Secure item identification and authentication system and method based on unclonable features
a technology of which is applied in the field of secure item identification and authentication system and authentication method based on unclonable features, can solve the problems of counterfeiters who previously benefited, the storage of item surface images (fingerprints), and the compressed version or feature of items in open or even encrypted form, so as to enhance the efficiency of search procedures, efficiently use, and compute the effect of cross-correlation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
)
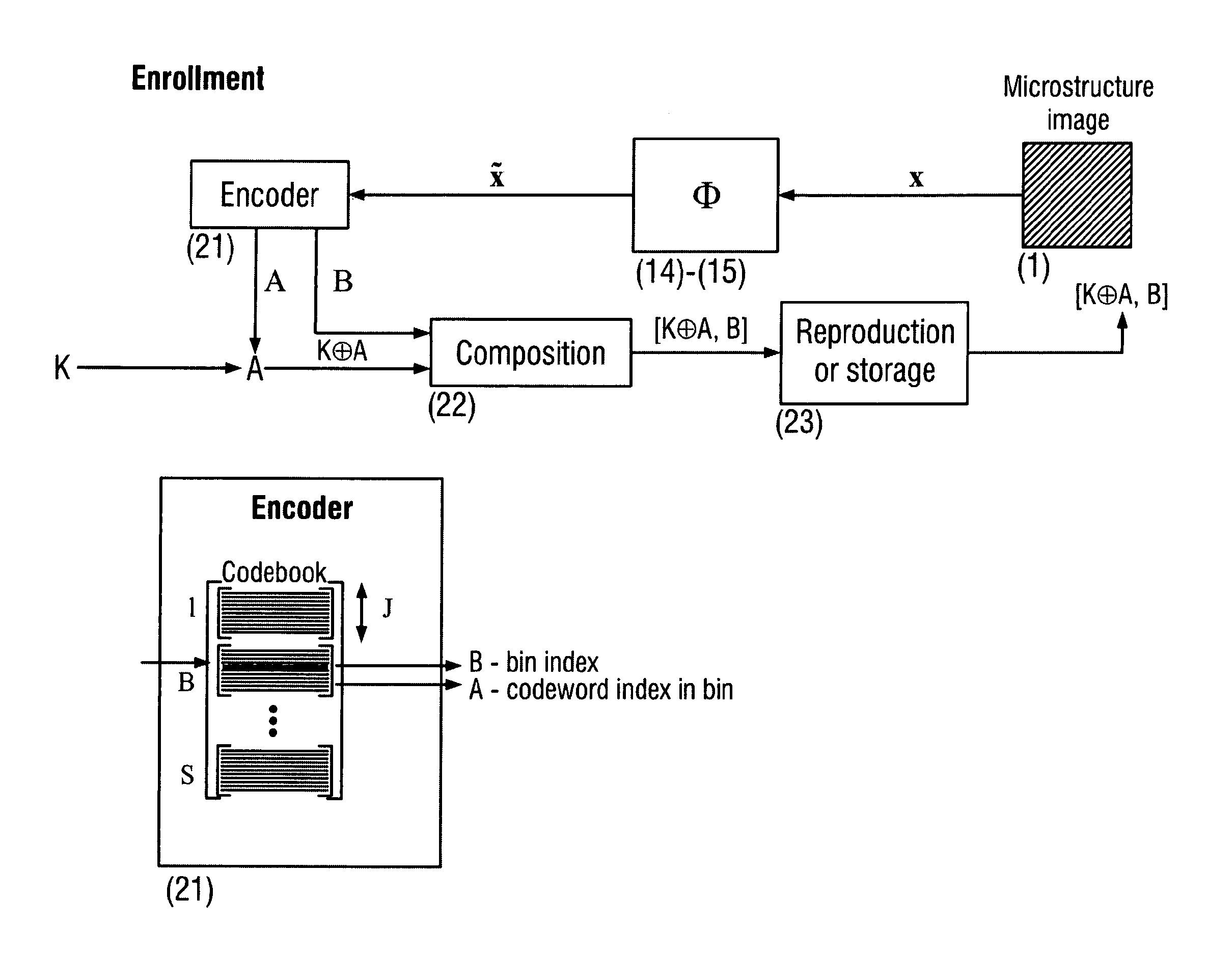
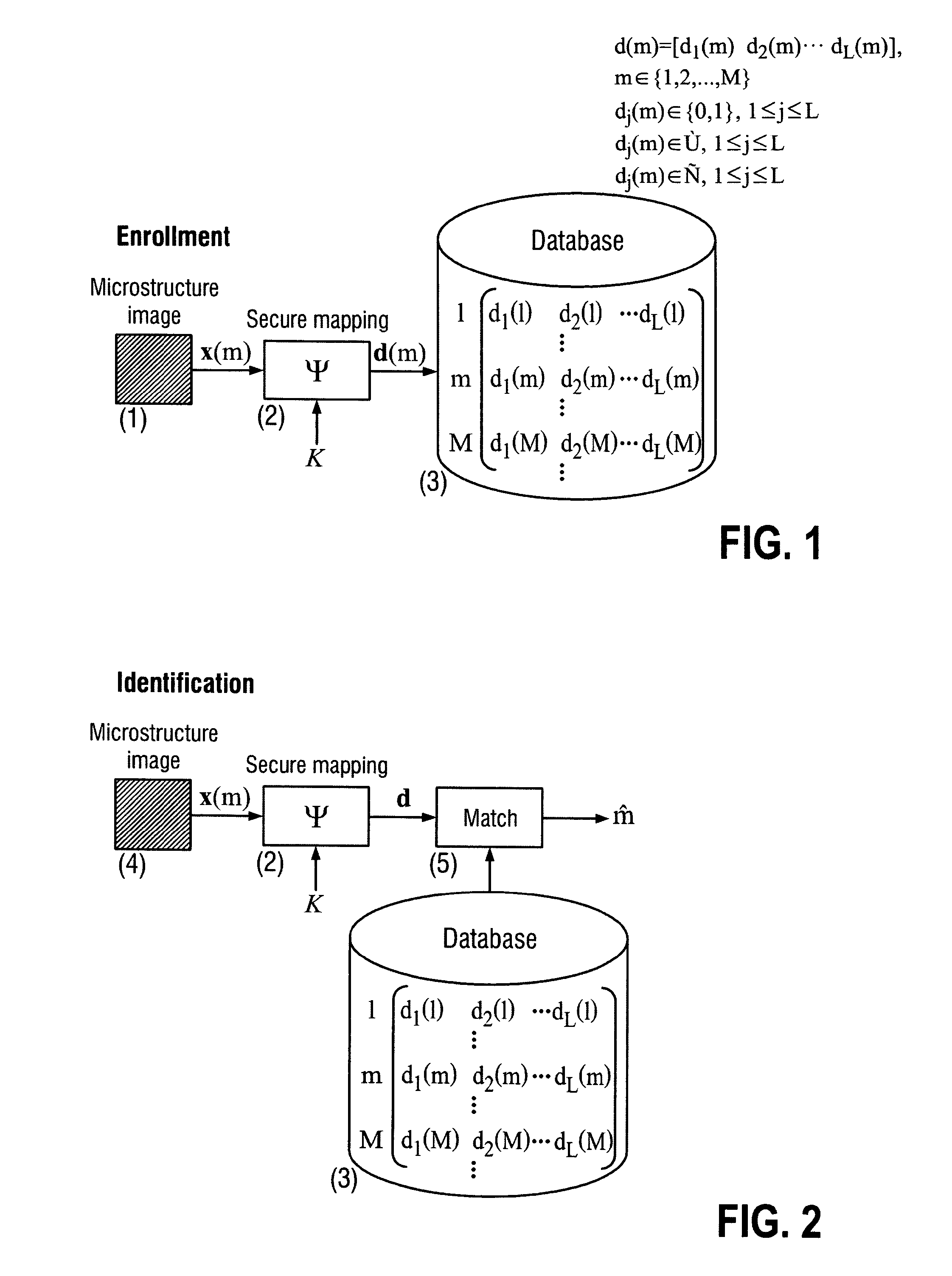
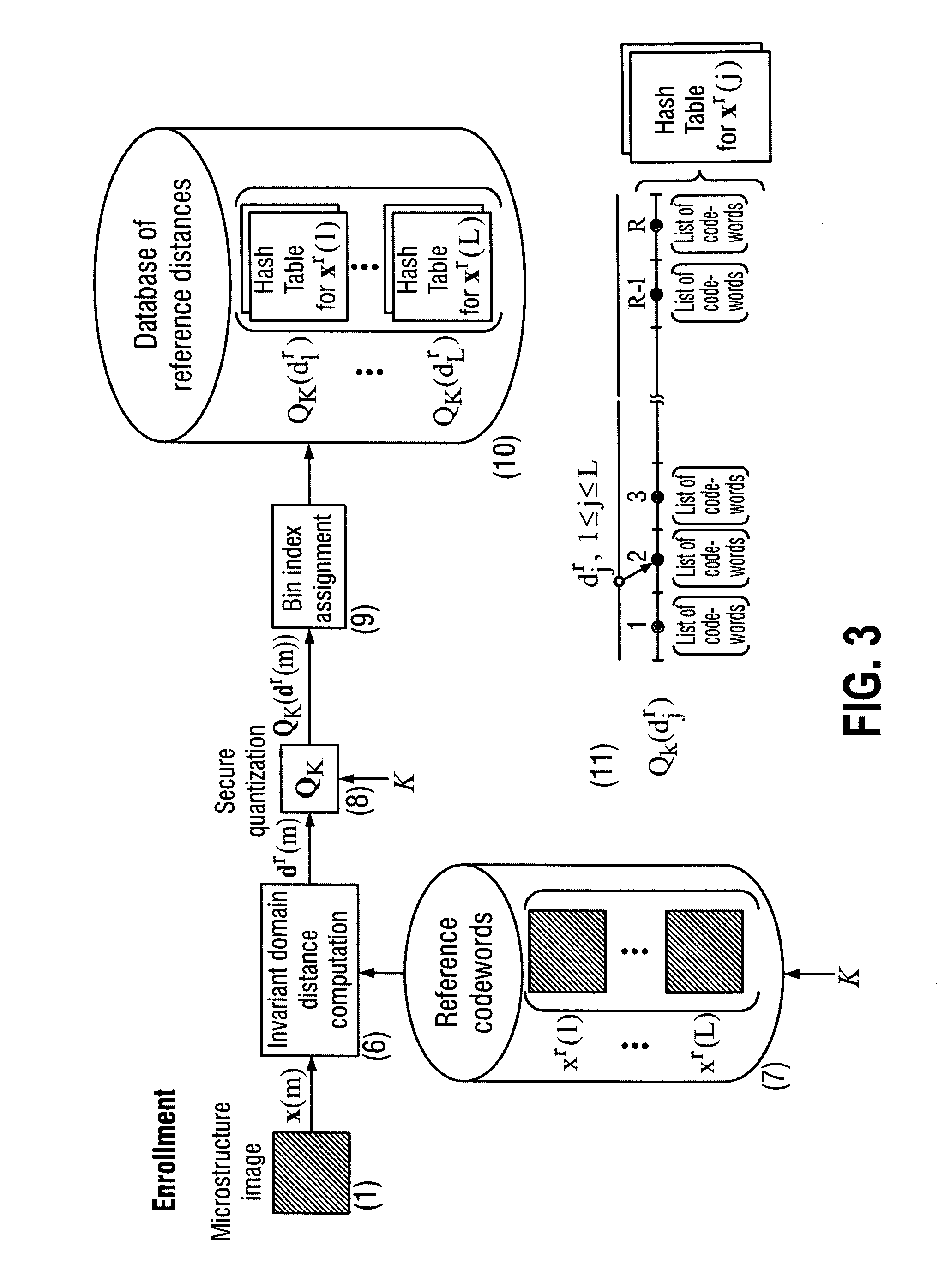
[0058]The invention proposes a novel protocol for secure identification and authentication of various items using unclonable features. The protocol acts in two modes, identity verification and authenticity verification. Both modes are implemented based on unique unclonable features of item surfaces that either have a natural origin or artificially produced by humans by printing, laser engraving, coating, gluing, sticking, painting, stamping, embedding, light exposition, heating, current passing, potential charging or any other forms of radiation or physical impact, etc. Due to the unfeasibility of their copying and reproduction, these features can be used as secure item identification / authentication codes as well as inputs for generation of such codes or secure keys extracted from the natural randomness. The second distinctive feature of the invention is the mobile platform in sense that item identification / authentication is performed based on typical mobile phones, Pocket PCs, Sma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com