Terminal access authentication authorization method and terminal access authentication authorization system
A technology of authentication authorization and terminal access, applied in the field of network security, can solve the problem that the terminal authentication method is difficult to ensure the overall security of the system, and achieve the effect of ensuring security and eliminating attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
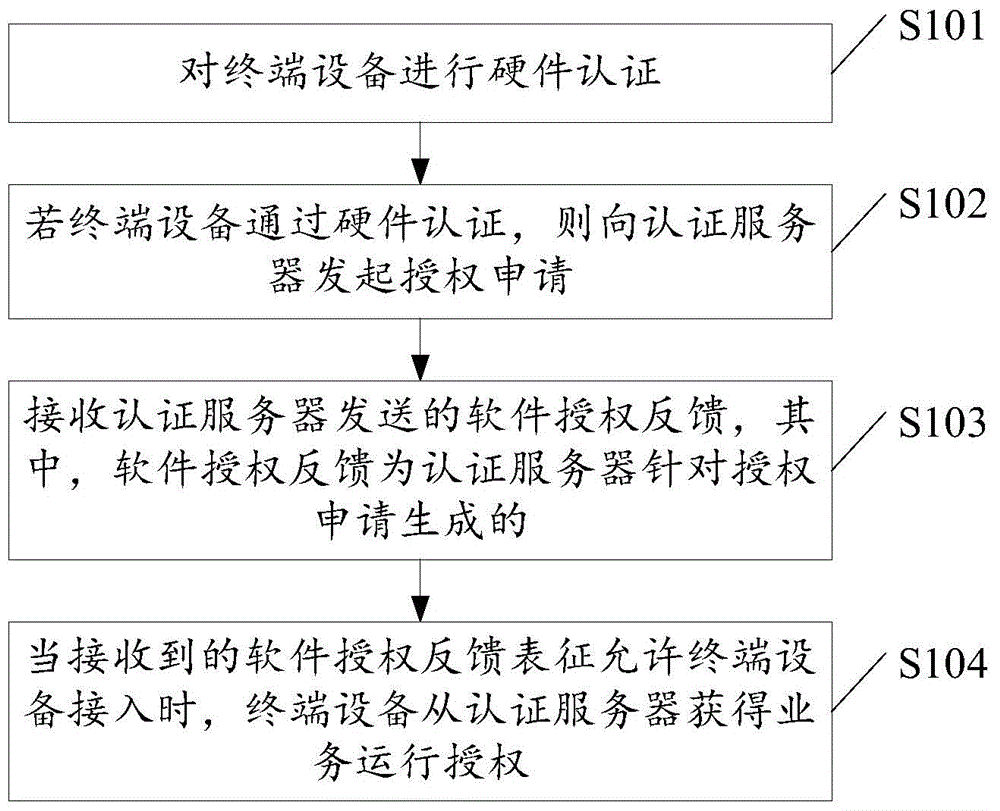
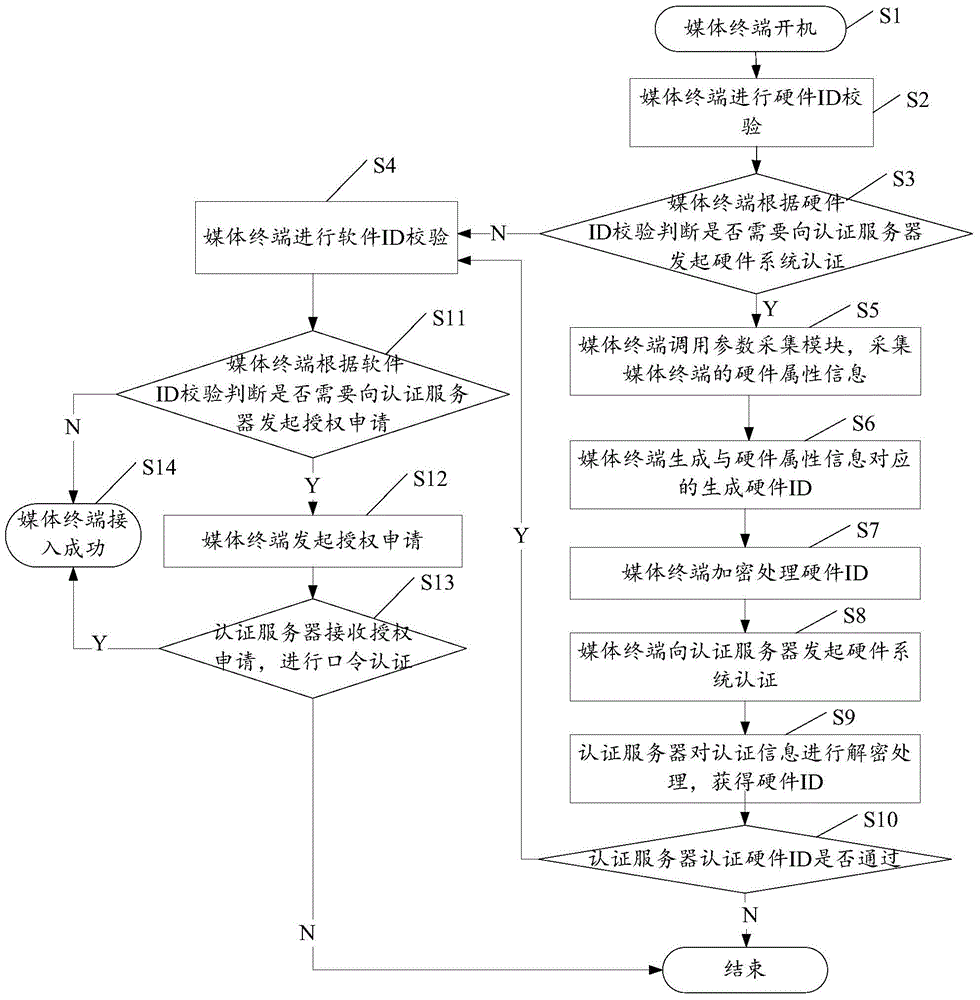
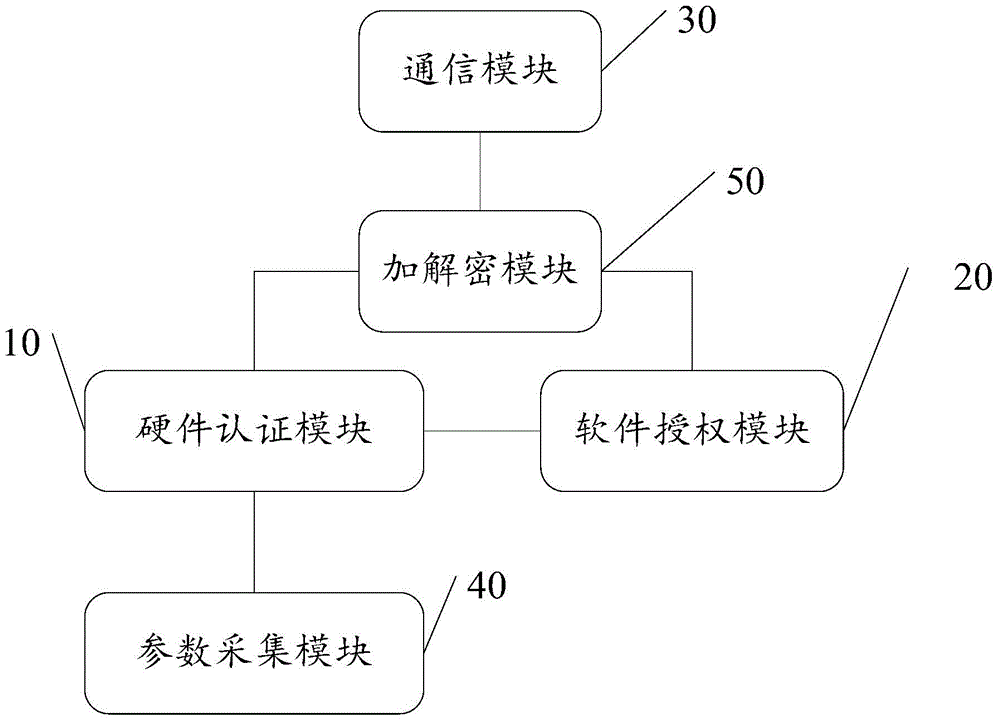
[0020] Embodiments of the present invention provide a terminal access authentication and authorization method and a terminal access authentication and authorization system, which solve the problem that a single terminal authentication method in the prior art cannot guarantee the overall security of the system itself. The general idea is as follows:
[0021] The first is to identify the type and attribute of the terminal device, authenticate the entity identity of the terminal device, and then perform reasonable software authorization according to the authentication result, so that the correct media information can be played on the correct terminal, which solves the problem of terminal device access control. The problem of "soft" or "hard" makes the terminal device perform access control management as a complete entity.
[0022] In order to better understand the above-mentioned technical solution, the above-mentioned technical solution will be described in detail below in conjun...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com