Perception-free authentication method and system, control method and system based on same
A non-perceptual authentication and control method technology, applied in transmission systems, wireless communications, network data management, etc., can solve problems such as roaming failure, slow switching speed, and increased delay of authentication messages, so as to improve authentication efficiency and provide a better user experience , The effect of reducing the process of authentication requests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
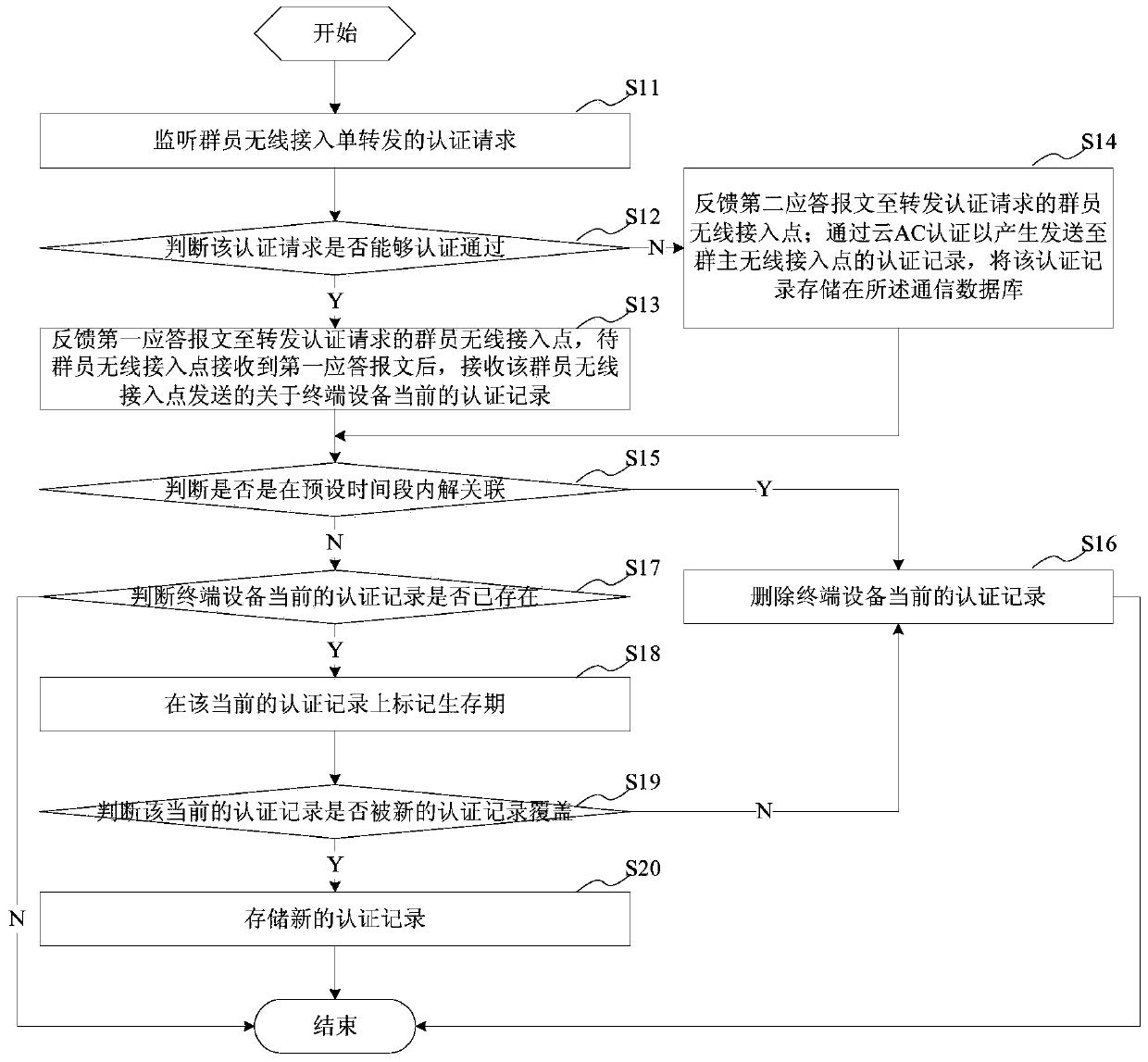
[0048] This embodiment provides a non-perceptual authentication method, which is applied to a wireless communication network composed of a terminal device, multiple wireless access points, and a cloud AC. The group includes a group master wireless access point and a plurality of group member wireless access points, and the non-aware authentication method includes the following steps:
[0049] After the cloud AC establishes communication links with a plurality of wireless access points, the monitoring group member wireless access point forwards the authentication request originating from the terminal device;
[0050] Judging whether the authentication request can be authenticated, if so, feed back the first response message to the wireless access point of the group member forwarding the authentication request to allow the terminal device to directly access the Internet; if not, feed back the second response message to forward the authentication request The wireless access point...
