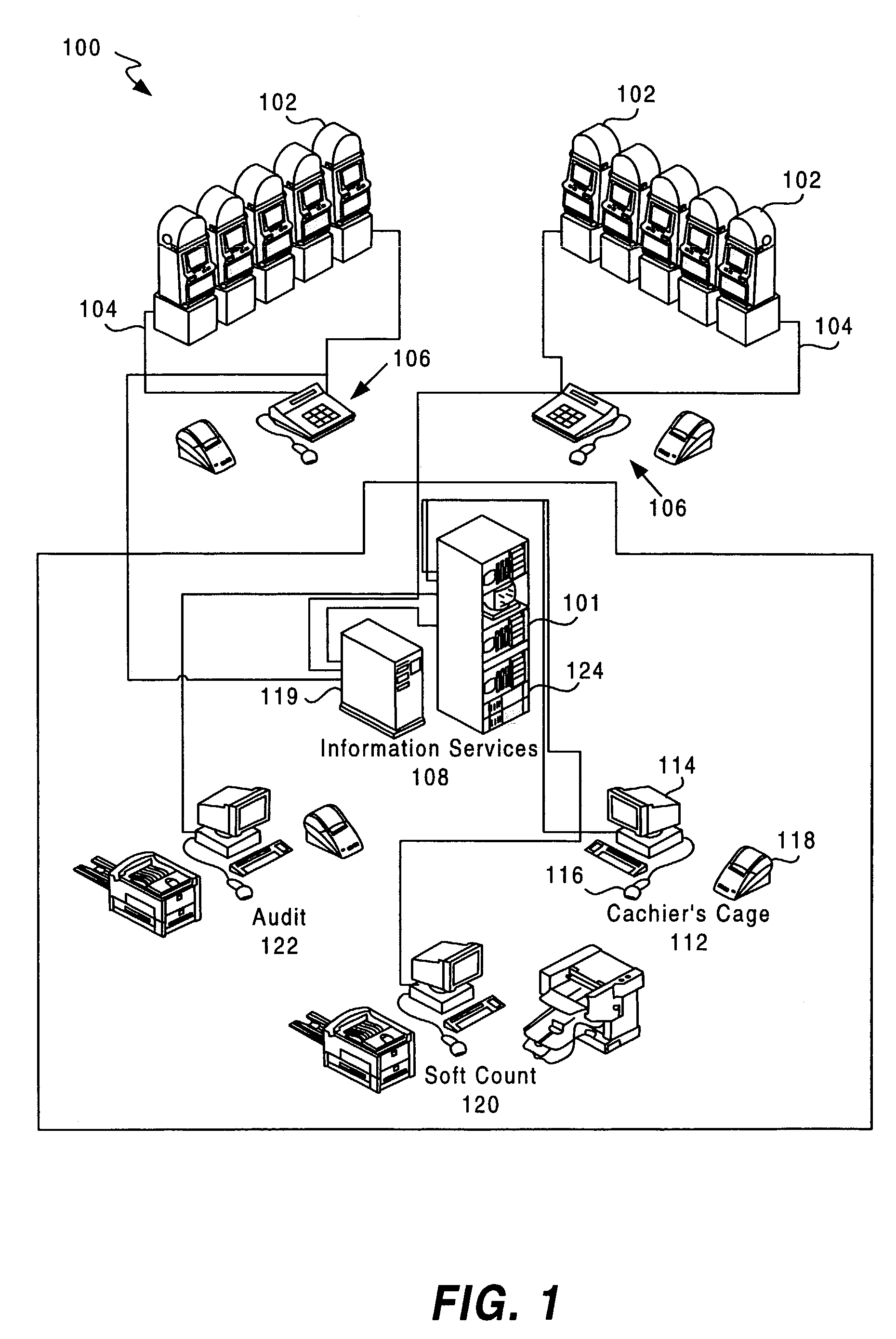
Patents
Literature
230 results about "Database transaction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
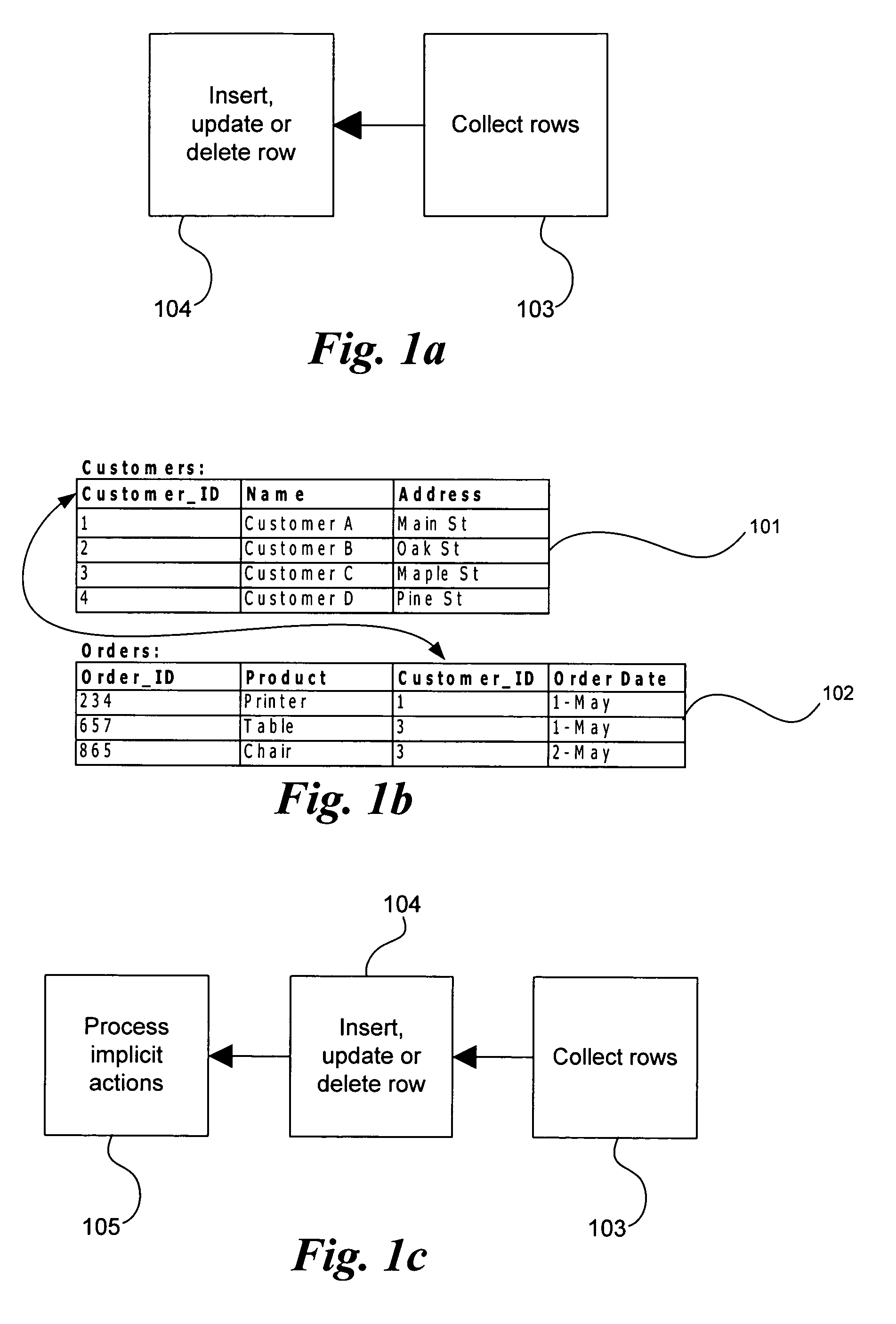
A transaction symbolizes a unit of work performed within a database management system (or similar system) against a database, and treated in a coherent and reliable way independent of other transactions. A transaction generally represents any change in a database.
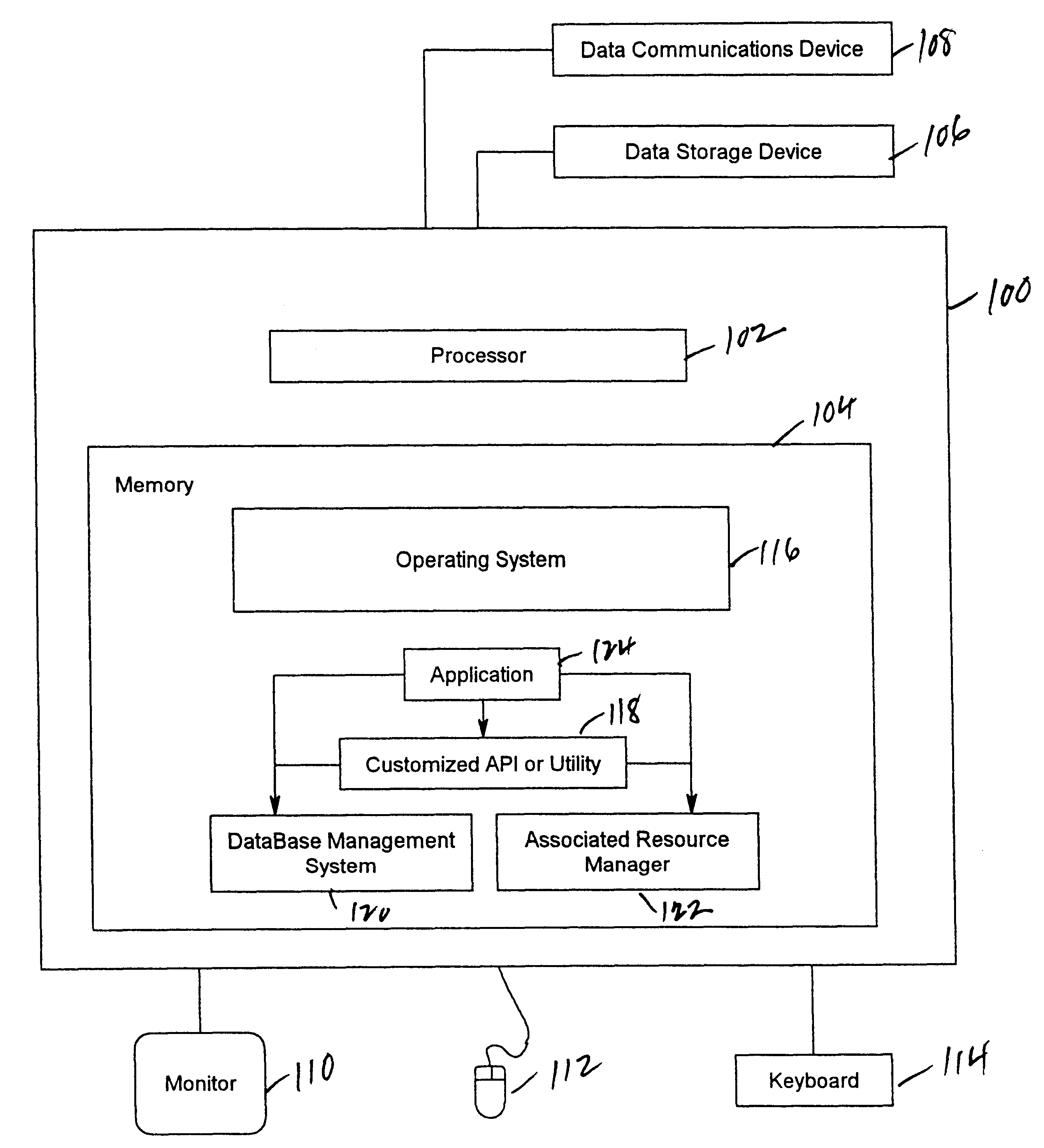
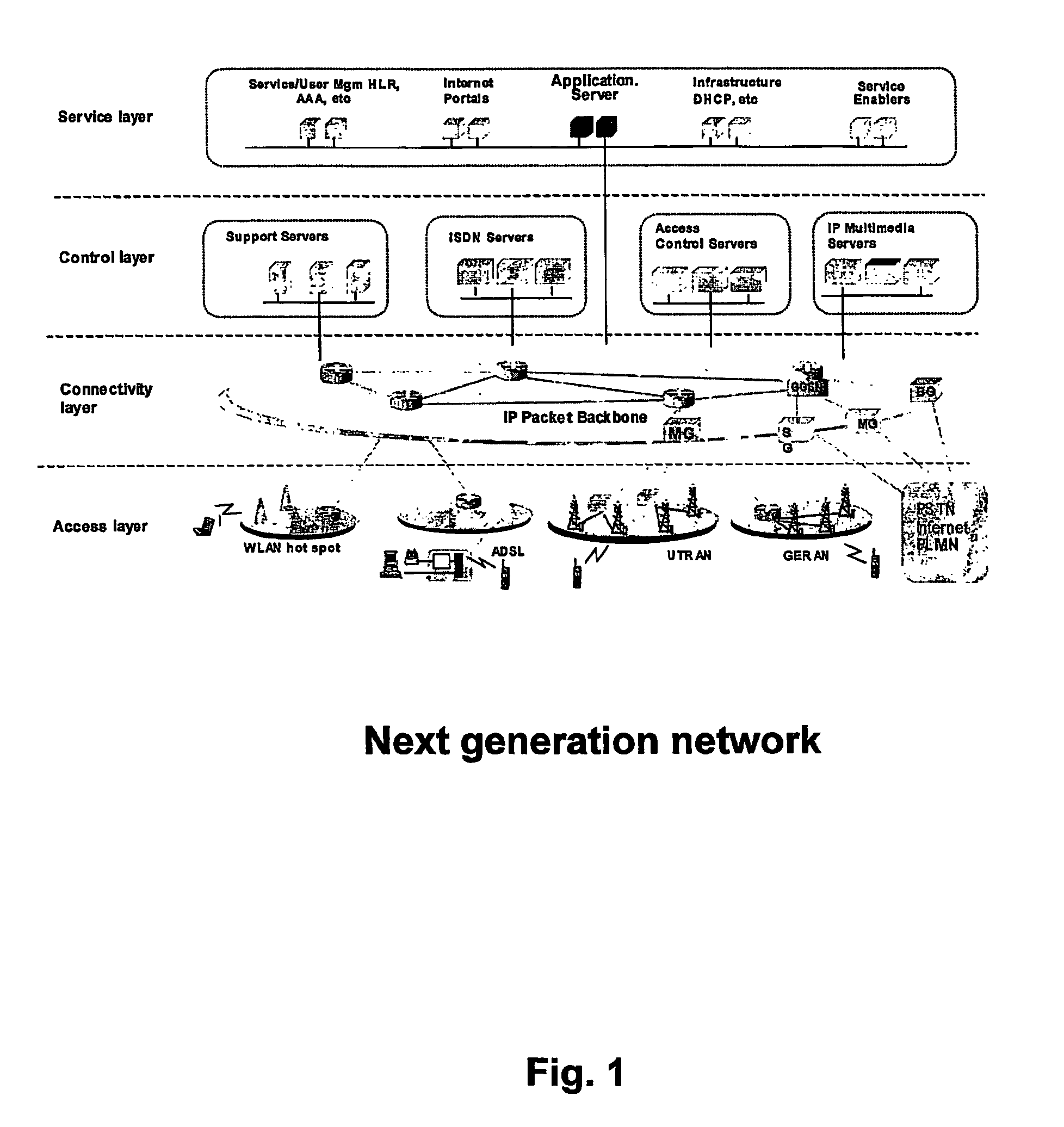
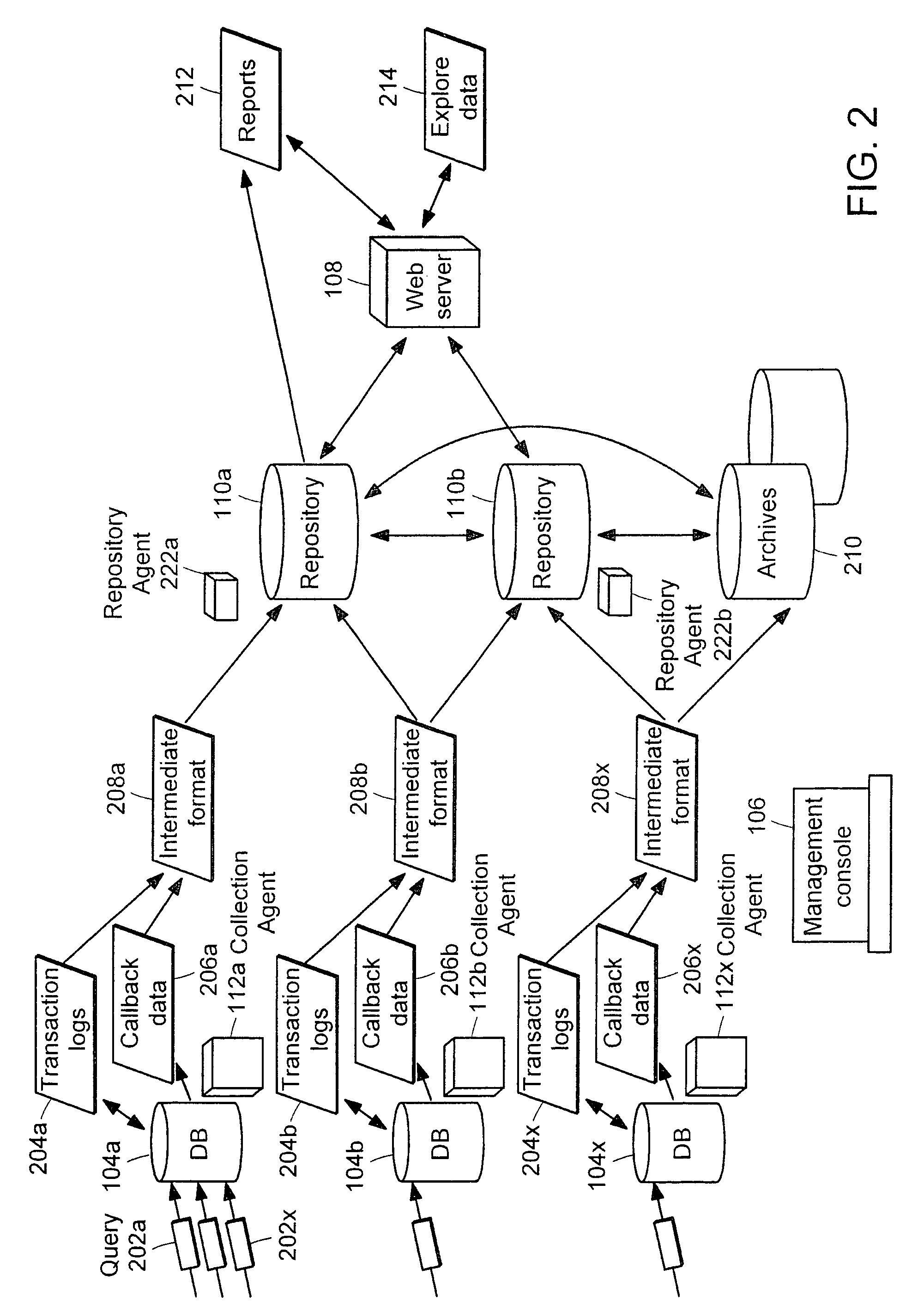
Internet database system
InactiveUS6523036B1Data processing applicationsDigital data processing detailsApplication serverHash function
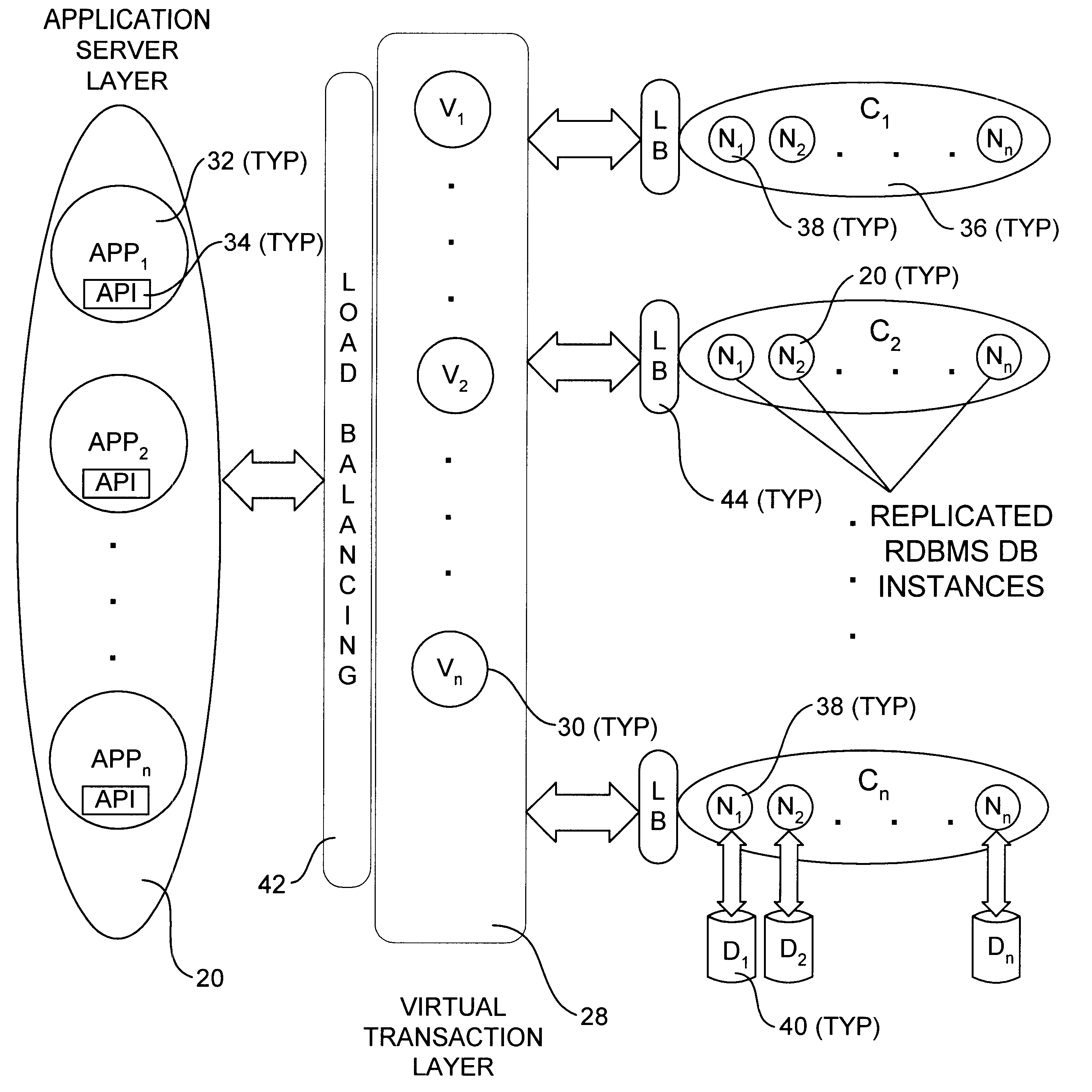
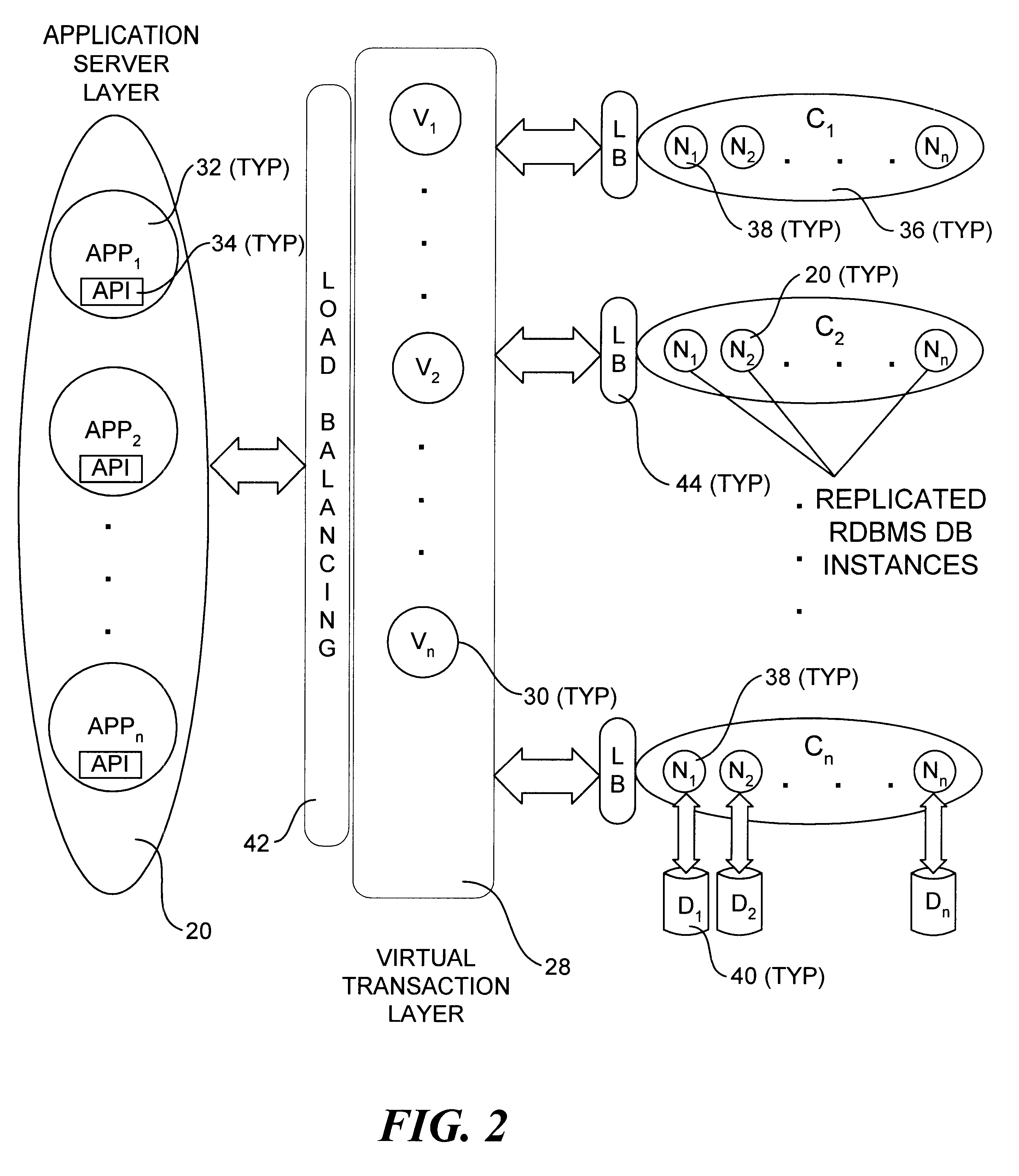
An incrementally-scalable database system and method. The system architecture enables database servers to be scaled by adding resources, such as additional servers, without requiring that the system be taken offline. Such scaling includes both adding one or more computer servers to a given server cluster, which enables an increase in database read transaction throughput, and adding one or more server clusters to the system configuration, which provides for increased read and write transaction throughput. The system also provides for load balancing read transactions across each server cluster, and load balancing write transactions across a plurality of server clusters. The system architecture includes an application server layer including one or more computers on which an application program(s) is running, a database server layer comprising two or more server clusters that each include two or more computer servers with replicated data, and an intermediate "virtual transaction" layer that includes at least two computers that facilitate database transactions with one or more databases operating in the database server layer. Data in the database(s) are evenly distributed across the server clusters in fragmented mutually exclusive subsets of data based on a hashing function. An application program interface is provided so as to enable application programs to perform a full range of database transactions without regard for where data is stored, or what database(s) is operating in the database server layer.
