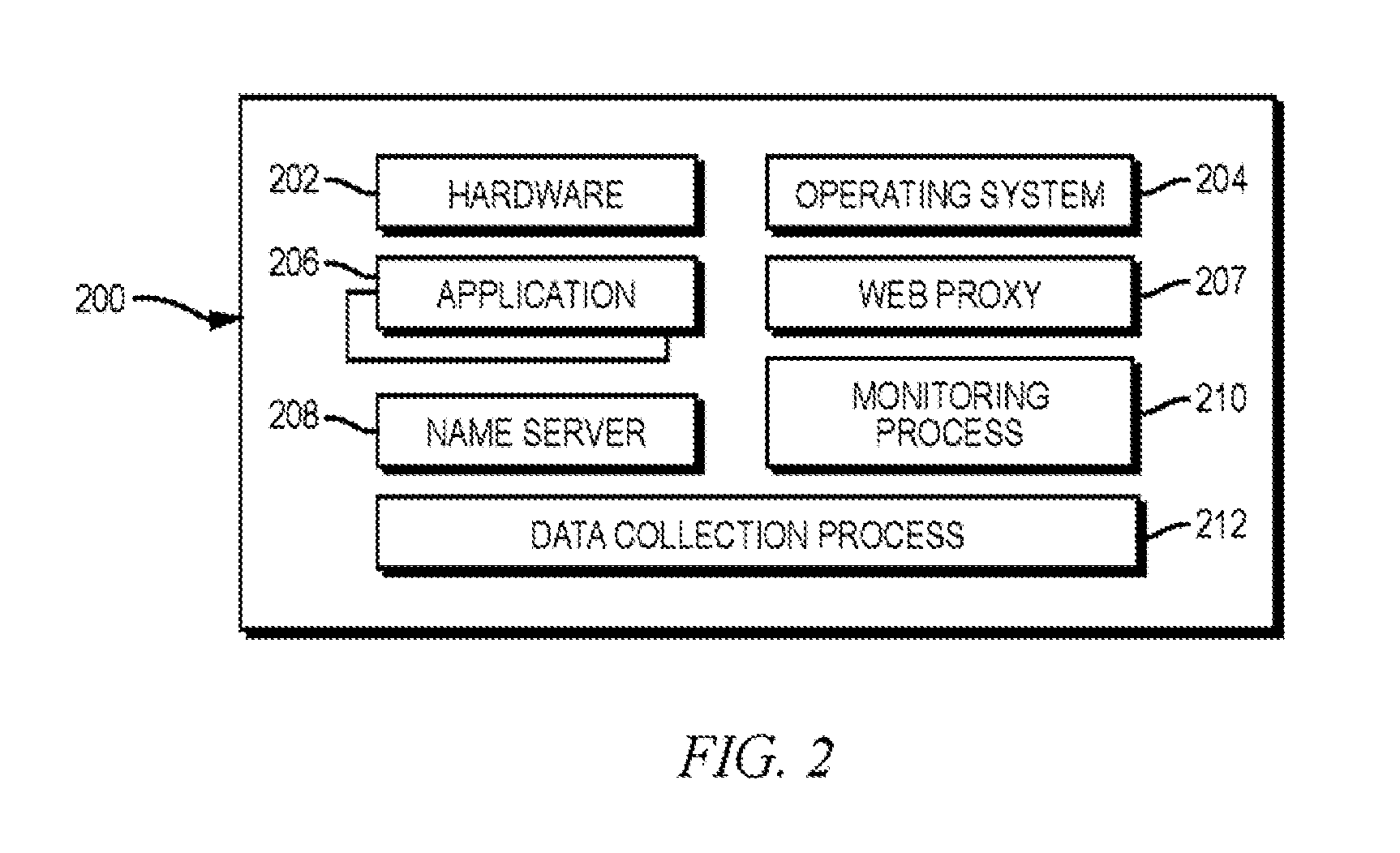
Patents
Literature
84 results about "Late binding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
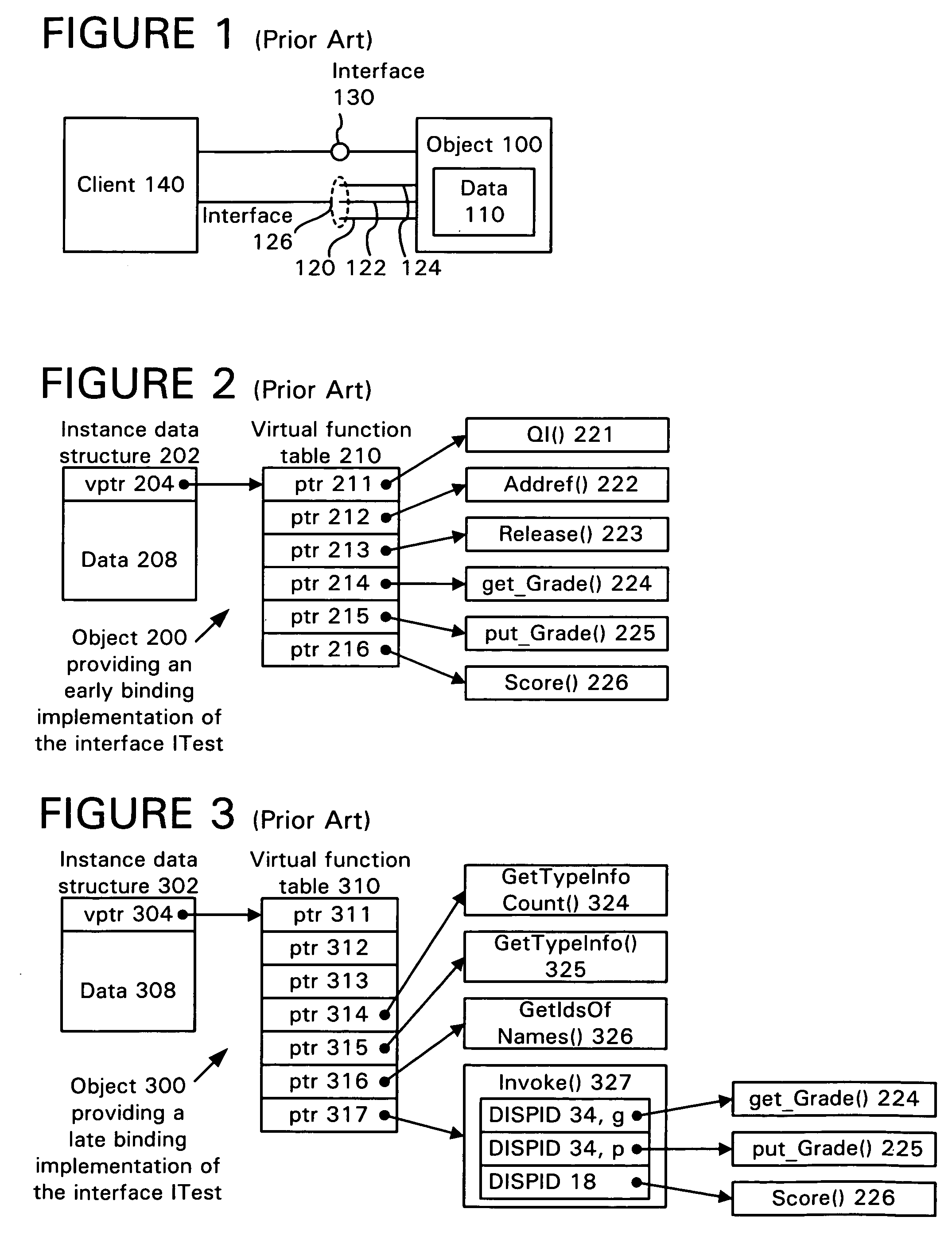
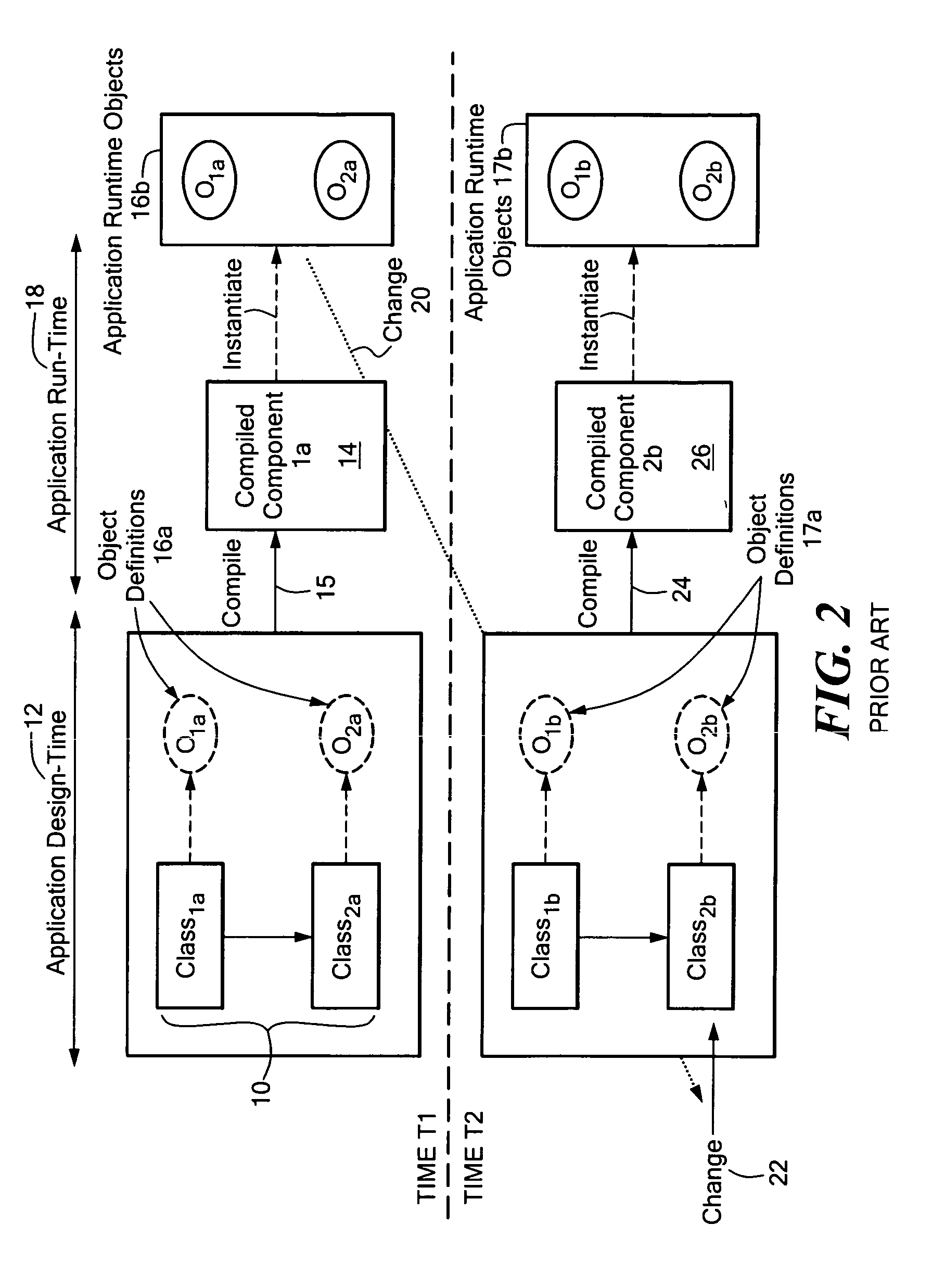
Late binding, dynamic binding, or dynamic linkage is a computer programming mechanism in which the method being called upon an object or the function being called with arguments is looked up by name at runtime.
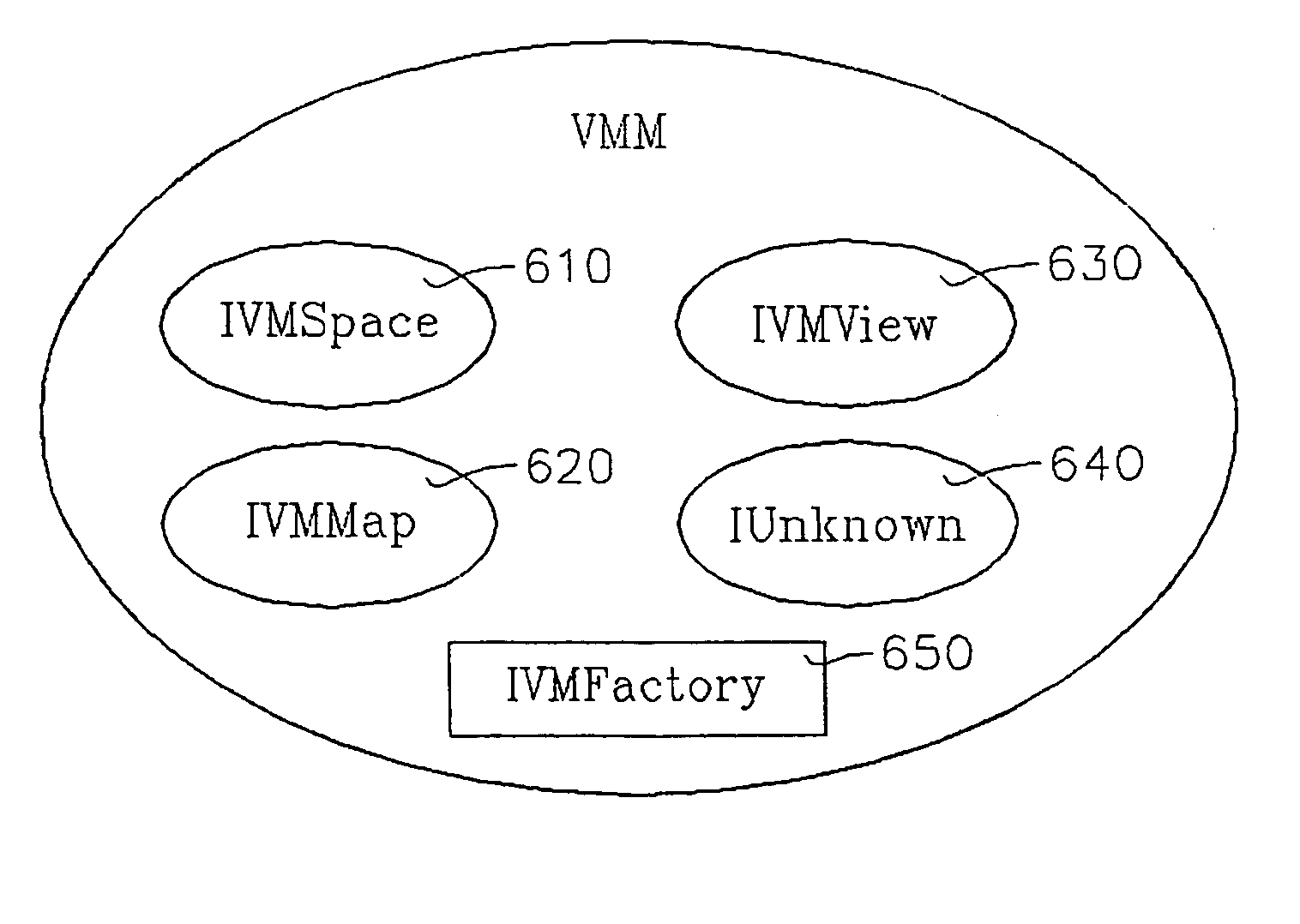
Late binding tokens
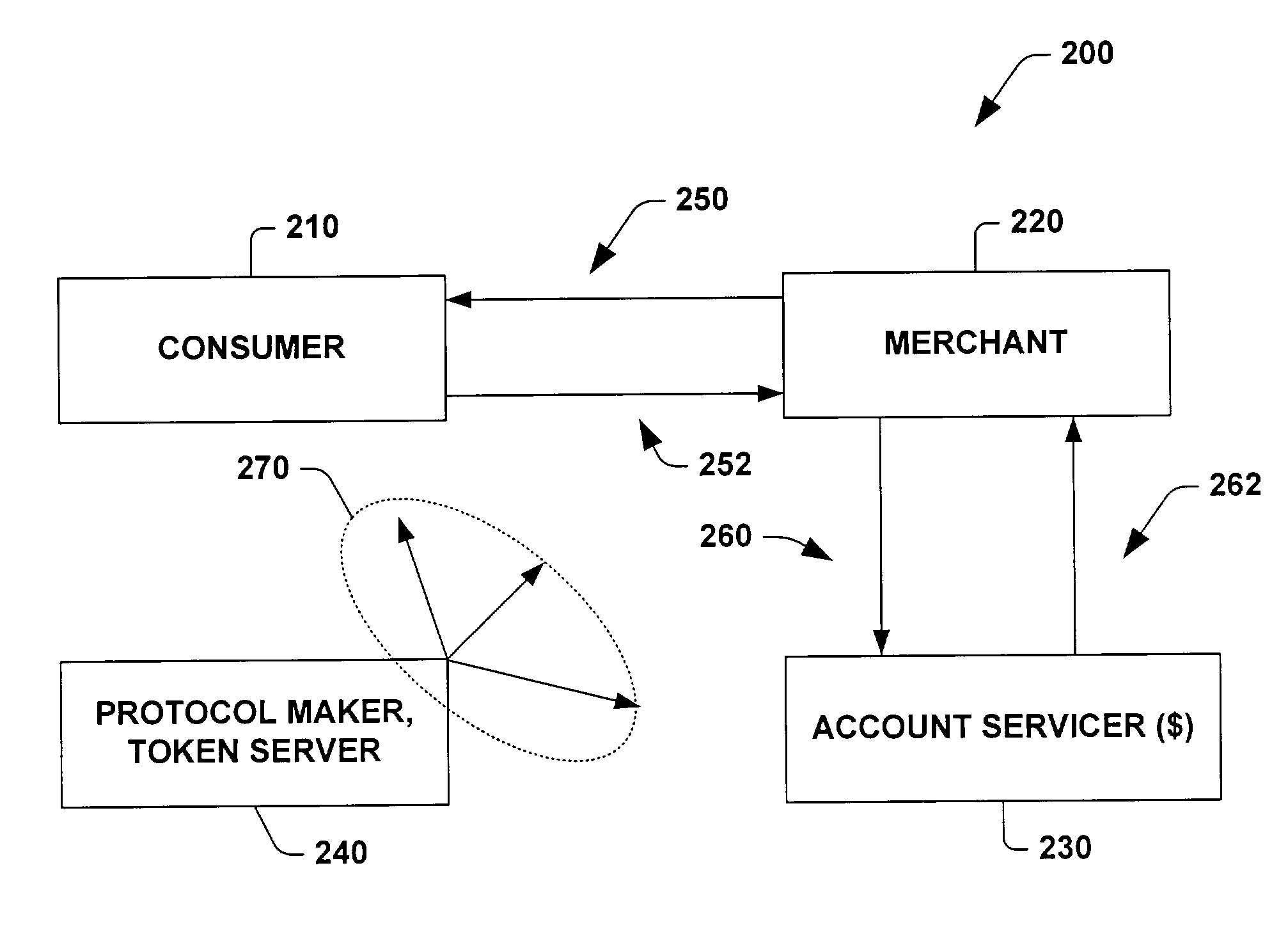
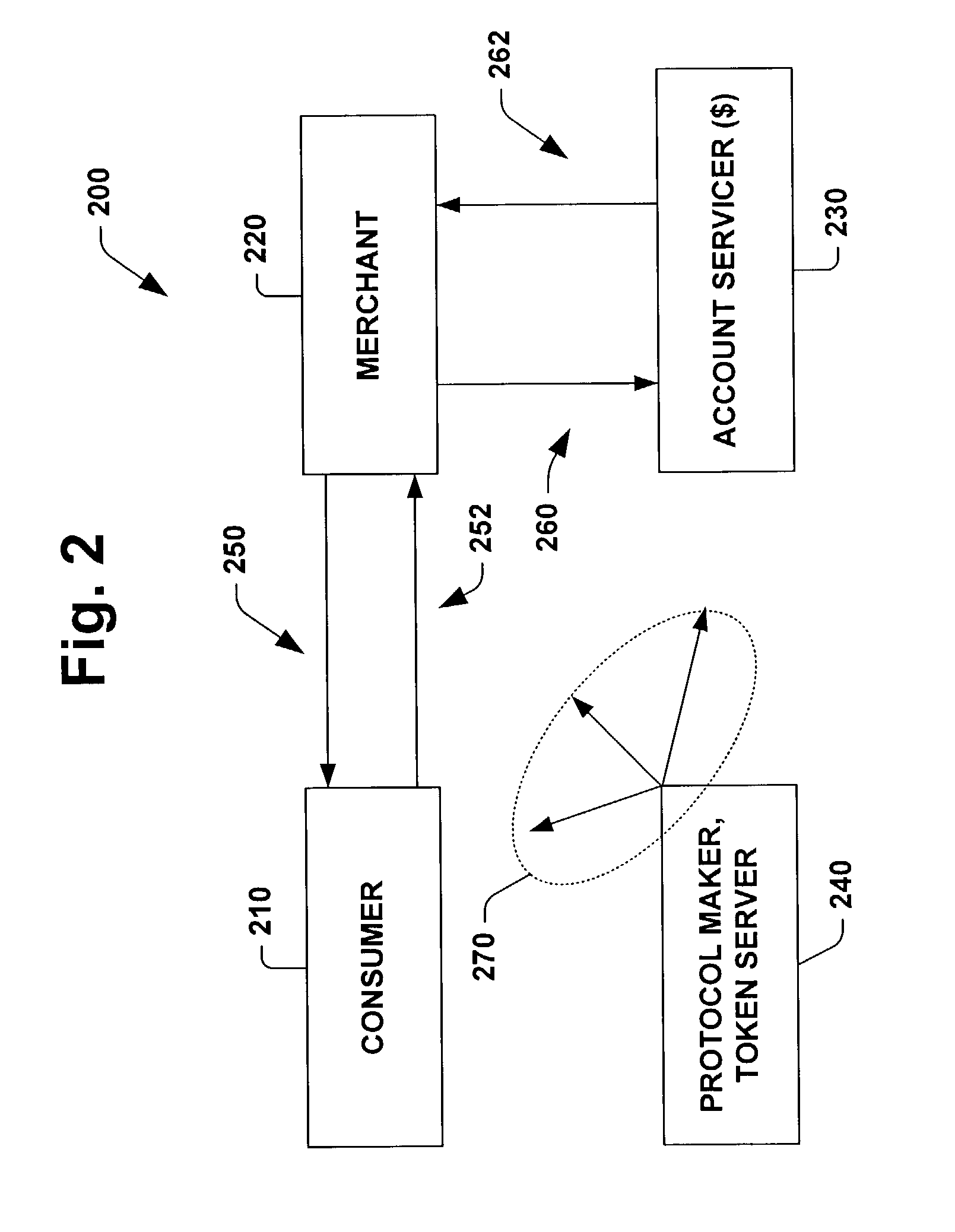
ActiveUS8060448B2Easy to createPrecise positioningFinanceMultiple digital computer combinationsClient-sideProtocol for Carrying Authentication for Network Access
A system for verifying intent in a card not present transaction is provided. The system includes a late binding token that is distributable to consumers without necessarily being bound to an account. The system also includes a client software that locates a token server configured to facilitate managing and communicating with the late binding token. The system also includes a protocol concerning how to build a verifiably secure structured proposal that carries an offer to the consumer through the client software.
