Virtual password security processing method and system
A technology of password security and processing method, which is applied in the field of virtual password security processing method and system, and can solve problems such as trial and error cracking passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
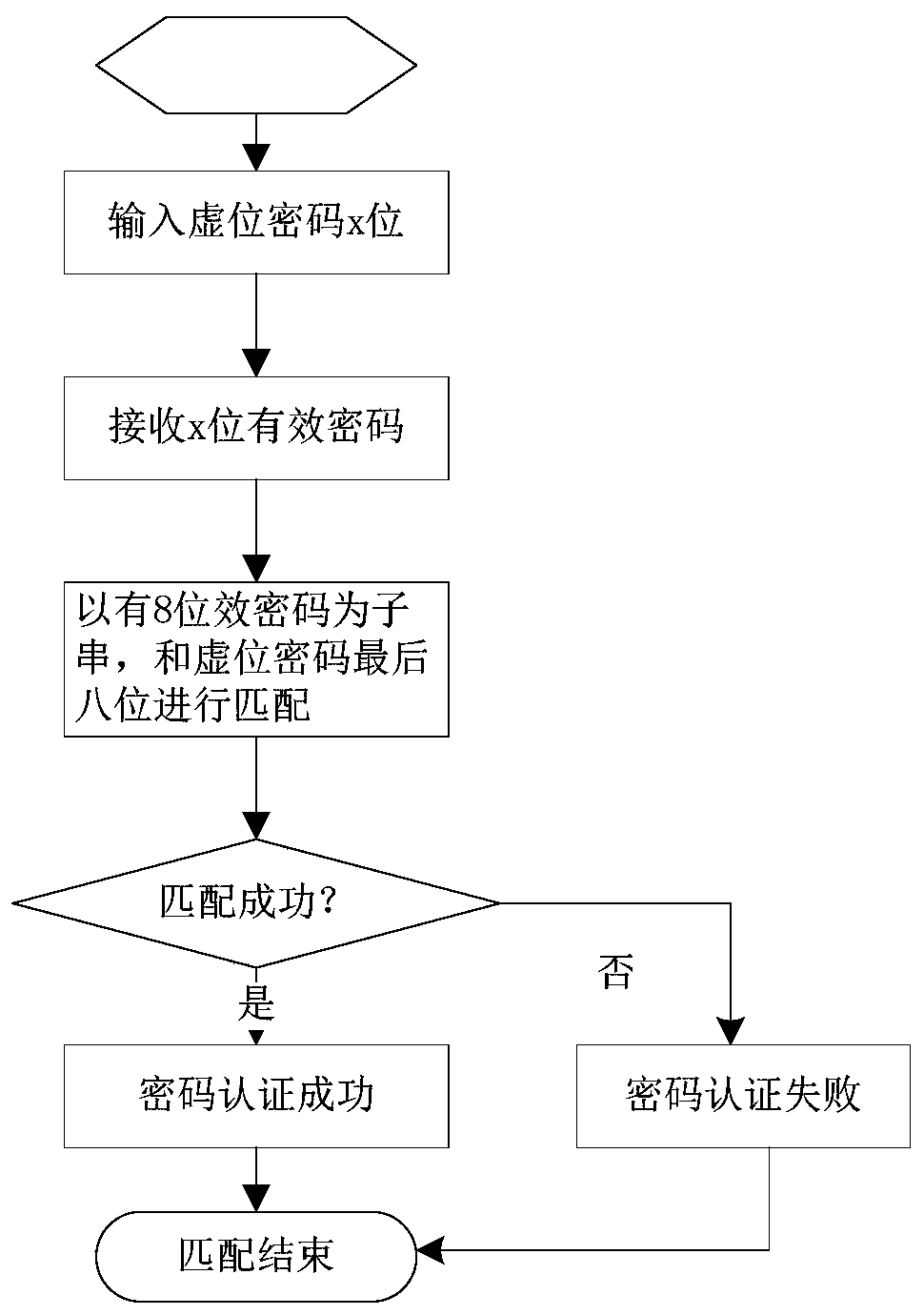
[0041] Such as figure 1 As shown, a virtual bit password security processing method comprises the following steps:
[0042] S1. Enter the x-digit dummy password;
[0043] S2. Receive the x-digit dummy password;
[0044] S3. Use the valid password of y digits as the substring, and perform character string matching in the received dummy password of x digits. If both the value of the substring and the position in the dummy password are successfully matched, the password authentication is successful and ends. Otherwise, Password authentication failed, end; where, x, y are both positive integers, y<x.