Owner:EMC IP HLDG CO LLC
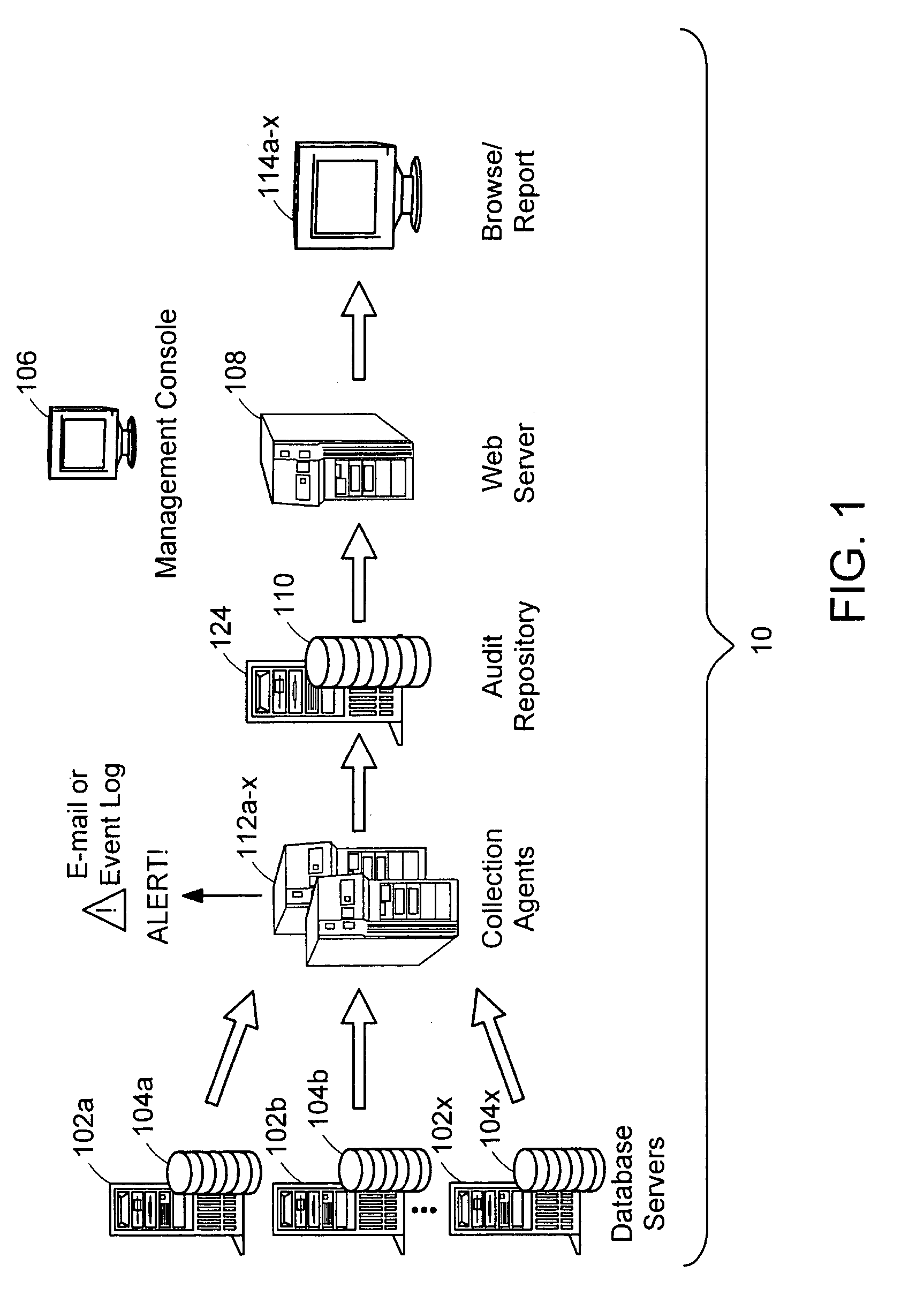
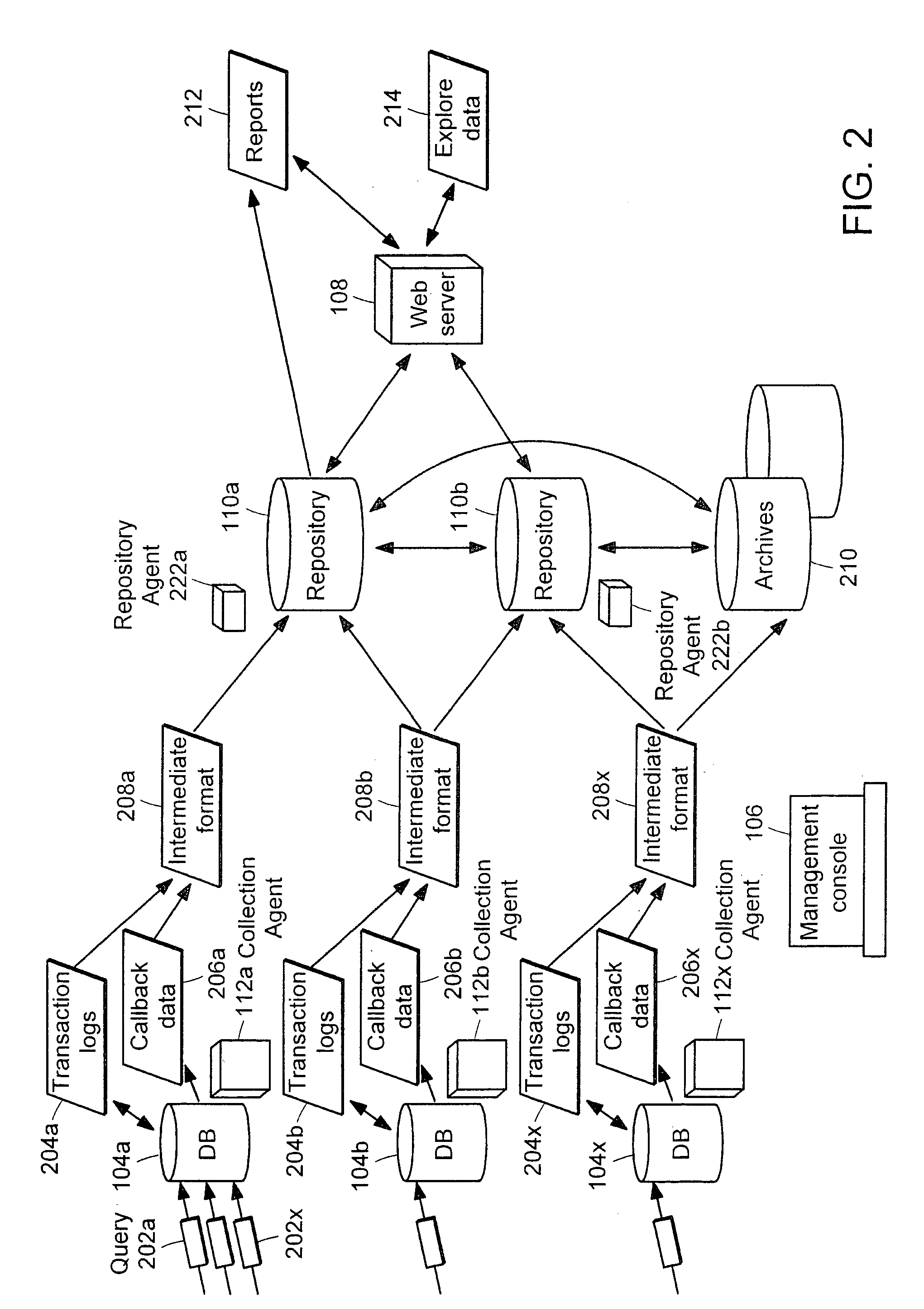
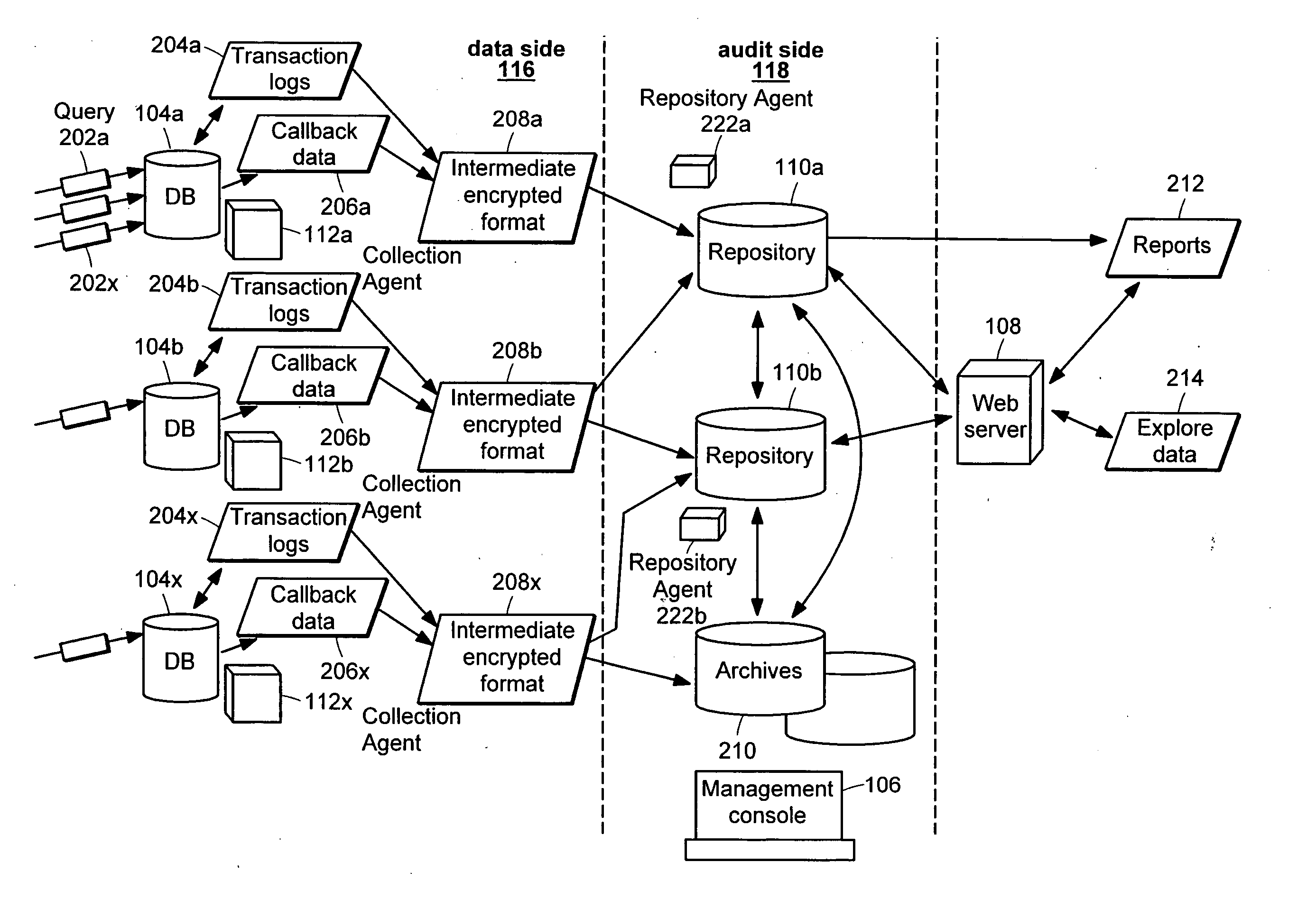
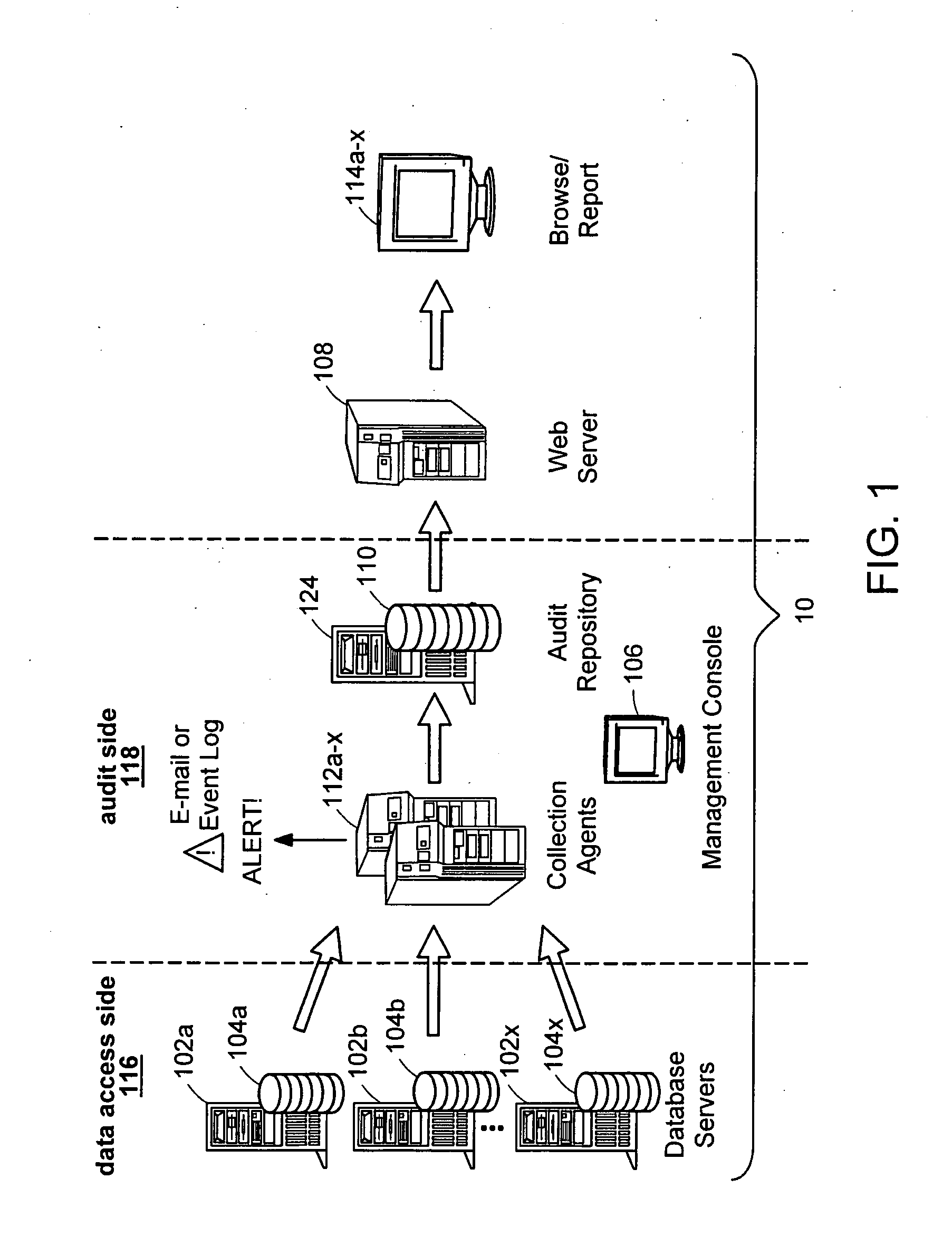
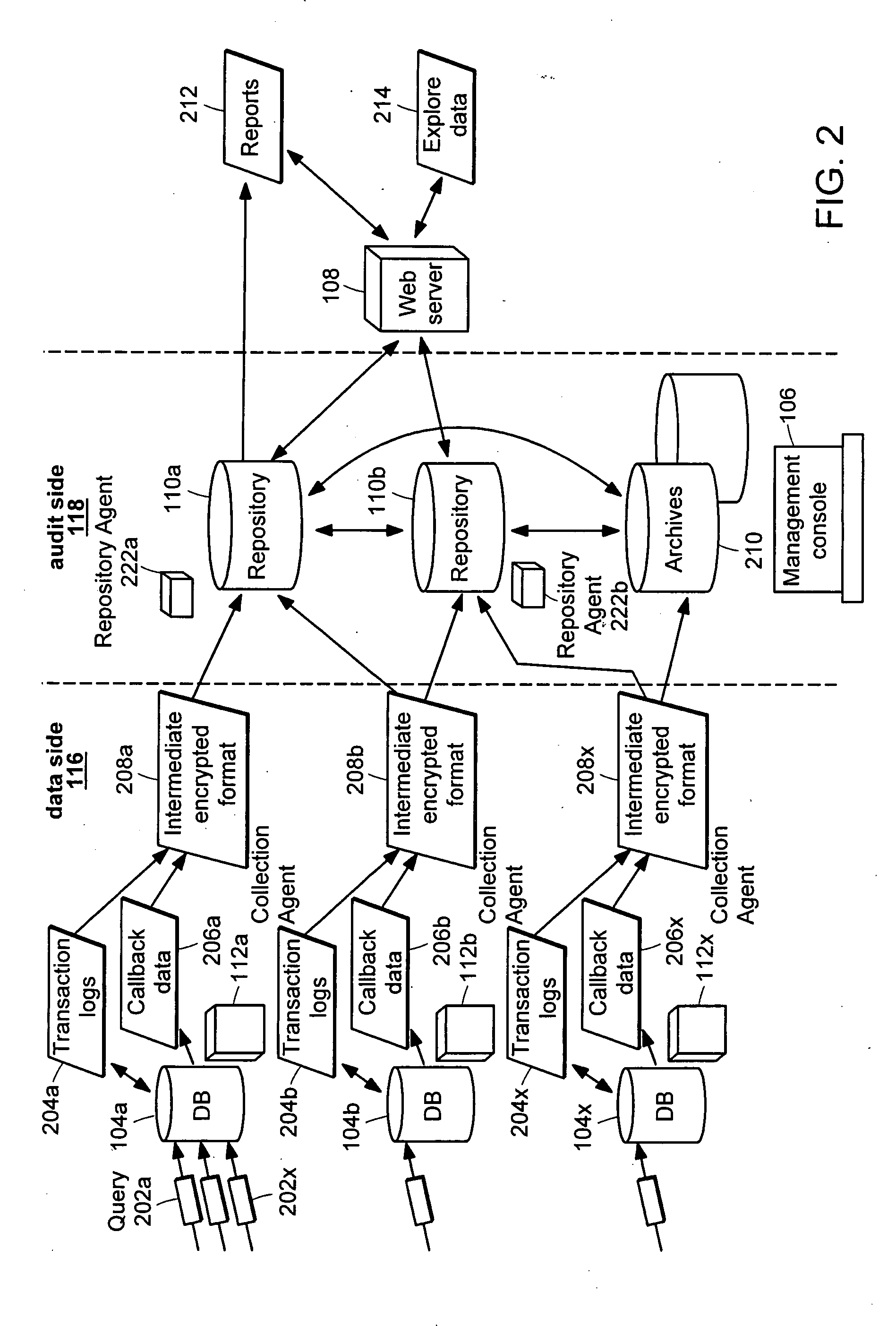
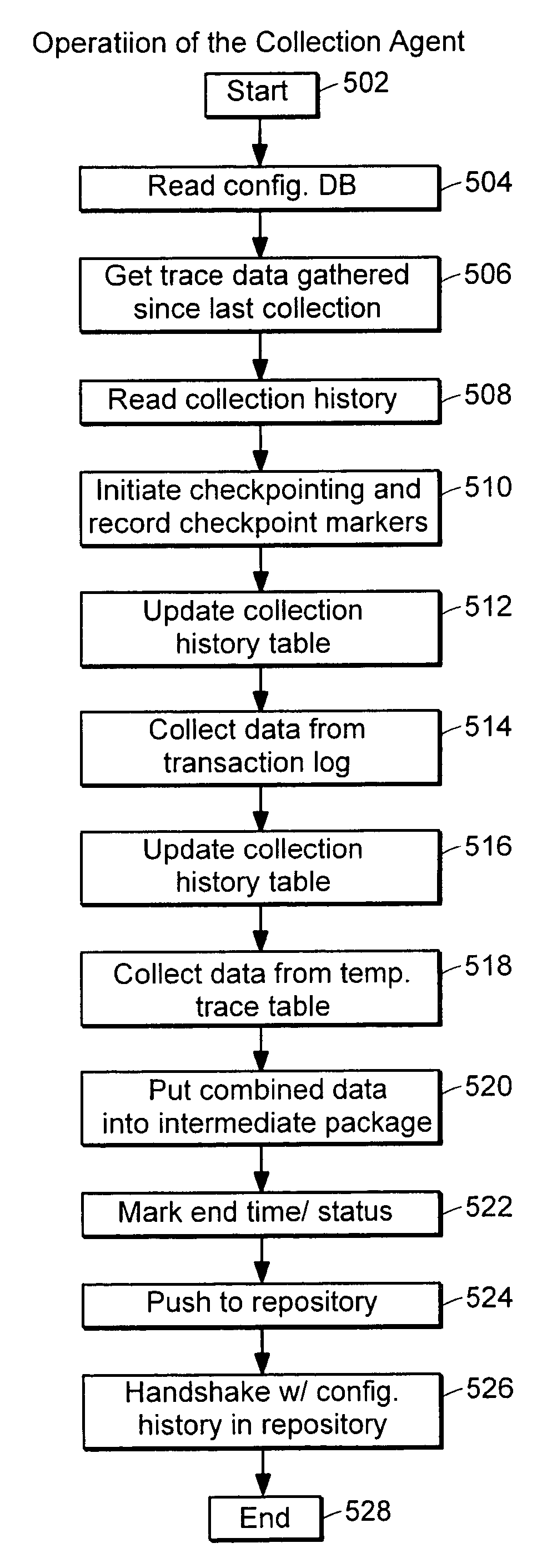
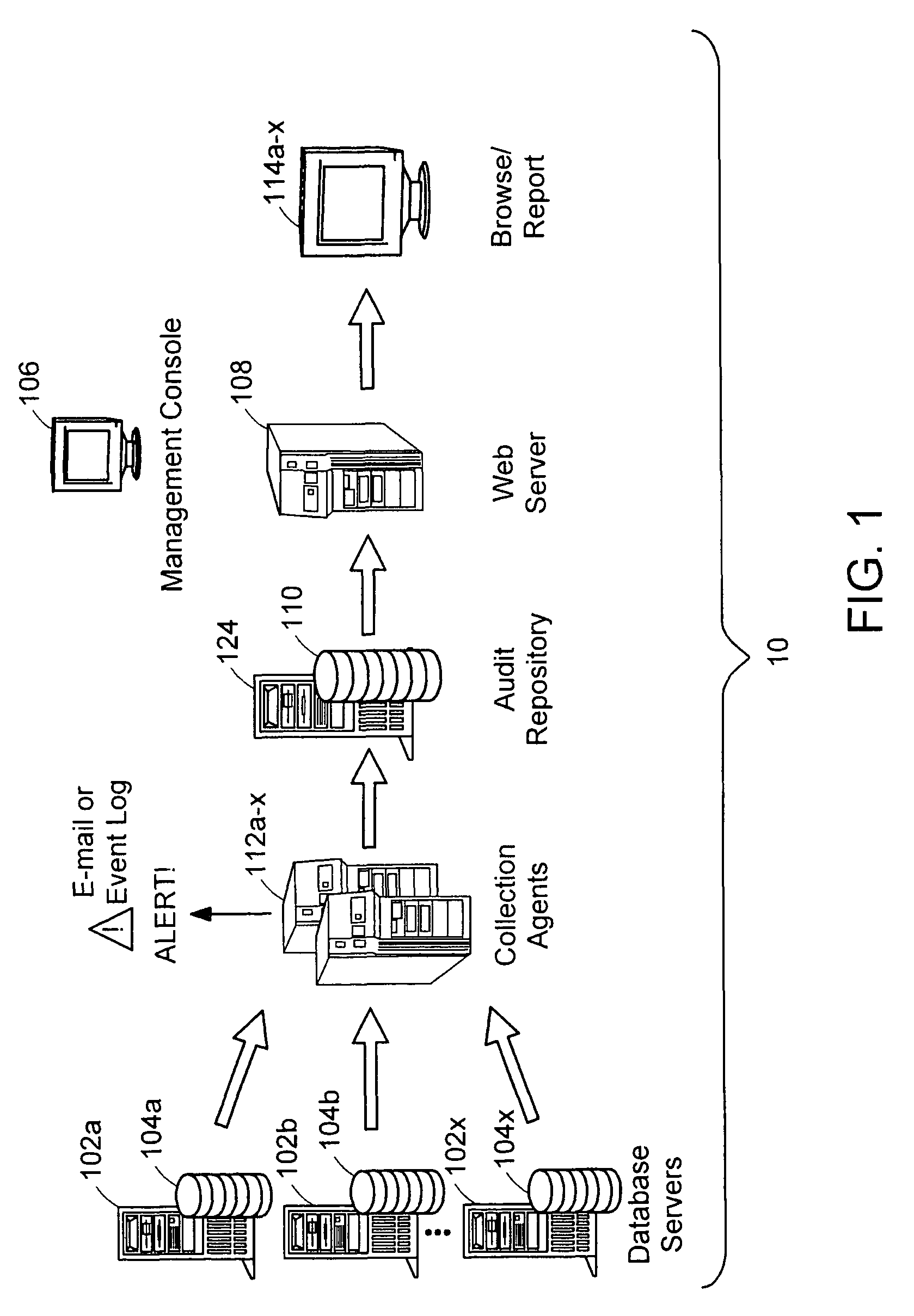
Data audit system
ActiveUS20050097149A1Digital data information retrievalComputer security arrangementsDatabase schemaCollections data
Described is a database audit system used to monitor, and optionally alert on database activity, providing a complete record of access to data and database structure. The data audit system may also provide an audit trail of data accesses and changes to database schema and permissions. A database audit may be performed by collecting data from database transaction logs and traces, exporting the collected data into a repository, and analyzing the data in the repository to create data audit reports and to provide data audit browsing capabilities.
Owner:BEYONDTRUST SOFTWARE INC
Apparatus and method for optimized application of batched data to a database
ActiveUS20110173619A1Flush cutImprove efficiencyDatabase distribution/replicationMultiprogramming arrangementsData applicationDependency relation
A computer readable medium storing executable instructions includes executable instructions to: receive a continuous stream of database transactions; form batches of database transactions from the continuous stream of database transactions; combine batches of database transactions with similar operations to form submission groups; identify dependencies between submission groups to designate priority submission groups; and apply priority submission groups to a database target substantially synchronously with the receipt of the continuous stream of database transactions.
Owner:ORACLE INT CORP
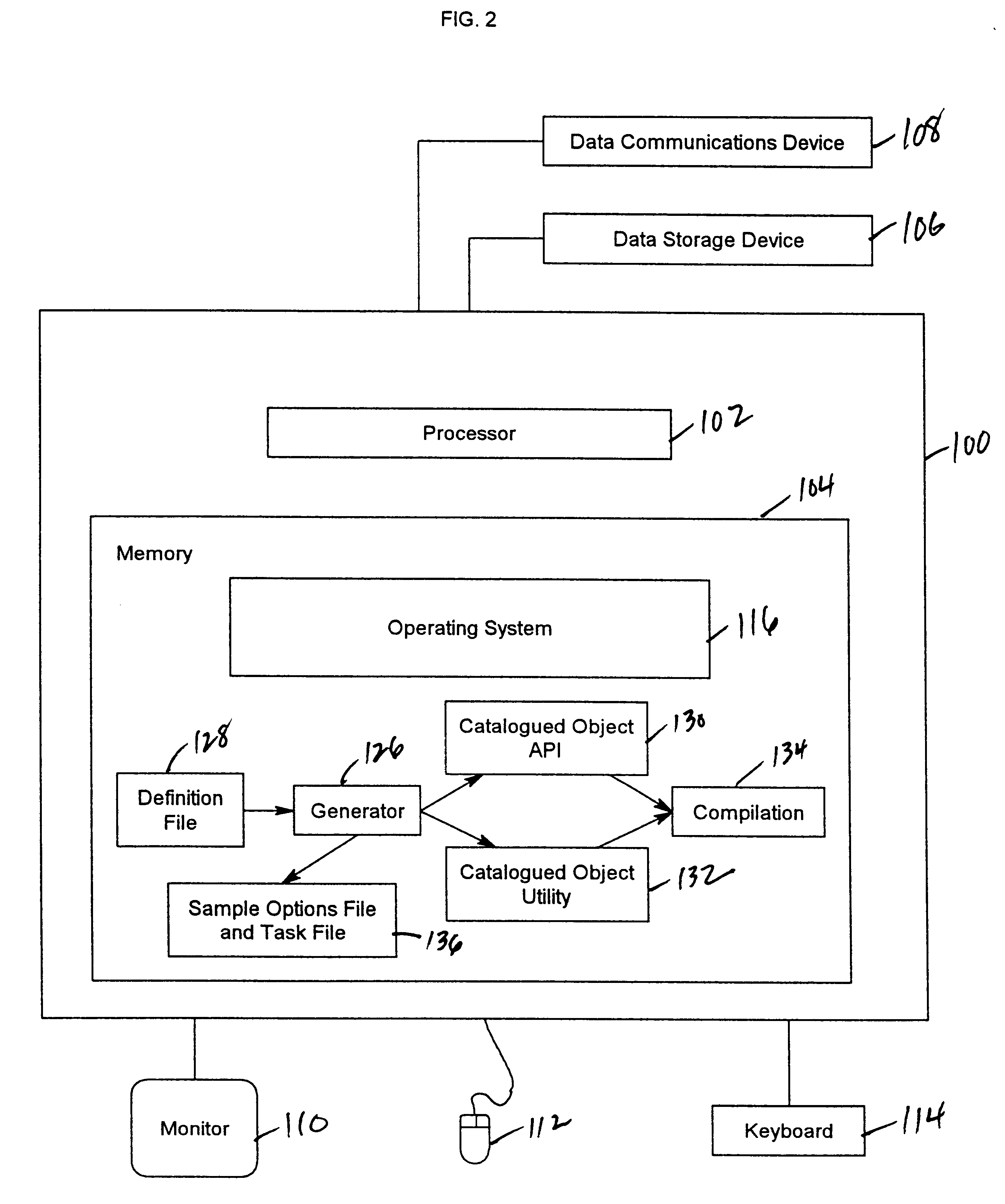
Application-independent generator to generate a database transaction manager in heterogeneous information systems
InactiveUS6321374B1Easy system integrationFacilitate application/middleware developmentData processing applicationsRelational databasesSystems integratorApplication software
A heterogeneous information system such as a digital library often uses a database manager together with other data resource manager(s), such as an object server or a video server, to manage digital content. Such a system often needs to maintain an application-specific database and / or to handle application-specific operational requirements. To facilitate system integration and application development, an application-independent reusable product is created which generates a custom system component or utility, such as a loader, according to a specification provided by a system integrator or an application developer.