Embodiment 2
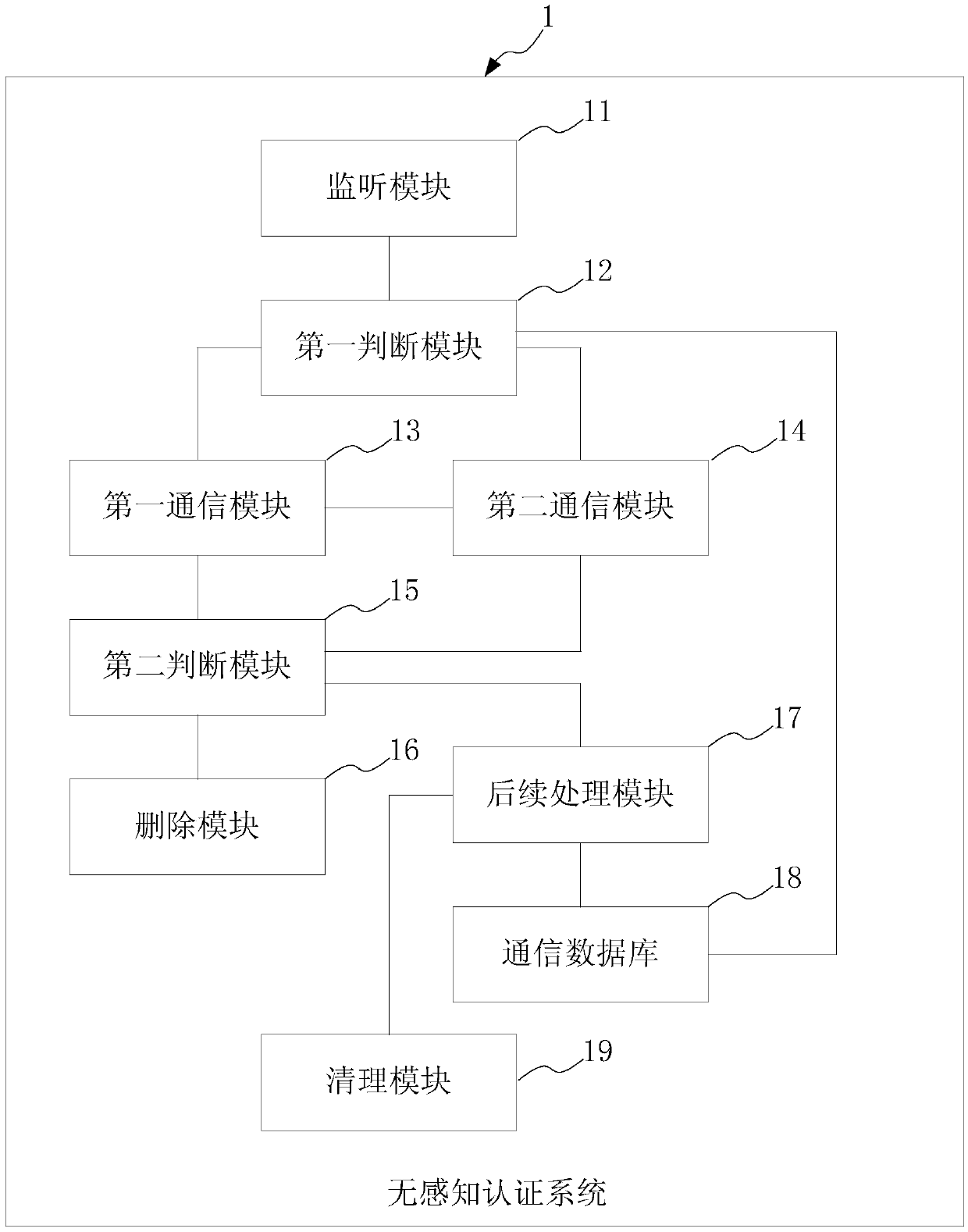
[0062] This embodiment provides a non-perceptual authentication system, which is applied to a wireless communication network composed of terminal equipment, multiple wireless access points, and cloud ACs. A group, the communication group includes a group of master wireless access points and a plurality of group member wireless access points, and the non-aware authentication system includes:
[0063] The monitoring module is used to listen to the wireless access point of the group members to forward the authentication request originating from the terminal device after the cloud AC establishes communication links with multiple wireless access points;
[0064] The first judging module is connected with the monitoring module, and is used to judge whether the authentication request can be authenticated, and if so, calls the wireless access point for feeding back the first response message to the group member wireless access point forwarding the authentication request to allow the te...
