Patents
Literature
66 results about "String Value" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
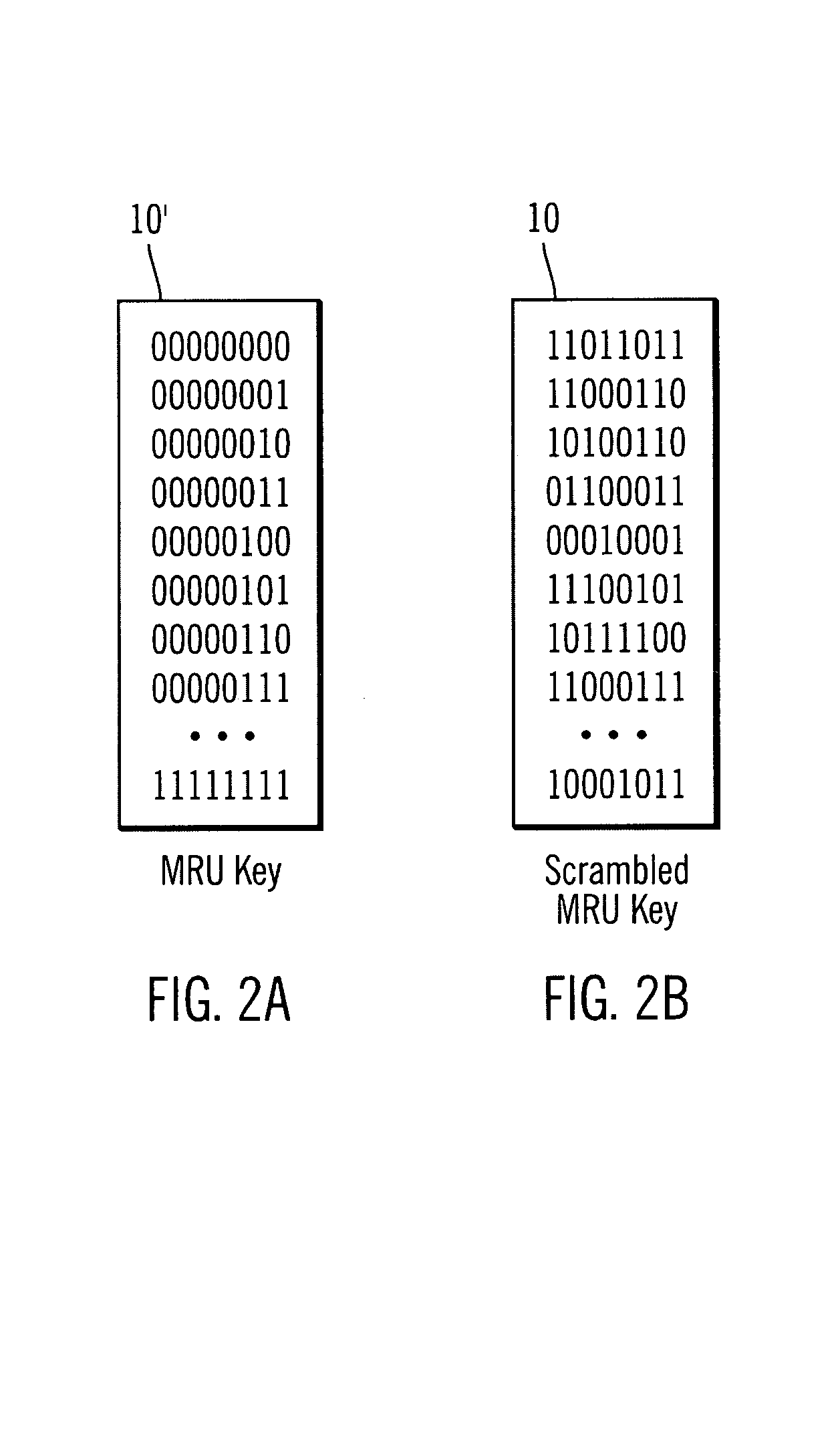
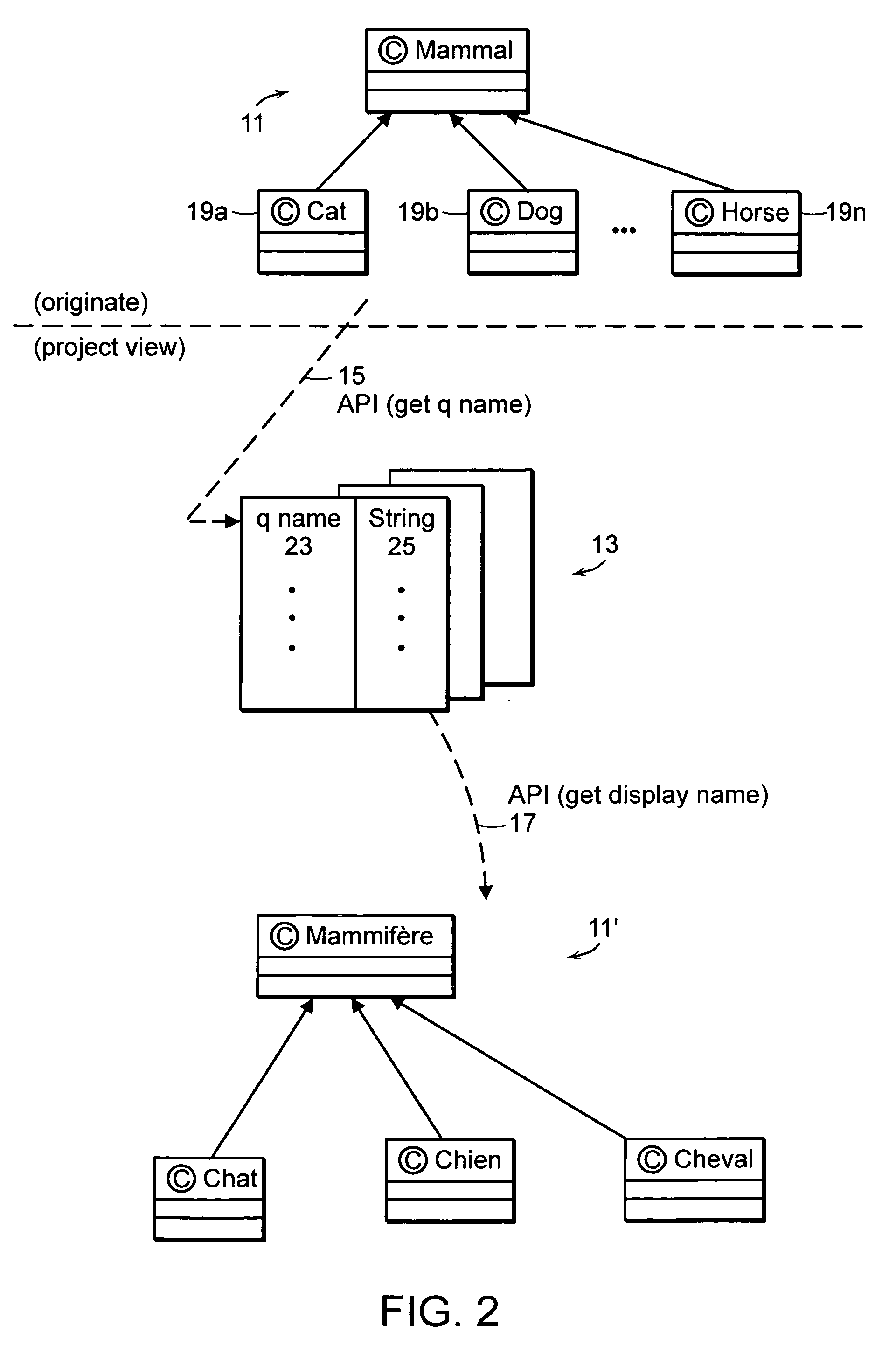
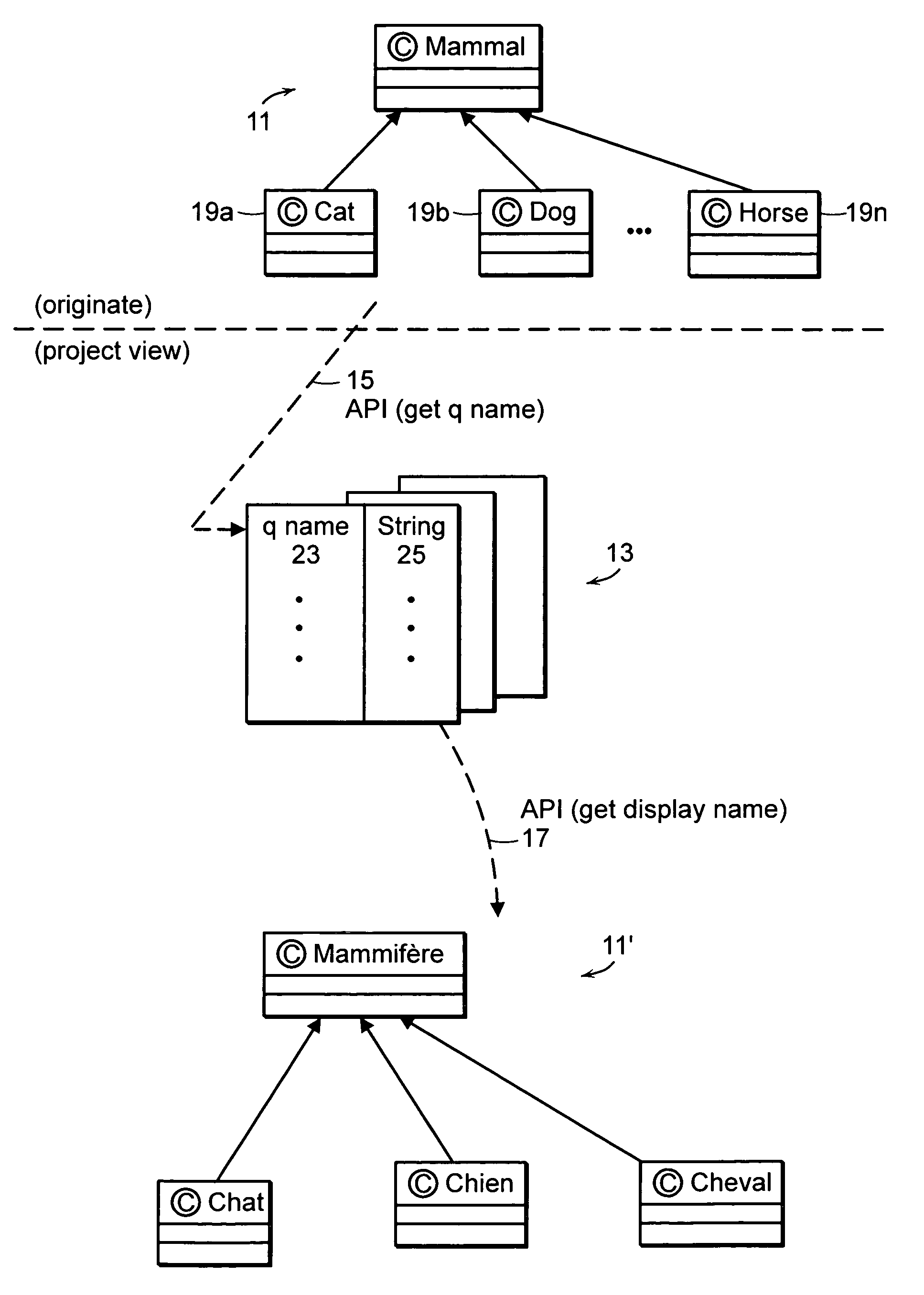
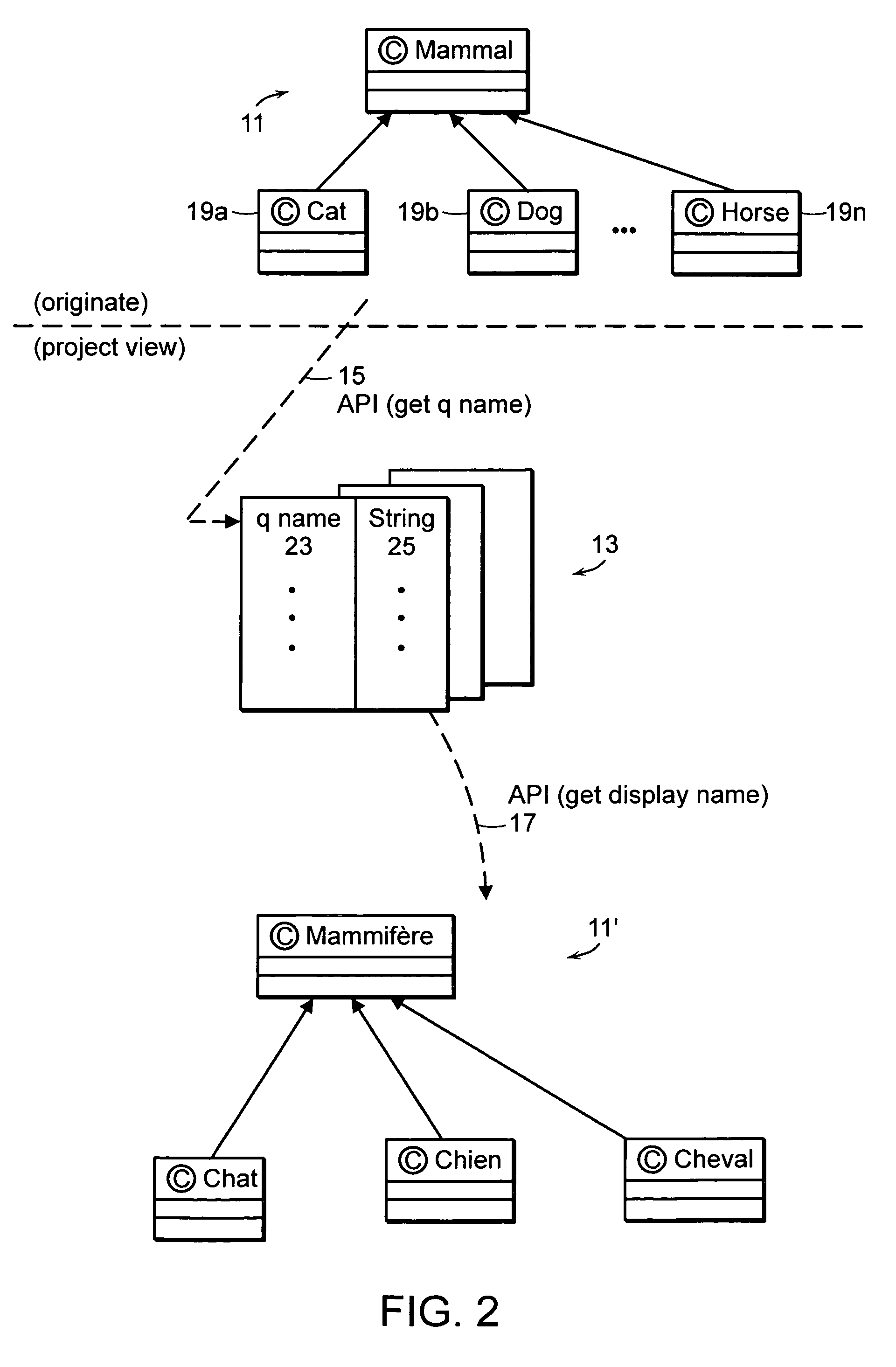
Compilers use string literals to create string values that are stored in string variables. When code containing a string literal is compiled, the compiler turns the literal into a string value. In the example below the string literals are converted to string value and assigned to their respective variables.
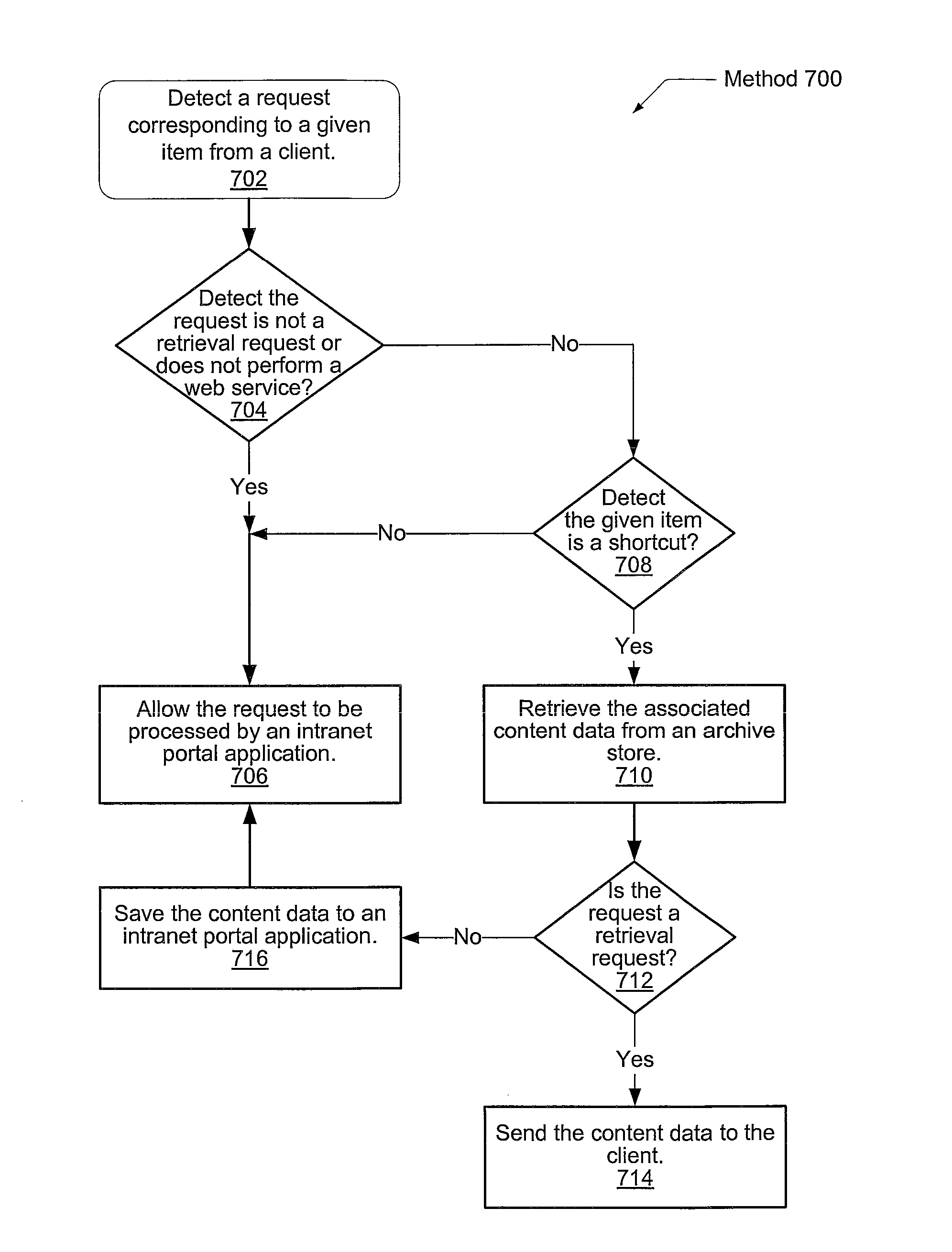
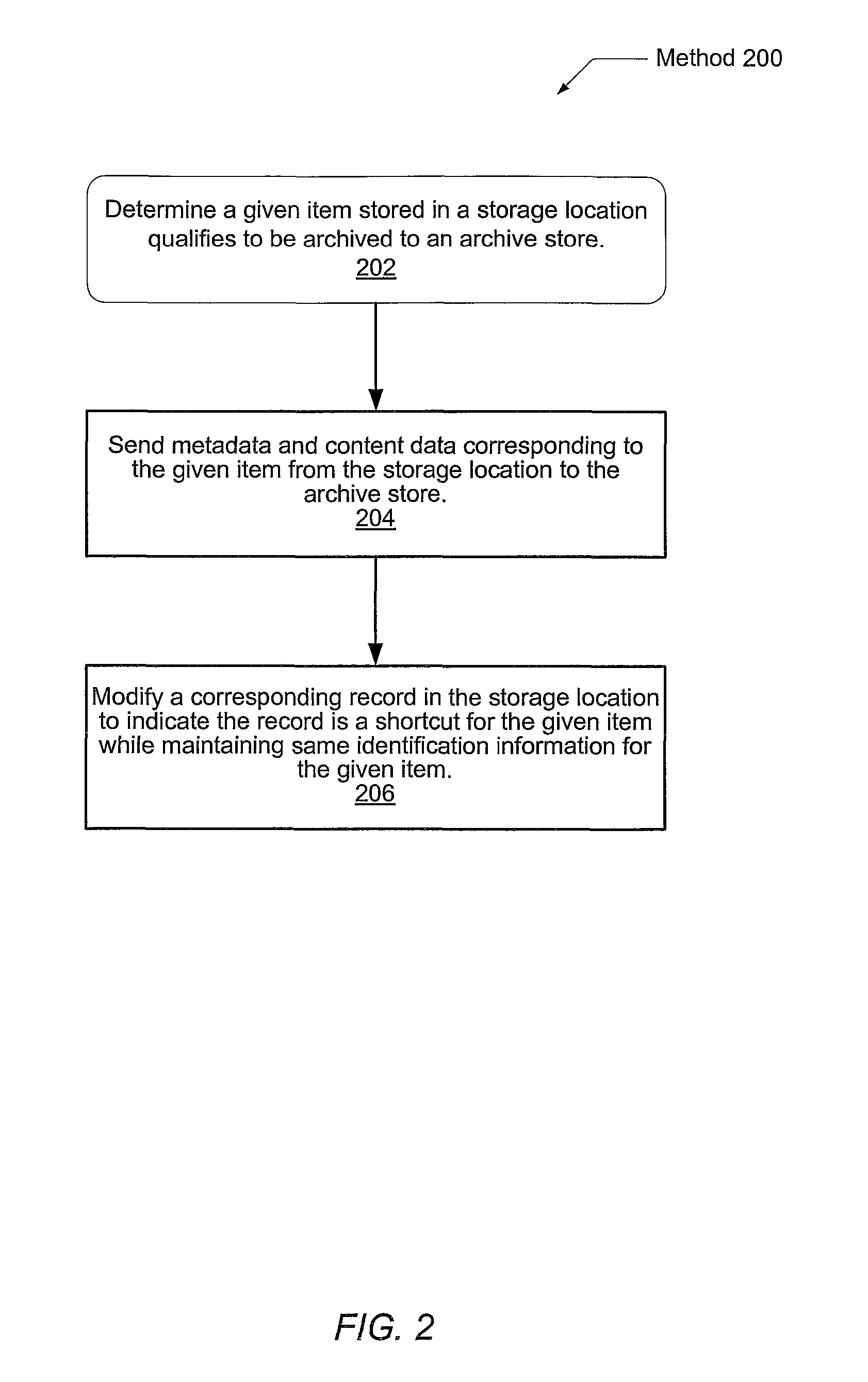
Technique for implementing seamless shortcuts in sharepoint
ActiveUS8489676B1Multiple digital computer combinationsWebsite content managementElectronic documentDocument Identifier
A system and method for creating shortcuts within a database for archived items. A client computer sends a retrieval request for a given item to a web server. The given item may be an electronic document. A custom HTTPModule within the web server intercepts the request. The HTTPModule uses a uniform resource locator (URL) provided in the request to locate a record associated with the given item. If a given fixed string value is read from the record in place of the original content data, then the web server requests original content data for the given item from an archive store. The record still maintains identification information, such as a document identifier and the URL in order to maintain links and workflows. The retrieval request is not rerouted to an alternate path, and the client computer receives the original content data, rather than an indication of a shortcut.
Owner:VERITAS TECH
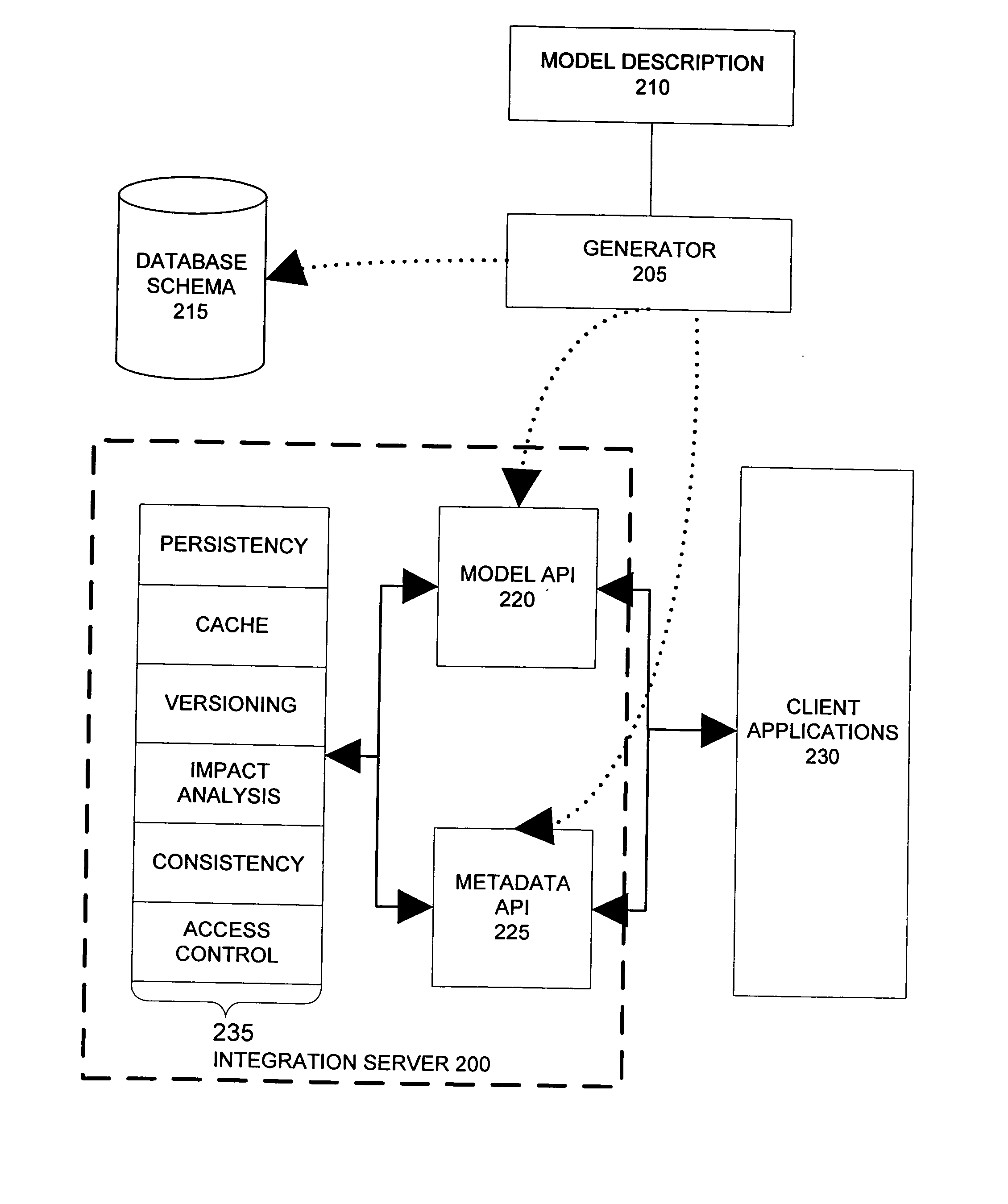
Object relational mapping layer
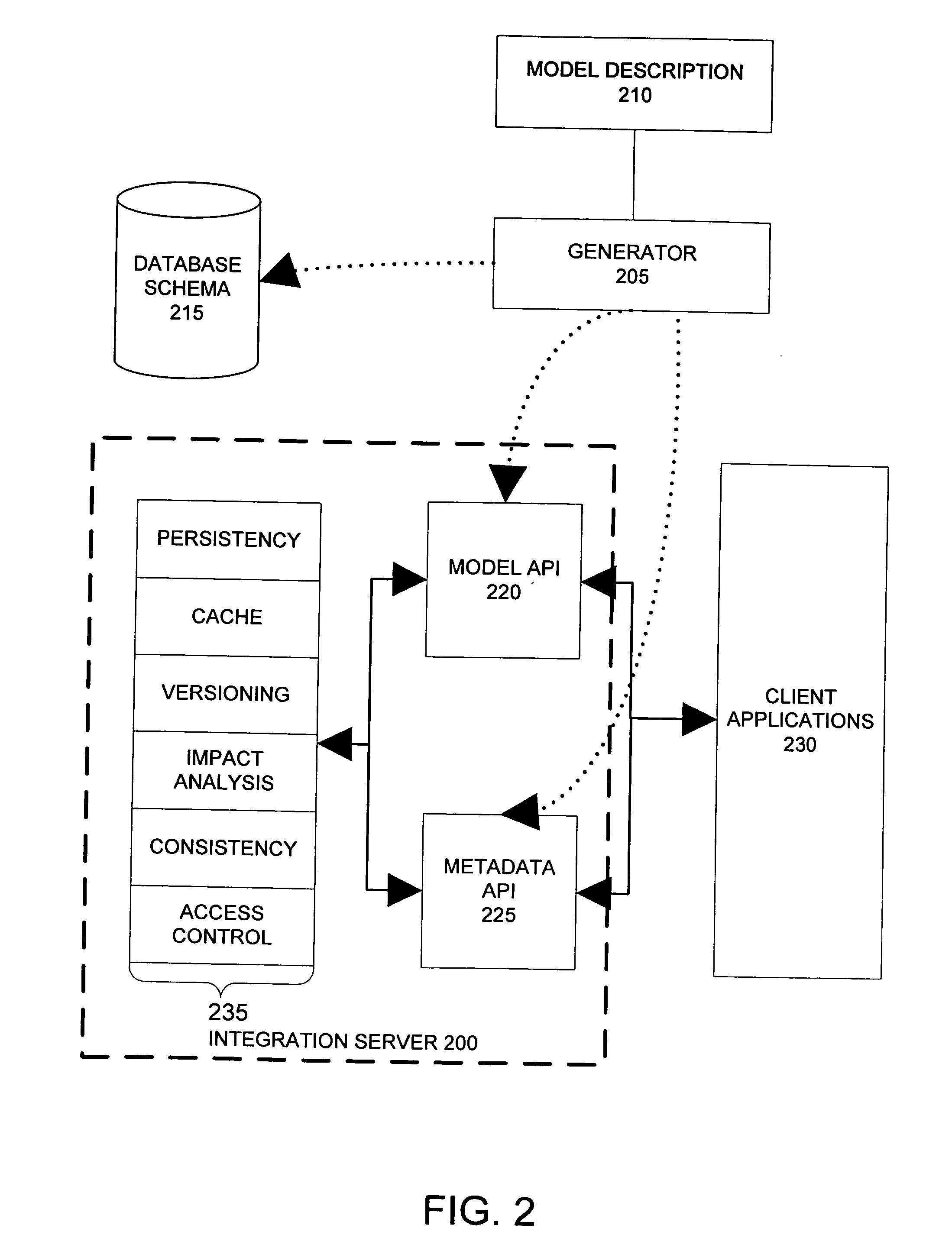
ActiveUS20050097187A1Improve performanceData processing applicationsDigital data information retrievalApplication programming interfaceDatabase schema
An integration server system for mapping data objects on a database schema offers a strongly-typed model API, complex constraint management, and association balancing. The integration server system also has improved performance through optimized handling of ordered associations of data object and of string-valued attributes. The integration server system comprises a database schema configured to store a set of data object instances. A metadata model represents a configuration of the set of data object instances in the database schema. A model application programming interface provides a client application with access to the set of data object instances, and a metadata application programming interface provides a client application with access to the set of data object instances via the metadata model.
