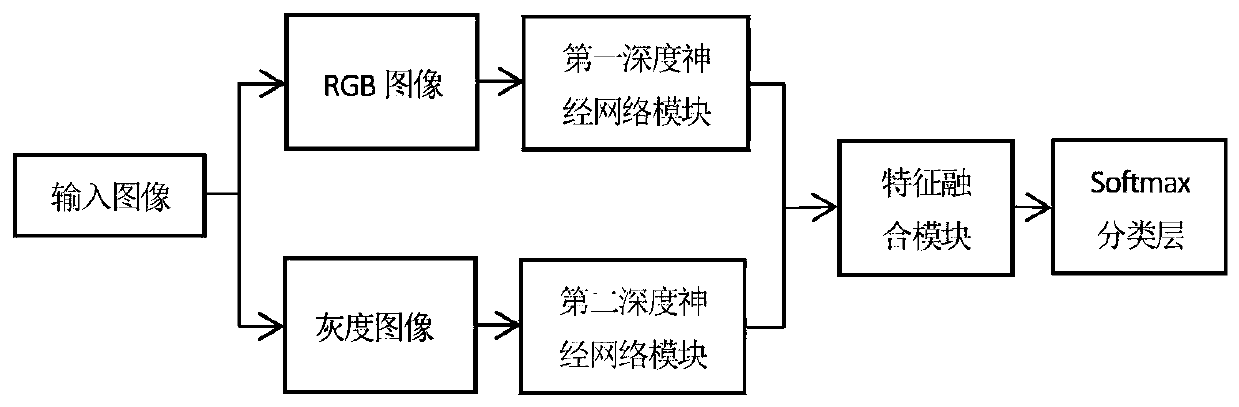
An image semantic segmentation method based on deep learning
ActiveCN109711413ARich coordinate featuresImprove generalization abilityInternal combustion piston enginesCharacter and pattern recognitionData setRgb image
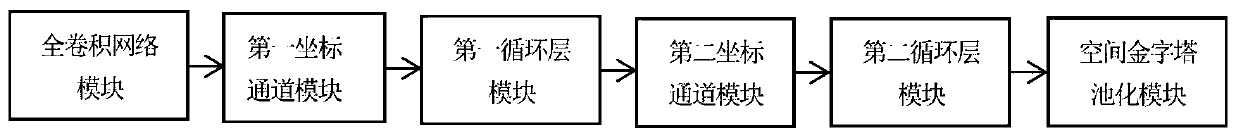
The invention discloses an image semantic segmentation method based on deep learning. The method comprises four parts of data set processing, deep semantic segmentation network construction, deep semantic segmentation network training and parameter learning, and semantic segmentation on a test image. The RGB image and the gray level image of the input image are used as the input of the network model, the edge information of the gray level image is fully utilized, and the richness degree of input characteristics is effectively increased; a convolutional neural network and a bidirectional threshold recursion unit are combined, and more context dependency relationships and global feature information are captured on the basis of learning image local features; coordinate information is added tothe feature map through the first coordinate channel module and the second coordinate channel module, the coordinate features of the model are enriched, the generalization ability of the model is improved, and a semantic segmentation result with high resolution and accurate boundary is generated.
Owner:SHAANXI NORMAL UNIV
Equipment fault warning and state monitoring method
ActiveCN104102773AImprove general performanceEfficient use ofSpecial data processing applicationsRobustificationReal-time data
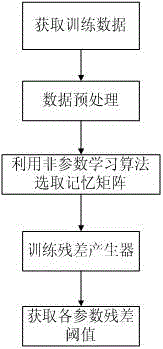
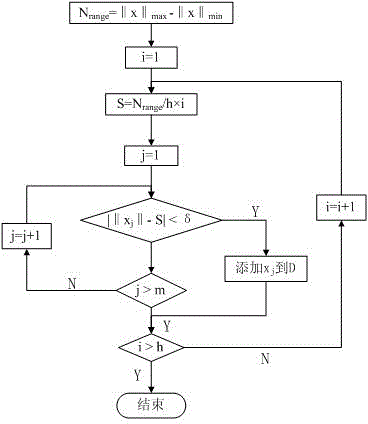
The invention relates to the technical field of equipment fault monitoring, and particularly discloses an equipment fault warning and state monitoring method. The equipment fault warning and state monitoring method is characterized by including two processes of model building and model operation; the process of model building includes the steps of acquiring training data, performing data preprocessing operation on the training data, then adopting a nonparametric learning algorithm to select a memory matrix, training a residual generator and acquiring a residual threshold of each parameter; the process of model operation includes the steps of acquiring real-time data, performing data preprocessing operation on the real-time data, then calculating all parameter residuals of the real-time data, analyzing the residuals to judge whether the equipment state is normal or not, and further positioning fault causes. The method has the advantages of data-driven method based universality, robustness and high adaptive capability, the shortcoming that warning results are difficult to analyze and explain is avoided, and additionally accuracy and efficiency of fault warning are both improved due to introduction of the nonparametric learning algorithm.
Owner:SHANDONG LUNENG SOFTWARE TECH +1
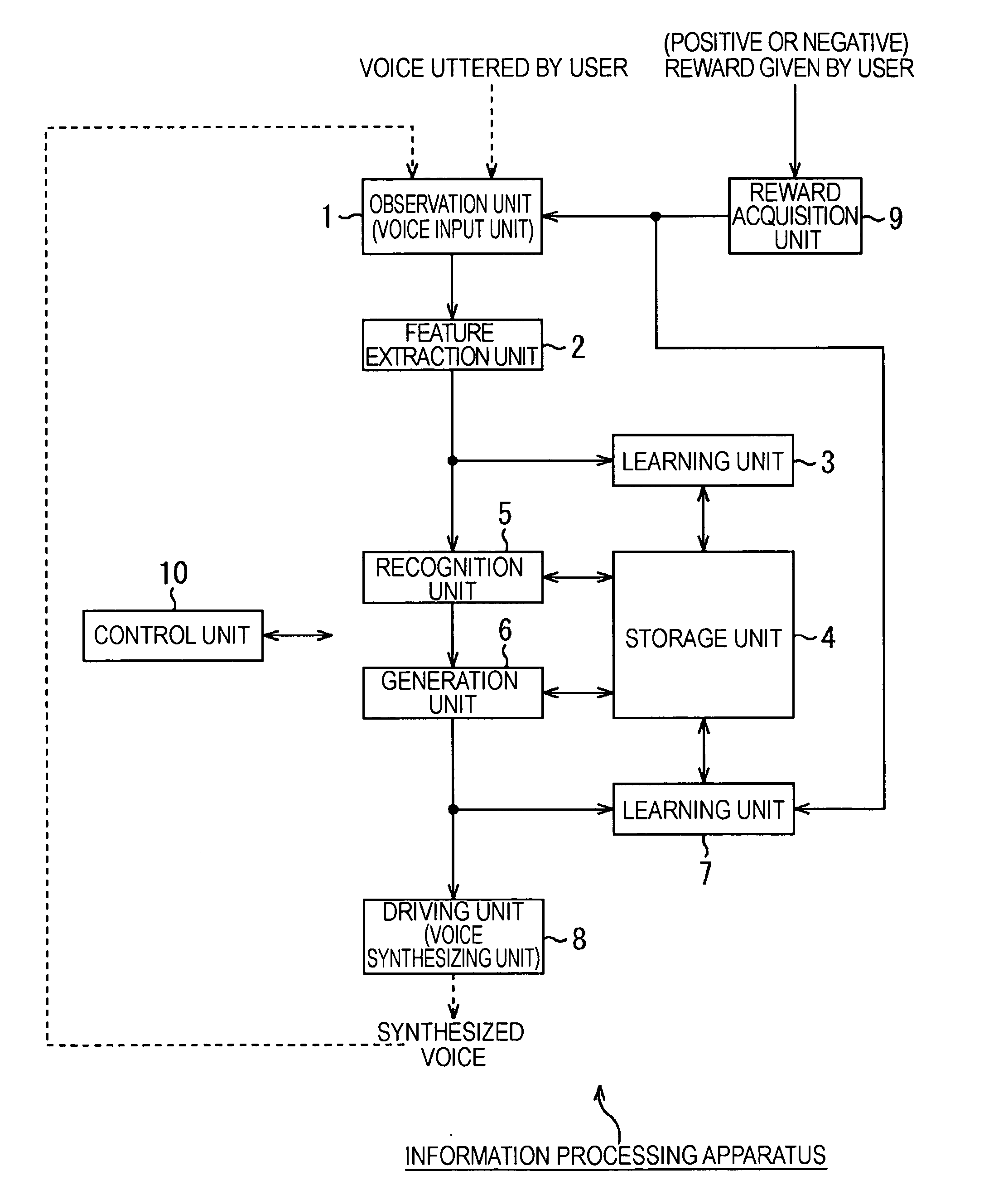
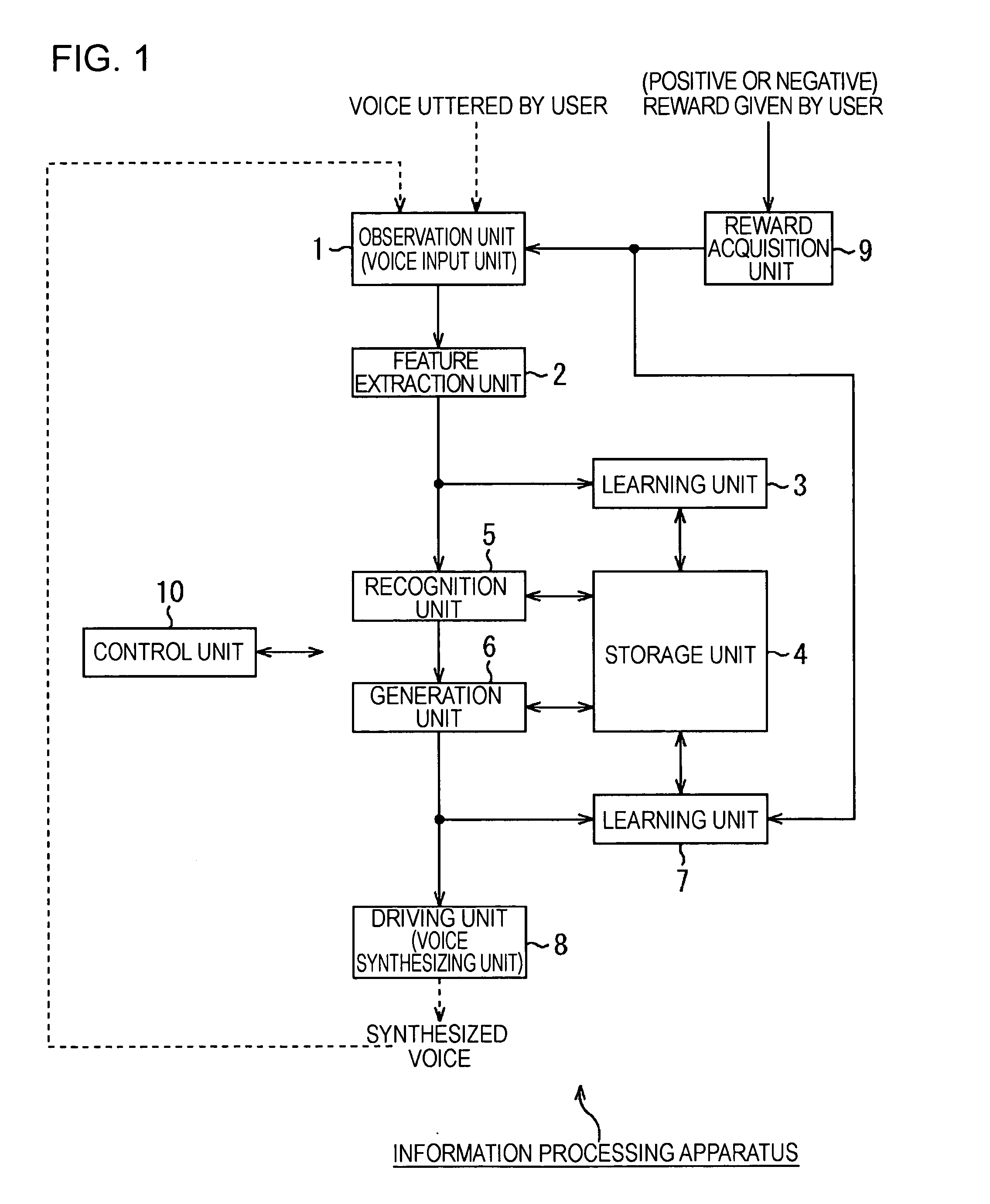
Information processing apparatus, information processing method, and program
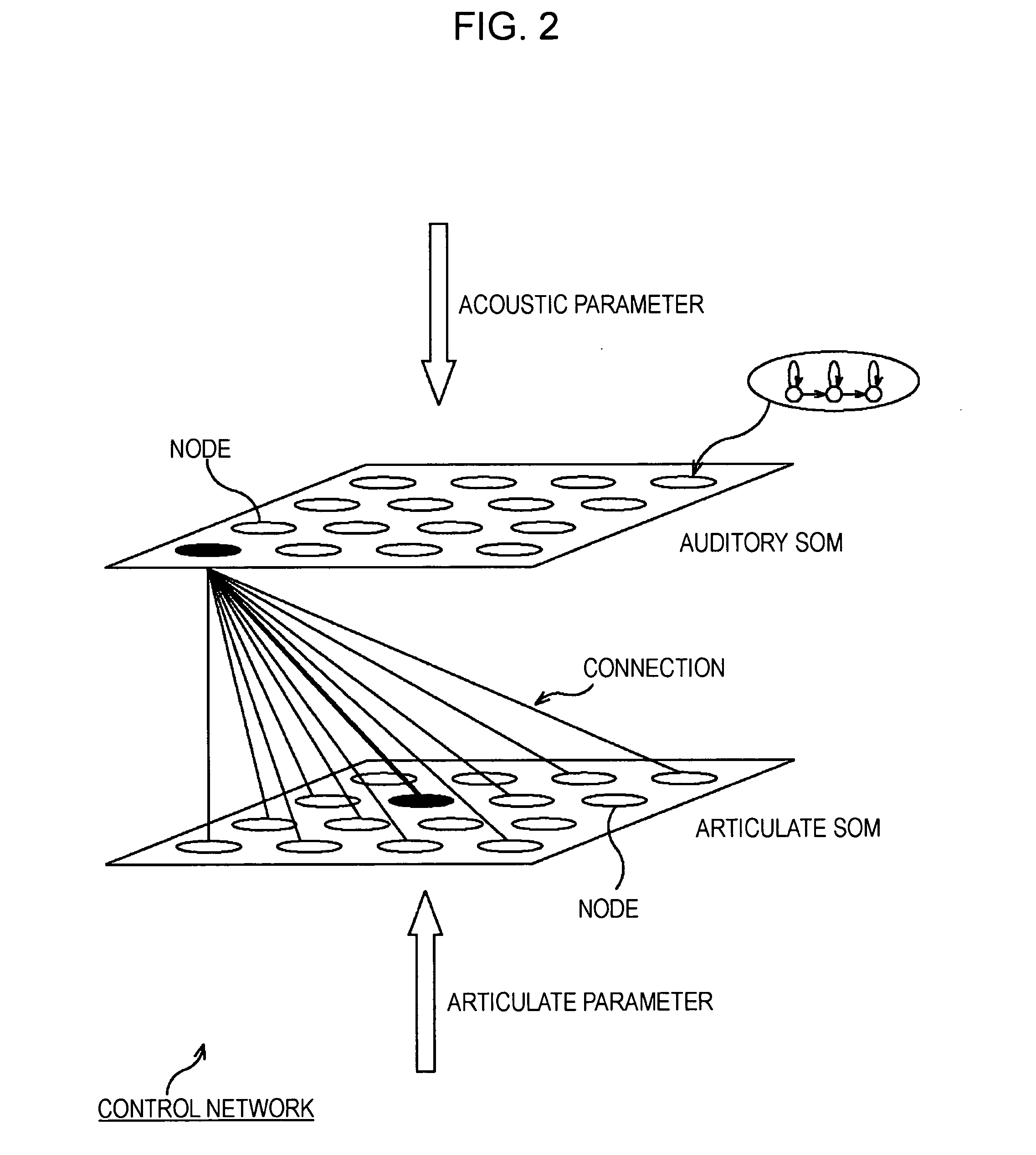
An information processing apparatus includes a first learning unit adapted to learn a first SOM (self-organization map), based on a first parameter extracted from an observed value, a winner node determination unit adapted to determine a winner node on the first SOM, a searching unit adapted to search for a generation node on a second SOM having highest connection strength with the winner node, a parameter generation unit adapted to generate a second parameter from the generation node, a modification unit adapted to modify the second parameter generated from the generation node, a first connection weight modification unit adapted to modify the connection weight when end condition is satisfied, a second connection weight modification unit adapted to modify the connection weight depending on evaluation made by a user, and a second learning unit adapted to learn the second SOM based on the second parameter obtained when the end condition is satisfied.
Owner:SONY CORP
Visual support and match analysis system for ping-pong match and method for running same
InactiveCN101833232ASimplify referee operationsImprove playbackImage enhancementImage analysisLearning machineSimulation
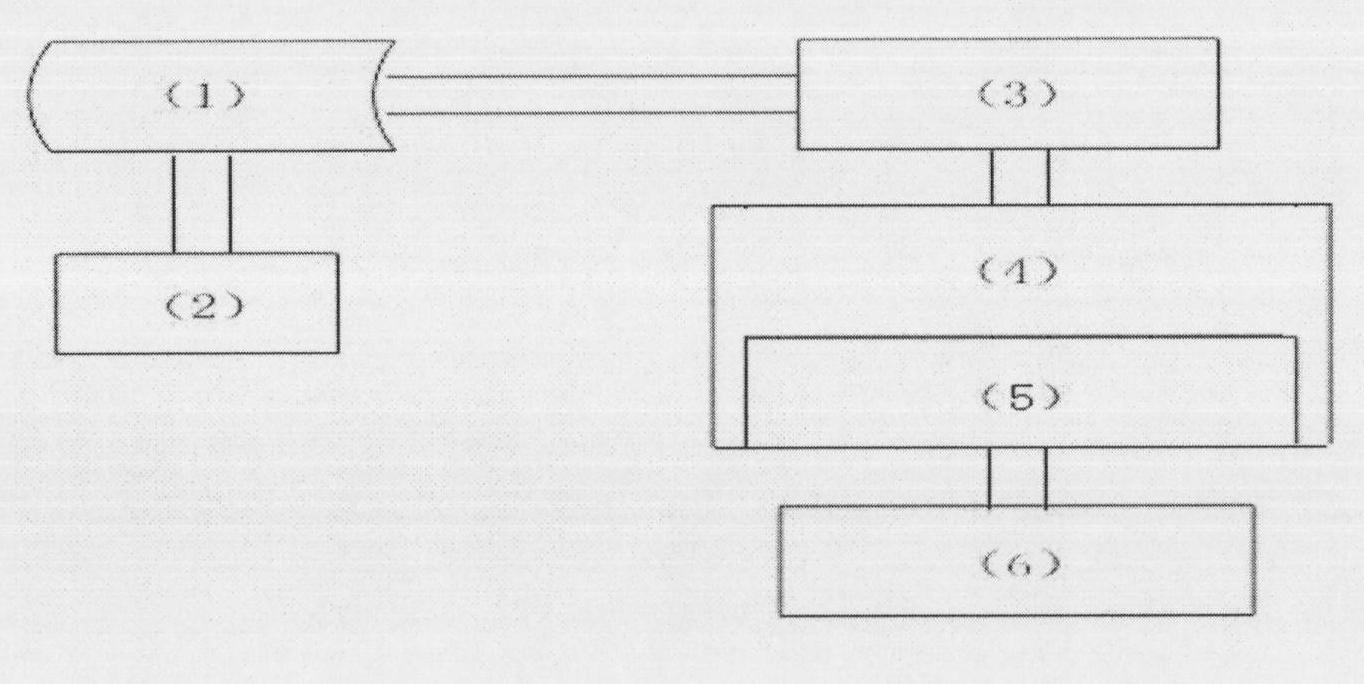
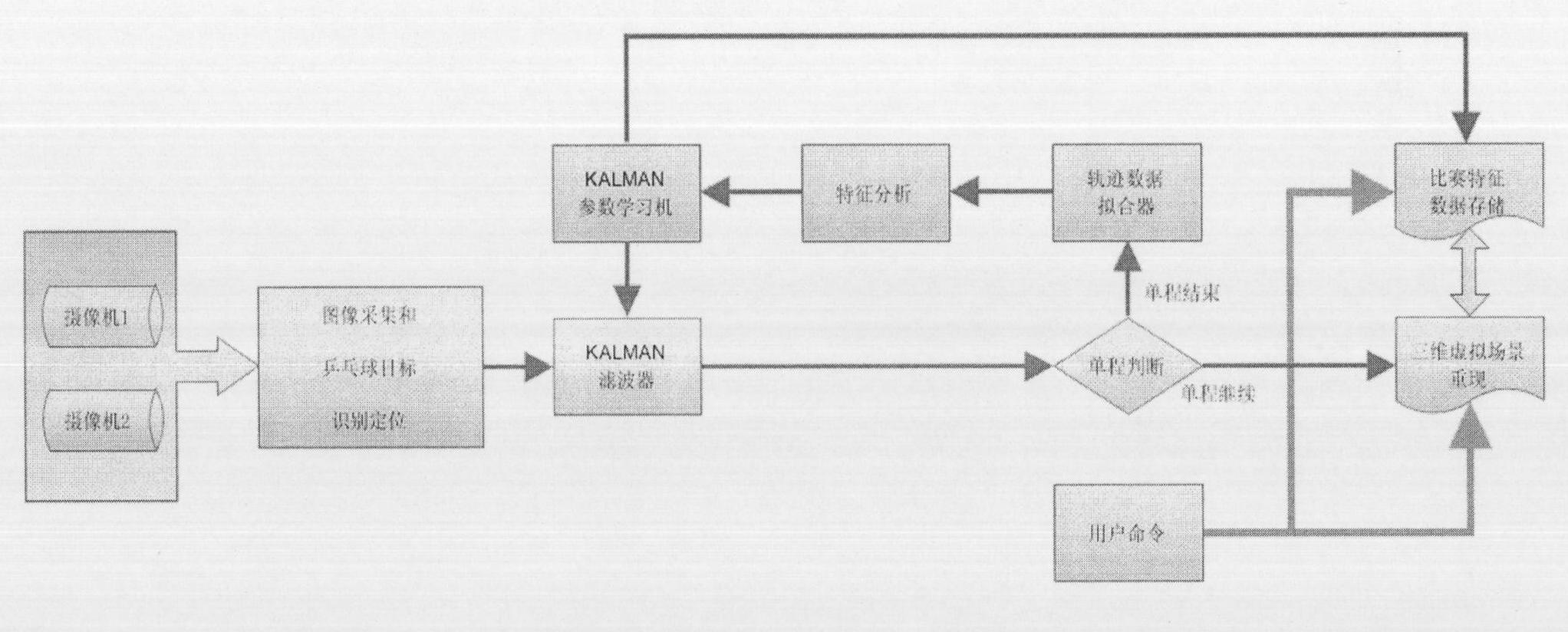
The invention provides a visual support and match analysis system for a ping-pong match. The system comprises the following modules: an image acquiring and ping-pong ball target recognizing and positioning module, a KALMAN filter module, a track data fitter module, a characteristic analyzing module, a kinematic parameter learning machine module, a single path judging module, a three-dimensional virtual scene reappearing module, a match characteristic data storing module and a user interaction module. A set of system with friendly and complete information extraction and storage, user interaction support and capability of performing track recording well and extracting characteristic information on ball hit of an athlete is developed through real-time visual acquisition. The system can process data in real time and filter and record the processed data in ping-pong trainings and matches, automatically extracts ping-pong ball path characteristic, bring convenience to a judge to replay, is applied to automatic judging and television relaying in the ping-pong match, has a complete, effective and overall analyzing function after the match and can automatically extract and store the characteristic information in a match process and intuitively counts and displays ball throwing and ball winning path characteristics of the ping-pong athlete.