Owner:JONES THOMAS C
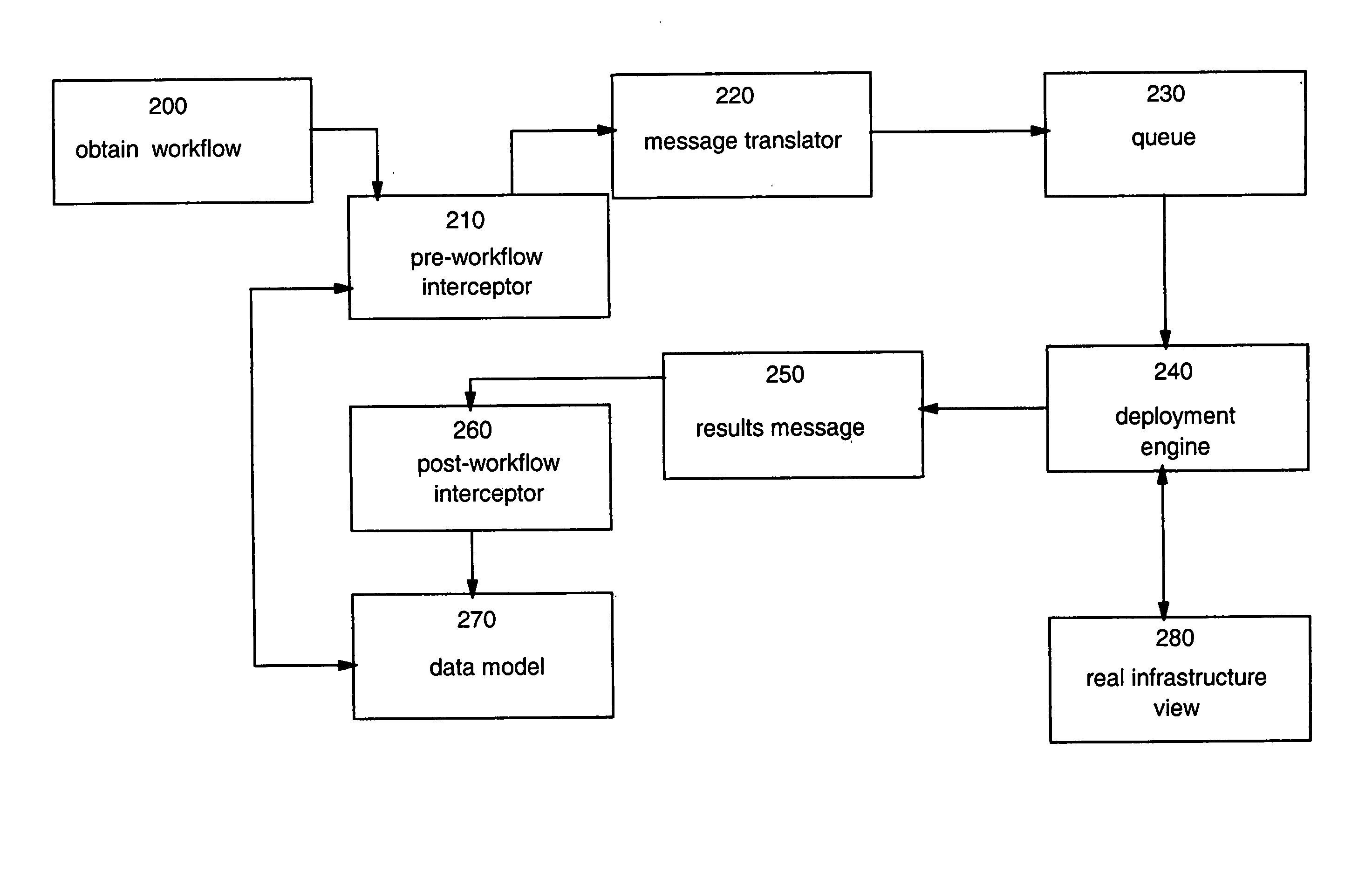
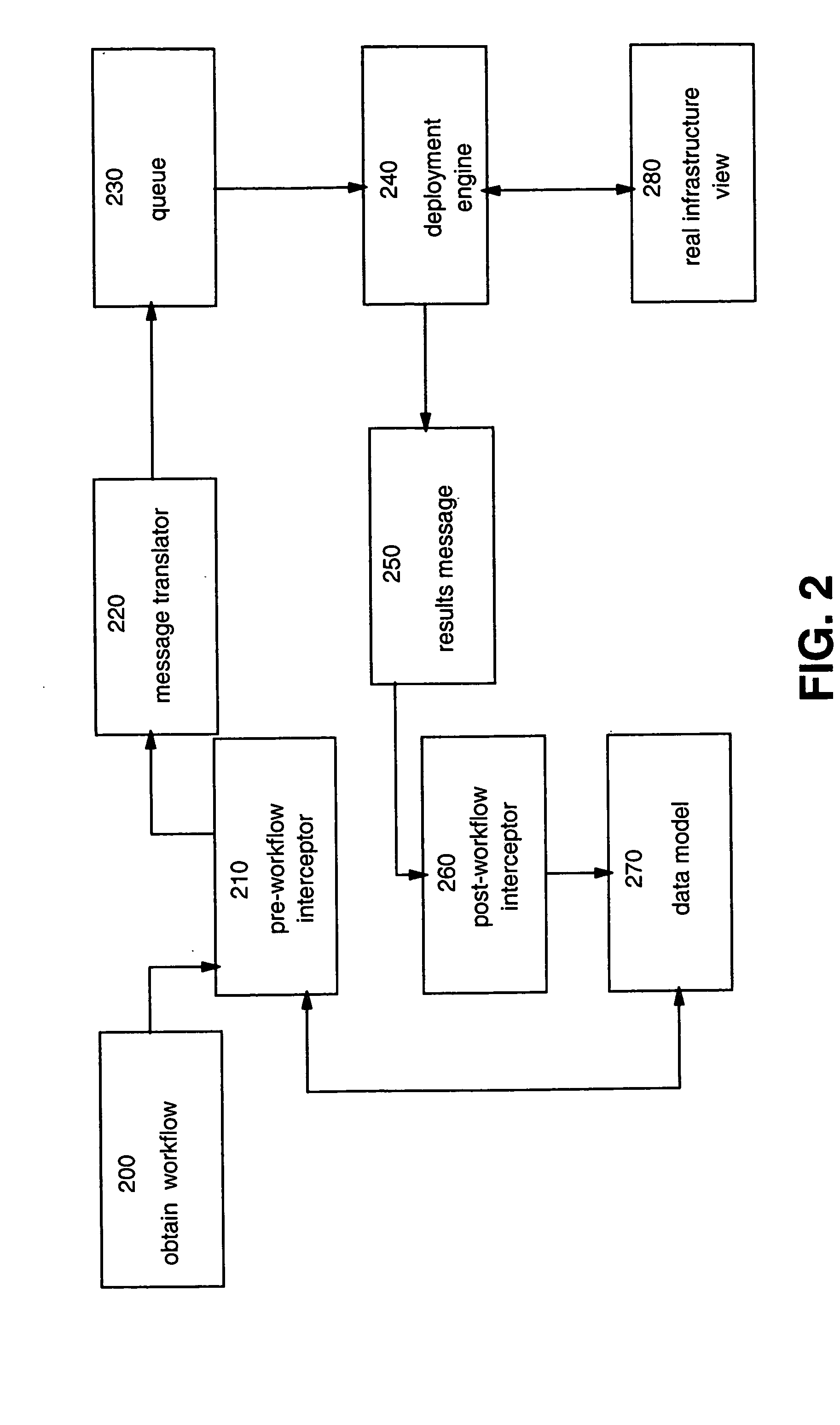
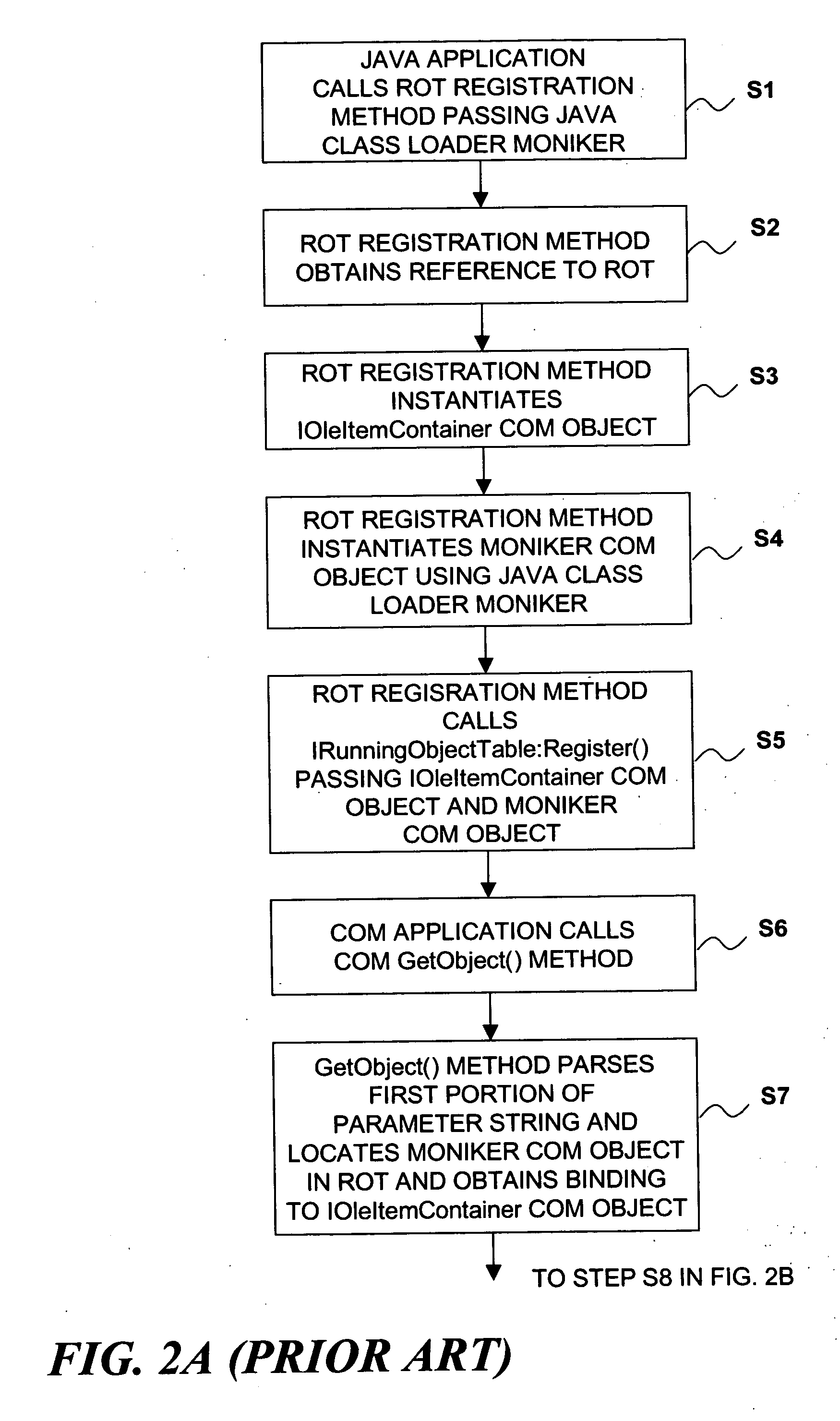
Binding a workflow engine to a data model
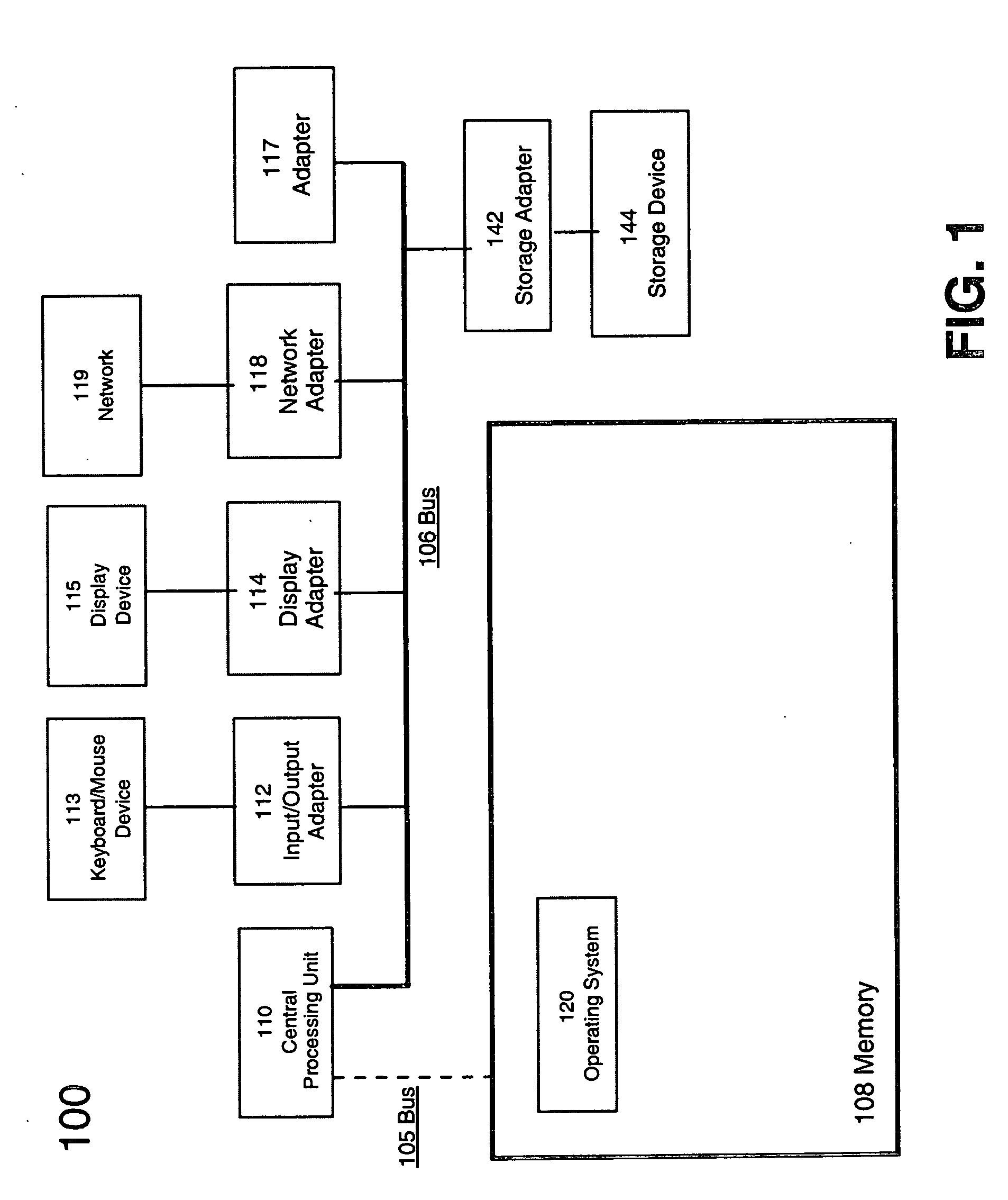
InactiveUS20050071209A1Effective flexibilityEffective resource selectionOffice automationResourcesData processing systemComputerized data processing
A method, system and program product for more effectively managing the operational complexity of computerized data processing systems using an aspect oriented technique of binding a workflow engine to a data model representing the real environment is provided. The late binding aspect of the workflow provides more effective resource selection and allows for linking to differing workflows in accordance with the data model. Further results provided by the completed workflow may also be used to augment the data model thereby assuring a more current and consistent representation is found in the data model. A synchronization aspect if provided by the workflow result being used to then synchronize the data model with the physical resources manipulated by the workflow.