Owner:ORACLE INT CORP
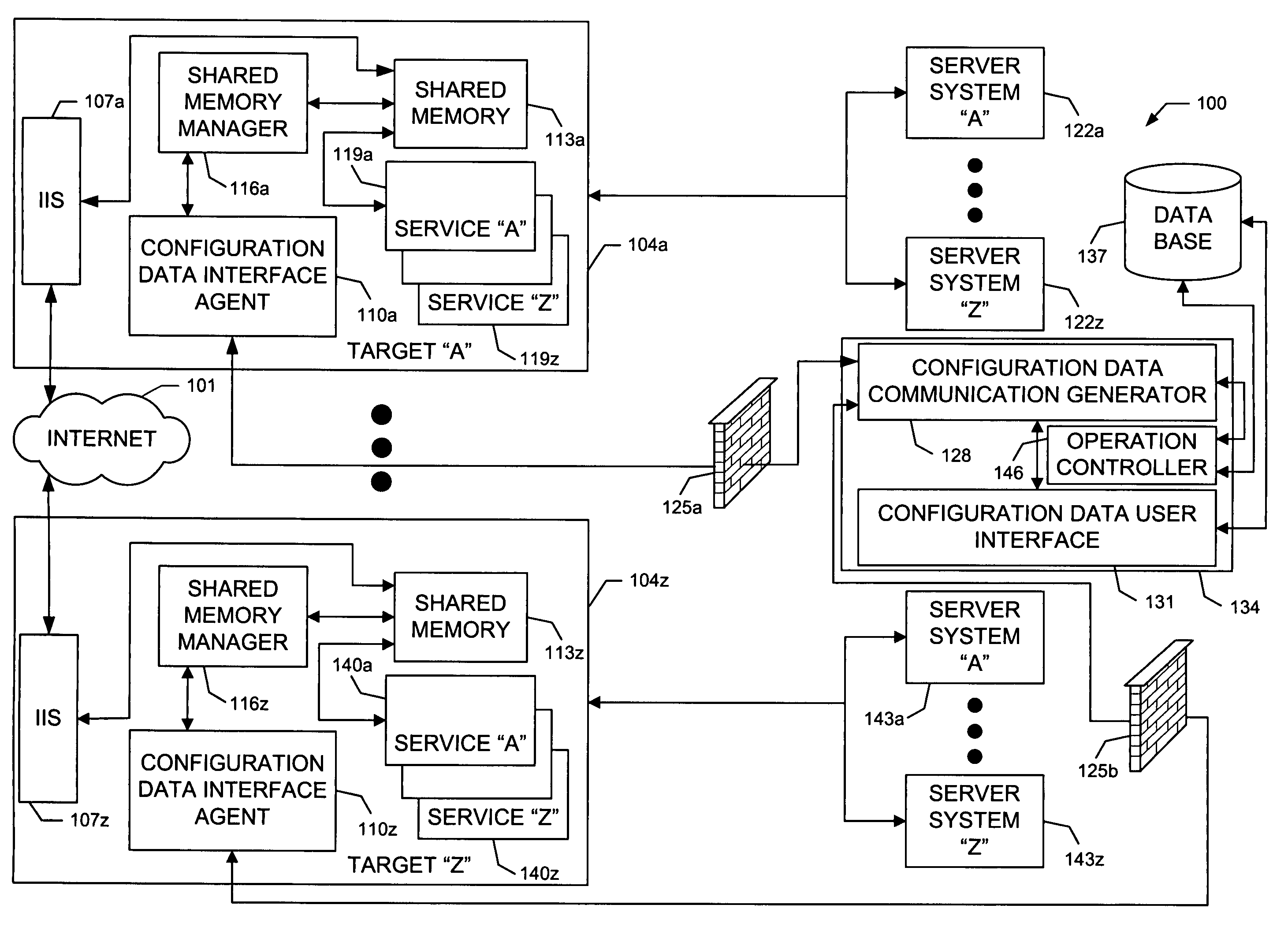
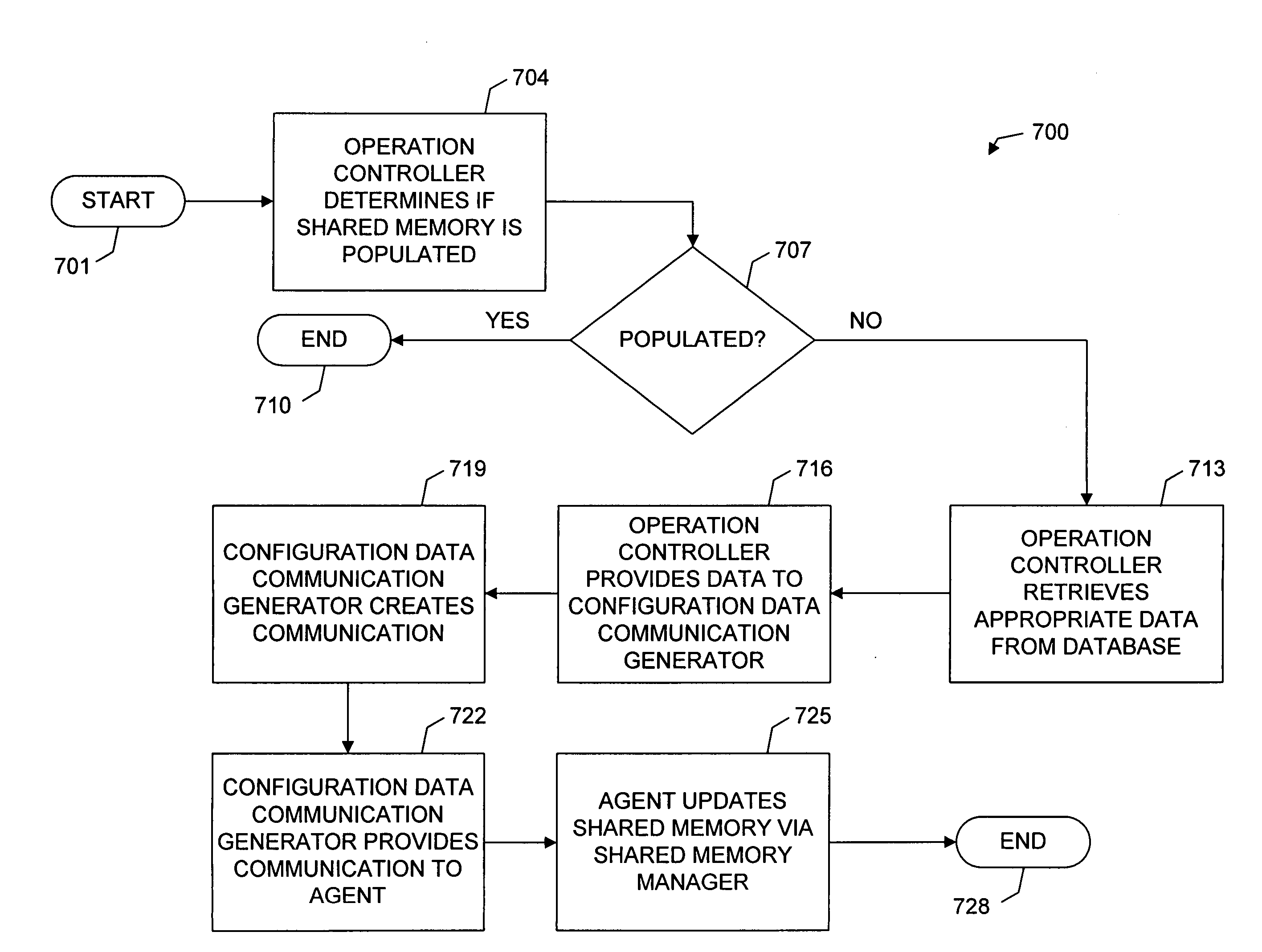
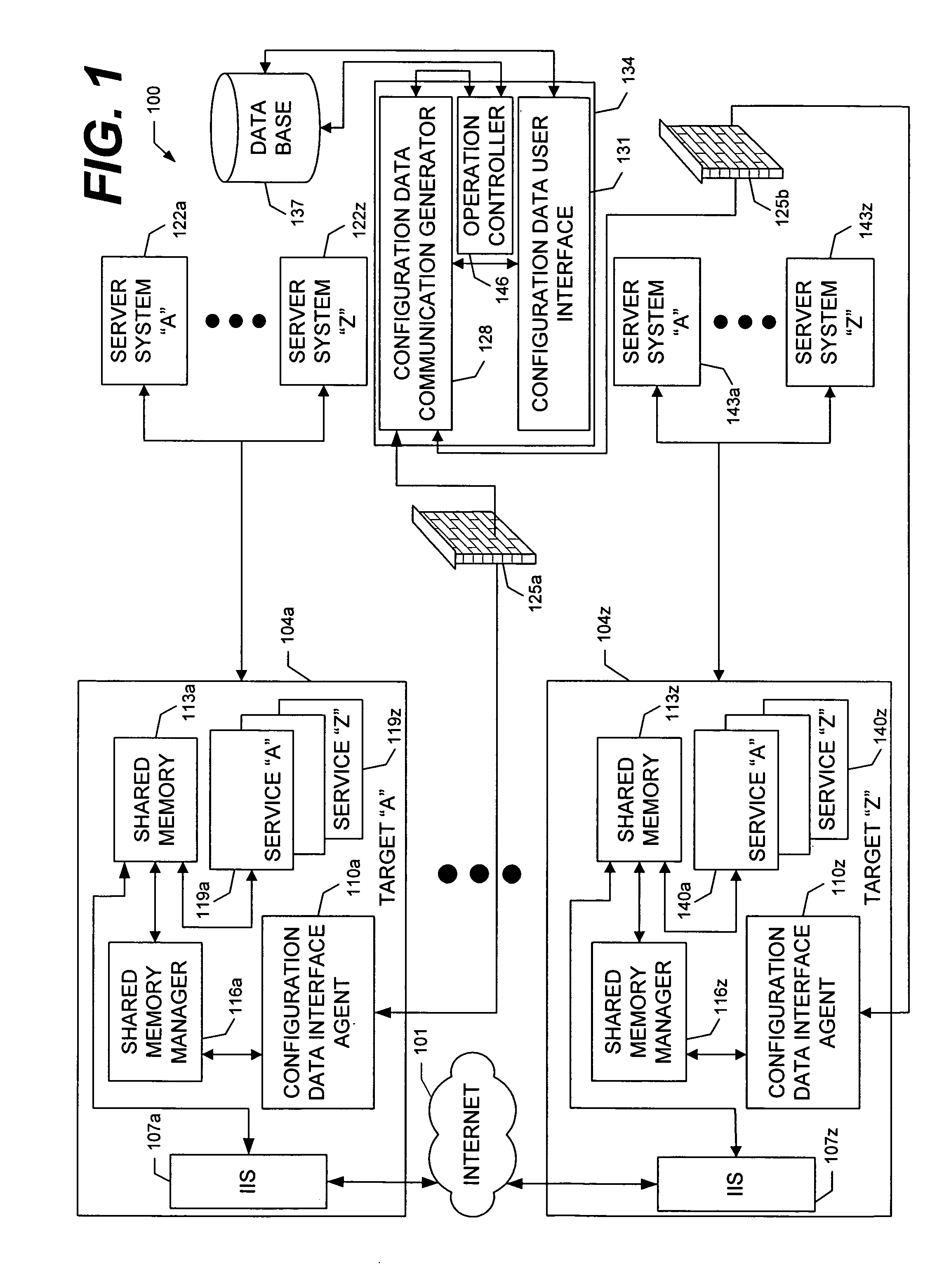
System and methods for sharing configuration information with multiple processes via shared memory
ActiveUS7139894B1Easy to shareImprove integrityData processing applicationsError detection/correctionComputer OperationShared memory
A system and methods for sharing configuration information with multiple services, or processes, via shared memory. The configuration information, typically, comprises runtime information utilized by processes during operation, including without limitation, information describing data communication connections between the local computer and other computing resources (i.e., port and wire information), and information defining numeric values or character string values (i.e., genre and record information). The system architecture includes a plurality of APIs which: reside at the local computer; populate, manage, and control access to a shared memory containing the configuration information; and, are executable only by processes executing at the local computer, thereby limiting access to the shared memory. Access to the configuration information is further limited to only those processes identified as having appropriate permission. The methods enable the configuration information of the shared memory to be modified during local computer operation and without impeding access to the configuration information.
Owner:MICROSOFT TECH LICENSING LLC
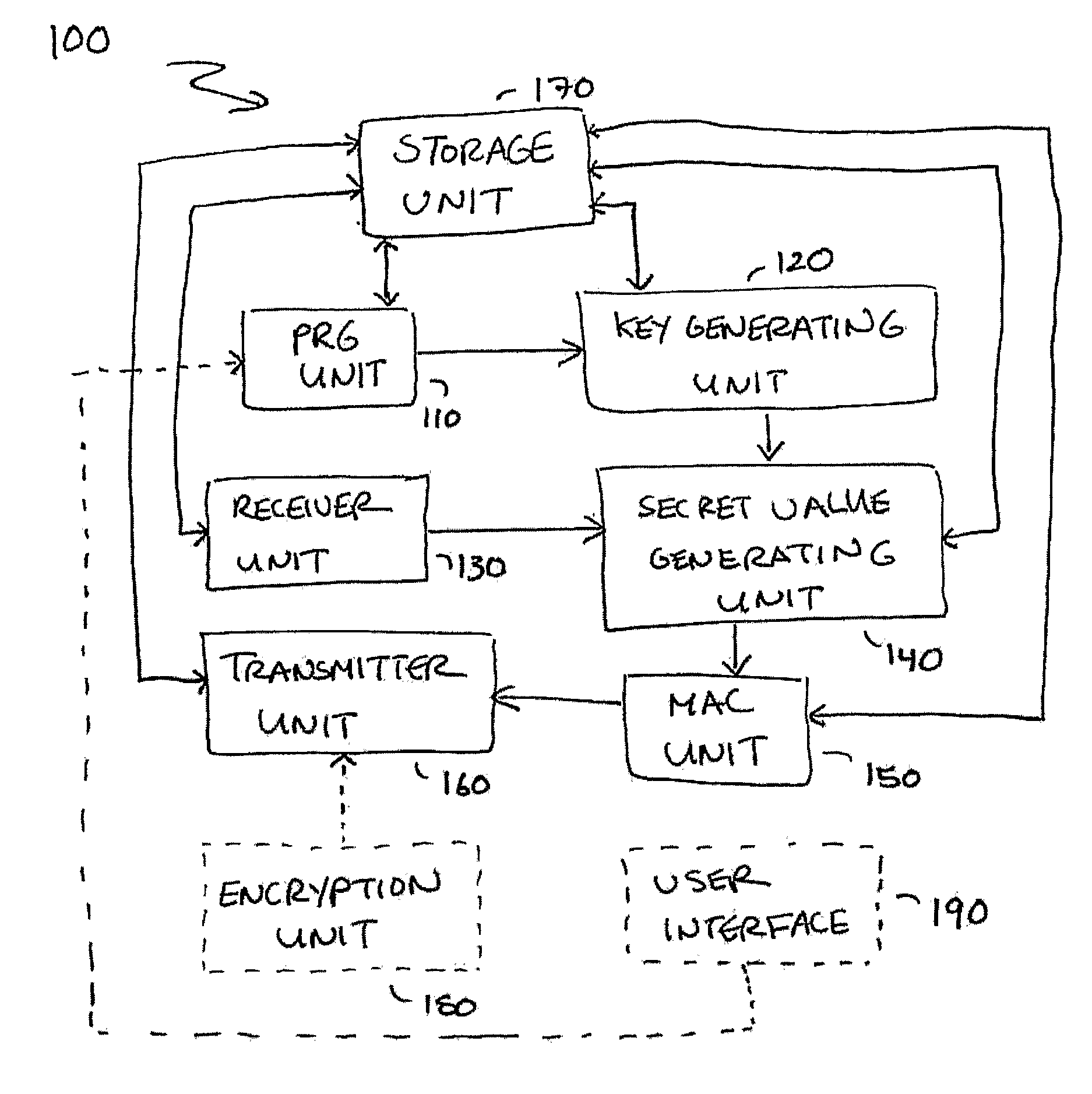
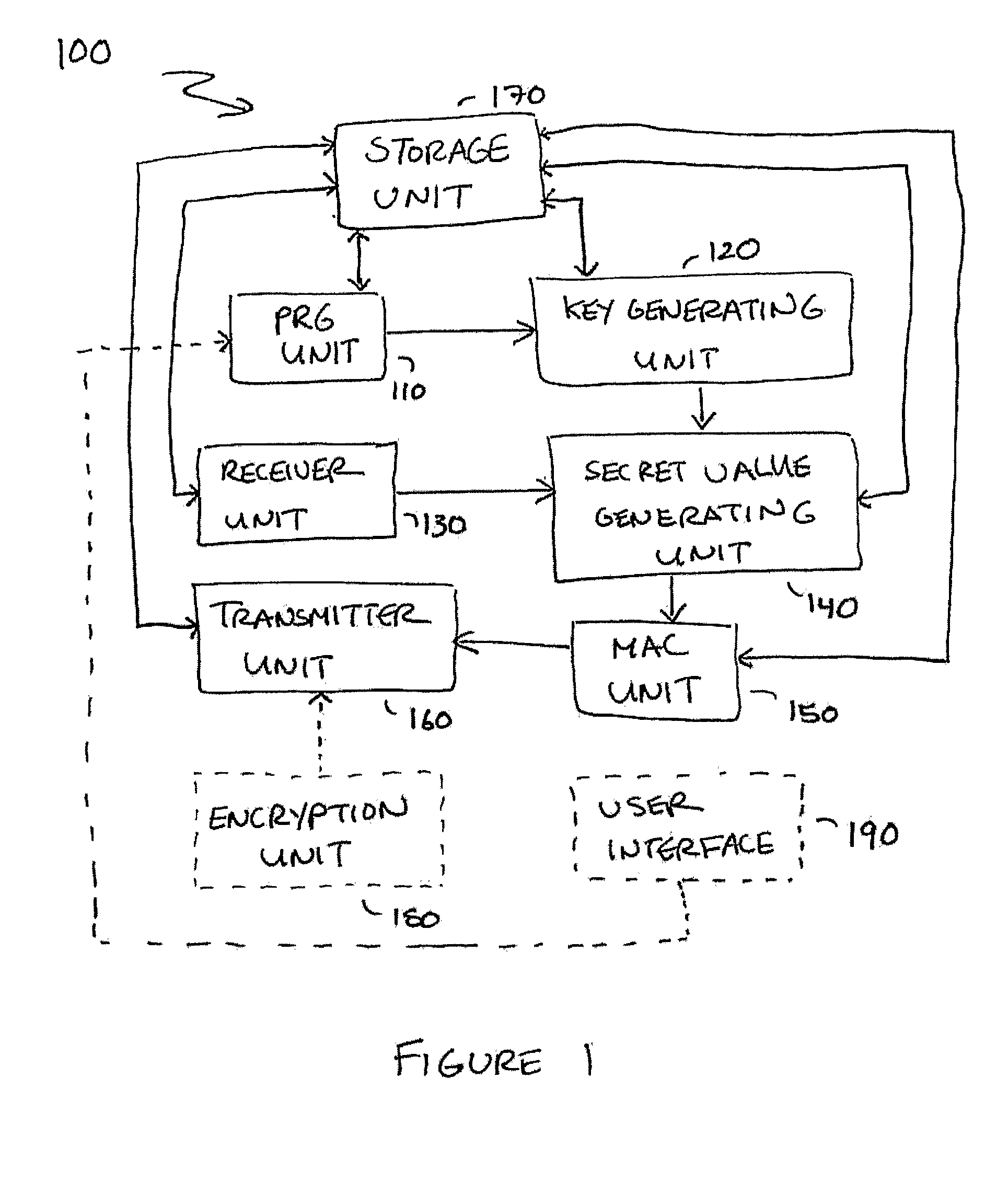
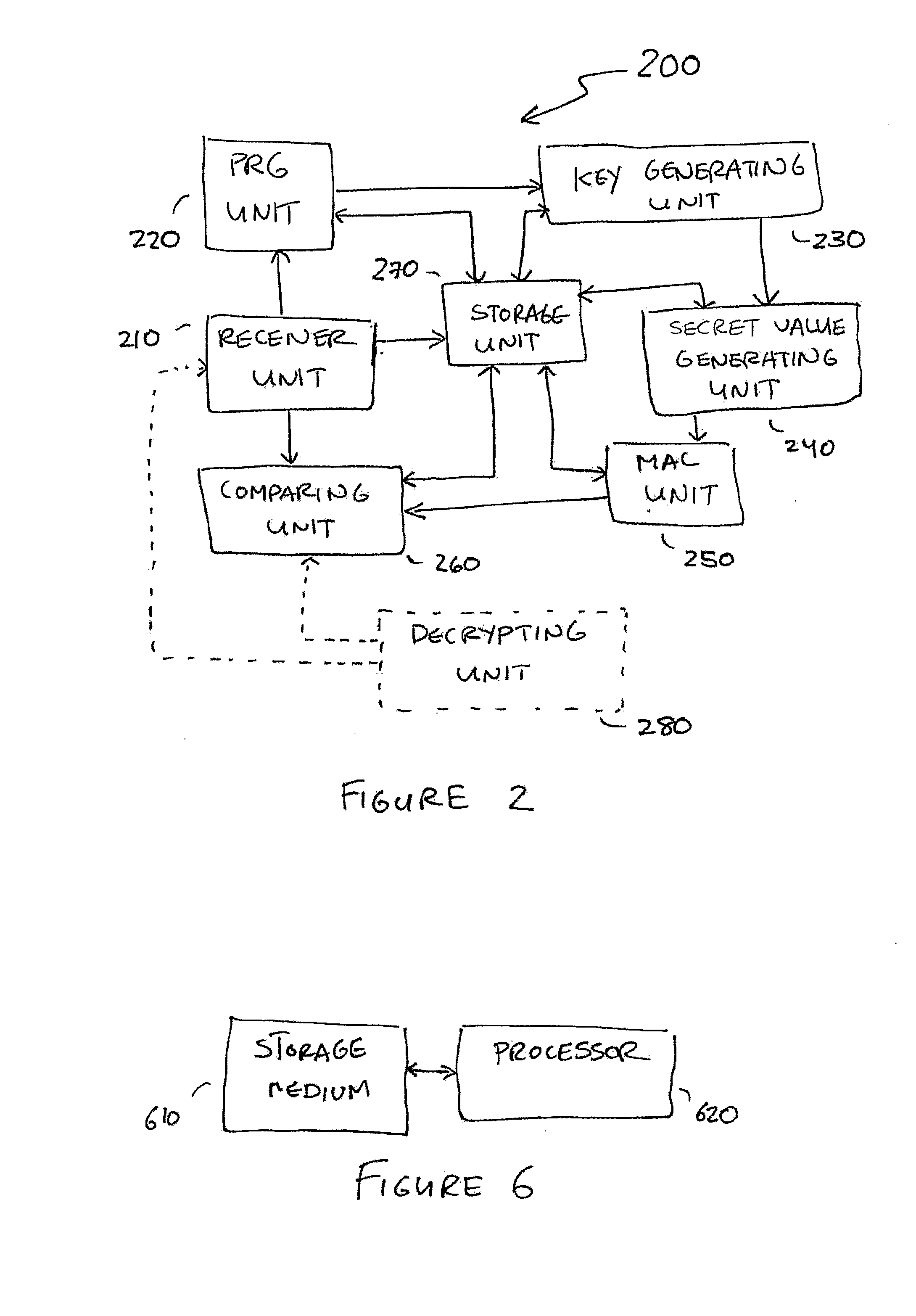
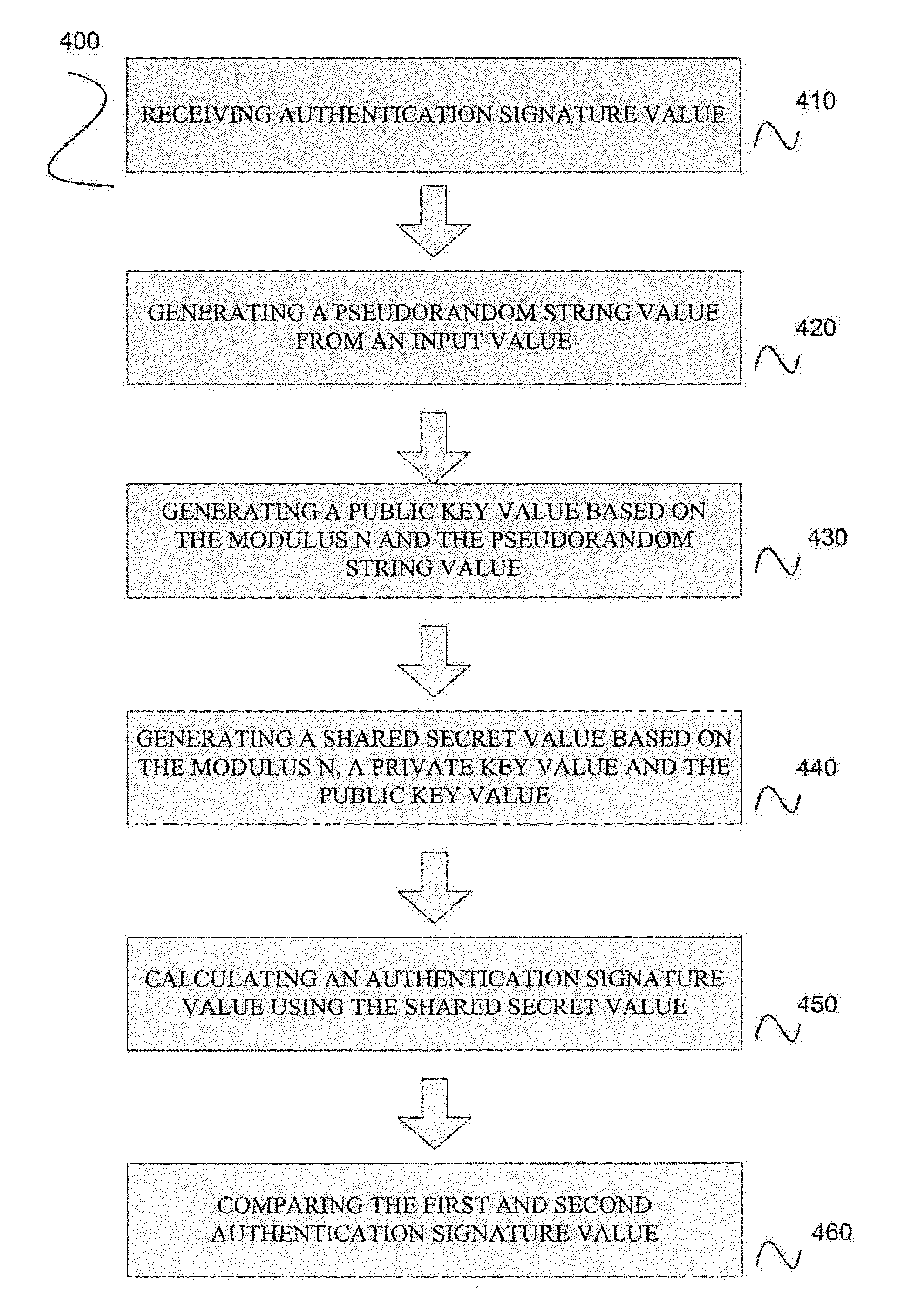
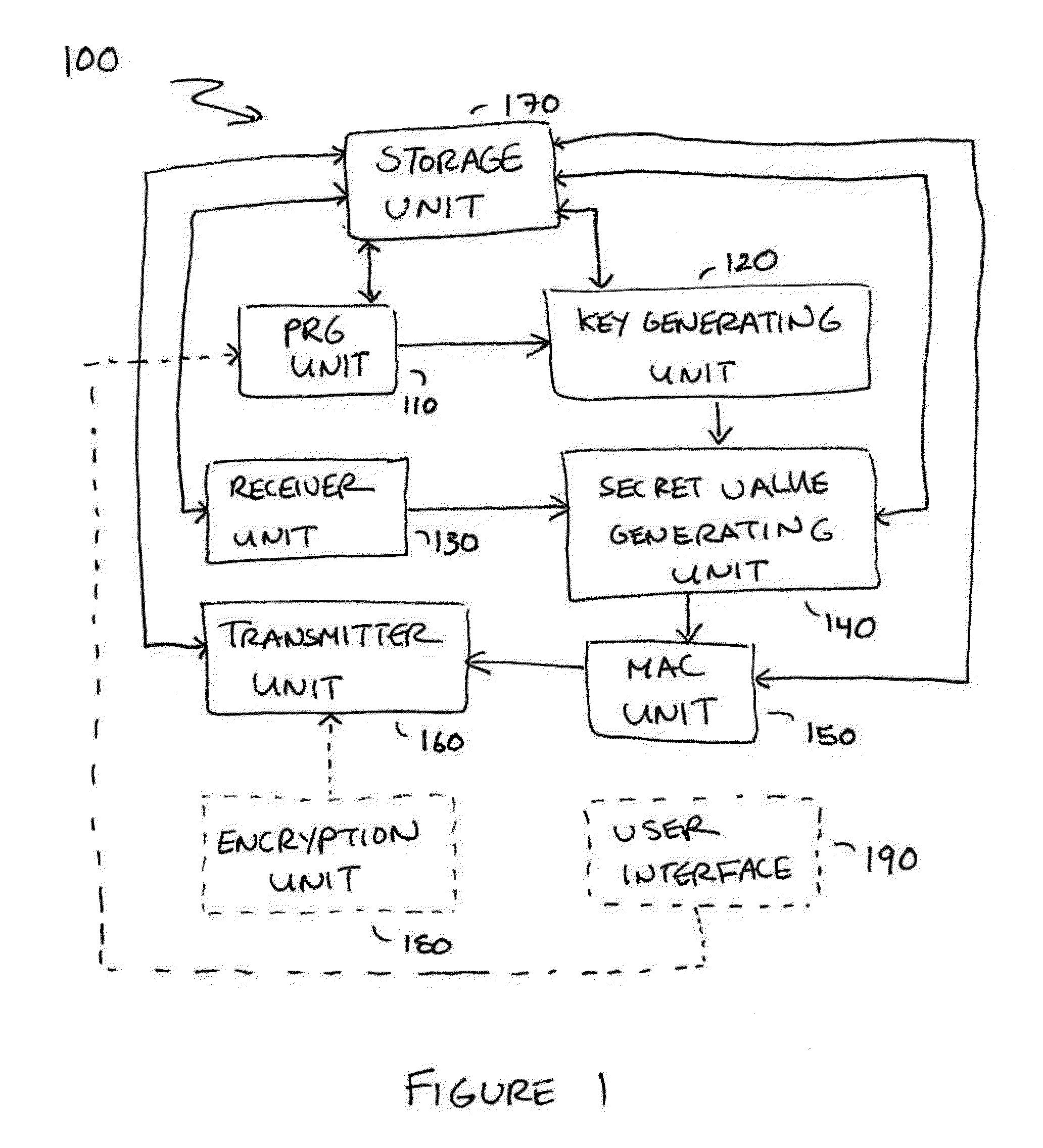
Small Public-Key Based Digital Signatures for Authentication
ActiveUS20090003597A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital signatureString Value
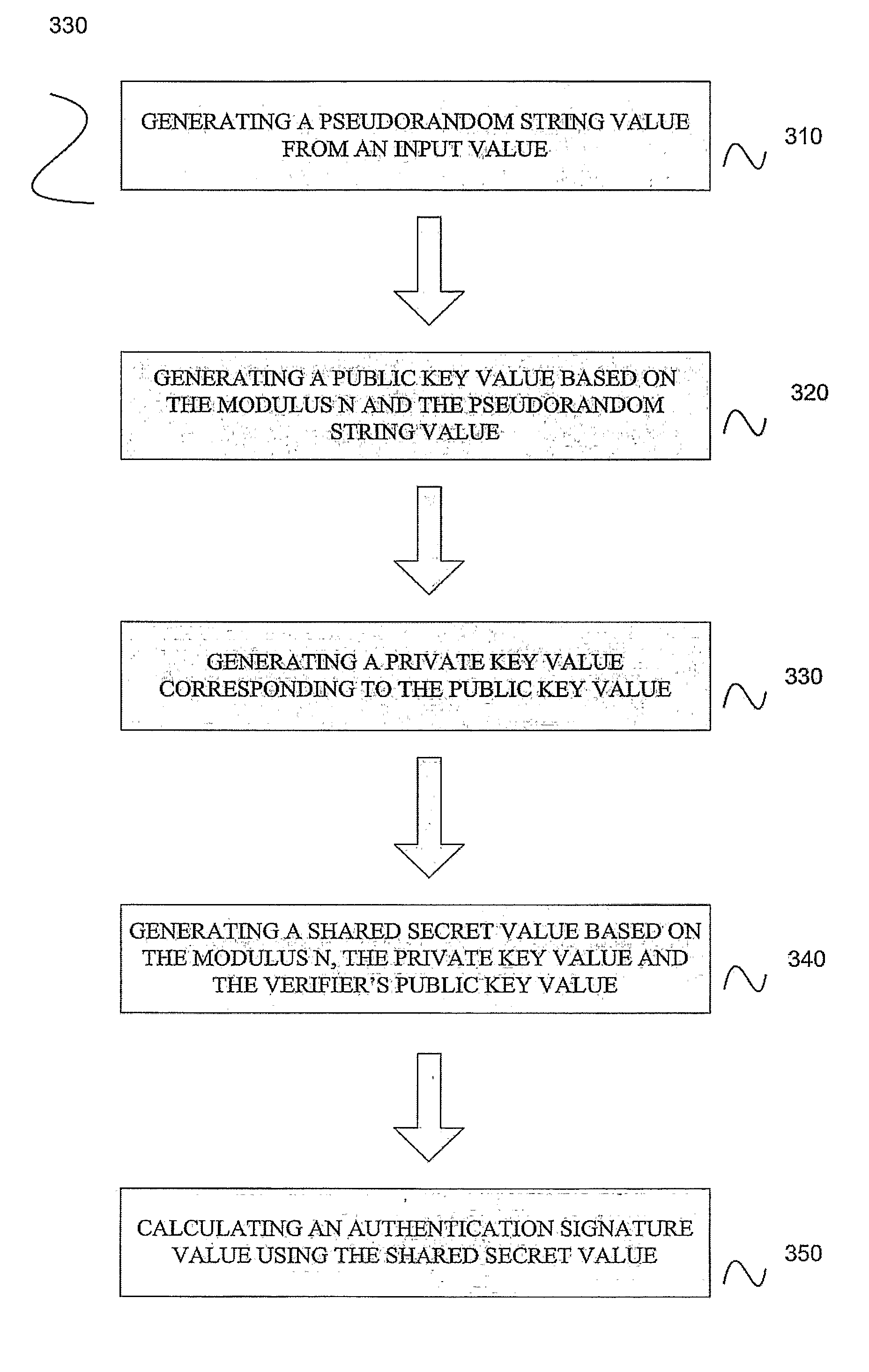
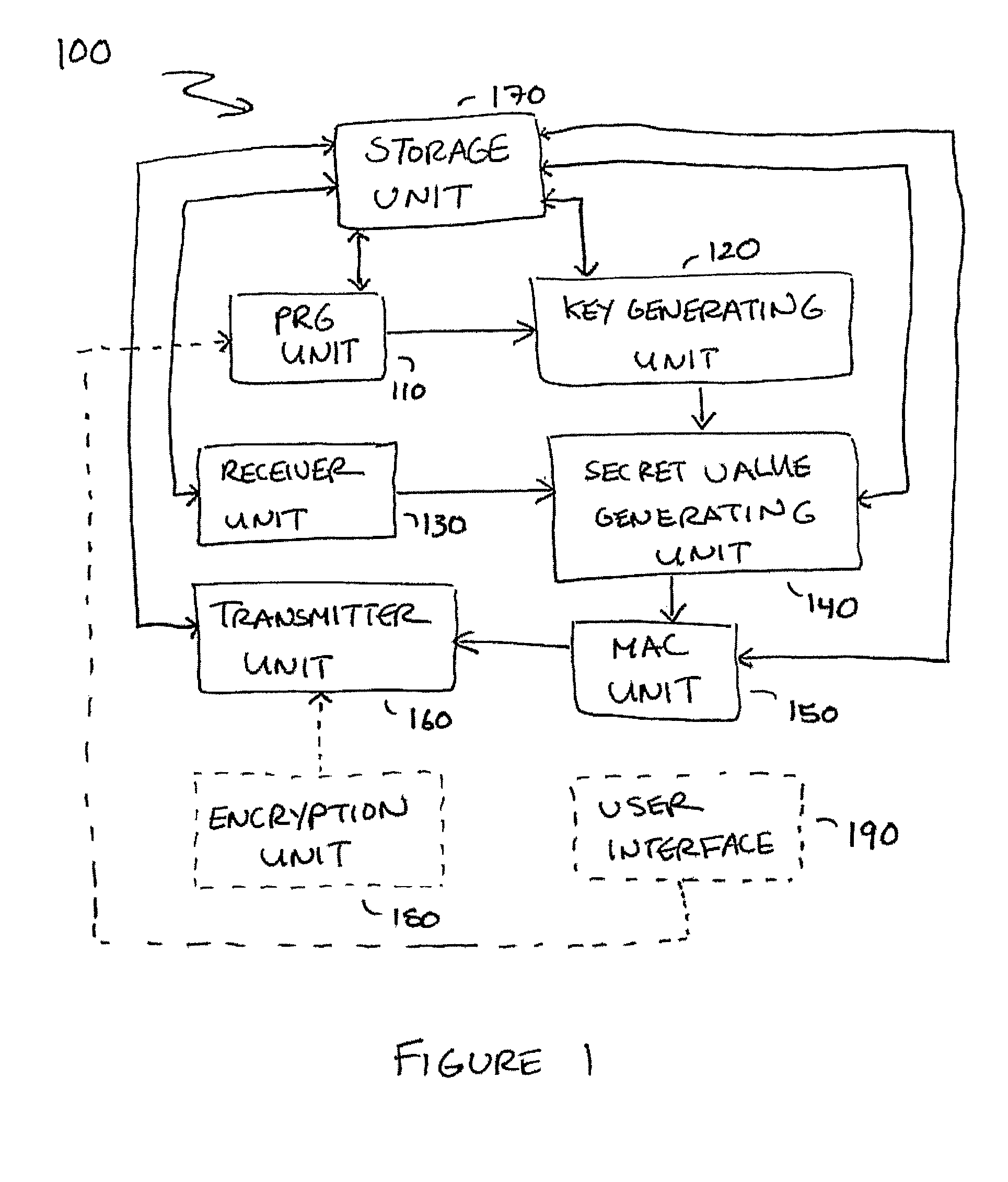
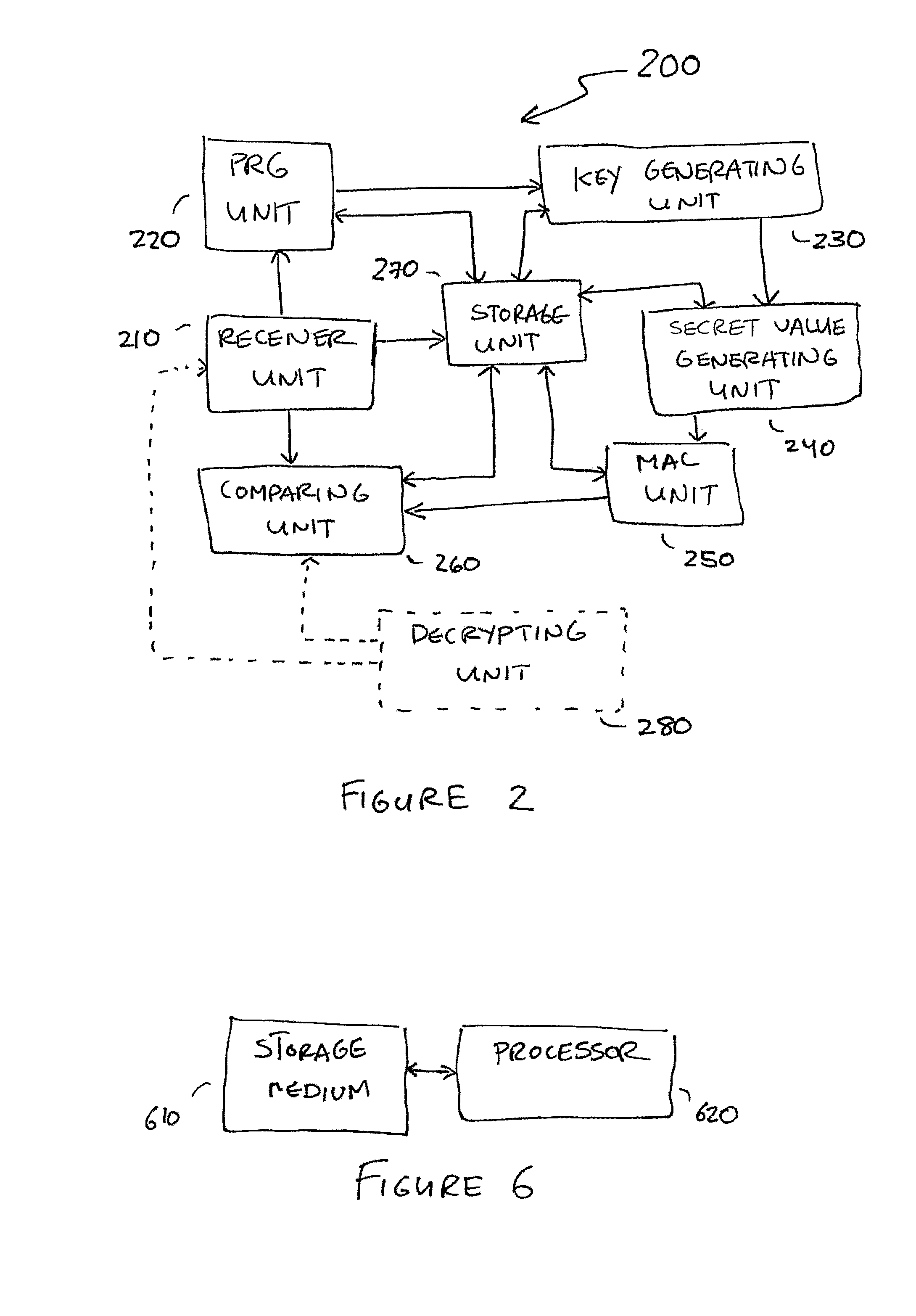
Embodiments disclosed allow authentication between two entities having agreed on the use of a common modulus N. The authentication includes generating a pseudorandom string value; generating a public key value based on the modulus N and the pseudorandom string value; generating a private key value corresponding to the public key value; receiving a verifier's public key value; generating a shared secret value based on the modulus N, the private key value and the verifier's public key value; calculating an authentication signature value using the shared secret value; and transmitting the authentication signature value for authentication. When the authentication signature is received, the public key value and the shared value are generated to calculate an authentication signature value. Thereafter, the authentication signature values are compared and authenticated.
