Method for encrypting and decrypting image based on cellular automata
A cellular automaton and image technology, applied in the field of information security, can solve problems such as failing to consider algorithm fault tolerance and decryption failure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be described in further detail below in conjunction with accompanying drawing and embodiment, and given embodiment is in order to explain the technical characteristic and function characteristic of the method of the present invention, rather than limit the scope of the present invention.
[0051] The embodiment of the present invention adopts Mathematica 8 software to carry out emulation, and the plaintext image selects the standard test gray-scale image "Lena" that size is 256 * 256, and each pixel of the image is made up of 8 bits, as Figure 5 shown.
[0052] The steps of the encryption method are as follows:
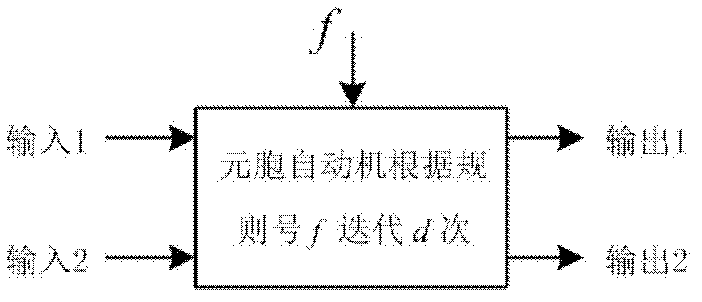
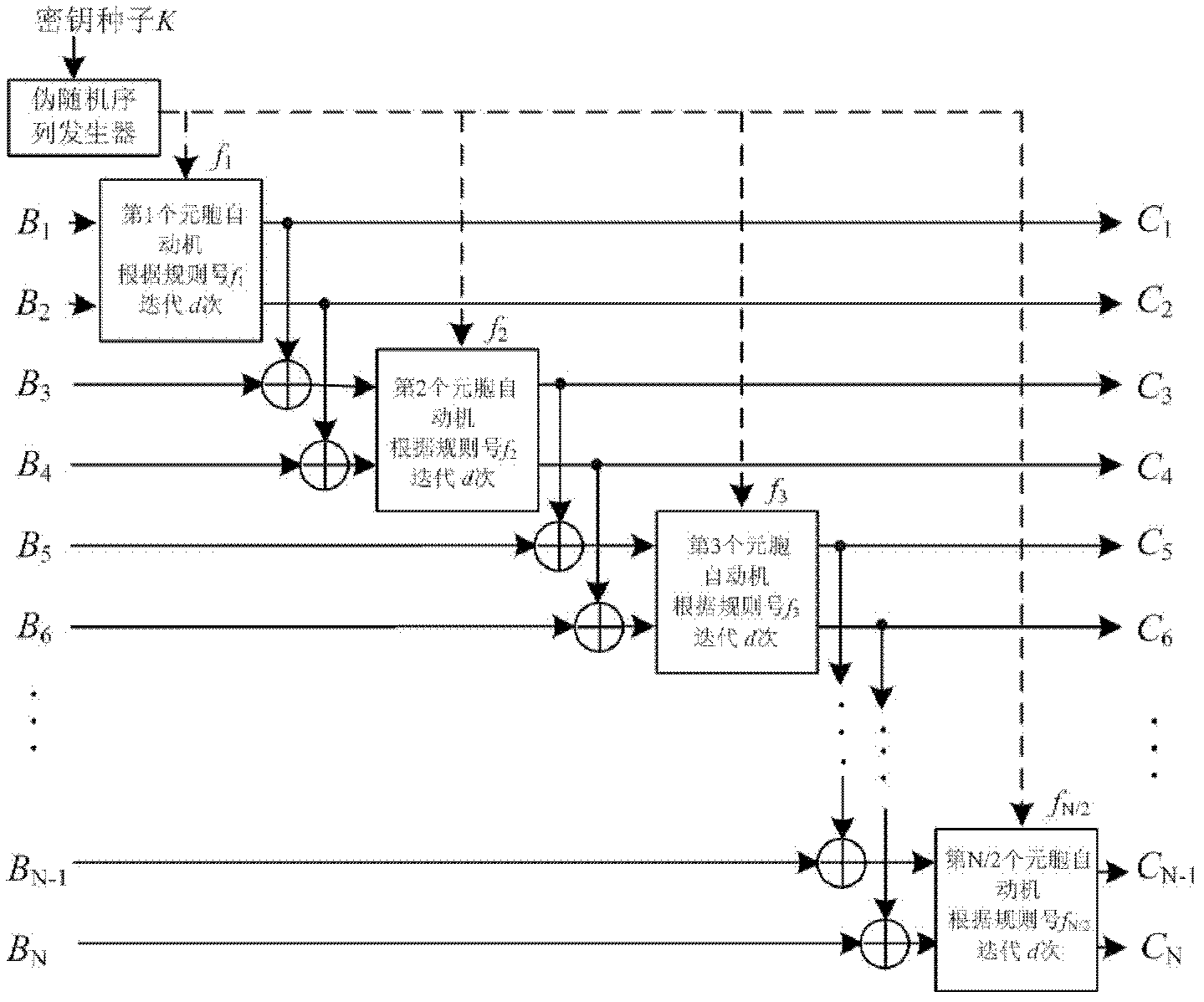
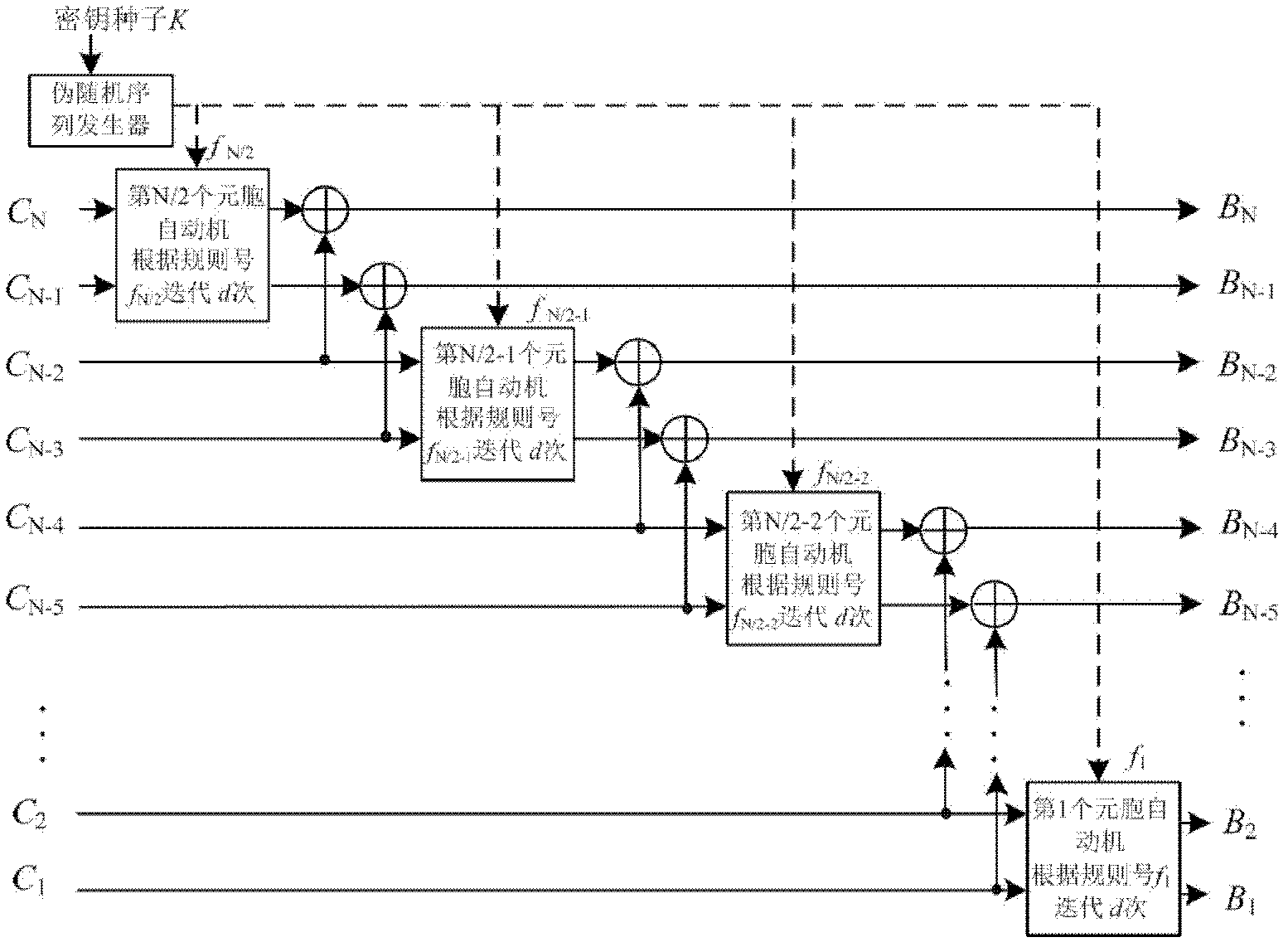
[0053] First, use the Import function of Mathematica to extract the pixel matrix I of the plaintext image 256×256 , and then convert each row of the pixel matrix into 256 binary sequences B 1 , B 2 , B 3 ,...,B 256 , the length of each binary sequence is 2048 bits. Set the number of iterations d=512. Then, use Mathematica's Ra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com