Sensitive information desensitization method and system for data sharing
A sensitive information, data-oriented technology, applied in the intersection of information technology and data security, can solve problems such as mismatch between type and source data type, inability to guarantee the uniqueness of identification and format consistency requirements, data loading errors, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
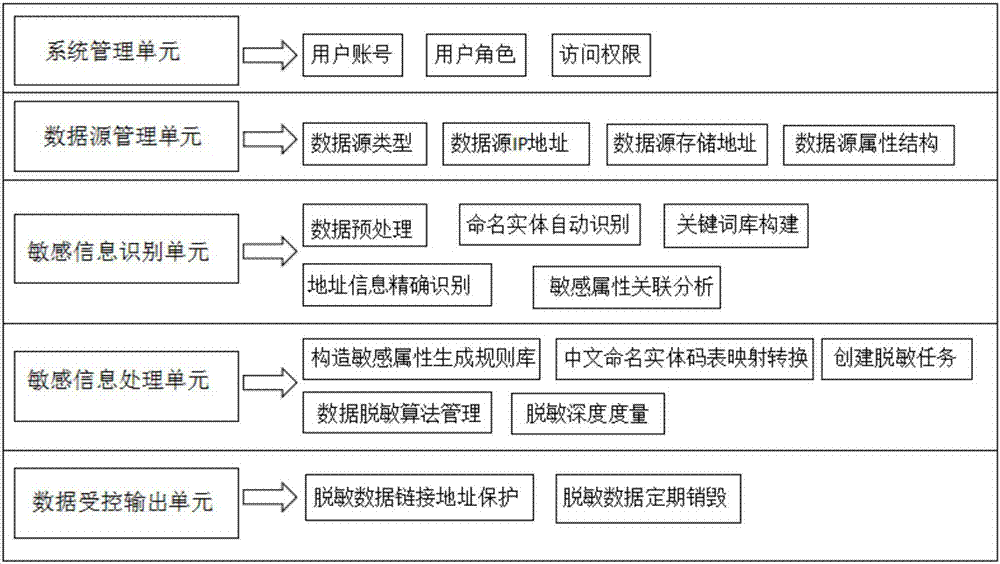
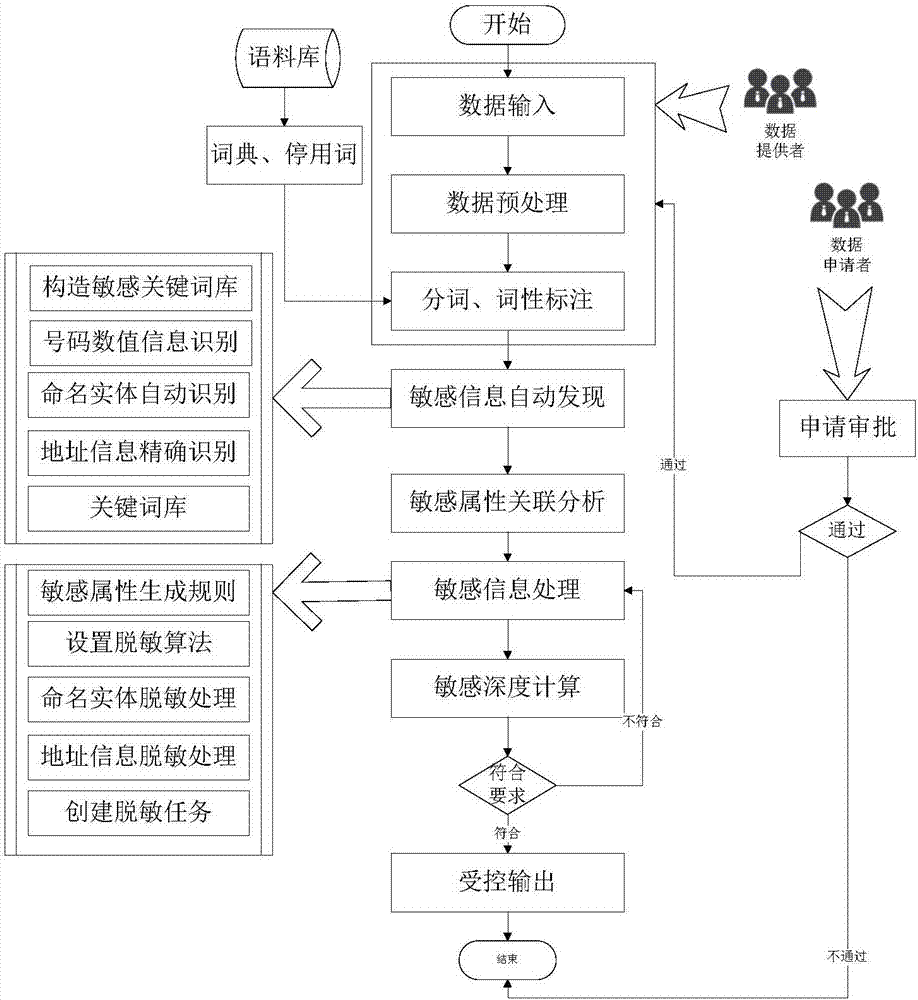
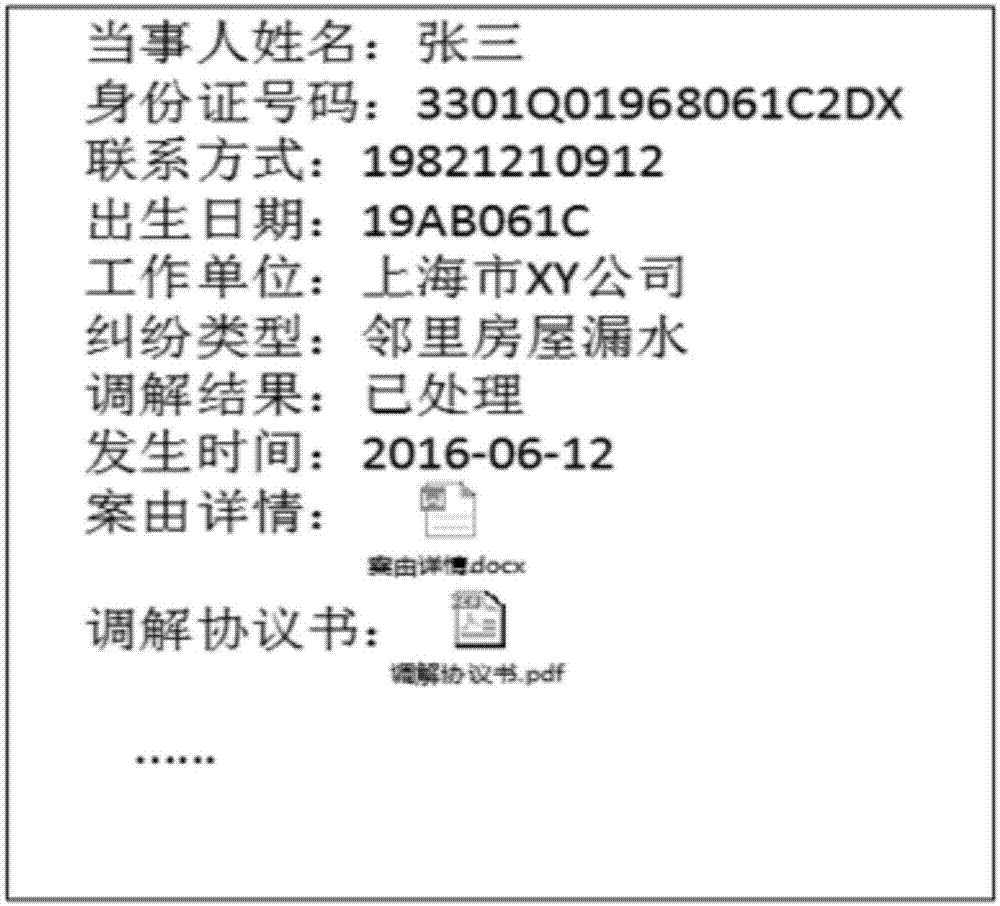
[0045] Example: such as figure 1 As shown, a sensitive information desensitization system oriented to data sharing includes a system management unit for setting and managing system user account information, and constructing role and authority configuration; a data source management unit for storing data source information; capable of automatically identifying each Sensitive information in type data sources, and a sensitive information identification unit that can calculate the correlation of sensitive attributes in a data source set; a sensitive information processing unit that can automatically create desensitization tasks and match desensitization strategies and desensitization algorithms; can safely and effectively A data output unit that controls the use of sensitive data. The system management unit includes building a desensitization system user account and access control, identifying the user's role and authority, and only allowing legal and authorized users to operate c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com