Owner:QUALCOMM INC
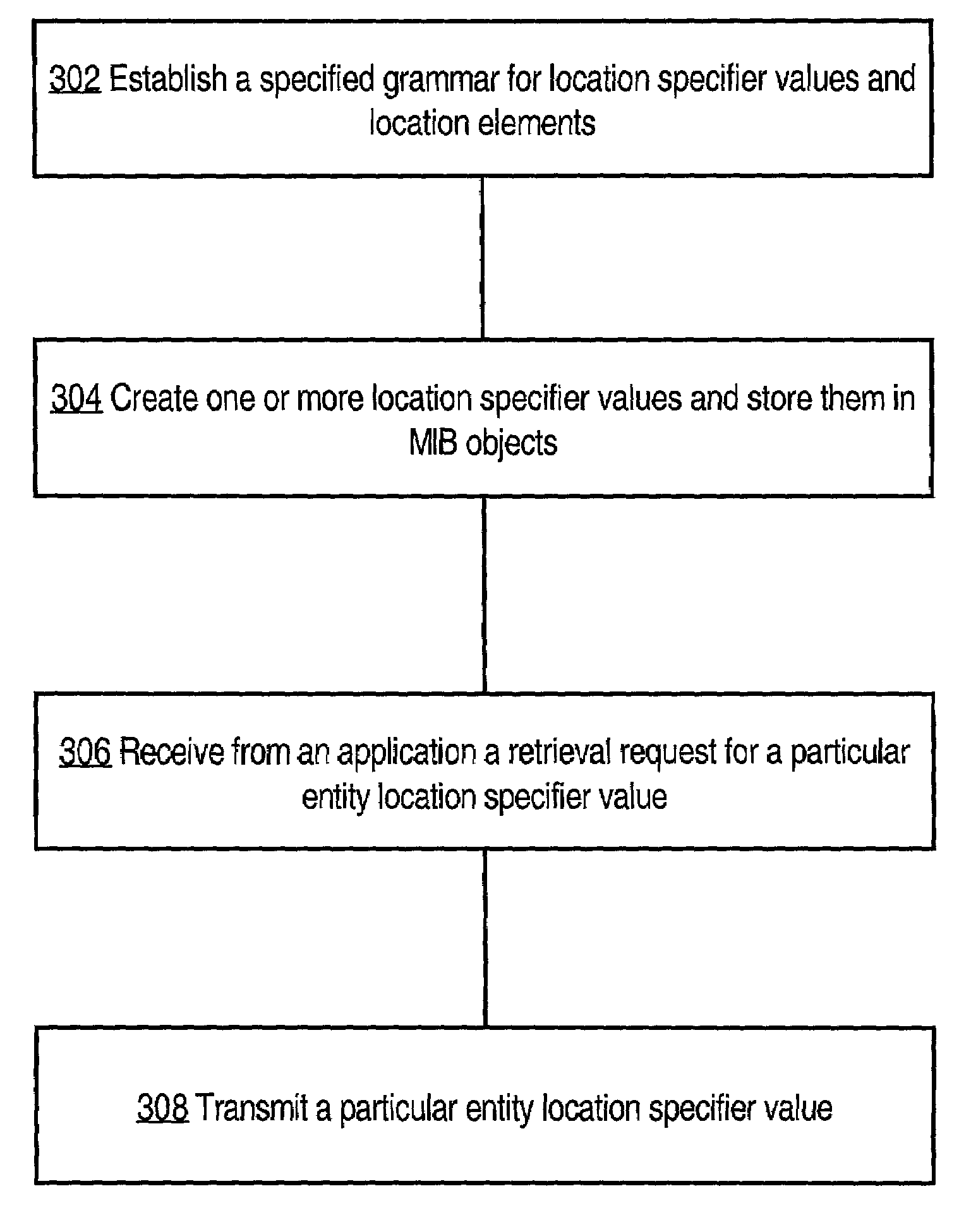
Method and apparatus for managing network devices using a parsable string that conforms to a specified grammar
InactiveUS7054926B1Multiple digital computer combinationsTransmissionAugmented Backus–Naur FormNetwork management application
A method and apparatus are disclosed for managing network devices using a parsable string that conforms to a specified grammar. The parsable string is used to represent locations of entities and is called an entity location specifier. The grammar may conform to Augmented Backus-Naur Form (ABNF). The entity location specifier comprises one or more location elements taken from a superset of location elements needed to specify the locations of entities for network device platforms. The superset of location elements can include both physical and logical entities. As a result, a network management application can retrieve a description of entities and elements contained in a network device using a single request, and can receive a single string value that is parsable to identify individual entities or elements in the device.
Owner:CISCO TECH INC
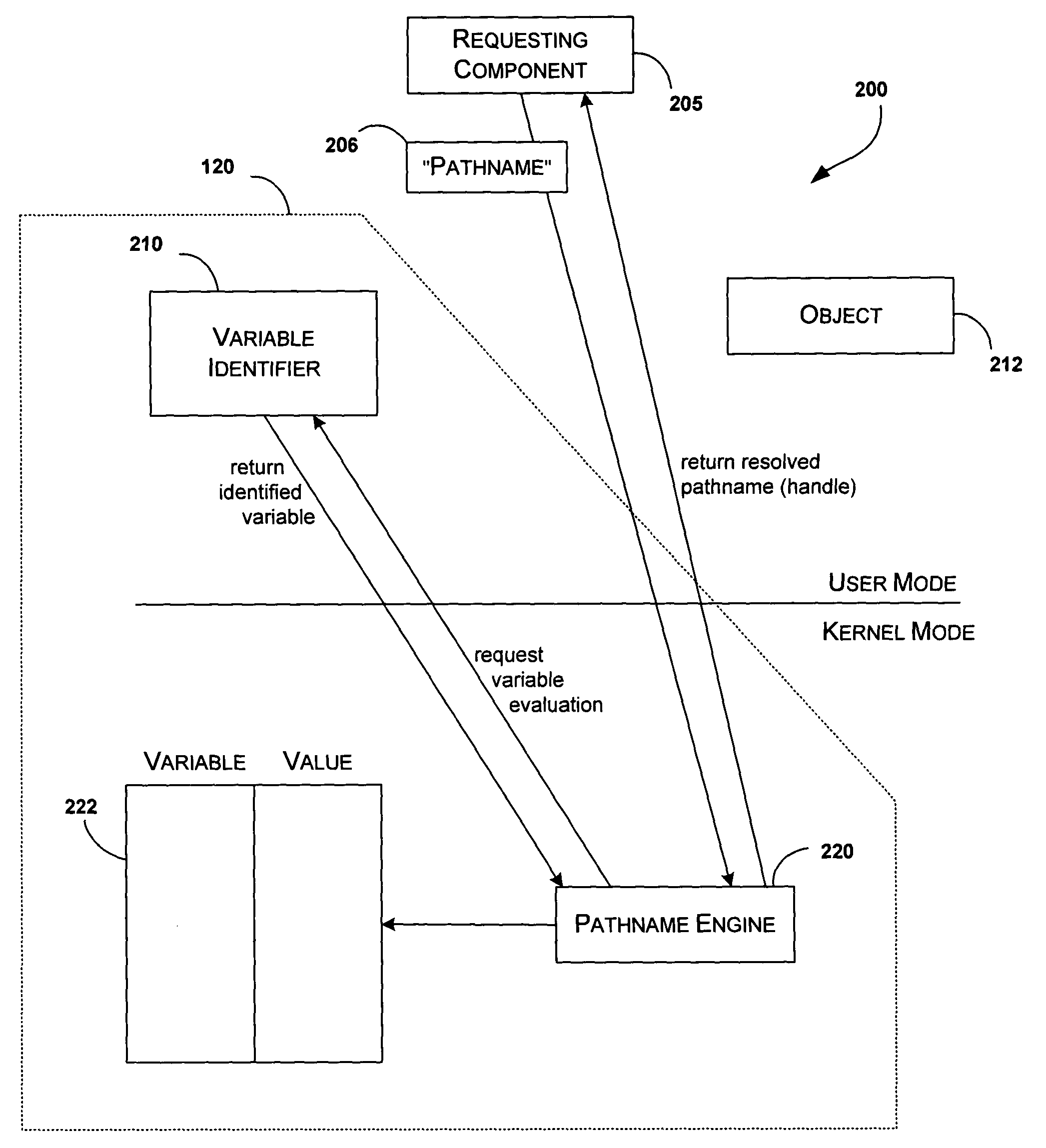
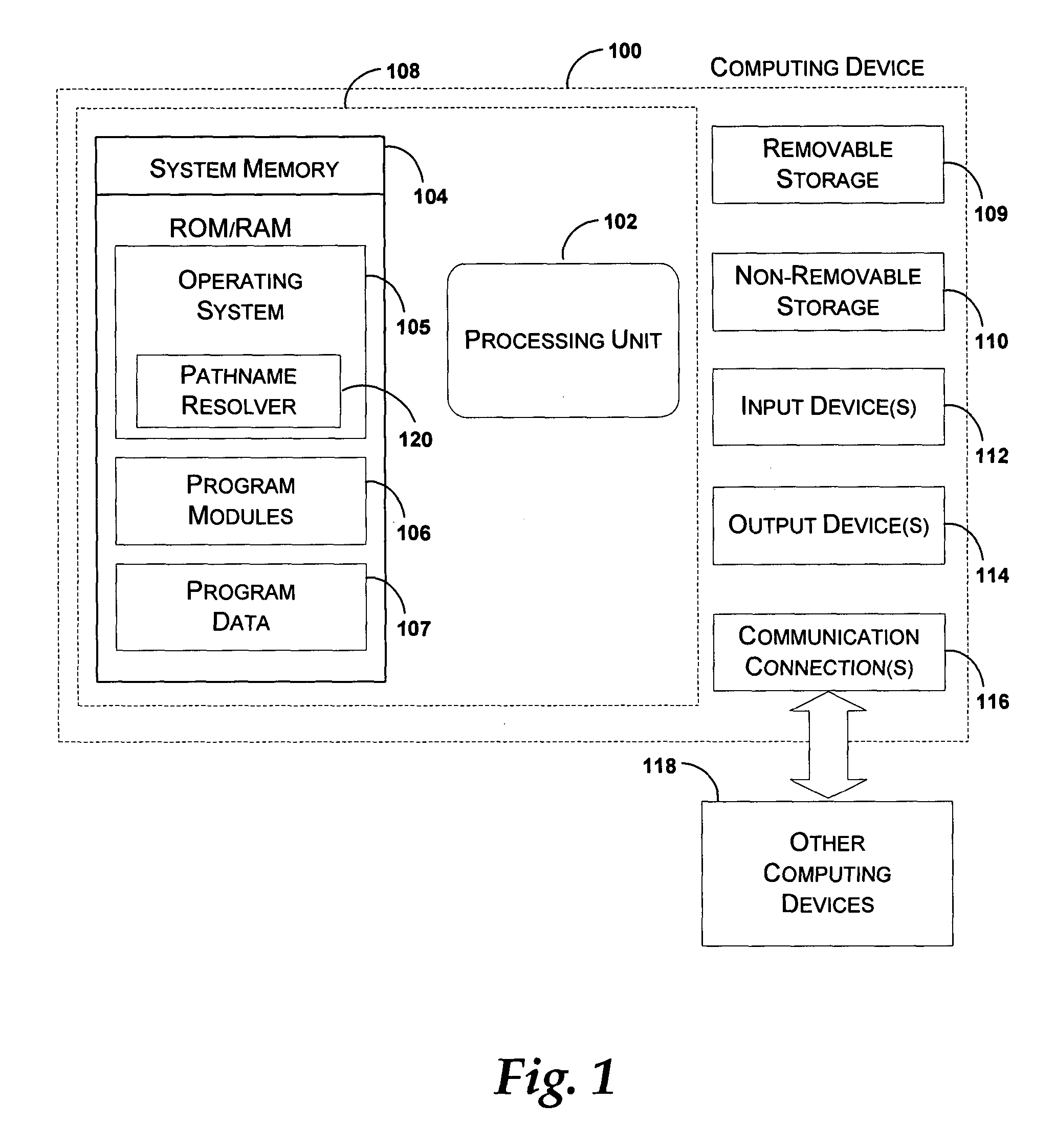
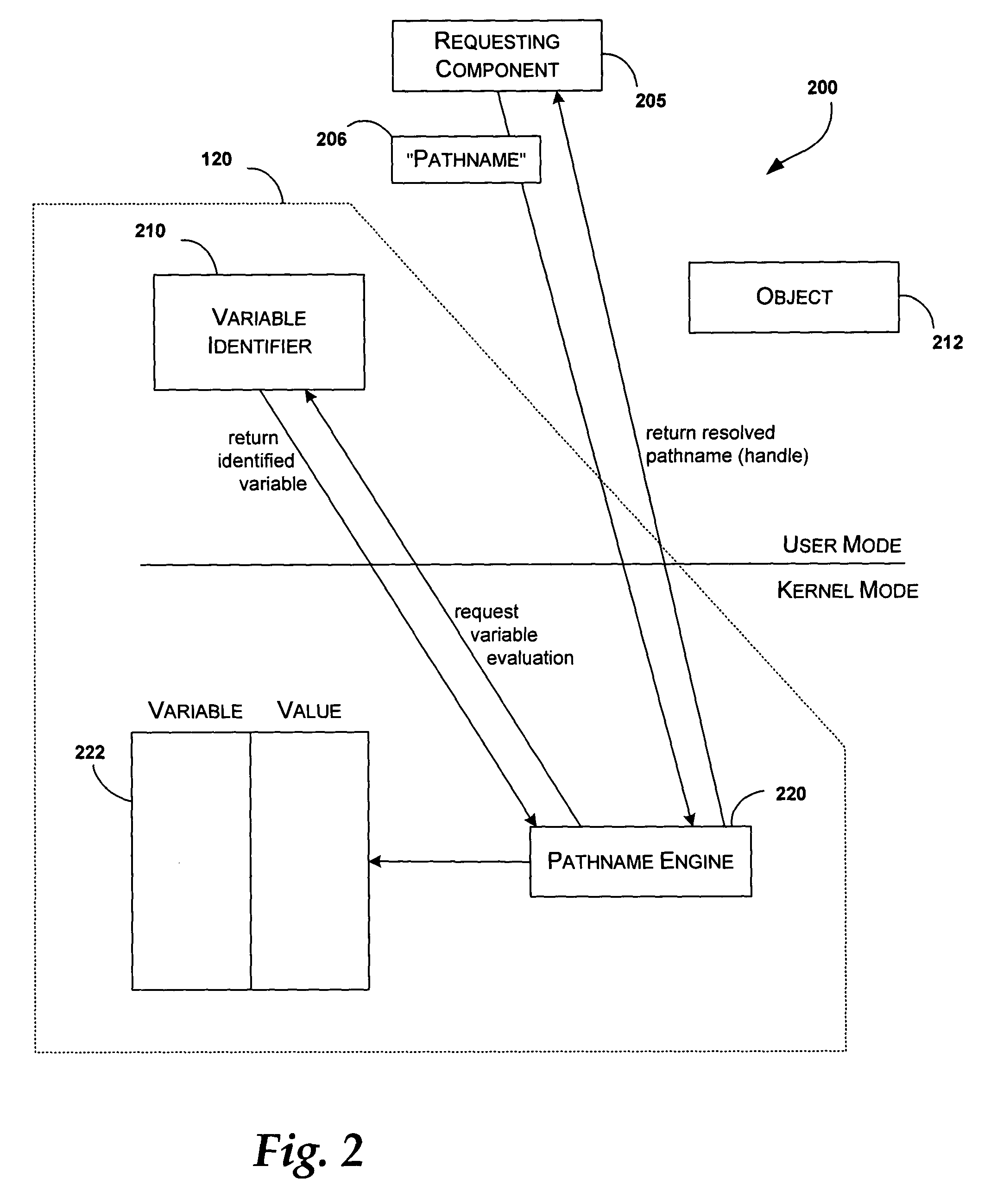
Method and apparatus for late-binding/dynamic pathname resolution
InactiveUS20050044075A1Digital data processing detailsSpecial data processing applicationsTheoretical computer scienceLate binding
Late-binding / dynamic pathname resolution can be performed by a variable identifier operating in user or kernel mode, and a pathname engine and a data structure operating in kernel mode. The variable identifier identifies a variable in a pathname. The pathname engine evaluates the variable by converting the variable into a character string such that a path to an object file is established. The pathname engine determines a scope of potential character string values for the variable by mapping the variable to corresponding values stored in the data structure. Each variable has a well-defined scope of values because the only values available are the values selected for storage in the data structure. The mechanism for establishing values is extensible such that variable / value pairs can be implemented in the data structure at any time.