Owner:IBM CORP
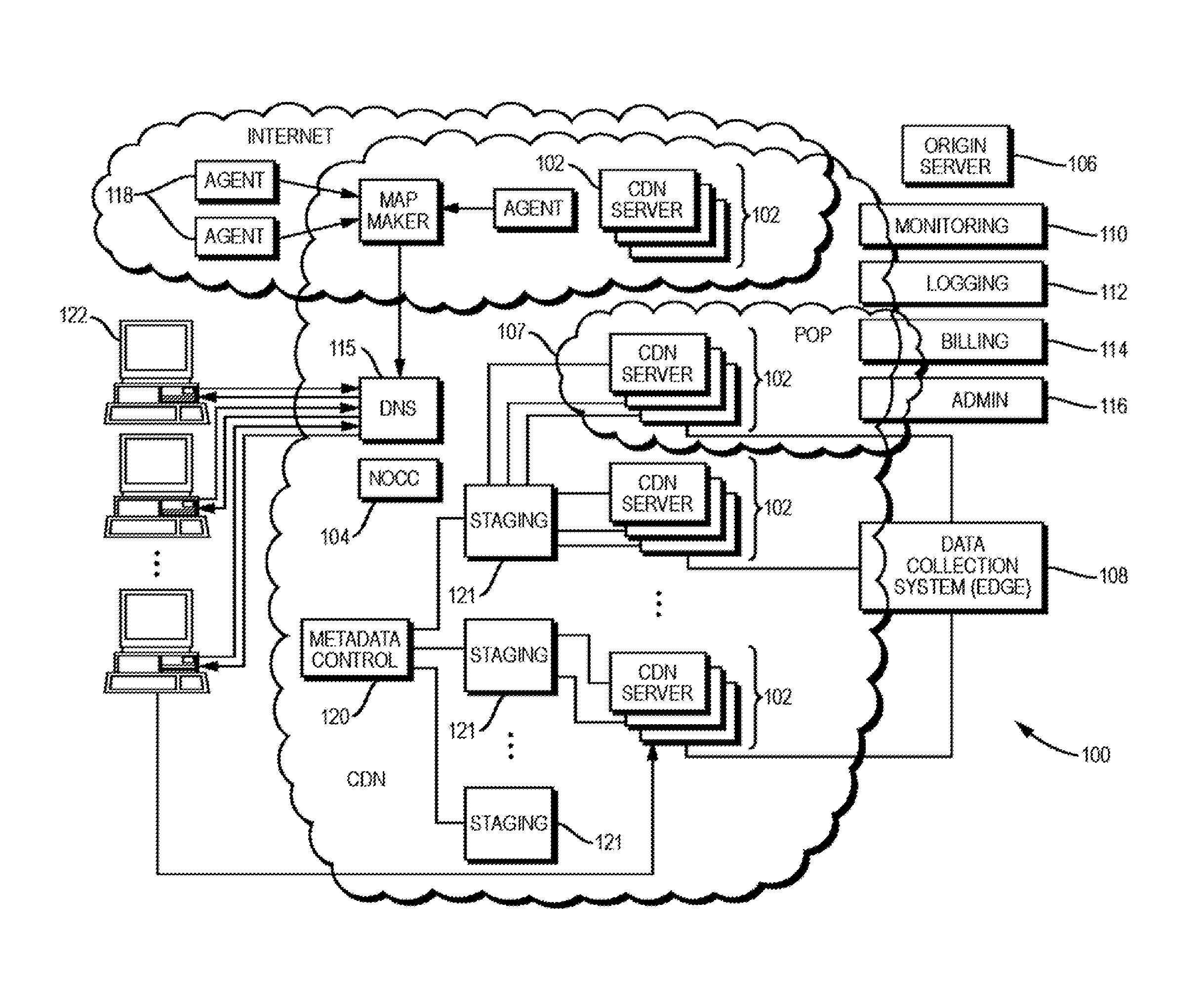
Scalable content delivery network request handling mechanism with usage-based billing
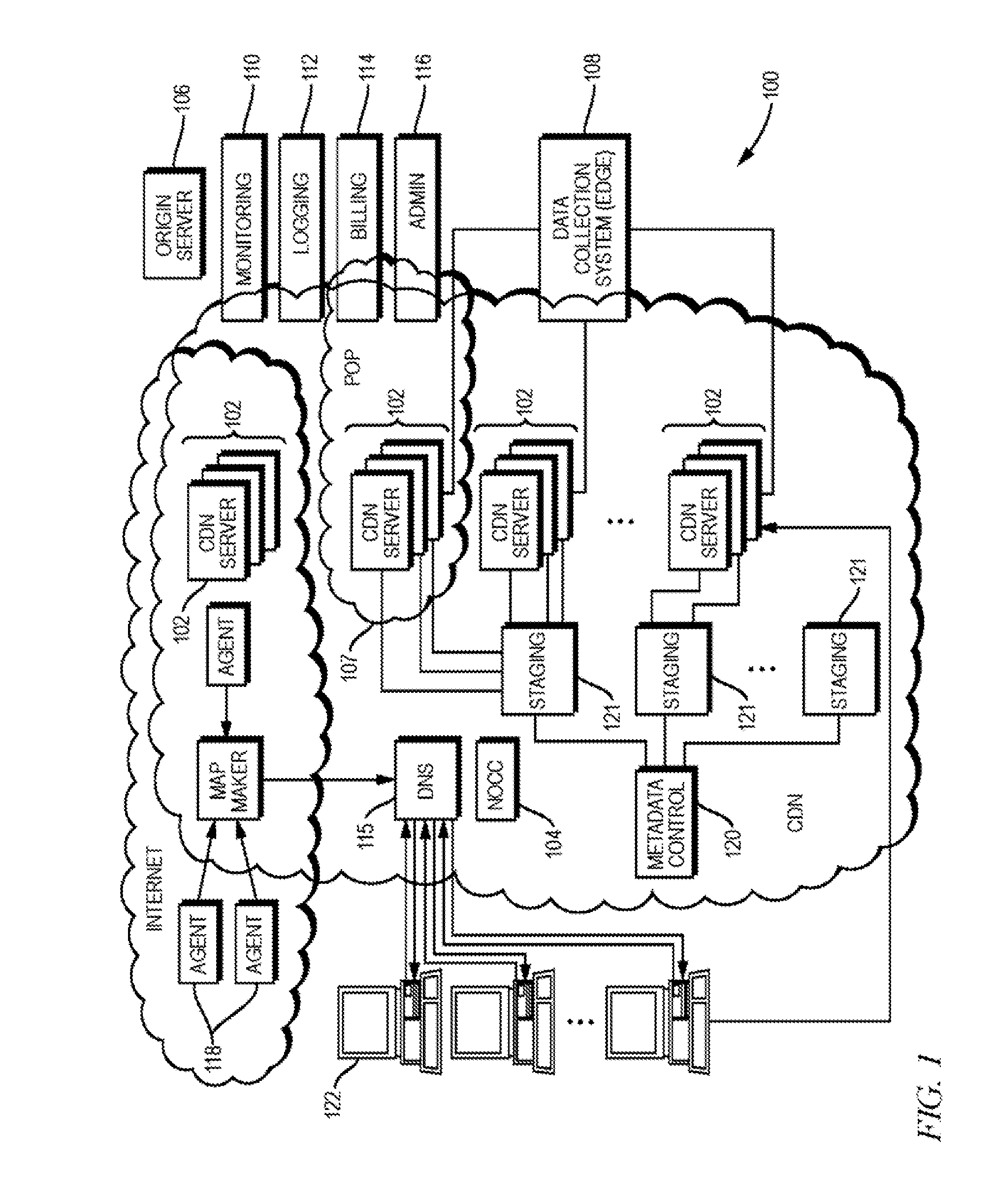
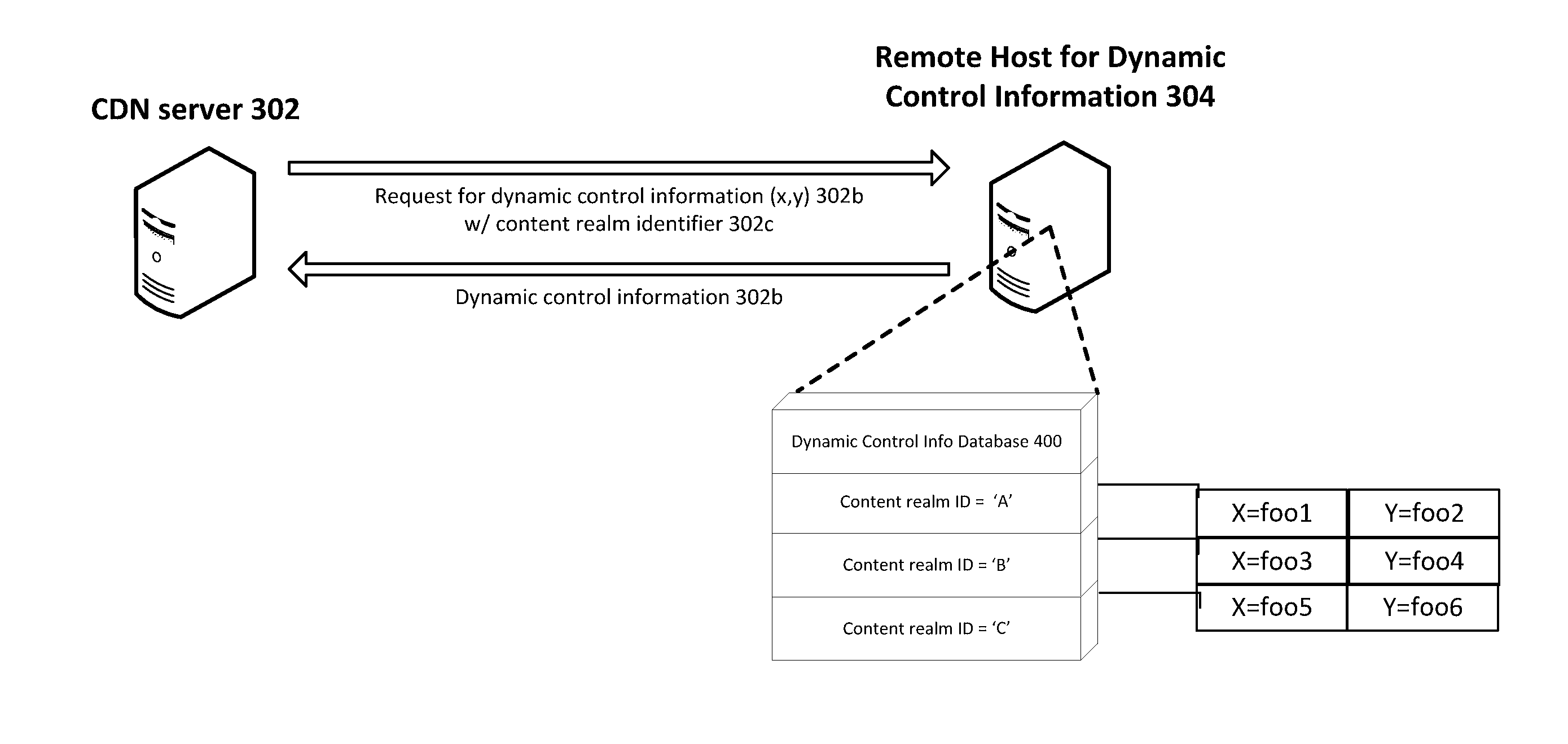
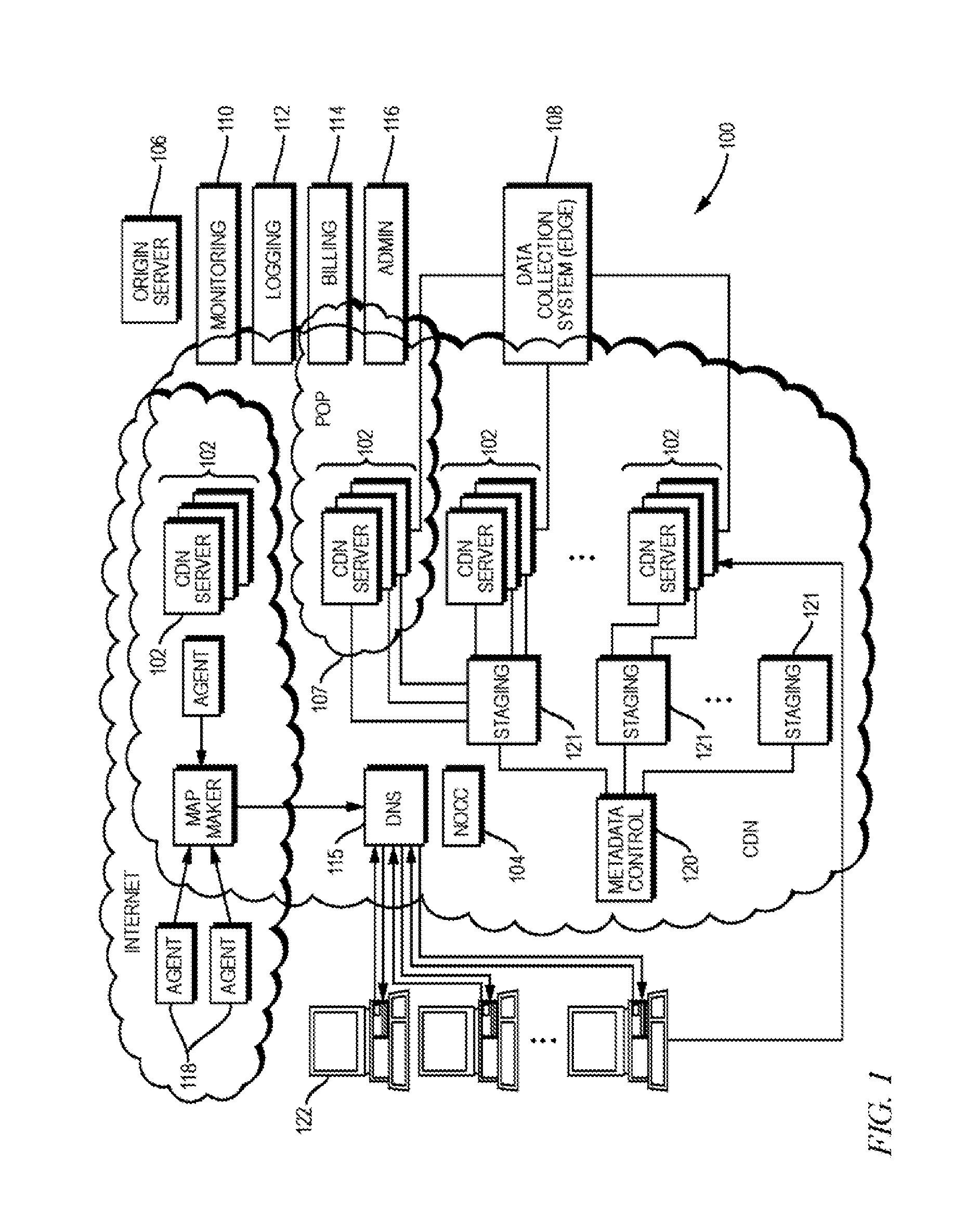
ActiveUS20140181285A1Faster and less-costlyDigital computer detailsData switching networksClient-sideLate binding
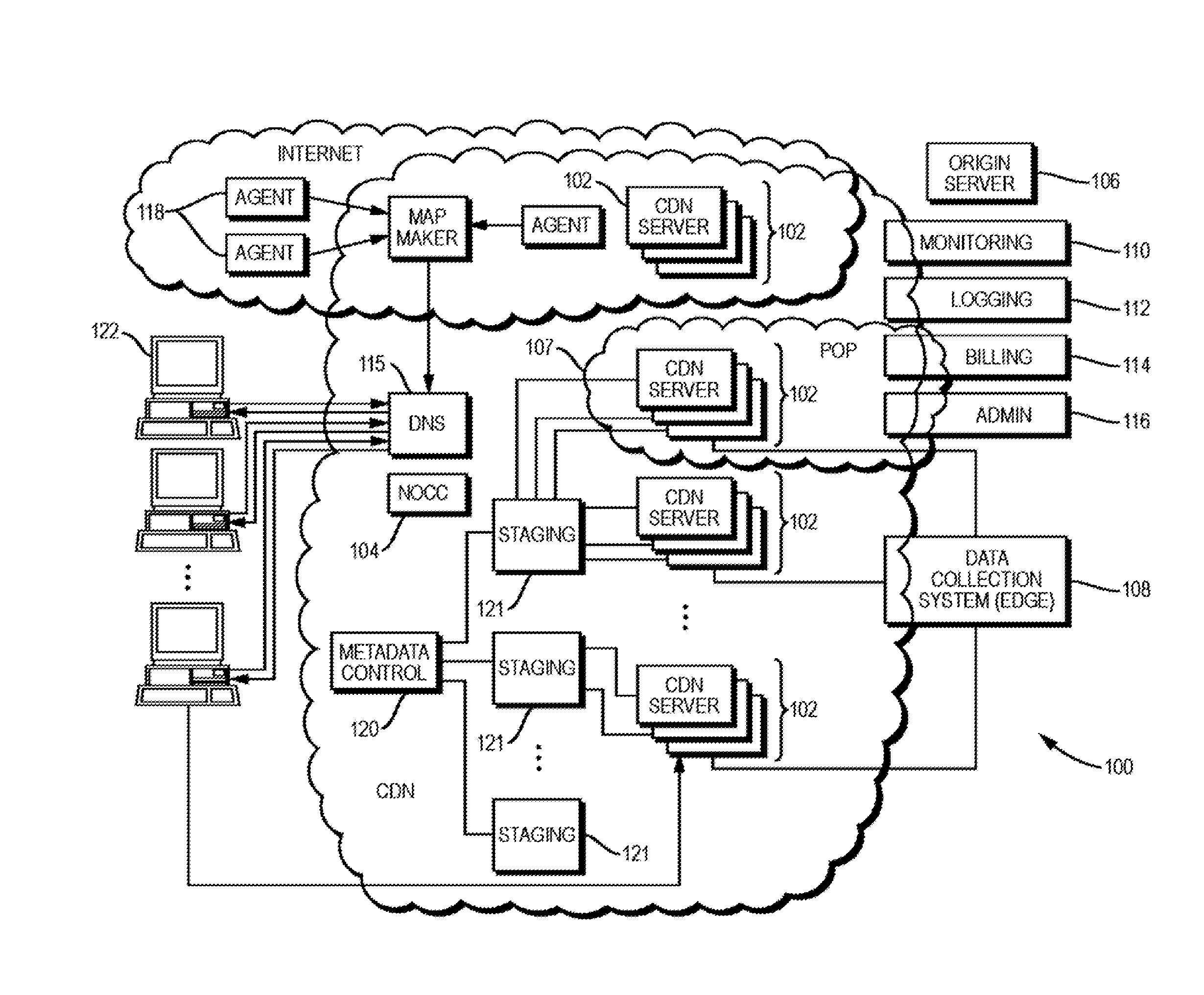
Described herein are improved systems, methods, and devices for delivering and managing metadata in a distributed computing platform such as a content delivery network (CDN) so as to configure content servers to handle client requests. The teachings hereof provide, among other things, scalable and configurable solutions for delivering and managing metadata, preferably by leveraging dynamically obtained control information. For example, in one embodiment, a given content server may store metadata, e.g., in a configuration file, that references dynamic, late-bound control information for use in satisfying dependencies. This dynamic control information can be requested by the CDN content server, typically from a remote host, when needed to parse and execute the metadata.
Owner:AKAMAI TECH INC
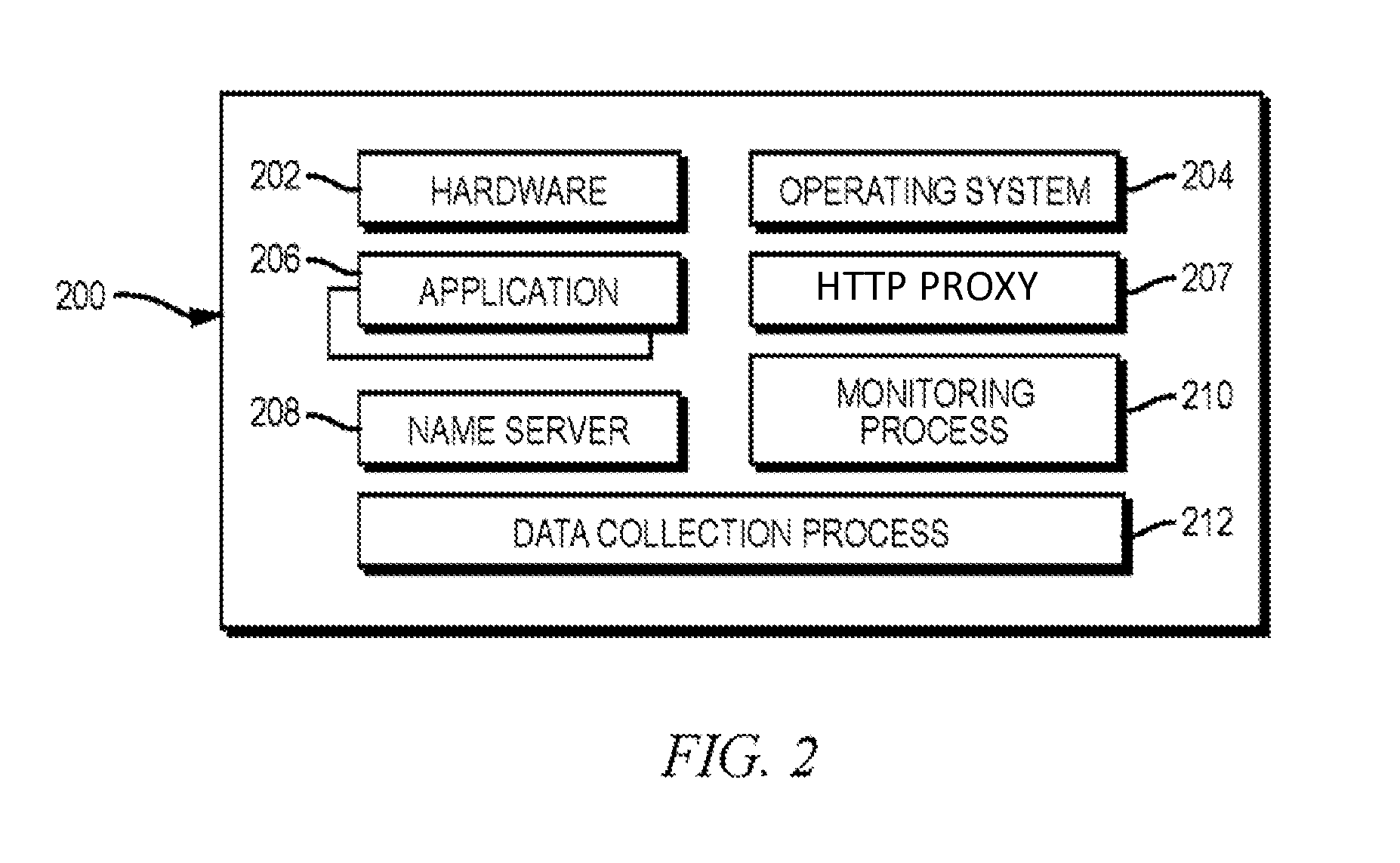
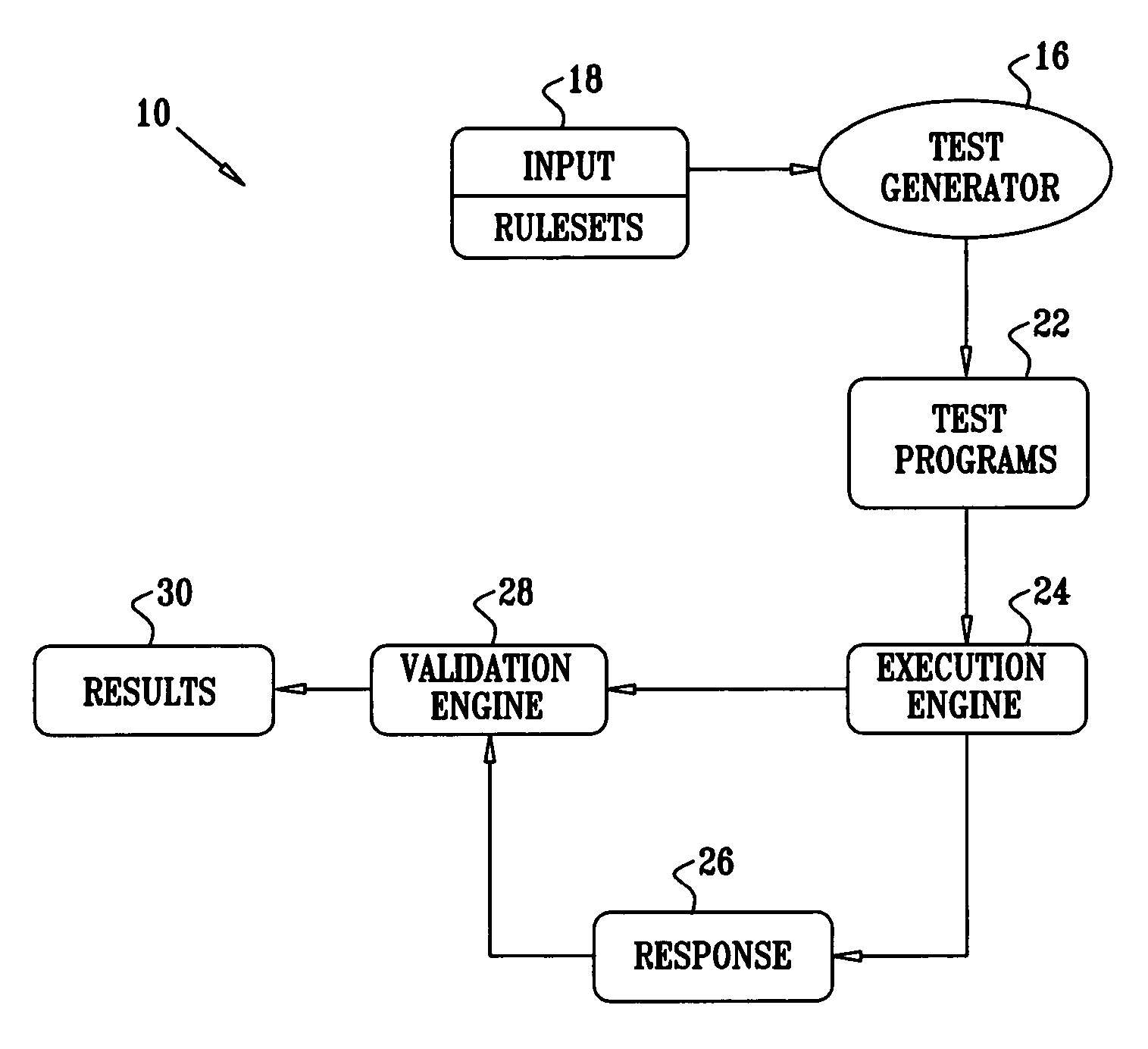
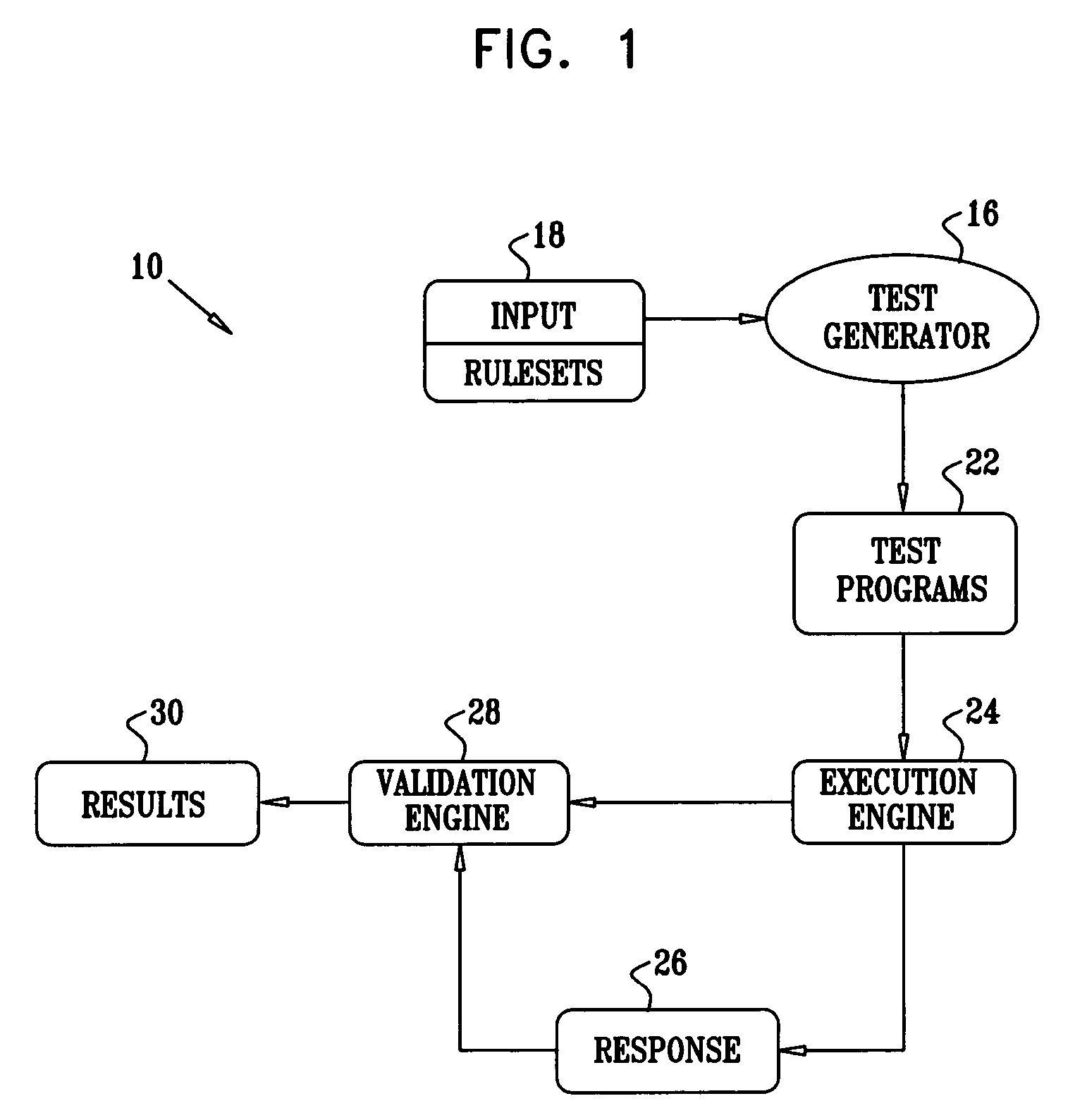
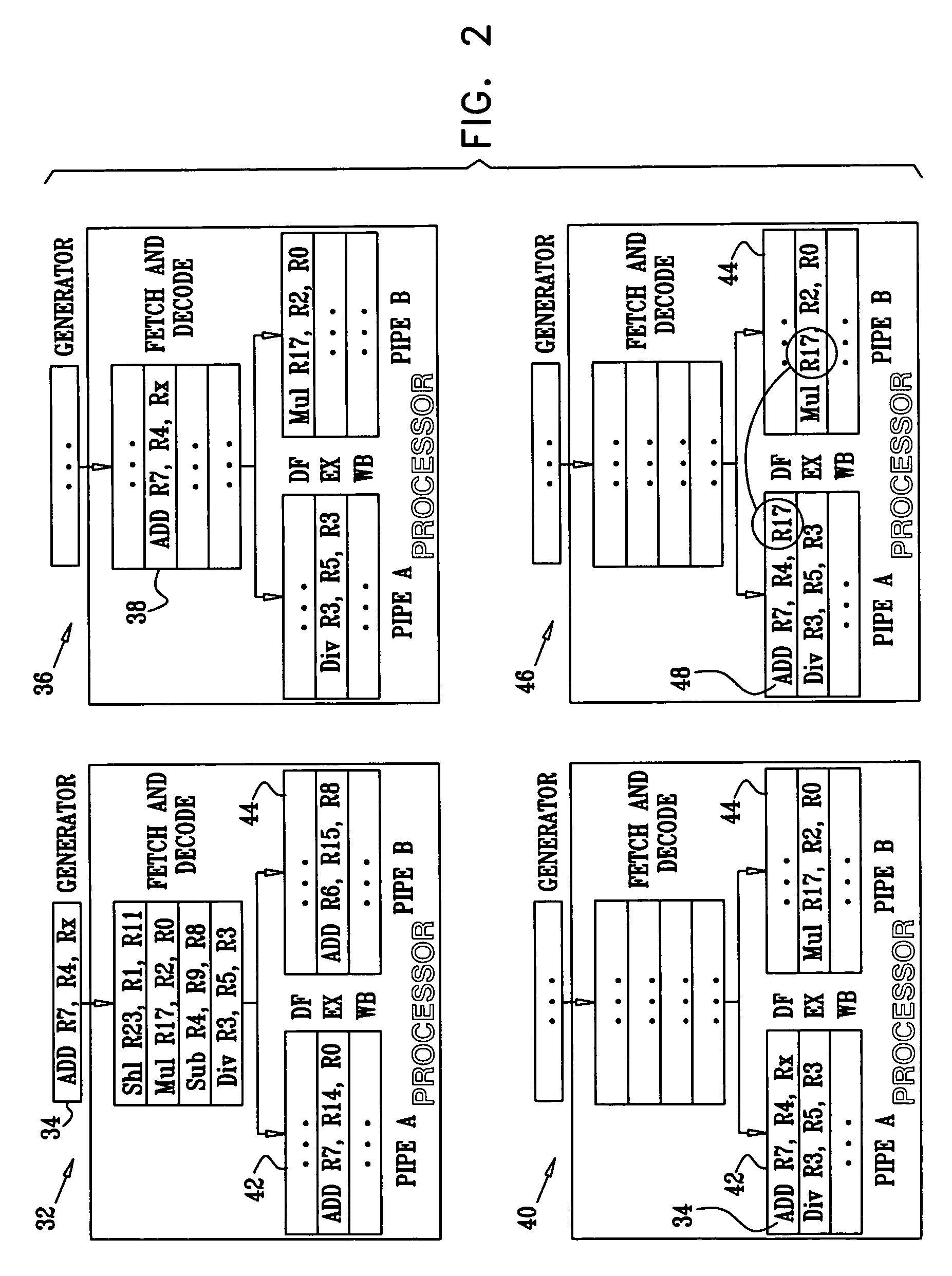
Late binding of variables during test case generation for hardware and software design verification