Owner:ZHEJIANG UNIV
Deep learning network construction method and system applicable to semantic segmentation
InactiveCN107180430ADeep learning network is goodImprove robustnessImage enhancementImage analysisConditional random fieldLearning network
The invention discloses a deep learning network construction method and system applicable to semantic segmentation. According to the invention, based on the deconvolution semantic segmentation, by considering the characteristic that a conditional random field is quite good for edge optimization, the conditional random field is explained to be a recursion network to be fused in a deconvolution network and end to end trainings are performed, so the parameter learning in the convolution network and the recursion network is allowed to act with each other and a better integration network is trained; through combined training of the deconvolution network and the conditional random field, quite accurate detail and shape information is obtained, so a problem of inaccuracy of image edge segmentation is solved; by use of the strategy of combining the multi-scale input and multi-scale pooling, a problem is solve that a big target is excessively segmented or segmentation of a small target is ignored generated by the single receptive field in the semantic segmentation; and by expanding the classic deconvolution network, by use of the united training of the conditional random field and the multi-feature information fusion, accuracy of the semantic segmentation is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
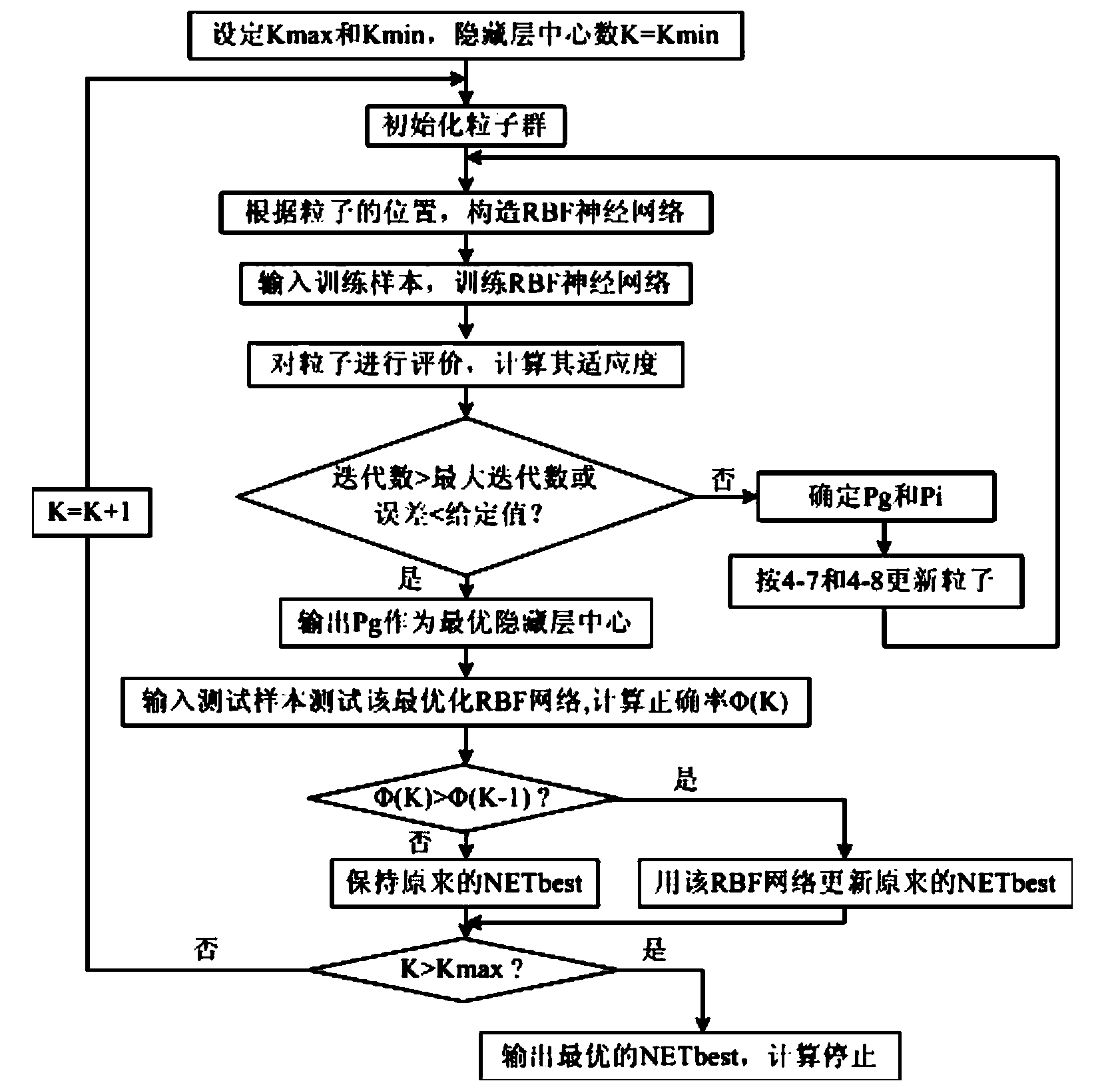
Method for diagnosing fault of transformer on basis of clustering algorithm and neural network
InactiveCN104299035AImprove diagnostic accuracyRich learningNeural learning methodsPattern recognitionGuideline
The invention discloses a method for diagnosing a fault of a transformer on the basis of a clustering algorithm and a neural network. The method comprises the following steps that (a) the type of the fault is determined according to an IEC standard and a DL / T722-2000 guideline, and the characteristic quantities of a fault sample set are selected from an original sample set; (b) clustering is carried out on samples by utilizing a K-means clustering method; (c) an RBF neural network is established; (d) parameter learning is carried out to determine the number, the center position, the width and the output weight of hidden layers; (e) optimization training is carried out by adopting PSO to determine the positions of the centers of the hidden layers, and the number, the width and the weight of the hidden layers are determined by utilizing a test method, a minimum distance method and a pseudo-inverse method respectively; (f) training samples are input, the posterior probability is solved, and the type of the fault is judged. According to the method for diagnosing the fault of the transformer on the basis of the clustering algorithm and the neural network, the training samples and the test samples can be evenly divided from the total samples, more complete test on the neural network can be carried out by good test samples, and therefore the neural network can be evaluated correctly and reasonably.
Owner:STATE GRID CORP OF CHINA +1
Method and system of electric automobile battery test
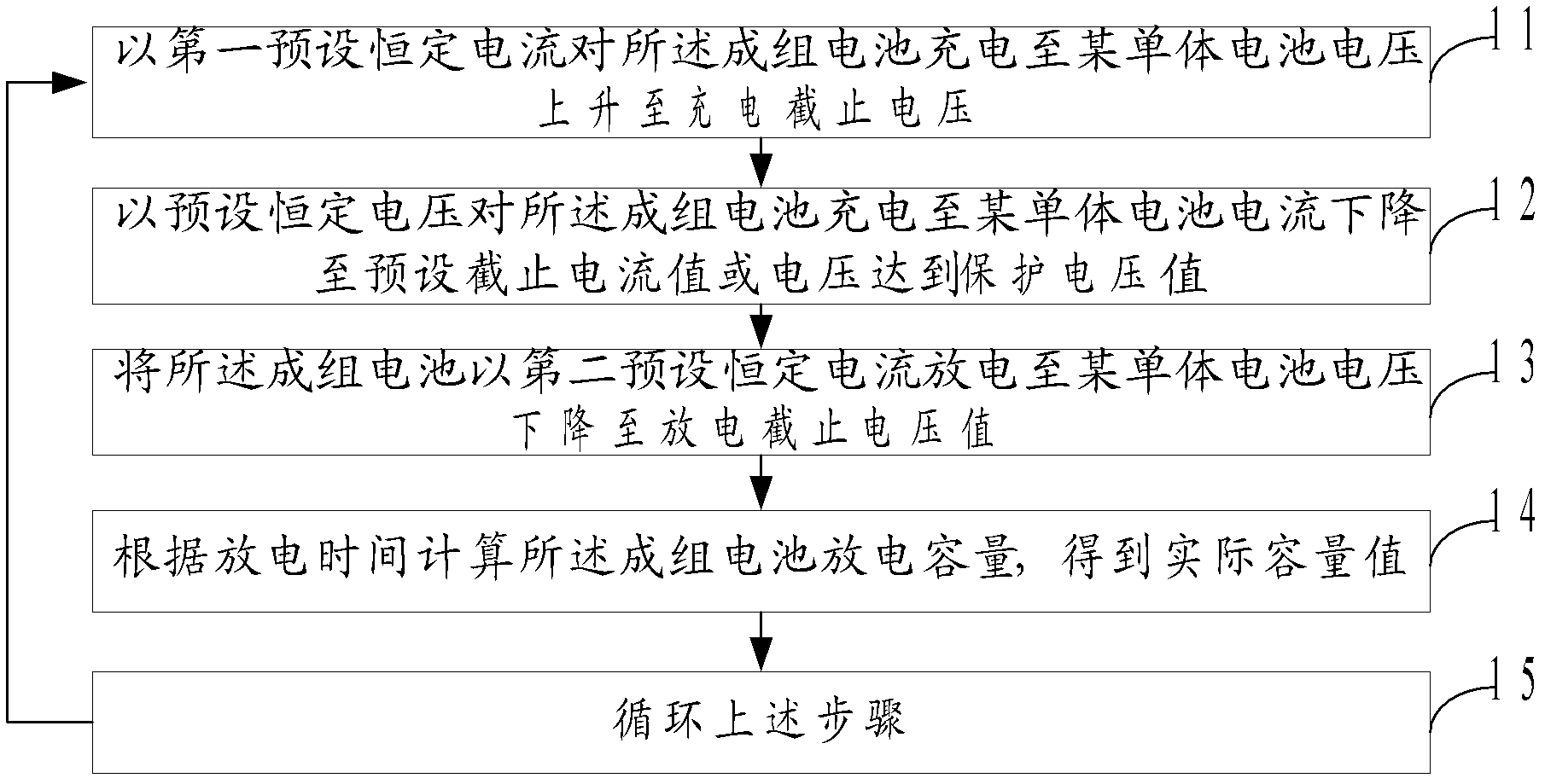
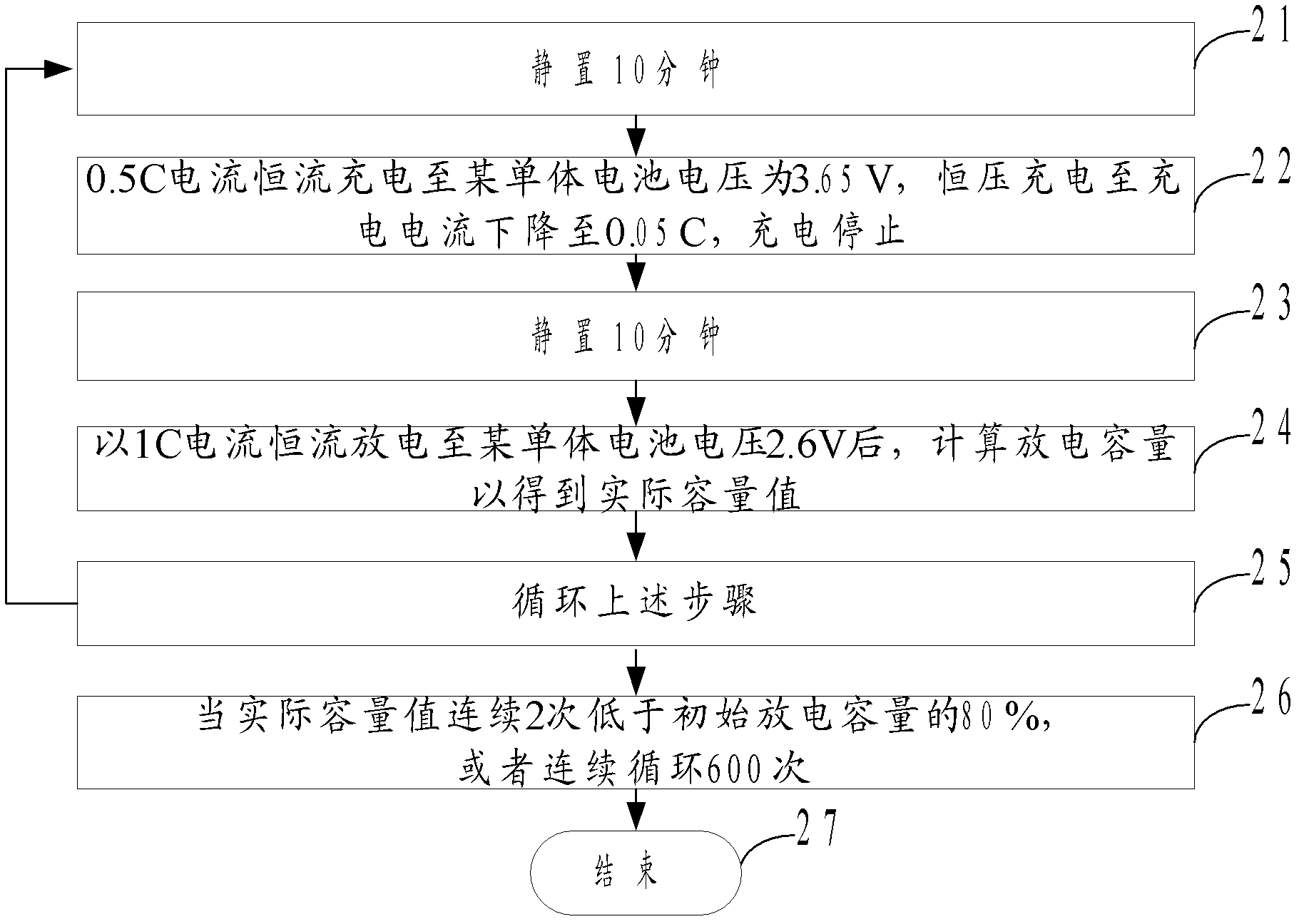
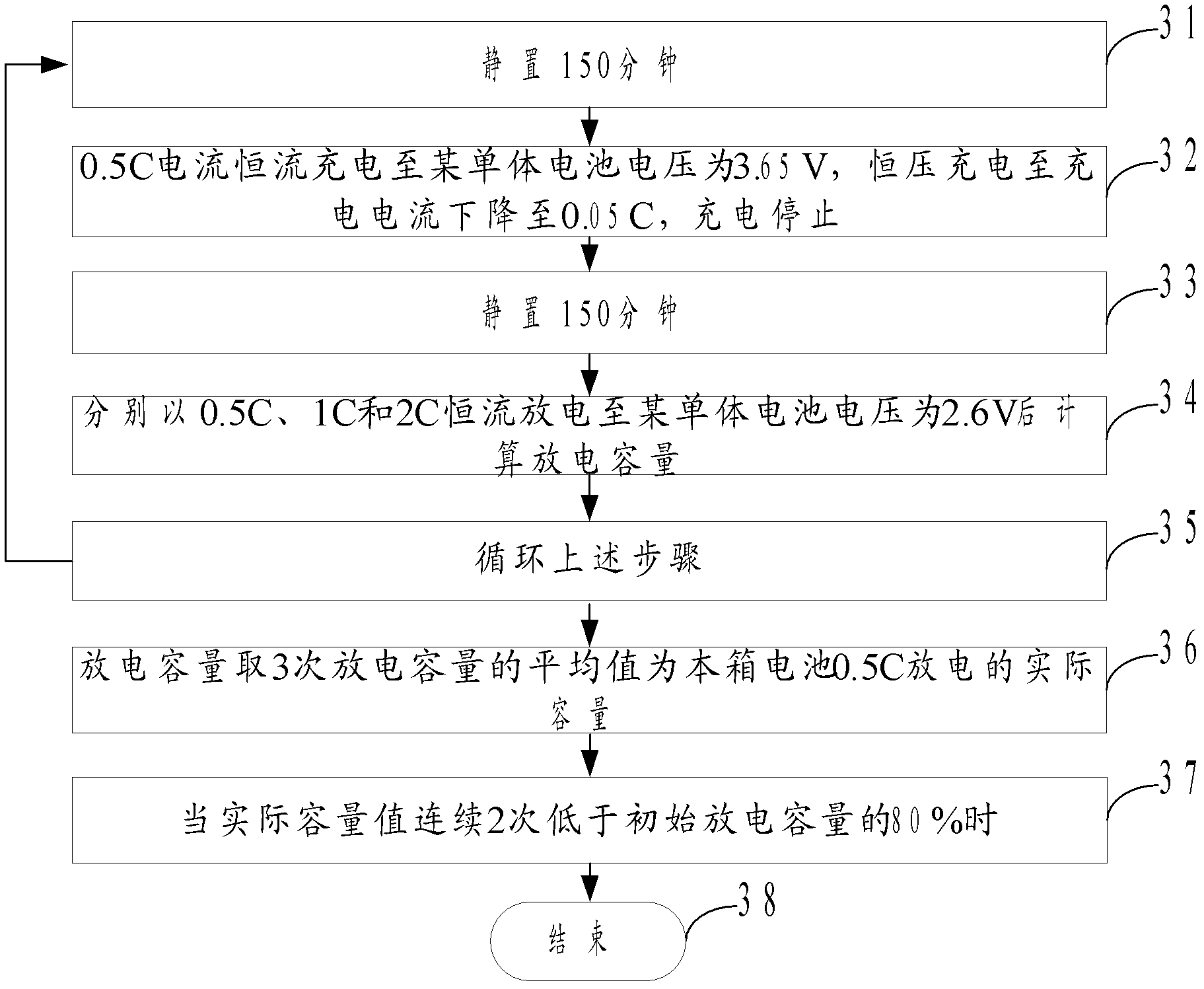
The invention discloses a method and a system of electric automobile battery test. The method comprises a test of ganged electric automobile batteries that a first preset constant current is used for charging the ganged electric batteries until voltage of a certain battery cell is built up to a max charge voltage value, preset constant voltage is used for charging the ganged electric automobile batteries until charging current is reduced to a preset cut-off current value or the voltage of a certain battery cell reaches a protection voltage value, a second preset current is used for discharging the ganged electric batteries until the voltage of a certain battery cell is reduced to a max discharge voltage value and an actual capacity value is obtained after the discharge capacity of the ganged batteries is calculated according to consuming time of discharge. The steps are circulated until the actual capacity value is less than a preset capacity value continuously for a plurality of times, or the steps are circulated until cycle-index reaches a preset number. Omni-directional test and parameter learning of a power battery is achieved. Reference is provided for follow-up application of the power battery.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD HANGZHOU POWER SUPPLY CO +2
Source node loophole detection method based on integrated neural network
InactiveCN104809069AAccurate and effective vulnerability detectionGuaranteed propertyBiological neural network modelsSoftware testing/debuggingSmall sampleAlgorithm
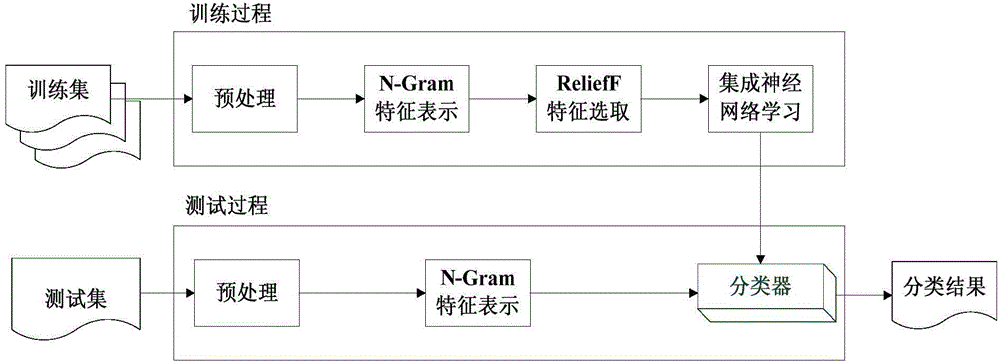
The invention provides a source node loophole detection method based on an integrated neural network. Source nodes are processed with an N-Gram algorithm, and a represented by an N-Gram set; implicit characteristics are mined from the N-Gram set with a probability statistics method, so that the attribute of code content is ensured, and the sequence correlation property among the codes is kept; characteristic selection is performed with a ReliefF algorithm to calculate a characteristic weight; specific to the aim of solving extreme imbalance of sample data, the functions of small type samples need to be fully considered during calculation, and different neighbor values are set for different types so that the characteristics of the small sample data can play certain roles in calculation; a multilayer feed-forward network is trained with a BP algorithm in the neural network for serving as individual networks, the trust scope of each individual network is learned through a series of parameter learning of identification rate, reject rate and the like with a DS evidence theory, and a final detection result is summarized according to different trust values of each network, so that accurate and effective source node loophole detection is realized.