[0045] In the present invention, the position of the correct password string in the dummy password is fixed. Therefore, in the process of password authentication, not only the matching of the string value but also the matching of the position is required. Only when both are successfully matched can the password be authenticated. success. Therefore, in the process of password cra...
Embodiment 2
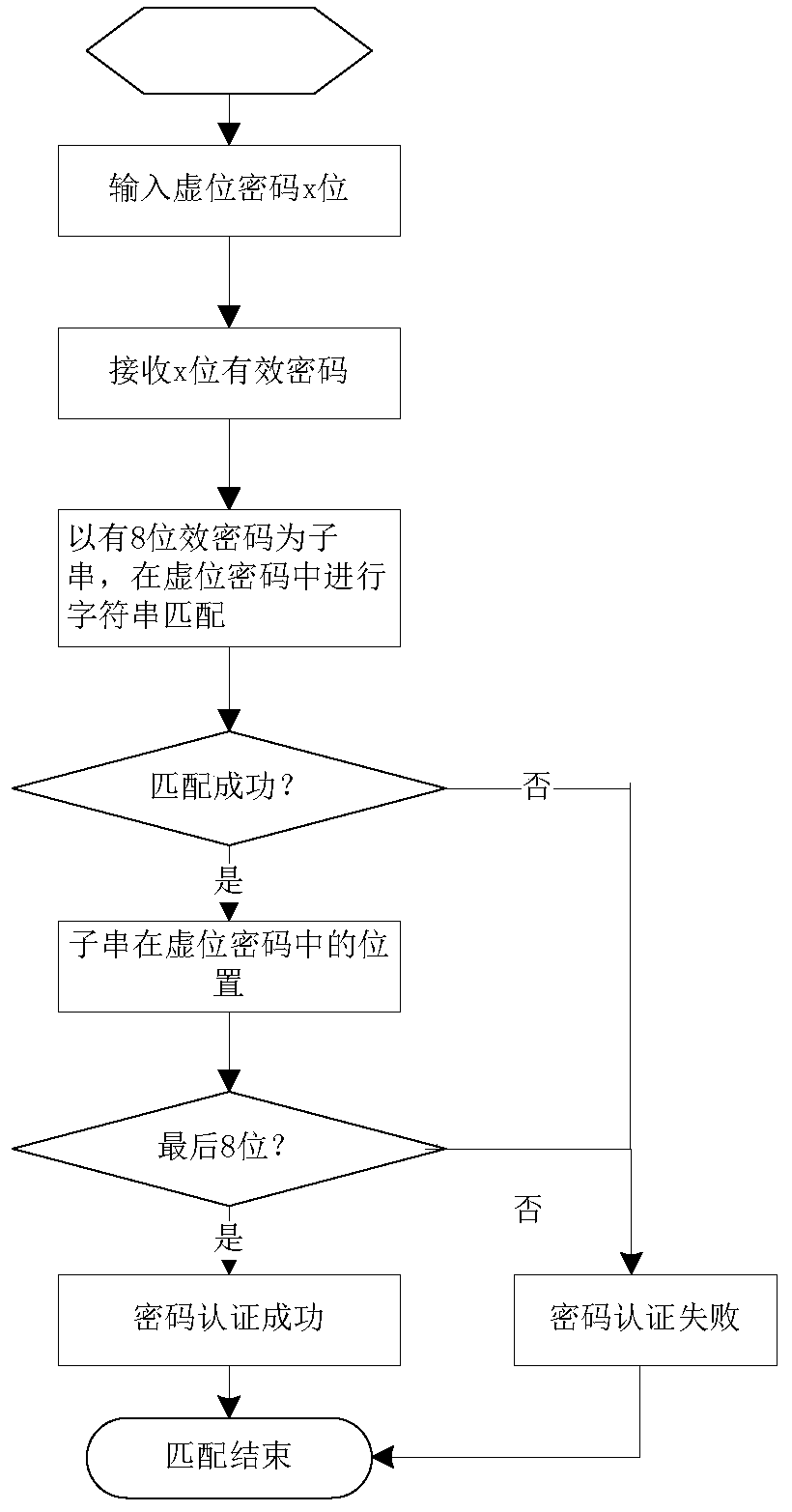
[0052] Such as figure 2 As shown, a virtual bit password security processing method comprises the following steps:
[0053] S1. Enter the x-digit dummy password;
[0054] S2. Receive the x-digit dummy password;
[0055] S3. Use the valid password of y digits as the substring, and perform character string matching in the received dummy password of x digits. If both the value of the substring and the position in the dummy password are successfully matched, the password authentication is successful and ends. Otherwise, Password authentication failed, end; where, x, y are both positive integers, y<x.