Owner:IBM CORP
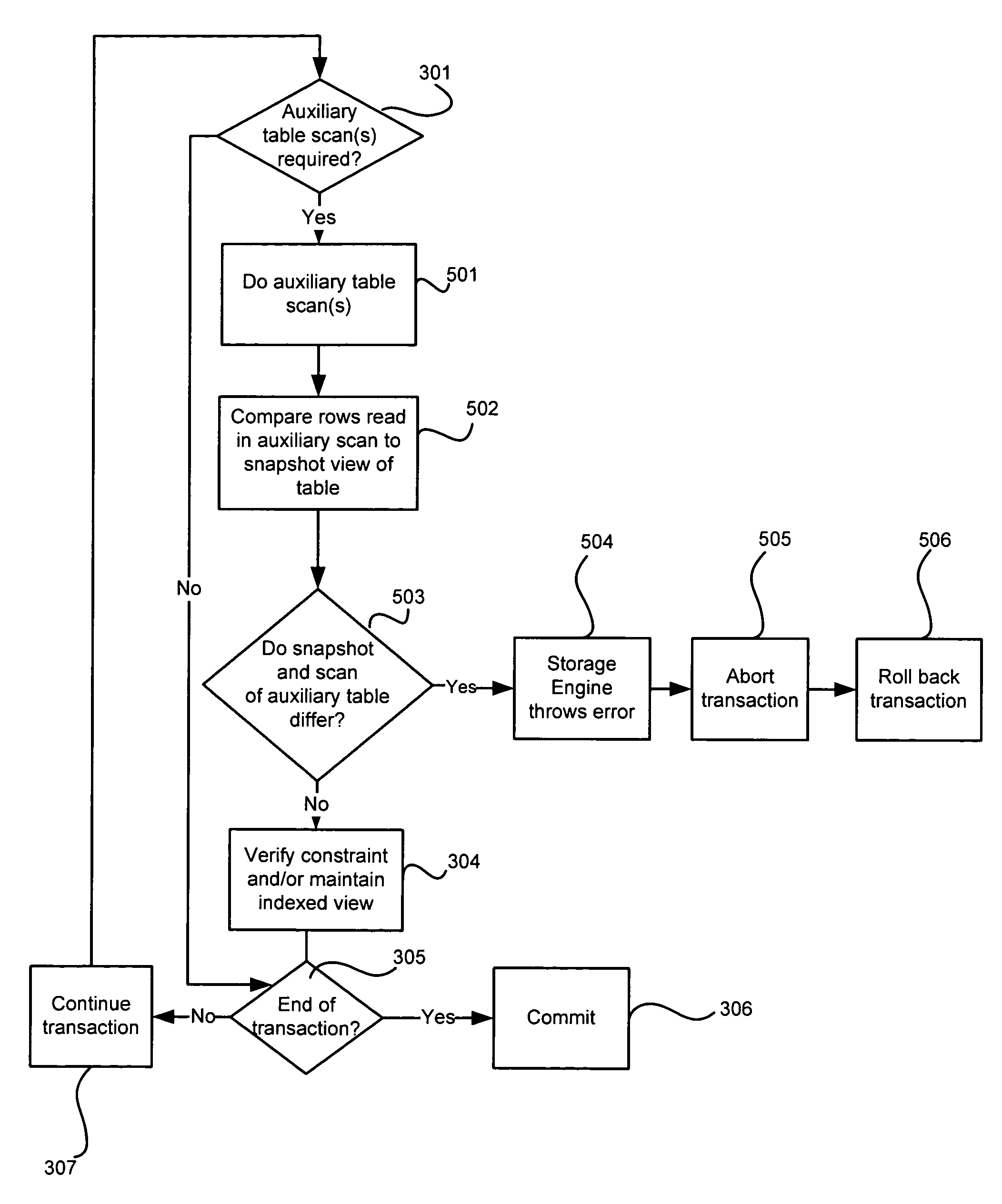
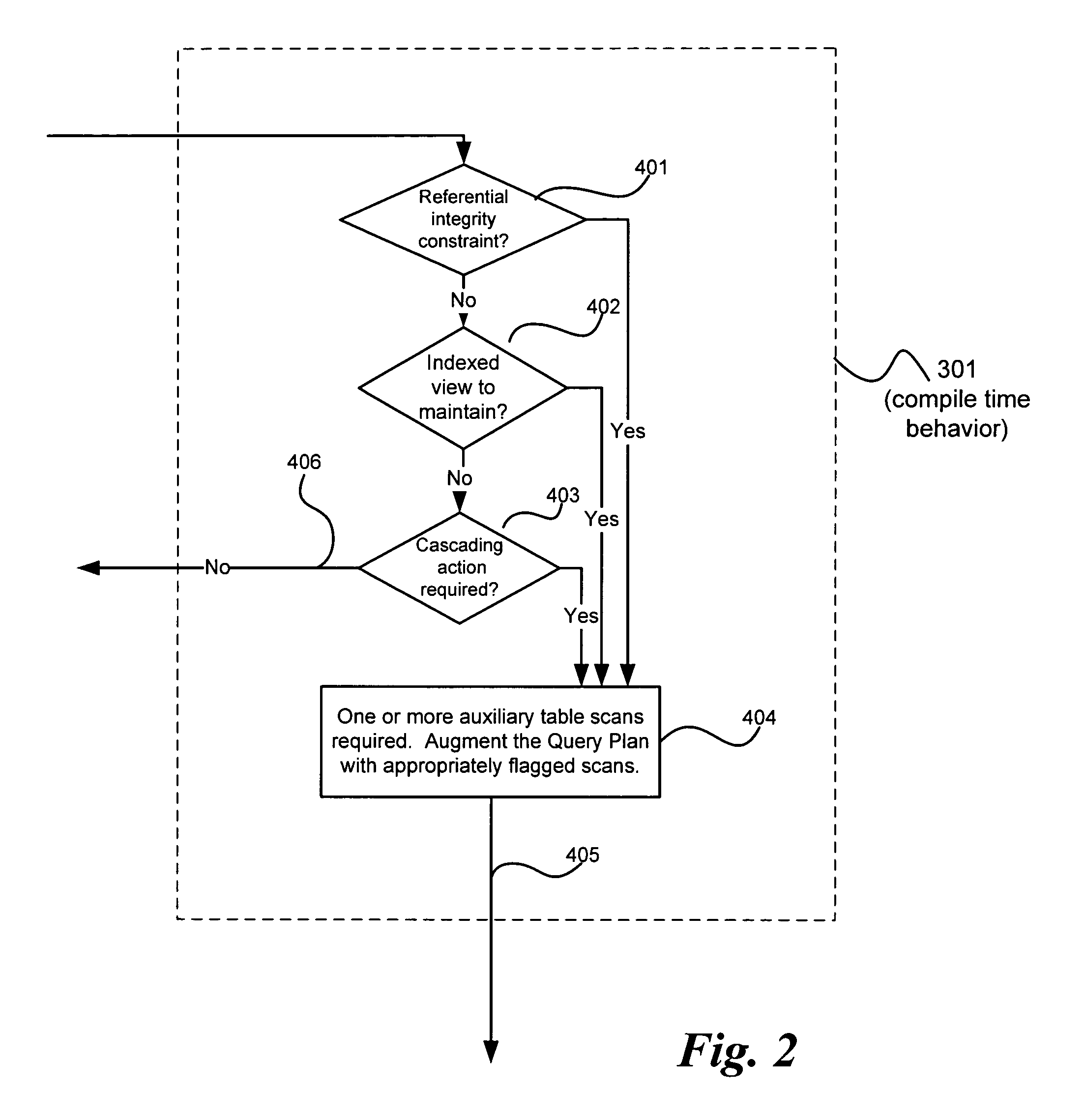
Systems and methods for avoiding database anomalies when maintaining constraints and indexes in presence of snapshot isolation
InactiveUS7653665B1Detecting and avoiding anomalyDigital data information retrievalDigital data processing detailsData validationSource Data Verification
A system and method avoids anomalies in presence of data manipulation language (DML) plans maintaining dependent objects and snapshot isolation. An anomaly due to using a snapshot isolation level within the transaction is detected within a database transaction and the transaction is aborted based upon that detection. Involved in making the anomaly detection is determining whether a view of particular data accessed during the transaction under a snapshot isolation view to ensure read consistency differs from a view of the data under another isolation level, such as the read committed isolation level. Then a detection is made that an anomaly may occur if it is determined that the view of the data accessed during the transaction under the snapshot isolation differs from the view of the data under the other isolation level. Such anomaly avoidance prevents an indexed view being maintained nor a referential integrity constraint validated based on incorrect data.
Owner:MICROSOFT TECH LICENSING LLC
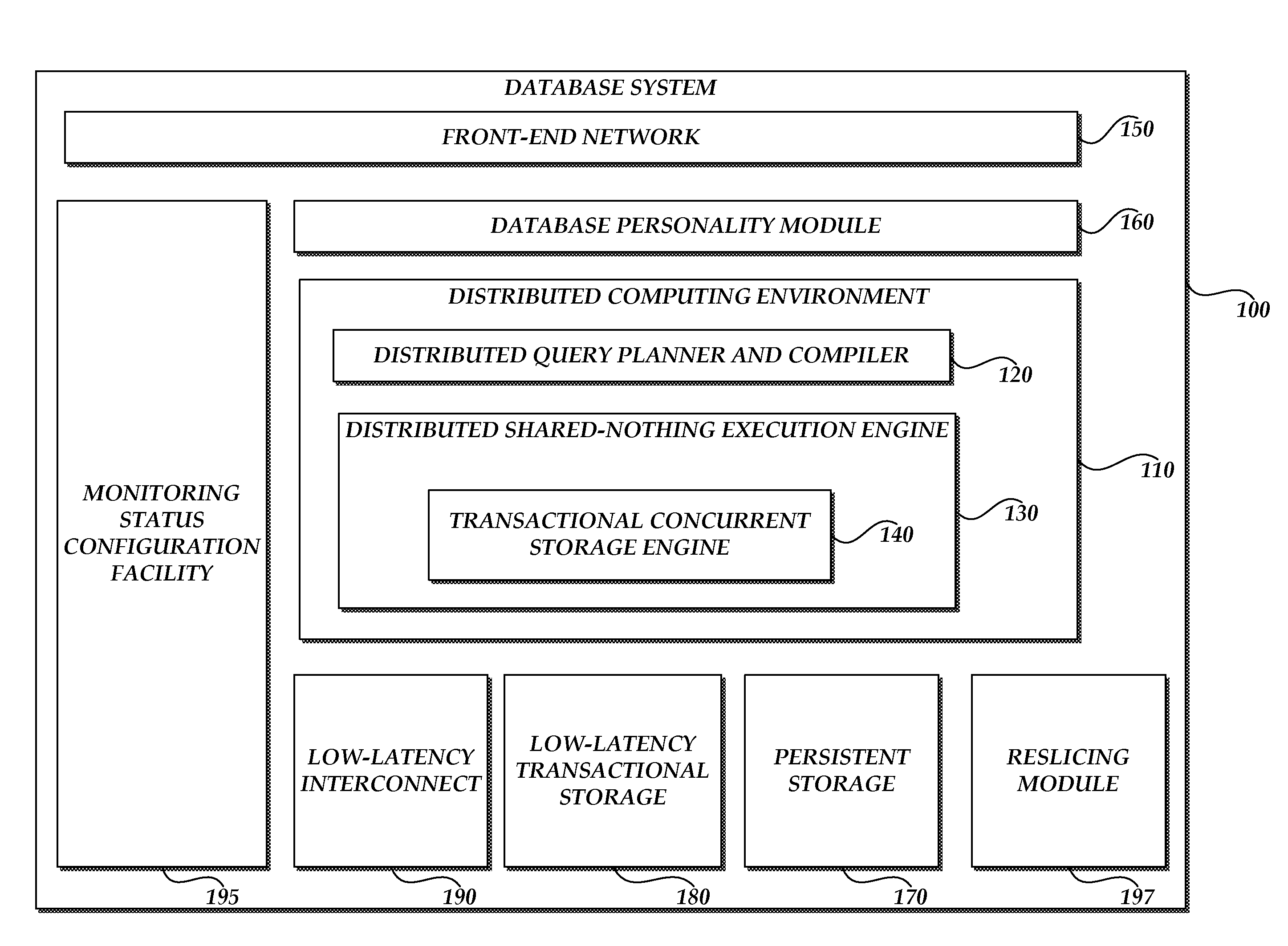
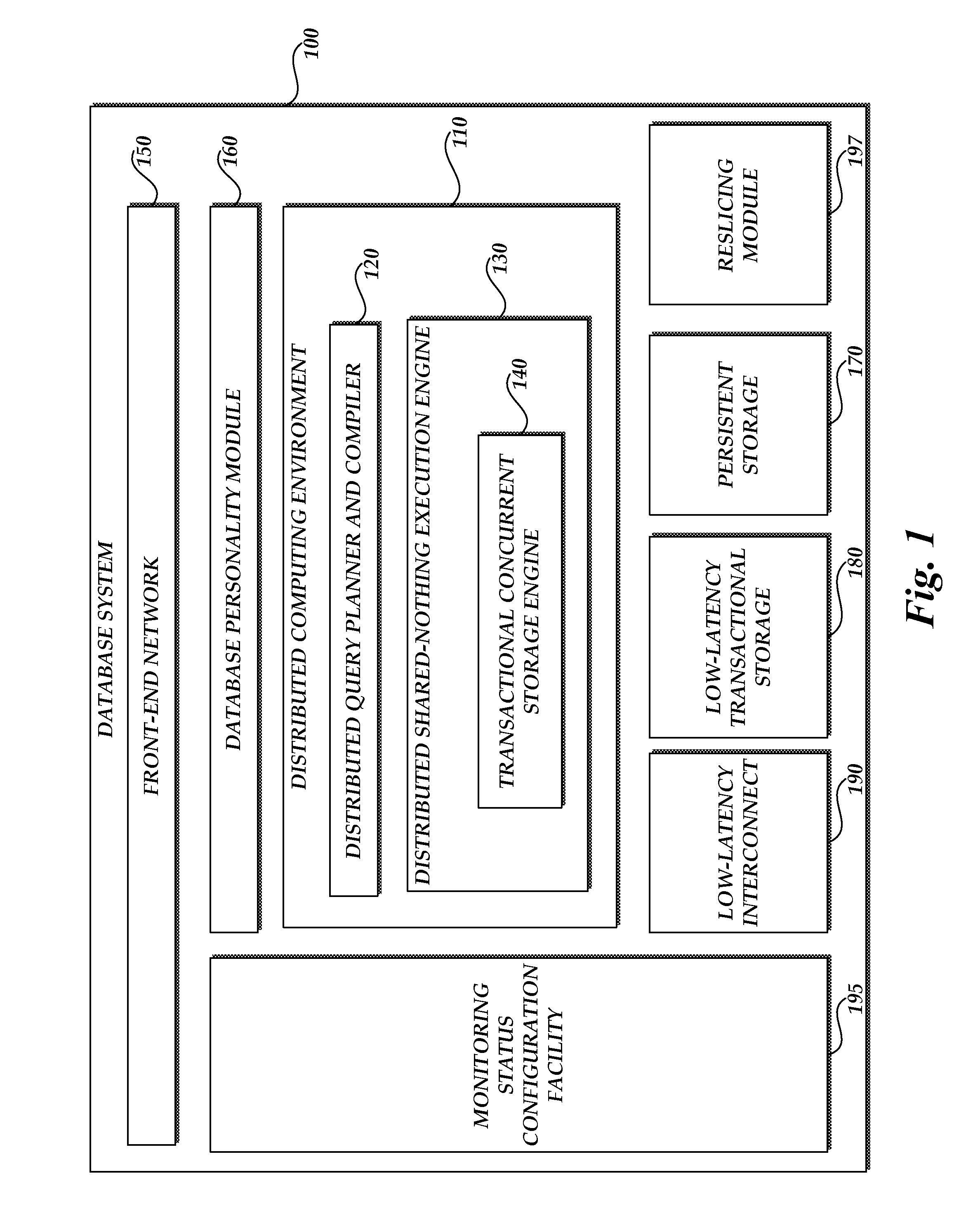
Systems and methods for reslicing data in a relational database
ActiveUS20120310991A1Digital data processing detailsRelational databasesRelational databaseDistribution function
Systems and methods for reslicing data in a representation of a relational database are disclosed. In one embodiment, the database includes a representation including a first slice. The database system creates a plurality of new slice and to create a plurality of write queues. The database system copies units of data in the first slice to the new slices according to a distribution function. The distribution function determines, for each unit of data in the first slice, one of the new slices into which to copy the unit of data. The database system asynchronously writes one or more actions of a set of one or more asynchronous database transactions to the first slice when copying the data in the first slice to the new slices. The database asynchronously enqueues the one or more actions of the set of asynchronous database transactions in the write queues according to the distribution function.
Owner:MARIADB USA INC
Efficient overcommitment of main-memory based virtual database system to disk
ActiveUS9122765B1Improve performanceAddressing slow performanceDigital data processing detailsWebsite content managementComputerized systemData needs
Owner:VMWARE INC
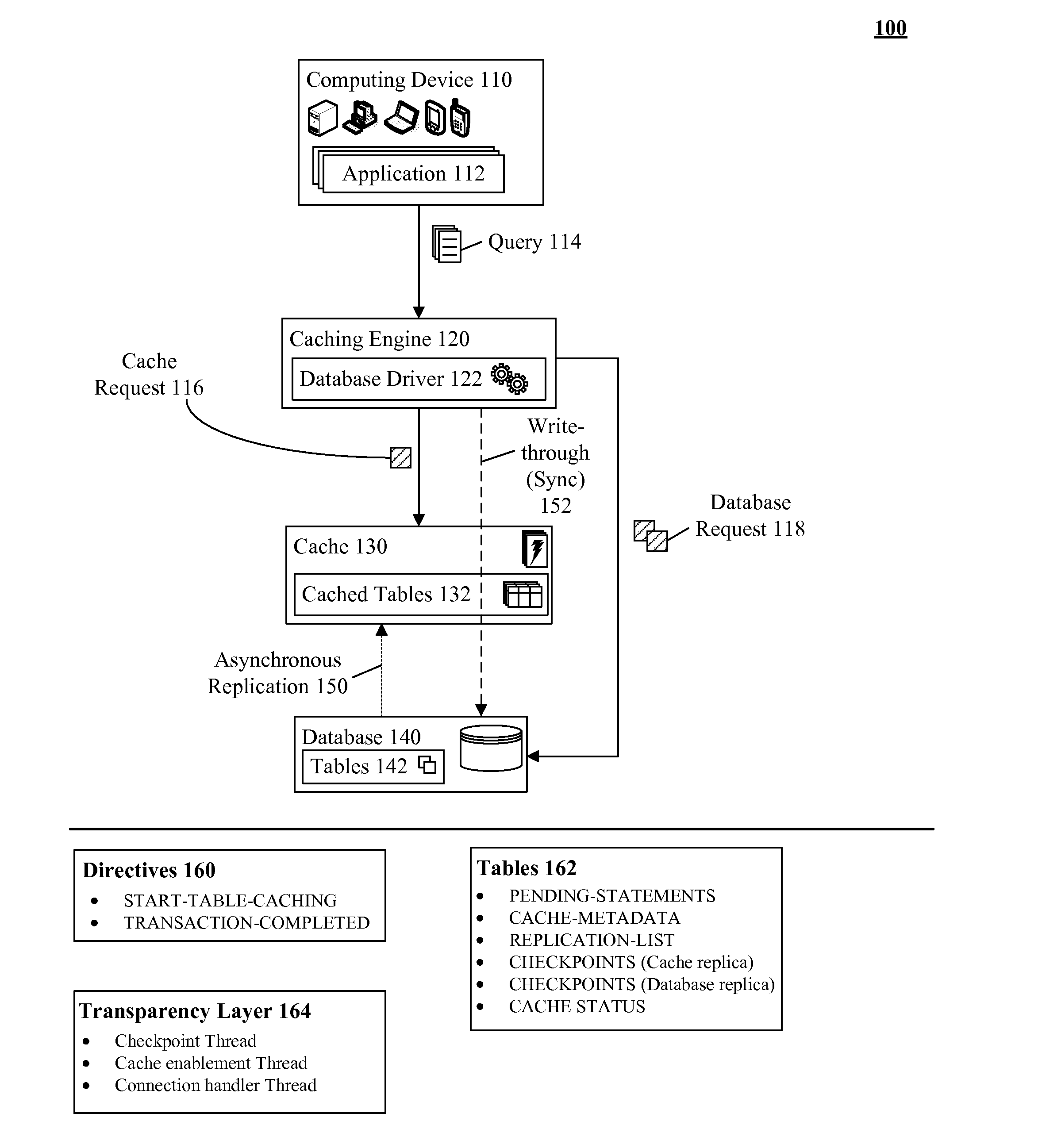
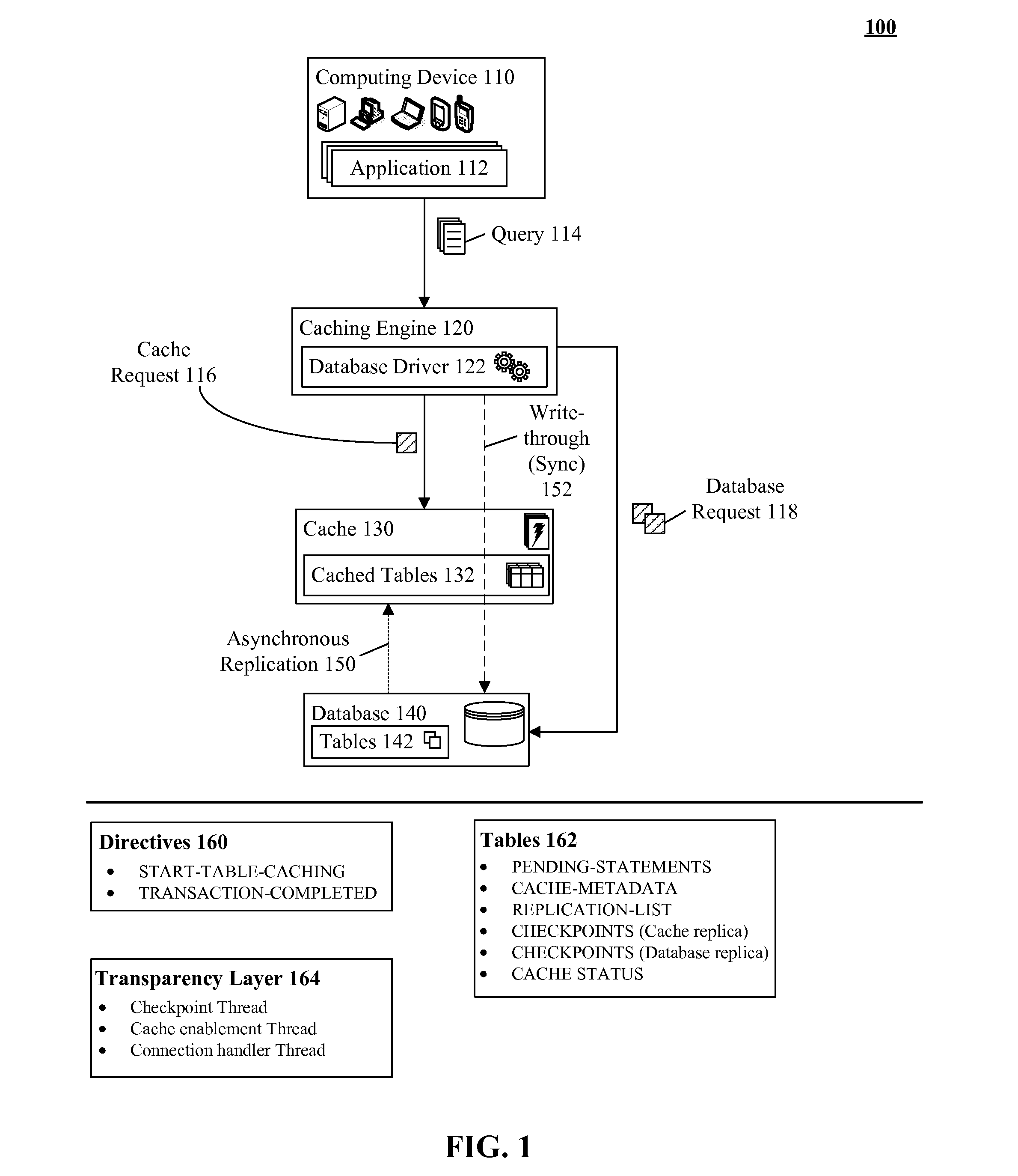
Database caching utilizing asynchronous log-based replication
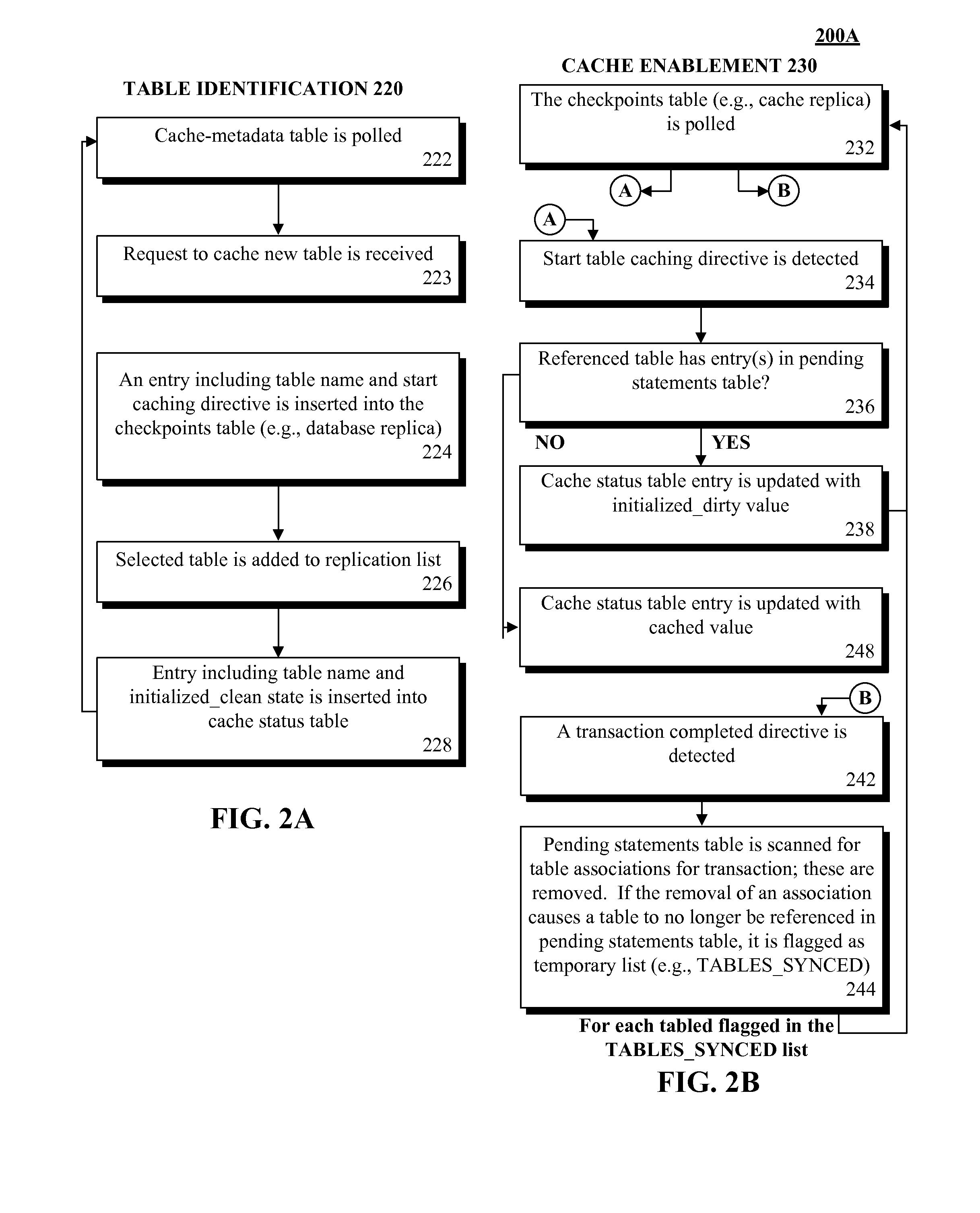
ActiveUS8548945B2Digital data information retrievalDigital data processing detailsRelational database management systemDatabase caching
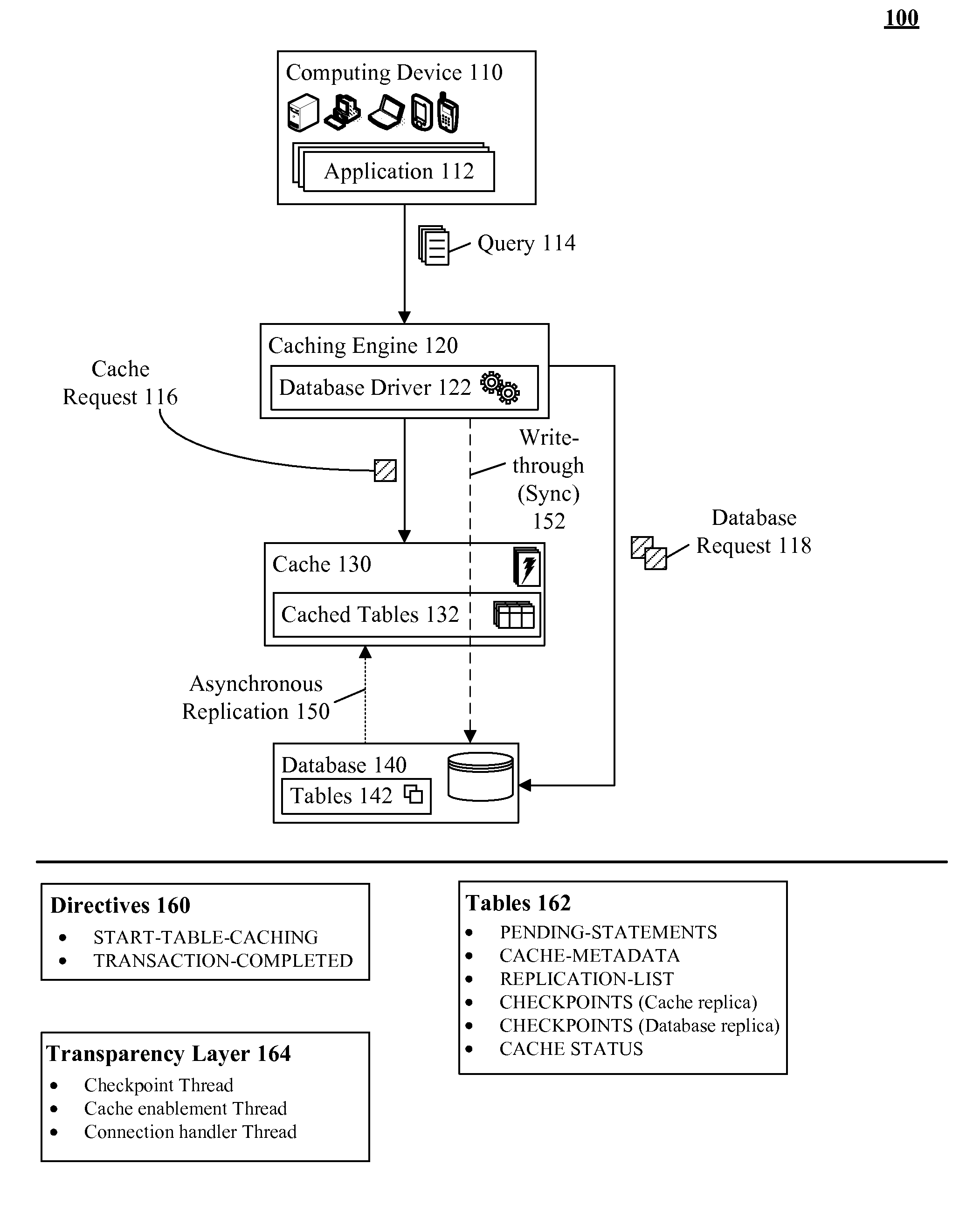
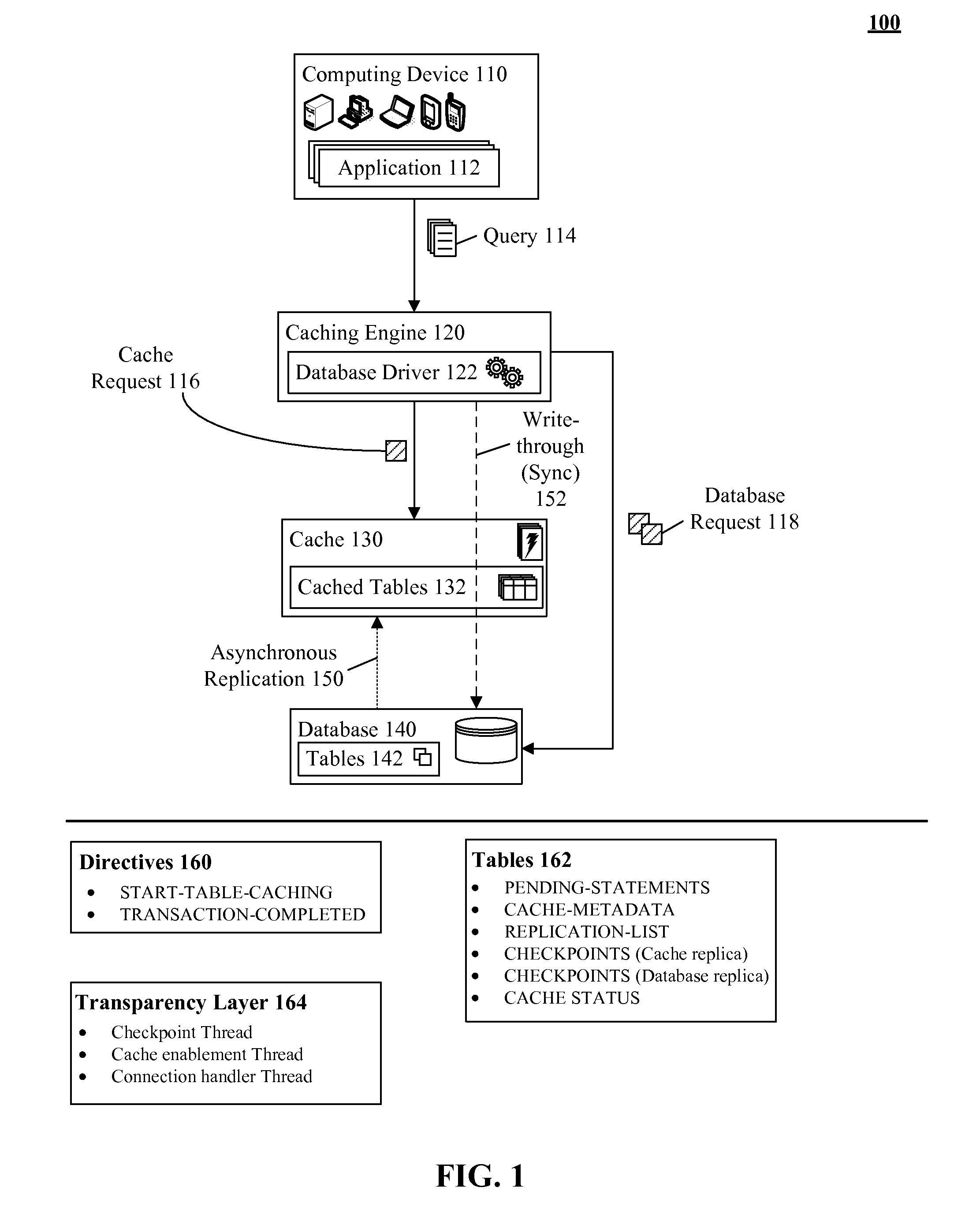
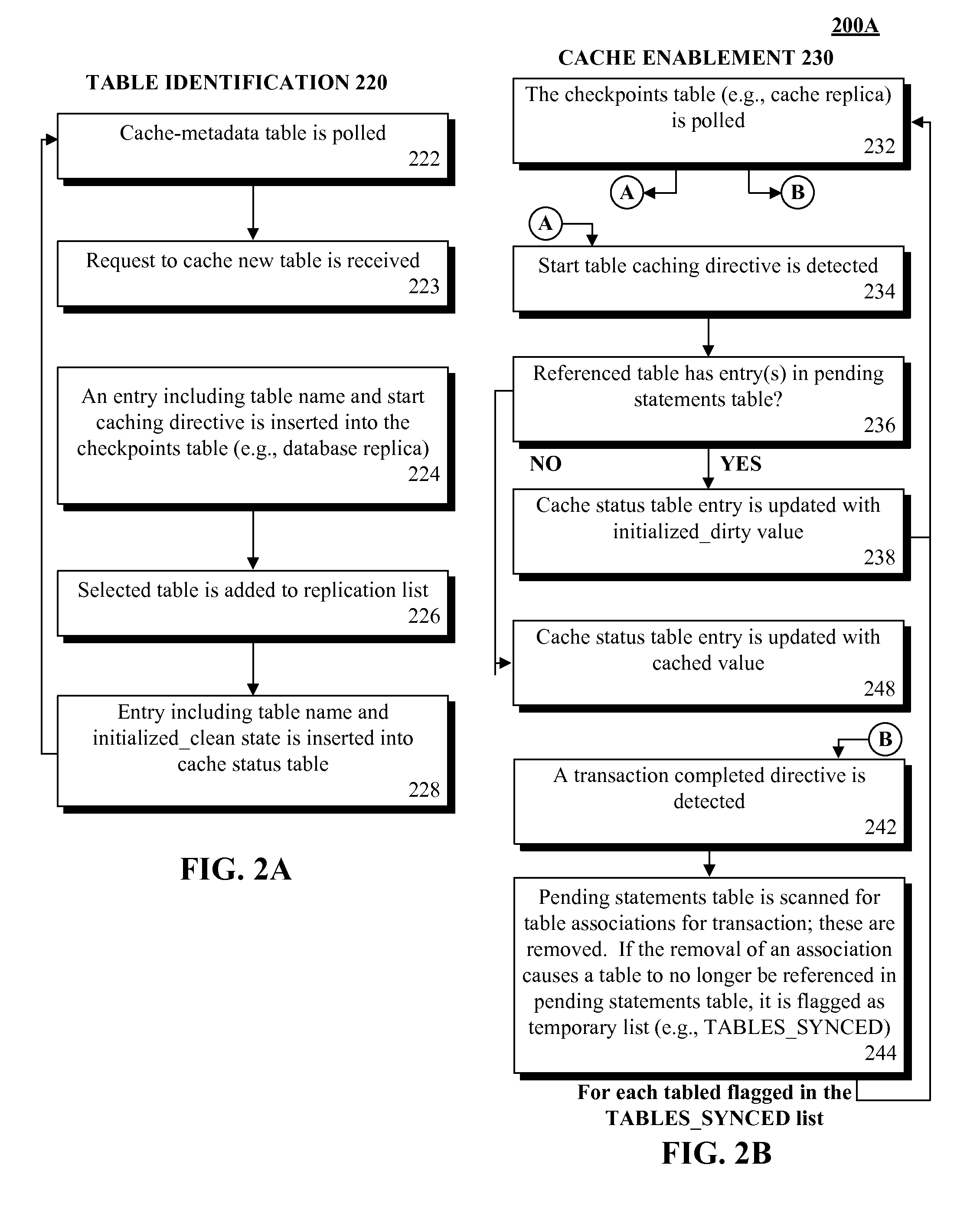
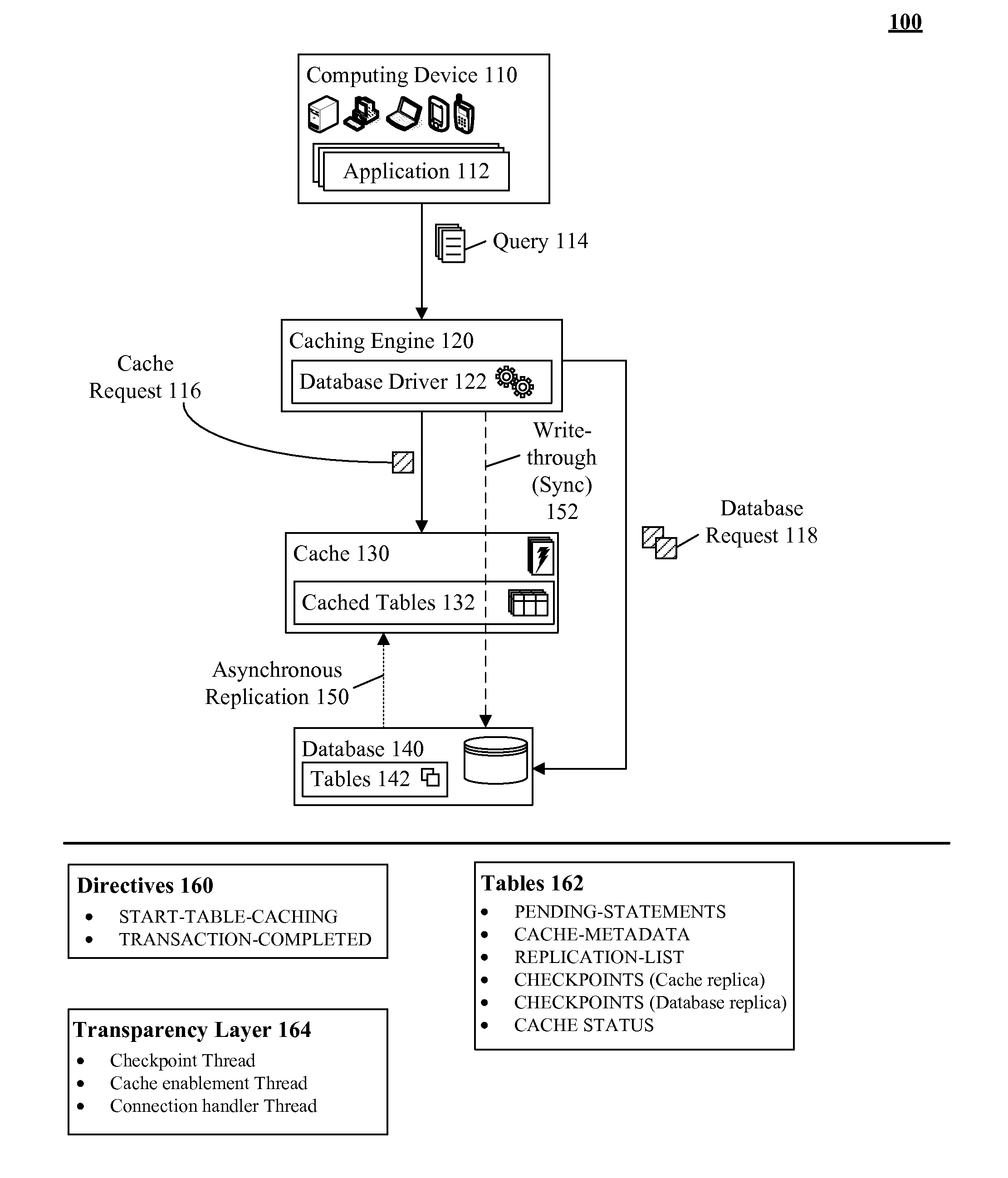
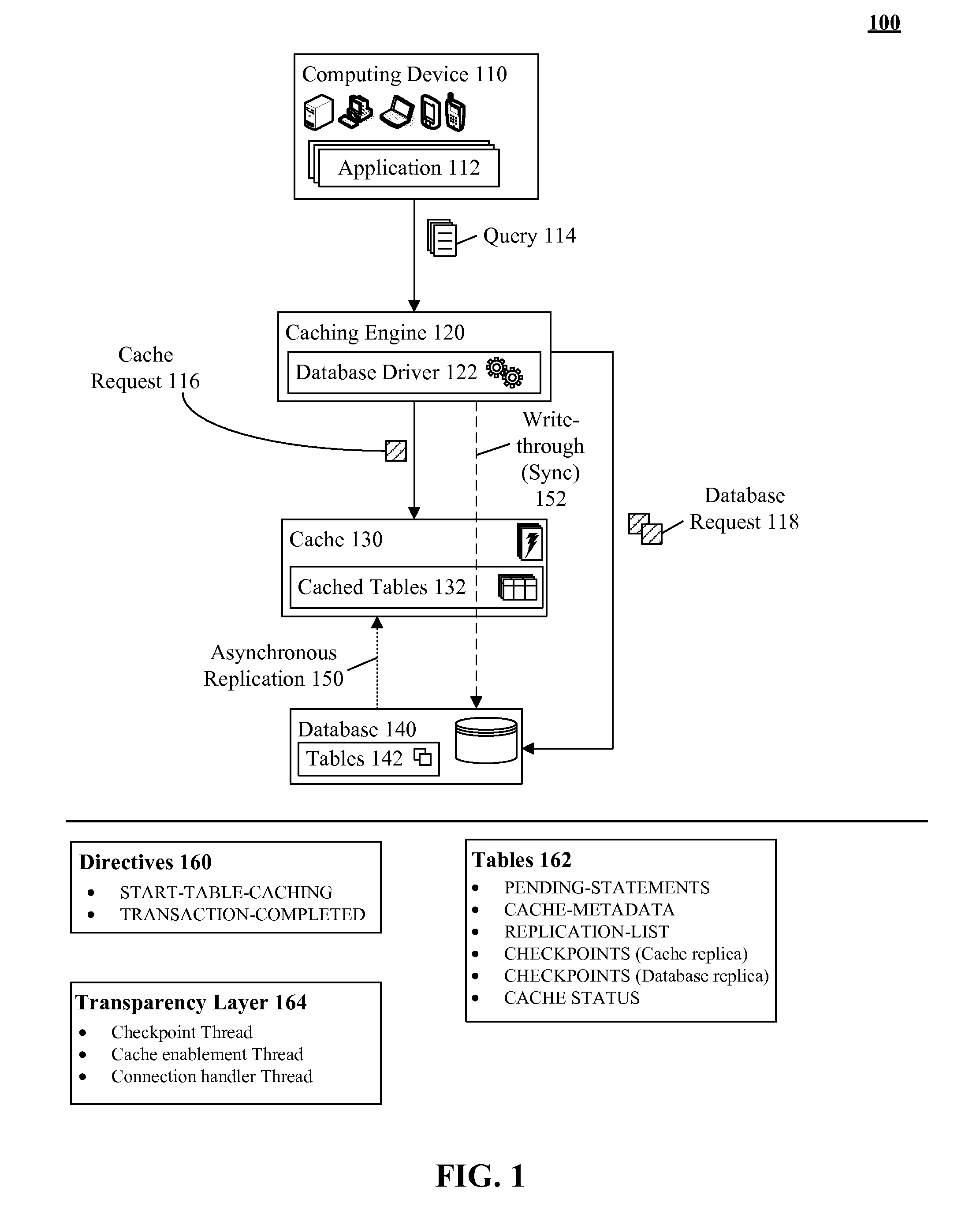
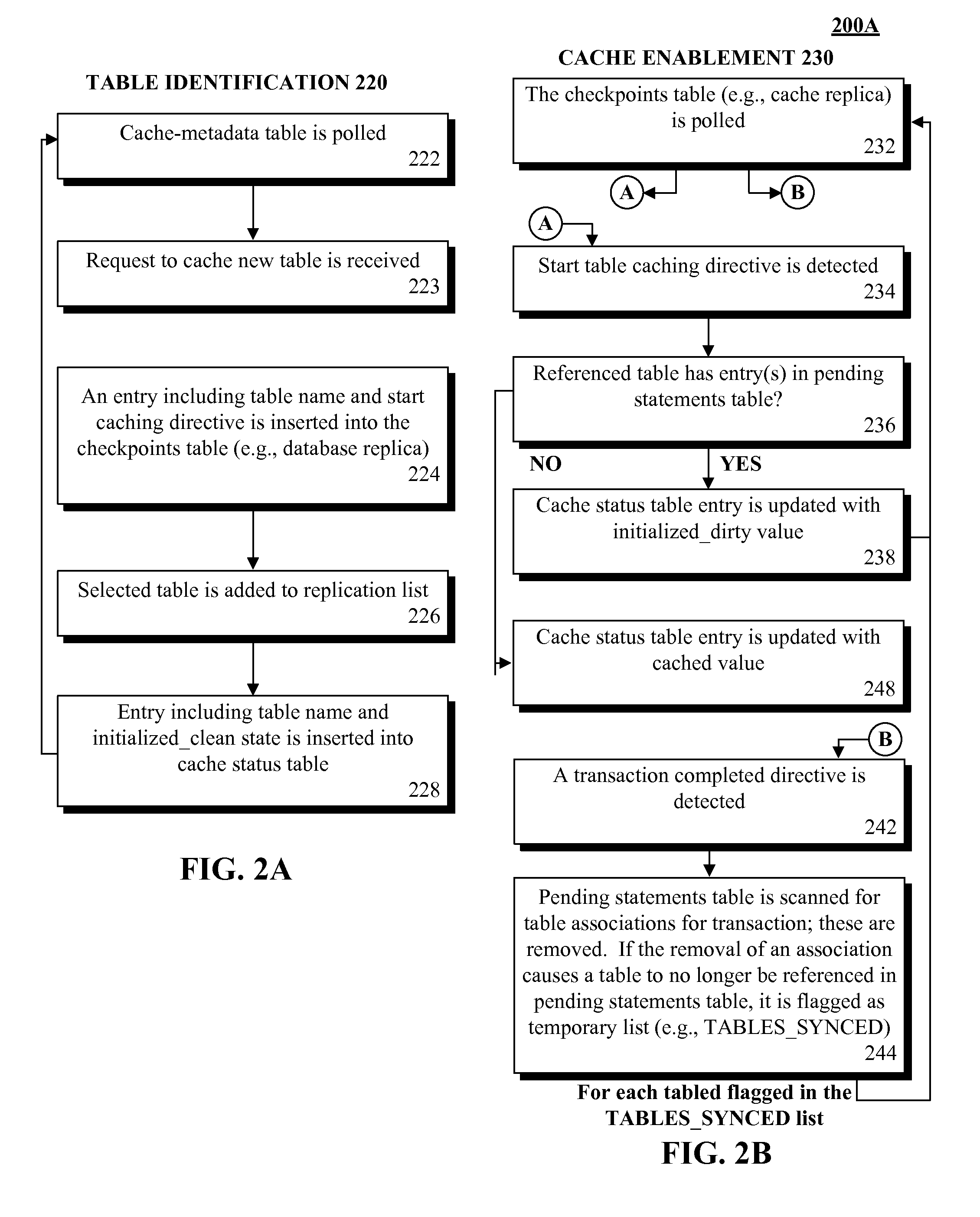
A database table within a database to persist within a cache as a cached table can be identified. The database can be a relational database management system (RDBMS) or an object oriented database management system (OODBMS). The cache can be a database cache. Database transactions within can be logged within a log table and the cached table within the cache can be flagged as not cached during runtime. An asynchronous replication of the database table to the cached table can be performed. The replication can execute the database transactions within the log table upon the cached table. The cached table can be flagged as cached when the replication is completed.
Owner:INT BUSINESS MASCH CORP
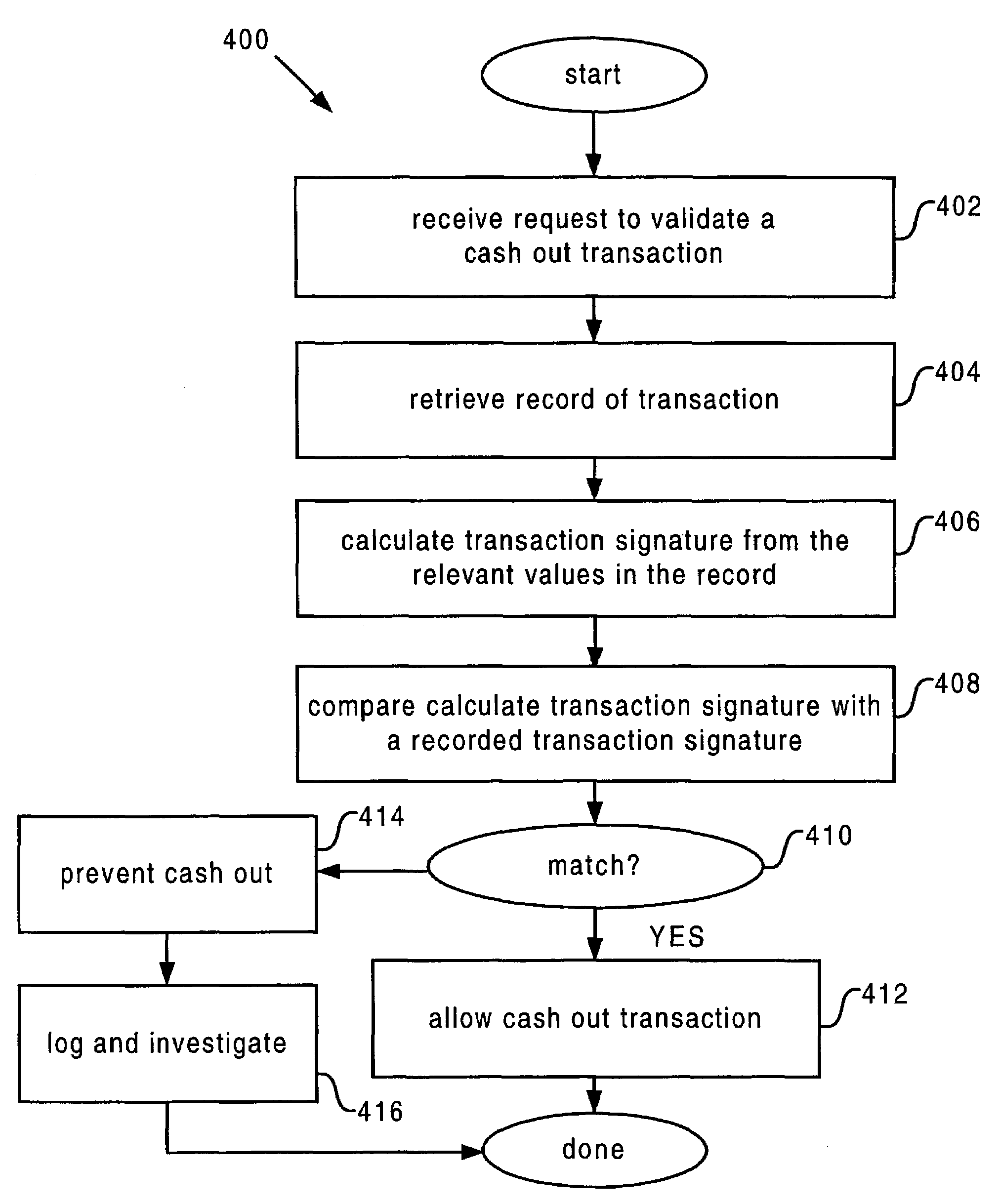
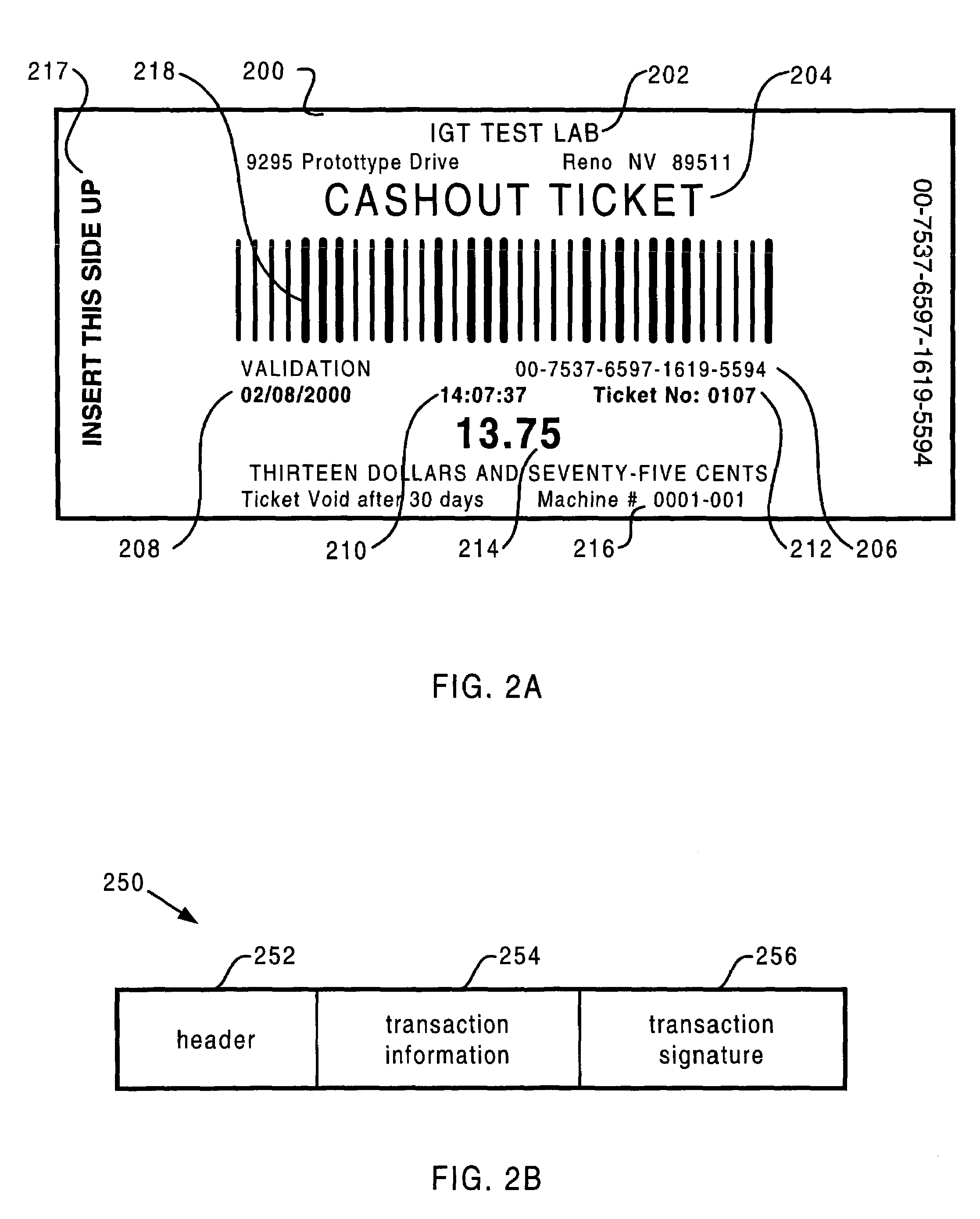
