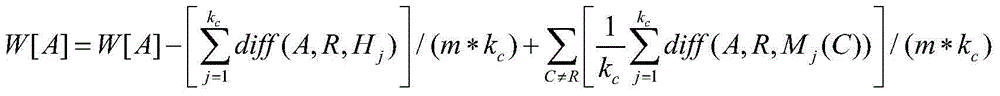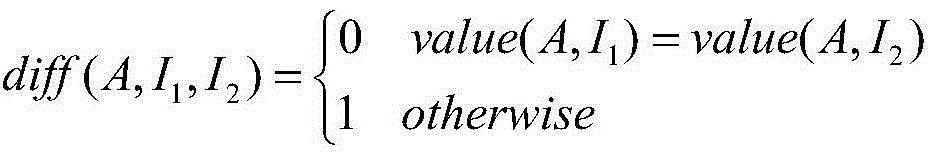Source node loophole detection method based on integrated neural network
A vulnerability detection and neural network technology, applied in the field of detection, can solve problems such as complex software security vulnerability detection requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The present invention will be described in further detail below in conjunction with the accompanying drawings.
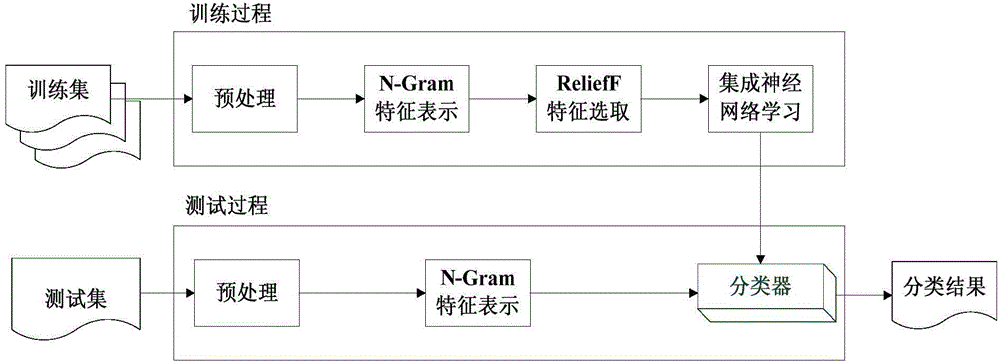
[0054] Such as figure 1 , the present invention provides a kind of source code loophole detection method based on integrated neural network, described method comprises the following steps:
[0055] Step 1: Establish a vulnerability detection model;
[0056] Step 2: Perform source code vulnerability detection based on the vulnerability detection model.
[0057] Described step 1 comprises the following steps:
[0058] Step 1-1: given training set;
[0059] Step 1-2: Preprocess the source code, and then perform feature extraction based on the N-gram algorithm;
[0060] Step 1-3: Based on the extracted features, use the ReliefF algorithm for feature selection;
[0061] Steps 1-4: Source code vulnerability detection learning based on the integrated neural network.
[0062] In the step 1-1, given the training set D={d through manual classification 1 , d 2 ,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com