Attack intention recognition method based on Bayesian network inference
A Bayesian network and identification method technology, applied in the field of attack intent identification based on Bayesian network reasoning, can solve problems such as difficult to understand and analyze, large amount of alarm information, and inability to predict attacker attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be described in detail below in conjunction with the drawings and specific embodiments.
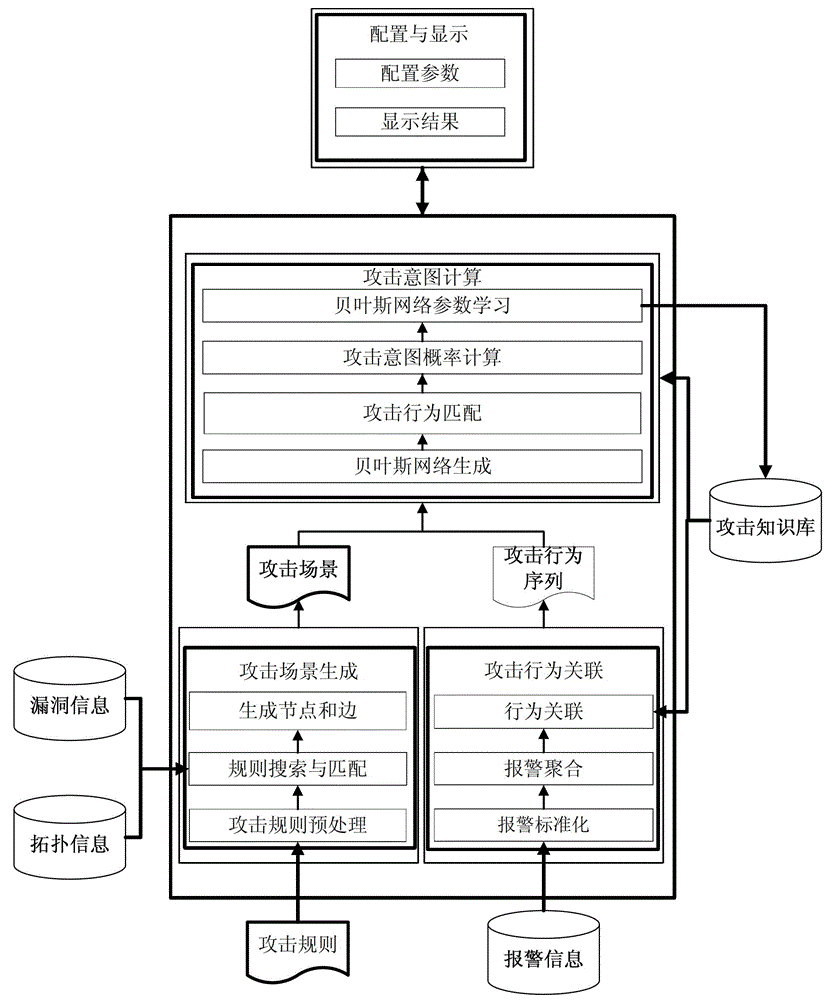
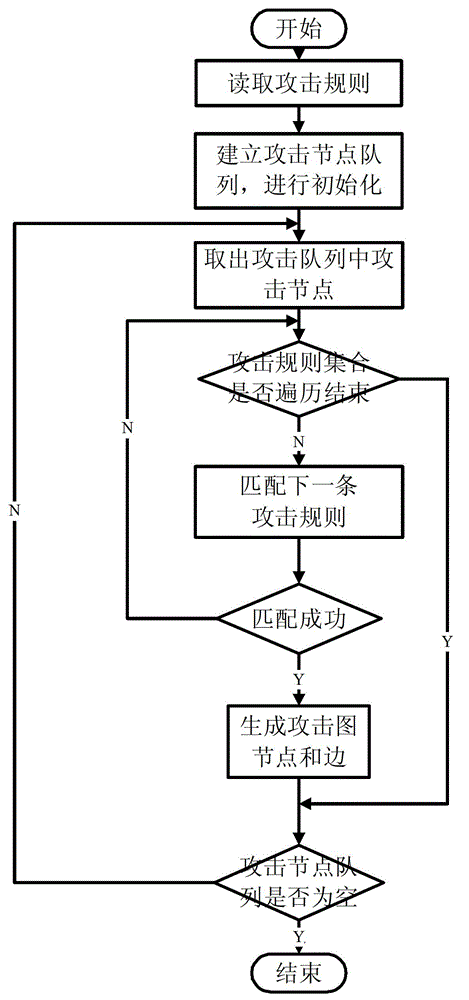
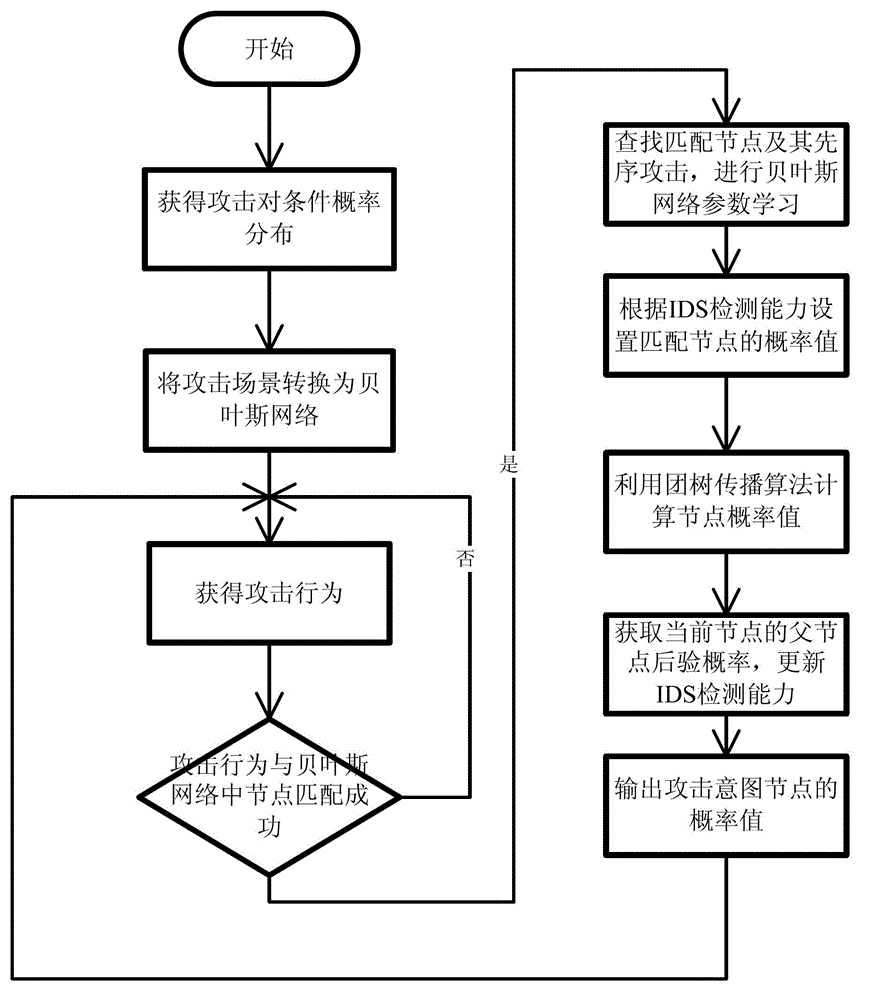
[0041] The present invention is an attack intention identification method based on Bayesian network reasoning, which can be used in computer network self-organizing confrontation. According to the given topology information, the vulnerability information of the host in the topology and the constraint relationship between attack behaviors, etc., use The breadth-first forward search method automatically generates the attack graph as the attack scenario, and then matches the generated attack scenario with the IDS alarm information. Based on the Bayesian network inference method, the attacker’s attack intention probability is calculated, and The calculated parameters can be updated based on the calculation results and historical information. The entity division and activity division in the attack intention recognition of the present invention are respectively sh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com