Transaction signature
The present invention provides systems and methods for protecting transaction information stored in a database of a gaming network. To accomplish this, a transaction signature is generated each time the user completes a transaction on a gaming machine. The transaction signature is generated using transaction information from a particular transaction. The transaction signature and transaction information are stored together in a network database. Upon subsequent access to the transaction information in the database, the transaction signature for the transaction information is recalculated based on the transaction information at that time. The new transaction signature is then compared to the transaction signature previously stored. Any differences between the two transaction signatures may be used to signal unauthorized alteration in the database transaction information.
Owner:IGT
Database caching utilizing asynchronous log-based replication
ActiveUS20130080388A1Digital data information retrievalDigital data processing detailsRelational database management systemDatabase caching
A database table within a database to persist within a cache as a cached table can be identified. The database can be a relational database management system (RDBMS) or an object oriented database management system (OODBMS). The cache can be a database cache. Database transactions within can be logged within a log table and the cached table within the cache can be flagged as not cached during runtime. An asynchronous replication of the database table to the cached table can be performed. The replication can execute the database transactions within the log table upon the cached table. The cached table can be flagged as cached when the replication is completed.
Owner:IBM CORP
Real-time transaction scheduling in a distributed database
InactiveUS20120278293A1Digital data processing detailsDatabase distribution/replicationDistributed databaseData bank
In one exemplary embodiment, a method of a distributed database system includes the step of receiving a database transaction with a node of the distributed database system. A priority of the database transaction is determined. A load of a transaction queue of the node is determined. The execution of a database transaction is delayed if the load of the transaction queue is greater than a first-water mark. The database transaction is delayed for a specified period. A portion of the database transaction is execution after the specified period. It is determined if the load of the queue is below a second-water mark after the specified period. A remaining portion of the database transaction can be processed if the load of the queue is below the second-water mark.
Owner:AEROSPIKE INC
Computer systems and methods for predictive performance management of data transactions
ActiveUS8015454B1Improve performanceIncrease the amount of resourcesError detection/correctionSpecial data processing applicationsComputer moduleComputerized system
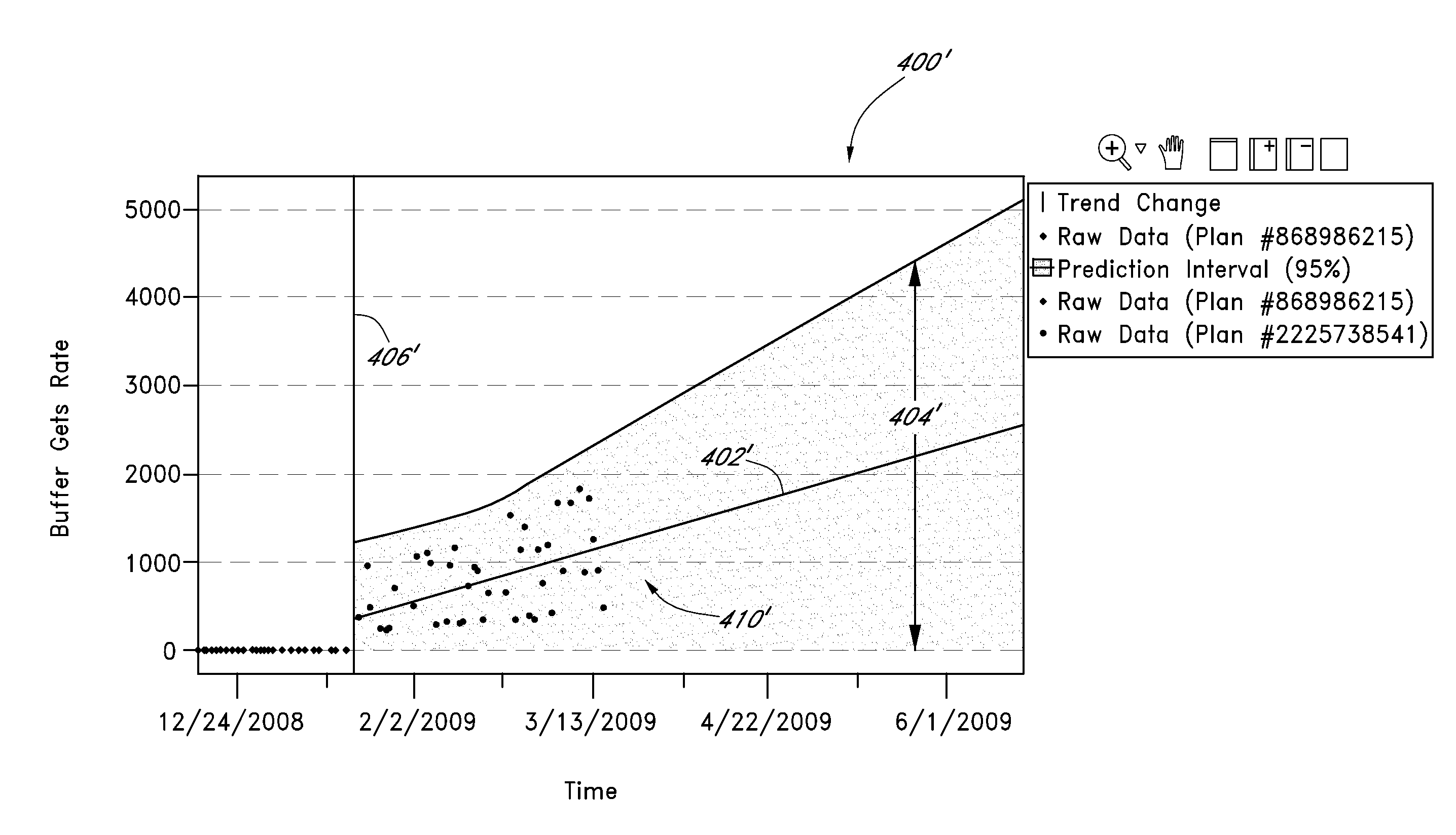
Systems and methods are disclosed for monitoring and managing data transactions, such as SQL transactions. In certain examples, a management subsystem generates an alert identifying degrading database transactions to facilitate preventative tuning or other maintenance. In particular, a monitor module tracks performance measurements (e.g., logical reads) of select transactions. A modeler correlates the performance measurements and assigns first performance model(s) to represent the performance measurements and predicted performance measurements of a particular transaction. A trend change module detects a significant change in a trend and / or variance of the performance measurements and can cause the modeler module to generate a second performance model to represent at least a portion of the performance measurements and the predicted performance measurements of the particular transaction. An interface module triggers an alert when the second performance model indicates that the predicted performance measurements of the particular transaction are degrading at or above a threshold rate.