[0056]In the present invention, the position of the correct password string in the dummy password is fixed. Therefore, in the process of password authentication, not only the matching of the string value but also the matching of the position is required. Only when both are successfully matched can the password be authenticated. success. Therefore, in the process of password cra...
Embodiment 3
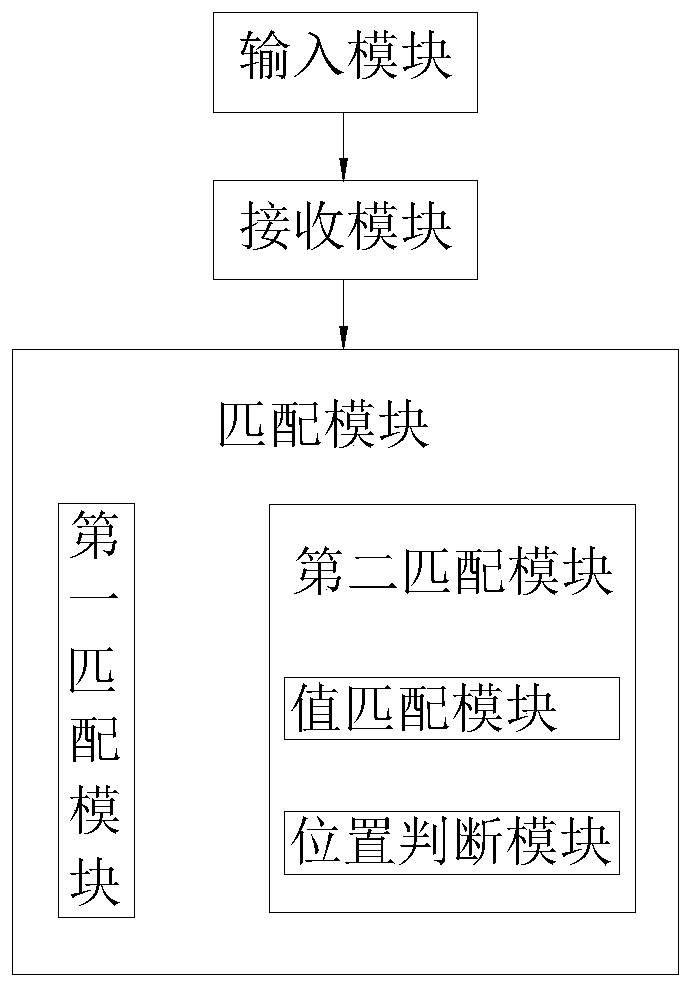
[0064] Such as image 3 As shown, a virtual bit password security processing system includes:
[0065] The input module is used to input the x-digit dummy password;
[0066] The receiving module is used to receive the x-digit dummy password;
[0067] The matching module is used to use the y-digit valid password as a substring to perform string matching in the received x-digit dummy password. If the value of the substring and the position in the dummy password all match successfully, the password authentication is successful, and the end , otherwise, the password authentication fails and ends; where, x and y are both positive integers, and y
[0068] In this embodiment, the position of the correct password string in the dummy password is fixed. Therefore, in the process of password authentication, not only the matching of the string value, but also the matching of the position is required. Authentication succeeded. Therefore, in the process of password cracking by trial ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com