InactiveUS7003420B2Improves quality and rapidityPerformance penaltyResistance/reactance/impedenceCAD circuit designSoftware designTheoretical computer science
Methods and systems are provided that improve design verification by test generators by delaying assignment of values in the generated stimuli until these values are used in the design. Late binding allows the generator to have a more accurate view of the state of the design, and in order to choose correct values. Late binding can significantly improve test coverage with a reasonable performance penalty as measured by simulation time.
Owner:IBM CORP
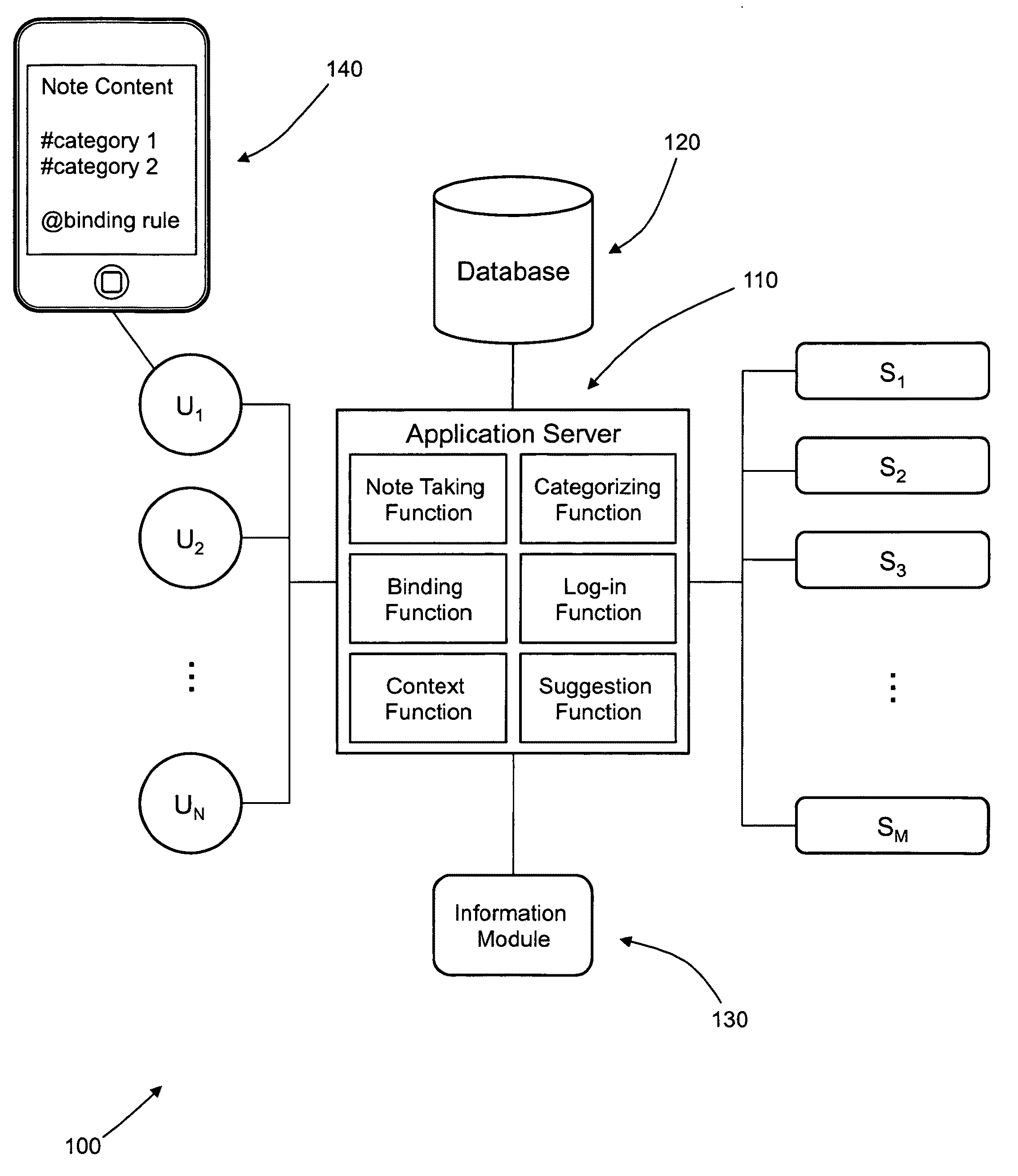
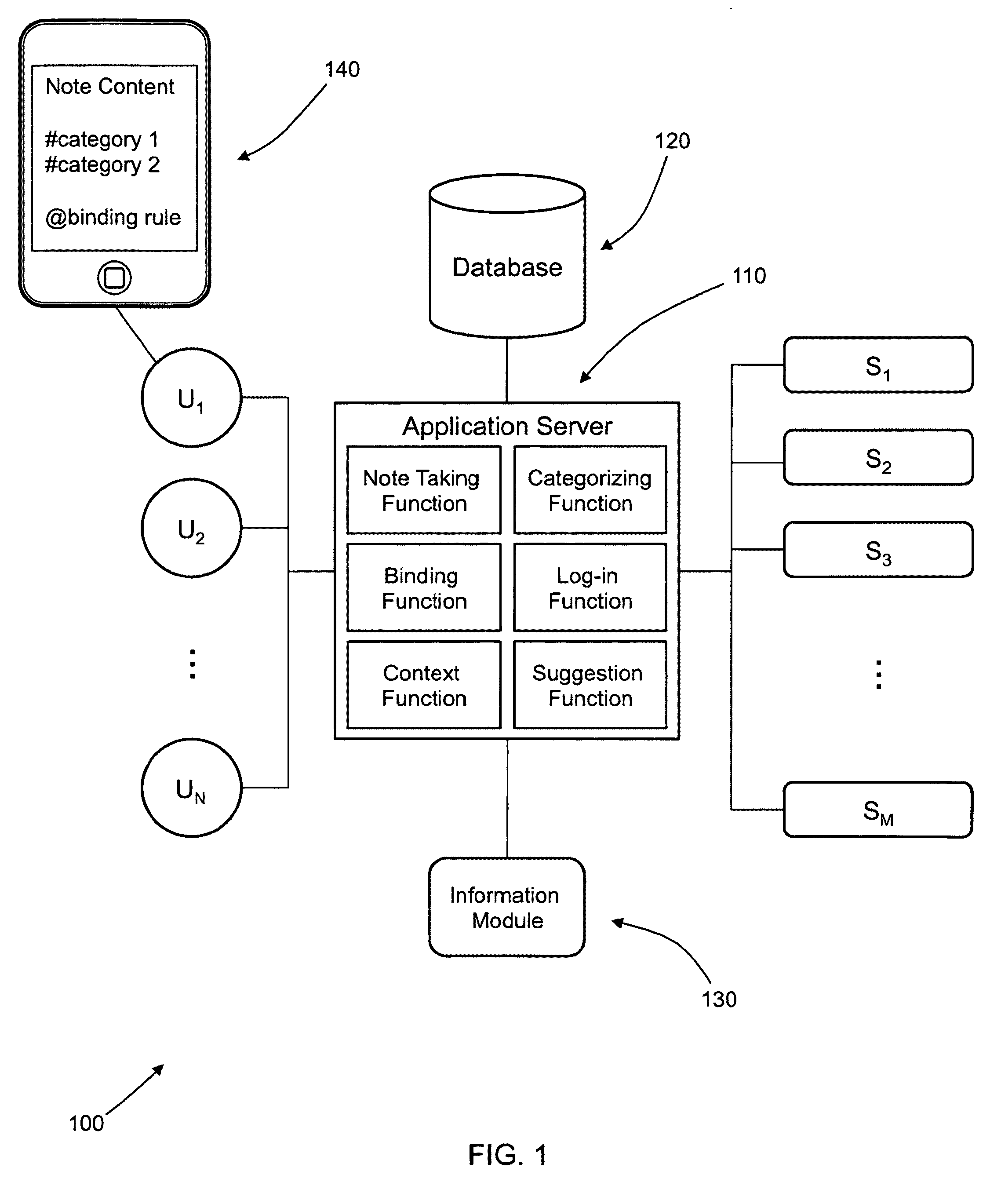
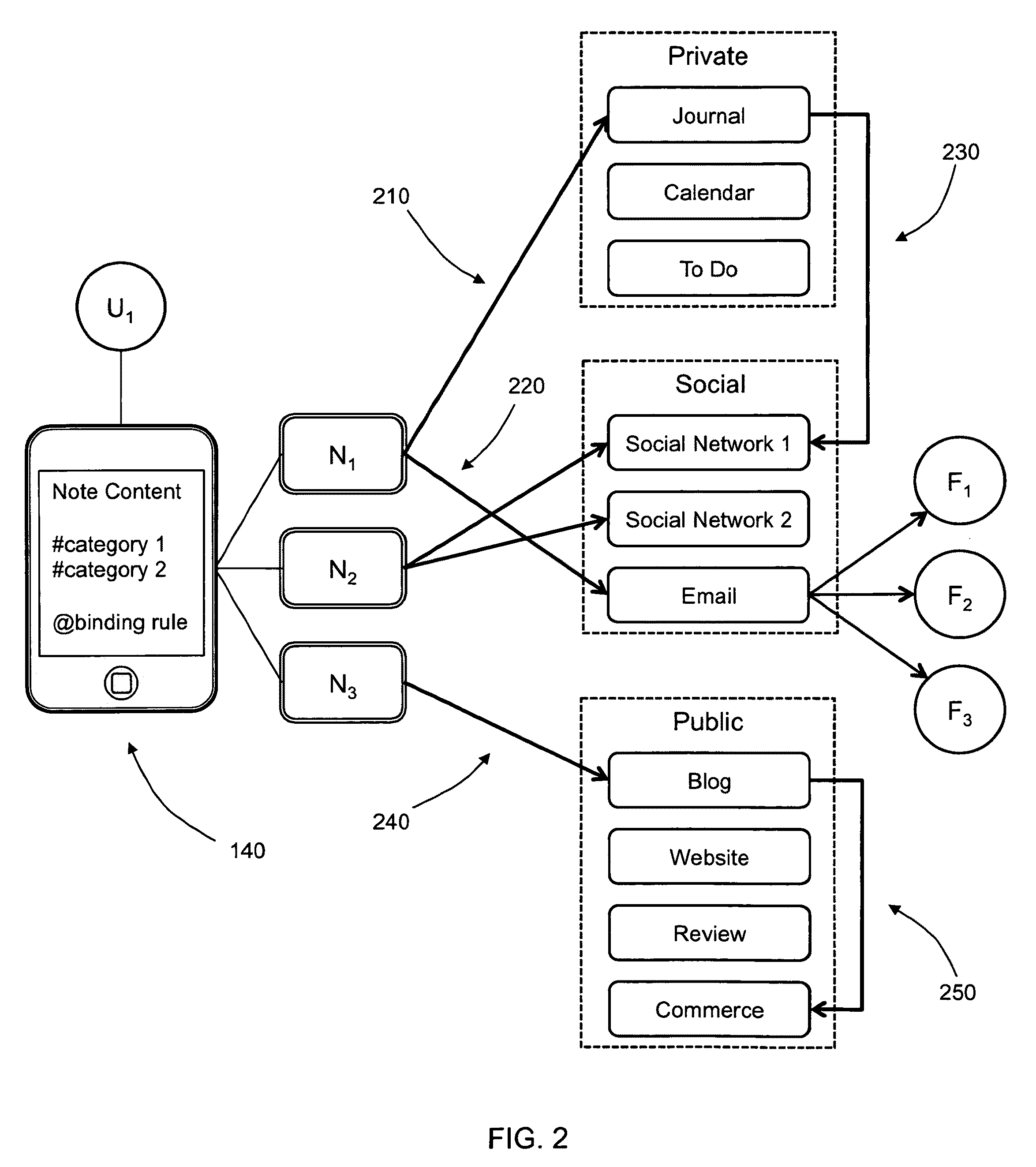
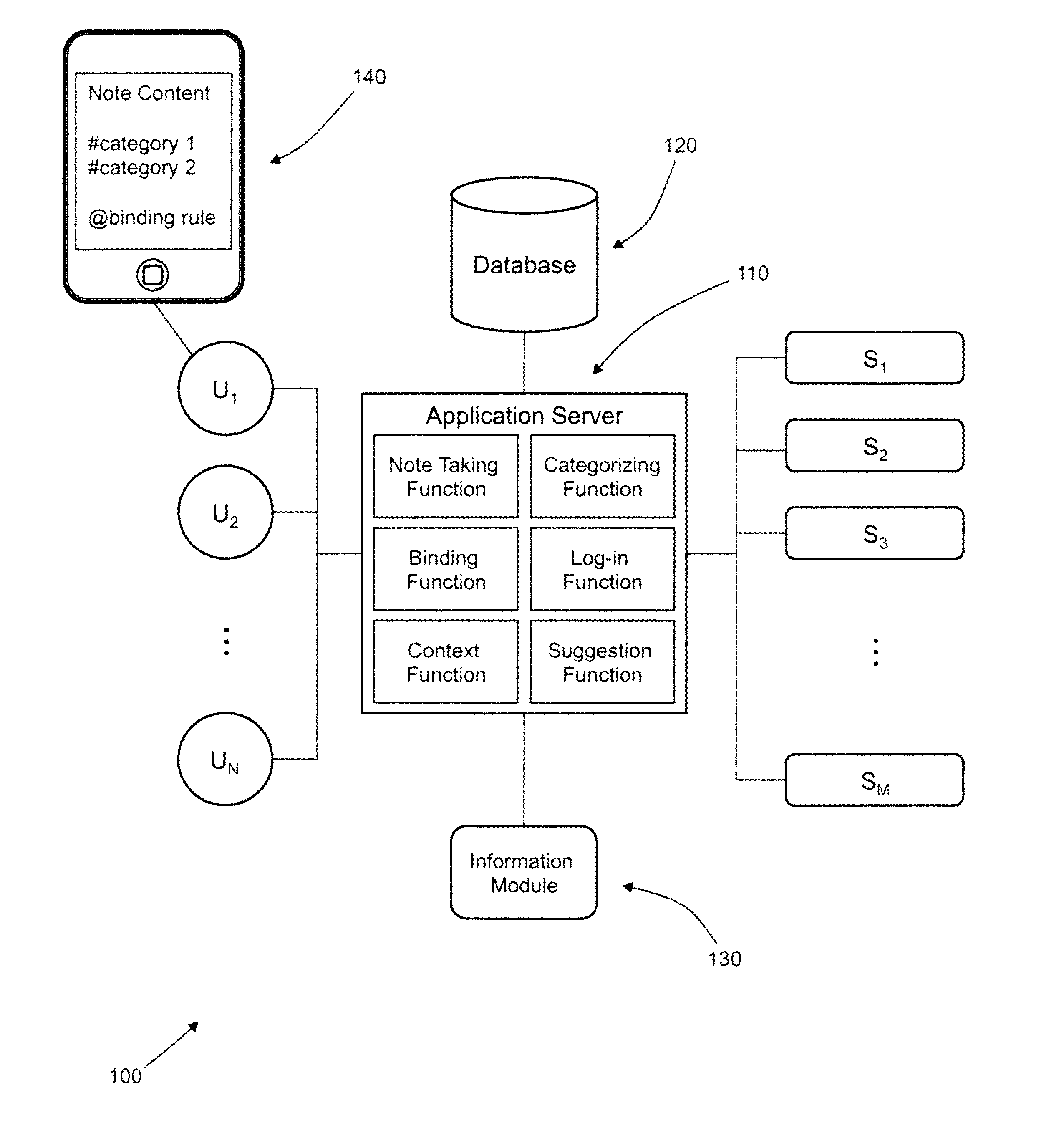
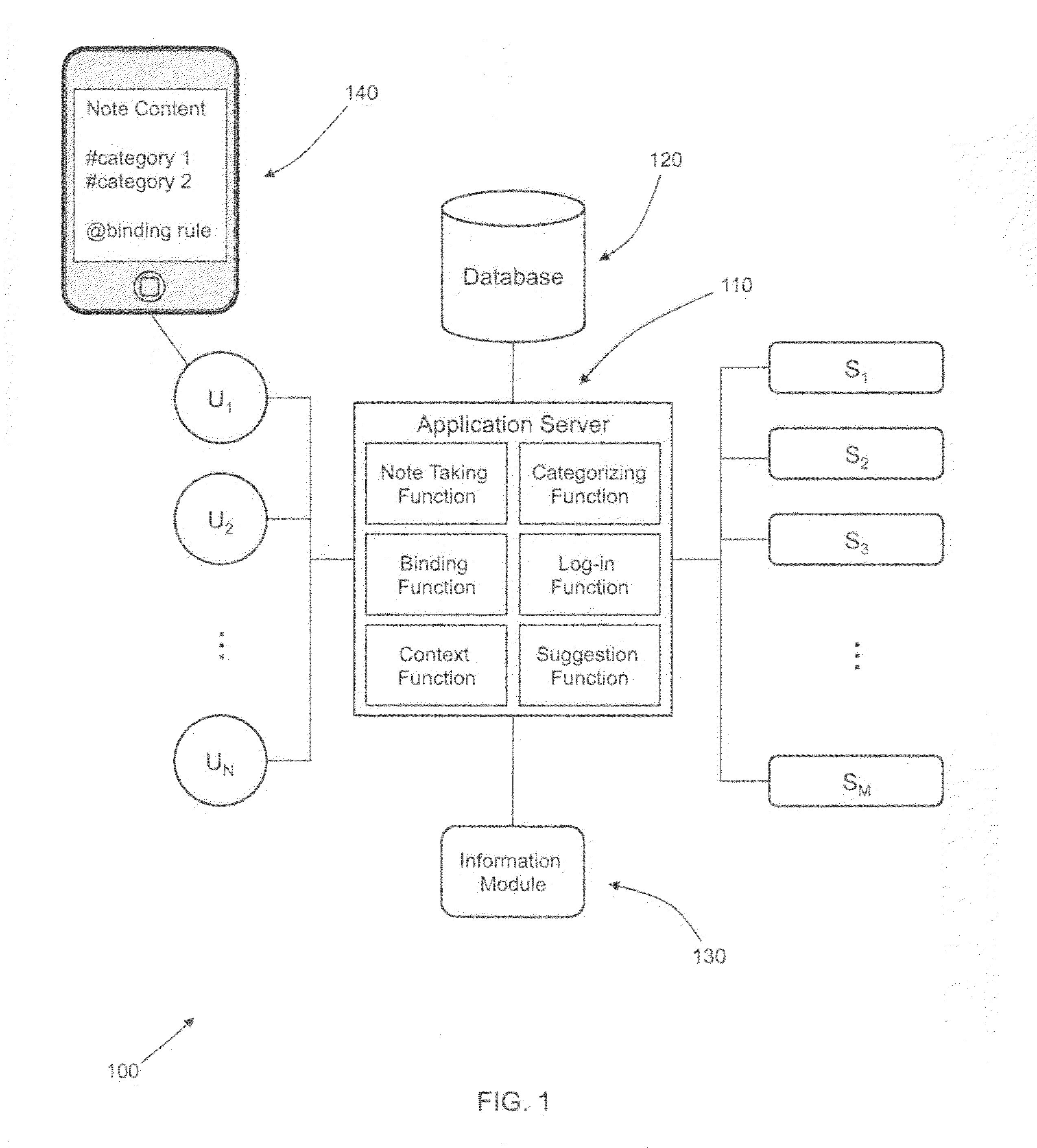
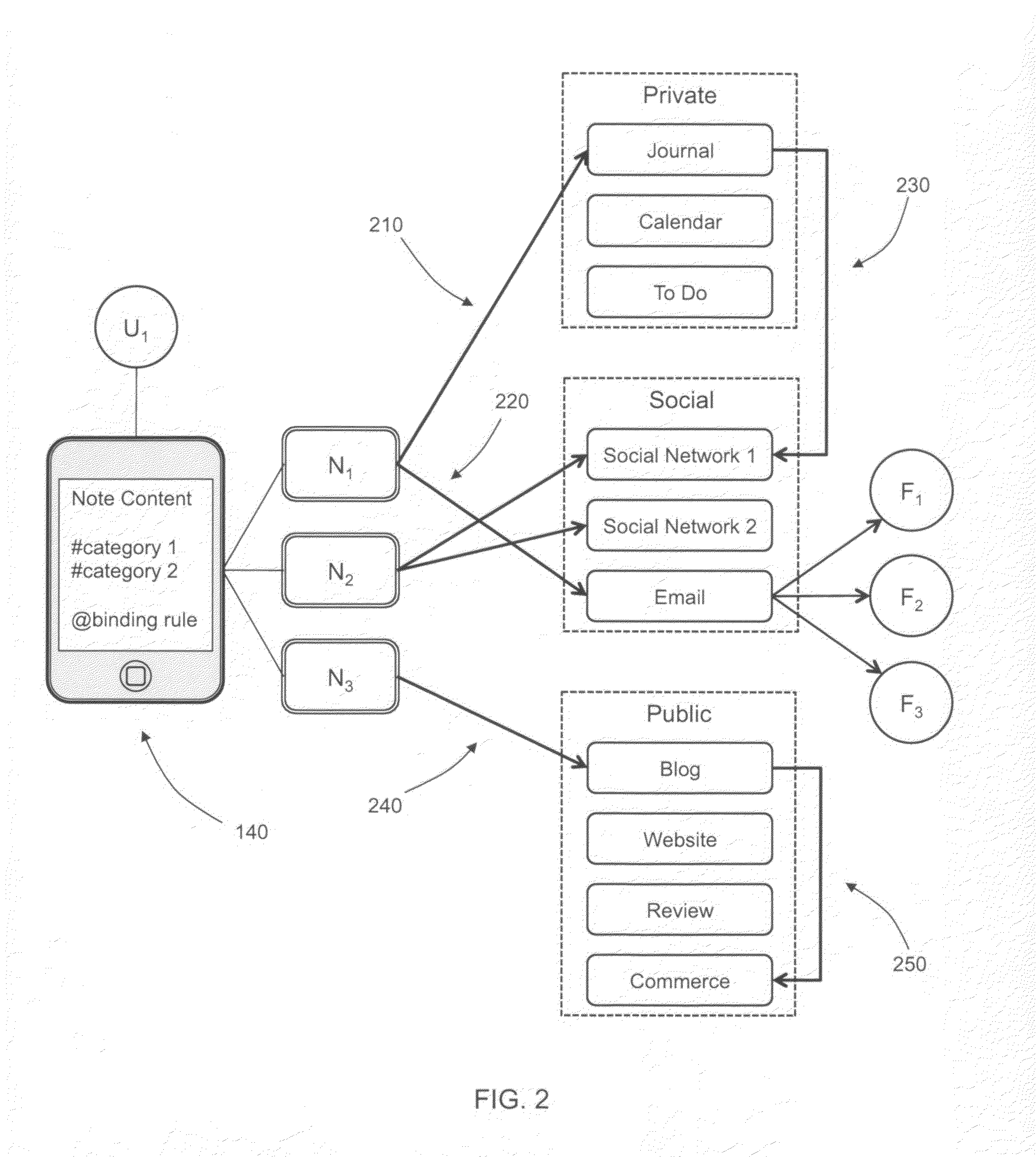
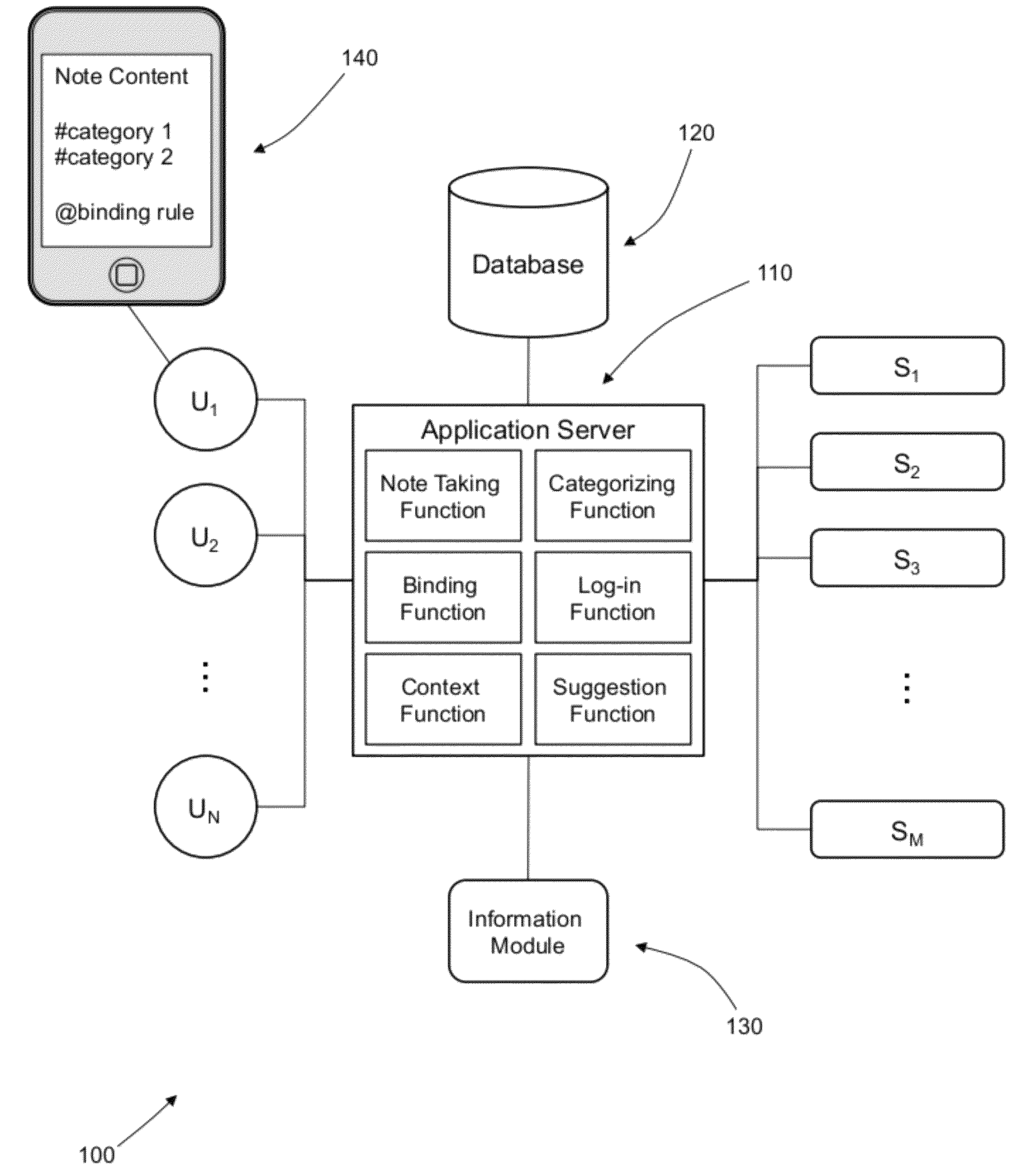
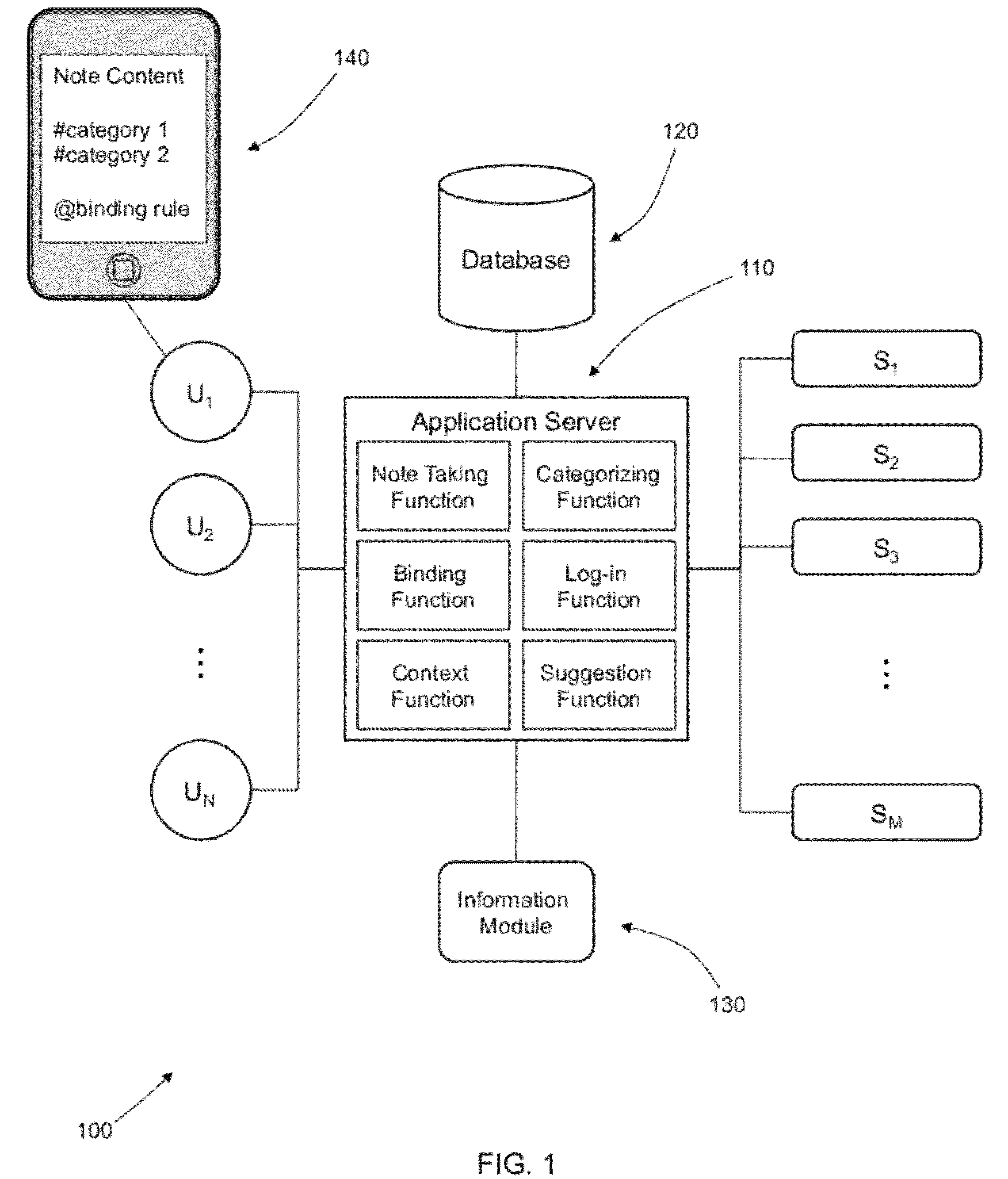
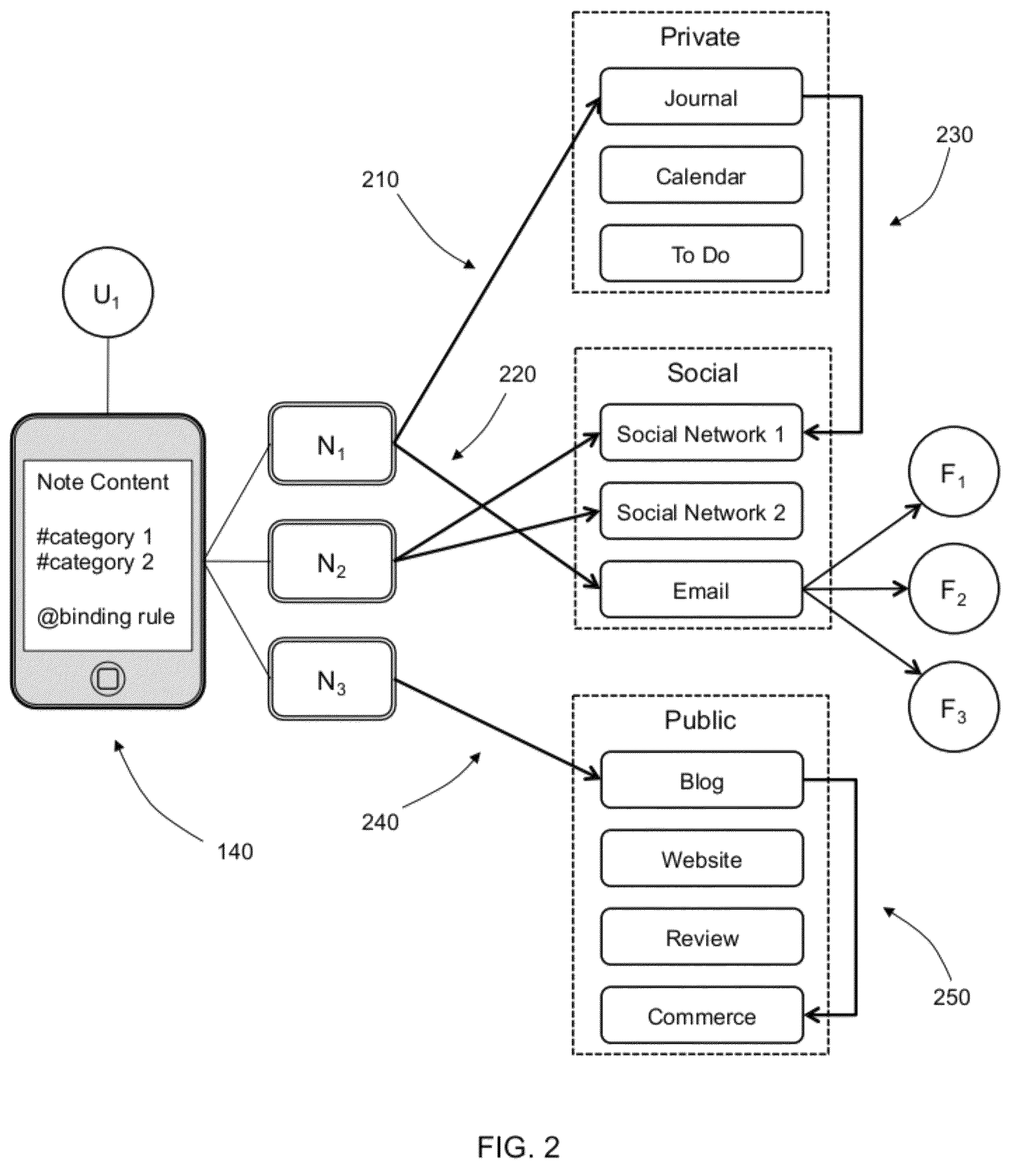
Semantic note taking system
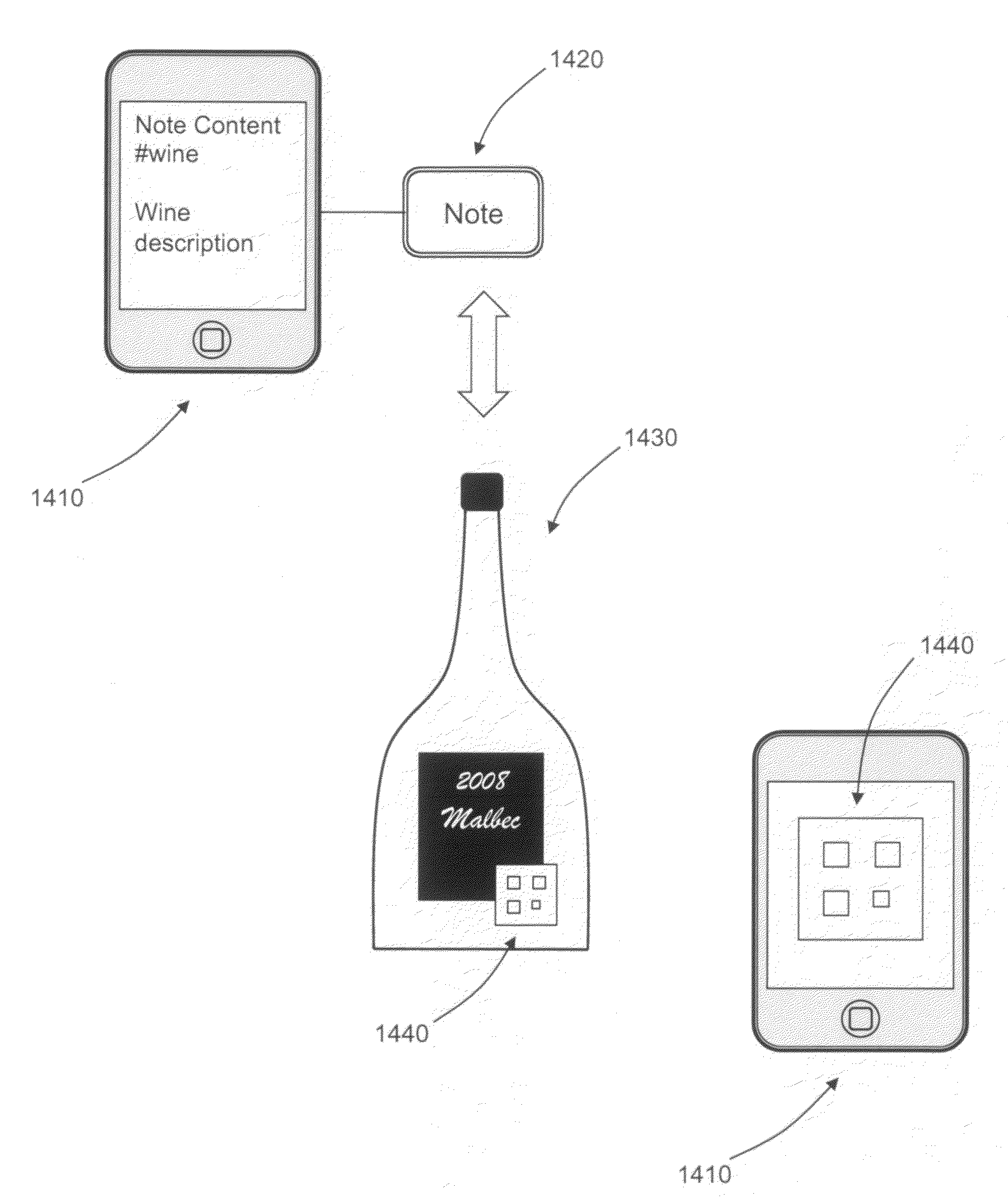
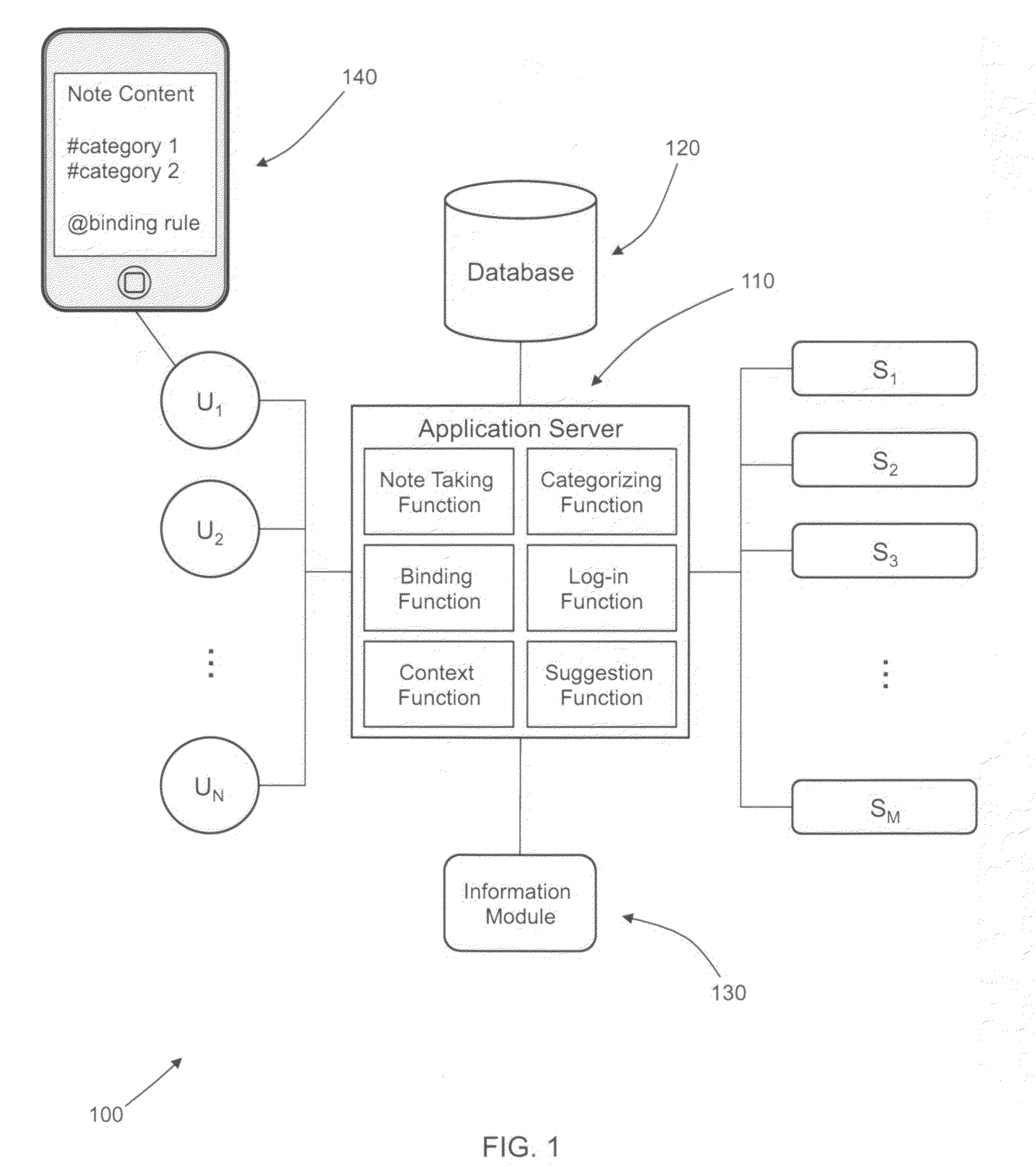
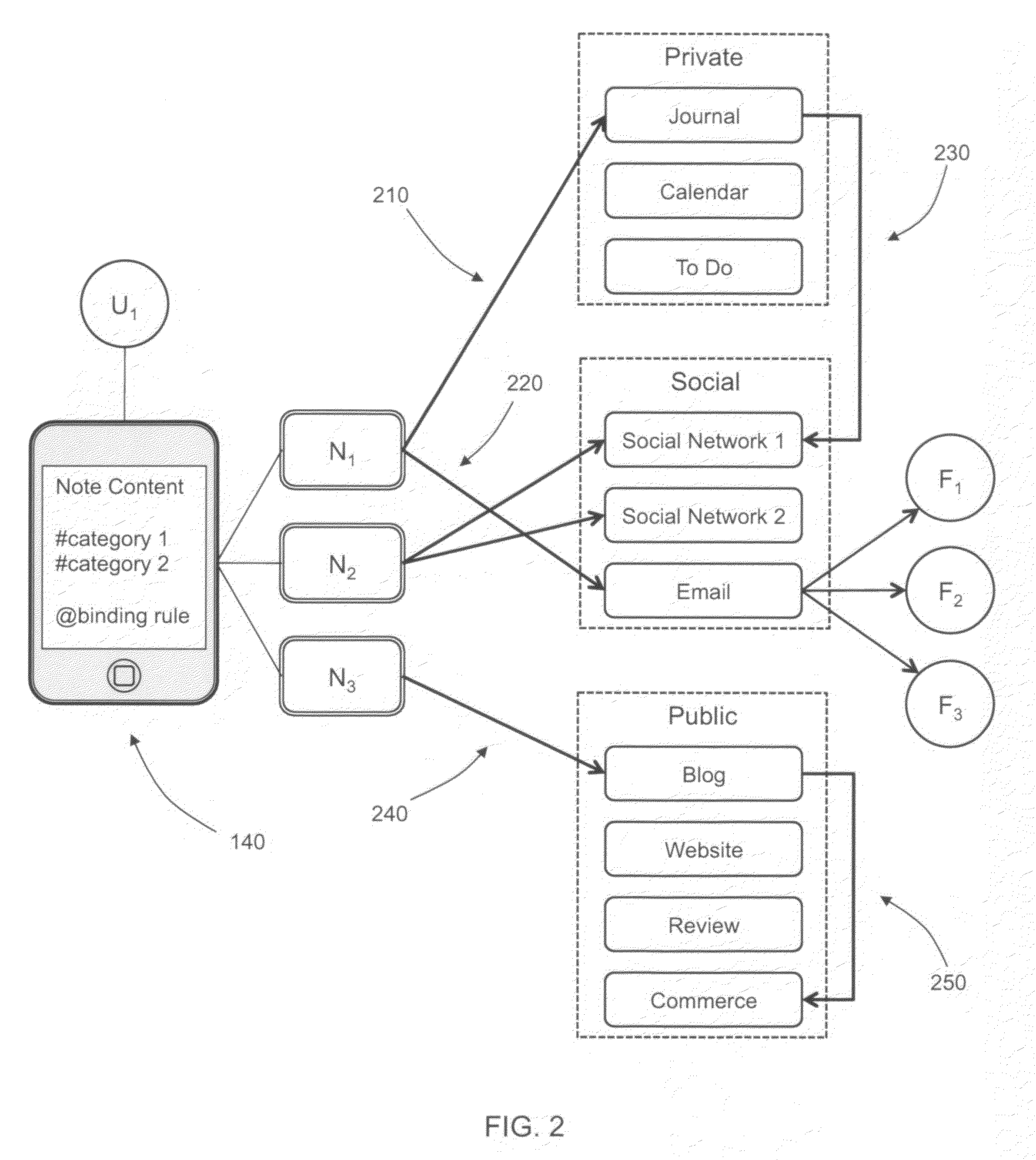
A semantic note taking system and method for collecting information, enriching the information, and binding the information to services is provided. User-created notes are enriched with labels, context traits, and relevant data to minimize friction in the note-taking process. In other words, the present invention is directed to collecting unscripted data, adding more meaning and use out of the data, and binding the data to services. Mutable and late-binding to services is also provided to allow