Owner:QUEST SOFTWARE INC
Method and system for log structured relational database objects
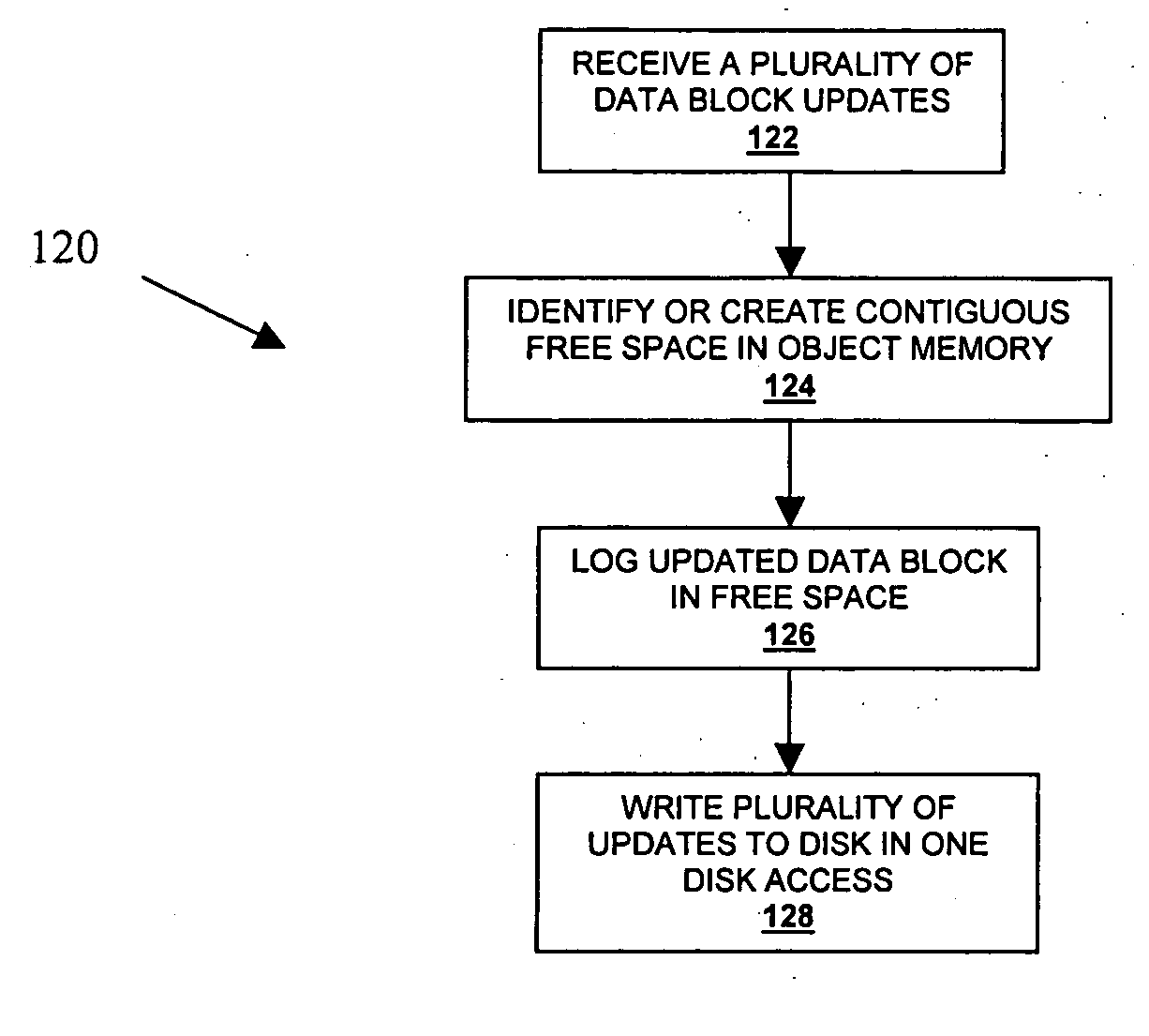
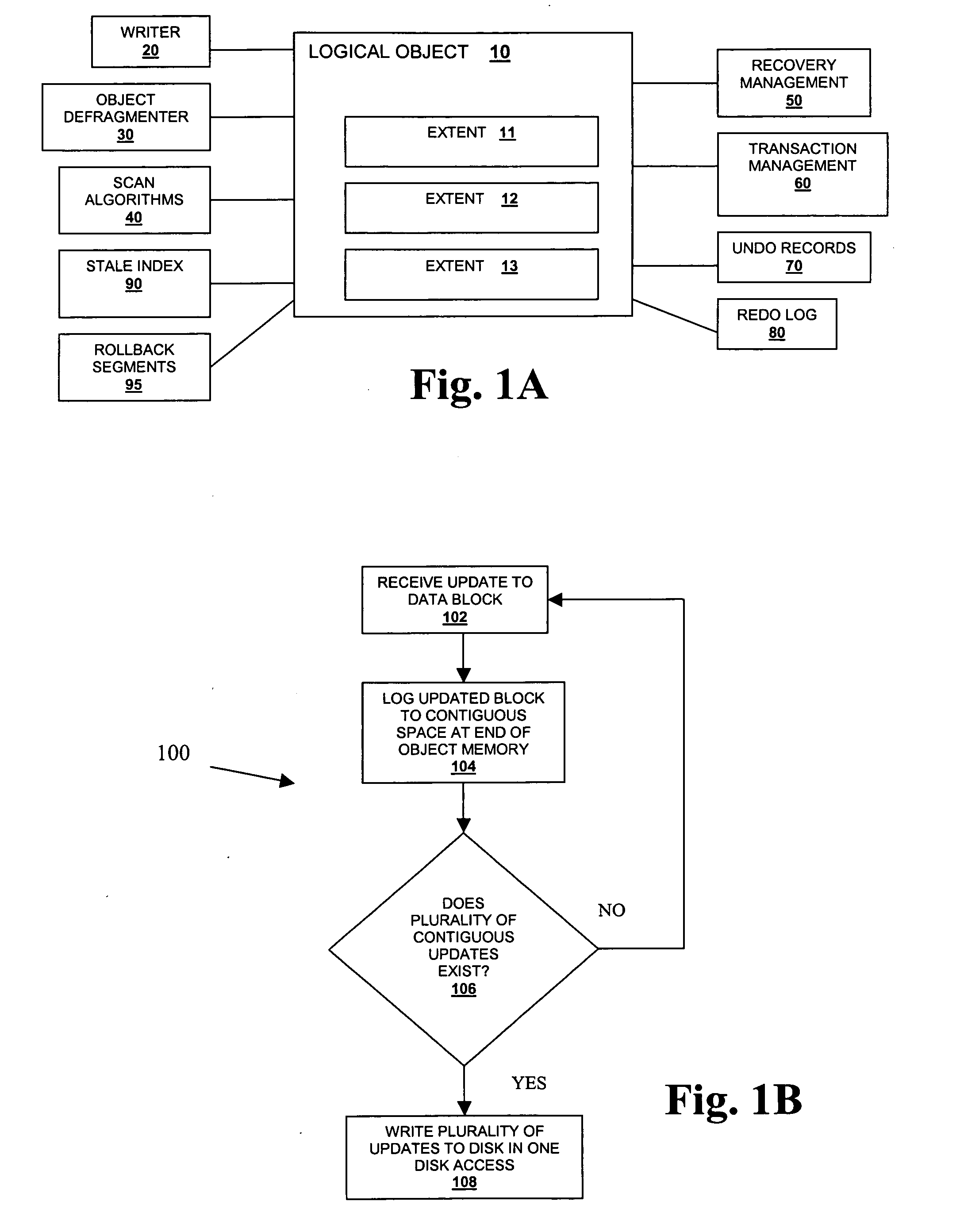
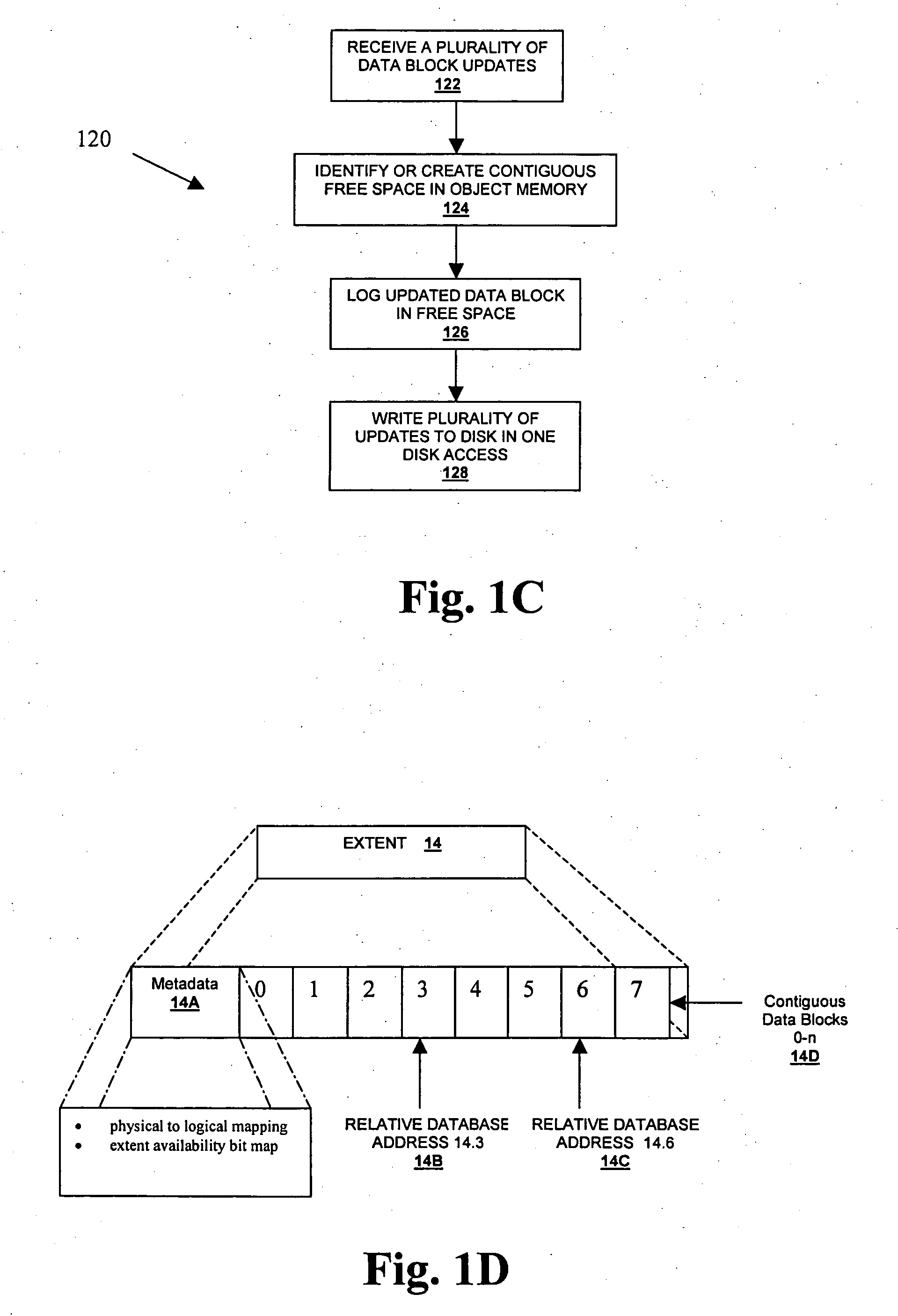
ActiveUS20070088912A1Reduces and eliminates disk access bottleneckExpand accessInput/output to record carriersSpecial data processing applicationsDatabase transactionDatabase object
A system, method, computer program and article of manufacture for updating a disk that moves updates for a specific database object into available contiguous free data blocks, and writes the multiple updates to disk using a single disk access, maintaining database transactional and durability semantics semantics.
Owner:ORACLE INT CORP
Distributed, fault-tolerant and highly available computing system
InactiveUS20080270838A1Improve usabilityProgram control using stored programsFault responseTimestampHigh availability
A method and system for achieving highly available, fault-tolerant execution of components in a distributed computing system, without requiring the writer of these components to explicitly write code (such as entity beans or database transactions) to make component state persistent. It is achieved by converting the intrinsically non-deterministic behavior of the distributed system to a deterministic behavior, thus enabling state recovery to be achieved by advantageously efficient checkpoint-replay techniques. The method comprises: adapting the execution environment for enabling message communication amongst and between the components; automatically associating a deterministic timestamp in conjunction with a message to be communicated from a sender component to a receiver component during program execution, the timestamp representative of estimated time of arrival of the message at a receiver component. At a component, tracking state of that component during program execution, and periodically checkpointing the state in a local storage device. Upon failure of a component, the component state is restored by recovering a recent stored checkpoint and re-executing the events occurring since the last checkpoint. The system is deterministic by repeating the execution of the receiving component by processing the messages in the same order as their associated timestamp.
Owner:GLOBALFOUNDRIES INC
Database caching utilizing asynchronous log-based replication
ActiveUS20130080386A1Digital data information retrievalDigital data processing detailsRelational database management systemDatabase caching
A database table within a database to persist within a cache as a cached table can be identified. The database can be a relational database management system (RDBMS) or an object oriented database management system (OODBMS). The cache can be a database cache. Database transactions within can be logged within a log table and the cached table within the cache can be flagged as not cached during runtime. An asynchronous replication of the database table to the cached table can be performed. The replication can execute the database transactions within the log table upon the cached table. The cached table can be flagged as cached when the replication is completed.
Owner:IBM CORP
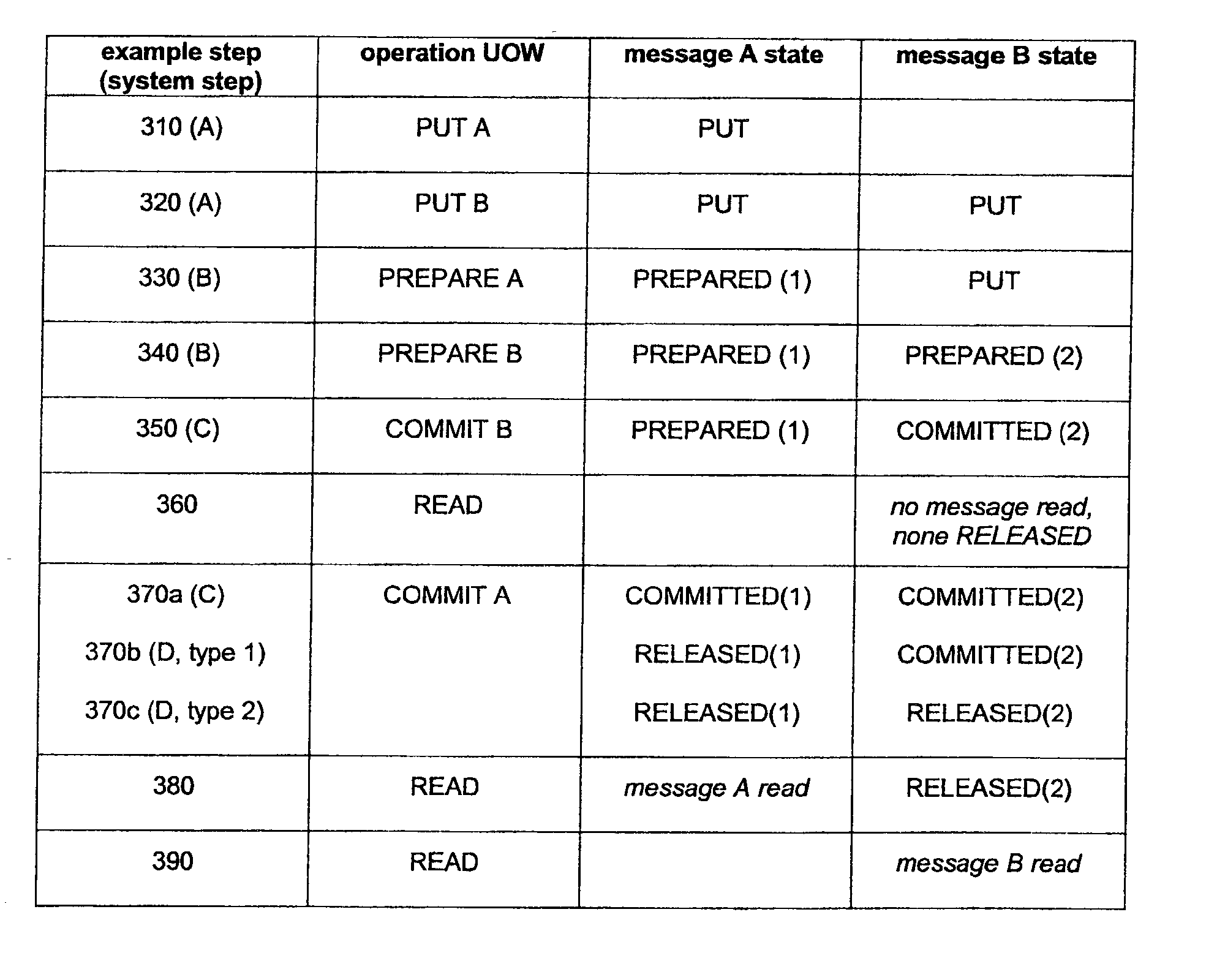
Message ordering in a messaging system
InactiveUS20030115276A1Digital data information retrievalMultiple digital computer combinationsMessage handlingApplication software
A method and system (200) for message handling in a messaging system by: receiving messages from applications associated with transactions and placing the received messages in a queue (230) for subsequent retrieval; receiving requests of prepare, commit and abort for the transactions; deferring retrieval of messages from the queue so as to occur in the same sequence as the prepare requests of the transactions with which the respective messages are associated; and retrieving from the queue messages associated with a transaction in the order in which the messages were put by the application. Preferably deferral is achieved by deferring completion of transaction commits as required to occur in the same order as the prepare message requests. Deferral may be implemented by (i) using a three phase commit protocol having Prepare, Commit, and Release phases and by implementing the Release phase within the Commit phase of the same or a different transaction so that a standard two-phase coordinator may be used, or (ii) by completing a first part of a commit phase as requested and deferring a second part of the commit phase as required. This permits appropriate message ordering in a transactional system, and in particular permits the correct implementation of a database replication system (220) using coordinated message transport that is fed the changes during database transactions.
Owner:IBM CORP
Synchronously logging to disk for main-memory database systems through record and replay
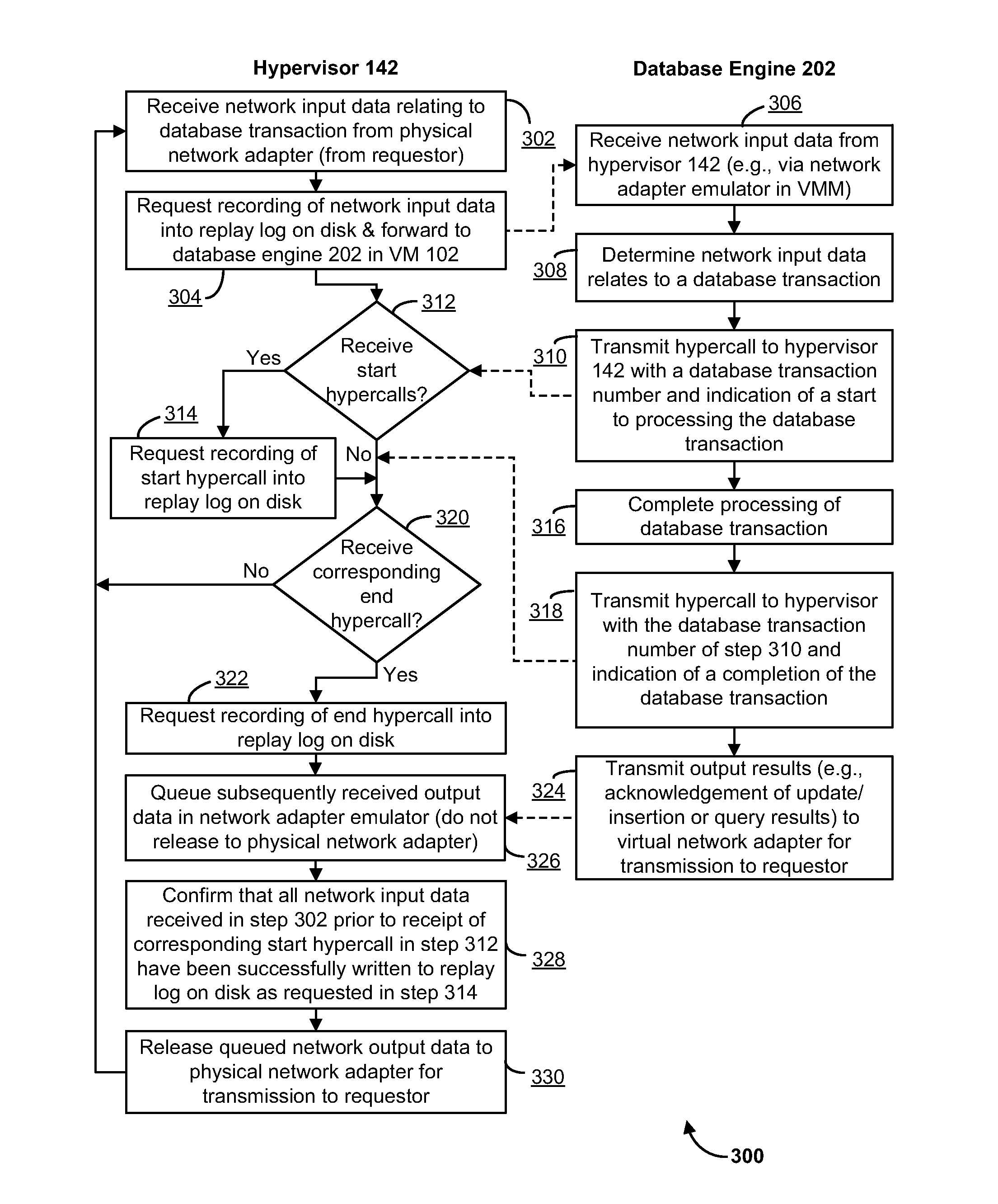
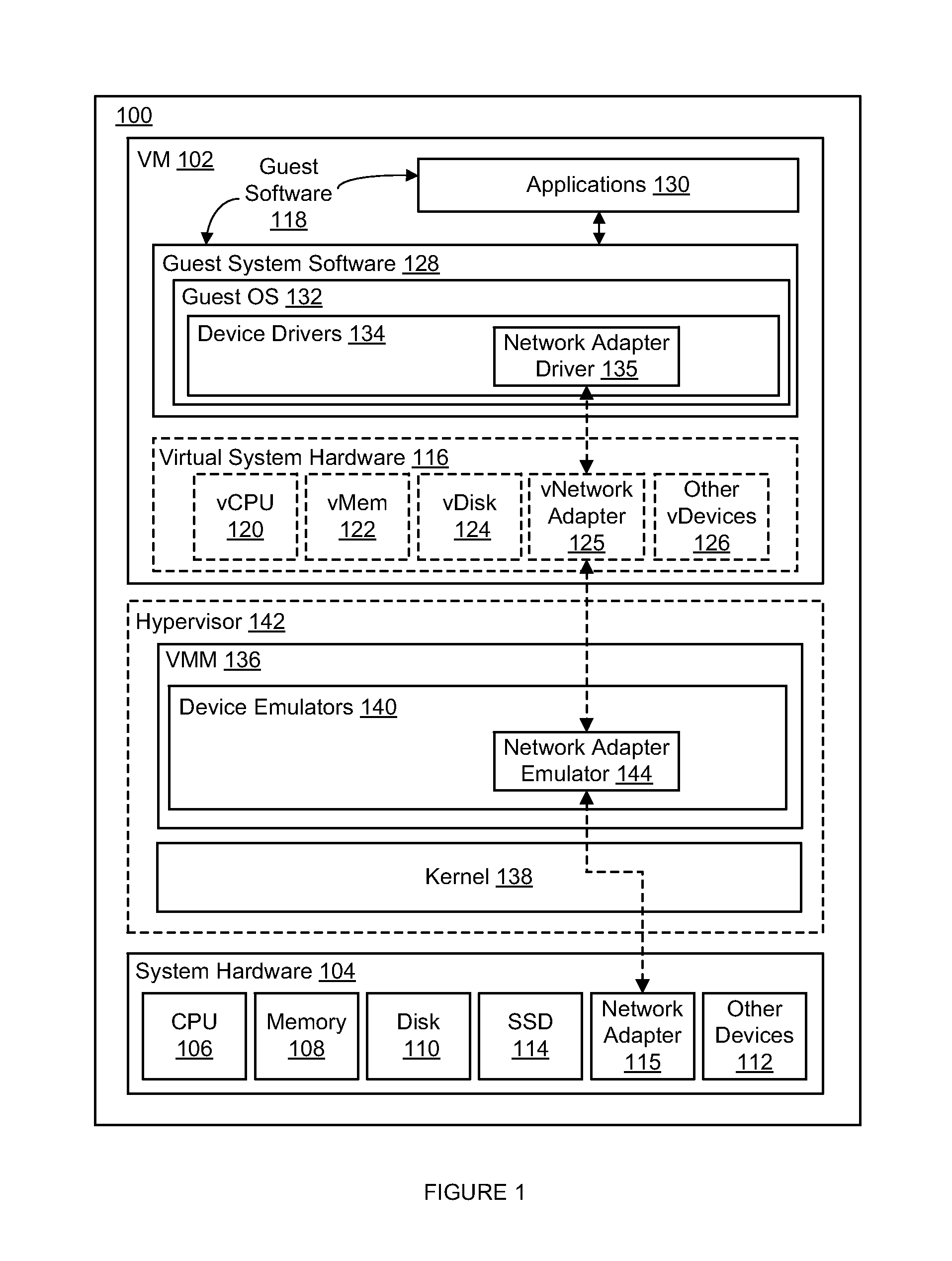
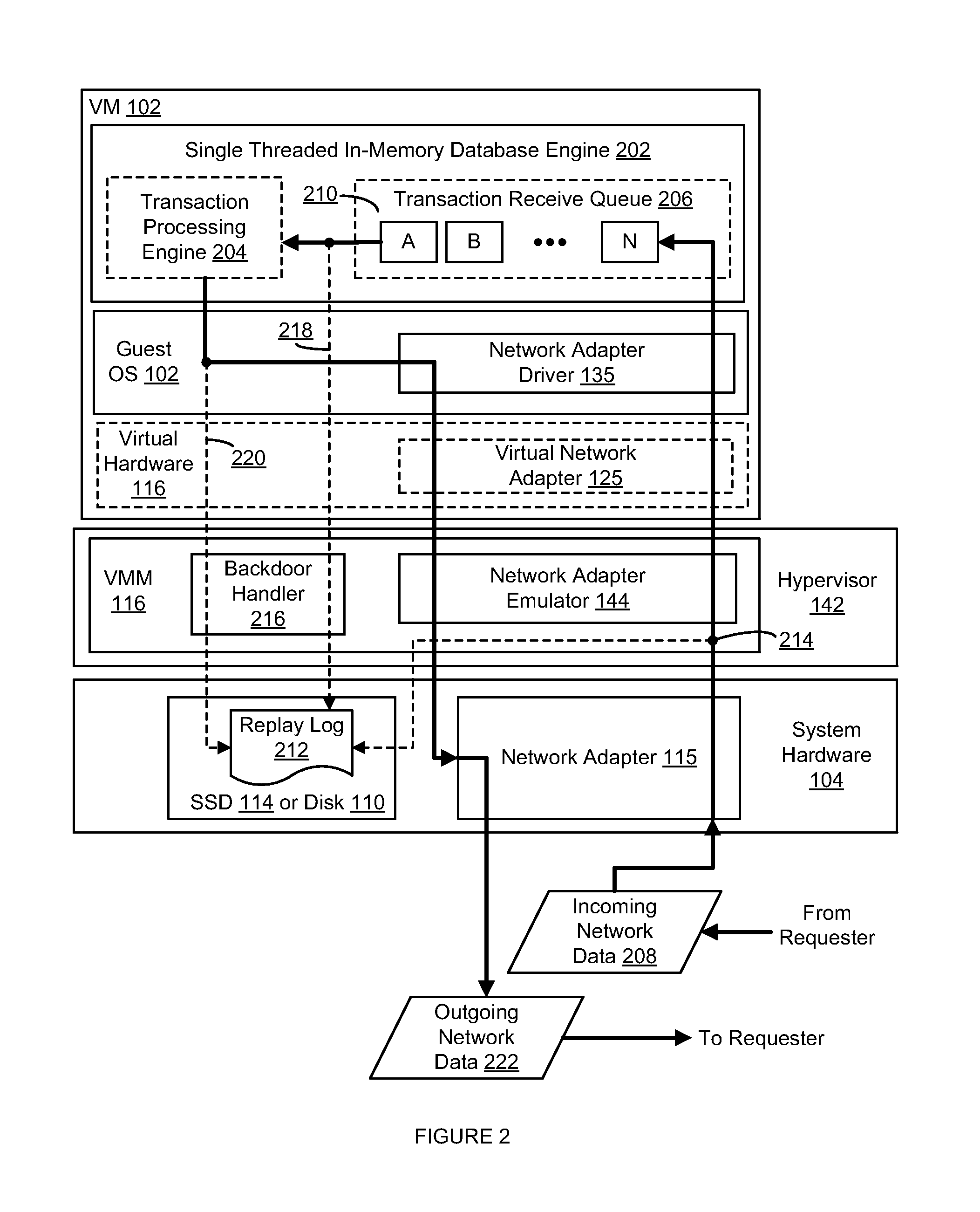
ActiveUS8826273B1Improve performanceSlow performanceError detection/correctionSoftware simulation/interpretation/emulationIn-memory databaseManagement system
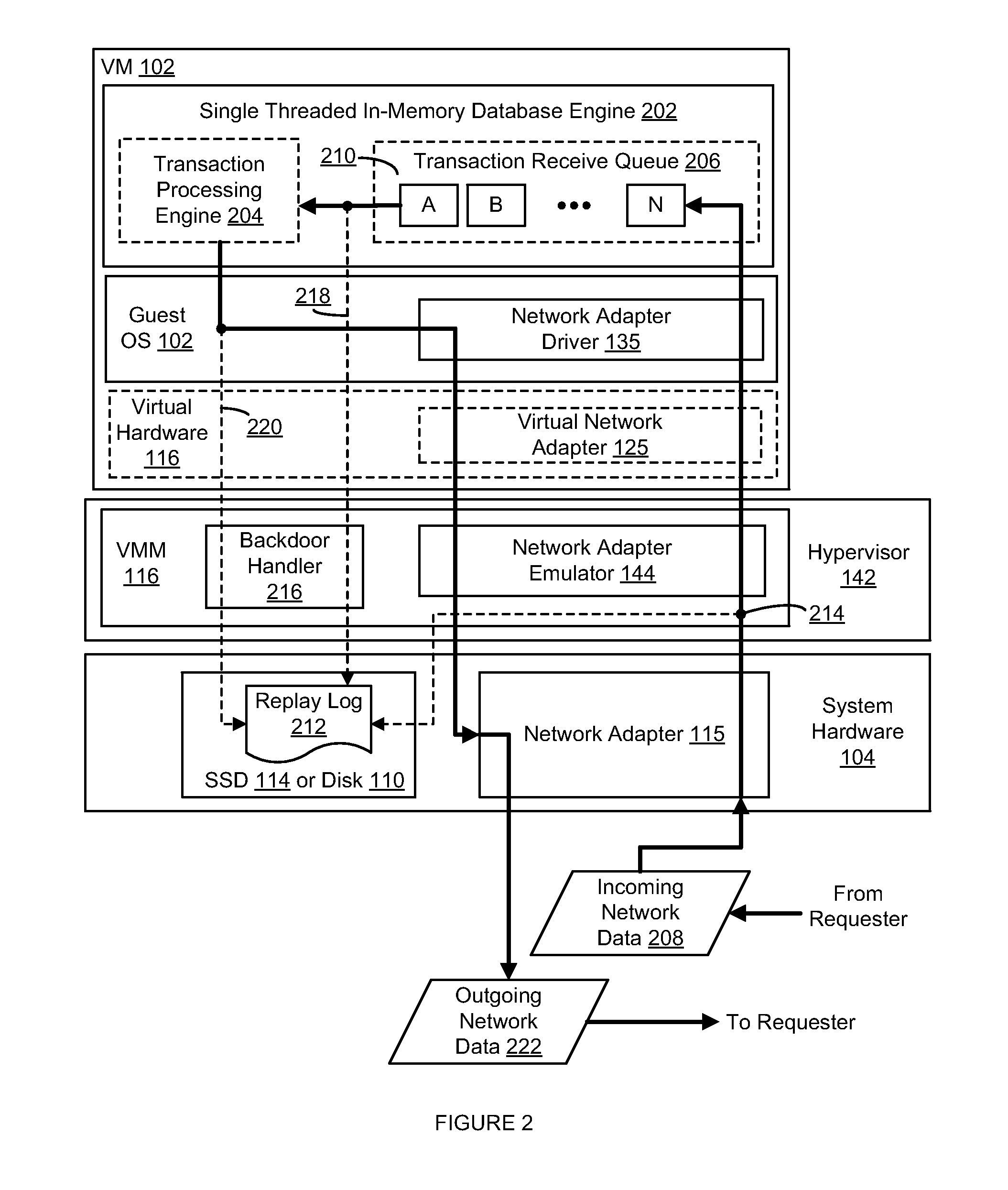
An in-memory database management system (DBMS) in a virtual machine (VM) preserves the durability property of the ACID model for database management without significantly slowing performance due to accesses to disk. Input data relating to a database transaction is recorded into a replay log and forwarded to the VM for processing by the DBMS. An indication of a start of processing by the DBMS of the database transaction is received after receipt of the input data by the VM and an indication of completion of processing of the database transaction by the DBMS is subsequently received, upon which outgoing output data received from the VM subsequent to the receipt of the completion indication is delayed. The delayed outgoing output data is ultimately released upon a confirmation that all input data received prior to the receipt of the start indication has been successfully stored into the replay log, thereby preserving durability for the database transaction.