Owner:CHINA ELECTRIC POWER RES INST +3
Monocular depth estimation method based on deep learning
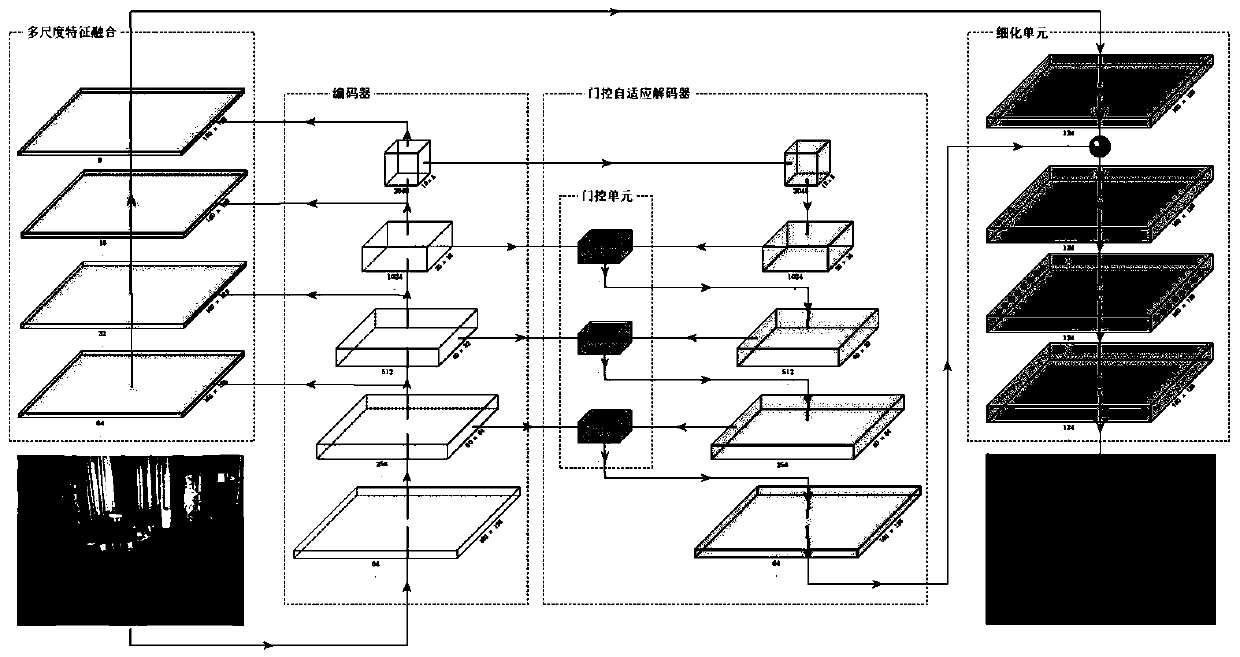
ActiveCN110738697AImproved depth reconstruction qualitySmall amount of calculationImage enhancementImage analysisData setBack propagation algorithm
The invention provides a monocular depth estimation method based on deep learning, and the method is based on an unsupervised convolutional neural network structure for monocular depth estimation, andcomprises an encoder, a multi-scale feature fusion module, a gating adaptive decoder, and a refinement unit. The method comprises the following steps: S1, preprocessing a data set; S2, constructing aloss function of the convolutional neural network, inputting a training set image, calculating a loss value of the loss function by using a back propagation algorithm, and performing parameter learning by reducing errors through repeated iteration to enable a prediction value to be close to a real value so as to obtain an optimal weight model of the convolutional neural network; and S3, loading the weight model trained in the step S2, and inputting the test set into an unsupervised convolutional neural network for monocular depth estimation to obtain a depth prediction image. The method solves the problems of large calculation amount during offline training and poor detail part recovery effect in deep reconstruction.
Owner:FUZHOU UNIV
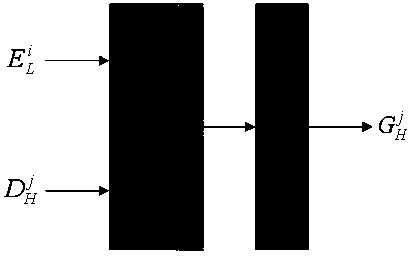
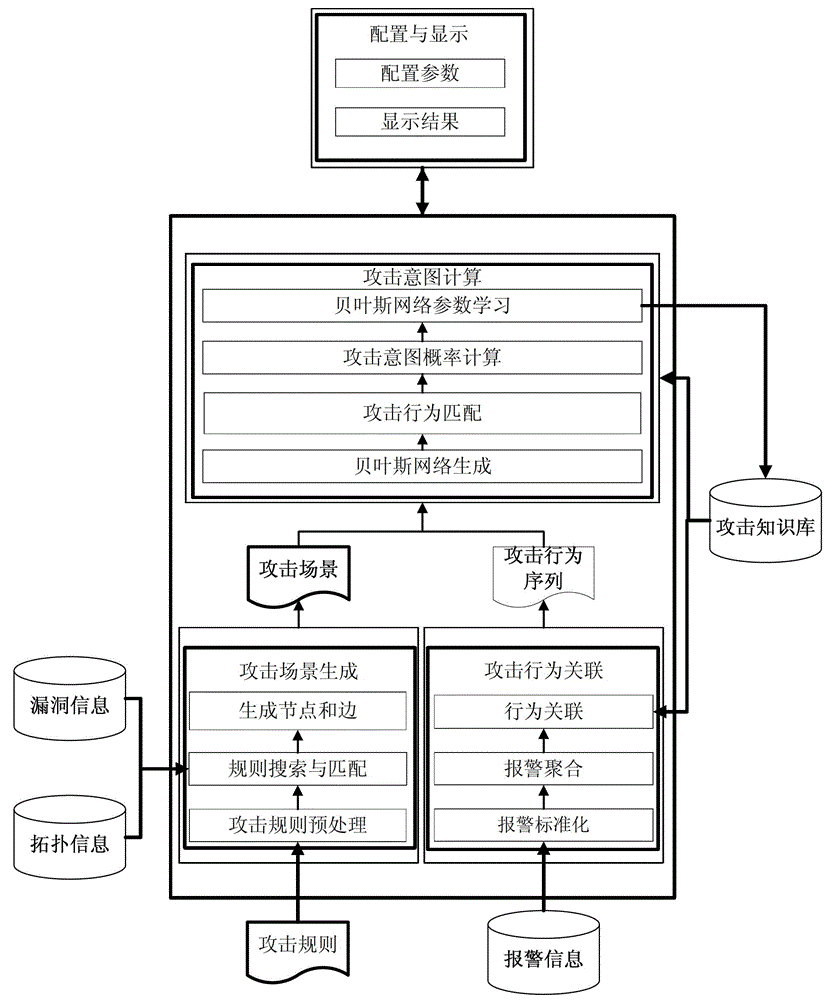
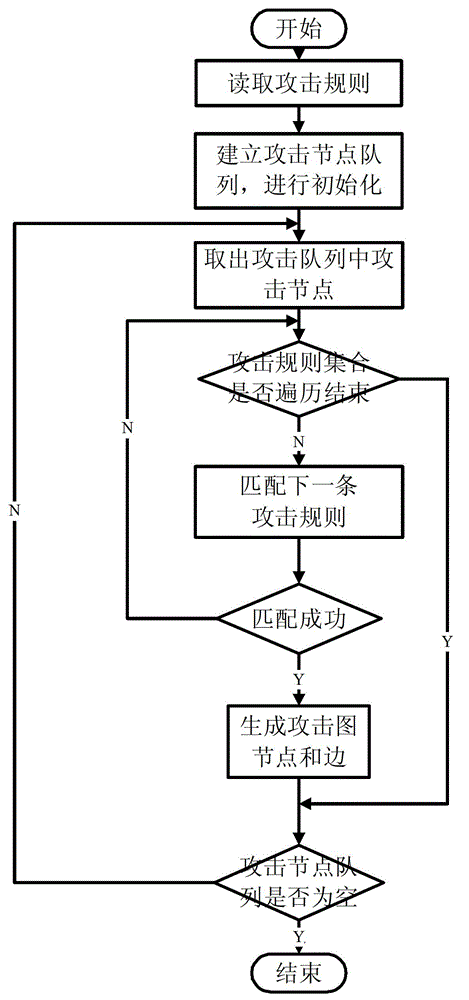
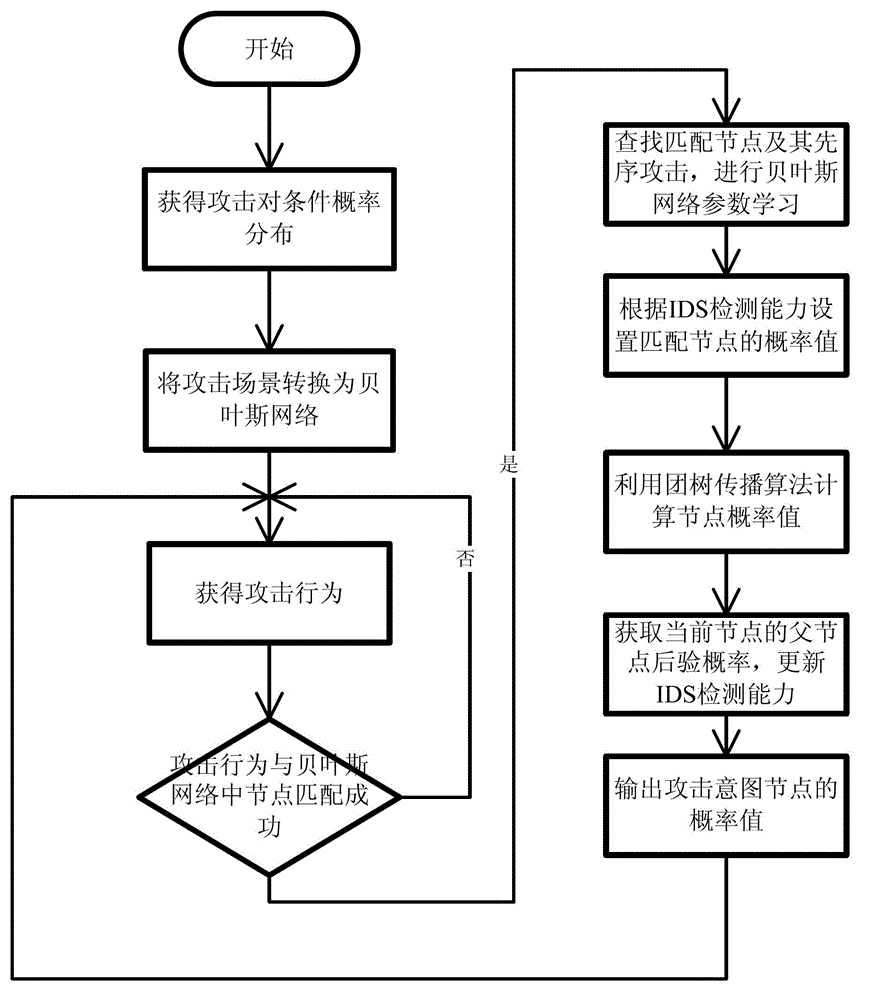
Attack intention recognition method based on Bayesian network inference
InactiveCN102724199AImprove scalabilityThe calculation result is accurateTransmissionPattern recognitionClique tree
The invention provides an attack intention recognition method based on Bayesian network inference. The attack intention recognition method is applied to the attack intention recognition of an intelligence and decision-making oriented system with a parameter learning mechanism in computer network self-organizing operation (CNSOO). The method can enable an intelligence system to recognize the attack intention of an attacker by using IDS (Intrusion Detection System) alarm information according to given host vulnerability information, network topological information and attack knowledge base and supply the attack intention to a decision-making system as a decision-making basis in a CNSOO environment. The attack intention recognition process comprises the following steps of: generating attacking scenes, fusing and matching IDS alarm information, updating conditional probability distribution caused by attacking behaviors, calculating the probability of attack intention nodes by using a clique tree propagation algorithm in the Bayesian network inference, and updating Bayesian network parameters and IDS detection capability. The calculation parameters are updated according to calculation results and historical information, so that the calculation results can be more accurate.
Owner:BEIHANG UNIV
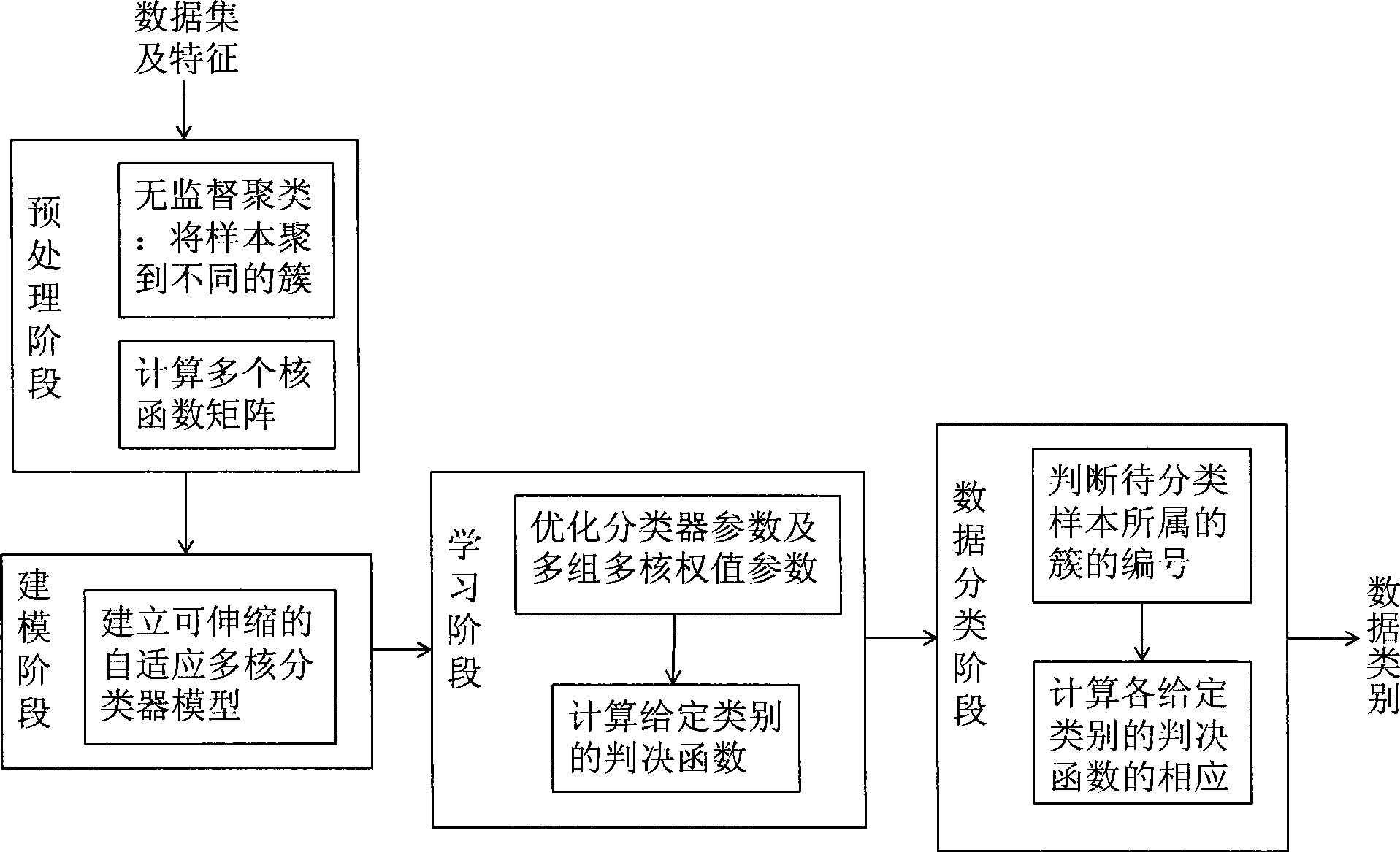
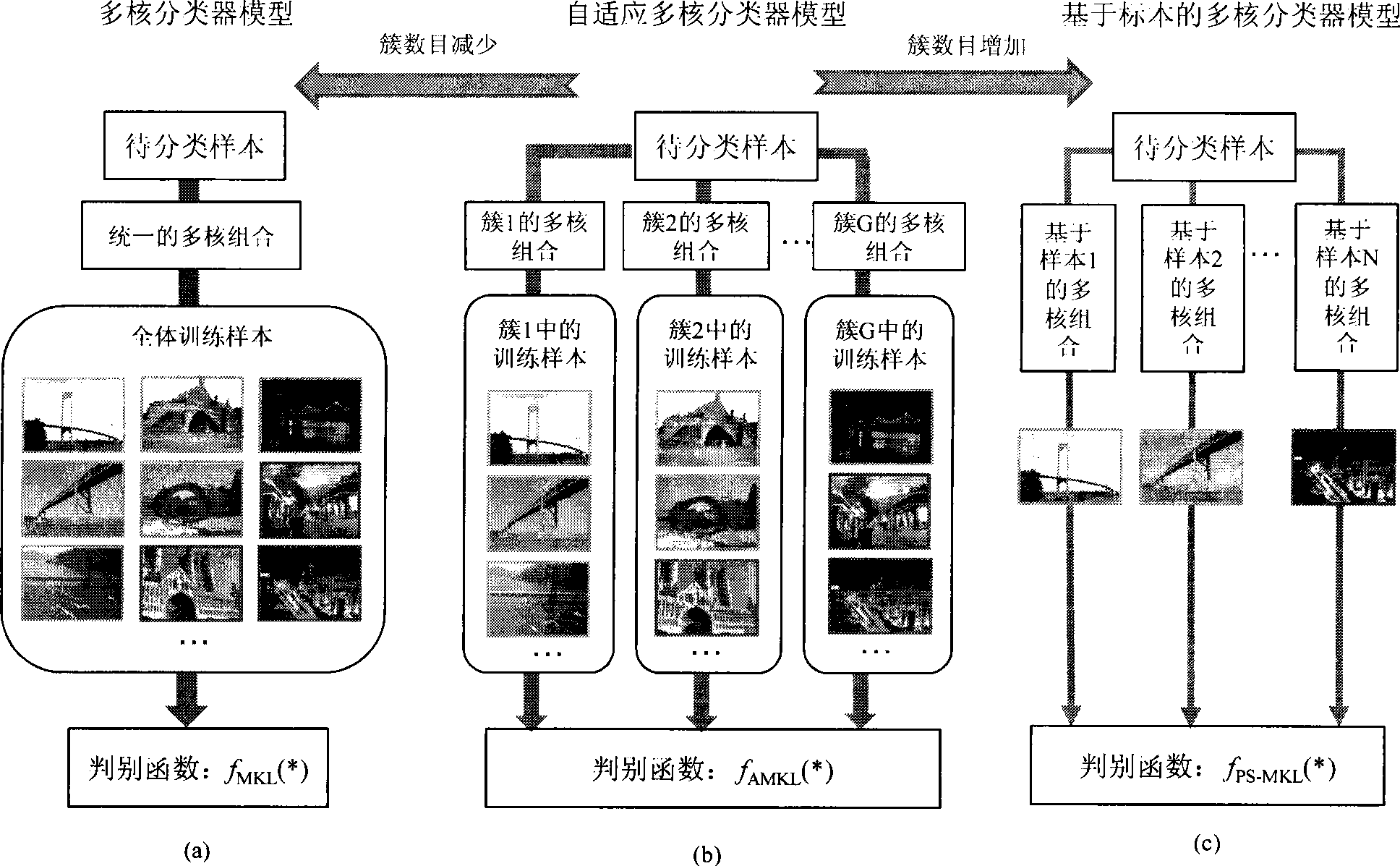
Extensible self-adapting multi-core classification method
InactiveCN101482926AAdaptableOptimizing Classifier ParametersCharacter and pattern recognitionData setClassification methods
A self-adaptive multi-core classification method relates to the field of artificial intelligence, especially to data mining technology. In a pre-processing phase, a multi-core matrix is obtained; in a modelling phase, a multi-core classifier relating to a cluster is built; in a parameter learning phase, classifier parameters and plural groups of multi-core weighting parameters are optimized in a uniform frame; in a data classifying phase, which cluster a sample to be classified belongs to is determined, and data are classified by the classifier having been studied. Correlation between classes and diversity in a class of complex data sets are mined by inducing medium expressing clusters in the invention; self adaptation relating to clusters and plural groups of multi-core classifiers are built; and the classifier parameters and plural groups of multi-core weighting parameters are optimized in a uniform studied frame by means of iteration. Problems on data classifications with many classes and complex features and on mixed data caused by correlation between classes and diversity in a class are solved; accuracy of classification is improved and classification effect is better.