private thoughts to be published to a myriad of different applications and services in a manner compatible with how thoughts are processed in the brain. User interfaces and semantic skins are also provided to derive meaning out of notes without requiring a great deal of user input. Linking physical objects to notes are also provided, such as through QR codes.
Owner:APPLE INC
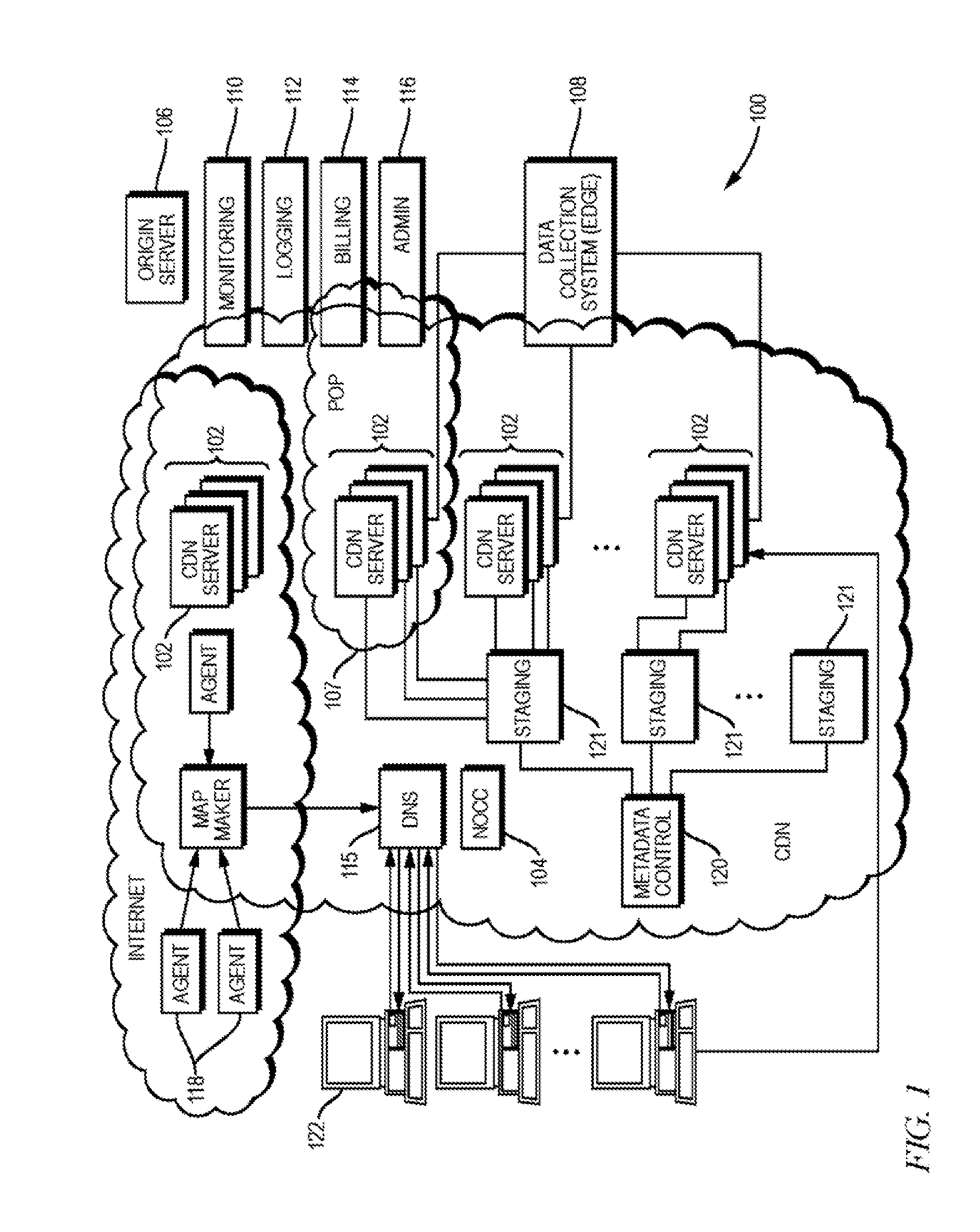
Scalable content delivery network request handling mechanism with support for dynamically-obtained content policies
Described herein are improved systems, methods, and devices for delivering and managing metadata in a distributed computing platform such as a content delivery network (CDN) so as to configure content servers to handle client requests. The teachings hereof provide, among other things, scalable and configurable solutions for delivering and managing metadata, preferably by leveraging dynamically obtained control information. For example, in one embodiment, a given content server may store metadata, e.g., in a configuration file, that references dynamic, late-bound control information for use in satisfying dependencies. This dynamic control information can be requested by the CDN content server, typically from a remote host, when needed to parse and execute the metadata.
Owner:AKAMAI TECH INC
Scalable content delivery network request handling mechanism