Owner:VMWARE INC
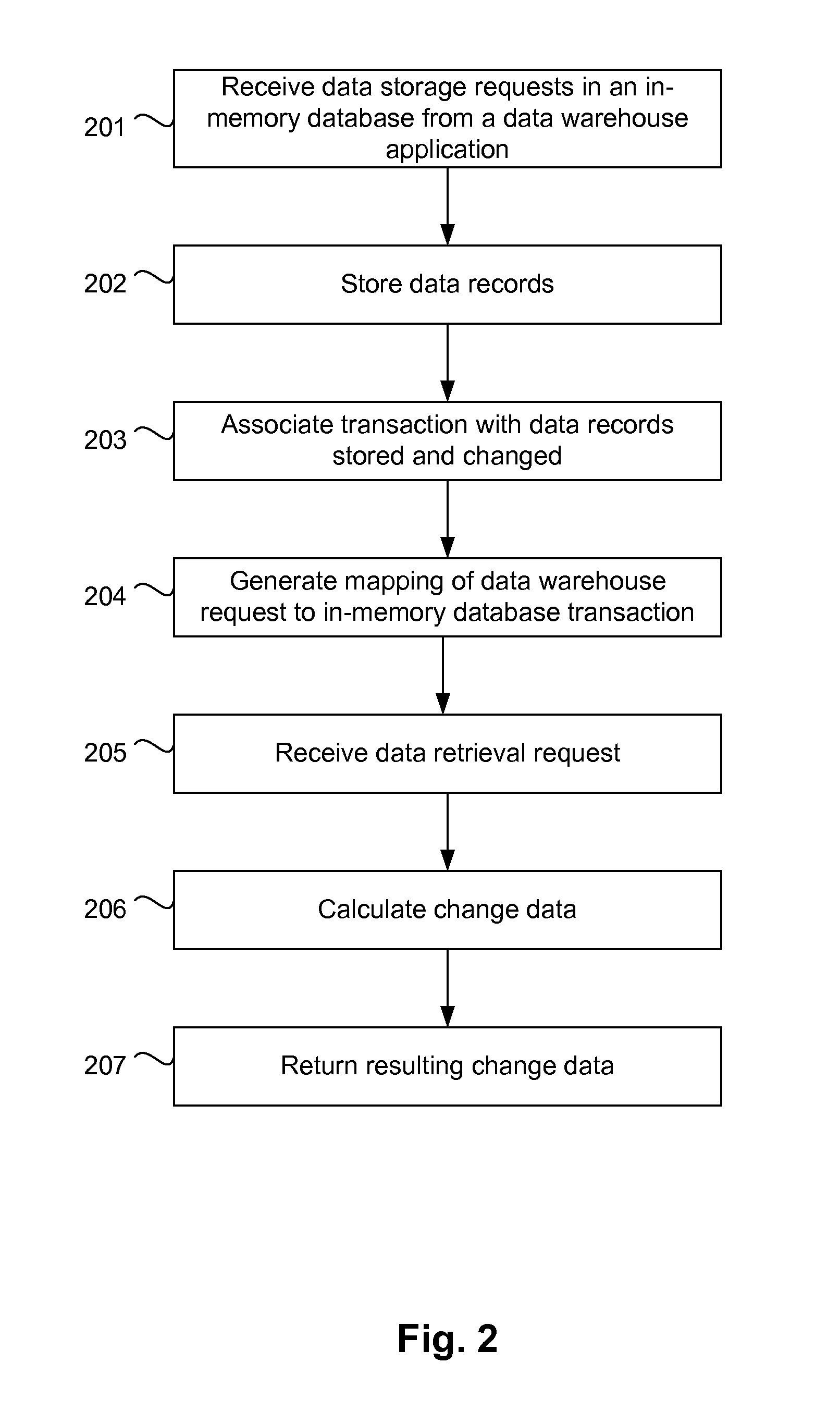
In-Memory Processing for a Data Warehouse
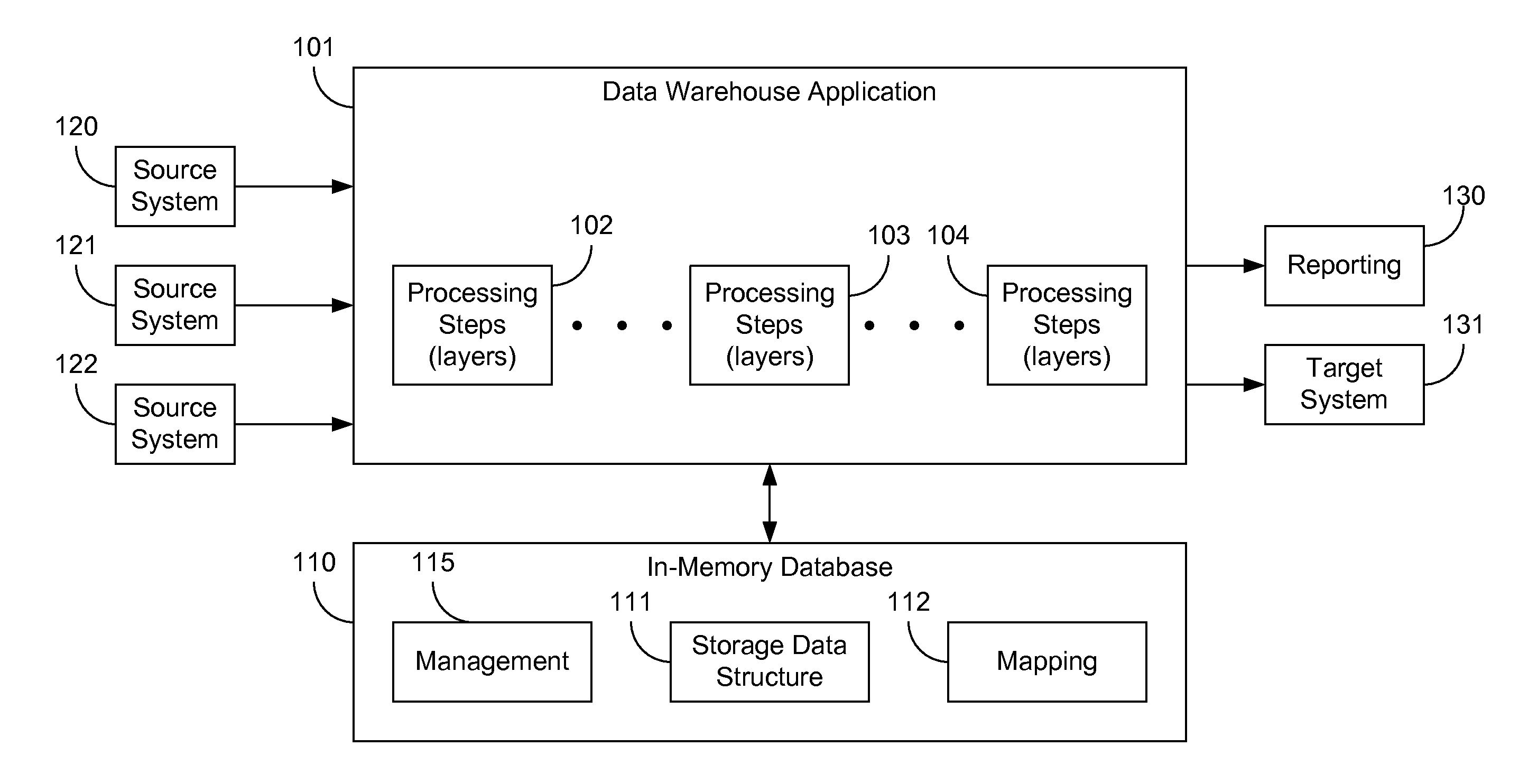
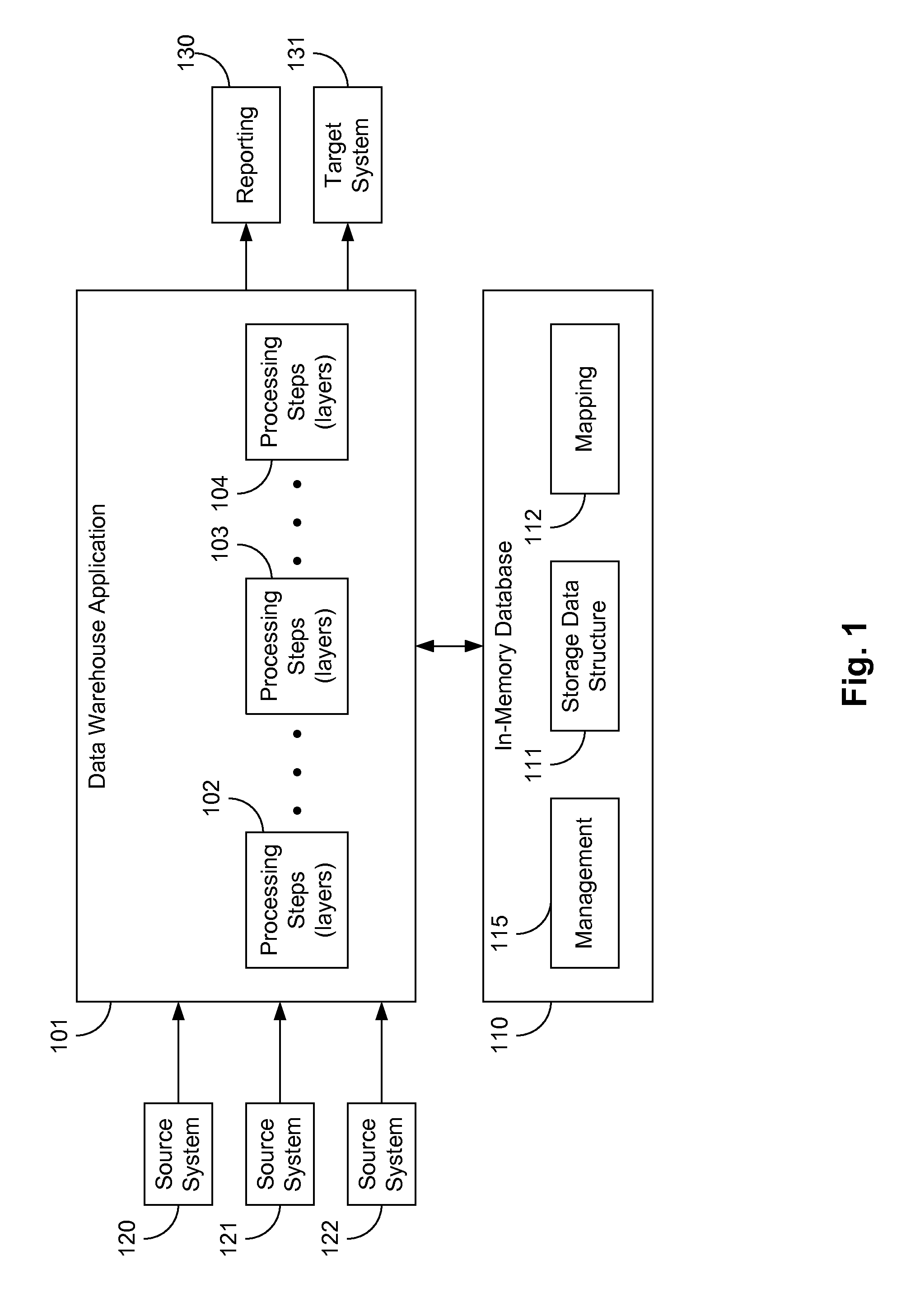
ActiveUS20120259809A1Digital data information retrievalDigital data processing detailsIn-memory databaseData warehouse
Embodiments of the present invention include in-memory processing for data warehouse applications. In one embodiment, data records from a data warehouse application are stored in a data storage structure of an in-memory database. Data received from the data warehouse may be stored in a queue and loaded into the data storage structure according to predefined rules. Stored data records are associated with in-memory database transactions that caused the stored data record to be stored, and may further be associated with transactions that caused the stored data records to be changed. A mapping is generated to associate requests from the data warehouse application with in-memory database transactions. The data warehouse application may retrieve data in a change data format calculated on-the-fly.
Owner:SAP AG +1
Separation of duties in a data audit system
InactiveUS20070005665A1Ensure integrityResourcesStructured data retrievalLimited accessSystem monitor
A database audit system monitors database activity, providing a complete record of access to data and database structure. A database audit may be performed by collecting data from database transaction logs and traces, exporting the collected data into a repository, and analyzing the data in the repository to create data audit reports and to provide data audit browsing capabilities. A separation between audit side and audited data side is maintained through limited access permissions.
Owner:LUMIGENT TECH
Apparatus and Method for Read Optimized Bulk Data Storage
ActiveUS20110010330A1Reliable handlingAvoid overheadDigital data information retrievalDigital data processing detailsData warehouseData store
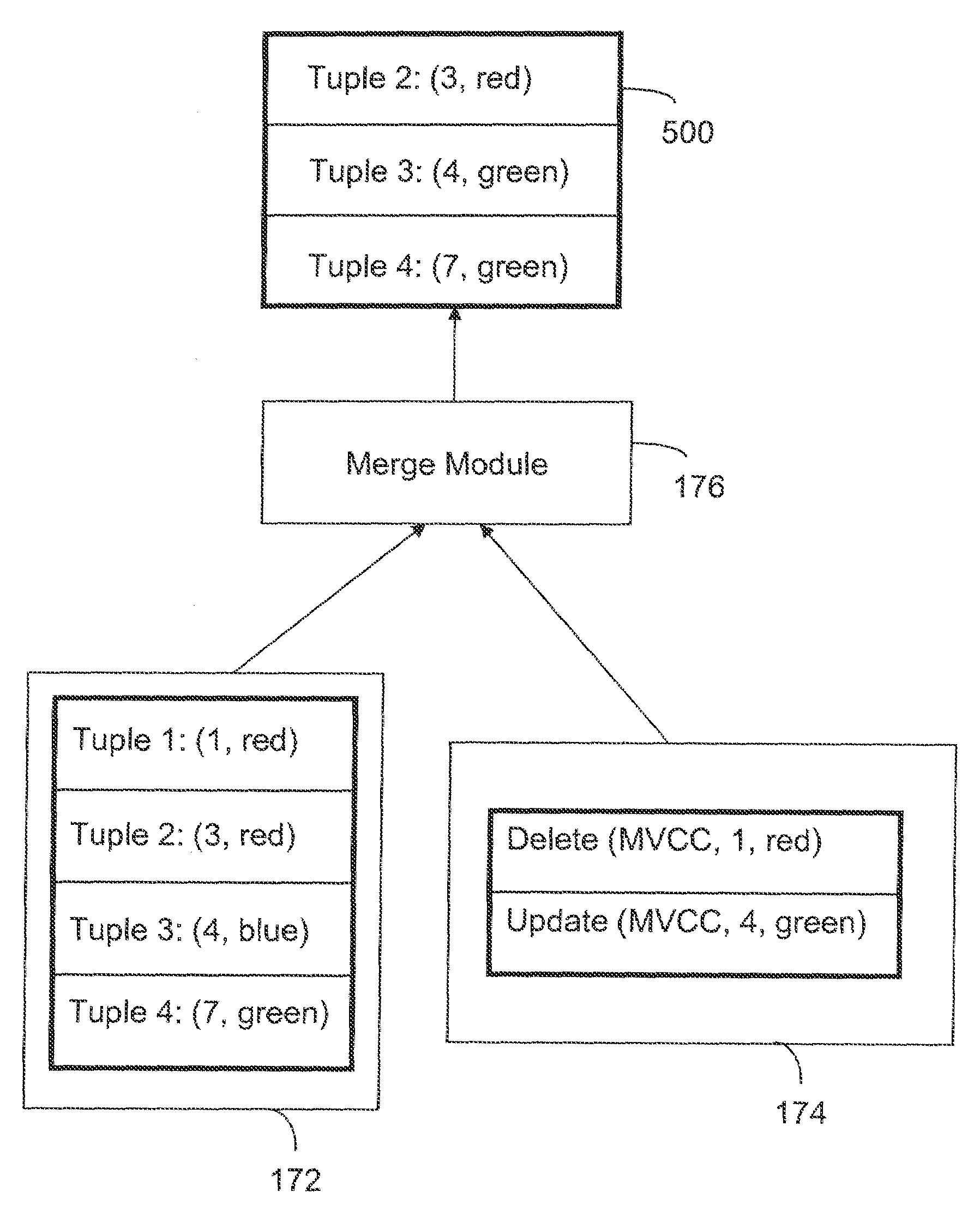
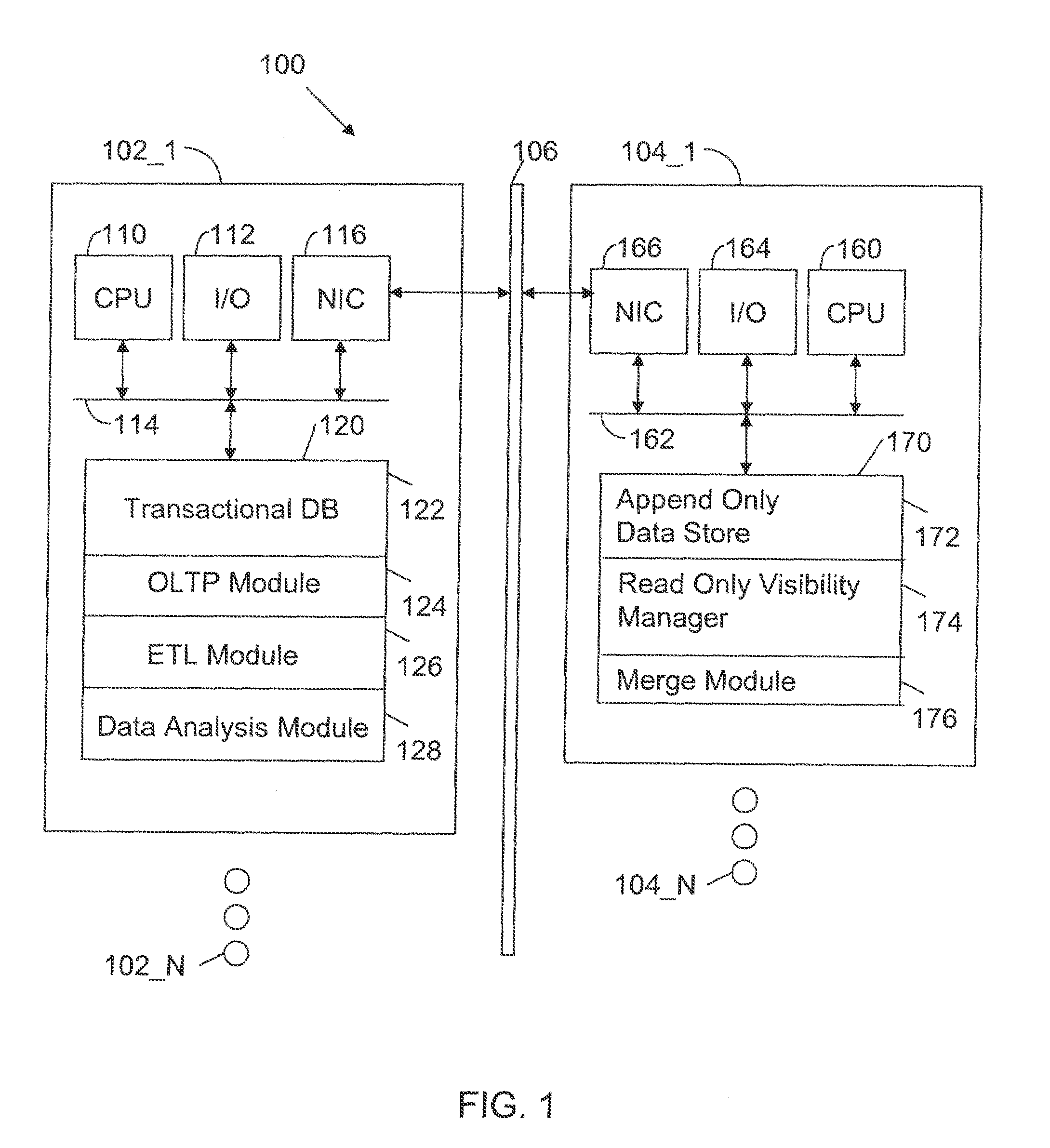
A computer readable storage medium includes executable instructions to store load data in new rows of an append only table within a data warehouse, without updating or deleting existing rows in the append only table. The new rows are added in a database transaction that guarantees that the distributed reads and writes of all transactions are processed reliably and that the transactions obey snapshot isolation rules. Data changes associated with the load data are maintained in a separate update table. Data from the append only table is merged with data changes from the update table to supply read data.
Owner:GOPIVOTAL
Method and medium for combining operation commands into database submission groups
ActiveUS8032885B2Flush cutImprove efficiencyDatabase distribution/replicationMultiprogramming arrangementsData miningContinuous data
Owner:ORACLE INT CORP
Locking Protocol for Partitioned and Distributed Tables
ActiveUS20140156619A1Digital data processing detailsSpecial data processing applicationsDistributed databaseComputer program
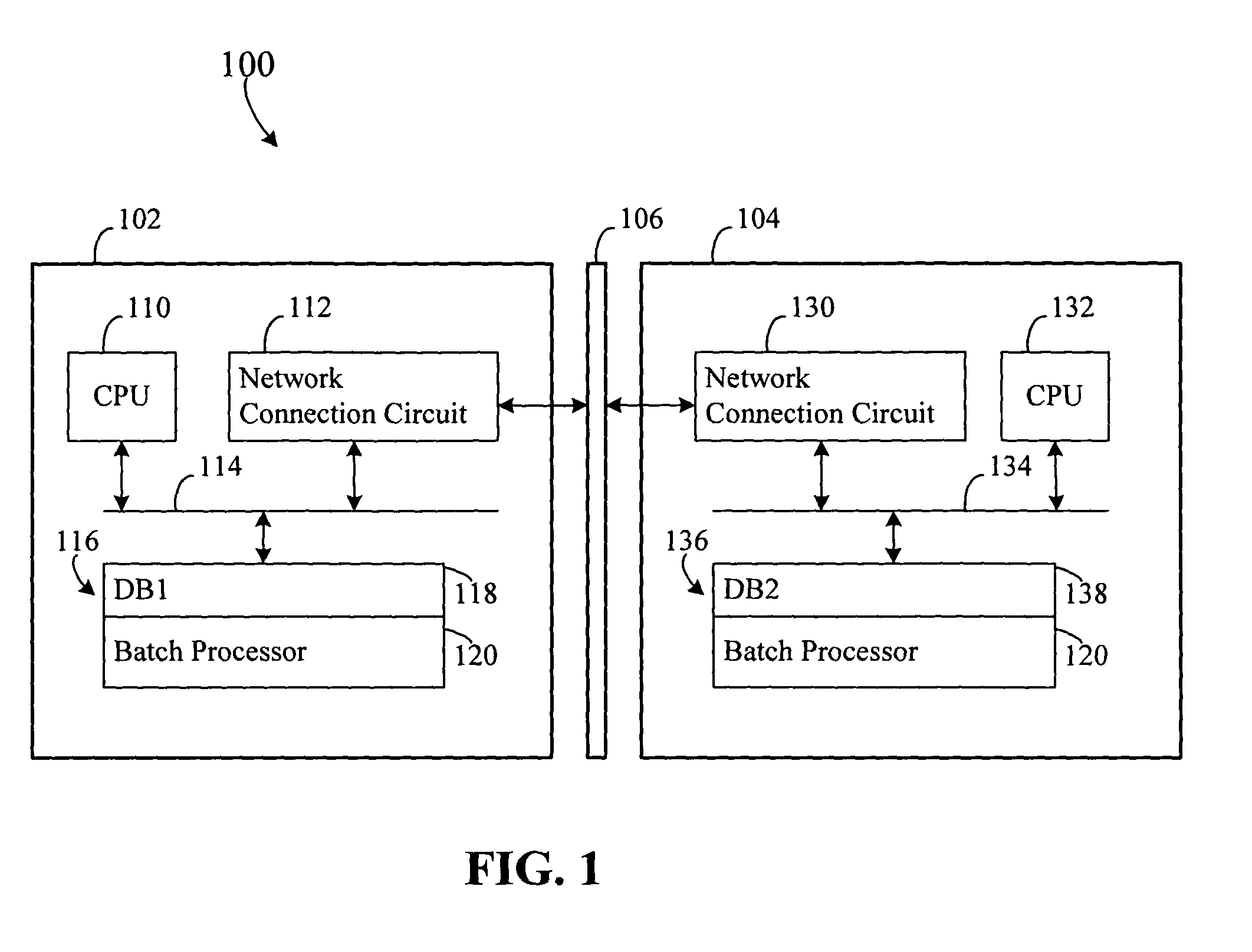
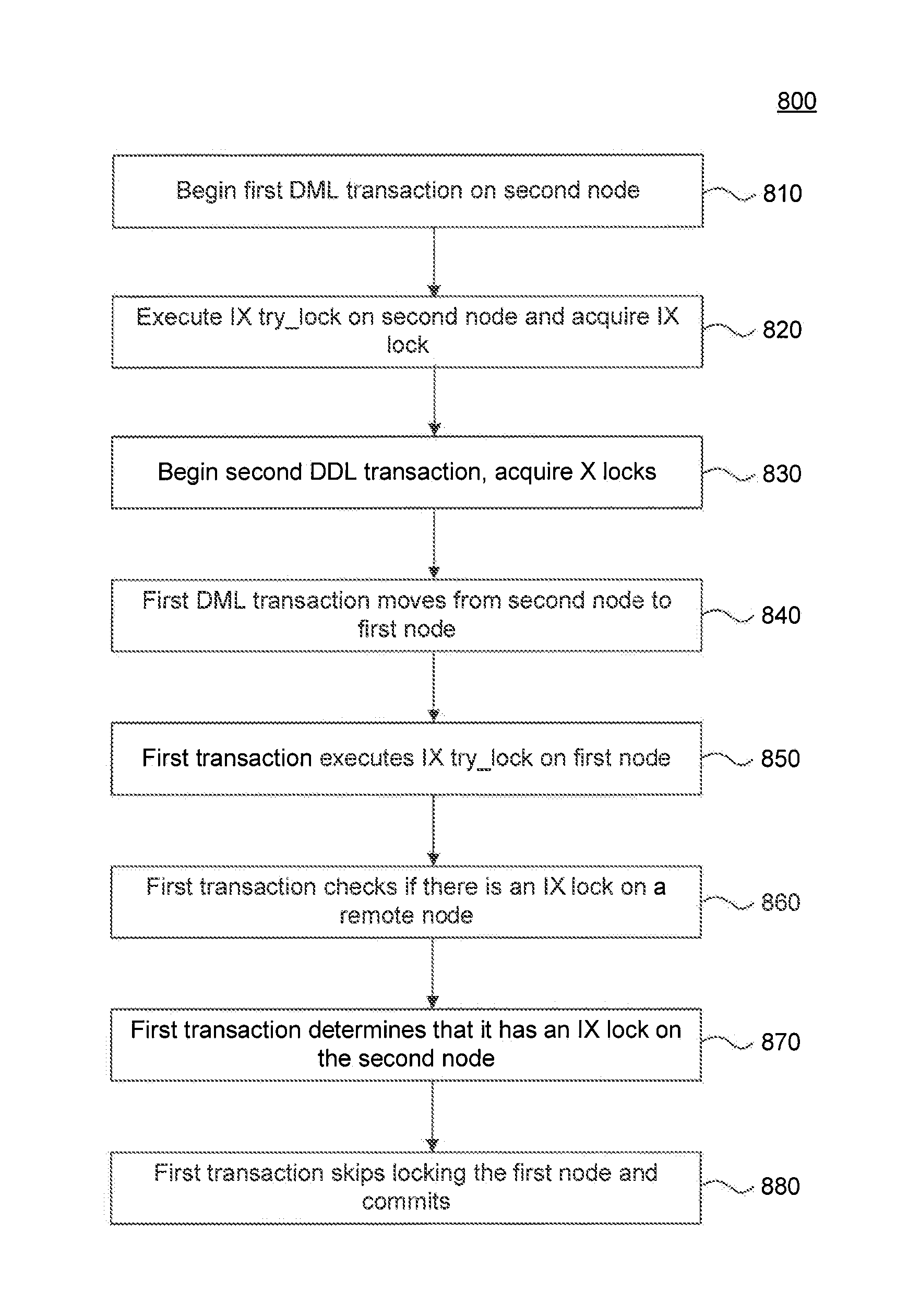
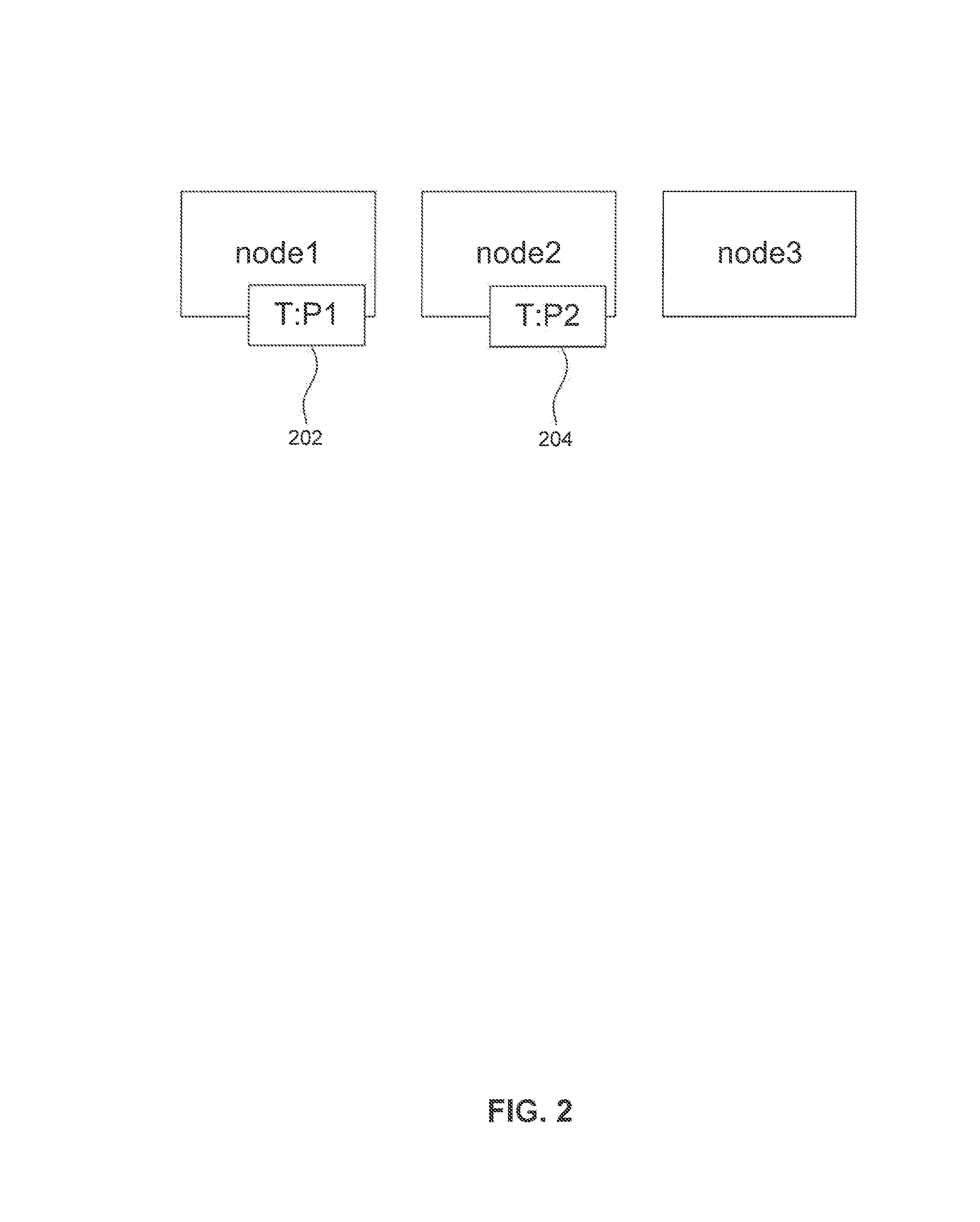
Systems, methods and computer program product embodiments for providing a locking protocol for partitioned and distributed database tables are disclosed herein. A locking method includes executing, by at least one processor, a first database transaction on a second node, attempting to acquire and acquiring a lock on the second node in intentional exclusive mode, executing, by the at least one processor, a second database transaction on a first node, acquiring a lock on the first node in exclusive mode and waiting to acquire a lock on the second node in exclusive mode, routing, by the at least one processor, the first database transaction to the first node and unsuccessfully trying to acquire a lock on the first node and committing, by the at least one processor, the first database transaction.