Owner:PEKING UNIV
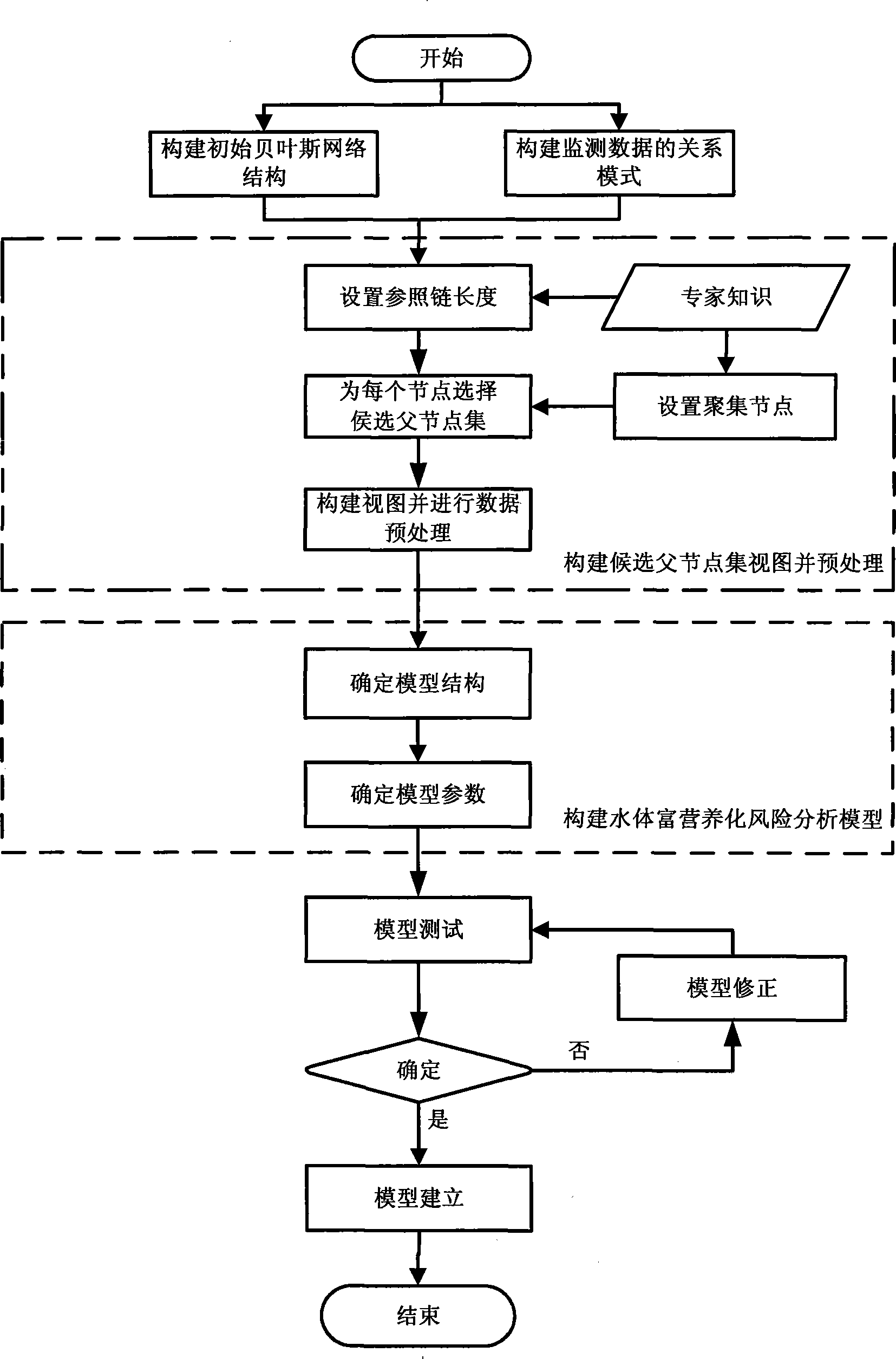
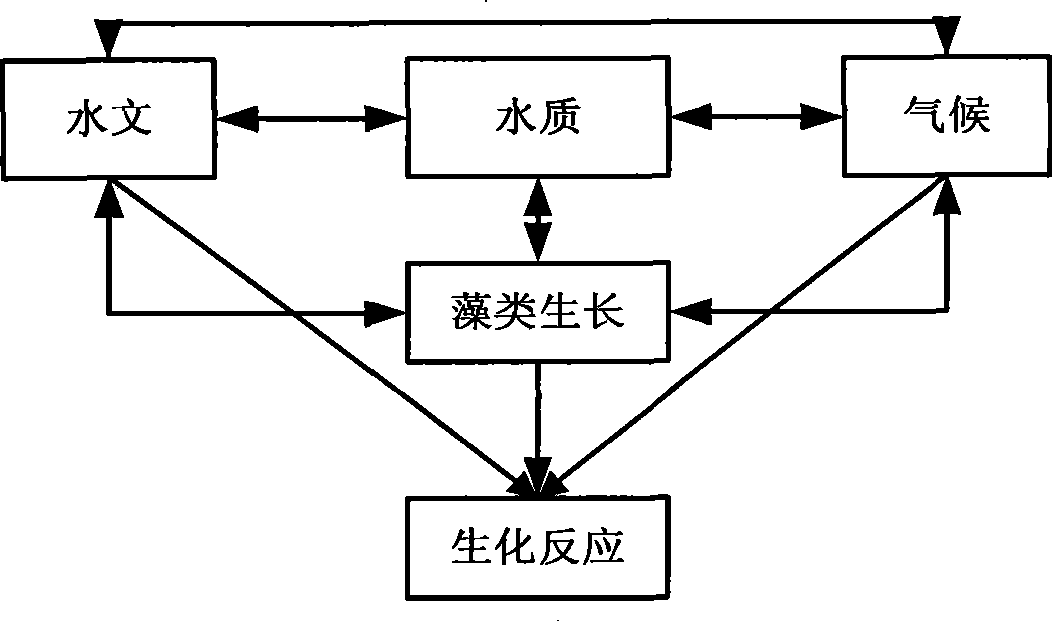
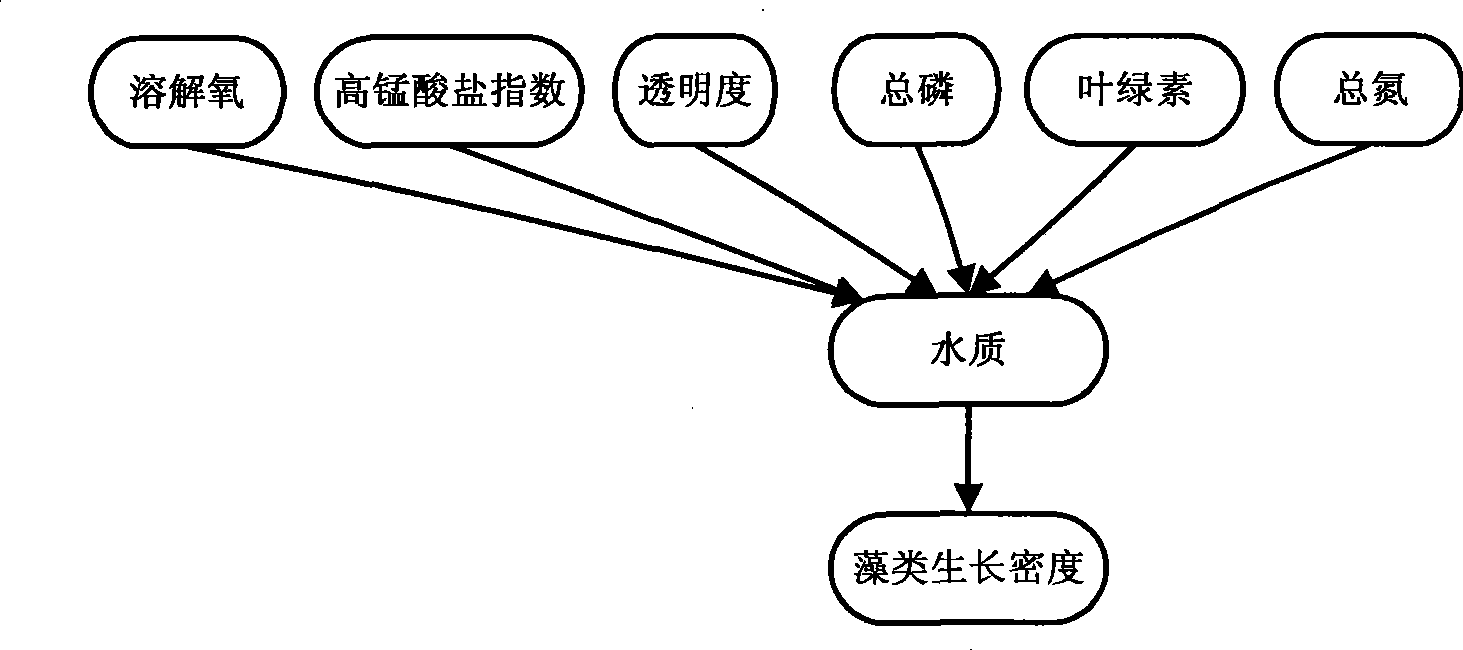
Method for constructing water eutrophication risk analysis model
InactiveCN101533000AEasy to explainEasy to analyzeGeneral water supply conservationTesting waterEutrophicationWater quality
The invention discloses a method for constructing water eutrophication risk analysis model, referring to a prediction / pre-warning method of water quality eutrophication risks. In terms of information technique, this invention includes: firstly creating Bayes network topology structure of water eutrophication risk analysis model via computer programmes in accordance with storage structure and stored content of respective monitoring data in water environment information system; analyzing various influencing factors and correlation causing the water eutrophication risks in adoption of parameter learning; lastly, generating a model via test and modification. Accordingly, the method of this invention takes various influencing factors and correlations thereof into consideration, thereby better analyzing degree of water eutrophication risk, realizing prediction / pre-warning of water eutrophication, and providing foundation of scientific decision to water environment management and water pollution control. As a result, this invention can be widely applied to water eutrophication risk analysis as well as prediction / pre-warning of rivers and lakes, in particular to water eutrophication risk tendency analysis and prediction of the Three Gorges Reservoir area.
Owner:CHONGQING UNIV +2
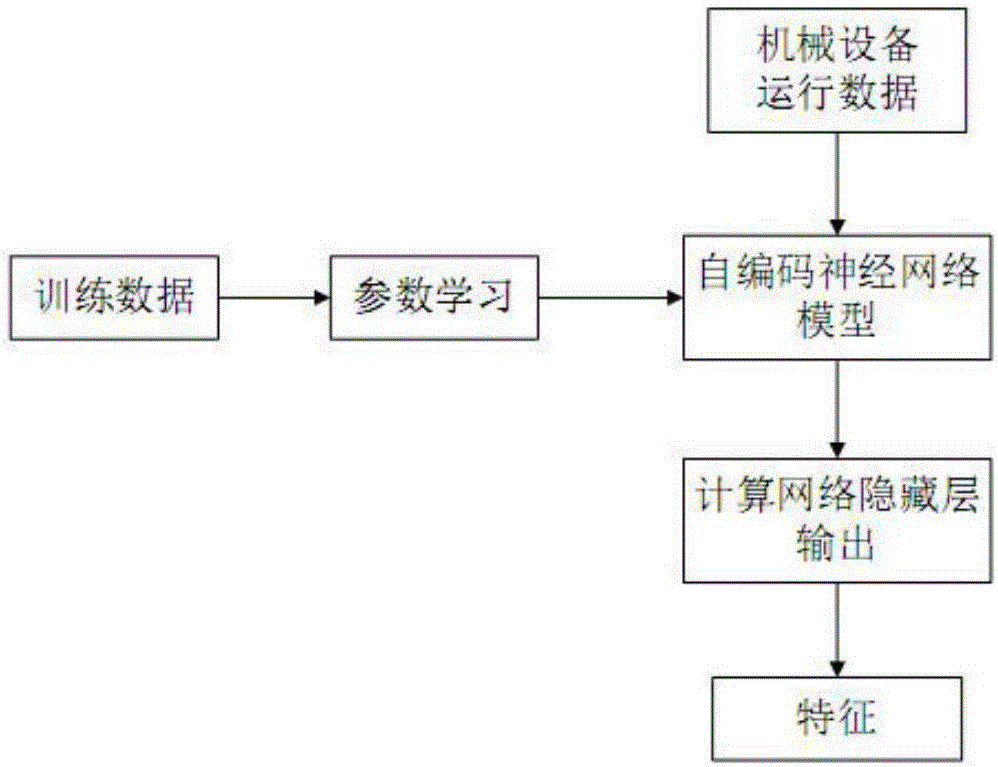
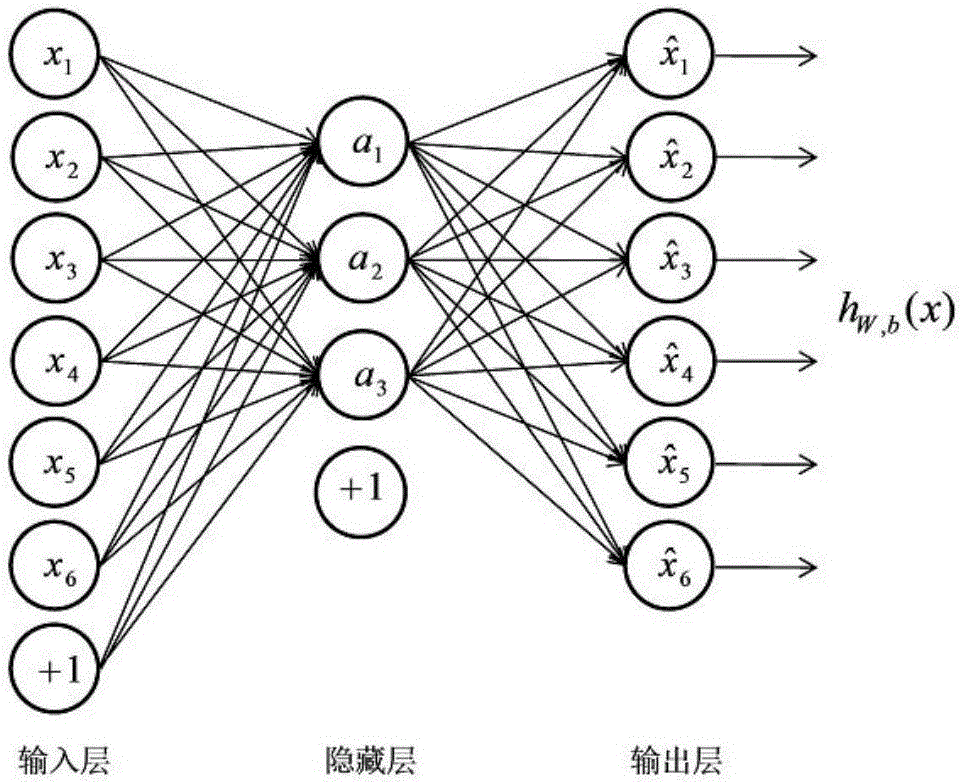
Non-supervision feature extraction method based on self-coding neural network
The invention provides a non-supervision feature extraction method based on a self-coding neural network. According to the method, firstly, training data matrix building is performed; then, each component value of a training data matrix is normalized to a position between [0,1]; next, parameter study is performed to obtain a self-coding neural network model; then, the output of a hidden layer is calculated; features are obtained; finally, the number of optimum hidden layer nerve cells is determined according to a halving value taking method; finally, a structure of the self-coding neural network is determined. In the network training study, the expected output of the self-coding neural network is specified to be equal to the input of the network; through such a study target, the providing of the expected network output by training data is not needed in the training process of the self-coding network training process. The method provided by the invention has the advantages that under the condition of being lack of priori knowledge, an internal rule of the equipment mass state data can be excavated and features can be extracted.
Owner:XI AN JIAOTONG UNIV
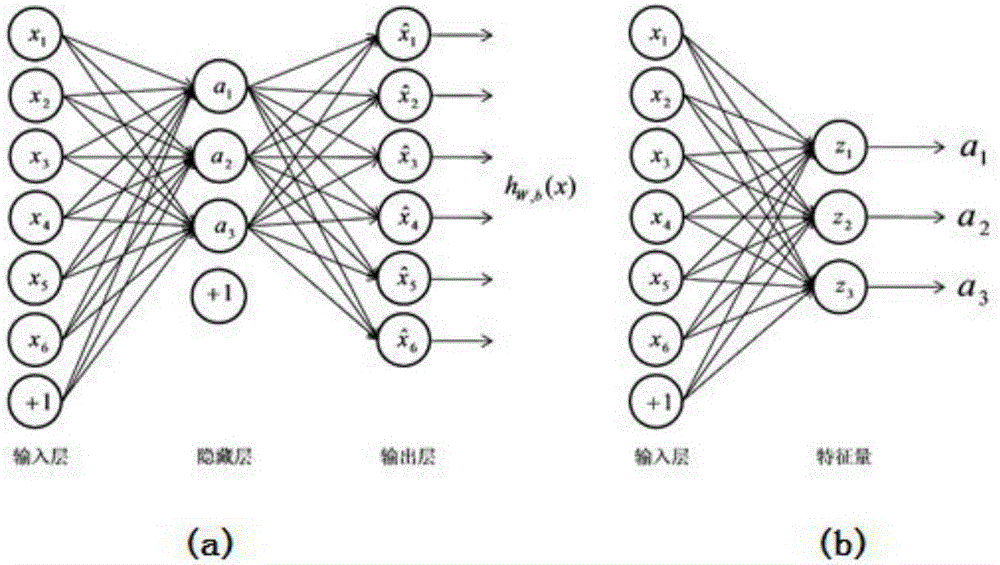
Pattern identification method, parameter learning method and apparatus
ActiveUS20090089235A1Increase speedImprove accuracyDigital computer detailsCharacter and pattern recognitionCharacteristic spaceStudy methods
In a pattern identification method in which input data is classified into predetermined classes by sequentially executing a combination of a plurality of classification processes, at least one of the classification processes includes a mapping step of mapping the input data in an N (N≧2) dimensional feature space as corresponding points, a determination step of determining whether or not to execute the next classification process based on the corresponding points, and selecting step of selecting a classification process to be executed next based on the corresponding points when it is determined in the determination step that the next classification process should be executed.
Owner:CANON KK
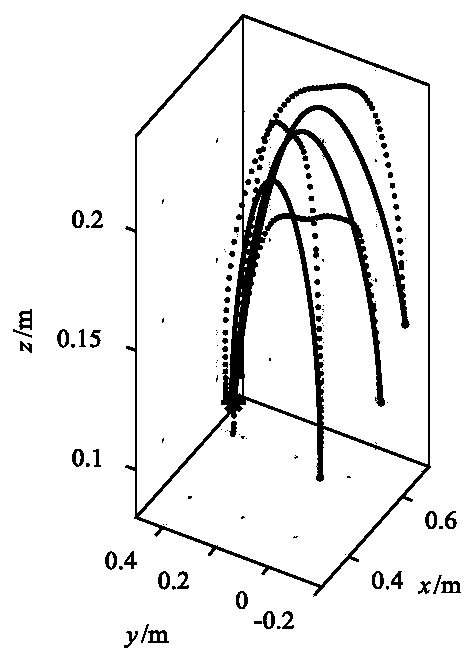
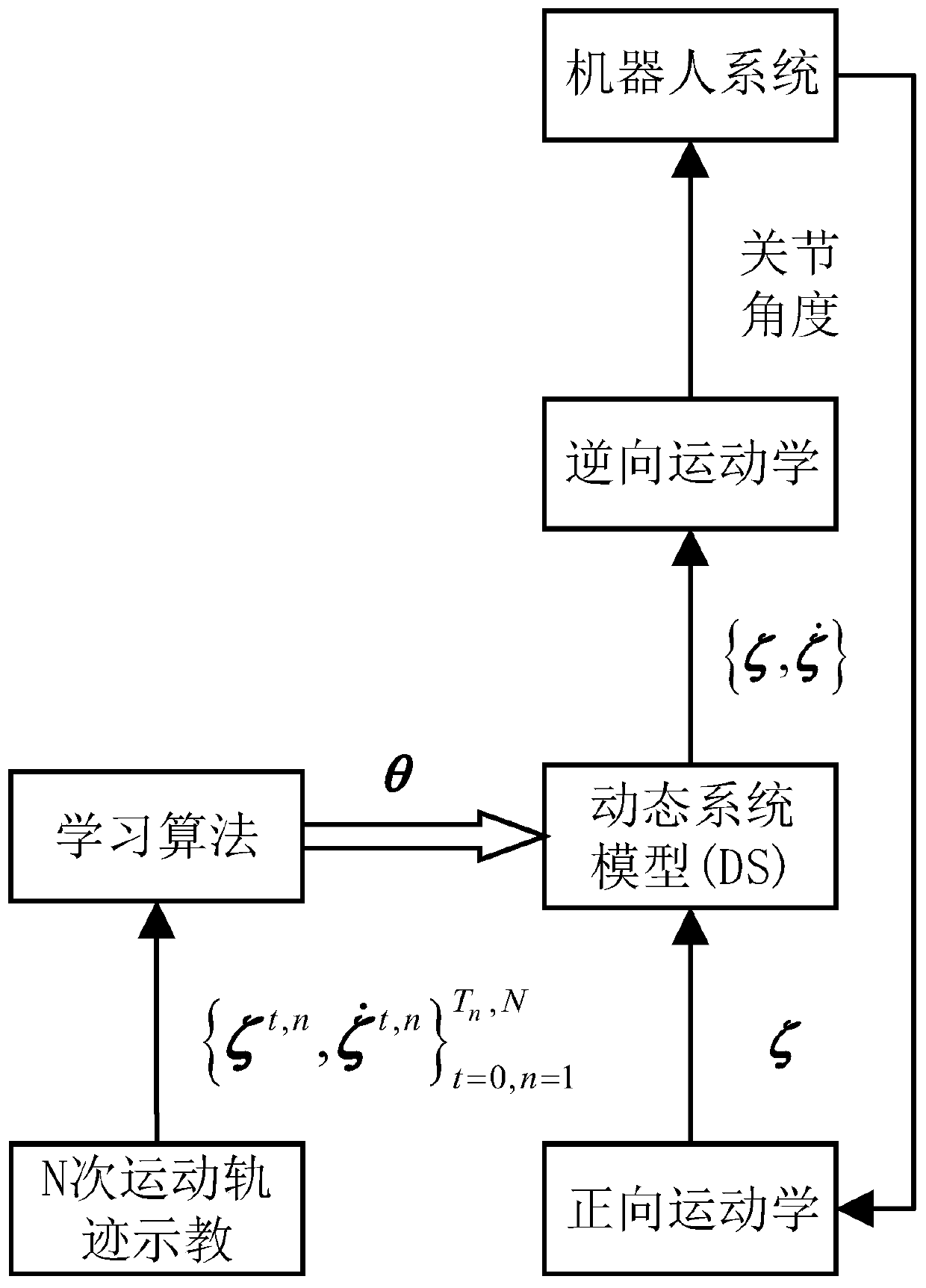
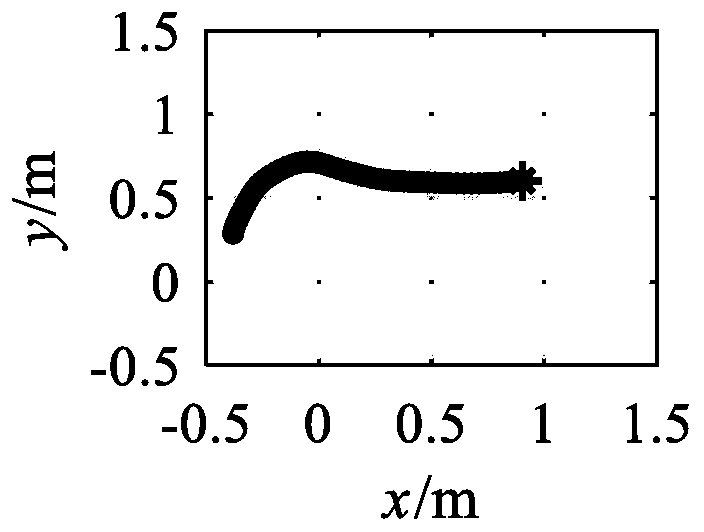
Robot simulation learning method based on dynamic system model
The invention discloses a robot simulation learning method based on a dynamic system model. Simulation of teaching movement of the robot is achieved through learning, specifically, the demonstration motion is modeled into a nonlinear dynamic system model through a gaussian mixture model, in addition, the stability of the motion model is guaranteed through the method with the additional stability constraint conditions, the parameter learning problem of the motion model is converted into a constraint optimization problem, so that a complete description of the motion model is obtained, and finally, the motion model obtained through learning is used as a control strategy to guide the robot to imitate the teaching motion. The method is used for teaching motion of target point fixation, the method has good stability, all the generated motion trails are converged to a target point, and has good expression capacity for simple and complex teaching movement, the generalization ability of the motion model is good, a motion track which is smooth and can be converged to a target can be generated outside the teaching movement range.