Owner:MICROSOFT TECH LICENSING LLC
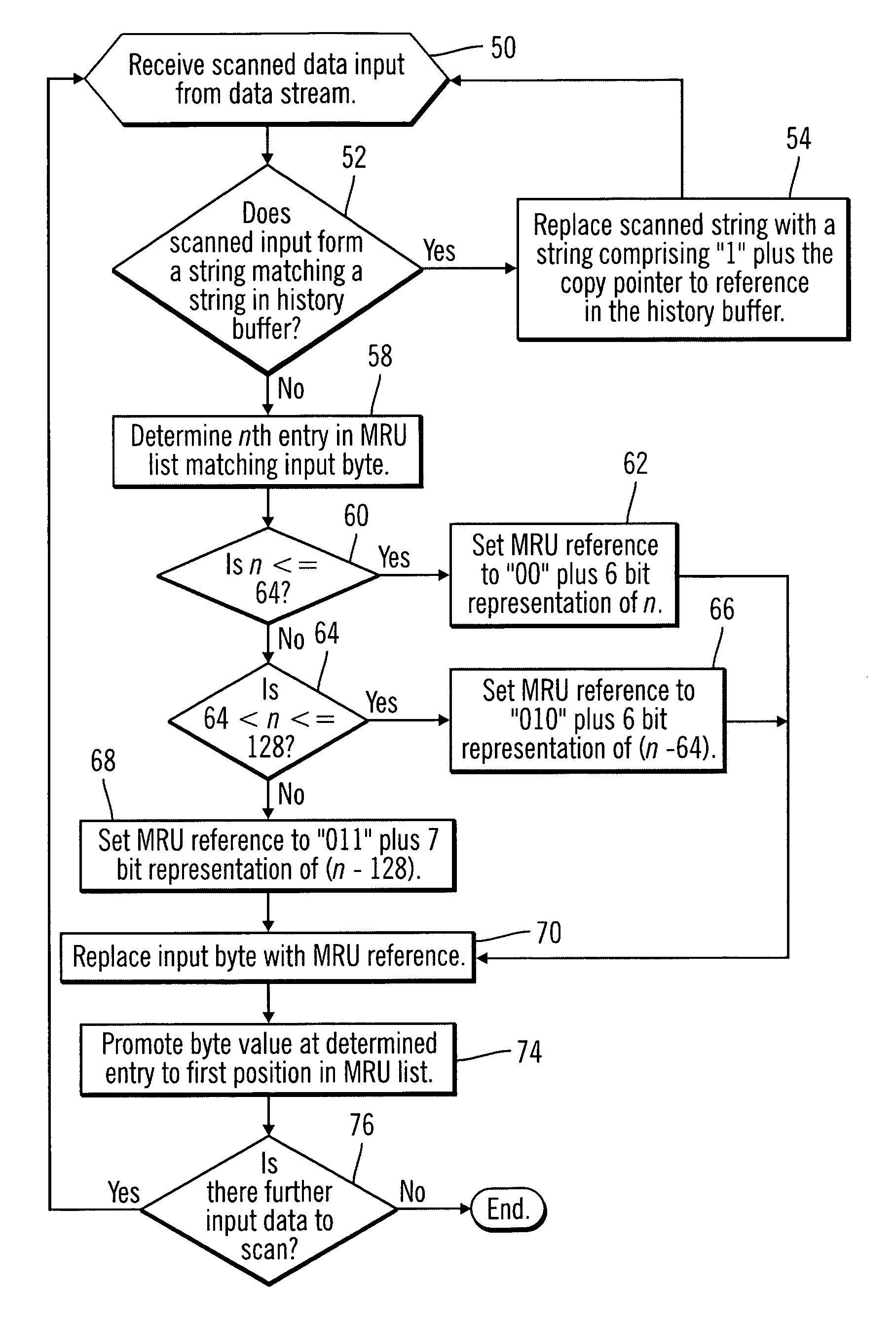
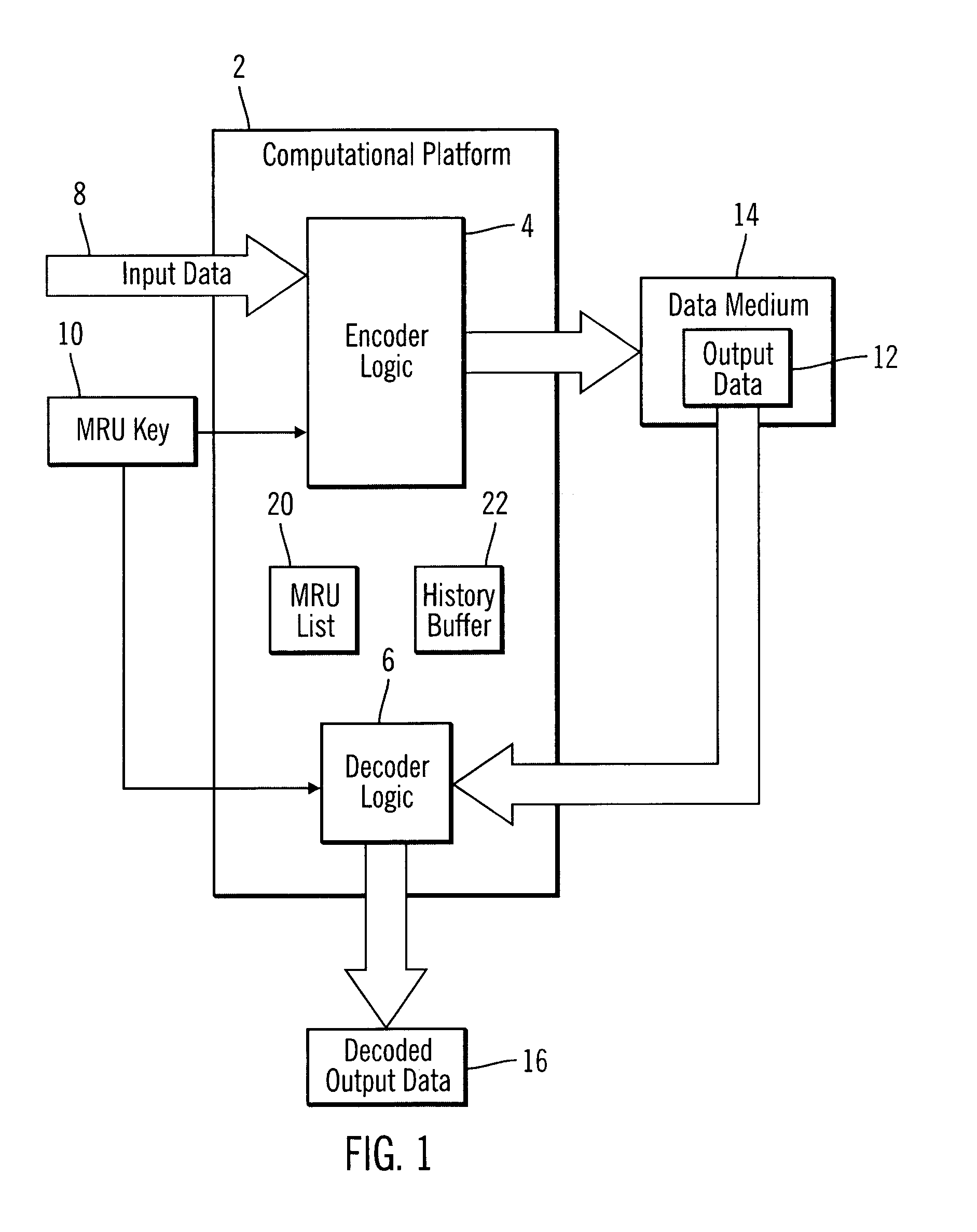
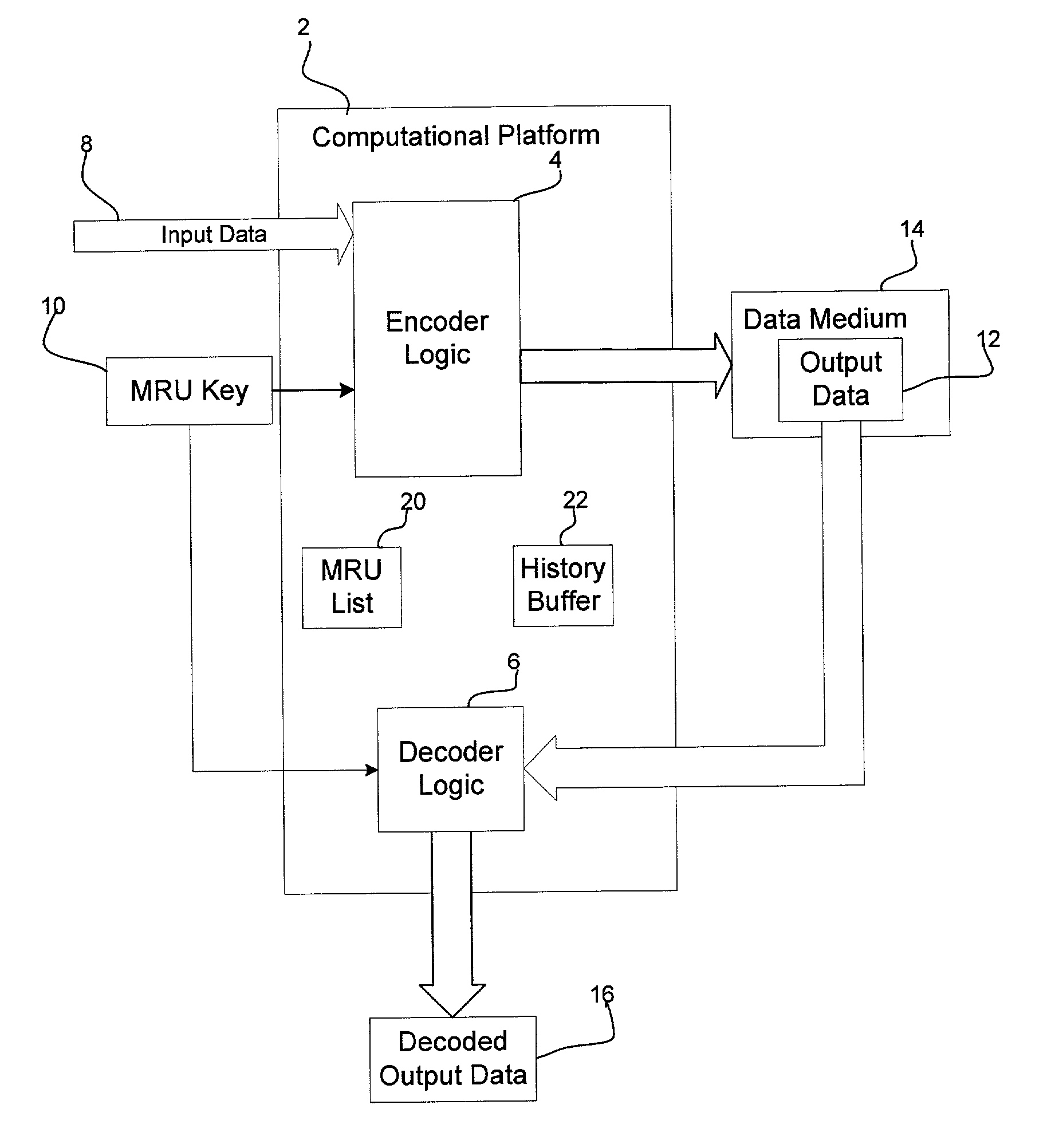
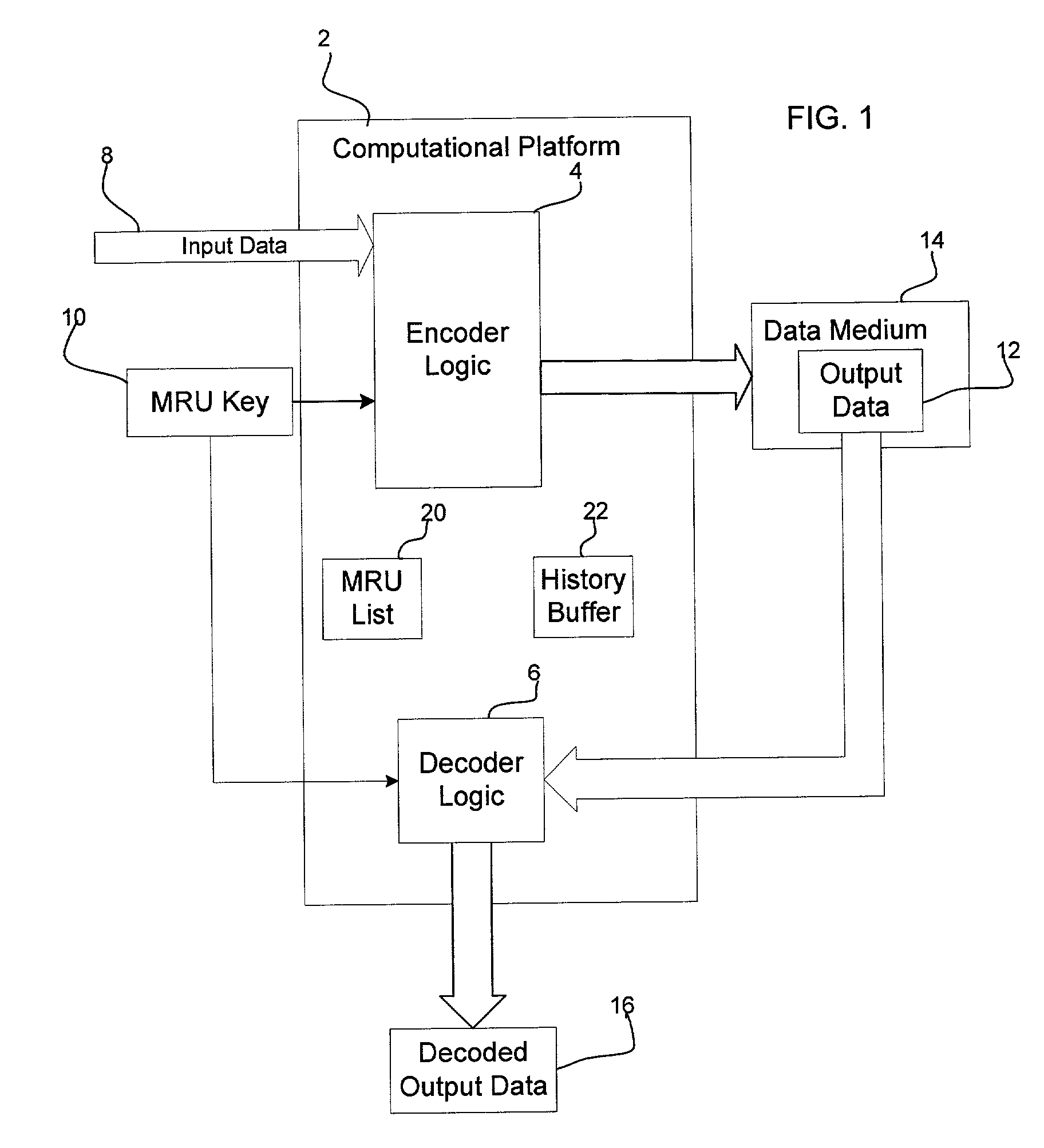
Method, system, and program, for encoding and decoding input data
ActiveUS7003111B2Computer security arrangementsSpecial data processing applicationsUser inputTheoretical computer science
Provided is a method, system, and program for encoding and decoding input data. A key is generated comprising a list of a plurality of binary values, wherein the key is available to a user during decoding. The input data is encoded by using the key to initialize a replacement list. A determination is made whether to replace strings in the input data with a string reference to a matching string value, wherein the input data not replaced with reference to one matching string value comprises one or more literals. Each literal is replaced with a literal reference to one entry in the replacement list matching the literal. The encoded input data is decoded by accessing the generated key in response to user input and using the accessed key to decode the literals replaced with literal references to entries in the replacement list.
Owner:TWITTER INC
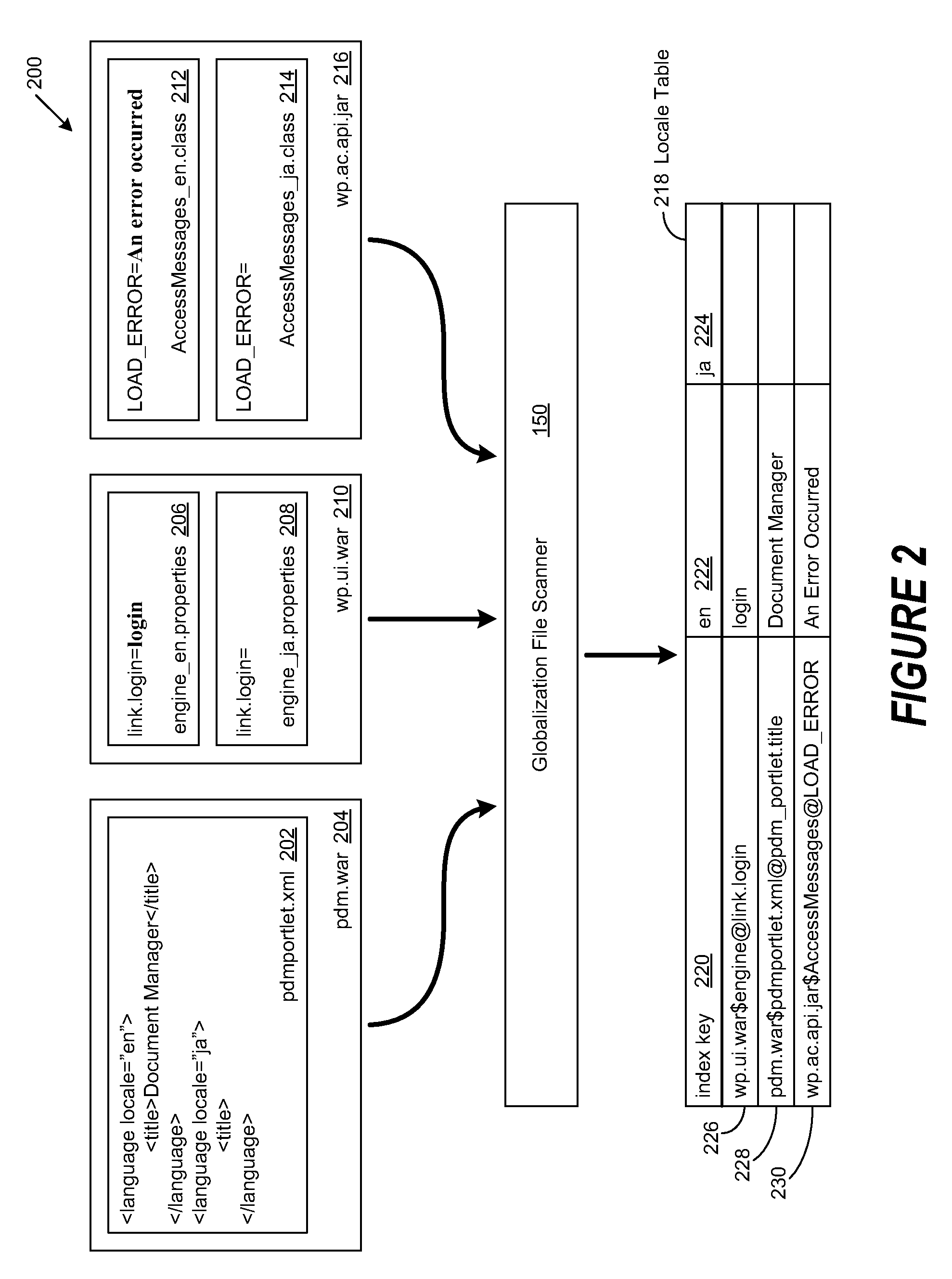
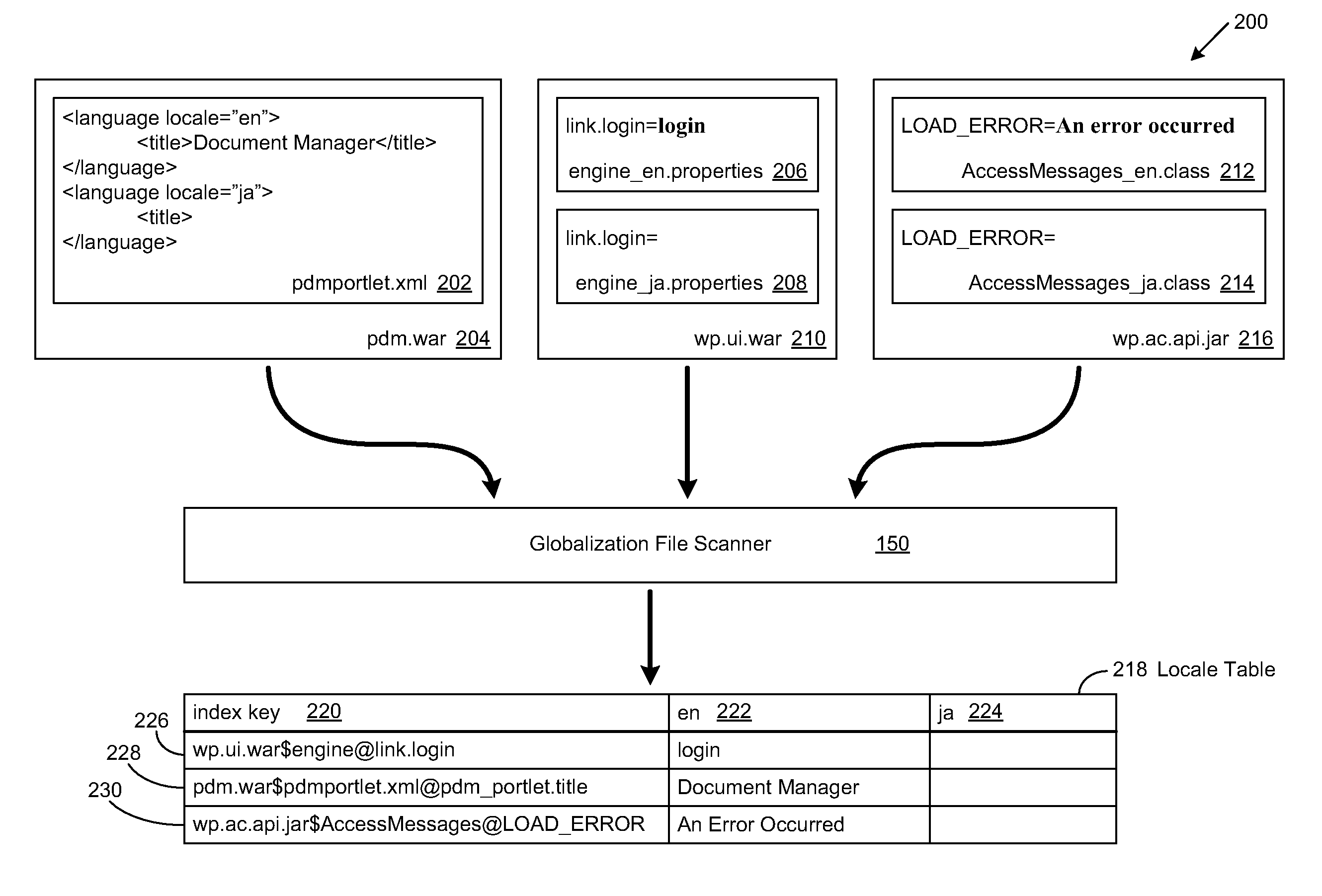
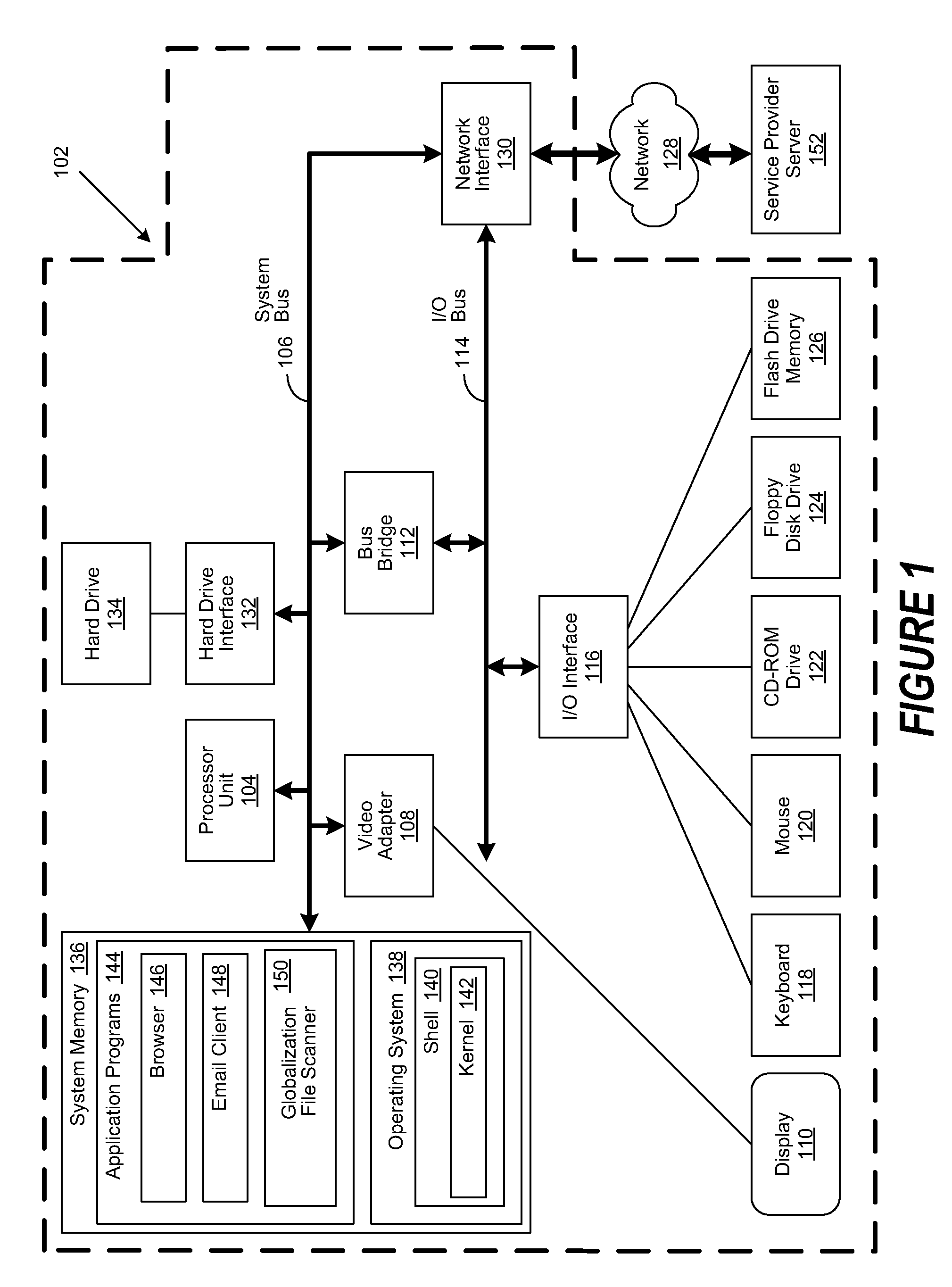
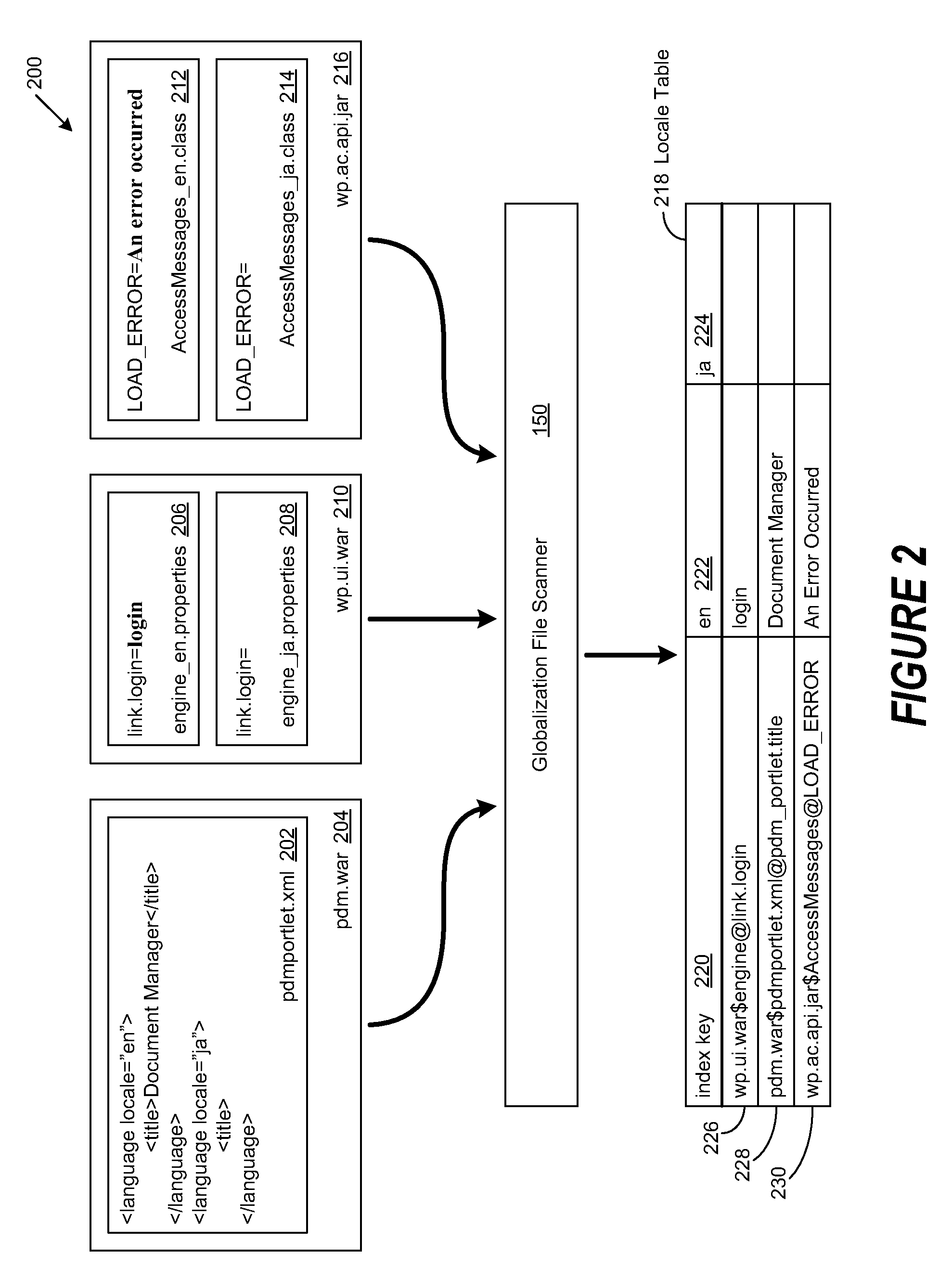
System and method to facilitate automatic globalization verification test
A method, system and program are disclosed for validating the generation of globalized versions of software programs. The directory structure of an installed software program is traversed to discover resource files containing globalized strings. The values of the globalized string and its corresponding key in the resource file are then used to generate a unique key, formatted to identify the location of the globalized string. The locale supported by the globalized string is determined and the unique key and the globalized string value are appended to a corresponding locale table. A globalized string value that causes the failure of a globalization test for a predetermined locale is identified. The corresponding locale table is then searched for the failed globalized string value. Once found, the unique key for the failed globalized string value is retrieved to identify the location of the defective globalized string and perform predetermined remedial actions.