Described herein are improved systems, methods, and devices for delivering and managing metadata in a distributed computing platform such as a content delivery network (CDN) so as to configure content servers to handle client requests. The teachings hereof provide, among other things, scalable and configurable solutions for delivering and managing metadata, preferably by leveraging dynamically obtained control information. For example, in one embodiment, a given content server may store metadata, e.g., in a configuration file, that references dynamic, late-bound control information for use in satisfying dependencies. This dynamic control information can be requested by the CDN content server, typically from a remote host, when needed to parse and execute the metadata.
Owner:AKAMAI TECH INC
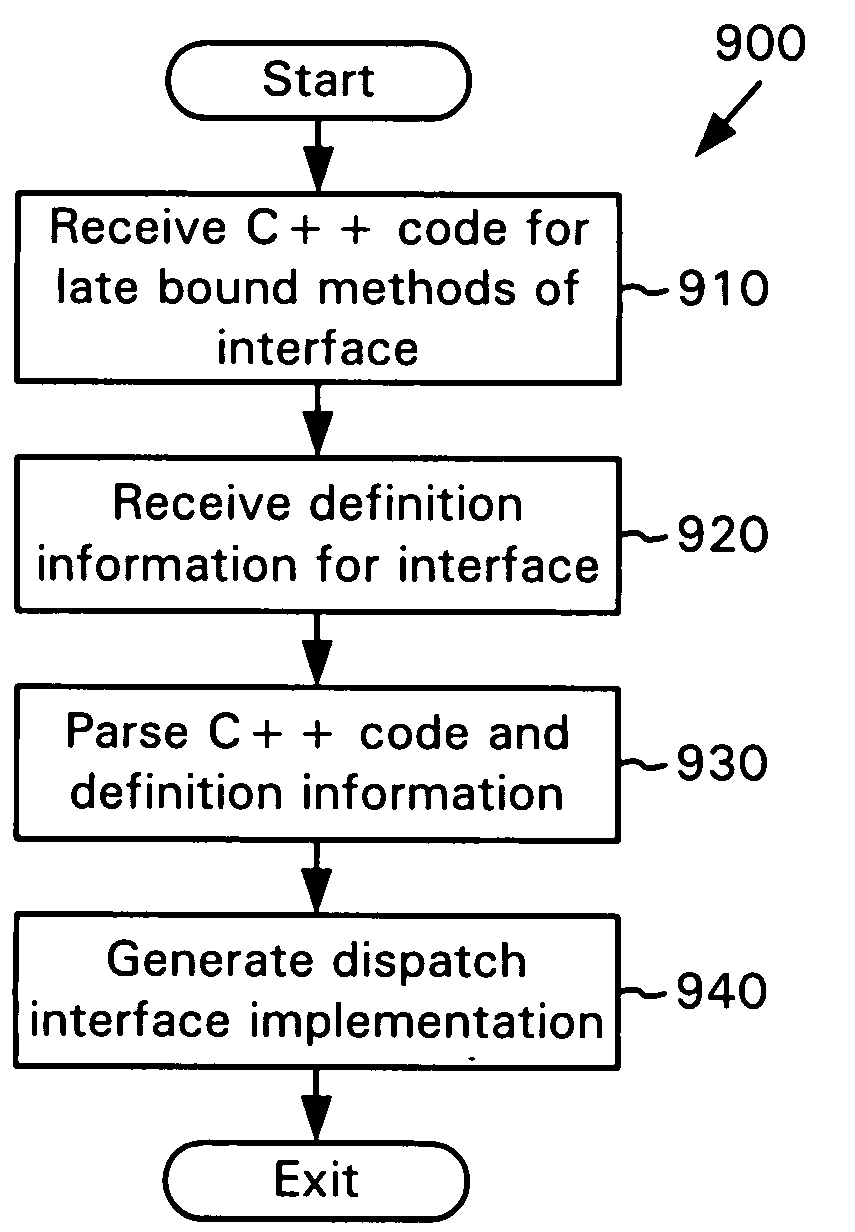
Compiler generation of a late binding interface implementation
InactiveUS7100153B1Prevents run time errorEasy to doSpecific program execution arrangementsMemory systemsClient-sideLate binding
A compiler automatically generates a late binding interface implementation based upon programming language code and definition information. The programming language code is for implementing the late bound methods of the interface, while the definition information defines late binding interface features of the interface. The late binding interface implementation includes code for invoking one or more late bound methods through a late binding mechanism, and also can include code for directly invoking the one or more late bound methods through an early binding mechanism. The compiler can also generate client-side code for calling a late bound method of a late binding interface.