Owner:BEIJING UNIV OF TECH
Scene text identification method based on Bayesian probability frame
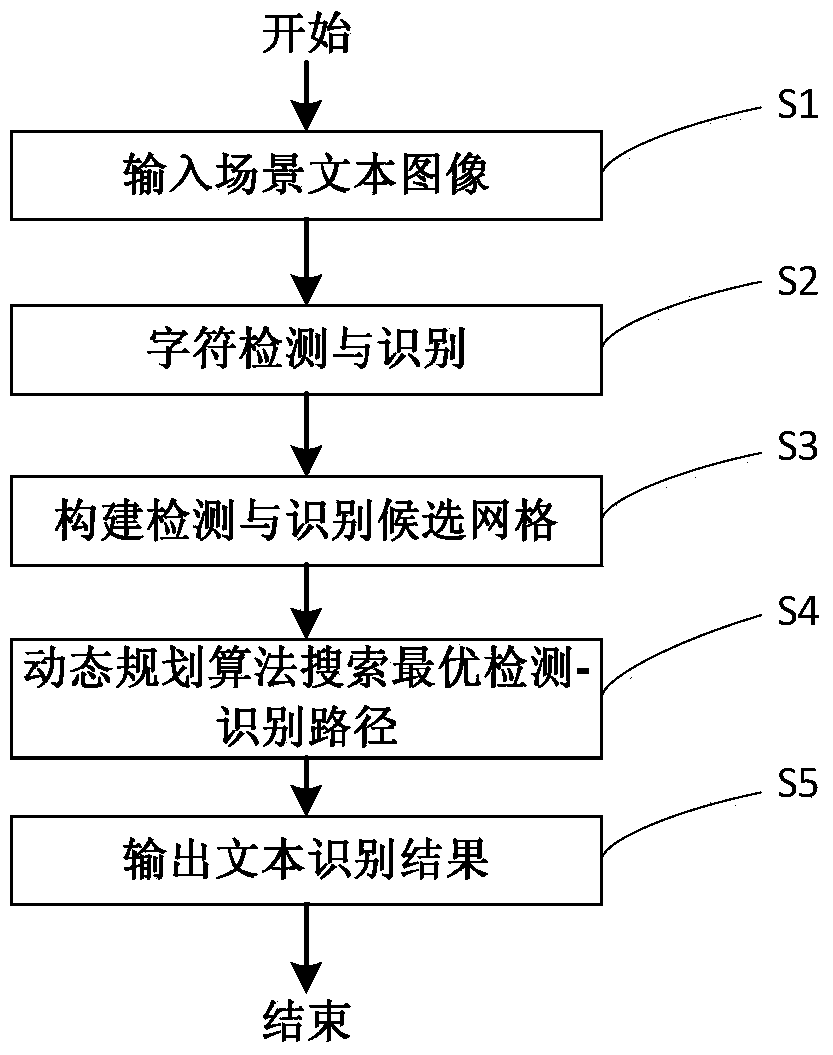
ActiveCN103984943AImprove recognition rateEfficient integrationCharacter and pattern recognitionText detectionDynamic planning
The invention discloses a scene text identification method based on a Bayesian probability frame, and relates to vision and mode identification of a computer. The scene text identification method based on the Bayesian probability frame comprises the steps that S1, scene image text is input; S2, character detection and recognition are carried out; S3, a detection-identification candidate grid is built, particularly, a candidate character area, a corresponding character class and a corresponding identification score are stored in the detection-identification candidate grid, each detection-identification route in the detection-identification candidate grid corresponds one text detection and identification result, and a route evaluation function is designed to evaluate each detection-identification route in the candidate grid; S4, the best detection-identification route is searched for from the candidate grid through a dynamic planning algorithm, that is to say, the identification result is obtained; S5, the text identification result is output. The scene text identification method based on the Bayesian probability frame achieves probability modeling and parameter learning of scene text identification integrating detection and identification.
Owner:XIAMEN UNIV
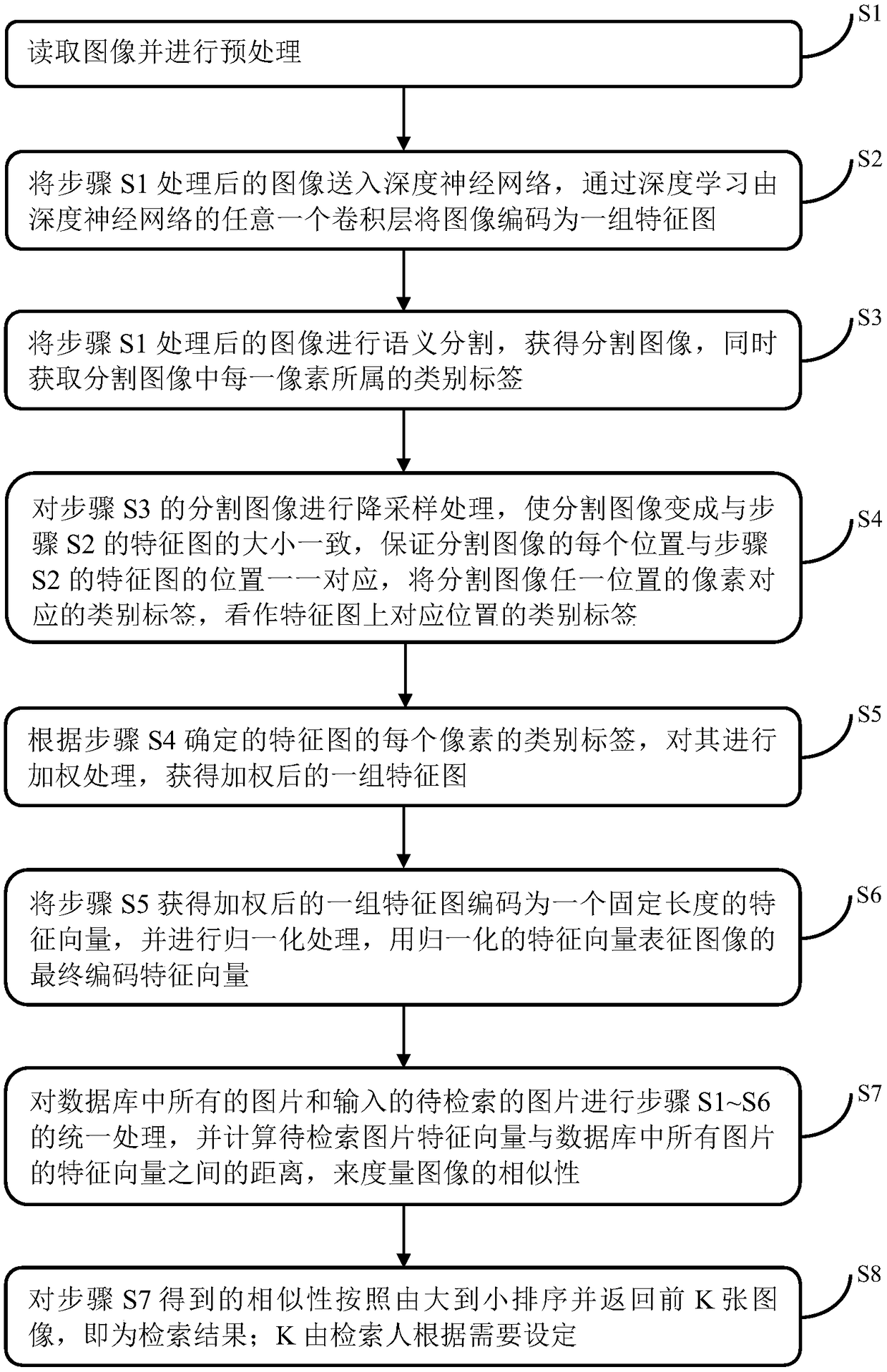
Image retrieval method based on depth learning and semantic segmentation
ActiveCN108829826ACalculation speedImprove performanceCharacter and pattern recognitionNeural architecturesFeature vectorImage retrieval
The invention discloses an image retrieval method based on depth learning and semantic segmentation, which comprises the following steps of: reading an image and preprocessing the image; encoding theimage into a set of characteristic graphs through depth learning by any convolution layer of the depth neural network; carrying out semantic segmentation on the image to obtain a category label of each pixel of the segmented image; carrying out weighting processing on the category labels according to each pixel category label on the characteristic graphs and the set category weight to obtain a setof weighted characteristic graphs; coding the set of weighted characteristic graphs to a feature vector of a fixed length, and carrying out normalization processing, and characterizing the final coded feature vector of the image by using a normalized characteristic vector; carrying out similarity calculation and returning the search result. According to the invention, the semantic segmentation technology is introduced into the feature code of image retrieval, and the retrieval effect is greatly improved. When the weight of each category of the image is acquired, the provided manual design method based on the prior knowledge and parameter learning method of the depth neural network are very effective.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
A method for constructing knowledge base of wireless cognitive network based on Bayesian network
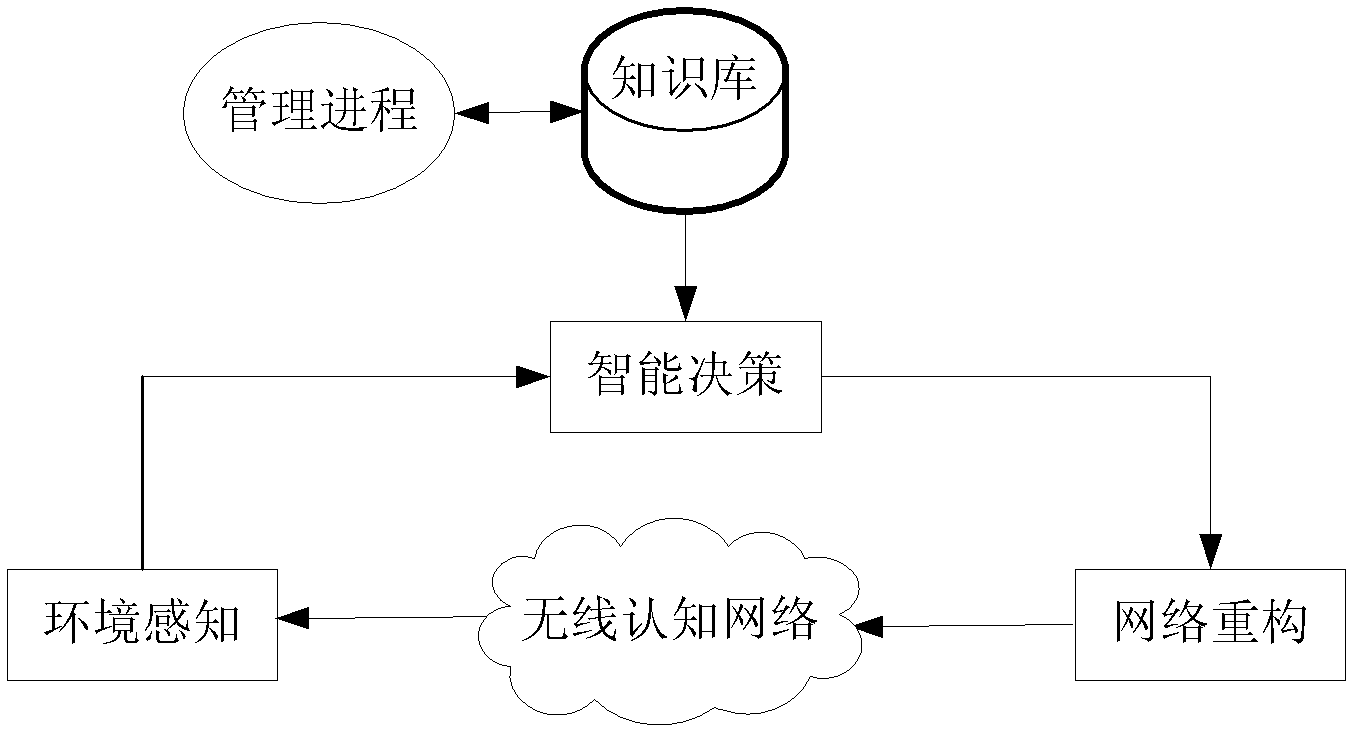
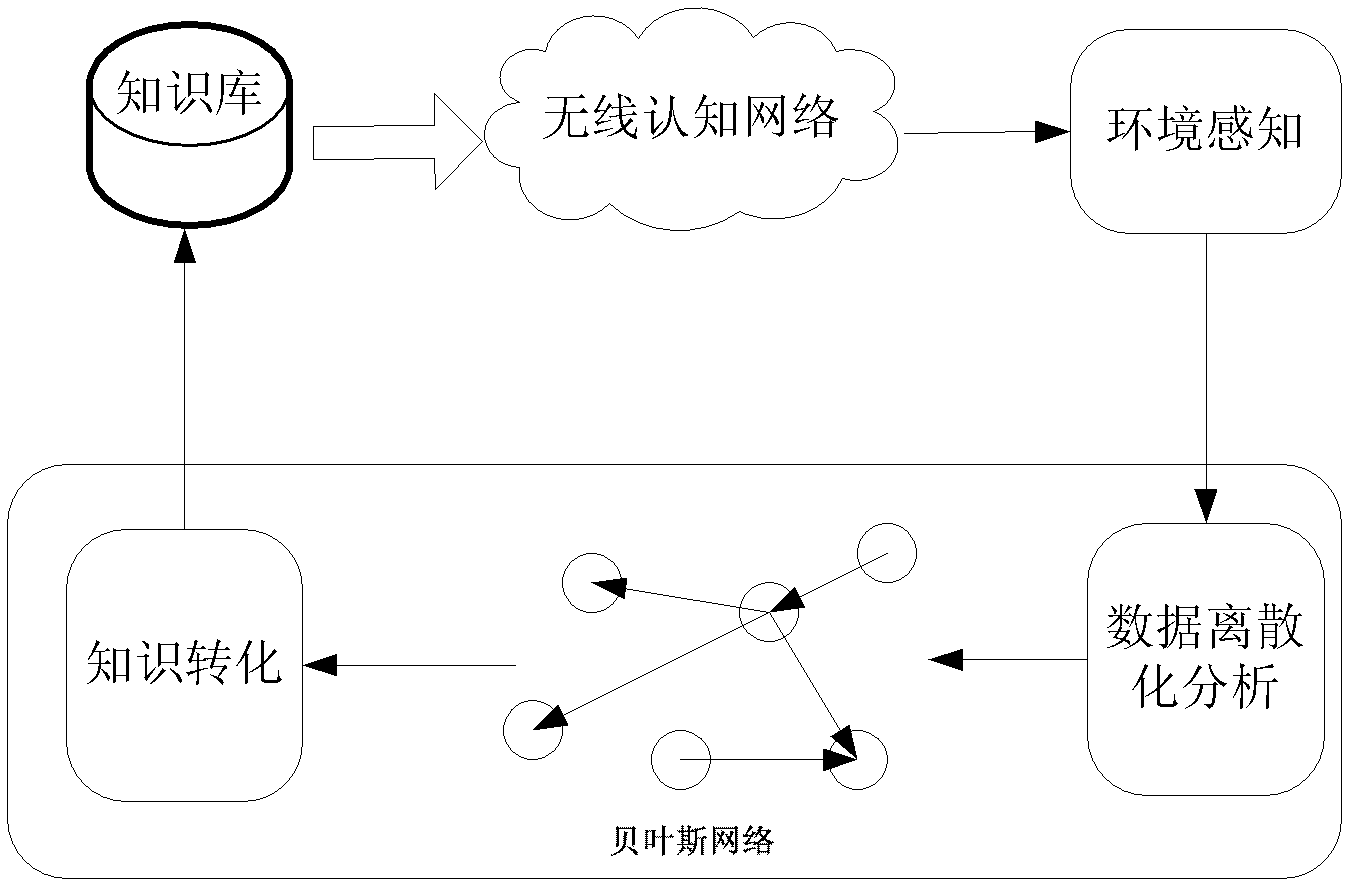
InactiveCN102289496AEmphasize the importanceImplement updateMathematical modelsSpecial data processing applicationsGaussian network modelStructure learning
The invention discloses a wireless cognitive network knowledge base constructing method based on a Bayesian network. A Bayesian network model is constructed by using perceived network performance parameters, so that the dependence among the parameters is obtained, and the conditional probability dependence is transformed into knowledge in a wireless cognitive network to be stored in a knowledge base for guiding a process of intelligent decision making. The process of constructing the knowledge base mainly comprises the steps of: perceiving the network performance parameters, discretizing and analyzing the parameters, constructing the Bayesian network model and transforming the knowledge to construct the knowledge base. The network performance parameters are collected through a perceiving process, and data is discretized and analyzed. Through a structure learning and parameter learning process, the Bayesian network model is constructed by using historical data. The conditional dependence among the parameters in the Bayesian network is transformed into the knowledge so that the knowledge base is constructed and updated.
Owner:BEIHANG UNIV
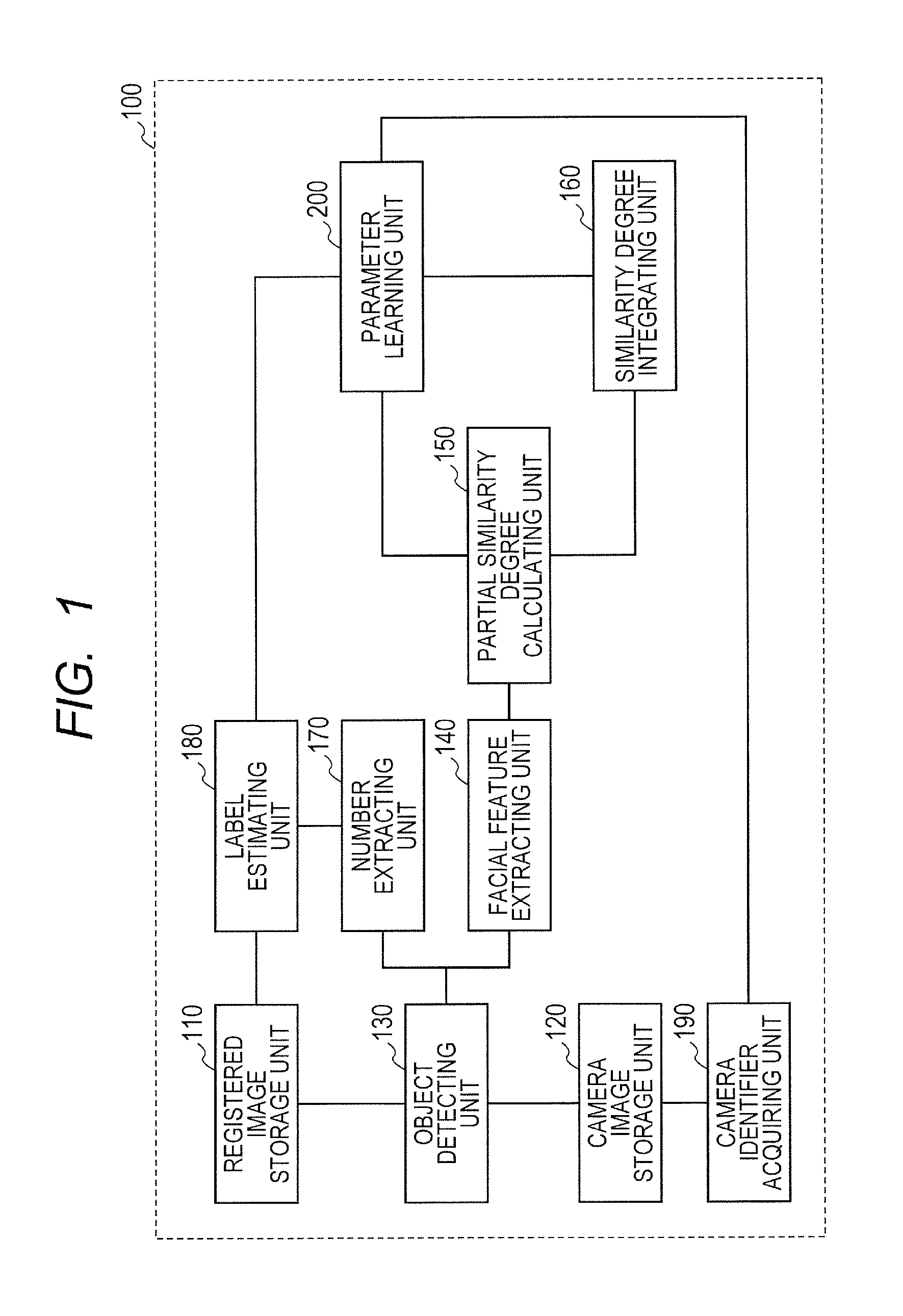
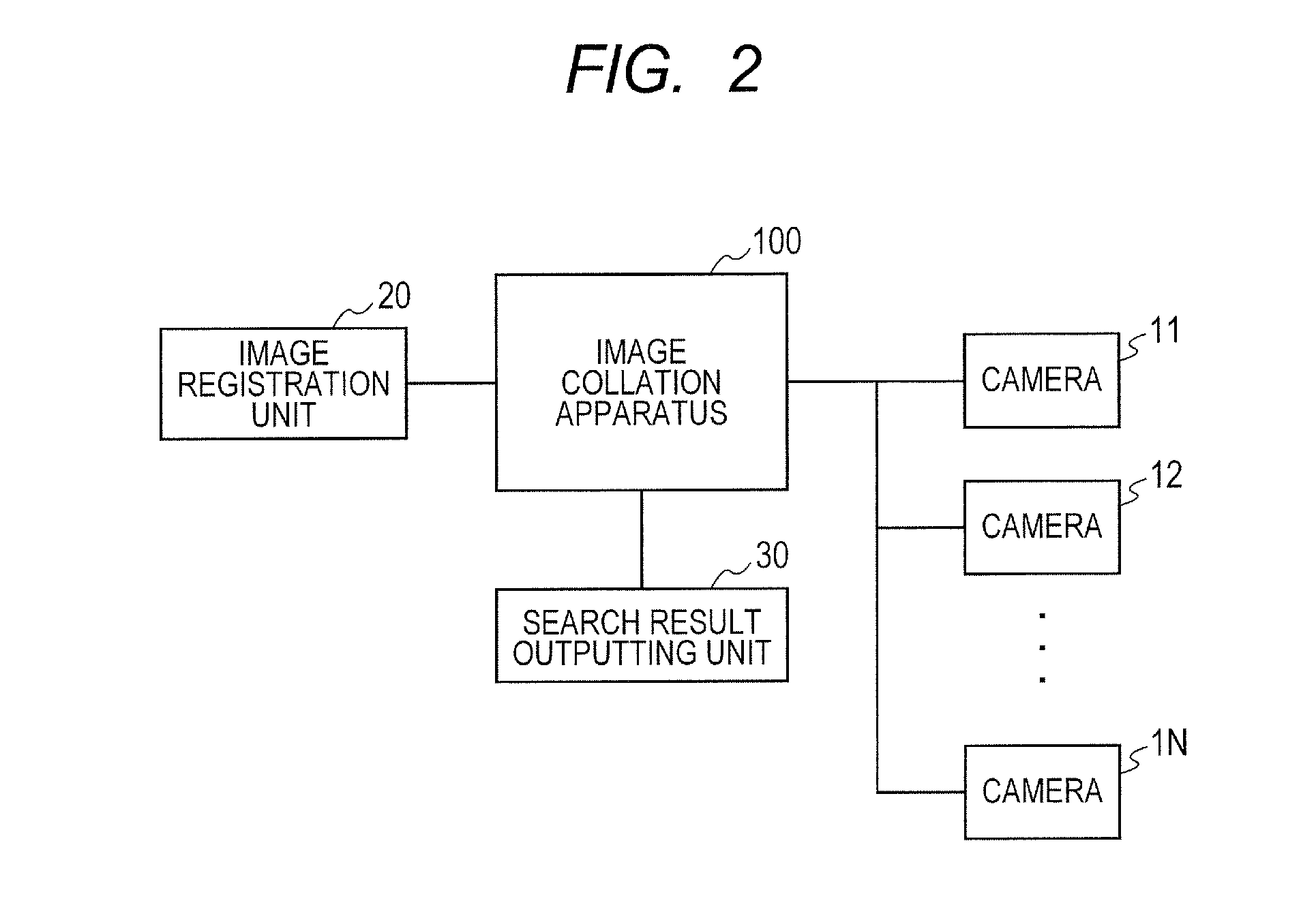
Collation apparatus and method for the same, and image searching apparatus and method for the same
A collation apparatus that collates an input image with registered images includes: a feature extracting unit extracting feature quantities from a region of an object in the input image; a calculating unit calculating, per each of the feature quantities, similarity degrees between the feature quantities extracted from the input image and corresponding feature quantities of the registered image, for each of the registered images; an integrating unit integrating, using a parameter, the similarity degrees for the feature quantities; an estimation unit estimating as to whether or not the object in the input image is identical with an object in each of the registered images; and a parameter learning unit learning the parameters to be used by the integrating unit, based on an estimation result of the estimation unit and the similarity degree integrated by the integrating unit.