Owner:LINKEDIN
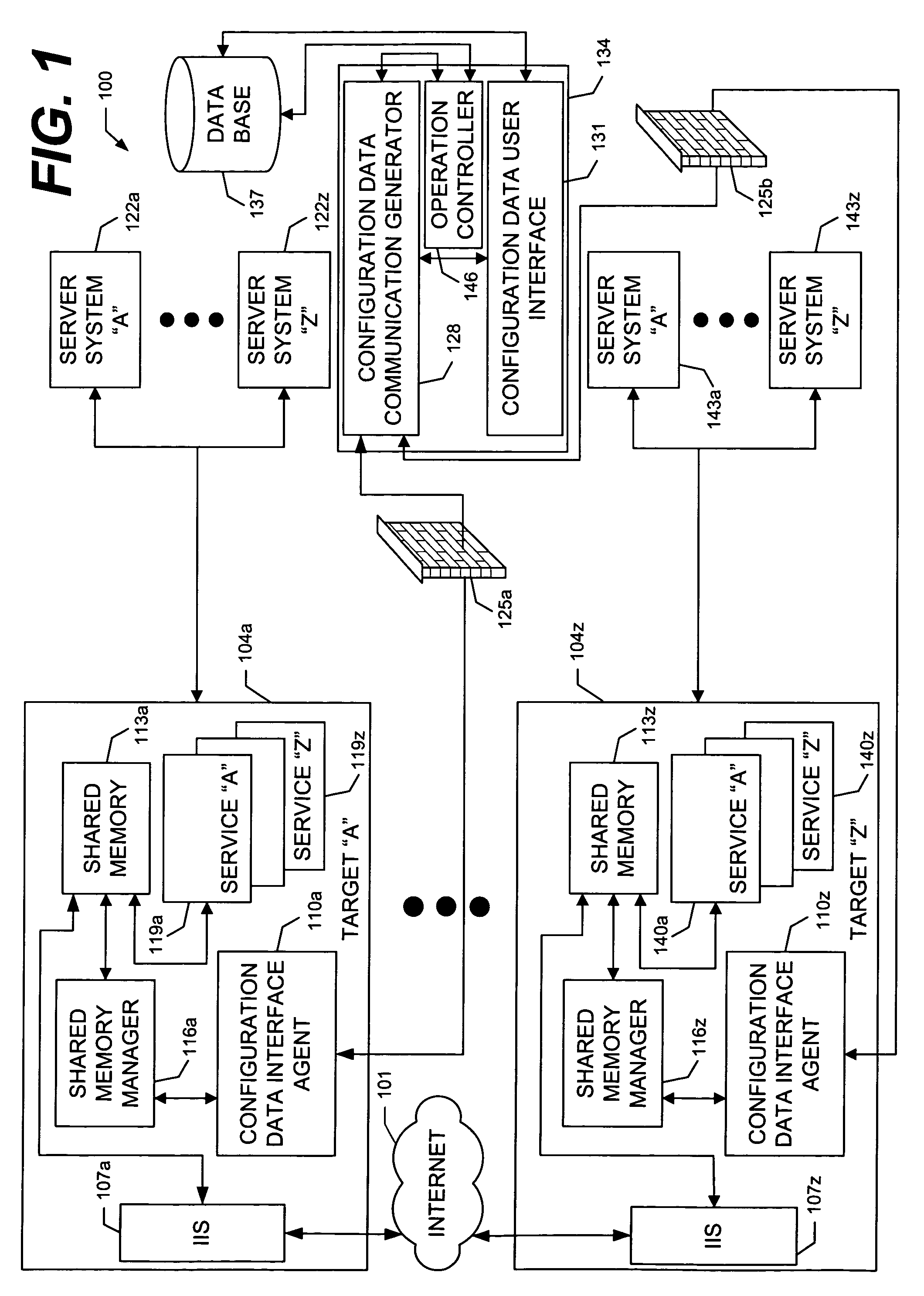
System and methods for sharing configuration information with multiple processes via shared memory
InactiveUS20070118700A1Easy to shareImprove integrityData processing applicationsProgram controlTerm memoryShared memory
A system and methods for sharing configuration information with multiple services, or processes, via shared memory. The configuration information, typically, comprises runtime information utilized by processes during operation, including without limitation, information describing data communication connections between the local computer and other computing resources (i.e., port and wire information), and information defining numeric values or character string values (i.e., genre and record information). The system architecture includes a plurality of APIs which: reside at the local computer; populate, manage, and control access to a shared memory containing the configuration information; and, are executable only by processes executing at the local computer, thereby limiting access to the shared memory. Access to the configuration information is further limited to only those processes identified as having appropriate permission. The methods enable the configuration information of the shared memory to be modified during local computer operation and without impeding access to the configuration information.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for localization of programming modeling resources
InactiveUS20060265207A1Digital data processing detailsNatural language data processingHuman languageString Value
A computer system localizes programming models. Given a model having one or more elements, each element has an element name, and each element name is in a language of an author of the model. For each element name, the invention system stores corresponding character strings (or string values) for generating the element name in different languages. During display of the given model in a certain locale, the present invention obtains the stored respective character strings of each element name in the language of the certain locale and uses the obtained character strings to display each element name in the language of the certain locale.
Owner:IBM CORP
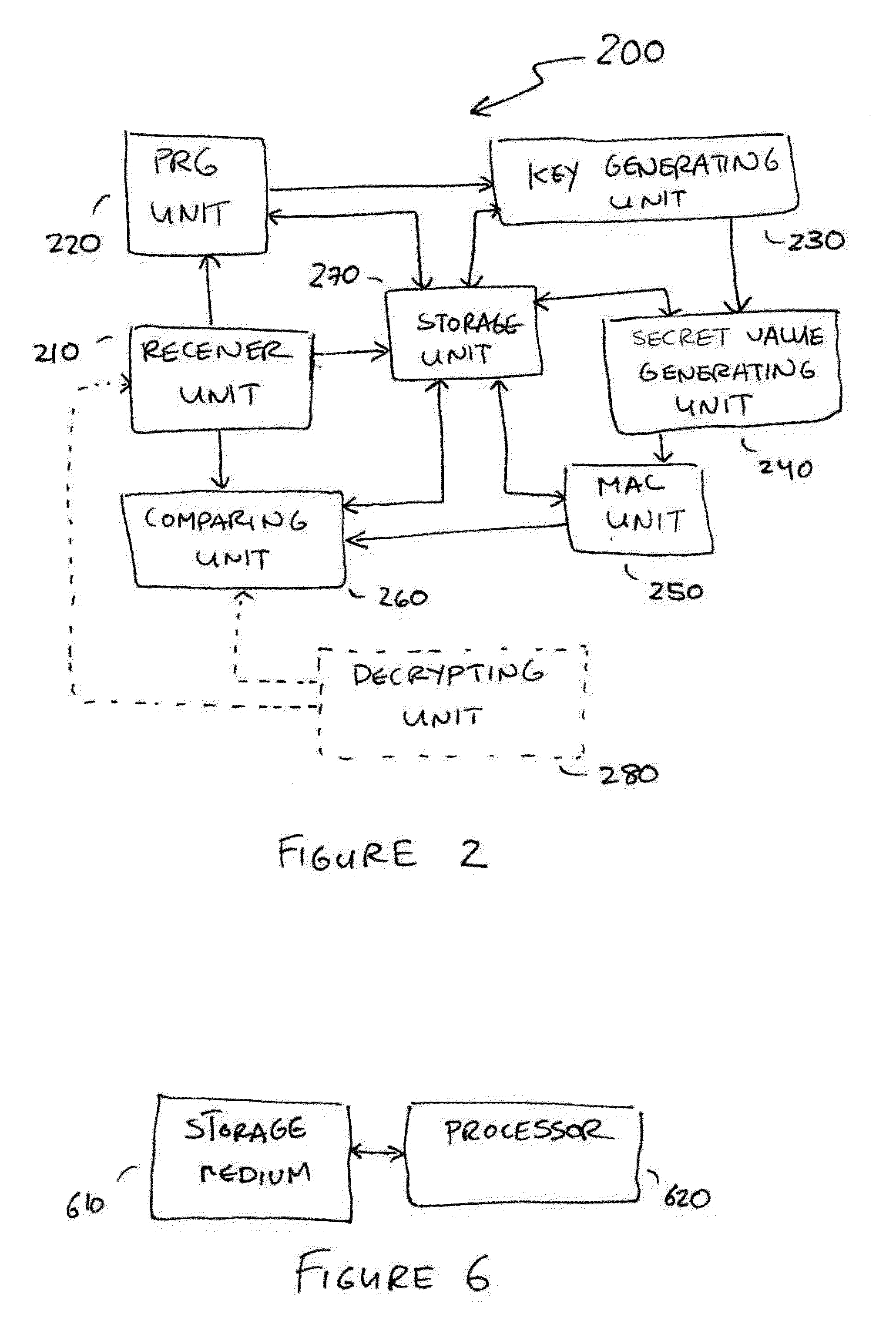
Small public-key based digital signatures for authentication
ActiveUS8437473B2Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital signatureDigital signature forgery
Embodiments disclosed allow authentication between two entities having agreed on the use of a common modulus N. The authentication includes generating a pseudorandom string value; generating a public key value based on the modulus N and the pseudorandom string value; generating a private key value corresponding to the public key value; receiving a verifier's public key value; generating a shared secret value based on the modulus N, the private key value and the verifier's public key value; calculating an authentication signature value using the shared secret value; and transmitting the authentication signature value for authentication. When the authentication signature is received, the public key value and the shared value are generated to calculate an authentication signature value. Thereafter, the authentication signature values are compared and authenticated.
Owner:QUALCOMM INC
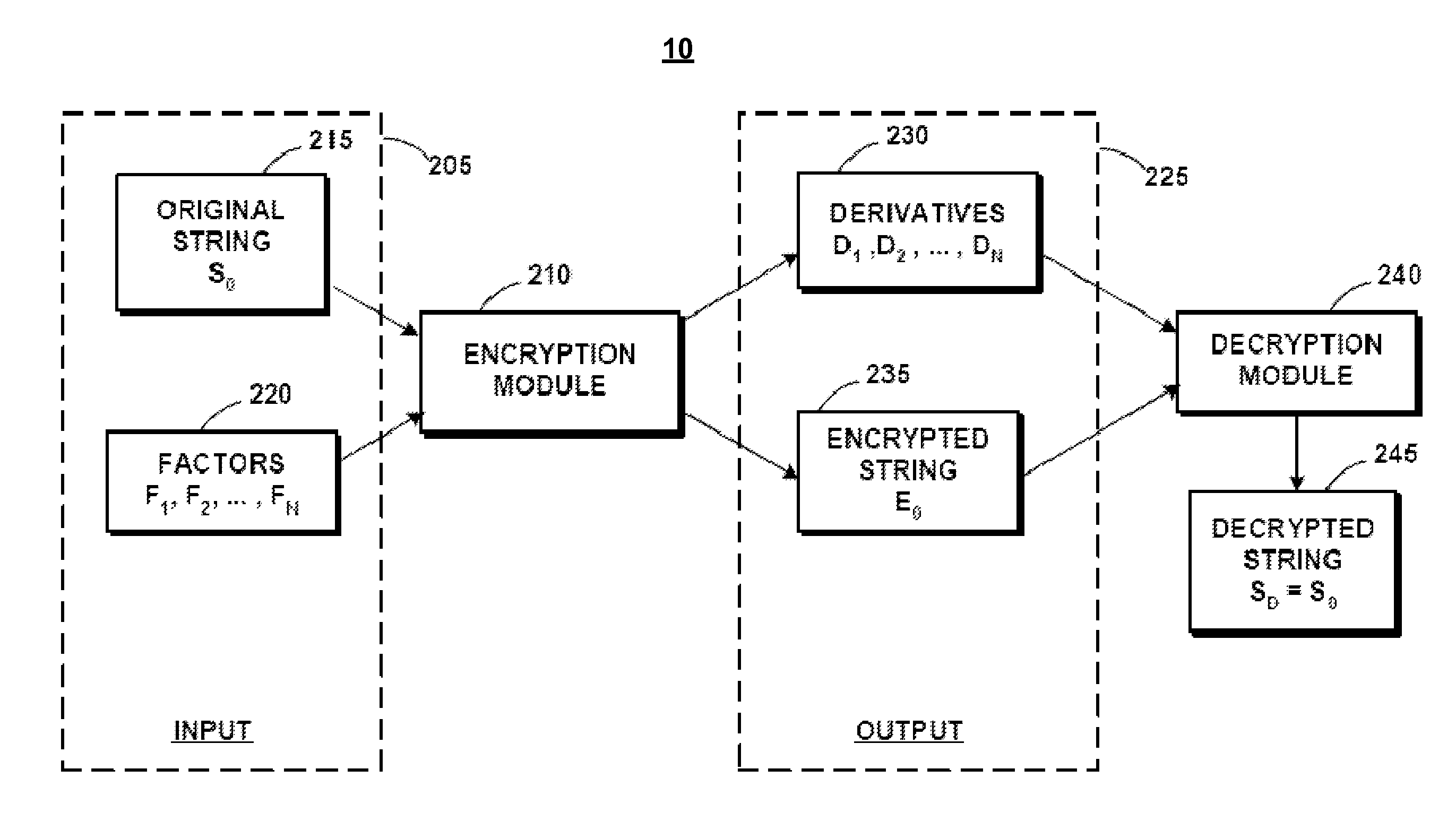
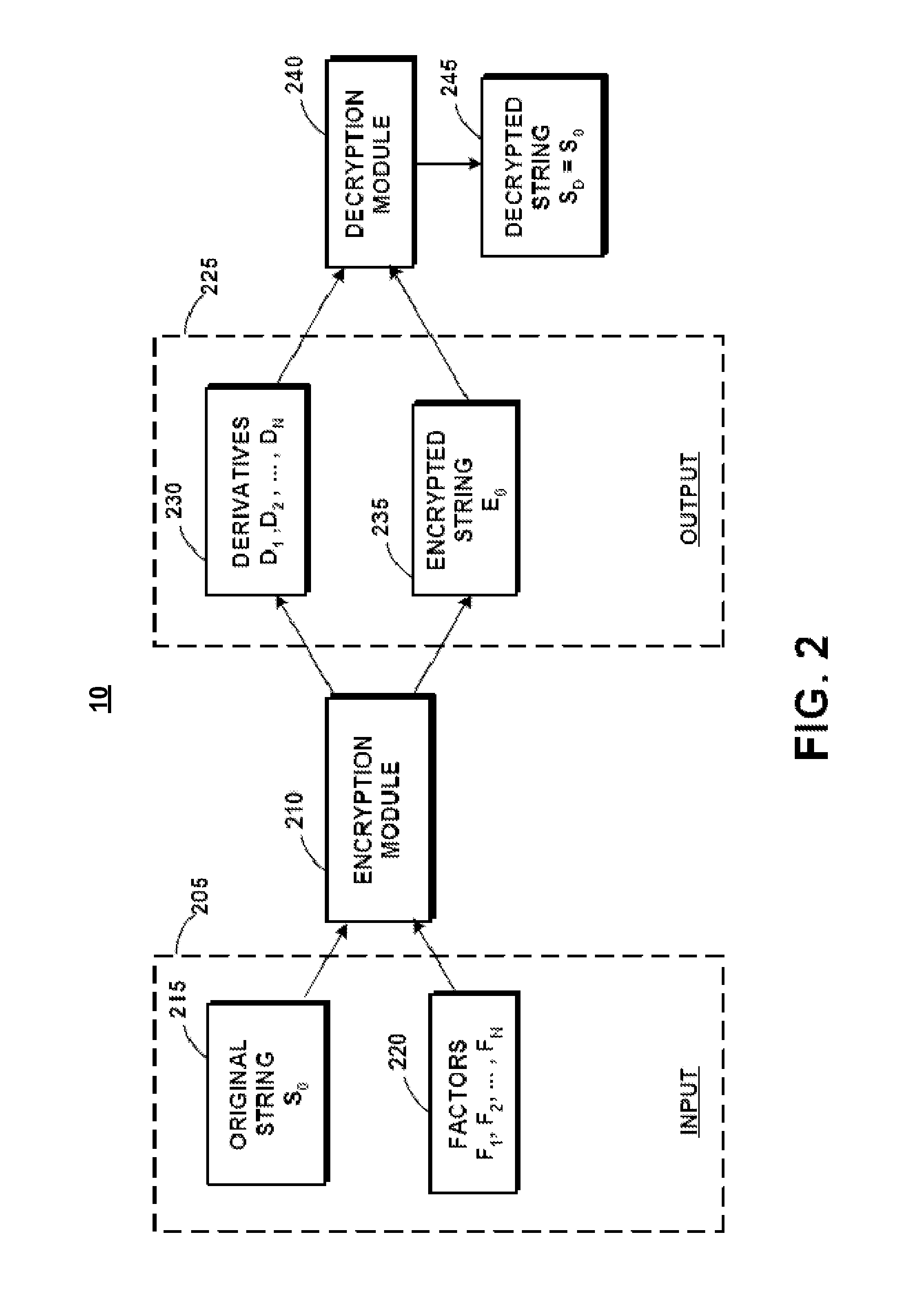
Method for encrypting and decrypting data using derivative equations and factors
InactiveUS7366299B2Simple methodSimple processPublic key for secure communicationUser identity/authority verificationComputer hardwareEncryption
A data cryptographer encrypts and decrypts character data of any given length using derivative equations and factors. The use of factors and derivative equations introduces the randomness required for effective encryption without the use of complex mathematics. A set of equations determined by the user is used in a manner similar to a key but with random results. Only a portion of the key is exposed to decrypt the encrypted information. The data cryptographer may be configured using either simple or complex equations and may be implemented in an unlimited number of variations. The data cryptographer is portable, and can be implemented in any programming language that supports cyclical character manipulation. The data cryptographer also supports input from a variety of sources, allowing control from the administrator side, string value side, or any other input that may be extracted from the desired programming language.
Owner:GOOGLE LLC
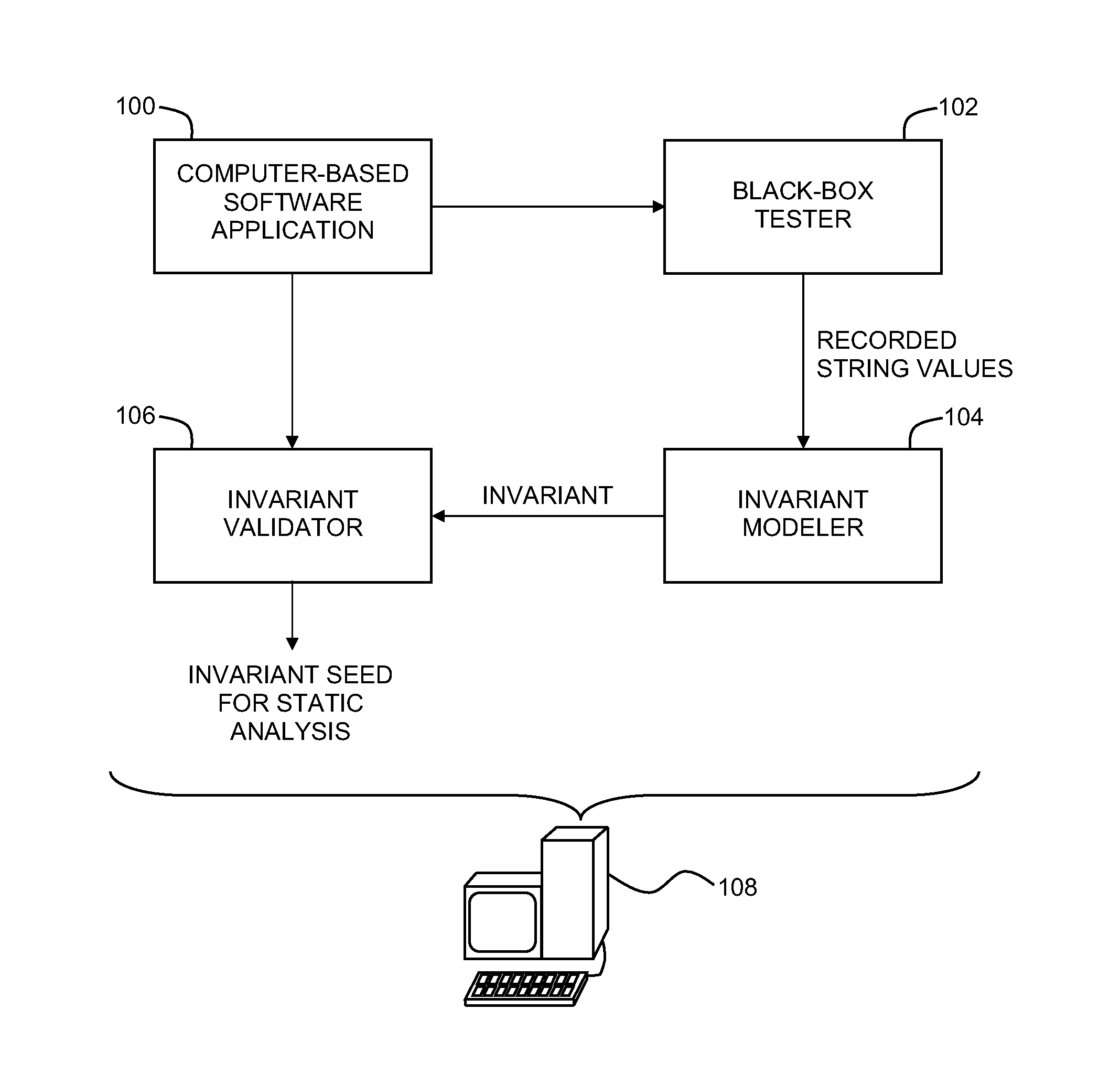
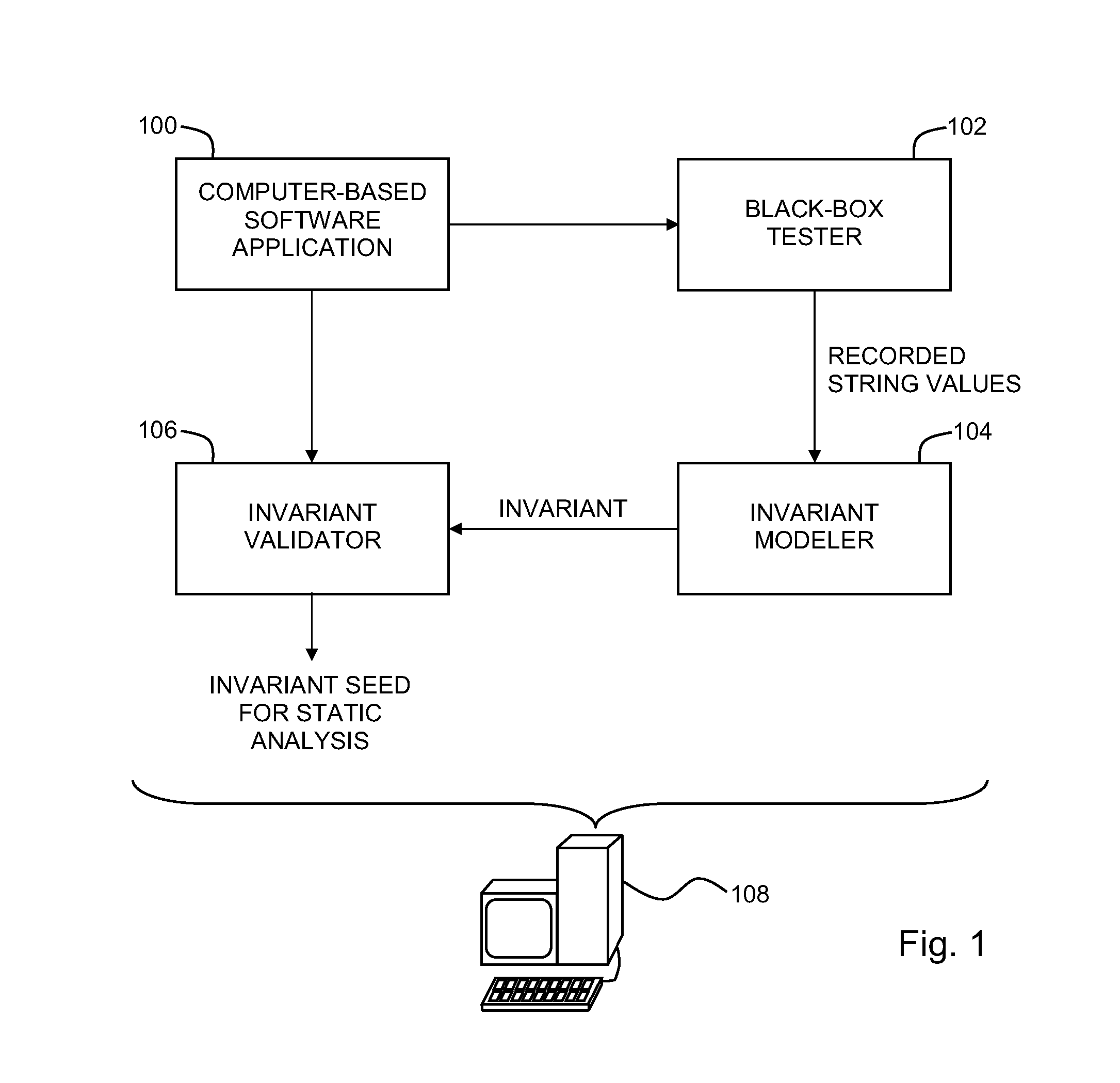
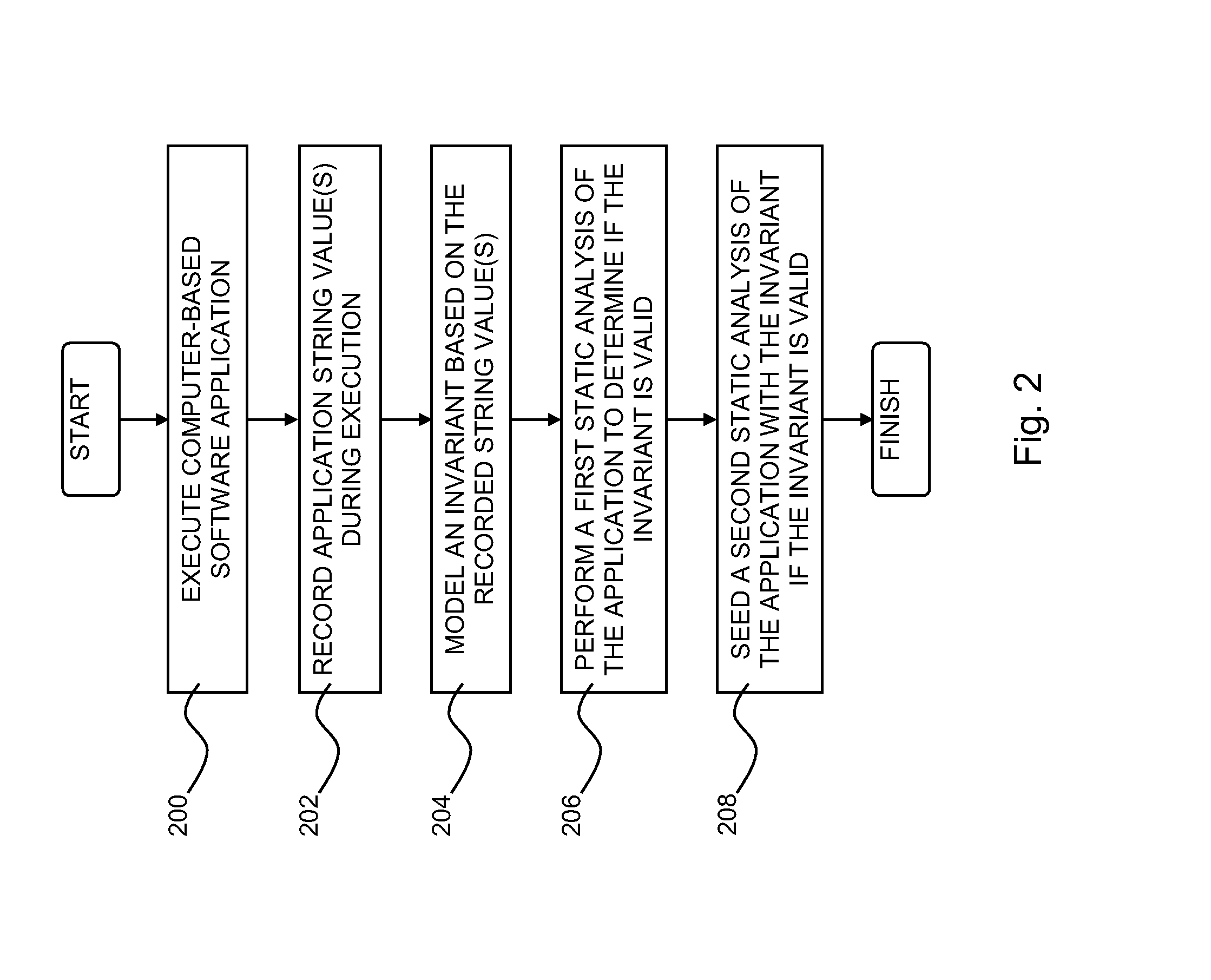
Static analysis based on observed string values during execution of a computer-based software application
Improving static analysis precision by recording a value pointed to by a string variable within the computer-based software application during the execution of a computer-based software application, modeling an invariant based on the recorded value, where the invariant represents at least one possible value pointed to by the string variable, performing a first static analysis of the computer-based software application to determine whether the invariant is valid with respect to the computer-based software application, and seeding a second static analysis of the computer-based software application with the invariant if the invariant is valid with respect to the computer-based software application.