Embodiment 3
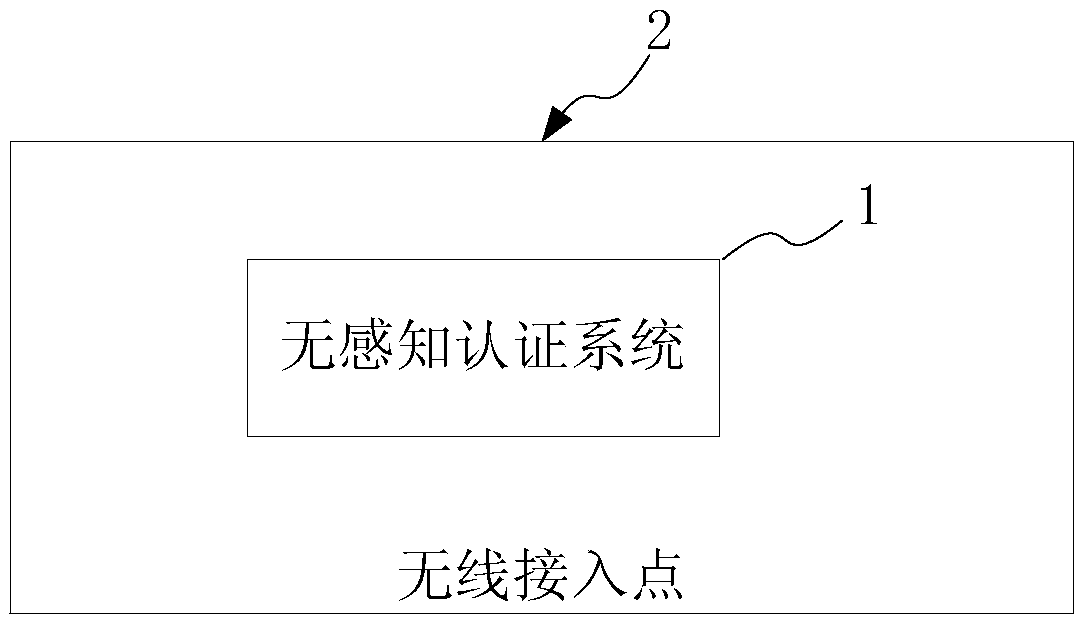
[0074] This embodiment provides a wireless access point 2, please refer to image 3 , which is a schematic structural diagram of a wireless access point in an embodiment. Such as image 3 As mentioned above, the wireless access point 2 includes the sensorless authentication system described in the second embodiment. In this embodiment, the wireless access point 2 includes a processor and a memory, the processor is used to implement all functions of the non-aware authentication system except the function of storing authentication records, and the memory is used to implement the communication database Function to store authentication records.
[0075] The wireless access point described in this embodiment can prevent the terminal device from obtaining authentication information from the remote cloud AC when it is in the roaming state, reducing the process of cross-public network authentication requests and improving authentication efficiency, so that users roaming A very good...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com