Owner:CANON KK
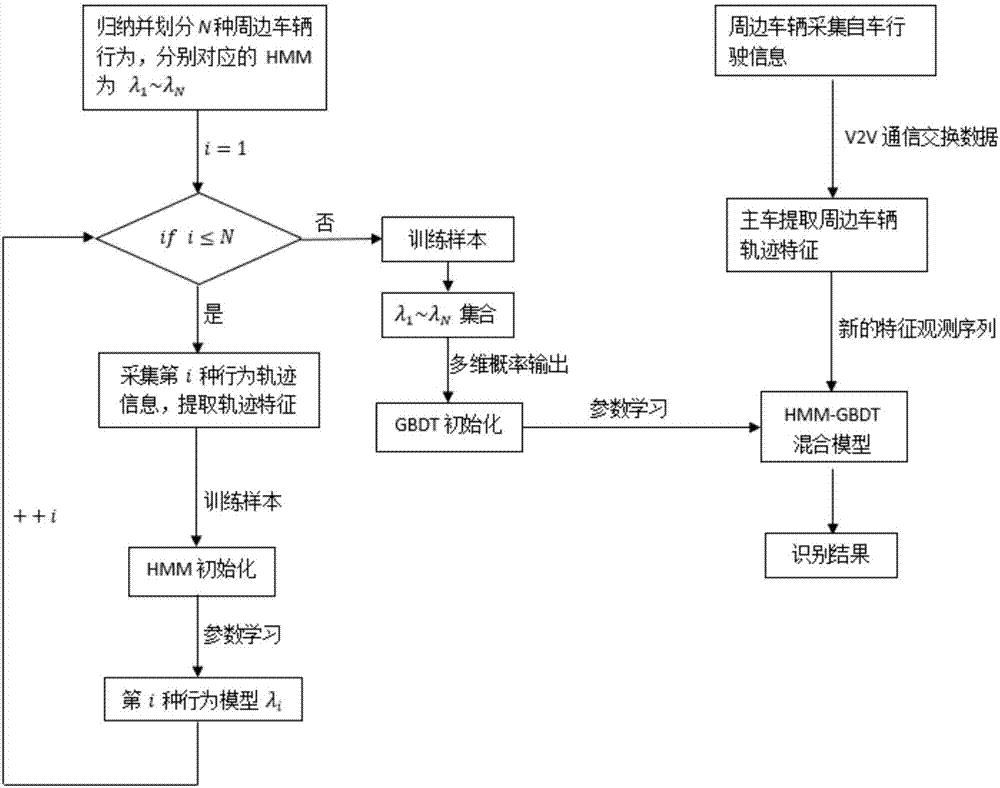
Surrounding vehicle behavior identification method based on V2V communication and HMM-GBDT hybrid model
ActiveCN107967486ABehavior recognition is accurateAccurate identificationParticular environment based servicesCharacter and pattern recognitionInformation transmissionVehicle behavior
The invention discloses a surrounding vehicle behavior identification method based on V2V communication and an HMM-GBDT hybrid model and belongs to the intelligent vehicle driving field. The method comprises steps that a, an offline training link, typical surrounding vehicle behaviors are concluded and divided, for each type of typical behaviors, based on real vehicle platform, the driving information of the surrounding vehicles under real traffic scenarios is collected, trajectory characteristic data is extracted, and parameter learning for the HMM-GBDT hybrid model is carried out. And b, anonline detection link, the acquired self driving information of a tracked target vehicle is transmitted to a driver in real time, a new characteristic observation sequence is constructed by the driverin combination with trajectory characteristic data of two vehicles, and the trained HMM-GBDT hybrid model is utilized to identify belonging behavior modes of the tracked vehicles. The method is advantaged in that the historical trajectory characteristics of vehicle are acquired in a passive information reception mode, influence of the traffic status and environmental factors on active detection is avoided, the method is not dependent on a fixed base station in a common vehicle network system, instant information transmission is guaranteed, and the target vehicle behaviors can be accurately identified.
Owner:JIANGSU UNIV
Method for detecting pedestrians in crowding scene
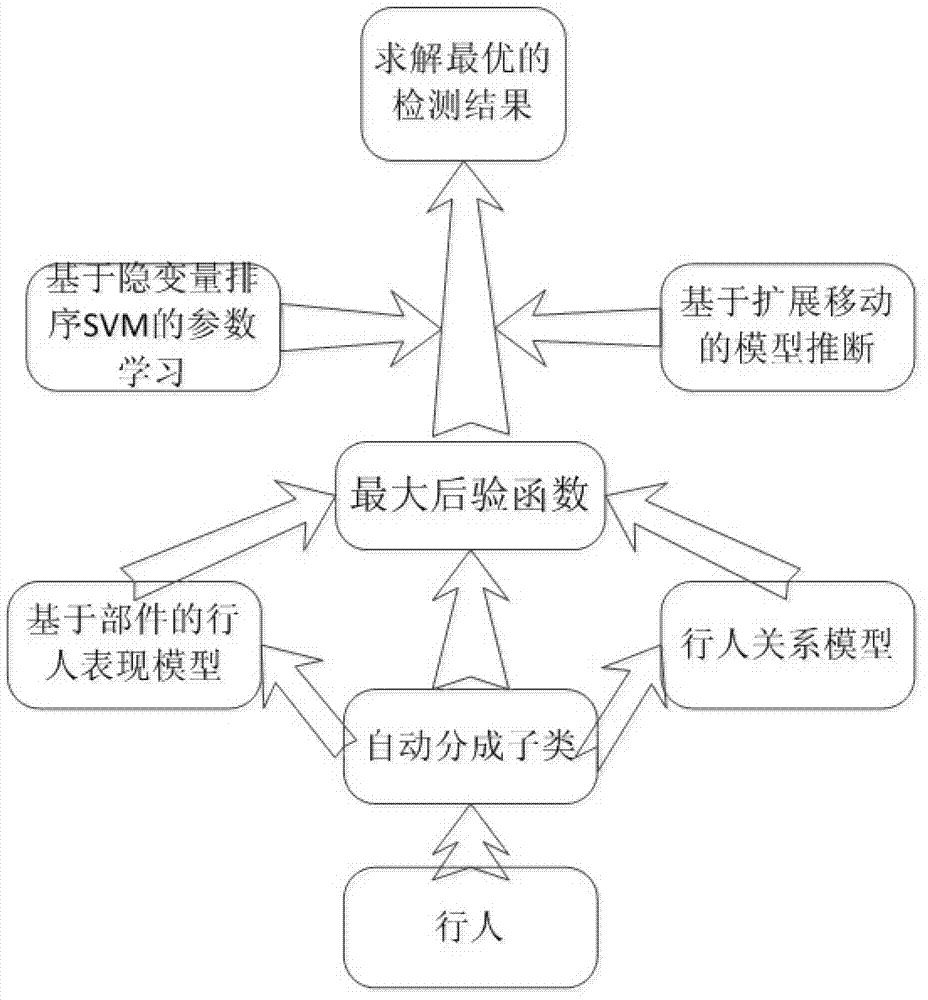
ActiveCN102810161AImprove detection accuracyCharacter and pattern recognitionProbit modelRelational model
The invention relates to a method for detecting a plurality of pedestrians in a crowding scene. The method comprises the following steps: a, inputting a training set containing a plurality training sample images, and dividing pedestrians in the training sample images into a plurality of subclasses, wherein each subclass is corresponding to one pedestrian change; b, establishing a training set pedestrian representation feature model; c, establishing a spatial relational model of pedestrians on the training set; d, establishing a probabilistic model to describe the pedestrians in the crowding scene, and converting the probabilistic model into an energy objective function; e, looking for the optimal parameter of the energy objective function in a parameter learning method based on a latent rank SVM (Support Vector Machine) so as to obtain a determined energy objective function; and f, inputting crowding scene pedestrian images to be detected, and detecting by a model deduction method based on expansion move and the determined energy objective function to obtain the result of the crowding scene pedestrian images to be detected. According to the method disclosed by the invention, the detection precision is improved, and the application range of the method is wide.
Owner:JIANGSU CAS JUNSHINE TECH
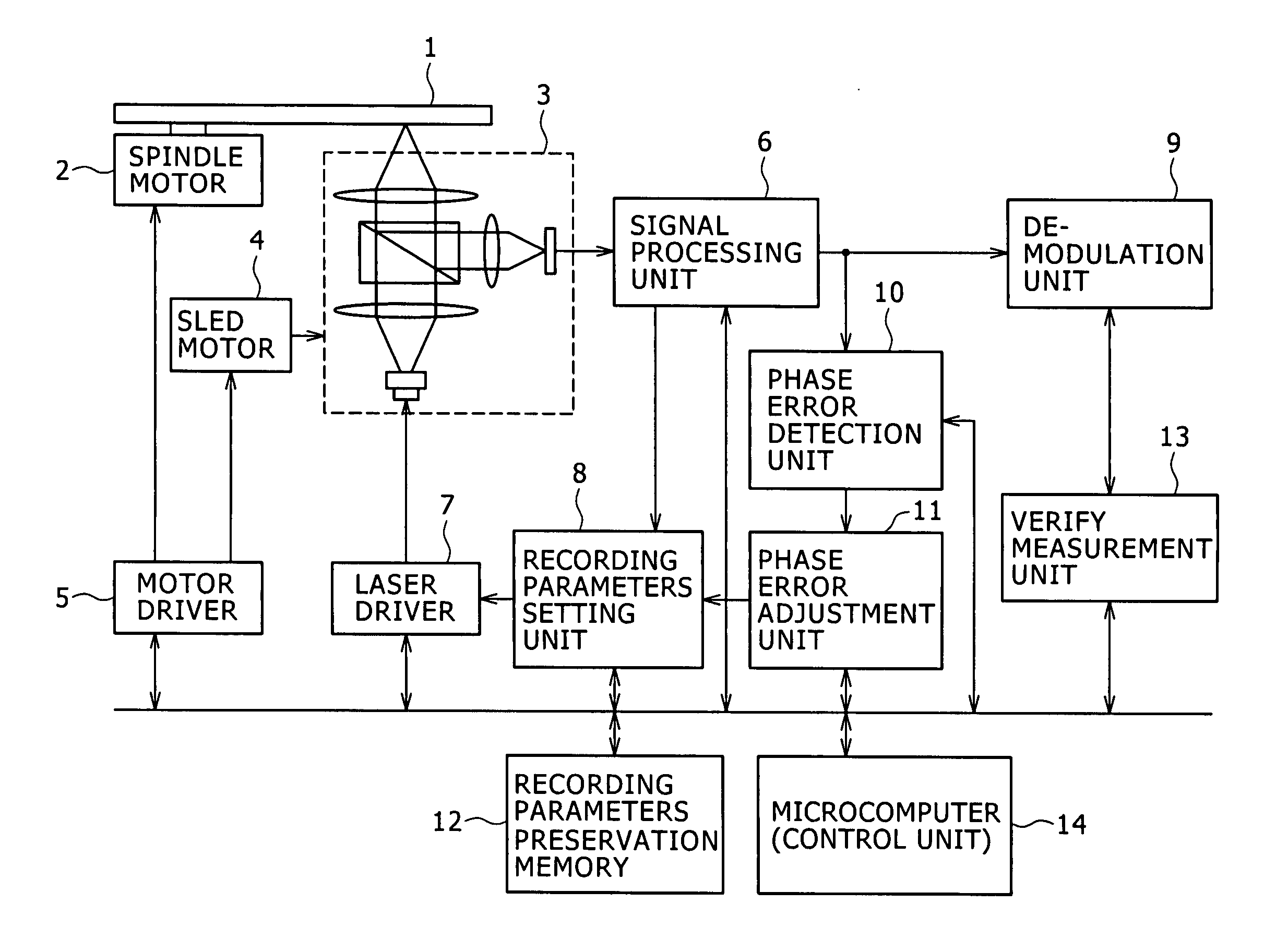
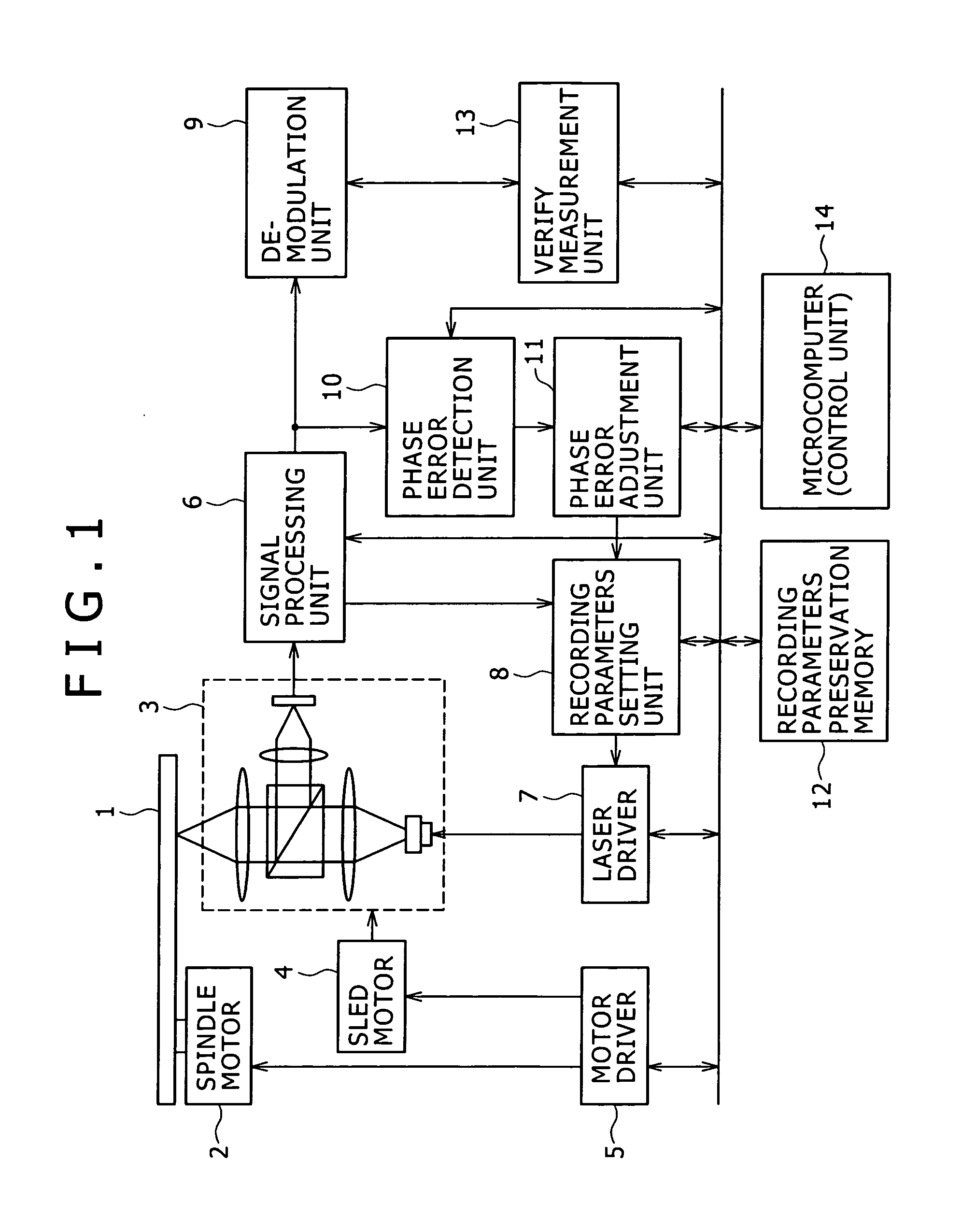
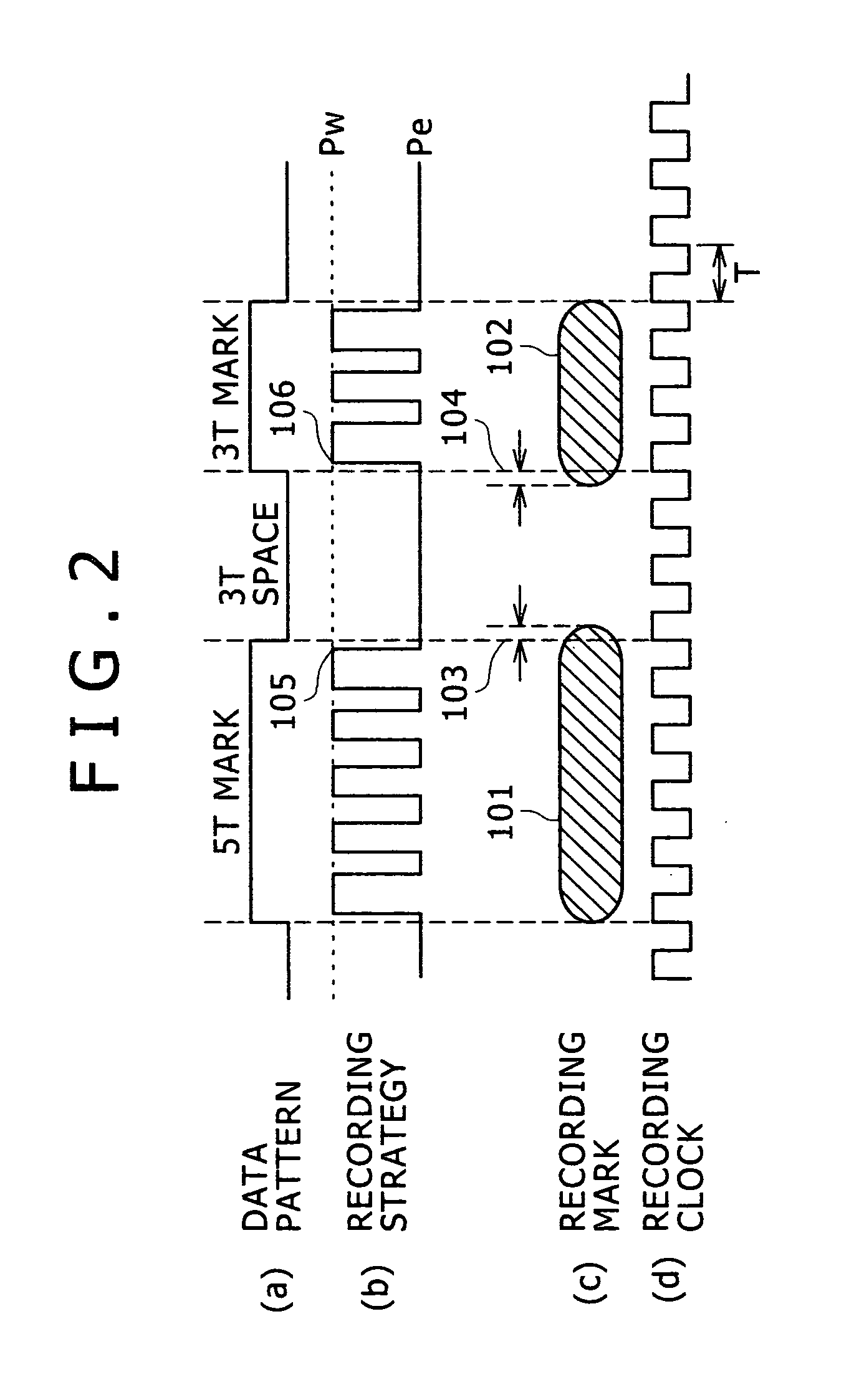
Optical disk apparatus and recording parameters setting method
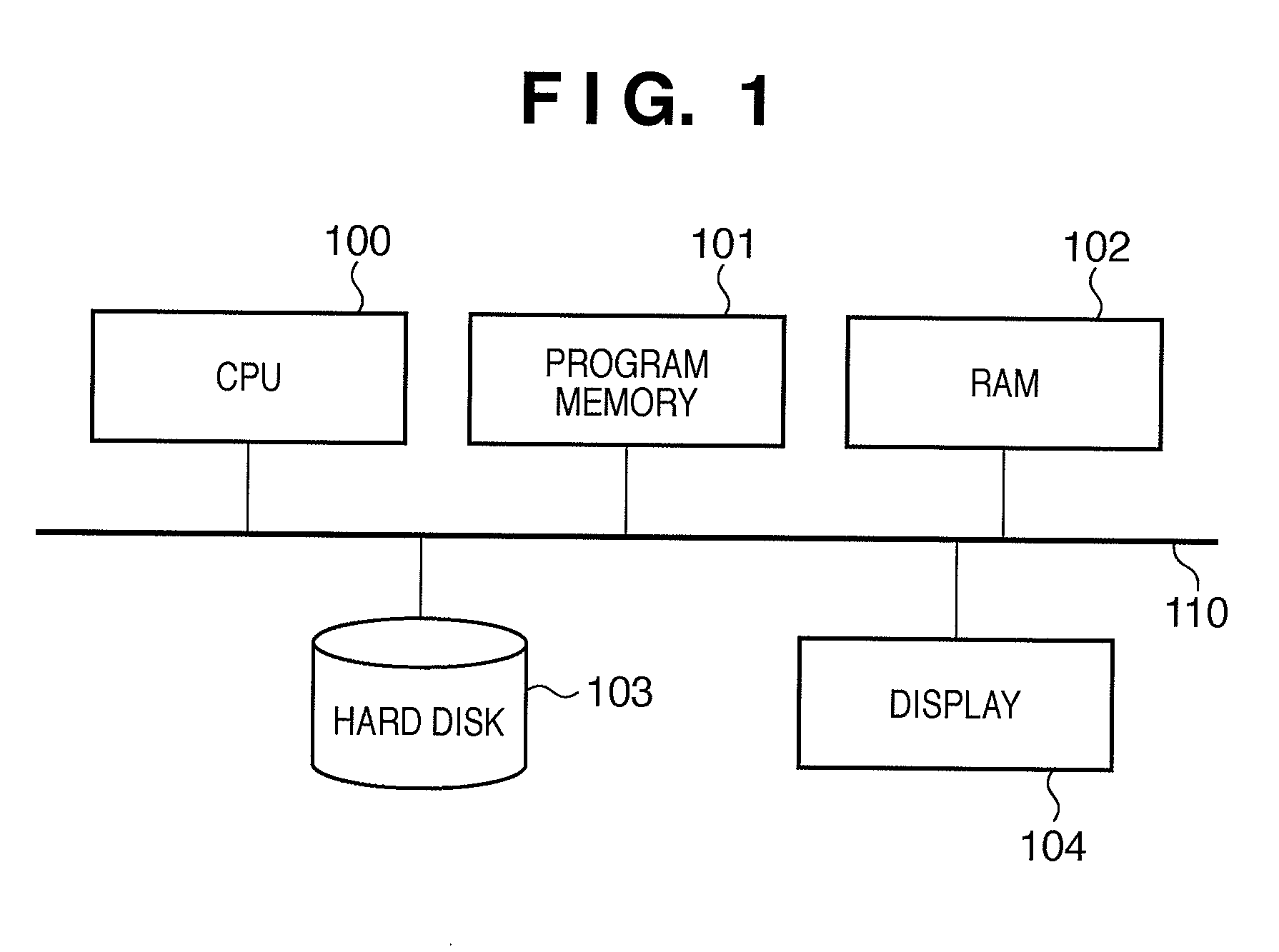
InactiveUS20070183285A1Shorten the timeRecording strategiesTelevision system detailsData recordingComputer science
An optical disk apparatus and a recording parameters setting method are provided to more effectively execute recording parameter learning during data recording on the optical disk, thereby shortening the time required for setting an optimum recording parameter. A phase error detection unit detects a phase error amount from a reproduction signal of actual data being recorded. A phase error adjustment unit adjusts recording parameters (recording strategy) set by a recording parameters setting unit based on the detected phase error amount. The phase error amount detection is executed simultaneously with a verify process of the actual data. If a verify process judgment results says that a target quality is not attained, test writing by a test signal is not executed but the adjustment of recording parameters is conducted on the basis of the phase error amount.