Owner:IBM CORP
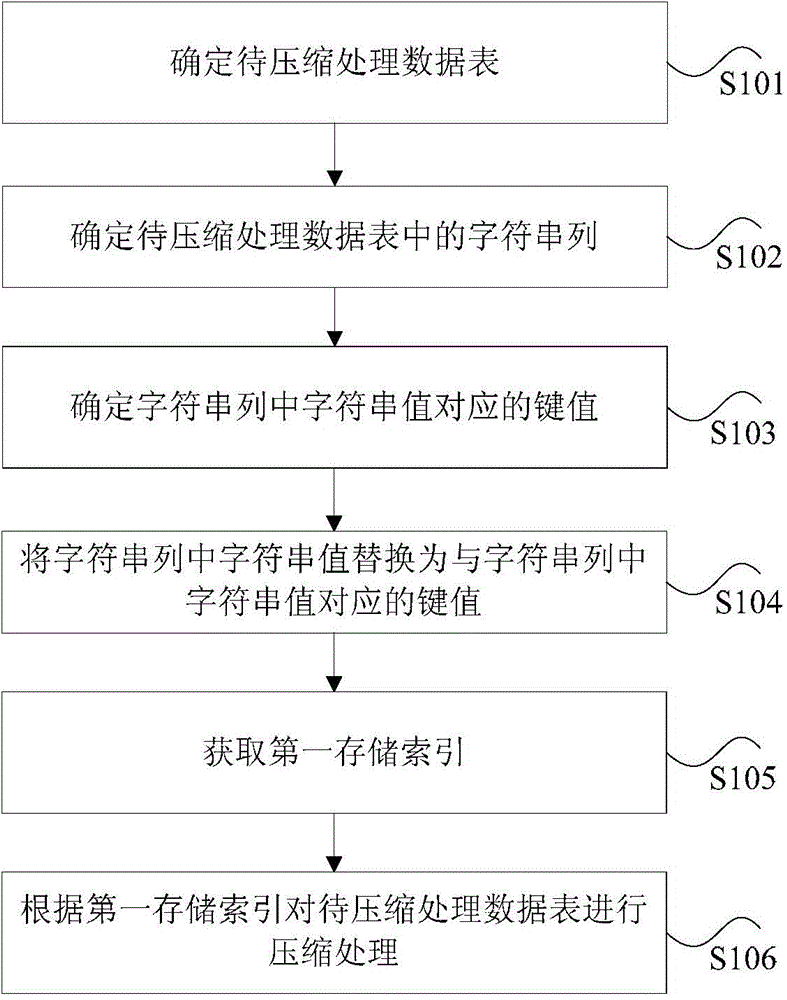
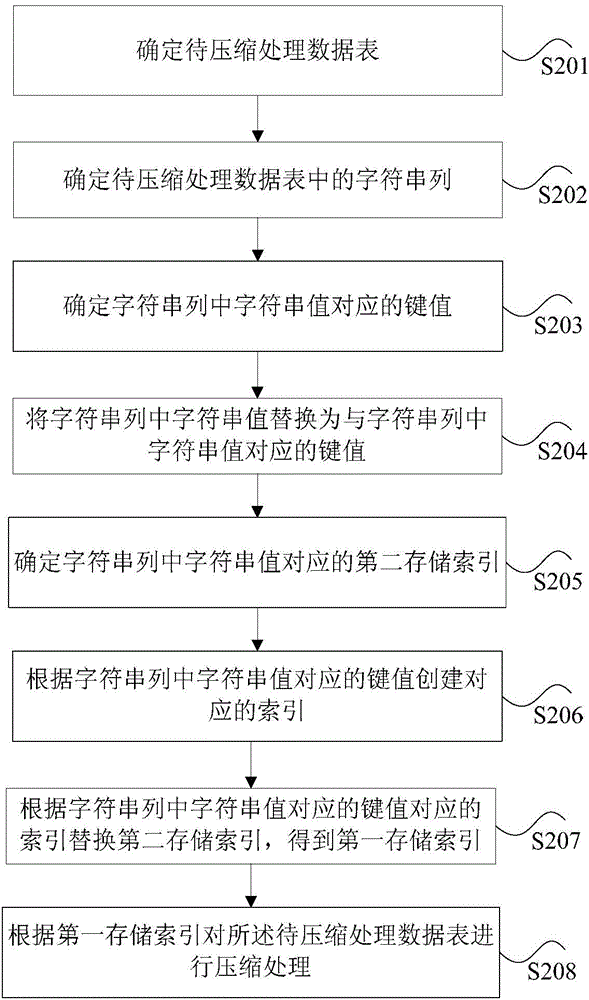
Compression processing method and device of character string type column
ActiveCN104408192ASolve the problem of low compression processing efficiencyImprove compression processing efficiencySpecial data processing applicationsAlgorithmTheoretical computer science
The invention discloses a compression processing method and a compression processing device of a character string type column. The compression processing method of the character string type column includes: confirming a data list to be compressed; confirming a character string column in the data list to be compressed, wherein using the character string column as the character string type column in the data list to be compressed; confirming key value corresponding to character string value in the character string column, wherein using the key value as value of data types; replacing the character string value in the character string column with the key value corresponding to the character string value in the character string column; obtaining a first storage index, wherein using the first storage index as a corresponding index built according to the key value corresponding to the character string value in the character string column; compressing the data list to be compressed according to the first storage index. The compression processing method and the compression processing device of the character string type column solve the problem that compression processing of the character string type column is low in efficiency in the prior art.
Owner:BEIJING GRIDSUM TECH CO LTD
Small public-key based digital signatures for authentication
InactiveUS20130227297A1Key distribution for secure communicationUser identity/authority verificationDigital signatureDigital signature forgery
Embodiments disclosed allow authentication between two entities having agreed on the use of a common modulus N. The authentication includes generating a pseudorandom string value; generating a public key value based on the modulus N and the pseudorandom string value; generating a private key value corresponding to the public key value; receiving a verifier's public key value; generating a shared secret value based on the modulus N, the private key value and the verifier's public key value; calculating an authentication signature value using the shared secret value; and transmitting the authentication signature value for authentication. When the authentication signature is received, the public key value and the shared value are generated to calculate an authentication signature value. Thereafter, the authentication signature values are compared and authenticated.
Owner:QUALCOMM INC
Method for localization of programming modeling resources
InactiveUS7882116B2Digital data processing detailsNatural language data processingProgramming languageModelSim
A computer method localizes programming models. Given a model having one or more elements, each element has an element name, and each element name is in a language of an author of the model. For each element name, the invention method stores corresponding character strings (or string values) for generating the element name in different languages. During display of the given model in a certain locale, the present invention obtains the stored respective character strings of each element name in the language of the certain locale and uses the obtained character strings to display each element name in the language of the certain locale.
Owner:INT BUSINESS MASCH CORP
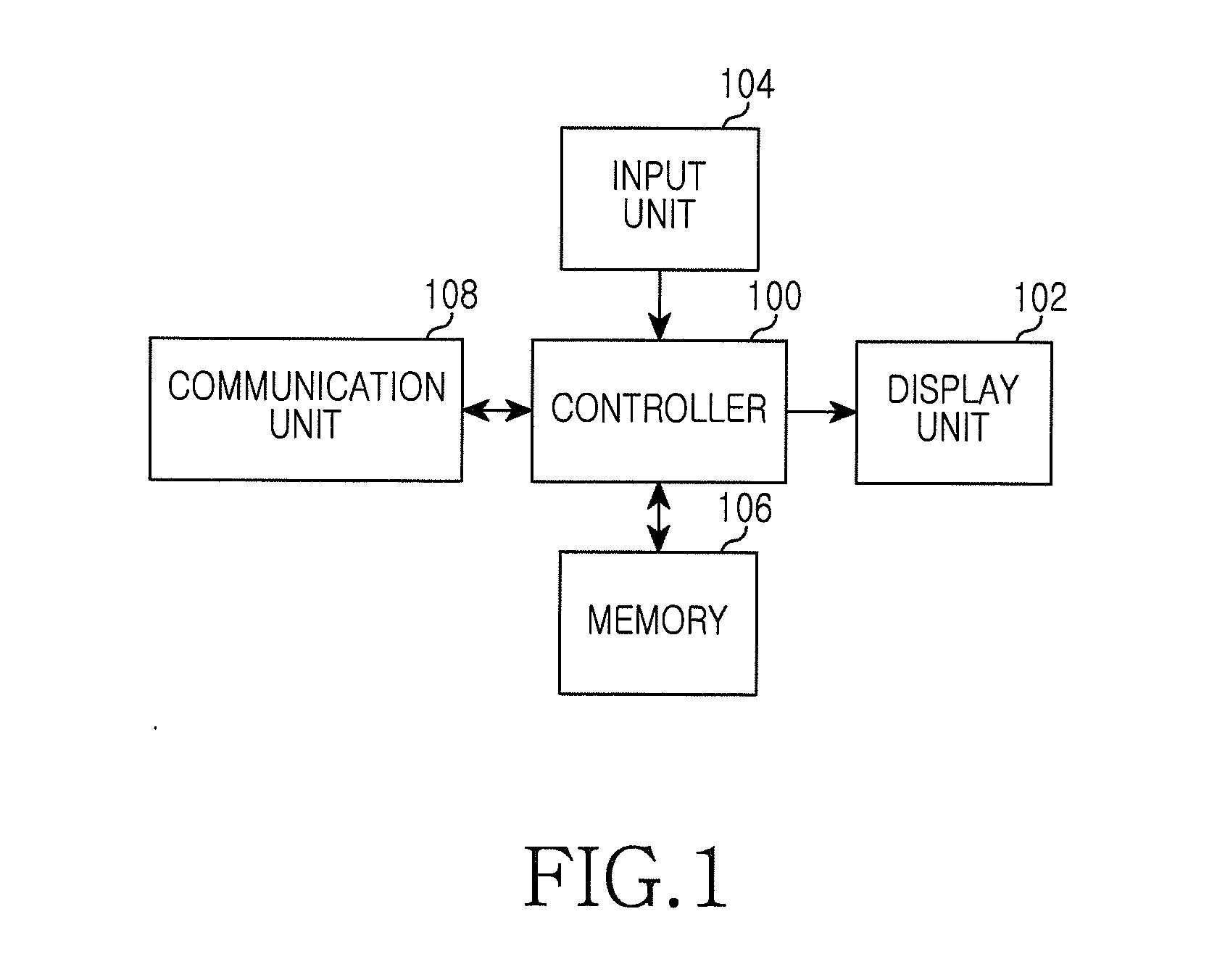
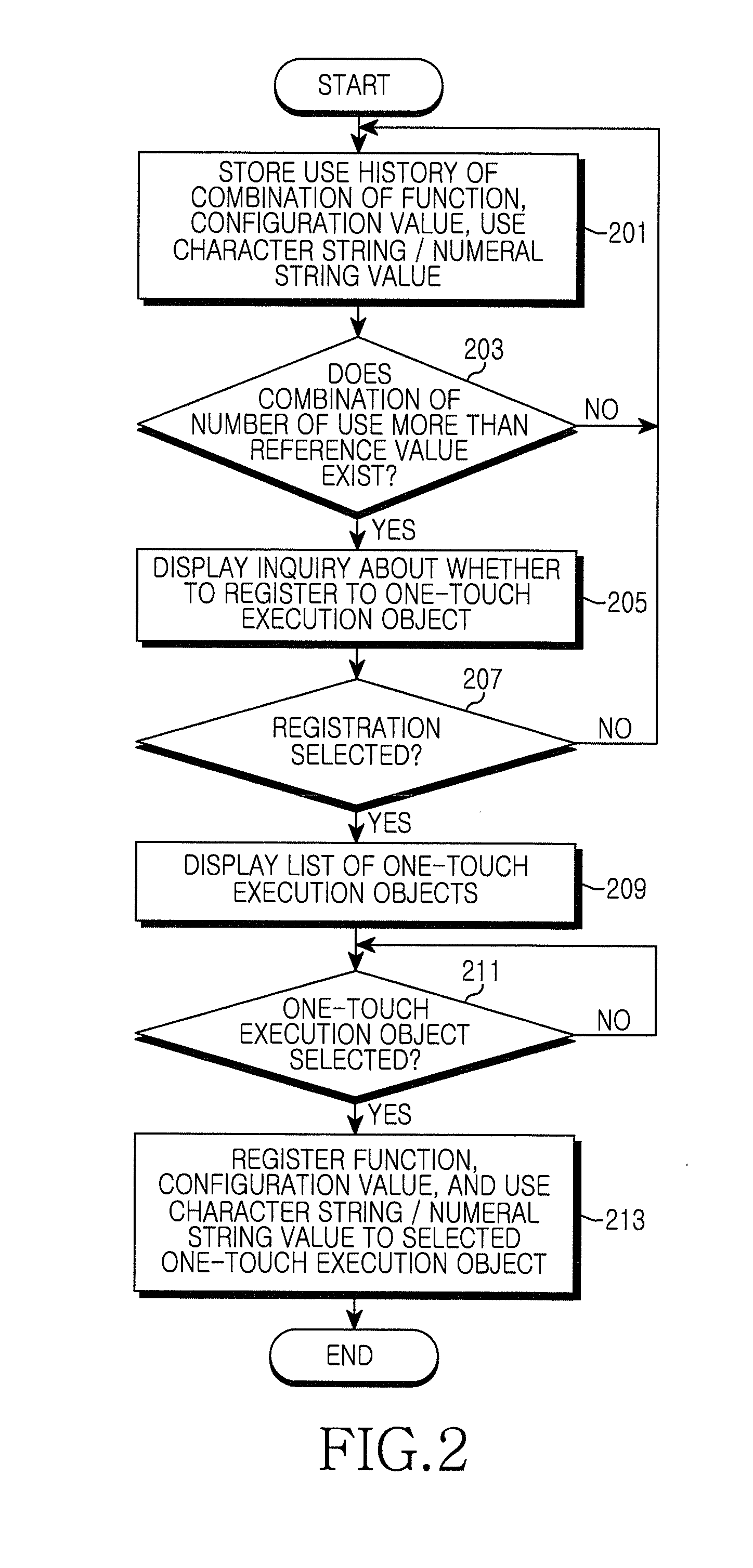
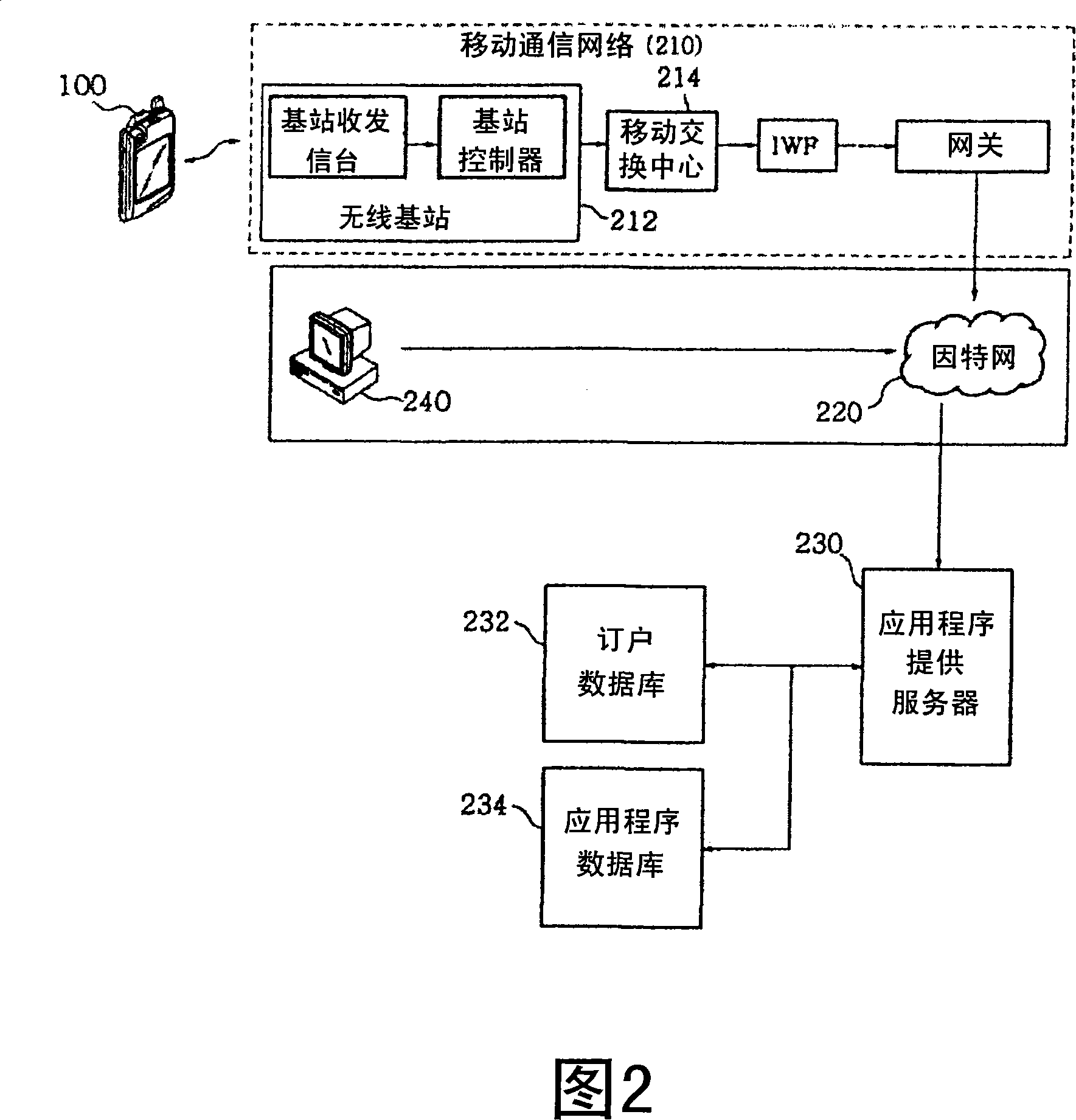
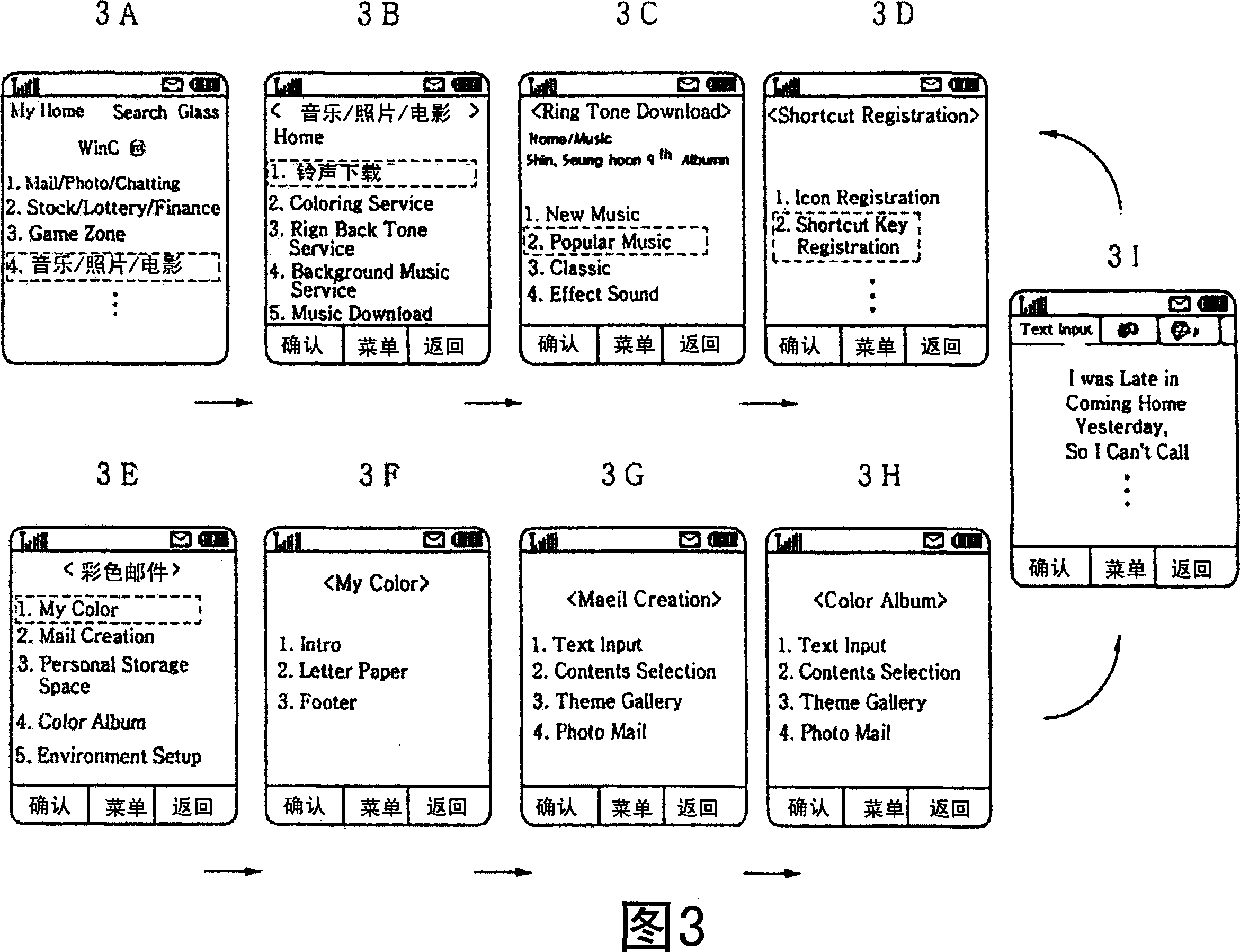
Apparatus and method for automatically registering and executing preferred function in a mobile communication terminal
ActiveUS20110216026A1Substation equipmentInput/output processes for data processingProgramming languageString Value
An apparatus and method for automatically registering and executing a preferred function in a mobile communication terminal. The method includes registering a function and a configuration value and use character string / numeral string value for the function, to a one-touch execution object. The method also includes, when a one-touch input for the one-touch execution object is sensed, executing the function registered to the one-touch execution object, by the configuration value and use character string / numeral string value registered to the one-touch execution object.
Owner:SAMSUNG ELECTRONICS CO LTD
Method, system, and program, for encoding and decoding input data
ActiveUS20030072446A1High strengthOptimizes encryption of dataComputer security arrangementsSecuring communicationUser inputTheoretical computer science
Provided is a method, system, and program for encoding and decoding input data. A key is generated comprising a list of a plurality of binary values, wherein the key is available to a user to provide during decoding. The input data is encoded by using the key to initialize a replacement list. A determination is made whether to replace strings in the input data with a string reference to a matching string value, wherein the input data not replaced with reference to one matching string value comprises one or more literals. Each literal is replaced with a literal reference to one entry in the replacement list matching the literal. The encoded input data is decoded by accessing the generated key in response to user input and using the accessed key to decode the literals replaced with literal references to entries in the replacement list.
Owner:TWITTER INC
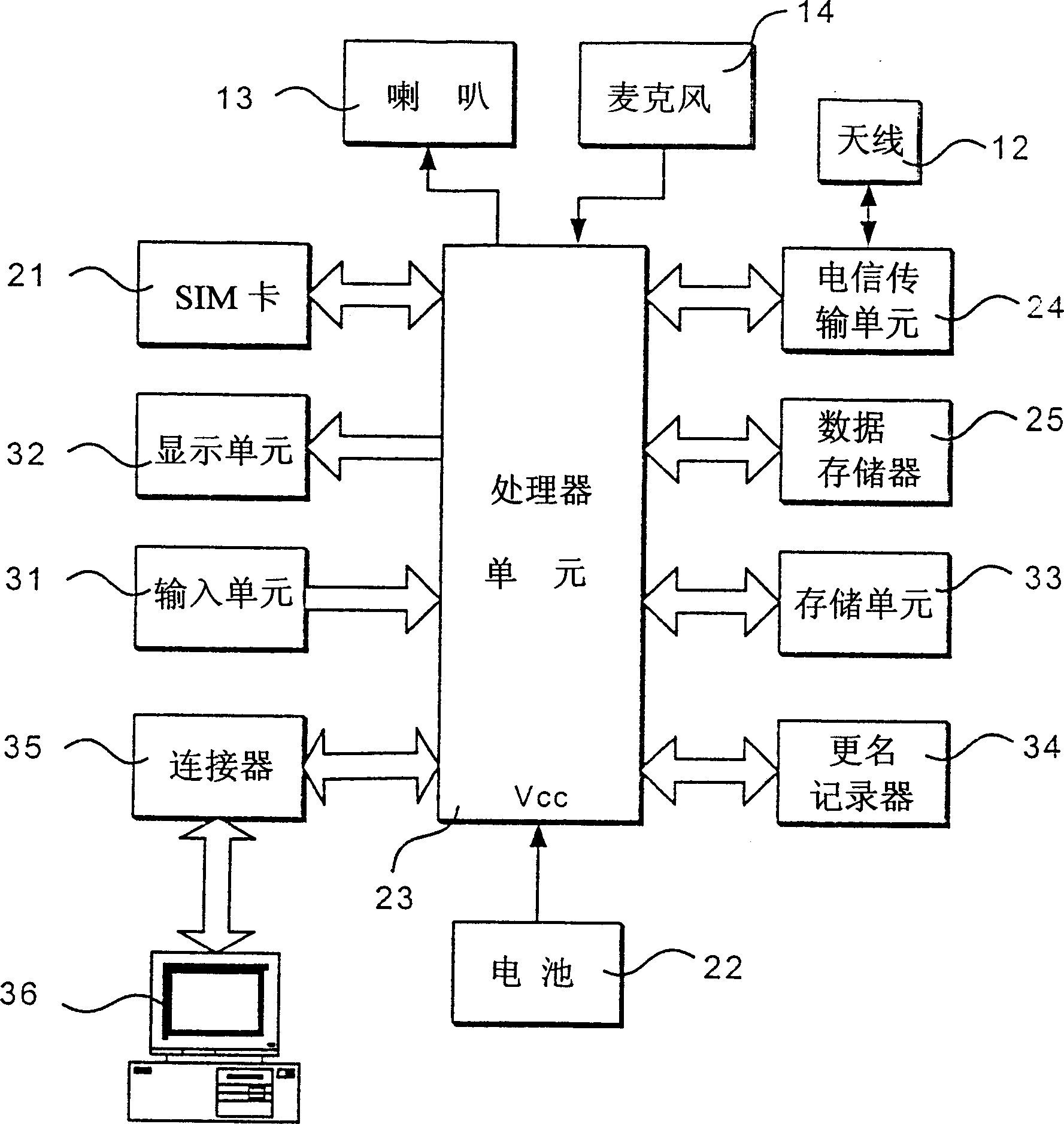
Handset catalogue name editing method and device
InactiveCN1420699ARadio/inductive link selection arrangementsSpecial data processing applicationsComputer hardwareData interchange
An editing method of list name for mobilephone comprises displaying the function of list operation using display unit in mobilephone, selecting the list name to be edited using input unit, inputting a character string value for the new list name using the input unit and storing this new value is storing unit, meanwhile setting a renaming determination code and storing this code in the rename recorder. The renaming determination code is used to judge whether the new list name is used or not. The device for it consists of an input unit, a display unit, a storage unit, a processor unit and a rename recorder as all the relative data exchanging of above mentioned components processed by the processor unit.