Owner:SAP AG
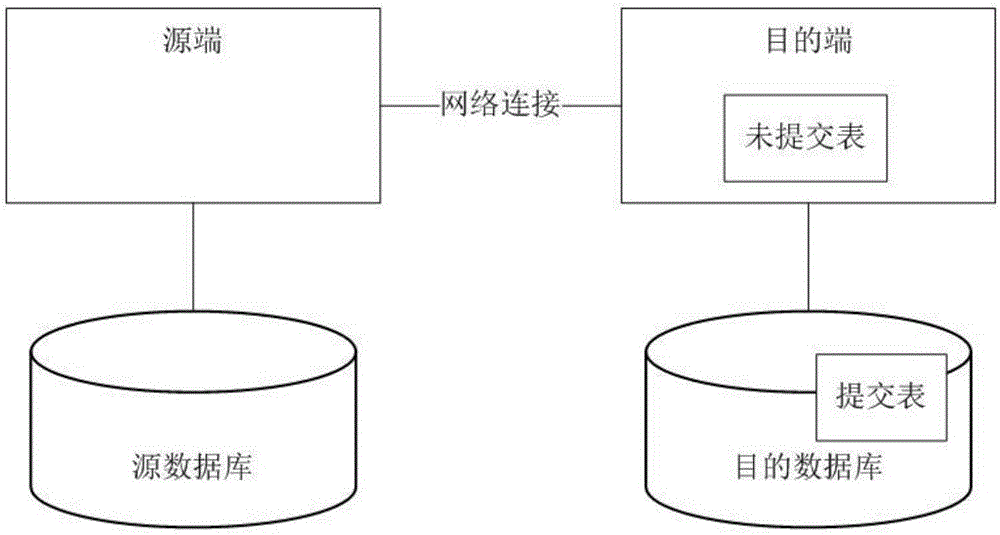
Database write-in method and system based on block chain network
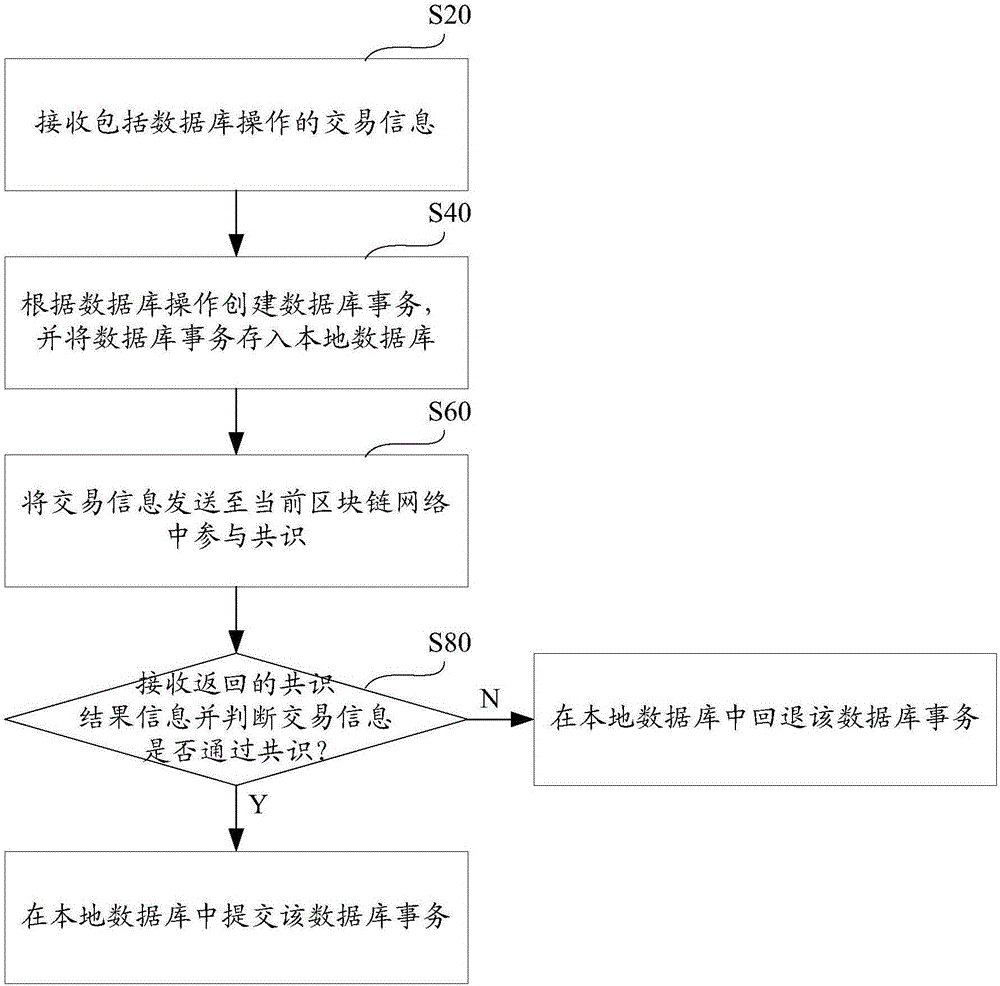
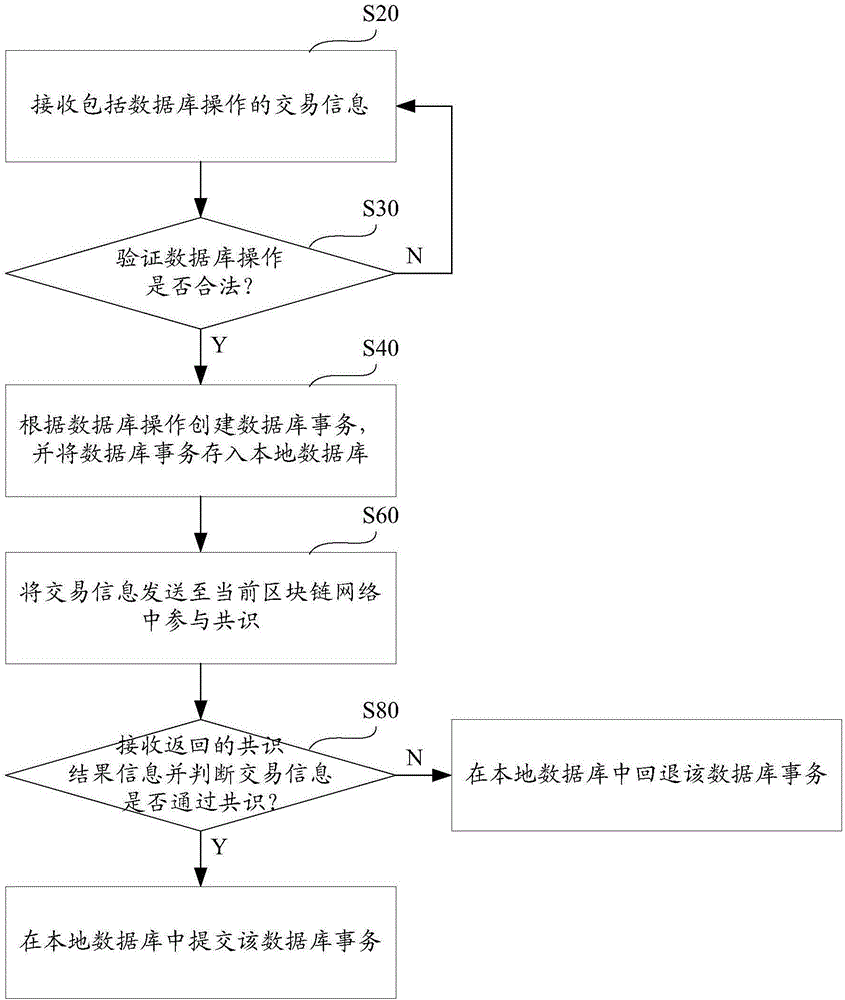
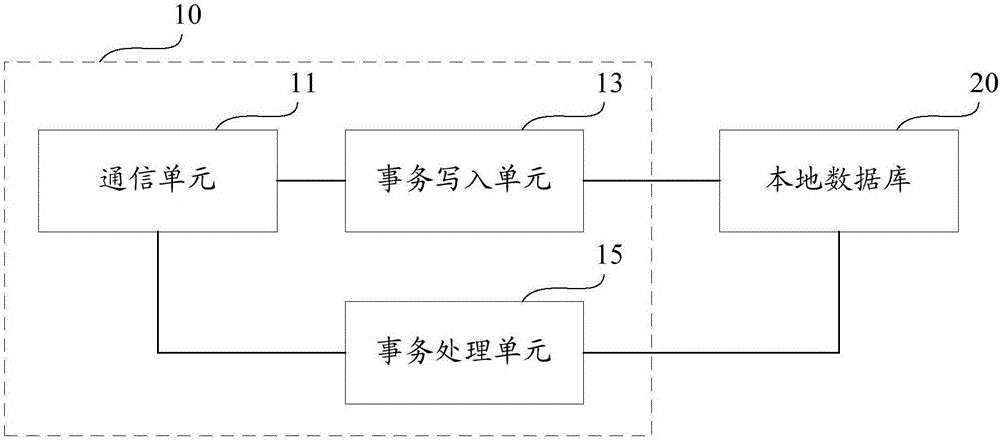
ActiveCN106611061ARead-write consistencyReduce stepsDatabase management systemsSpecial data processing applicationsChain networkDatabase transaction
The invention provides a database write-in method and system based on a block chain network. The method comprises the following steps: receiving transaction information comprising database operation; establishing database transaction according to the database operation, and storing the database transaction in a local database; sending the transaction information into a current block chain network to participate in consensus; receiving returned consensus result information and judging whether the transaction information passes through the consensus or not; if yes, submitting the database transaction in the local database; and if not, retreating the database transaction in the local database. The database operation is stored in the database before the consensus is performed in a database transaction manner, that the database transaction is submitted or retreated is judged according to the consensus result after the consensus is completed, so that read-write consistency of the database is guaranteed in the consensus process.
Owner:BEIJING ZHONGXIANG BIT TECH
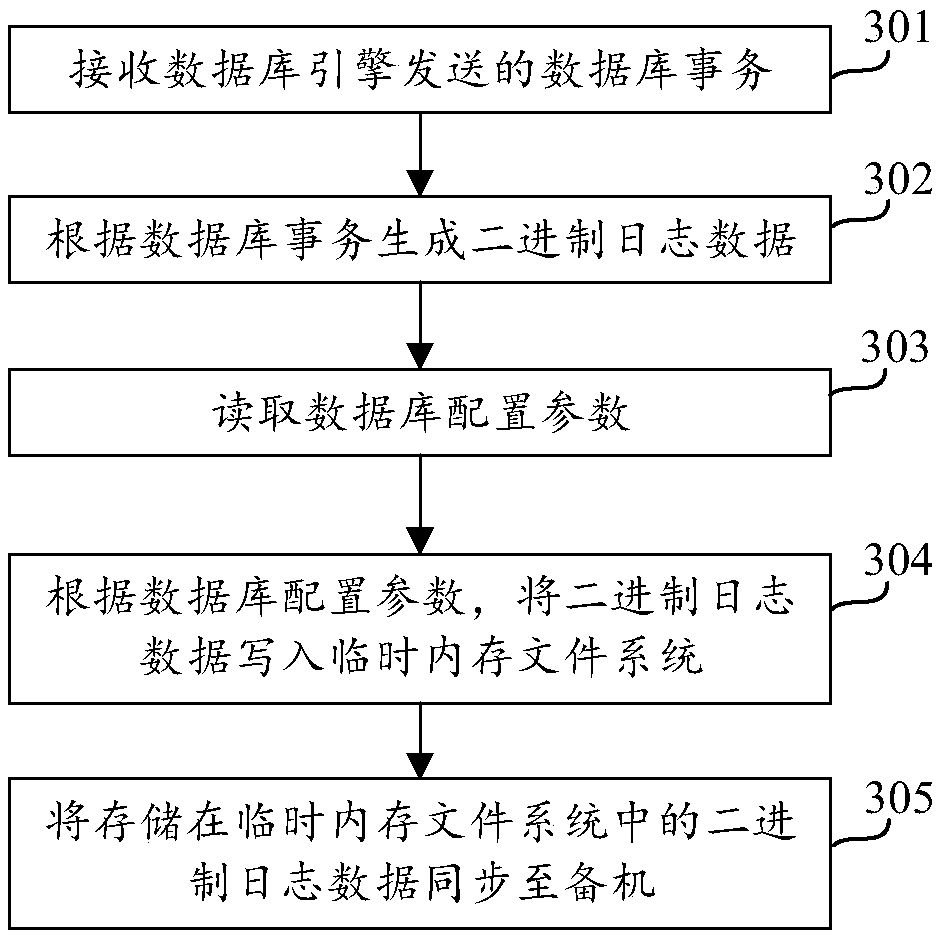
Database synchronization method and device and readable medium
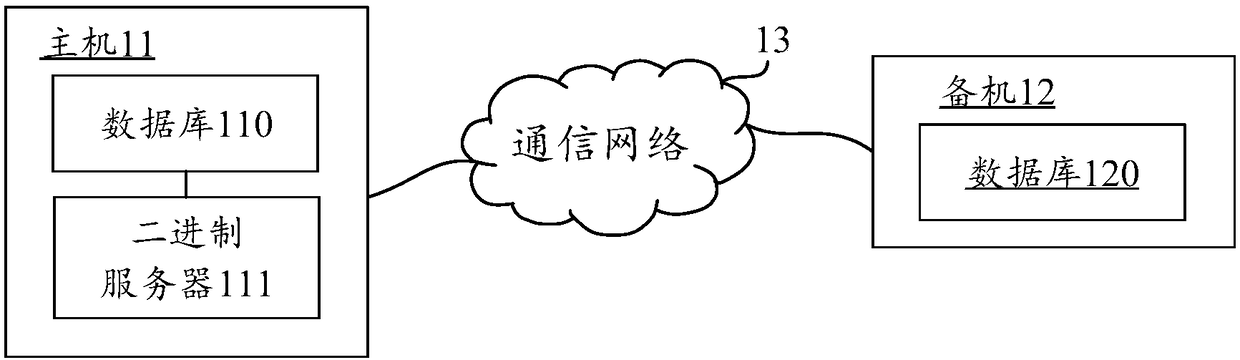
ActiveCN108170768AImprove writing efficiencyImprove reading efficiencyDatabase distribution/replicationHardware monitoringData synchronizationFile system
The application discloses a database synchronization method and device and a readable medium, and relates to the field of databases. The method includes: acquiring a database transaction; generating binlogs according to the database transaction; writing the binlogs into a temporary memory file system, wherein the temporary memory file system is a file system carrying out writing through a manner of memory writing; and synchronizing a standby machine with the binlogs stored in the temporary memory file system, wherein the standby machine is used for synchronizing a database according to the binlogs. Through writing the binlogs into the temporary memory file system in the manner of memory writing, the problem that efficiency of writing the binlogs into a binary log file by a host is lower due to lower file writing speed of the binary log file is avoided, and writing efficiency of the binlogs is improved.
Owner:TENCENT CLOUD COMPUTING BEIJING CO LTD
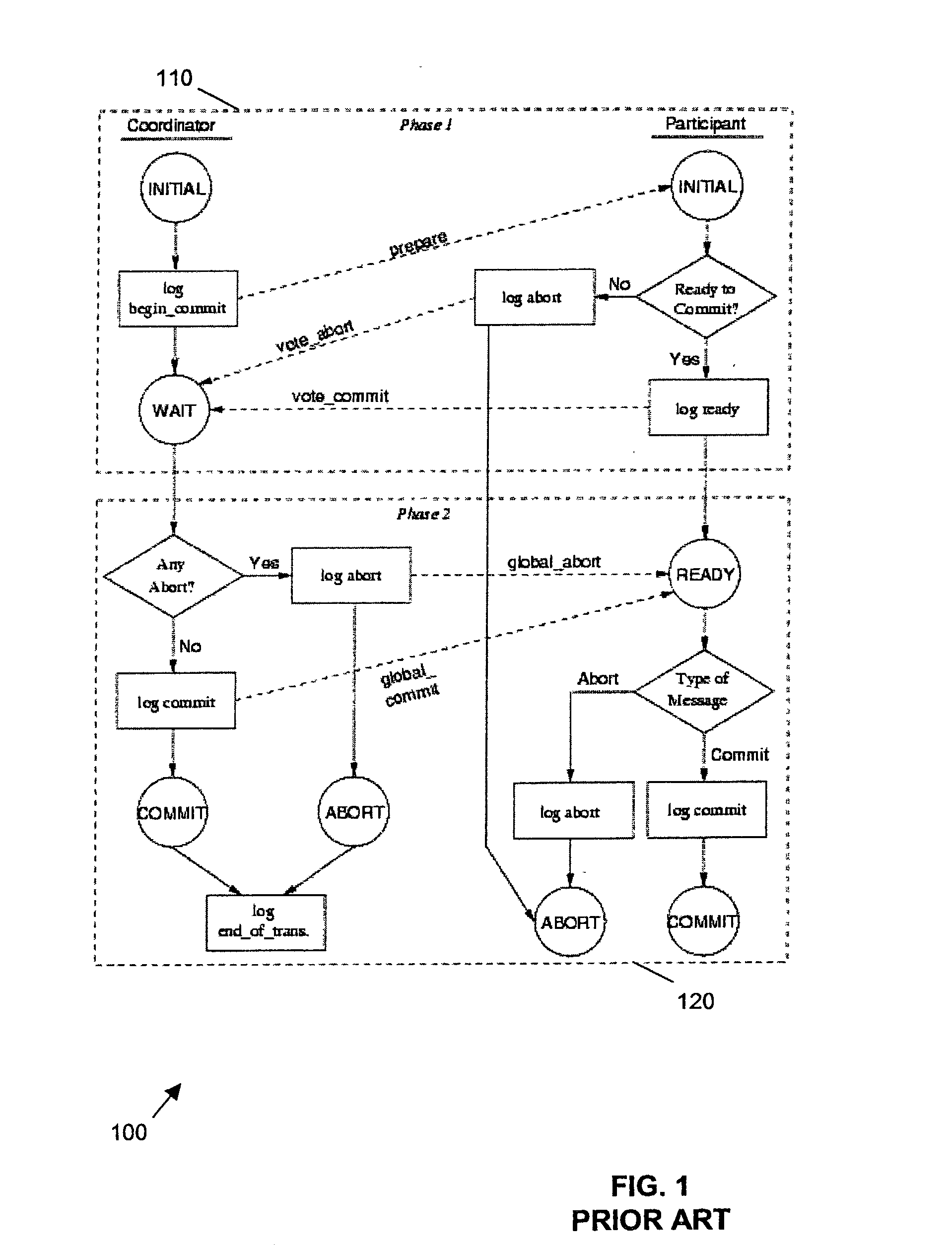
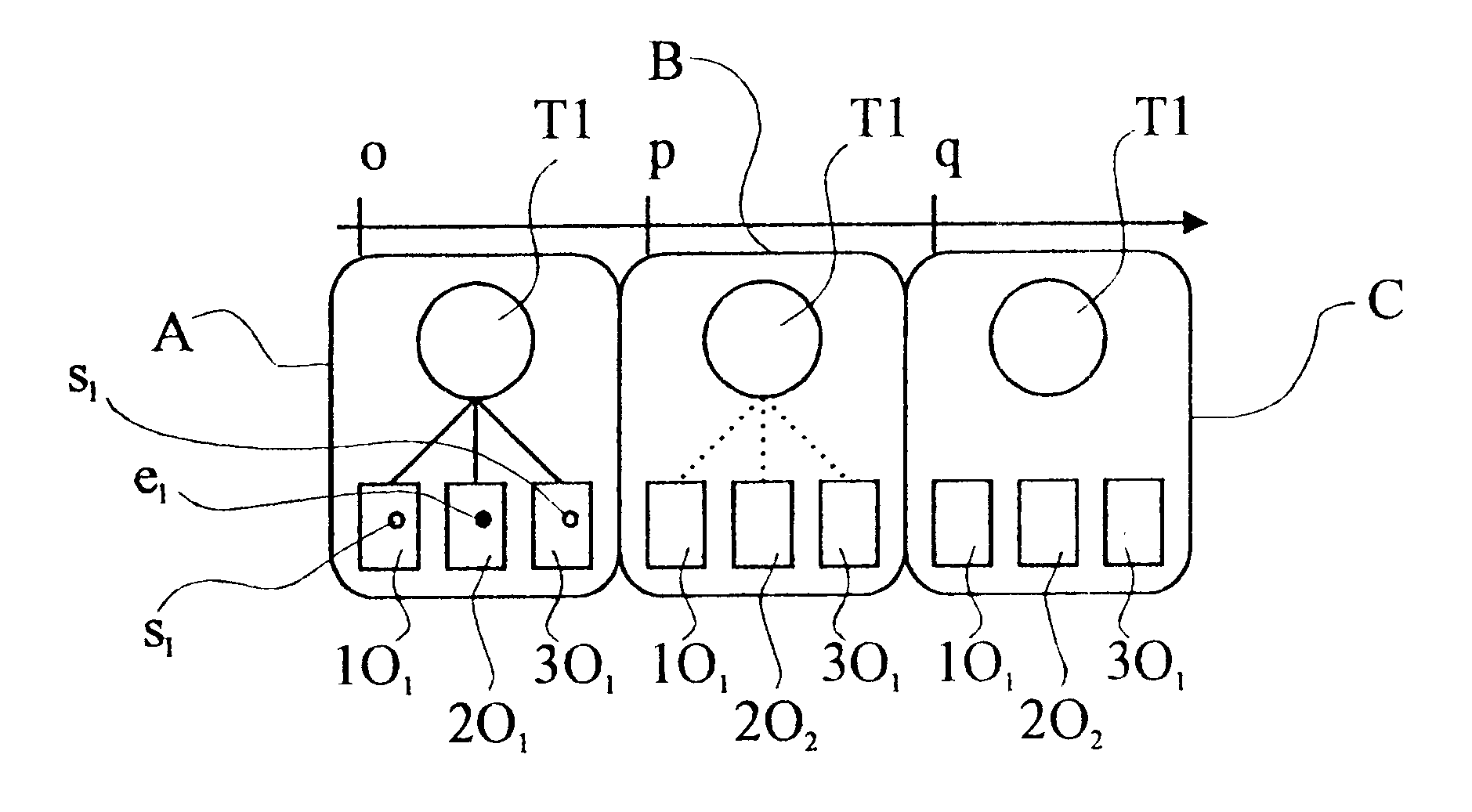
Database transaction with locking in two phases and multiple versions of objects
InactiveUS6560601B1Shorten the timeThe process is simple and fastData processing applicationsDigital data information retrievalThird phaseTwo-phase locking
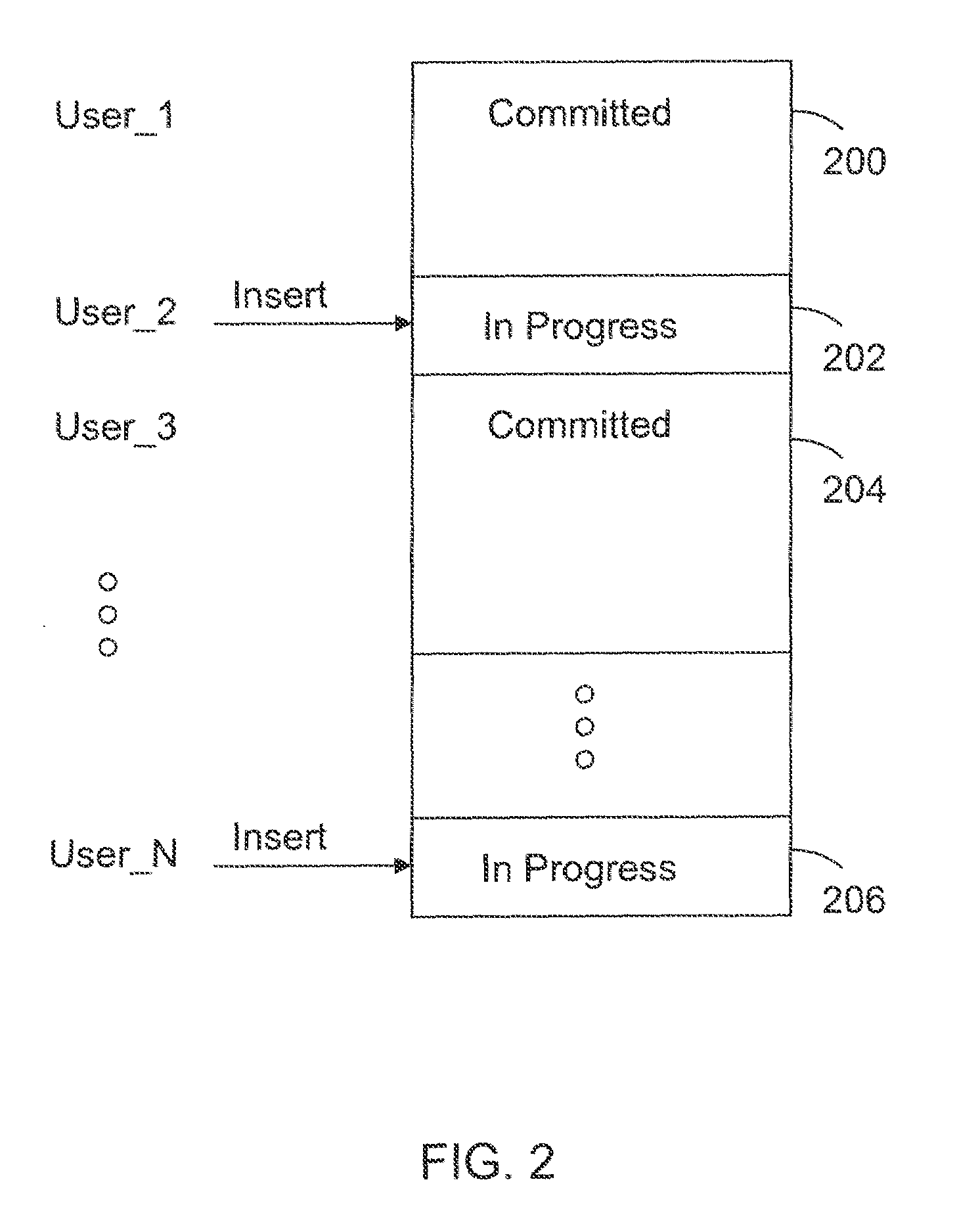
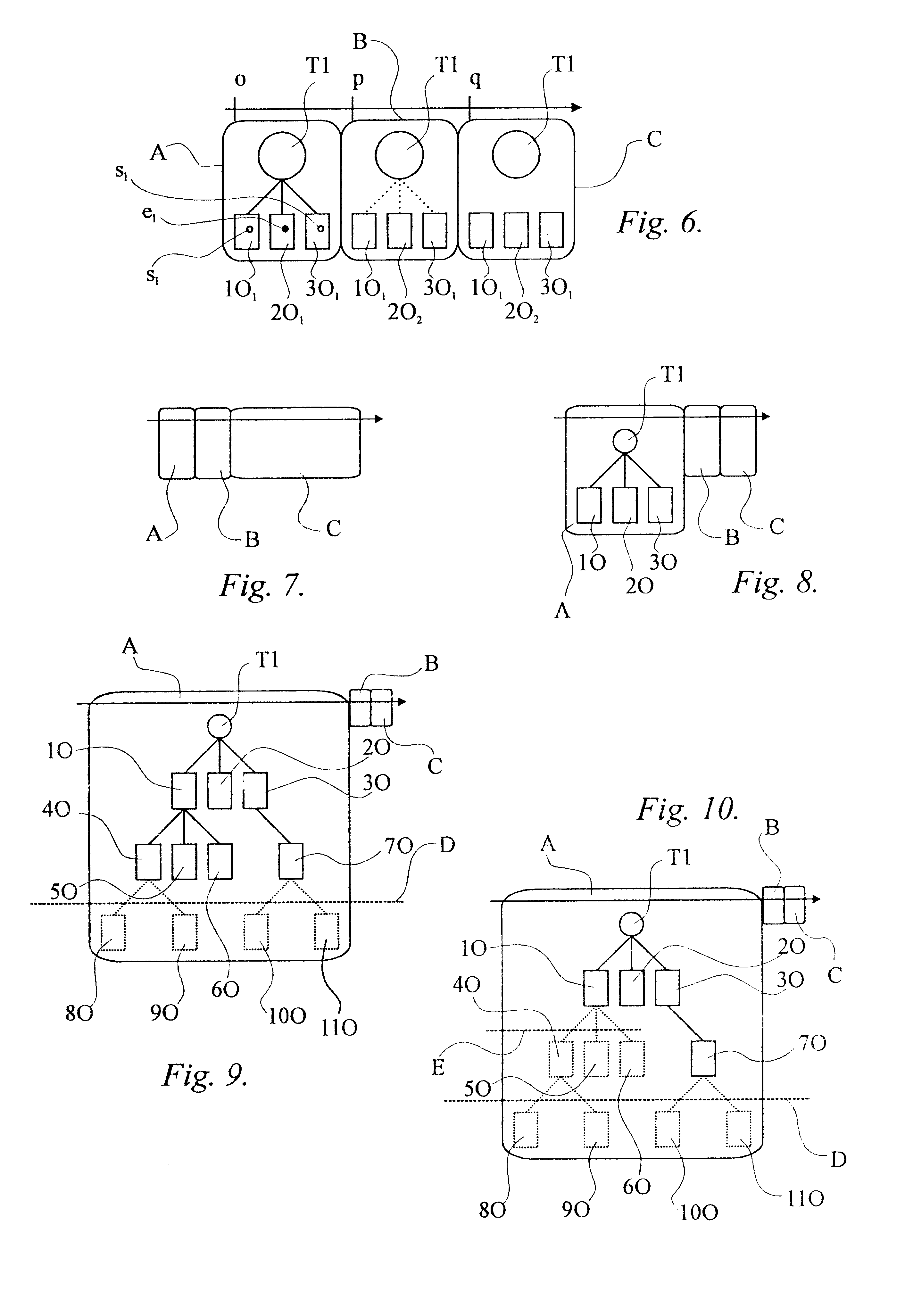
A method is provided for consistent reading of a number of objects (1O, 2O, 3O) within a database. The method is adapted for use with a database in which transactions are managed by two-phase locking. A first phase (A) includes a request for access to objects (1O, 2O, 3O) affected by the transaction and locking of these objects as soon as access thereto has been granted. A second phase (B) includes committing the transaction and releasing all locks that were set in the first phase. The actual work performed in a transaction may be summarized as object changing actions and / or object non-changing actions. A change, or an update, of the content of an object is performed by writing the new content into a new version of the object, where the current version of the object prior to the transaction is retained until no further transactions make use of this version. The transaction performs all changing actions within the first phase (A). The transaction is adapted to retain access to the objects (1O, 2O, 3O) after the second phase (B). The transaction is also adapted to perform the largest possible number of non-changing actions in a third phase (C), after the second phase (B), whereafter the transaction closes access to the objects. Thus, the transaction is provided with a consistent snapshot of effected objects (1O, 2O, 3O) in the database after the locks have been released, with regard to non-changing actions.