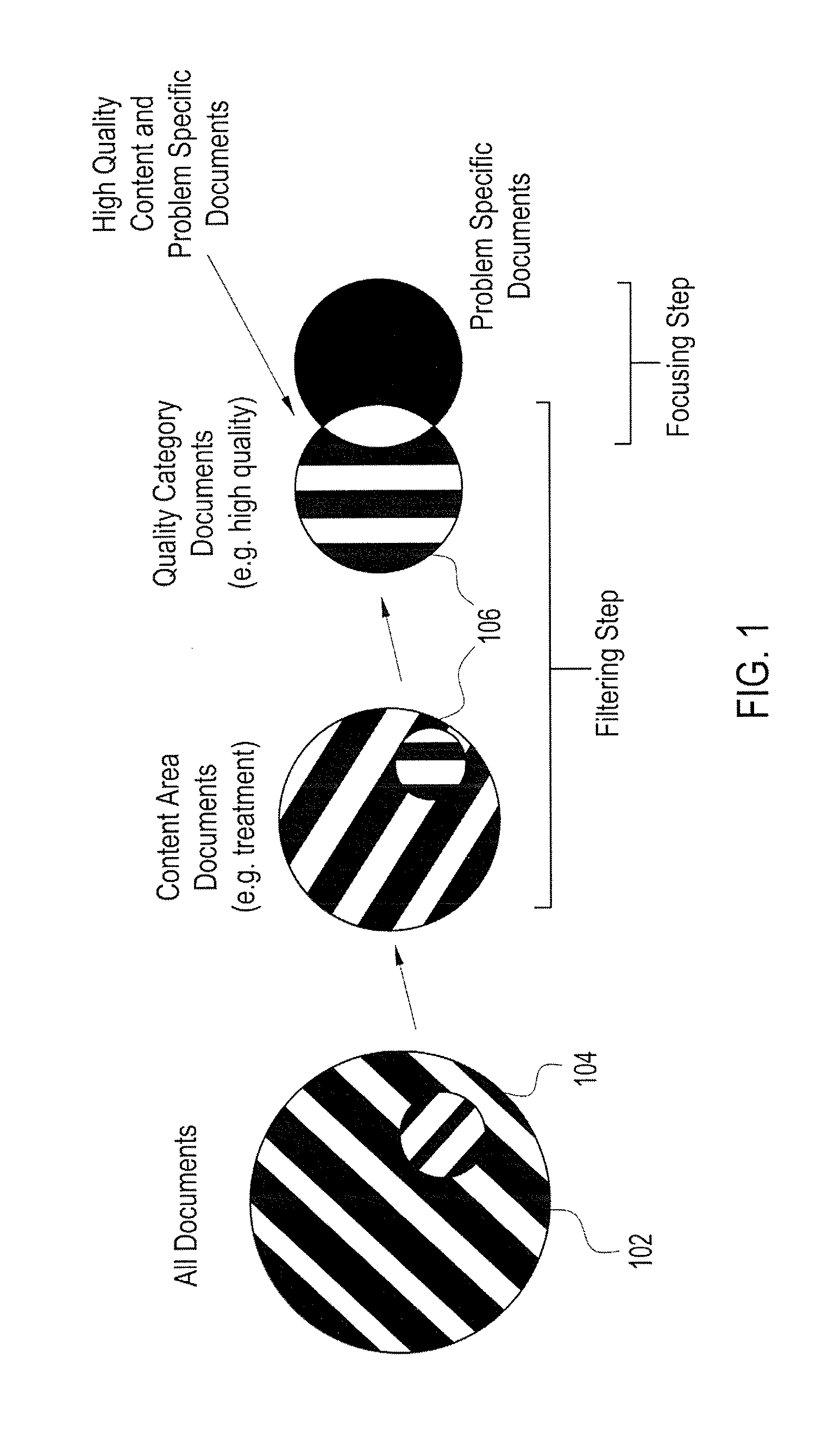
Owner:HITACHI LTD +1
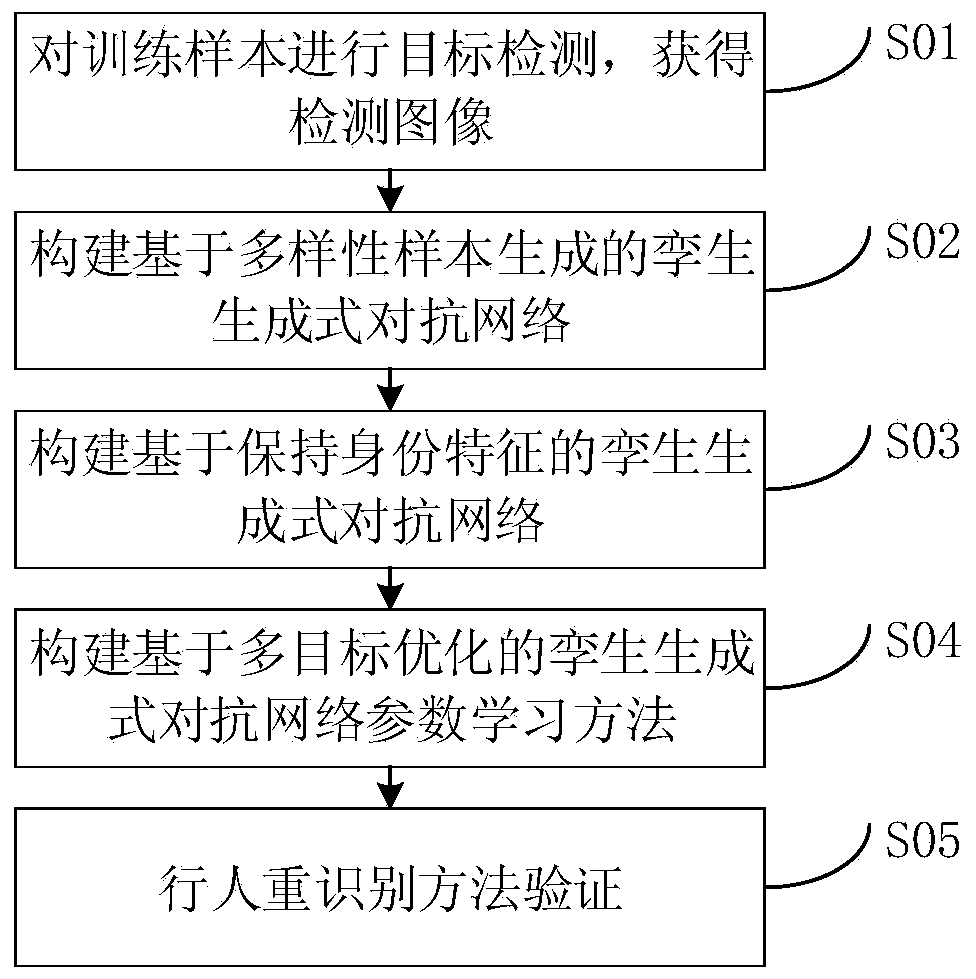
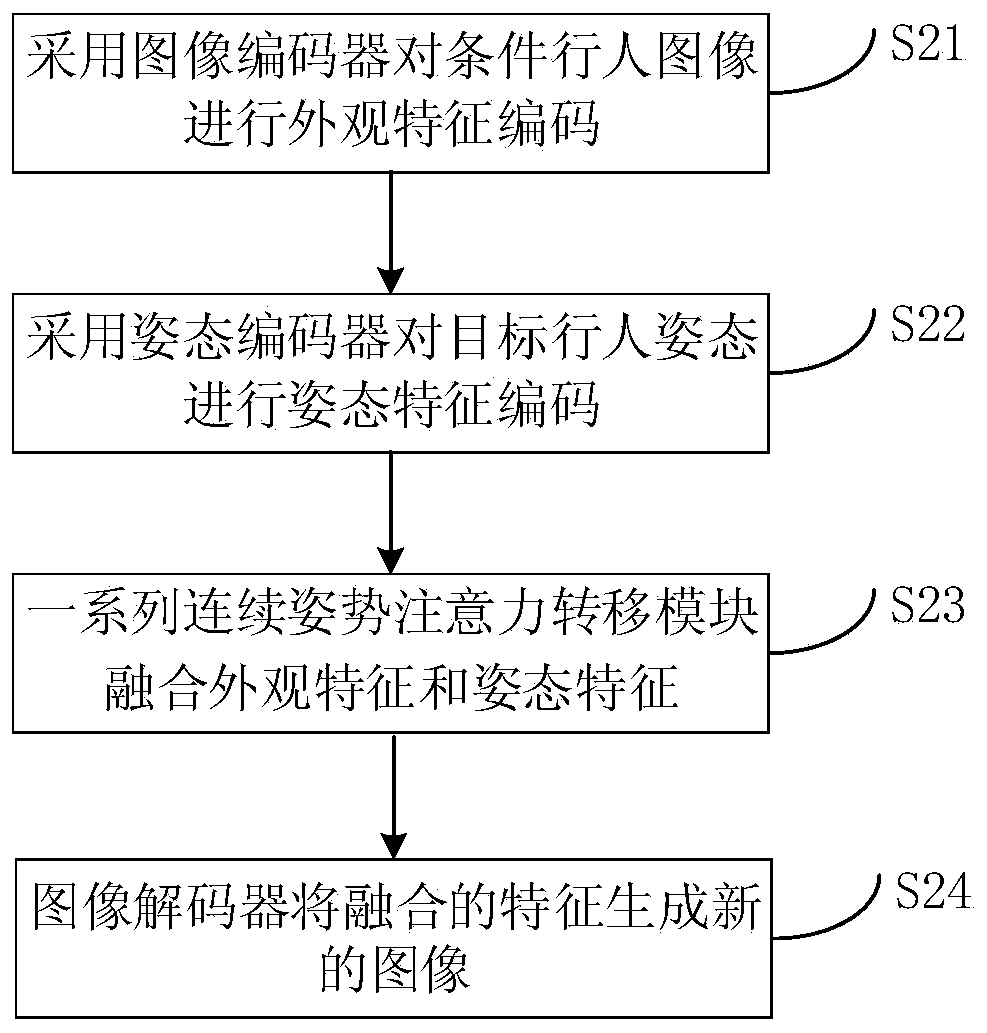
Pedestrian re-identification method of twin generative adversarial network based on attitude guidance pedestrian image generation
ActiveCN110427813AImprove stabilityImprove robustnessImage enhancementImage analysisDiscriminatorData set
The invention discloses a pedestrian re-identification method of a twin generative adversarial network based on attitude guidance pedestrian image generation. According to the implementation scheme, the method includes: carrying out target detection on pedestrian images according to a pedestrian image data set to obtain training samples; constructing a twin generative adversarial network model based on diversity sample generation, and exchanging attitude attribute information of two groups of pedestrian images input after target detection by the model to realize generation of diversity samples; constructing a twin generative adversarial network model based on identity feature maintenance, wherein identity information of a generated pedestrian image is reserved by the model through an identity discriminator, so that the robustness of pedestrian re-identification on the identity of the generated pedestrian image is improved; aiming at the problem that the generative adversarial network is difficult to optimize, constructing a twin generative adversarial network parameter learning method based on multi-objective optimization; in order to verify the effectiveness of the pedestrian re-identification method, carrying out pedestrian re-identification method verification on a data set formed by generated pedestrian images.
Owner:CHINA UNIV OF MINING & TECH
Intelligent control method based on adaptive planning of virtual ship for under-drive unmanned ship formation
ActiveCN108073175AAvoid Overhead ProblemsAchieving formation keepingTransmission systemsNeural learning methodsControl signalSelf adaptive
The invention relates to an intelligent control method based on adaptive planning of a virtual ship for an under-drive unmanned ship formation. The method comprises the following steps of 1, setting aformation and initializing parameters; 2, collecting a position coordinate (xL, yL) and a heading angle psiL of a leader ship, conducting wave filtering, and transmitting the position coordinate andthe heading angle to a following ship; 3, according to the formation, the position coordinate and the heading angle information of the leader ship, obtaining a reference position (xr, yr) and a reference motion posture psir of the following ship in the formation in real time; 4, introducing the virtual ship and conducting real-time adaptive planning to obtain a reference track of the following ship; 5, using a combination strategy of RBF neural networks and a minimum parameter learning algorithm to train learning parameters online to generate intelligent formation control signals, wherein theintelligent formation control signals include the rotating speed nF of a mainframe of the following ship and a rudder angle command signal deltaF. Compared with the prior art, the method has the advantages that the method adapts to curved path tasks, overhead is avoided, leader ship speed information is not needed, and the method is simple, convenient and excellent in real-time performance.
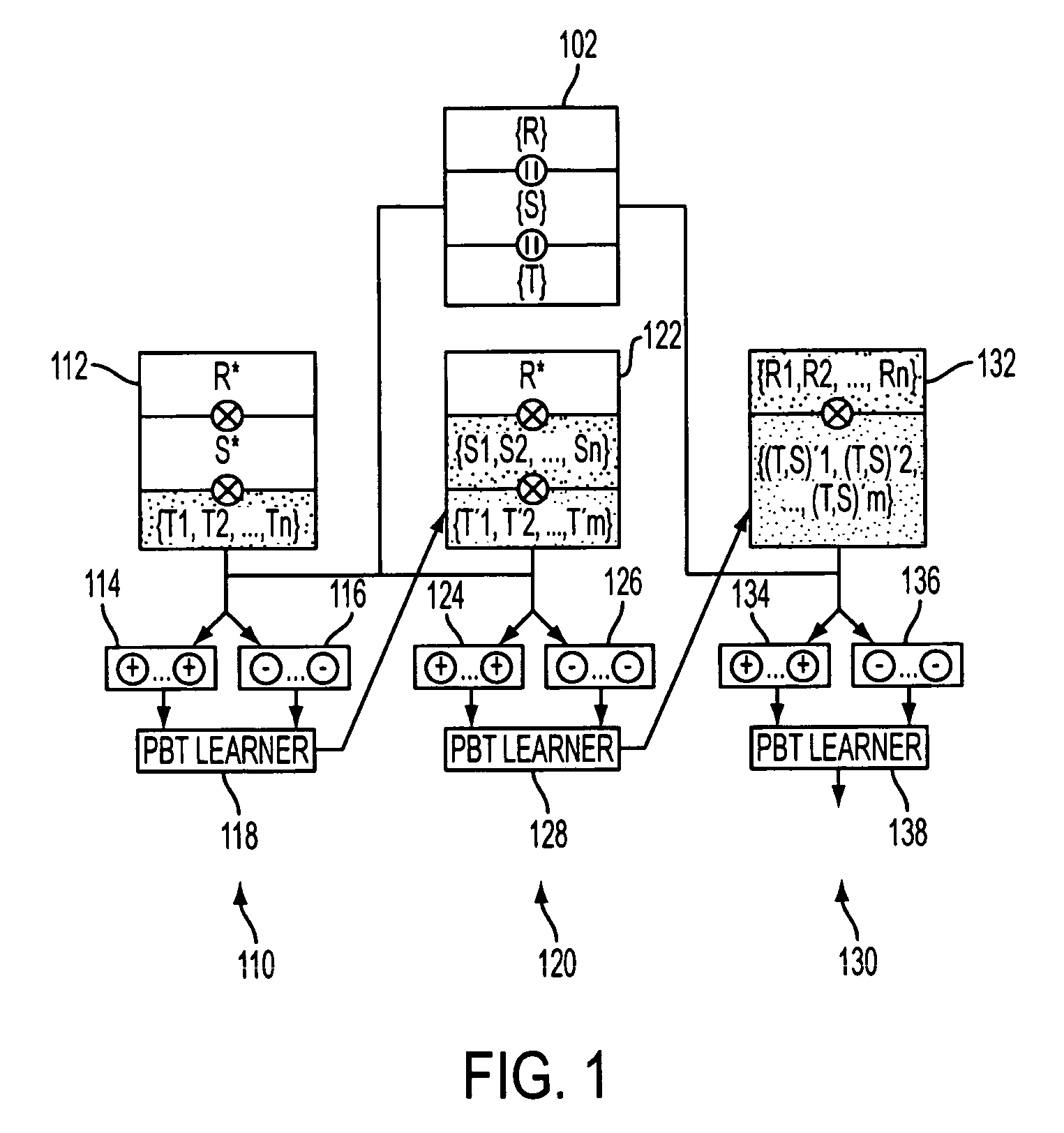
Owner:SHANGHAI JIAO TONG UNIV
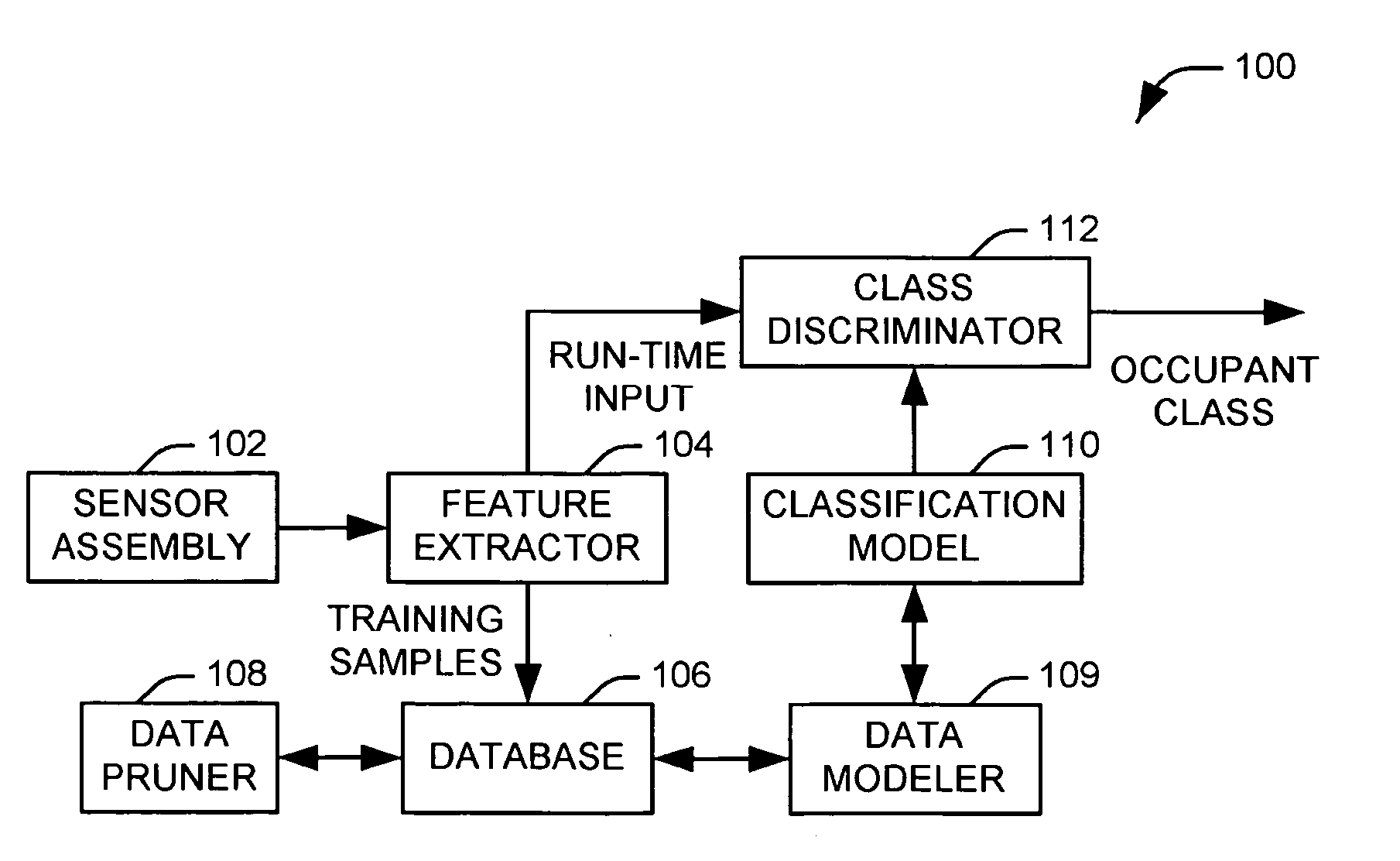
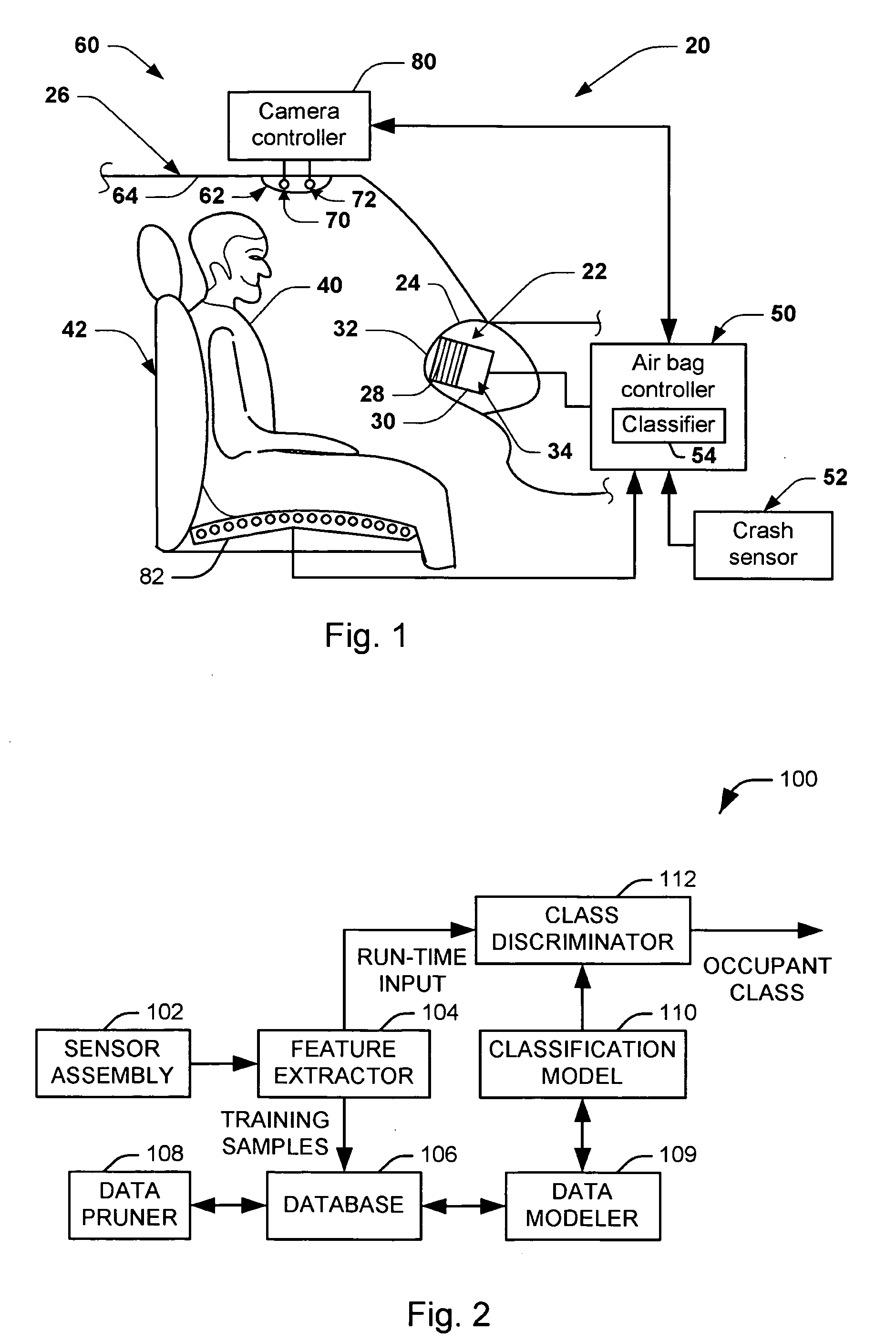
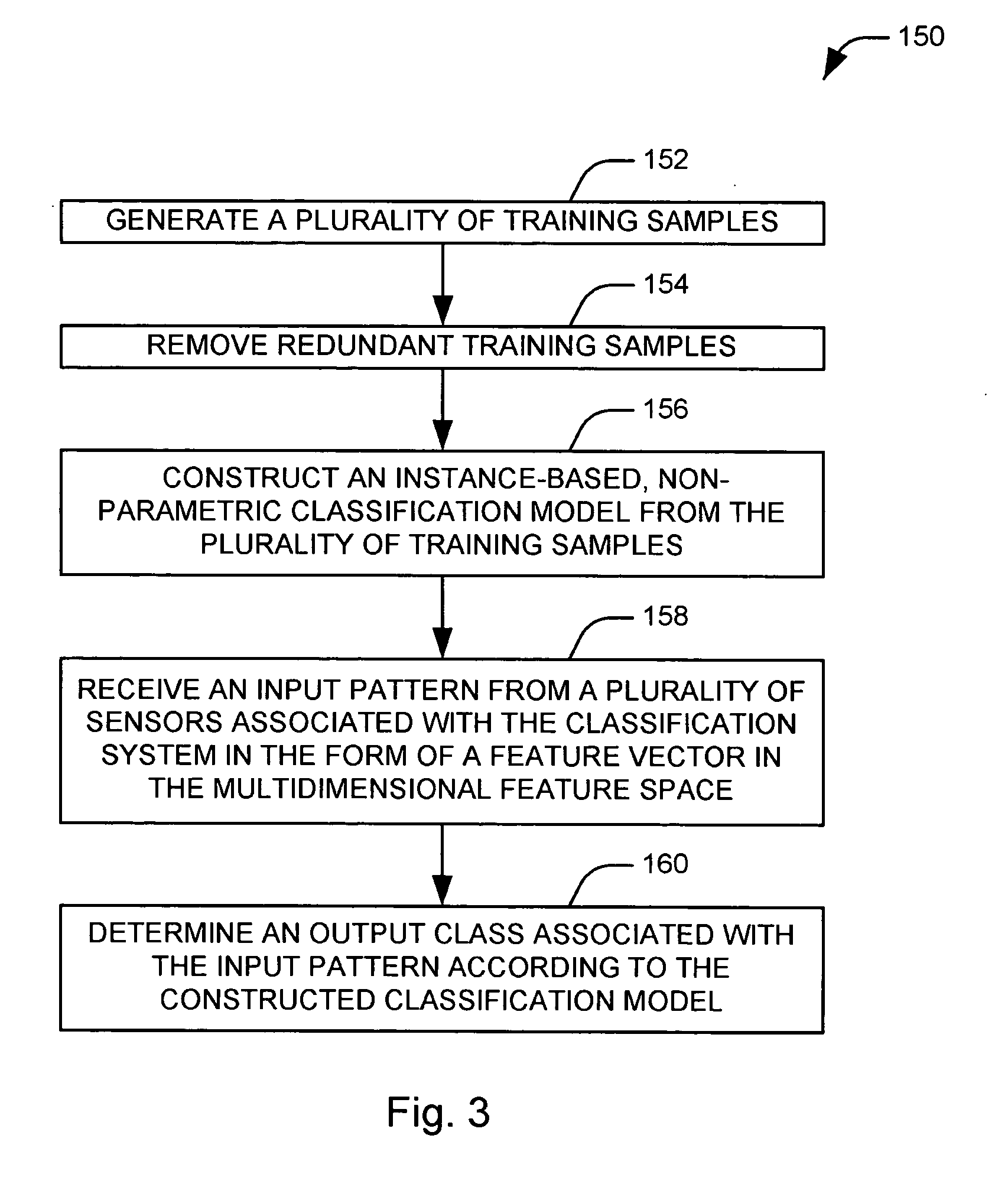
Method and apparatus for classifying a vehicle occupant via a non-parametric learning algorithm
Systems and methods are provided for classifying an input feature vector, representing a vehicle occupant, into one of a plurality of occupant classes. A database (106) contains a plurality of feature vectors in a multidimensional feature space. Each feature vector has an associated class from the plurality of output classes. A data pruner (108) eliminates redundant feature vectors from the database. A data modeler (109) constructs an instance-based, non-parametric classification model (110) in the multidimensional feature space from the plurality of feature vectors. A class discriminator (112) selects an occupant class from the plurality of occupant classes according to the constructed classification model.
Owner:TRW AUTOMOTIVE US LLC
Method and system for detection and registration of 3D objects using incremental parameter learning
