Safety isolation method based on firewall system
A security isolation and firewall technology, applied in the computer field, can solve problems such as increasing server security risks, and achieve the effect of improving privacy and security, and strong defense functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
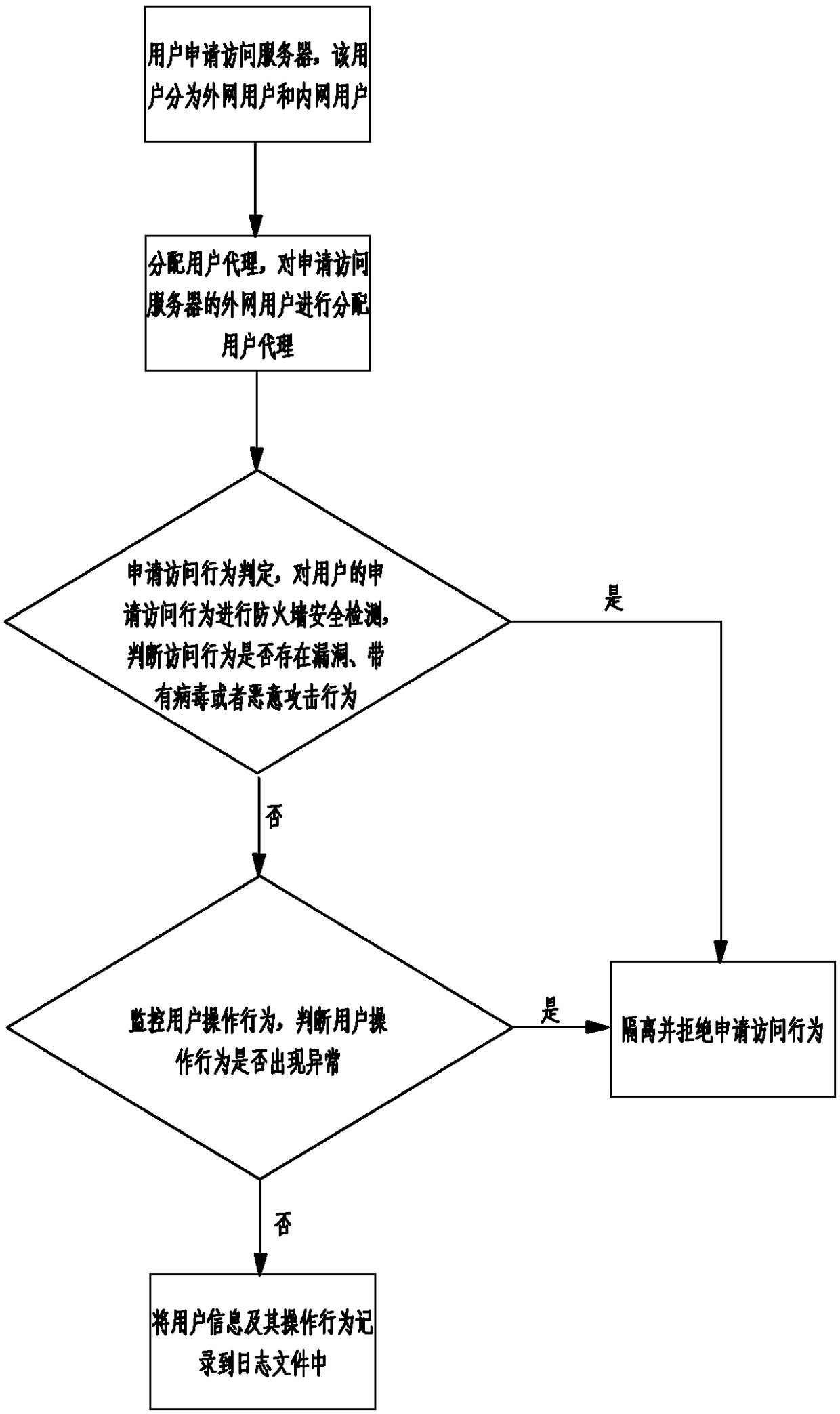
[0017] Such as figure 1 As shown, a security isolation method based on a firewall system includes a user applying for access to a server, and the user is divided into an external network user and an internal network user;
[0018] Assign user agents, and assign user agents to external network users who apply for access to the server;
[0019] Judgment of application access behavior, conduct firewall security inspection on the user's application access behavior, and judge whether there are loopholes, viruses or malicious attacks in the access behavior, if so, isolate and reject the application access behavior, otherwise allow the application access behavior.
[0020] The invention distinguishes internal network users and external network users, and restricts external access by assigning user agents to external network users, so that the system is more secure and safe. At the same time, external network users and internal network users are isolated from each other. Network user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com