Owner:MICROSOFT TECH LICENSING LLC
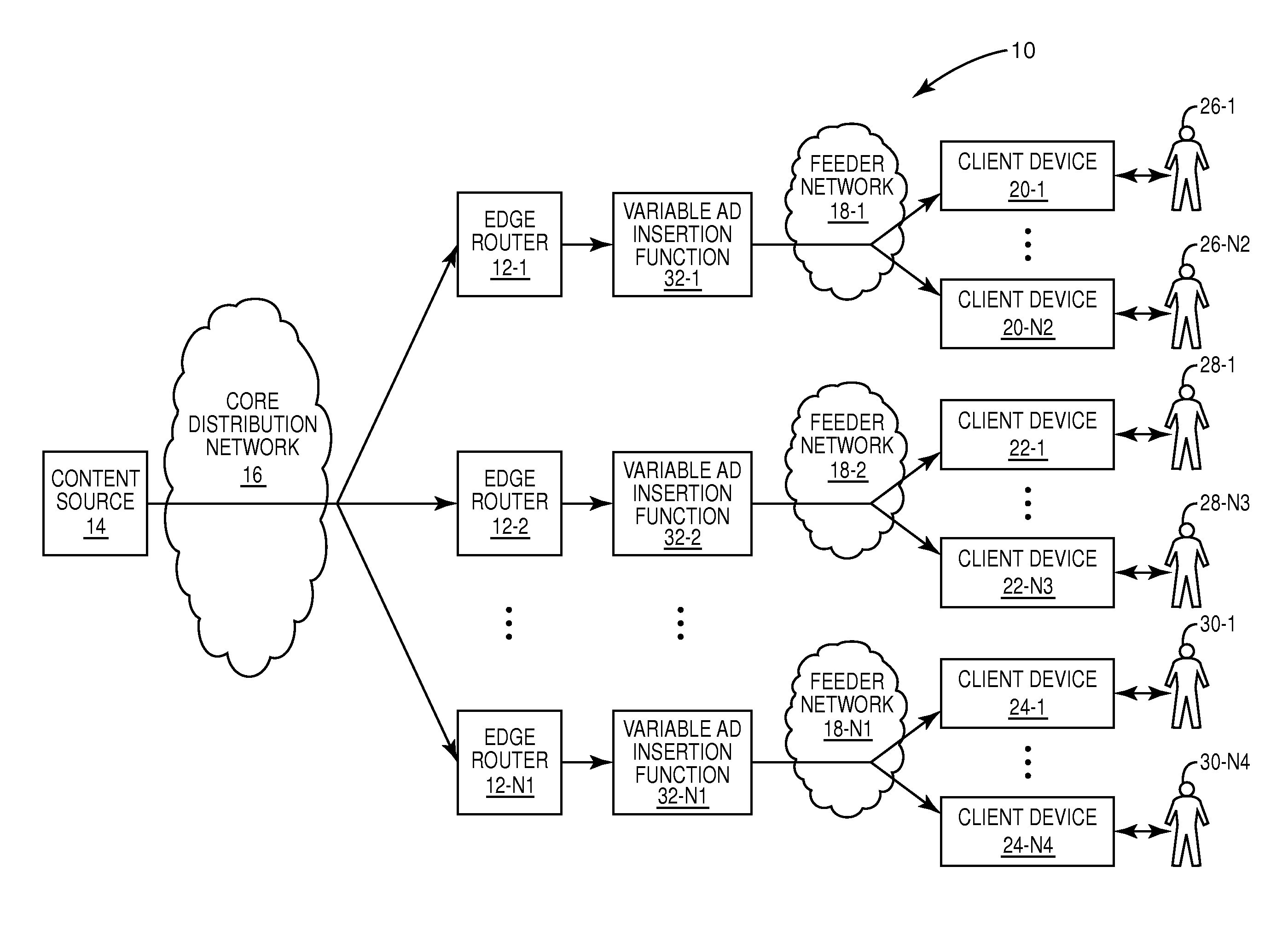
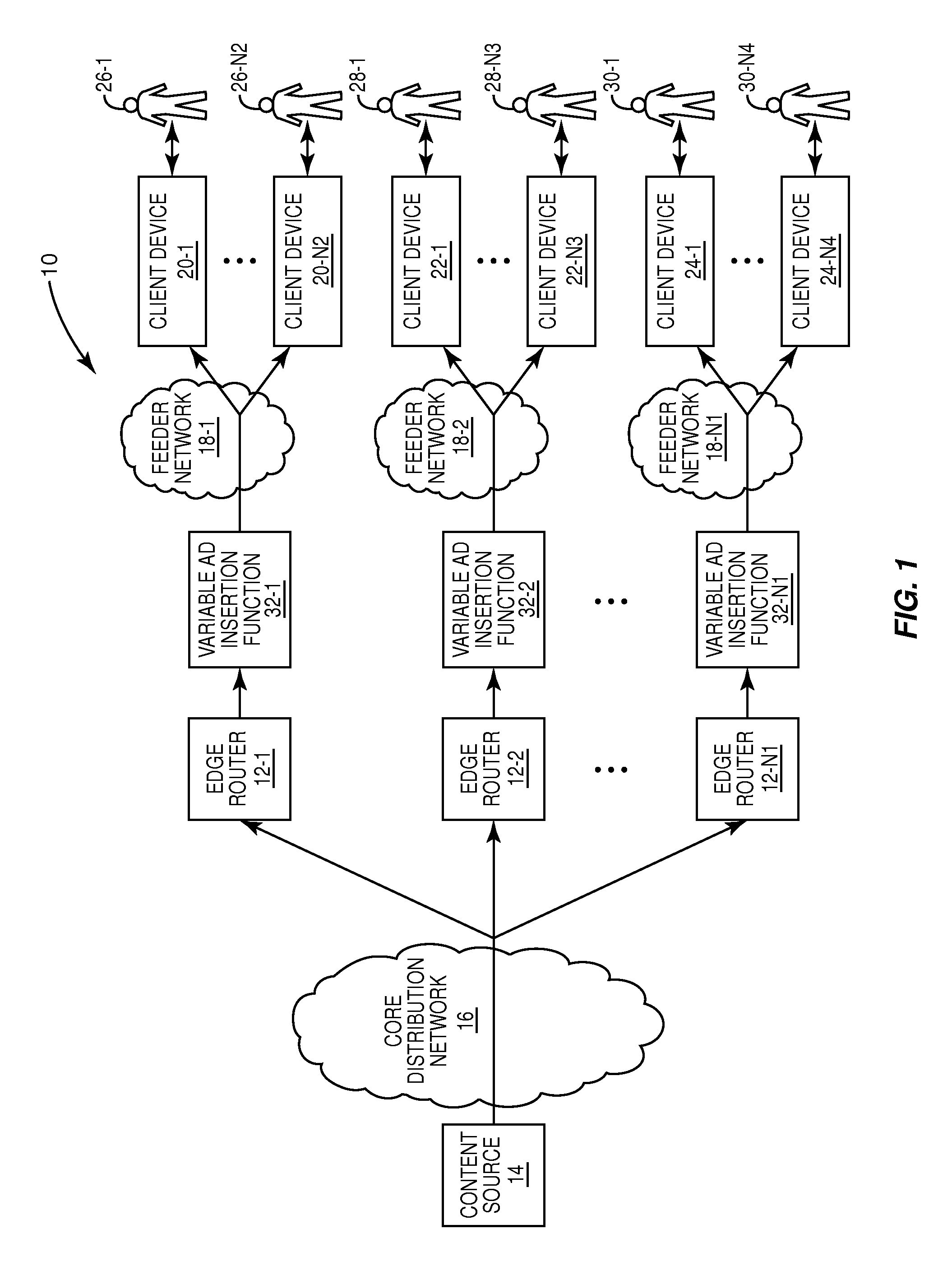
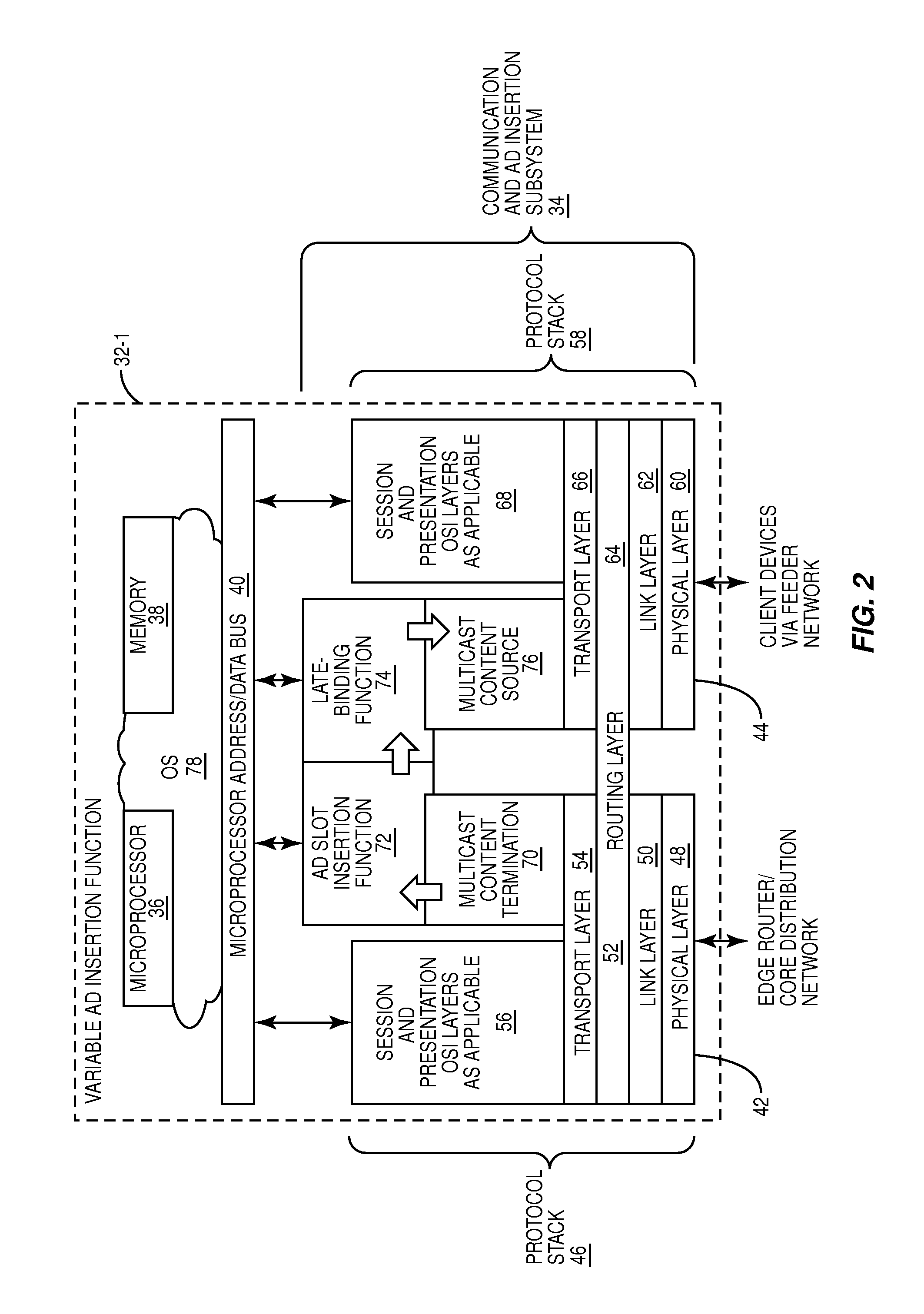
Dynamic load based ad insertion
ActiveUS8060904B1Television system detailsGHz frequency transmissionDistribution networksLate binding
A system and method are provided for dynamically adjusting advertisement (“ad”) time for a multicast channel. In one embodiment, a variable ad insertion function operates to receive one or more multicasts of media content from a core distribution network, insert ad timeslots into the media content, and optionally perform late-binding of ads to the ad timeslots. The media content including the inserted ad timeslots and late-binded ads, if any, is then multicast to associated client devices over a feeder network using corresponding multicast channels. For each multicast channel, insertion of ad timeslots into the associated media content is dynamically controlled based on the number of users currently consuming or predicted to consume the multicast channel, the number of client devices receiving or predicted to receive the multicast channel, or both.
Owner:QURIO HLDG
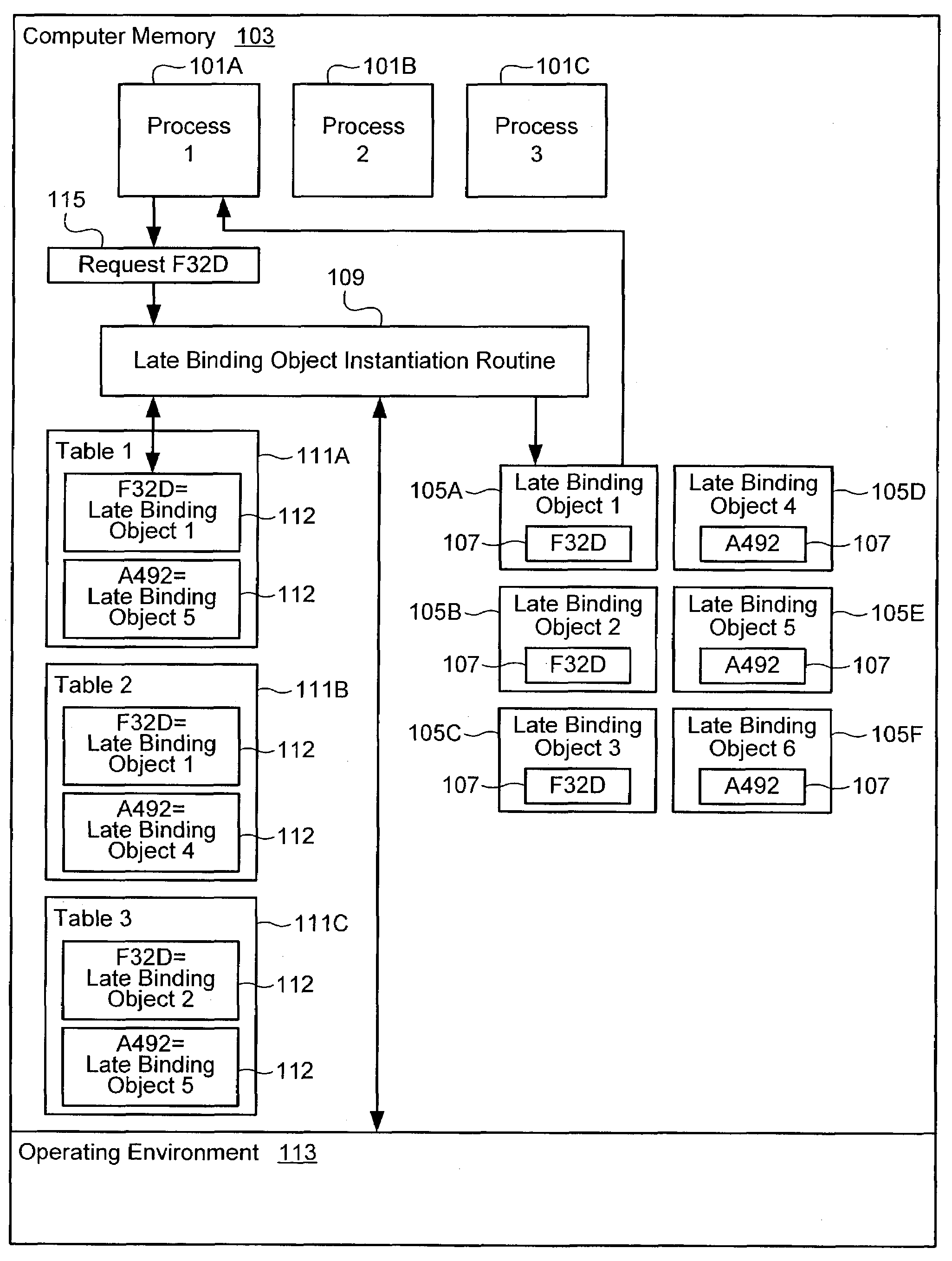
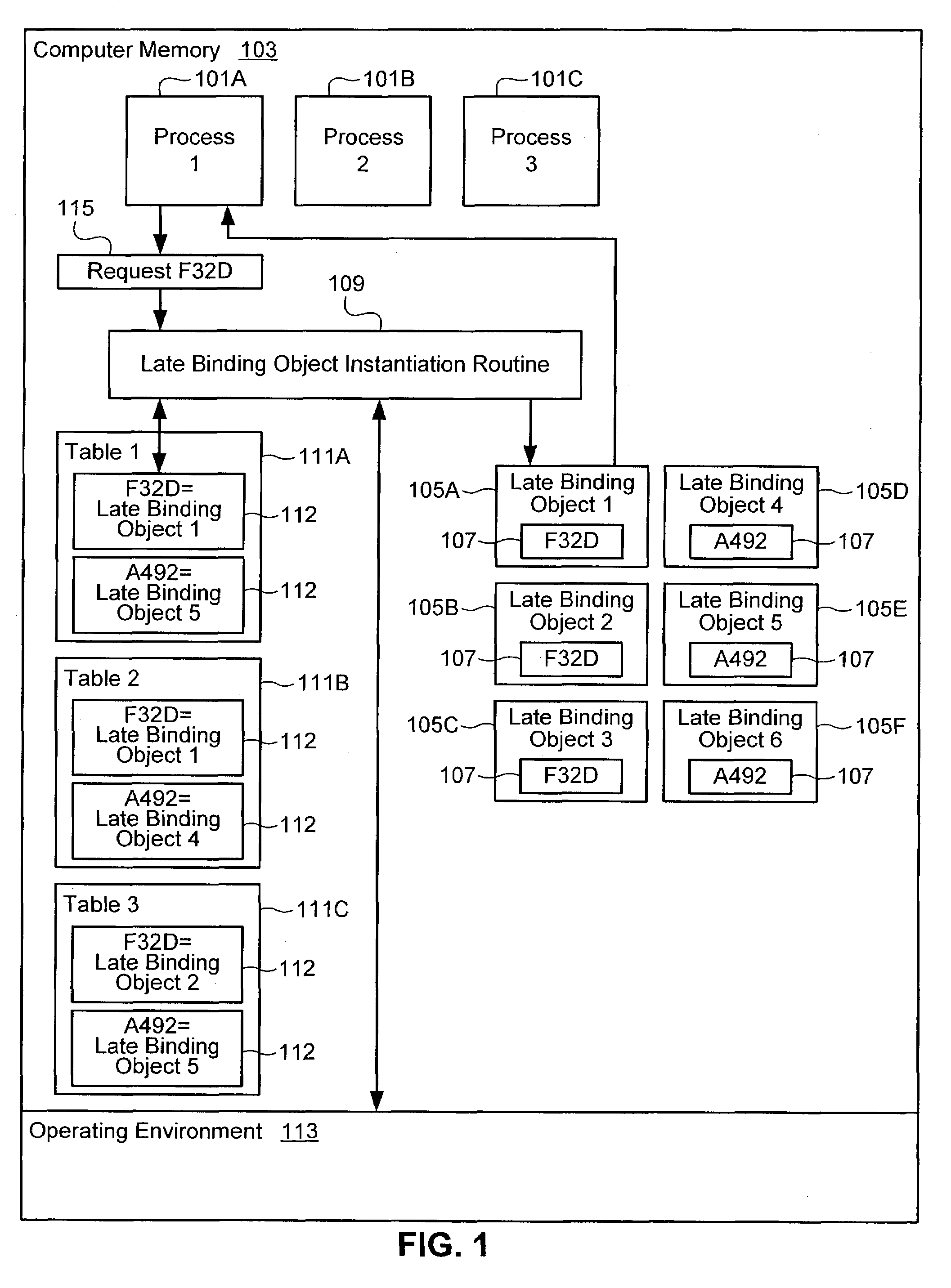
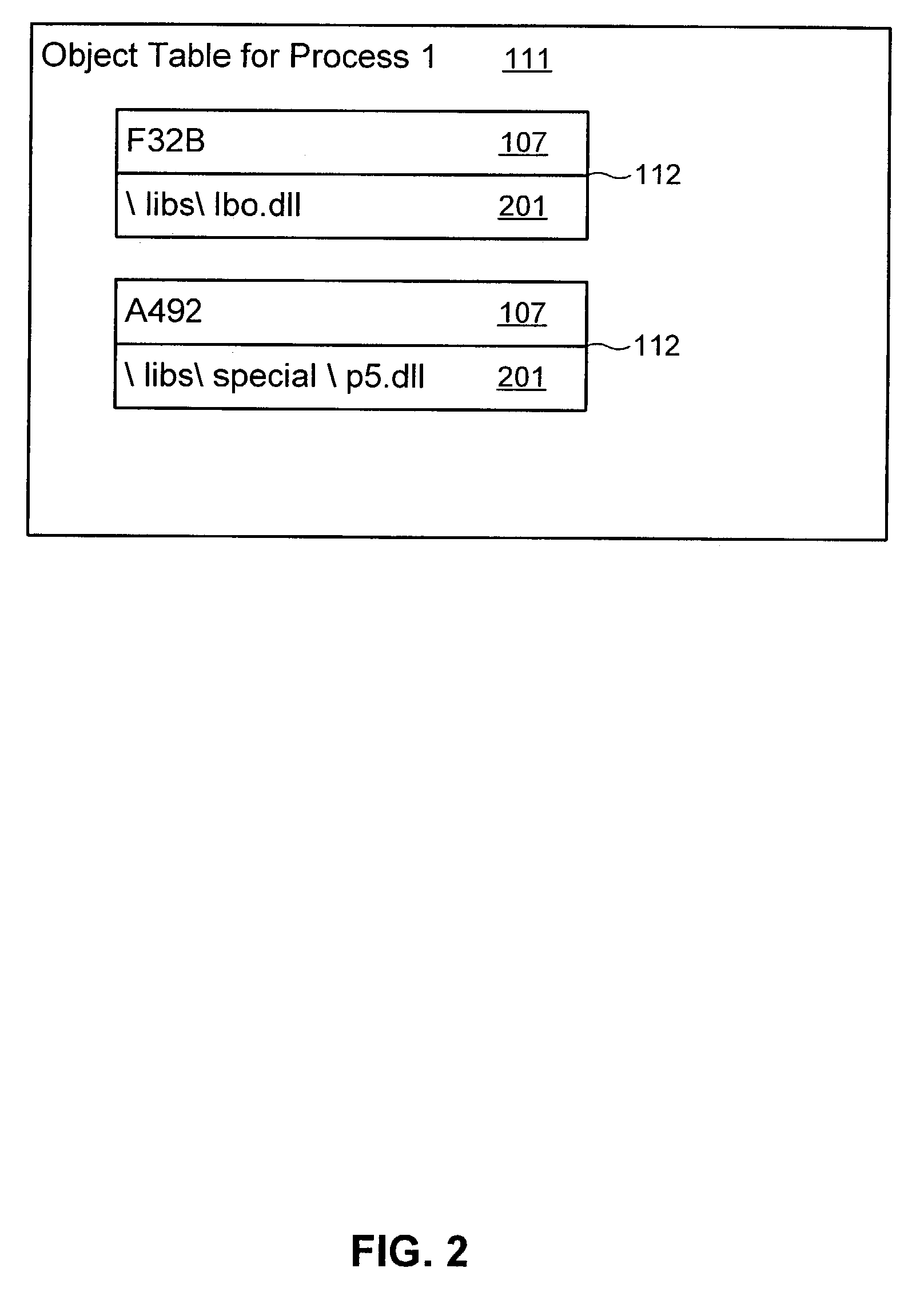
Supporting multiple late binding objects with the same identifier
Support is provided for multiple late binding objects with a same identifier, in an operating environment that only supports registration of a single late binding object with the same identifier. Each of a plurality of processes is associated with one of a plurality of late binding objects, such that at least two processes are each associated with a separate late binding object having the same identifier. Responsive to one of the plurality of processes attempting to access a late binding object by its identifier, a determination is made as to which late binding object is associated with the process. The associated late binding object is made available to the process.