A method and system for detecting 3D objects in images is disclosed. In particular, a method and system for Ileo-Cecal Valve detection in 3D computed tomography (CT) images using incremental parameter learning and ICV specific prior learning is disclosed. First, second, and third classifiers are sequentially trained to detect candidates for position, scale, and orientation parameters of a box that bounds an object in 3D image. In the training of each sequential classifier, new training samples are generated by scanning the object's configuration parameters in the current learning projected subspace (position, scale, orientation), based on detected candidates resulting from the previous training step. This allows simultaneous detection and registration of a 3D object with full 9 degrees of freedom. ICV specific prior learning can be used to detect candidate voxels for an orifice of the ICV and to detect initial ICV box candidates using a constrained orientation alignment at each candidate voxel.
Owner:SIEMENS HEALTHCARE GMBH +1
Content and quality assessment method and apparatus for quality searching
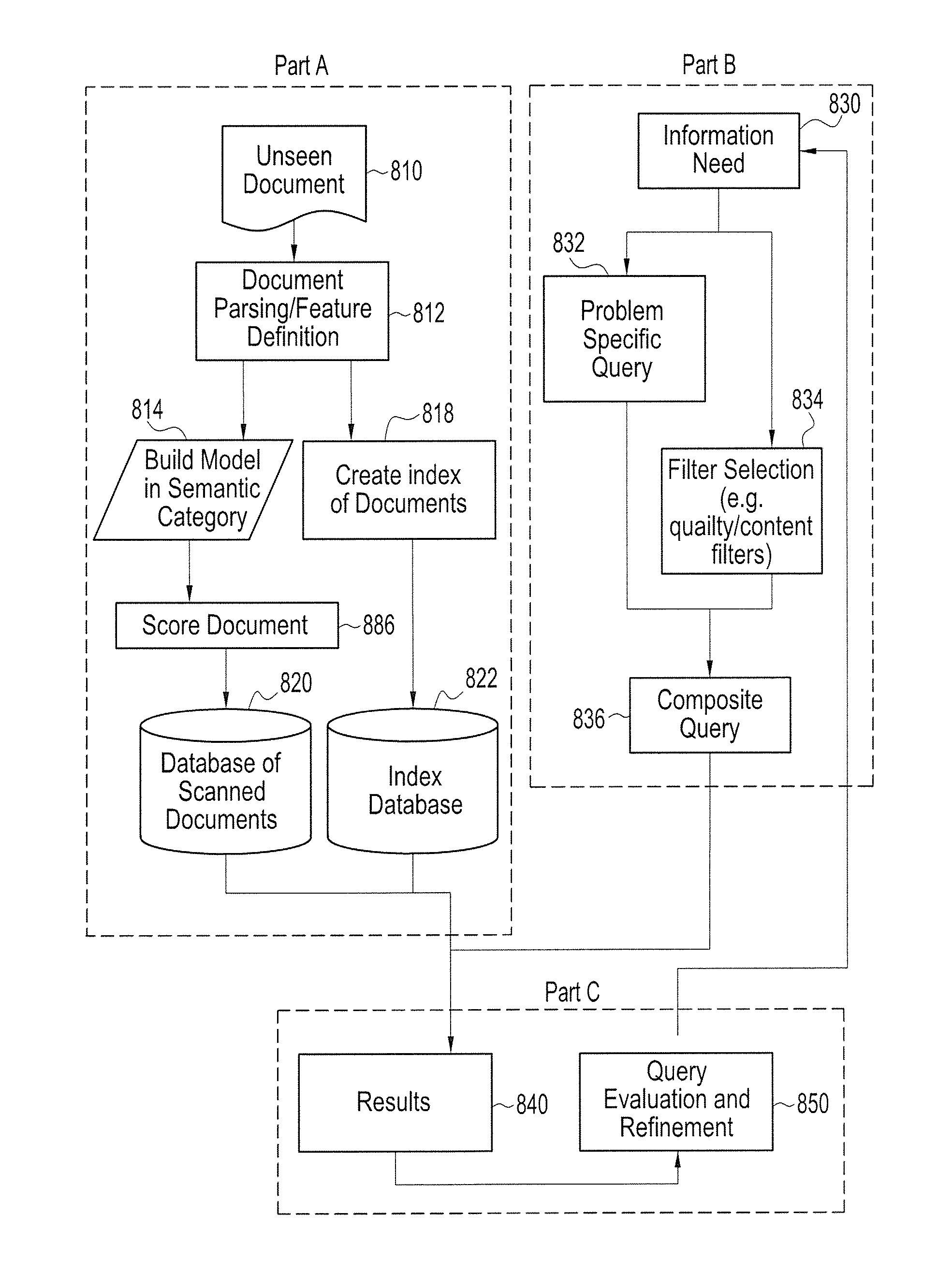
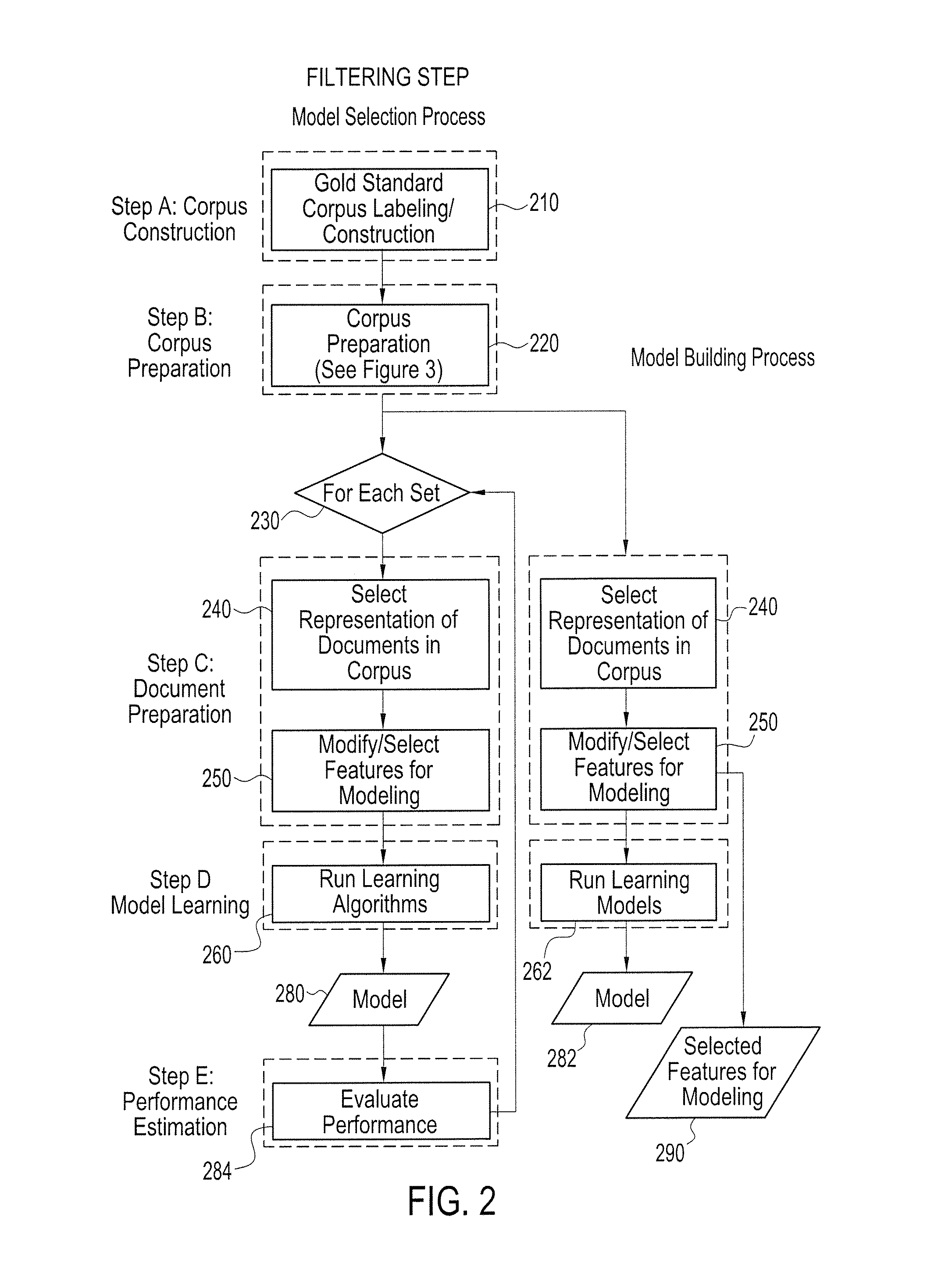
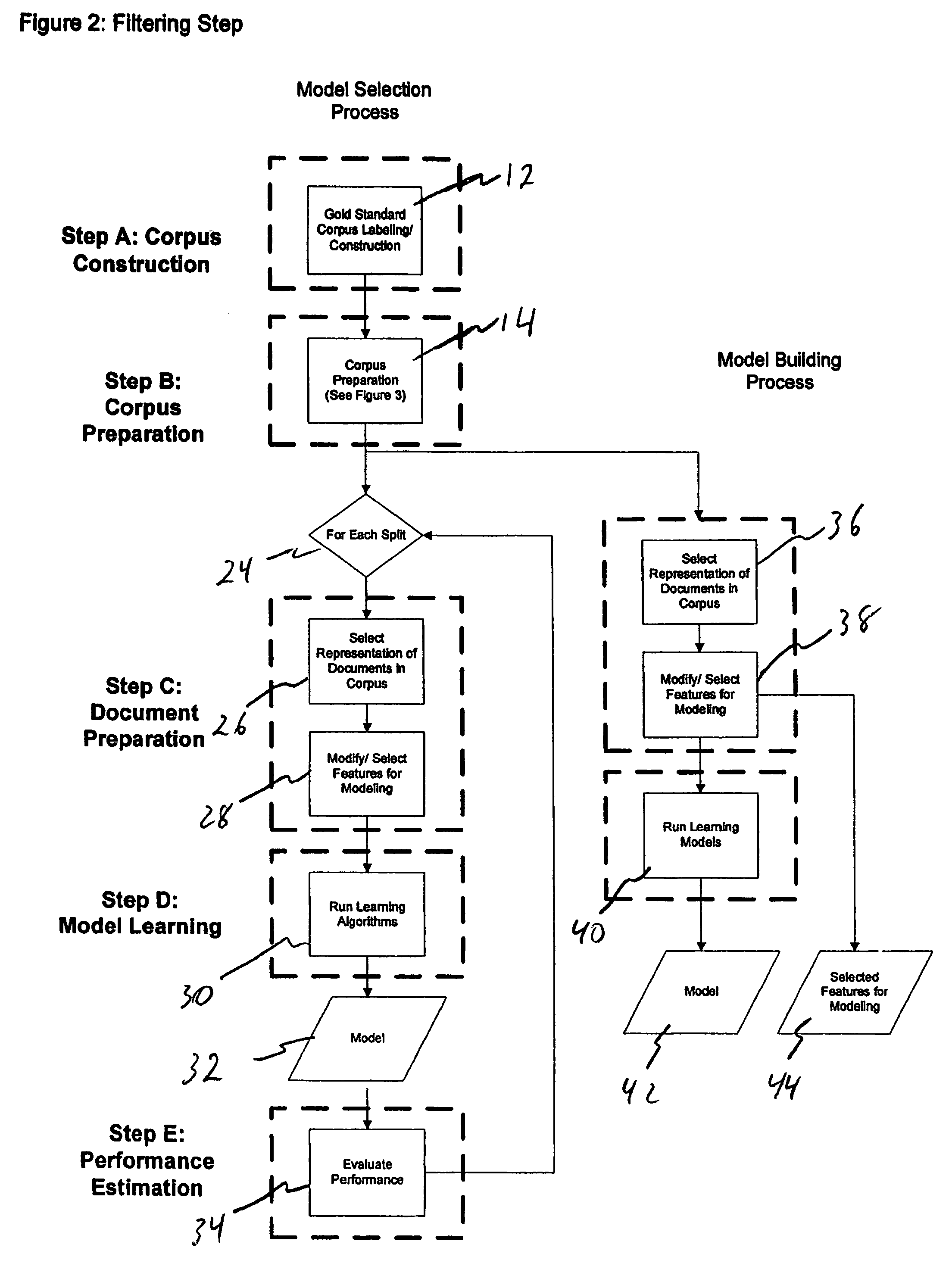
ActiveUS20090077068A1Evaluate performanceDigital data information retrievalDigital data processing detailsModel parametersDocument preparation
A computer-based process retrieves information organized in documents containing text and / or coded representations of text. The process involves obtaining and labeling a selected set of documents based on content quality, and extracting and representing features from each document in the selected set. The extracted and selected features are modified, and models are constructed using parametric learning algorithms. The constructed models are capable of assigning a label to each document. The model parameters are instantiated using a first subset of the selected set of documents. Parameters are chosen by validating the corresponding model against at least a second subset of the full document set. The constructed models also are capable of assigning labels to similar documents outside a selected subset not previously given to the process of model construction.
Owner:APHINYANAPHONGS YIN +1
Content and quality assessment method and apparatus for biomedical information retrieval
ActiveUS7529737B2Data processing applicationsDigital data processing detailsModel parametersDocument preparation
A computer-based process retrieves information organized in documents containing text and / or coded representations of text. The process involves obtaining and labeling a selected set of documents, and extracting and selecting features from each document in the selected set. The extracted and selected features are represented, and models are constructed using parametric learning algorithms. The constructed models are capable of assigning a label to each document. The model parameters being instantiated use a first subset of the selected set of documents. Parameters are chosen by validating the corresponding model against at least a second subset of the full document set. The constructed models also are capable of assigning labels and ranks to similar documents outside a selected subset not previously given to the process of model construction.
Owner:APHINYANAPHONGS YIN +1
A target tracking method based on an LSTM neural network
PendingCN109740742AEffective real-time trackingAchieving Target Motion EstimationNeural architecturesNeural learning methodsLinear motionUltrasound attenuation
The invention discloses a target tracking method based on an LSTM neural network, and belongs to the technical field of target tracking. According to the method, the LSTM is used for tracking the complex and non-linear motion target, and the problems that target tracking is difficult, a target model is difficult to establish and the tracking precision is low are solved; the method comprises the following steps: firstly, acquiring latitude and longitude information and speed information of a target, and processing acquired data; designing an LSTM neural network structure for single target tracking; and finally, adjusting LSTM neural network parameters to realize target tracking. According to the method, the nonlinear filtering process is effectively simplified, and a complex nonlinear target can be effectively tracked; the establishment of a target motion model and the utilization of a traditional filtering algorithm are not needed; estimating the target motion state of the next momentby using historical target motion information; adjusting internal parameters of the neural network by using a back propagation algorithm; the learning rate attenuation method reduces the calculation amount and improves the precision.
Owner:HARBIN ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com