Owner:GUAN TECH
Static security analysis using a hybrid representation of string values
InactiveUS20140075561A1Memory loss protectionError detection/correctionTheoretical computer scienceString group
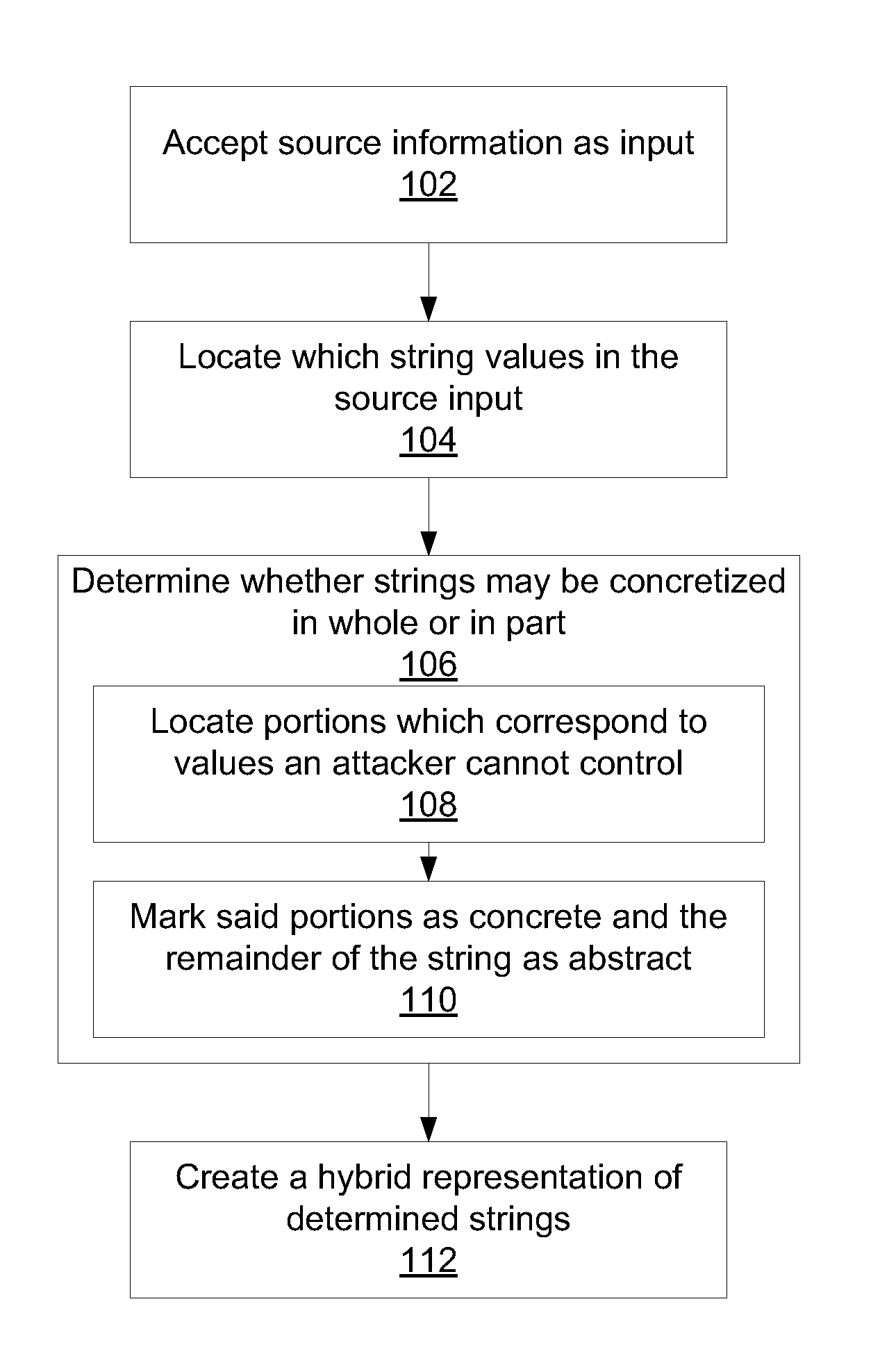
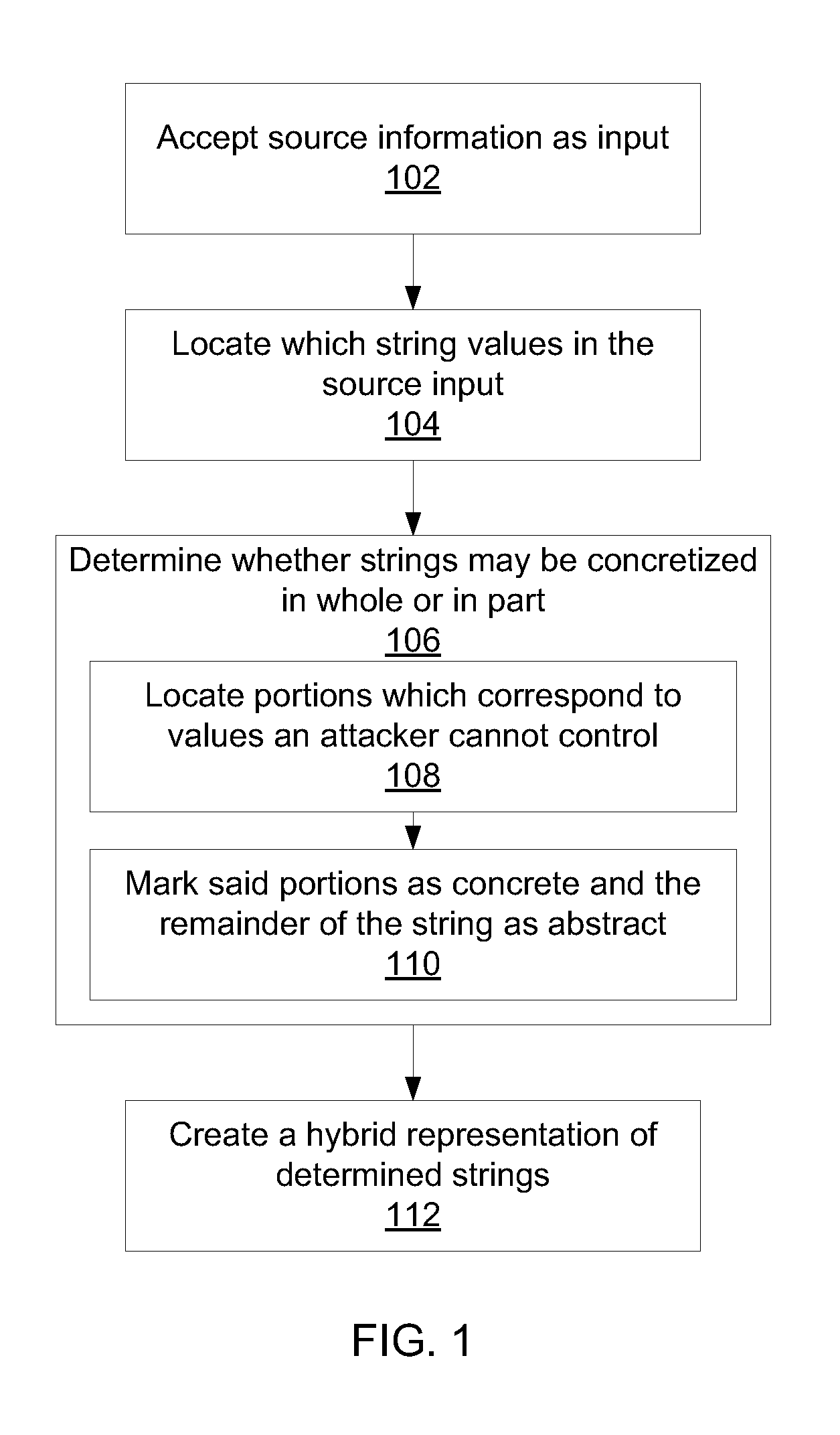
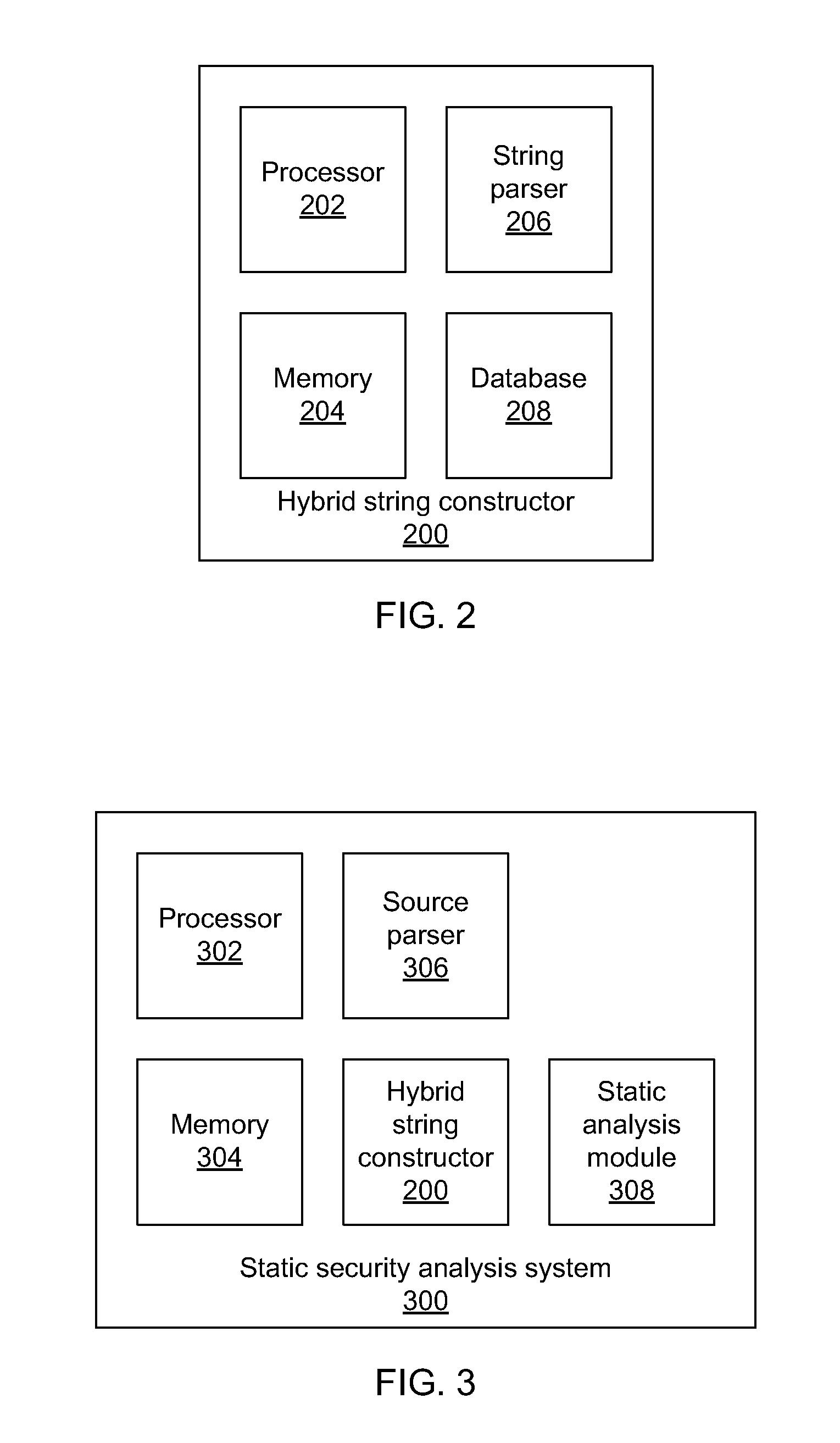
Methods for creating a hybrid string representations include receiving string information as input; parsing the string information to produce one or more string components; determining string components that may be represented concretely by comparing the one or more components to a set of known concretizations; abstracting all string components that could not be represented concretely; and creating a hybrid string representation that includes at least one concrete string component and at least one abstracted string component.
Owner:IBM CORP
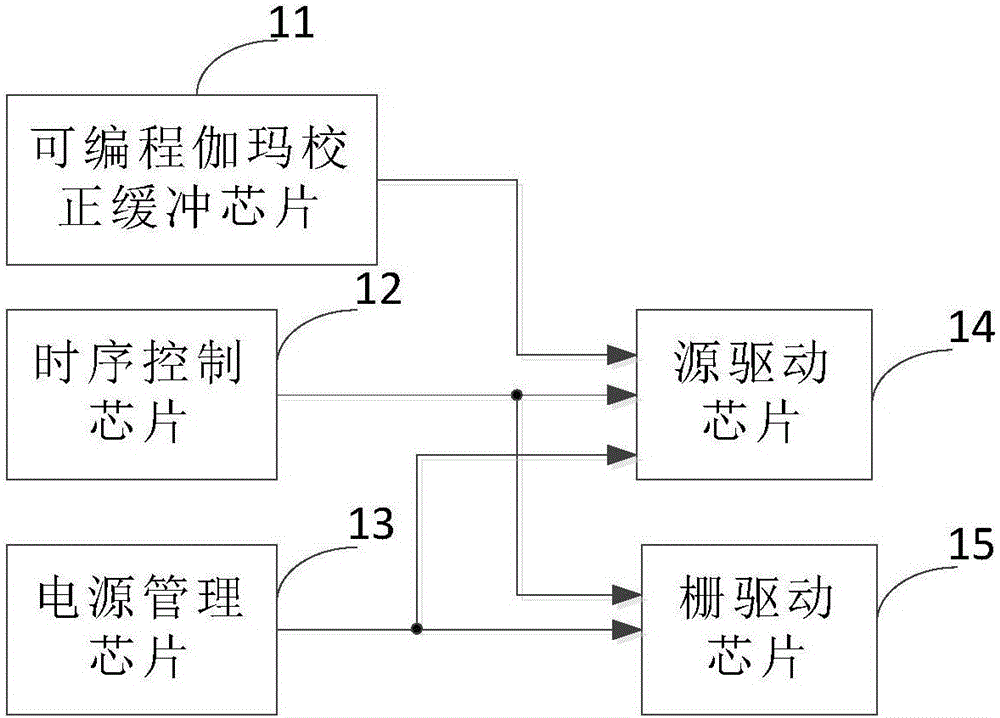
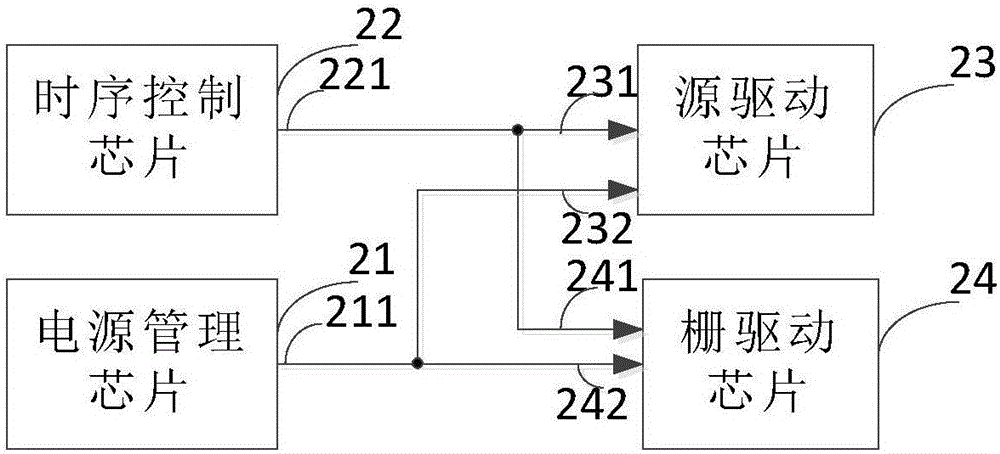
Driving circuit and liquid crystal display device
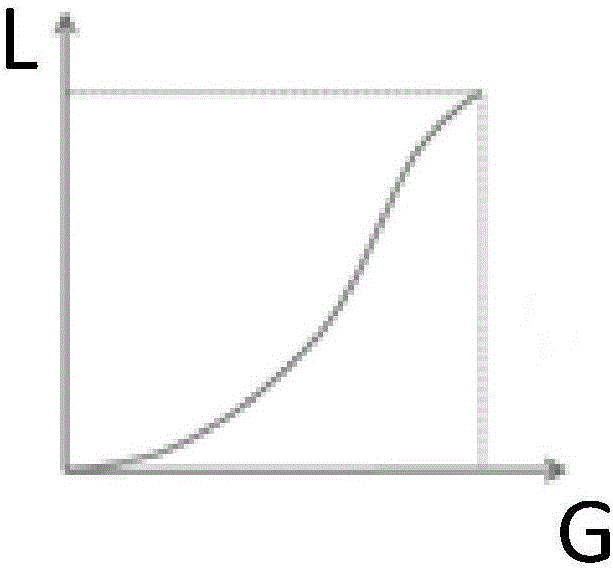
The invention provides a driving circuit and a liquid crystal display device. The driving circuit comprises a power management chip, a timing sequence control chip and a source driving chip, wherein the power management chip is used for generating data control voltage; the timing sequence control chip is used for providing a first timing sequence control signal and a video signal; the source driving chip is used for converting the video signal into a plurality of gray-scale voltages, pre-obtaining a relation between brightness of a display panel and gray scale and a relation between the brightness of the display panel and the voltage under a preset gamma curve, obtaining a relation between the gray scale and the voltage after dividing voltage according to the relation between brightness of the display panel and gray scale and the relation between the brightness of the display panel and the voltage, obtaining a resistance string value according to the relation between the gray scale and the voltage after dividing voltage, and generating data signals according to the data control voltage, the first timing sequence control signal, the video signal and the resistance string value to enable the display effect of the panel to meet a preset condition. Through the driving circuit and the liquid crystal display device, the production cost can be reduced.
Owner:TCL CHINA STAR OPTOELECTRONICS TECH CO LTD
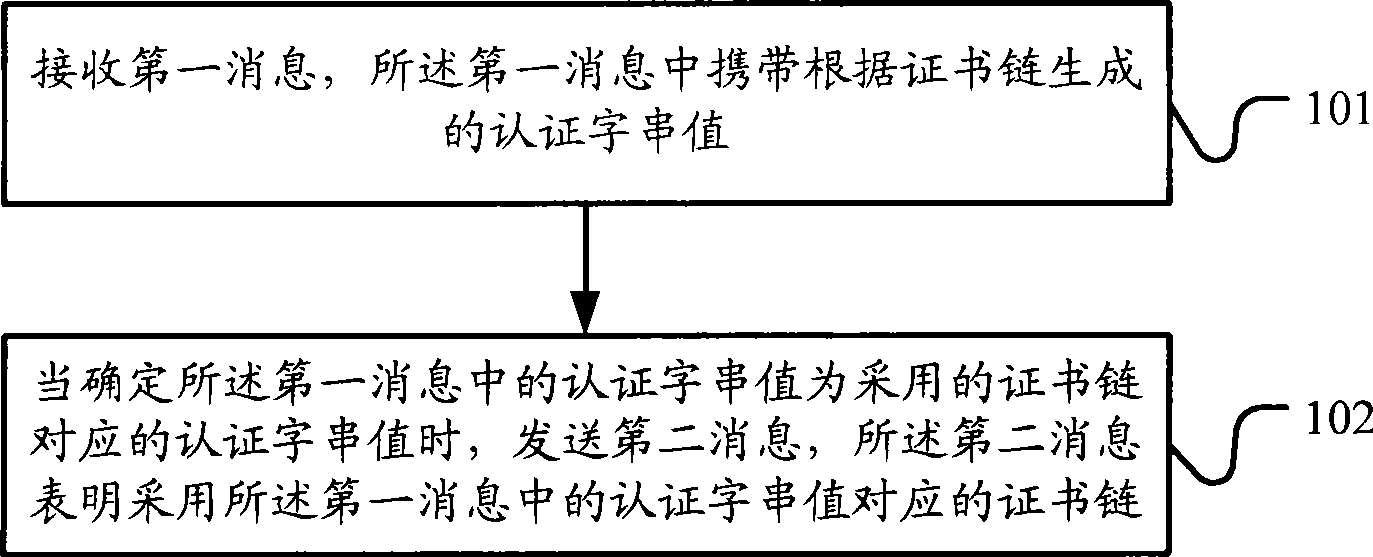
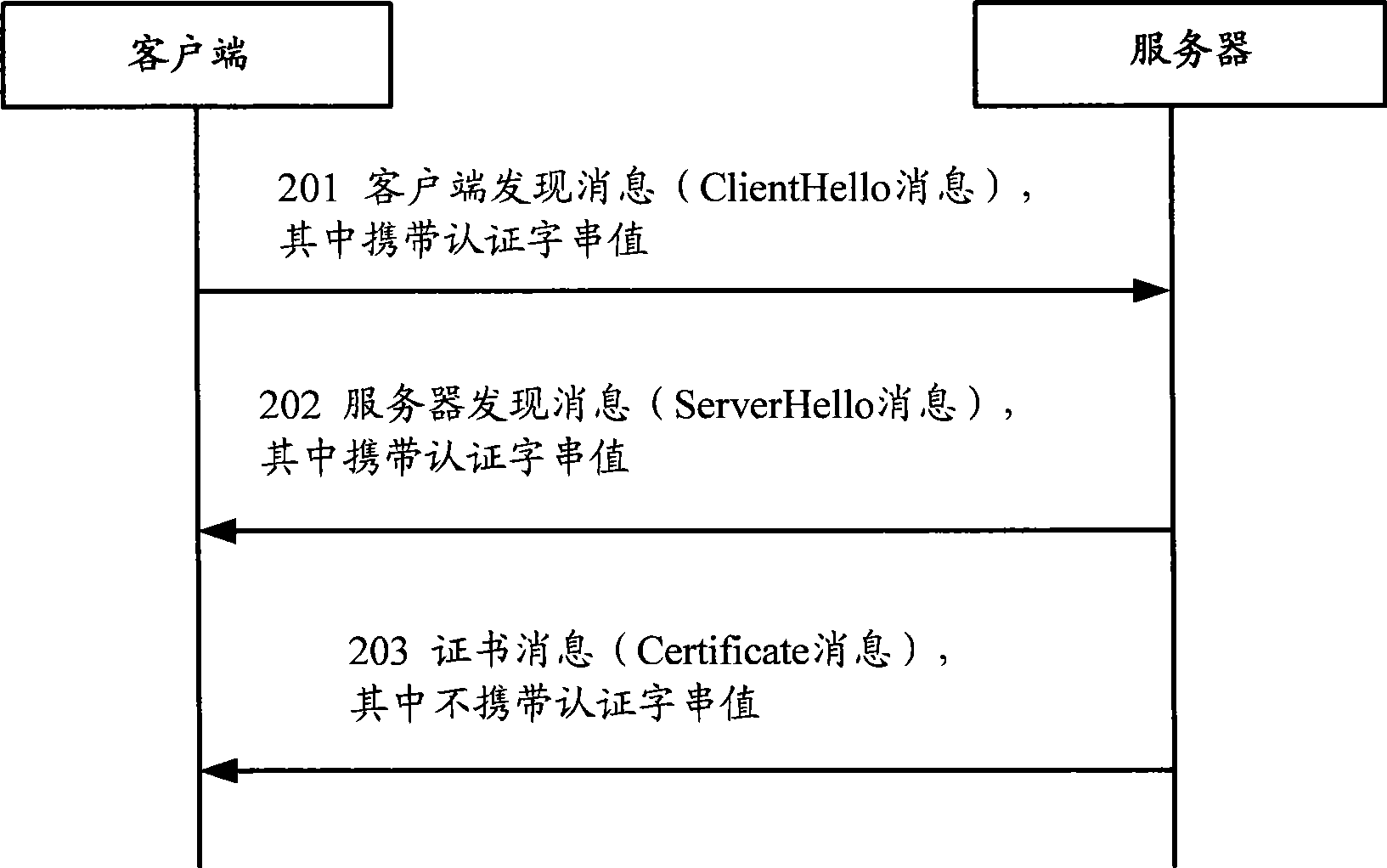
A message transmission method, network device and network system
ActiveCN101534262AAvoid transport overheadUser identity/authority verificationData switching networksComputer hardwareNetworked system
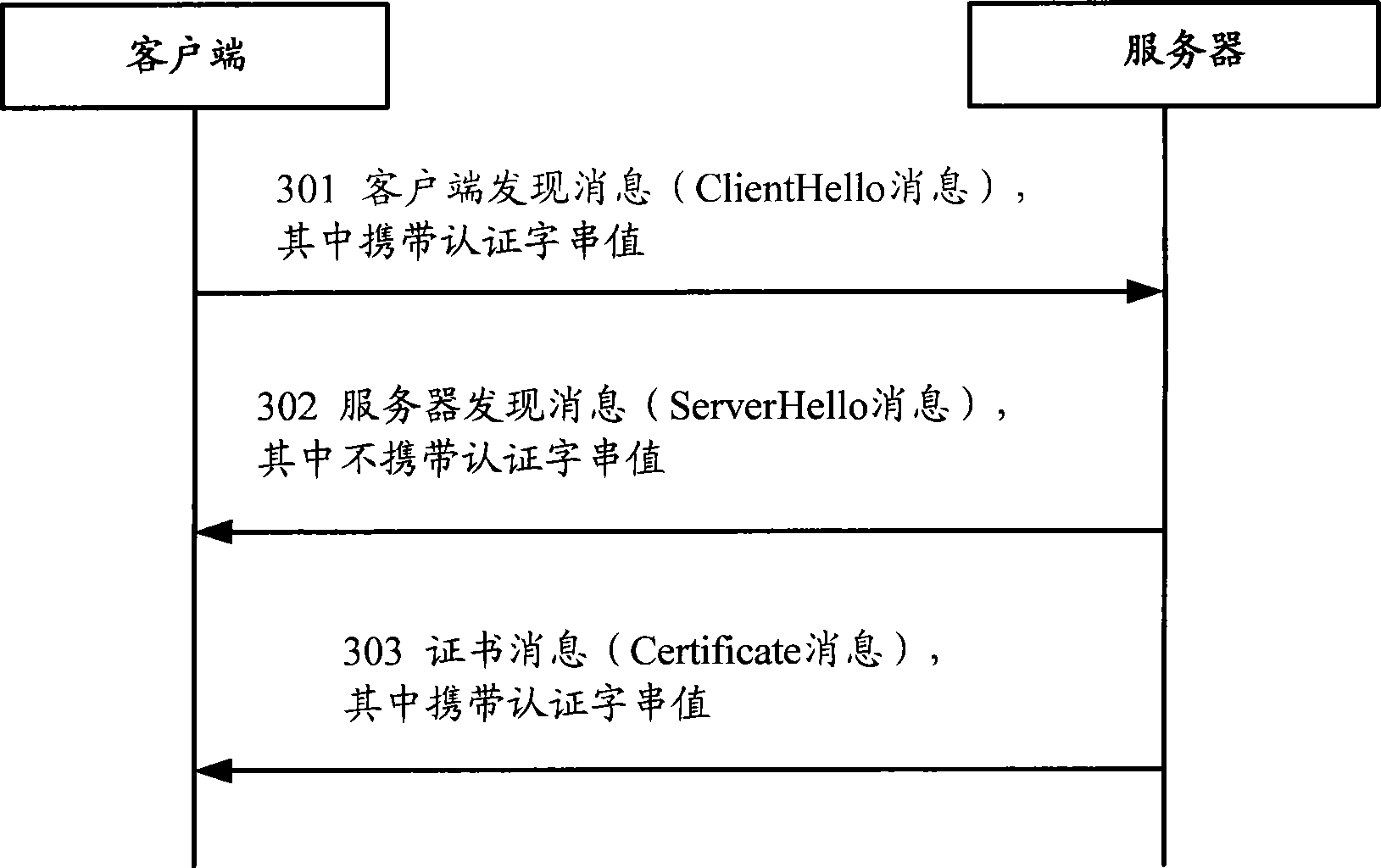
The embodiment of the invention discloses a message transmission method, network device and network system. The message transmission method comprises: receiving a first message which carries approved string value produced according to a certificate chain; sending a second message, when the approved string value in the first message is the adopted corresponding approved string value. The second message shows that the approved string value in the first message is the corresponding certificate chain. Correspondingly, the embodiment of the invention also provides a network device and network system. The technique proposal provided by the embodiment of the invention can reduce the cost of the transmission process.