Owner:TELEFON AB LM ERICSSON (PUBL)
System and method of failover recovery
In some example embodiments, a method comprises: receiving, by a first node of a plurality of nodes in a distributed database system on a shared disk cluster infrastructure, a transaction request to perform a user database transaction a data item in a user database on a shared disk; acquiring, by the first node, a transaction lock for the data item; storing a lock file for the user database transaction in a lock information database on the shared disk, the lock file comprising lock information for the transaction lock and an indication of a status of the user database transaction, and the lock information comprising an identification of a location of the data item; and storing a transaction record of the user database transaction in the user database on the shared disk subsequent to the storing of the lock file in the lock information database on the shared disk.
Owner:SYBASE INC
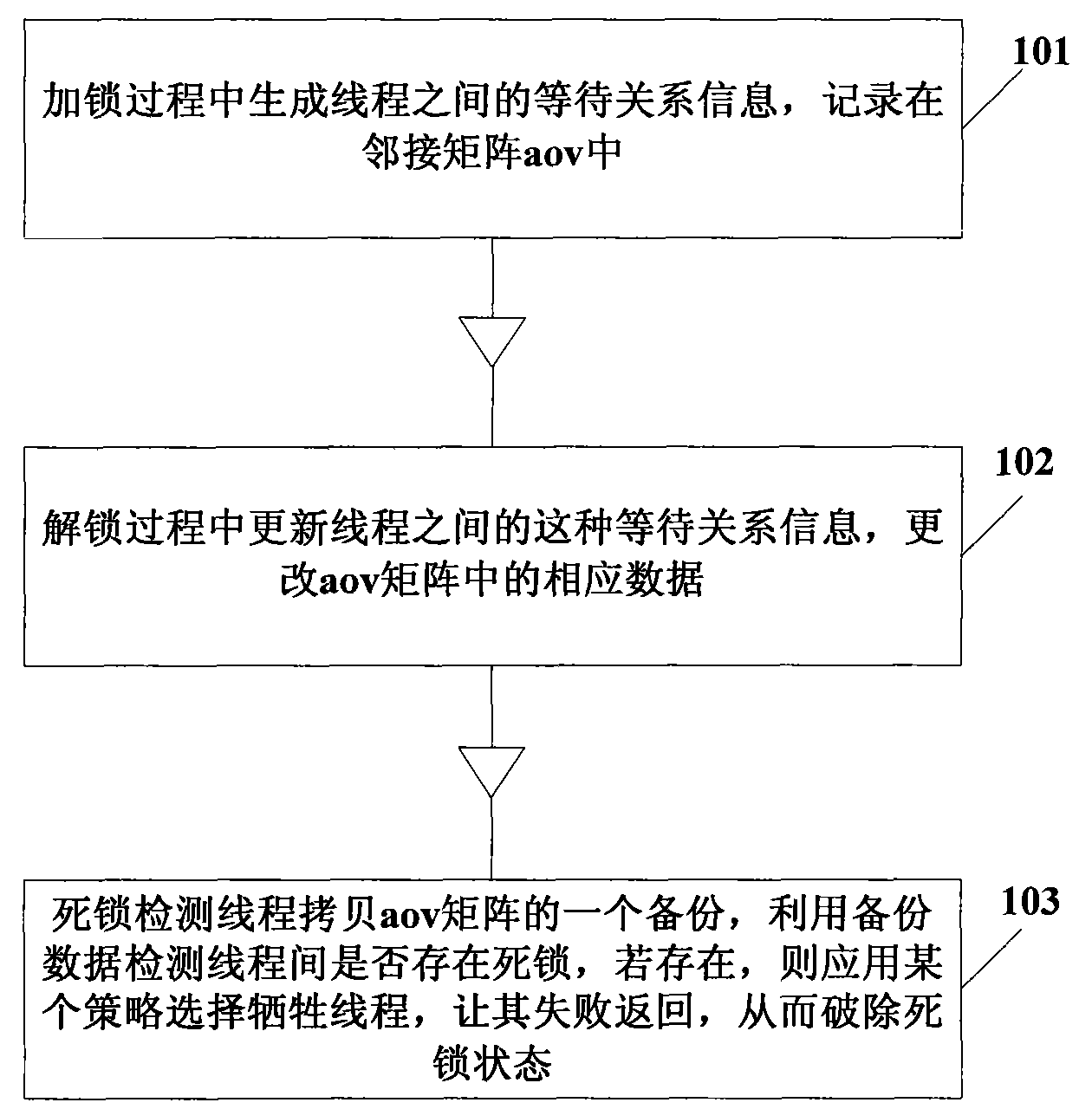
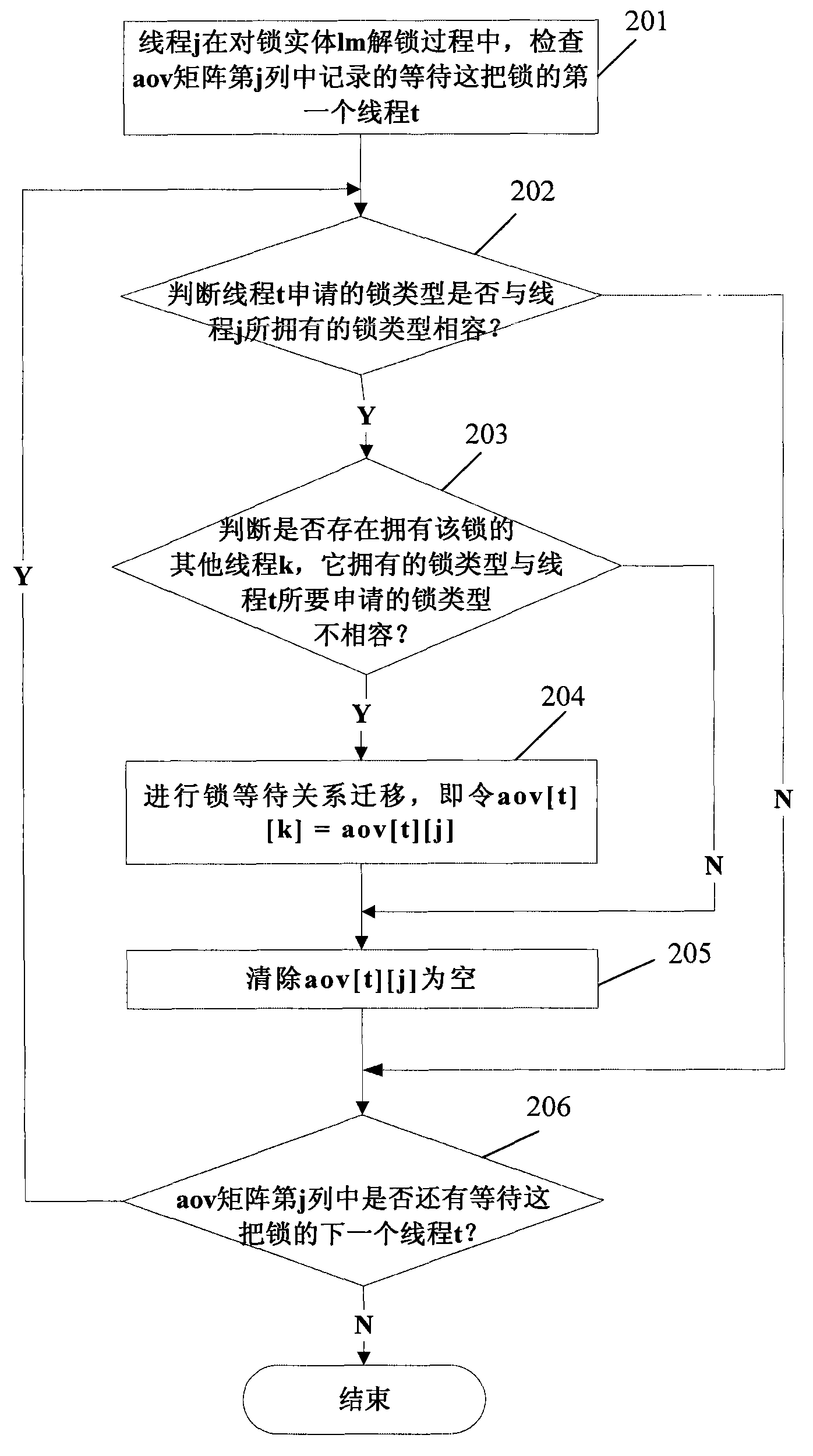
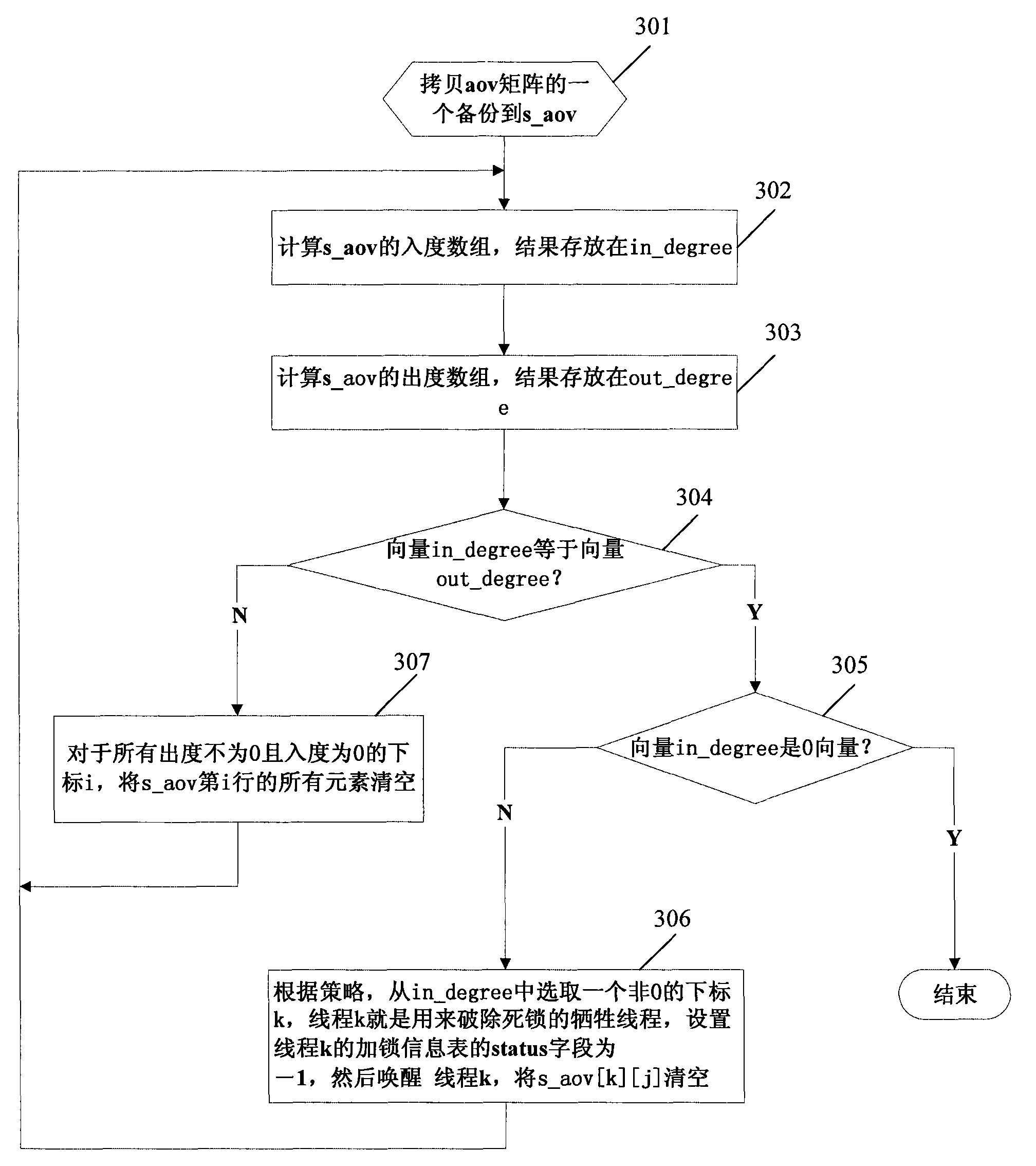
Deadlock detection method and device of database transaction lock mechanism
ActiveCN101576830AHigh deadlock detection speedSave computing resourcesDigital data information retrievalMultiprogramming arrangementsLocking mechanismComputer science
The invention discloses a deadlock detection method and a device of a database transaction lock mechanism, which is characterized by predefining an adjacency matrix for storing cross-thread waiting relation messages. The method comprises the following steps: a locking thread records the cross-thread waiting relation messages generated in the process of locking in the adjacency matrix; an unlocking thread updates corresponding waiting relation messages in the adjacency matrix in the process of unlocking according to the requirements; a deadlock detection thread detects and calculates the thread by adopting the adjacency matrix and principles of graph theory so as to judge whether deadlock exists. The device comprises a message storage module, a deadlock detection module, and a message record module and a message update module. The technical proposal of the invention has extremely high deadlock detection speed, can fully utilize useful messages obtained in the processes of locking and unlocking to assist subsequent deadlock detection and saves calculation resources.
Owner:FORTUNE TECH CO
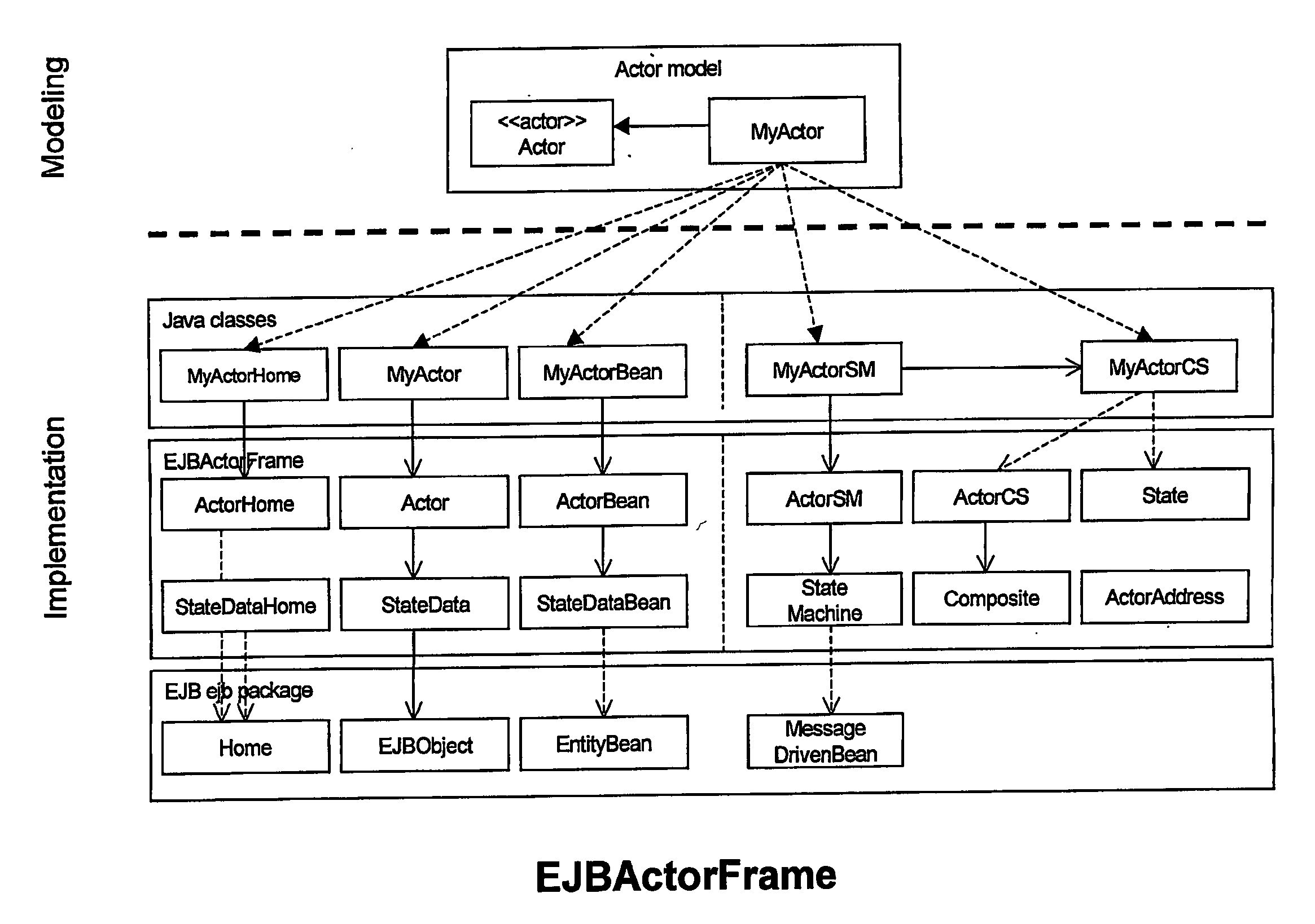
Non blocking persistent state machines on enterprise java bean platform
InactiveUS20060294493A1Specific program execution arrangementsSecuring communicationMessage oriented middlewareEnterprise Java Bean
The present invention discloses a method and an arrangement for using a platform independent model comprising one or more state machines, and a generic middleware platform for orthogonally mapping the platform independent model to a source code and / or byte code platform, where an asynchronic behaviour is shown on the modelling level, and the source code or byte code level is achieved using message oriented middleware application API adapted for message exchange between clients both in point to point and publish / subscribe messaging regime and, persistency for one or more state machines is achieved using one or more modules adapted for database transactions, where the modules may handle concurrent access from multiple clients to the database.
Owner:TELEFON AB LM ERICSSON (PUBL)
Process and system for auditing database activity
ActiveUS8799225B2Digital data information retrievalDigital data processing detailsData accessDatabase schema
Described is a database audit system used to monitor, and optionally alert on database activity, providing a complete record of access to data and database structure. The data audit system may also provide an audit trail of data accesses and changes to database schema and permissions. A database audit may be performed by collecting data from database transaction logs and traces, exporting the collected data into a repository, and analyzing the data in the repository to create data audit reports and to provide data audit browsing capabilities.
Owner:BEYONDTRUST SOFTWARE INC
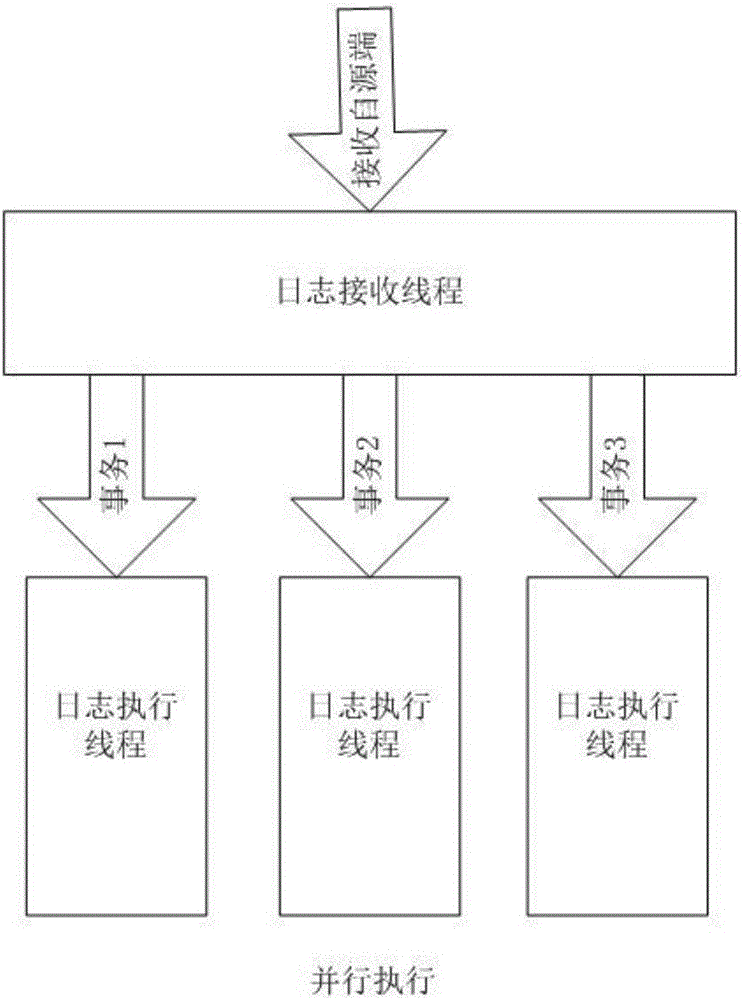
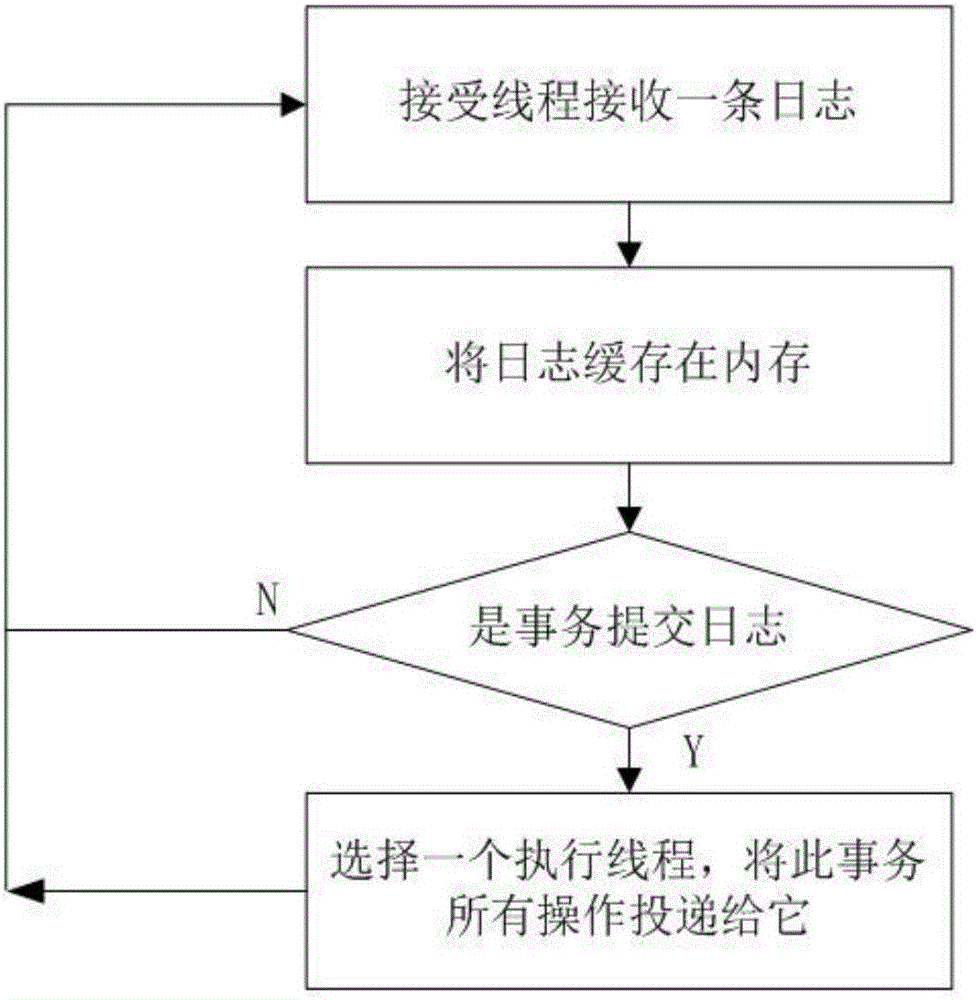
Heterogeneous-database-replication parallel execution system and method based on synchronization of commit-point timelines
InactiveCN106777270AImprove replication efficiencySolve the technical problem of replication inefficiencySpecial data processing applicationsChronological timeTime line
The invention discloses a heterogeneous-database-replication parallel execution system and method based on synchronization of commit-point timelines. The system includes a source database, a target database and a replication system. The system and method have the advantages that for preventing destination-end events from execution failure, a traditional data replication system based on logs serially executes logs of various events according to the time sequences (LSN numbers) of the logs and does not consider the probability of the parallel execution of events. According to the system and method, commit-point timelines are adopted to form fences, the characteristic that all upload operations between two timelines do not colloid with one another is adopted, the operations are executed at the destination end in parallel, the replication efficiency is greatly improved, and the technical problem of the low replication efficiency caused by the serial execution of events in the target database is solved.
Owner:TRAVELSKY +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com