Owner:CHENGDU HUAWEI TECH
Software debugging log output control achievement method
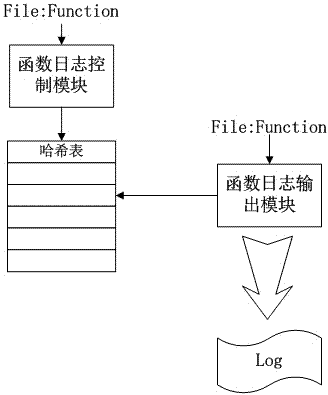
ActiveCN104750488AReduce lossHardware monitoringSpecific program execution arrangementsComputer moduleHash table
The invention particularly relates to a software debugging log output control achievement method. The software debugging log output control achievement method adopts a function log control module and a function log output module. Functions needing to open log output are added into a Hash table for achieving log switching, and character string values of source program file names and function names are used for conducting Hash calculation of the Hash table and conflict detection is performed according to Hash values; log output points perform Hash search according to the character string values of the source program file names and the function names and perform log output for the functions opening log output. The software debugging log output control achievement method utilizes the character string values of the source program file names and the function names to perform Hash calculation and controls output of function logs in a matched mode, and performance loss caused by log control can be effectively reduced at the high-performance requests of driver development and the like.
Owner:SHANDONG INSPUR SCI RES INST CO LTD
Graph similarity calculation system, method, and program
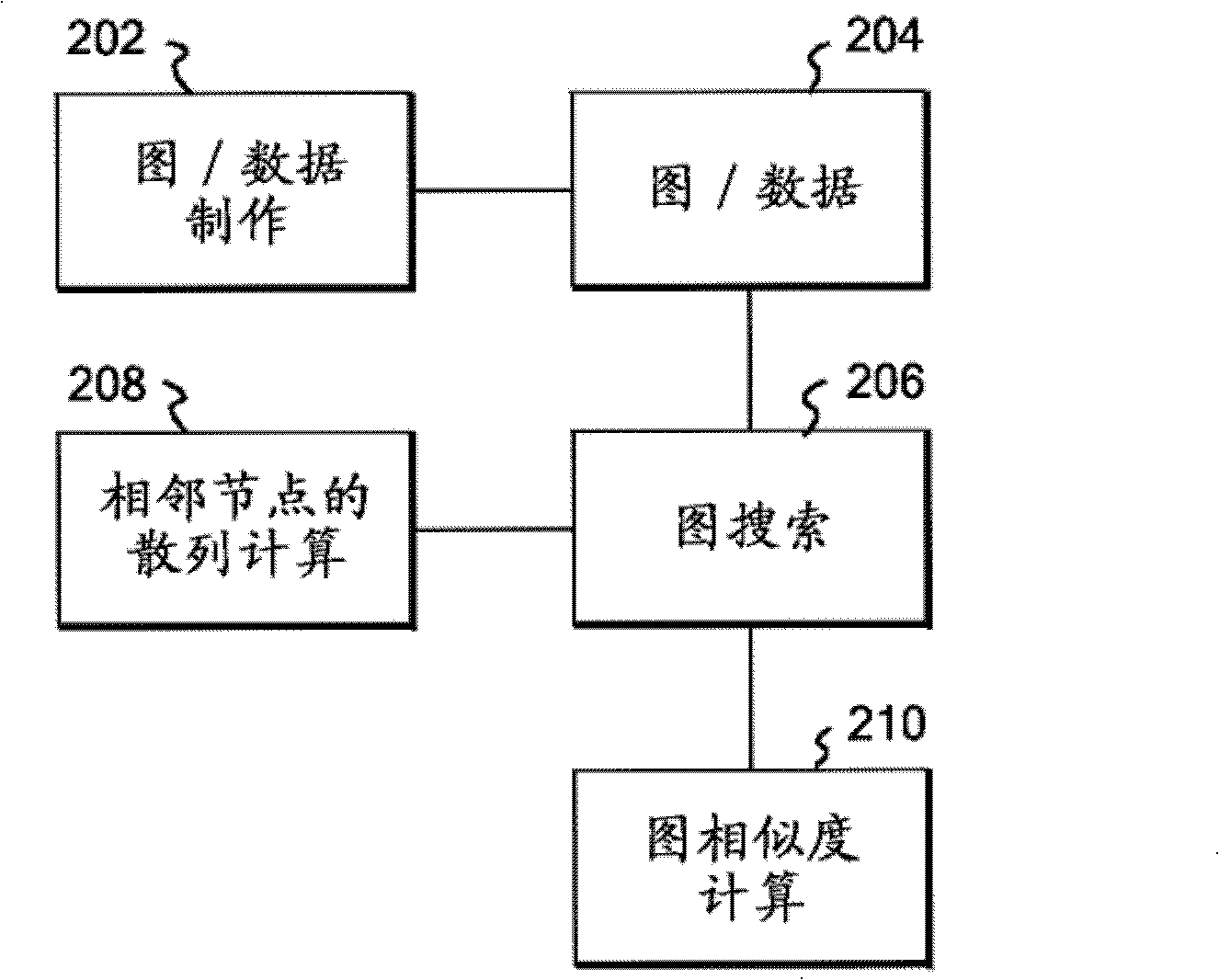
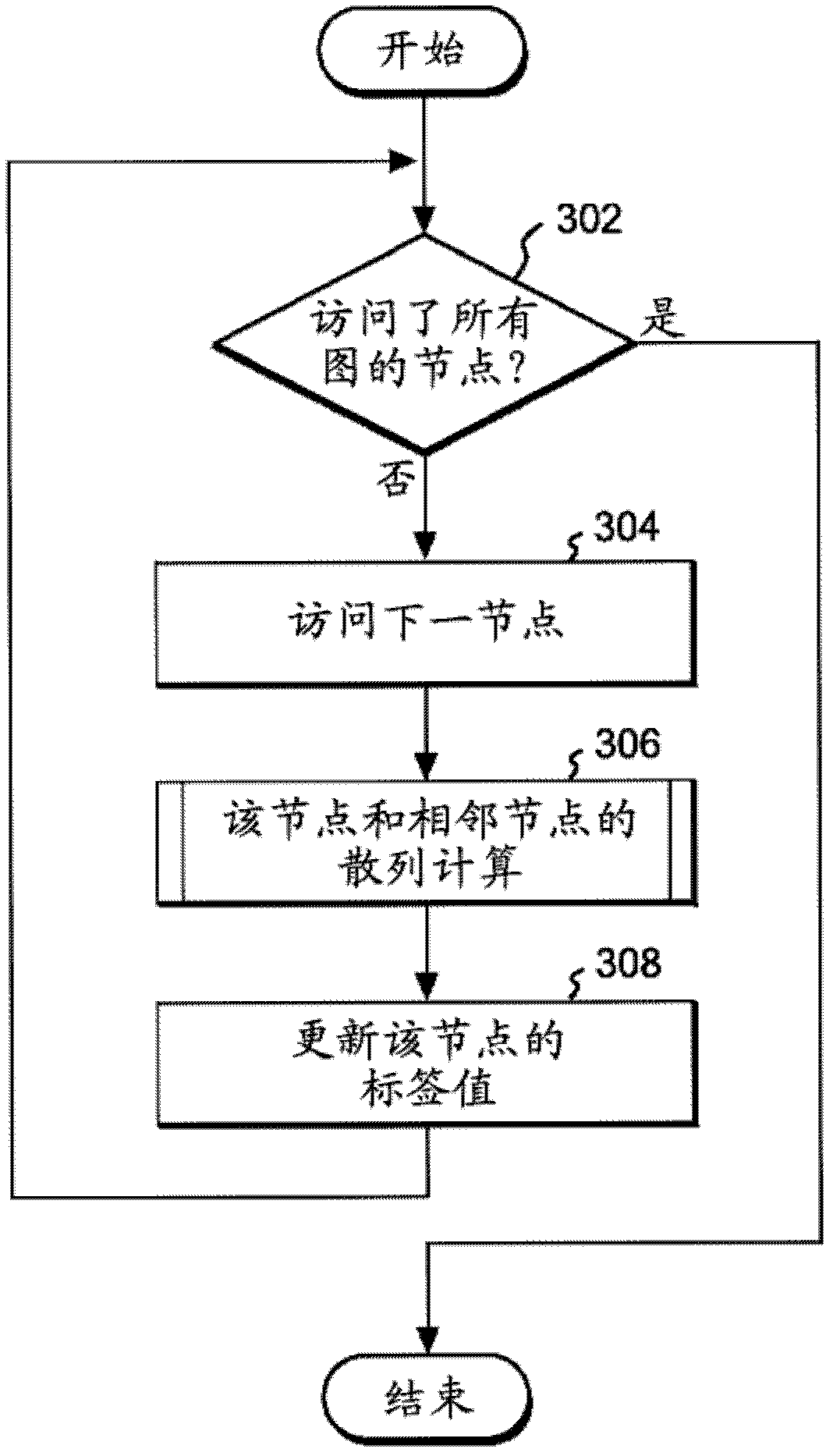
ActiveCN102341802AThe effect of high speedImprove reliabilityDigital data information retrievalCharacter and pattern recognitionDepth-first searchTheoretical computer science
The similarity between graphs having an extremely large number of nodes, such as an SNS, a link of WWW, etc., can be obtained within a reasonable time. A unique value is provided to a label of a node in a graph. Preferably, the value is a fixed-length bit string. In this case, the length of the bit string is selected to be sufficiently larger than the number of digits by which types of labels can be expressed. With respect to one graph, nodes of the graph are sequentially visited by an existing graph search method, such as a depth-first search, a breadth-first search, and the like. At this time, in the system, when one specific node is visited, a calculation is performed for bit string label values of all nodes adjacent to the specific node and the bit string label value of the specific node, to obtain a bit string value. The hash calculation is performed for the calculated bit string value and the original bit string label value of the node to obtain another bit string label value, and this value becomes the label value of the node. After finishing the visit to all nodes in one graph, the label values of all nodes are rewritten. When the same treatment is performed for another graph which becomes a target of the graph similarity comparison, label values of all nodes in this graph are rewritten. Therefore, with respect to one graph, a ratio of label values which are identical to the label values in another graph, per all nodes is calculated to obtain the similarity.
Owner:IBM CORP
JNI-based calling method for JAVA function in C++
ActiveCN107832056AImprove stabilityReduce workloadTransformation of program codeMaintainabilityBase calling
The invention discloses a C++ and JAVA function mutual calling method. The method comprises the steps that a C++ variable parameter template and template specialization are used to obtain a string value literal object of a JNI data type signature in a compiling period, the data type signature supported by a JNI is preset, and the JNI is established; after a JAVA function is called, the C++ variable parameter template and template specialization are used to realize direct data type conversion between C++ and the JNI and generate a function signature; and a function execution result is convertedfrom a JNI data type to a C++ data type, and finally the result is returned. By the adoption of the method, C++ and JAVA seamless calling is realized, a calling process of the JNI is hidden, a developer can complete C++ and JAVA interaction without the need for learning JNI development or writing a long JNI function calling signature, therefore, the workload is greatly reduced, maintainability and stability of programs are improved, and labor cost is saved.
Owner:SNAIL GAMES
Character string value domain segmenting method and device
ActiveCN106294371AAvoid problemsGuaranteed to be completely undistortedProgram controlMulti-dimensional databasesData warehouseAlgorithm
The invention discloses a character string value domain segmenting method and a character string value domain segmenting device which are applied to the field of data warehouse integration. The method comprises the following steps: extracting character strings with the maximal ASCII (American Standard Code for Information Interchange) code value and the minimal ASCII code value in a data primary key to be extracted; converting the character strings into big integers by weight expansion sum according to the ASCII code values and a preset scale cardinal number to form a range to be segmented; solving a range difference; performing equal segmenting on the range to be segmented according to the range difference and a preset segmenting number to obtain a segmenting step length so as to obtain big integers corresponding to segmenting nodes; reducing the big integers corresponding to the segmenting nodes into segmenting node character strings by adopting an Euclidean algorithm; generating a plurality of data extracting statements according to the segmenting node character strings to realize multithreaded accelerated extracting. The method is also optimized, namely, a reduced scale cardinal number is adopted in the processes of the weight expansion sum and the Euclidean algorithm. According to the method and the device, the concurrency and the high efficiency in a data transmission process are greatly improved.
Owner:ALIBABA GRP HLDG LTD
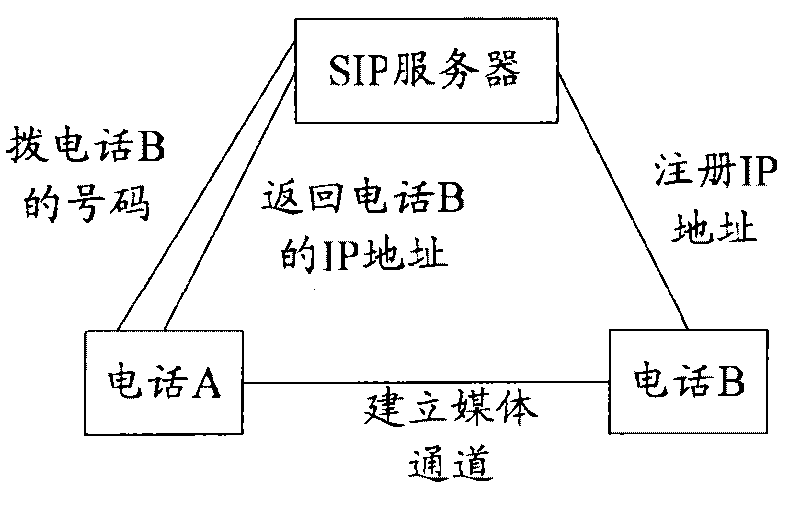
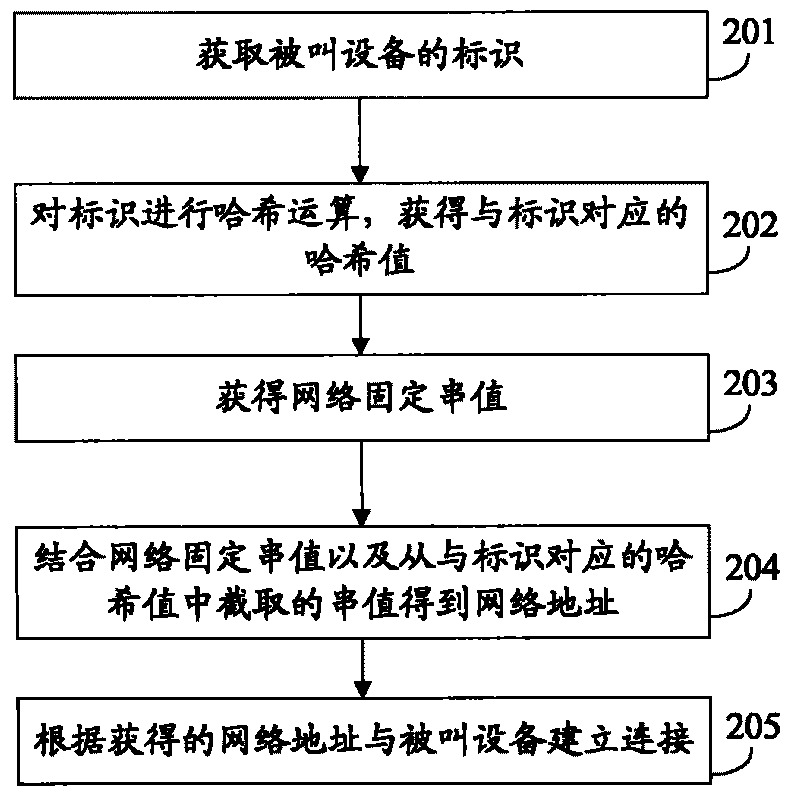
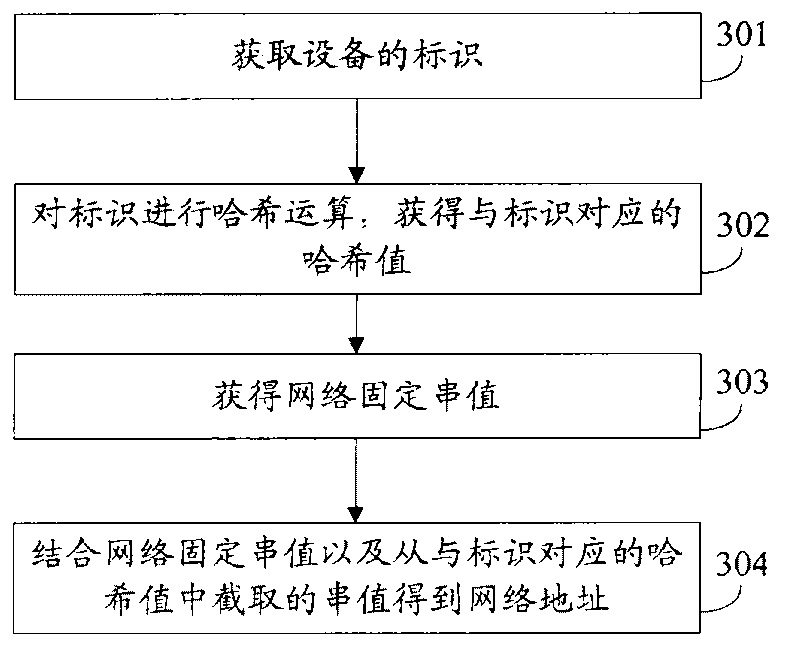
Communication method, network address acquisition method and network apparatus
InactiveCN101753631AReduce operating costsReduce resource consumptionInterconnection arrangementsTransmissionResource consumptionNetwork addressing
The invention discloses a communication method, a network address acquisition method and a network apparatus, relating to the technical field of communication, wherein the communication method comprises the following steps: acquiring an identifier of a called apparatus, wherein the mark is exclusively corresponding to the called apparatus; implementing HASH operation on the identifier to acquire a HASH value corresponding to the identifier; acquiring a network fixed string value; resulting in a network address by combining the network fixed string value with a string value intercepted in the HASH value; and establishing connection between the network address and the called apparatus; by using the technical proposal provided by the embodiment of the invention, the address of the called apparatus can be acquired without a server to communicate with the called apparatus, thereby lowering operational cost and resource consumption.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Method and system for status of application storing by using mobile communication terminal
Disclosed is a method for executing an application by using a mobile communication terminal and storing both a parameter (application parameter) of the application being executed and a status (application status) of the application, which includes the steps of: (a) if a user of the mobile communication terminal selects the application in the mobile communication terminal, determining by the mobile communication terminal if the application needs wireless network access; (b) if the application needs the wireless network access, accessing by the mobile communication terminal an application-providing server, searching for the application from an application database, and downloading the application; (c) if the application does not need the wireless network access, setting and checking the application parameter necessary for the executed application; (d) determining if it is necessary to perform shortcut storage for the application parameter and the application status; (e) if it is necessary to perform the shortcut storage for the application parameter and the application status, generating a single string value corresponding to the application parameter and the application status, and performing the shortcut storage; and (f) if it is not necessary to perform the shortcut storage for the application parameter and the application status, using a service provided by the application and terminating the application.
Owner:SK PLANET CO LTD
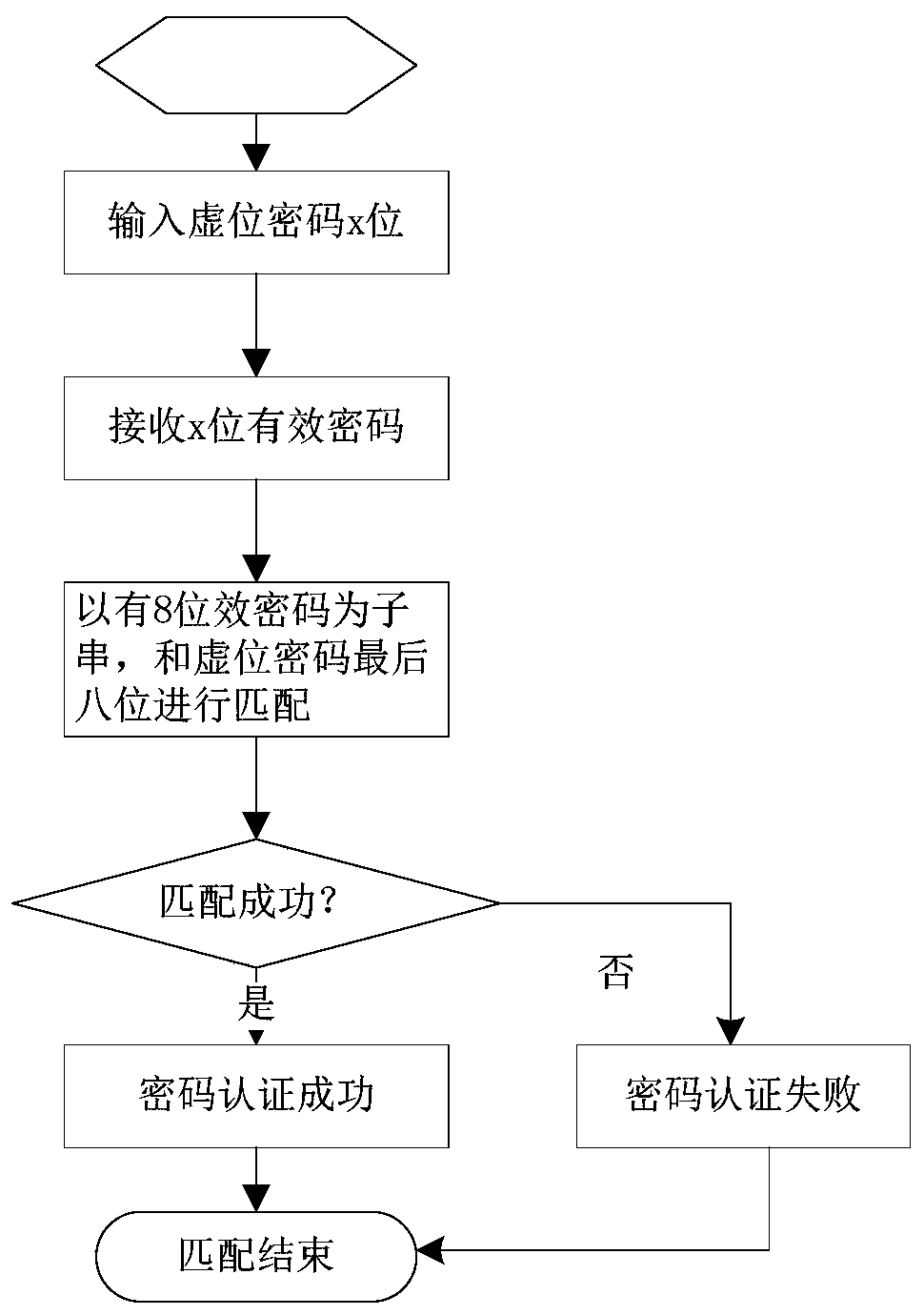
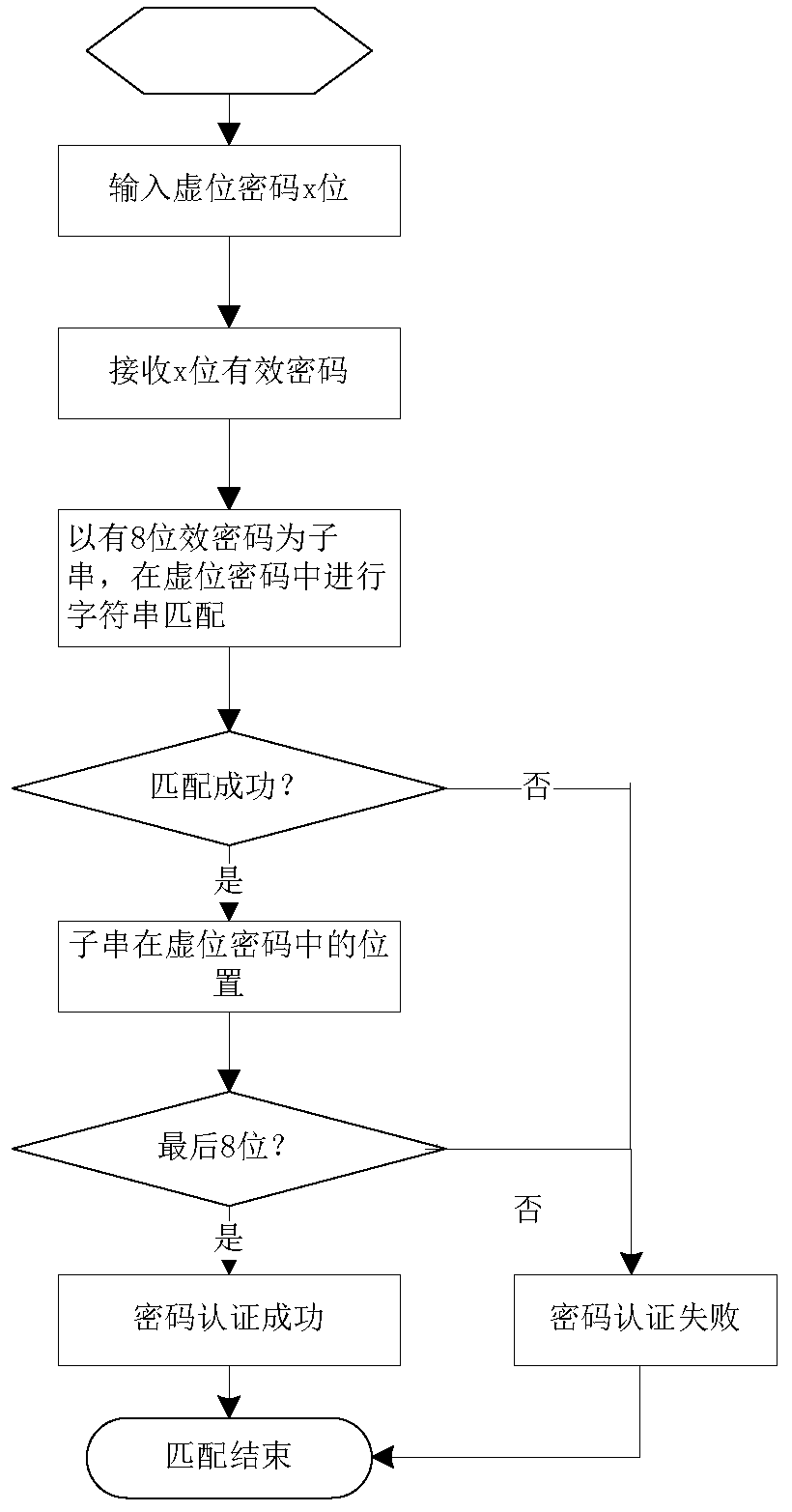
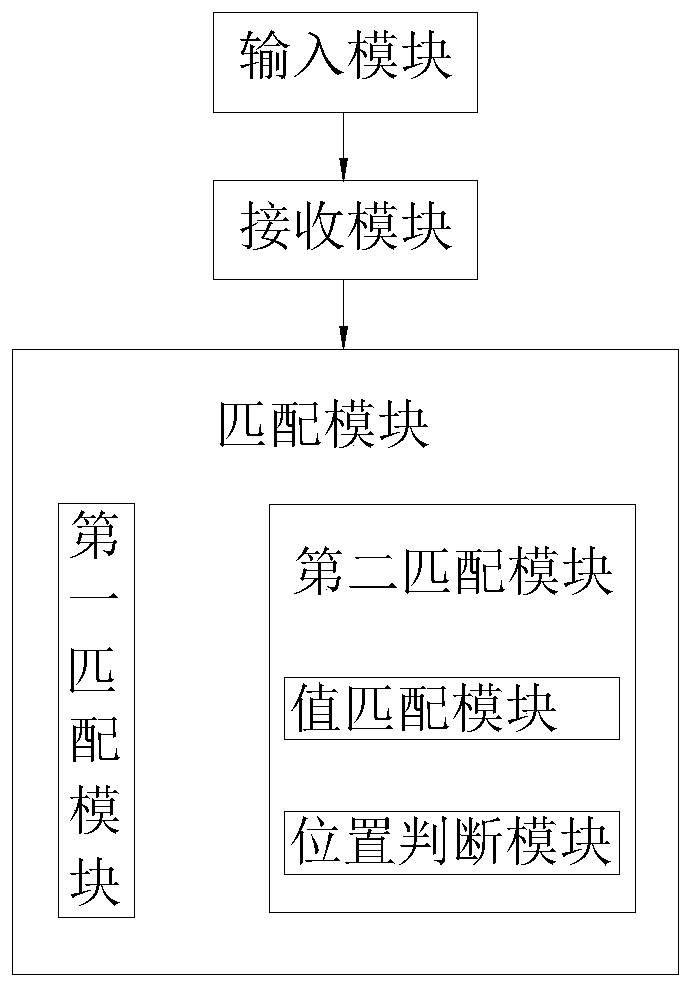
Virtual password security processing method and system
The invention discloses a virtual bit password security processing method. The method comprises the following steps: S1, inputting an x-bit virtual bit password; S2, receiving an x-bit virtual password; and S3, taking the y-bit effective password as a substring, carrying out character string matching in the received x-bit virtual password, and if the value of the substring and the position in thevirtual password are successfully matched, indicating that the password authentication is successful and ending, otherwise, indicating that the password authentication is failed and ending. The invention also discloses a virtual password security processing system. In the invention, the position of the correct password character string in the virtual bit password is fixed, so that in the passwordauthentication process, not only the character string value but also the position matching need to be carried out, and the password authentication is successful only if the character string value andthe position matching are successful. Therefore, in the trial and error cracking process of the password, the correct password needs to be found, the position of the correct password in the virtual password needs to be found, and the trial and error cracking difficulty is undoubtedly and greatly increased.
Owner:广州技象科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com