Owner:INTUIT INC
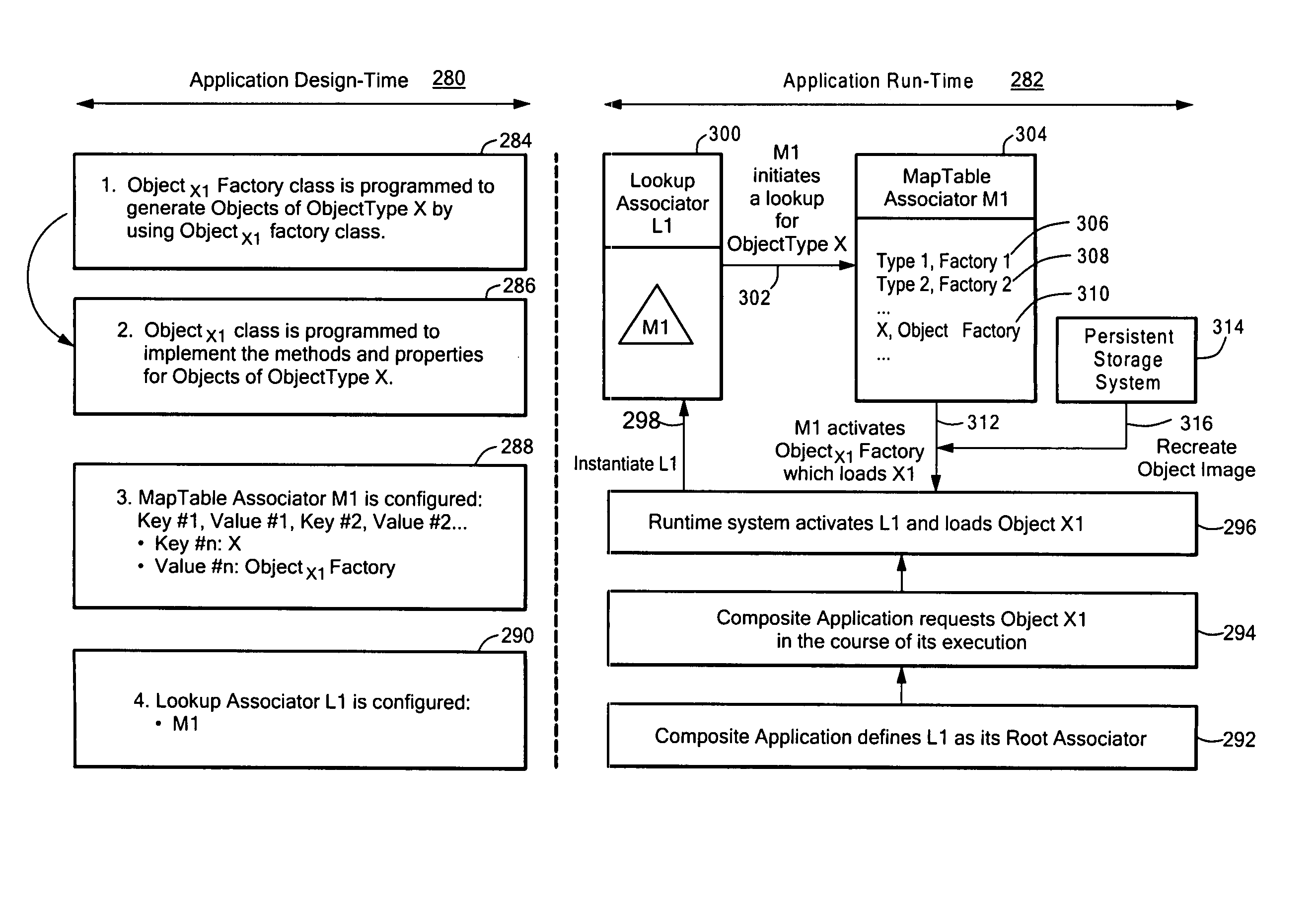
System and method for providing composite applications
InactiveUS7421716B1Easy to reuseEasy to integrateProgram controlSoftware deploymentGeneral purposeComposite application
A system and method for providing composite applications for software-based systems that uses a built-in application model having at least one general purpose object type, and providing dynamic late-binding of object implementations through an object typing system decoupled from pre-run time program code, using persistently stored objects. The application model may require that program objects in a conformant application be instances of a predefined active object type, or optionally instances of a predefined reactive object type. The application model enables integration of applications into composite applications, and further integration of composite applications into subsequently defined systems. The run-time object typing system for persistently stored objects is independent of the class typing system that is defined at compile-time or link-time, and enables convenient and practical modifications during development, deployment and maintenance of composite applications.
Owner:CERYLION
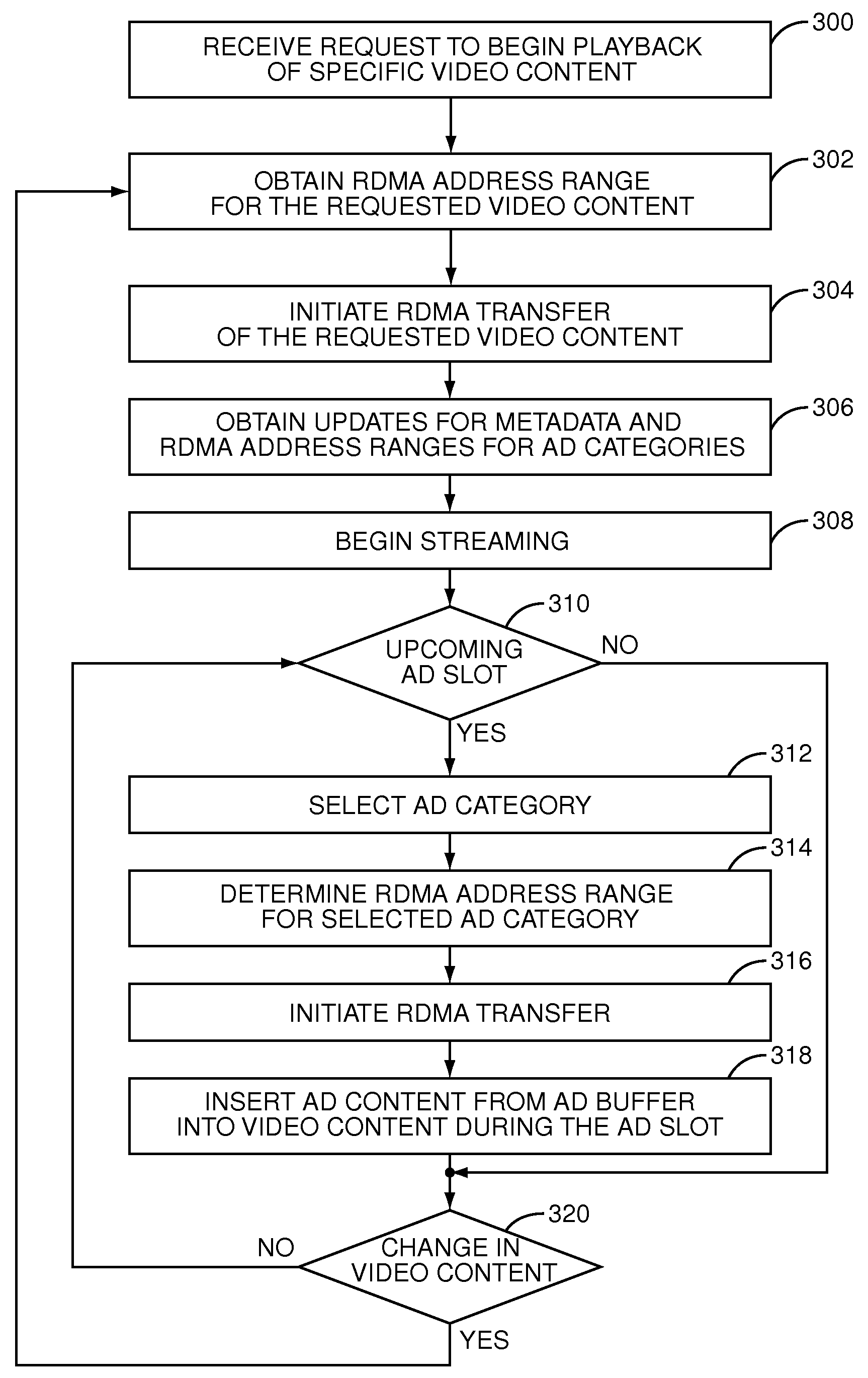
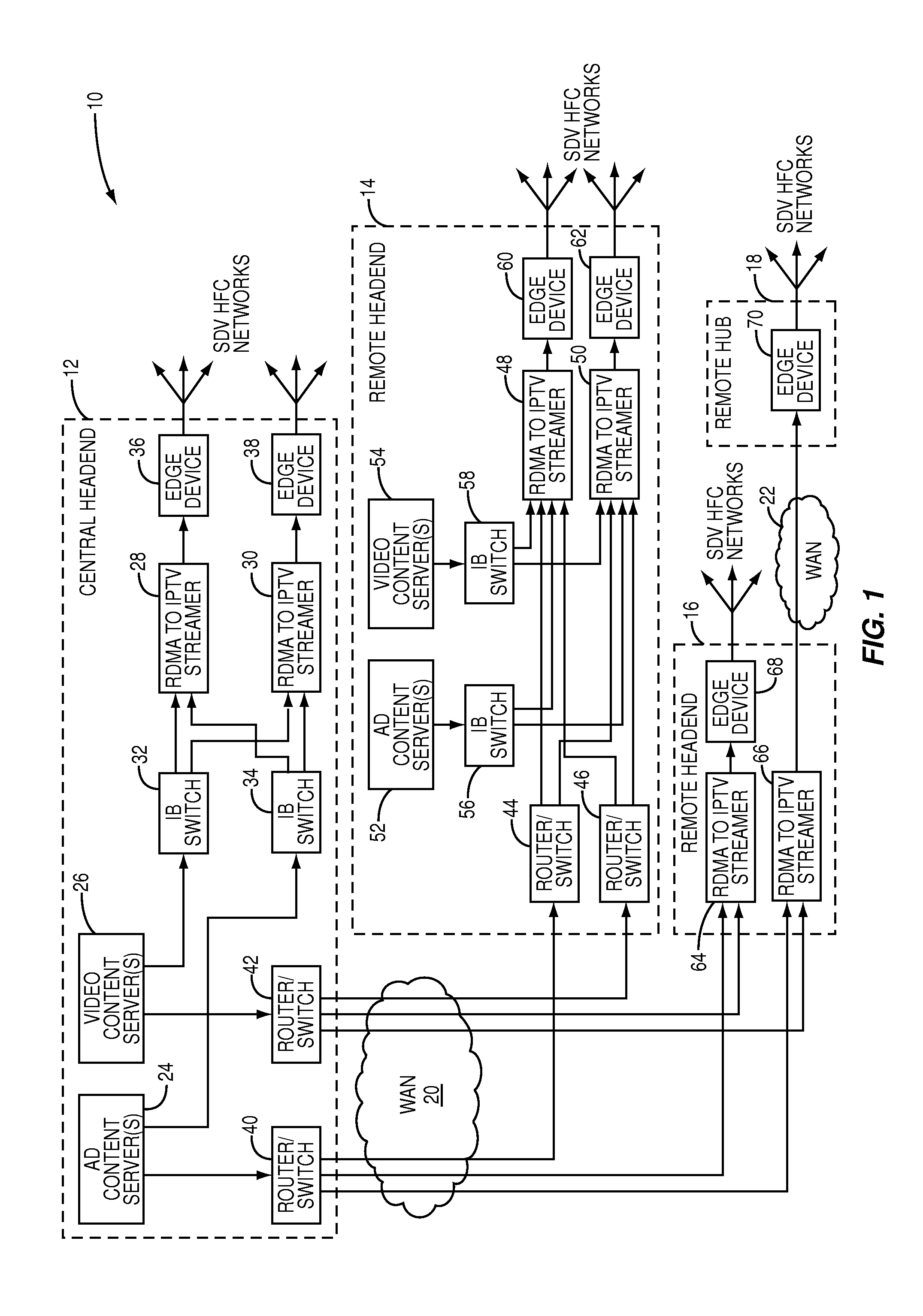
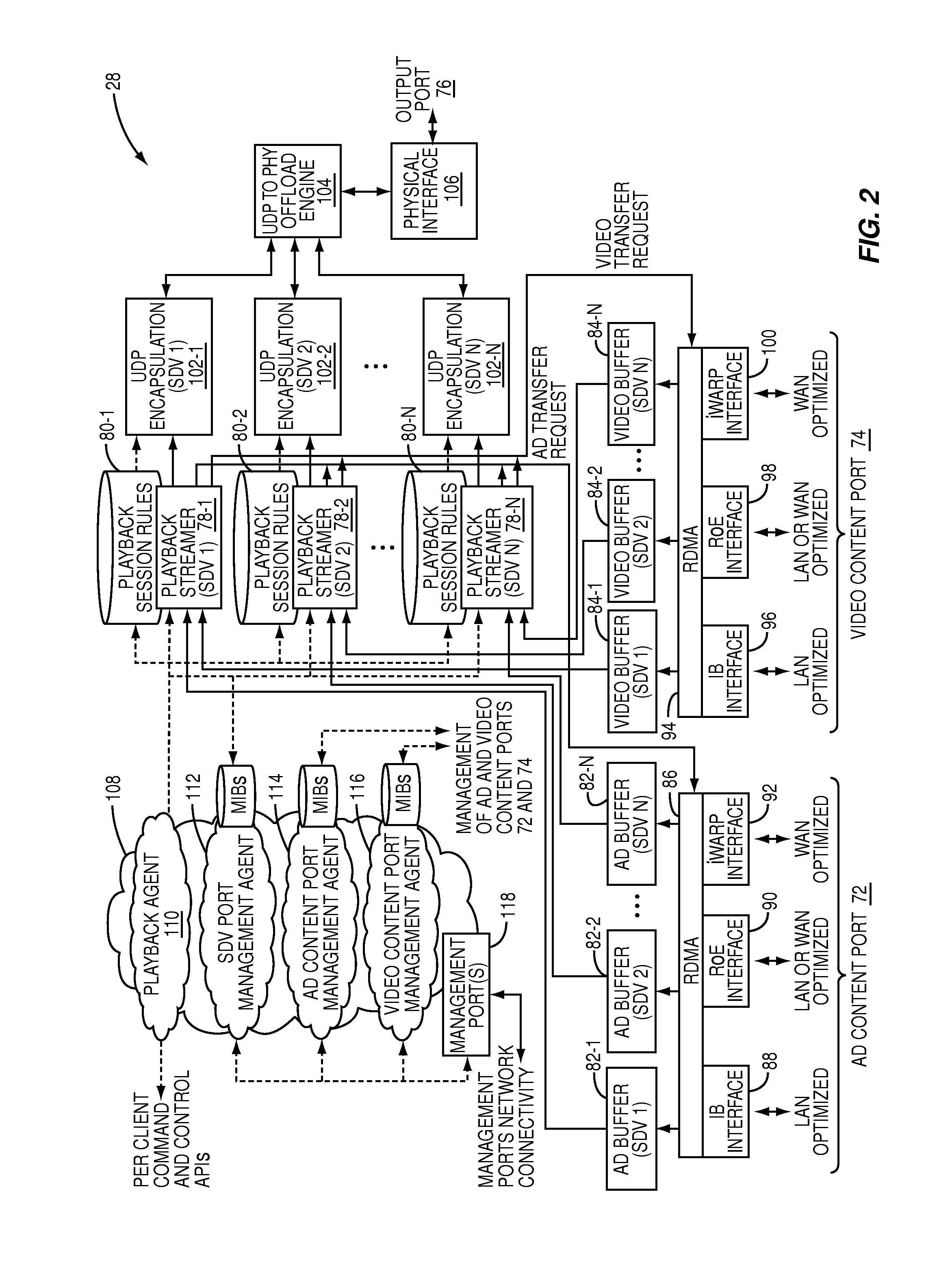
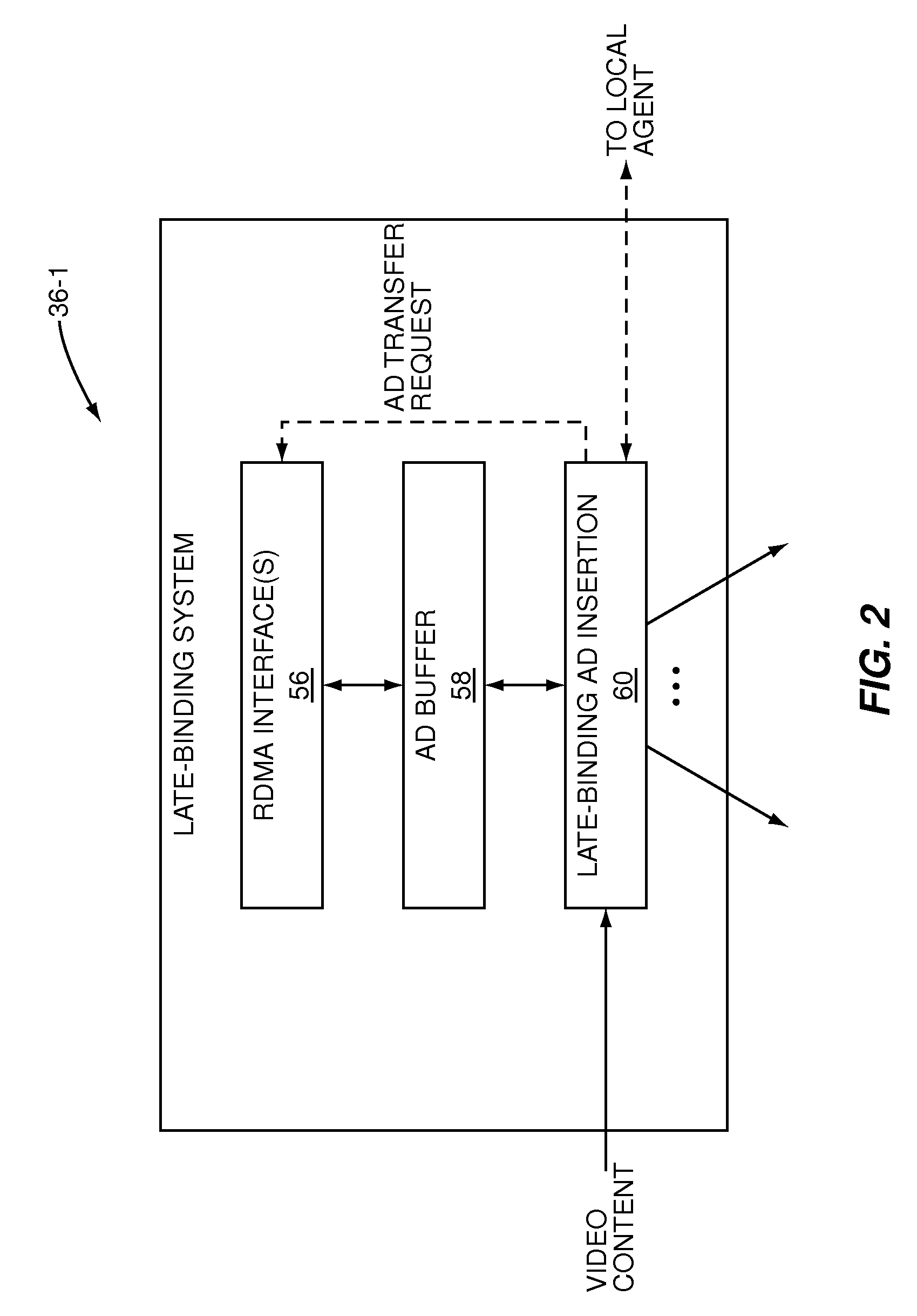
Multi-client streamer with late binding of ad content
A late-binding multi-client streamer utilizing Remote Direct Memory Access (RDMA) transfers to obtain video and advertisement content is provided. For each client device, the streamer receives a video content selection. In response, the streamer initiates an RDMA transfer of the video content or a segment of the video content from a storage device of a video content server to an associated video buffer and begins streaming the video content from the video buffer to the client device. When an upcoming advertisement slot in the video content is detected, the streamer initiates an RDMA transfer of an advertisement for the ad slot from a storage device associated with an advertisement content server to an associated ad buffer. The streamer then inserts the advertisement from the ad buffer into the ad slot in the video content as the video content is streamed to the client device.
Owner:QURIO HLDG
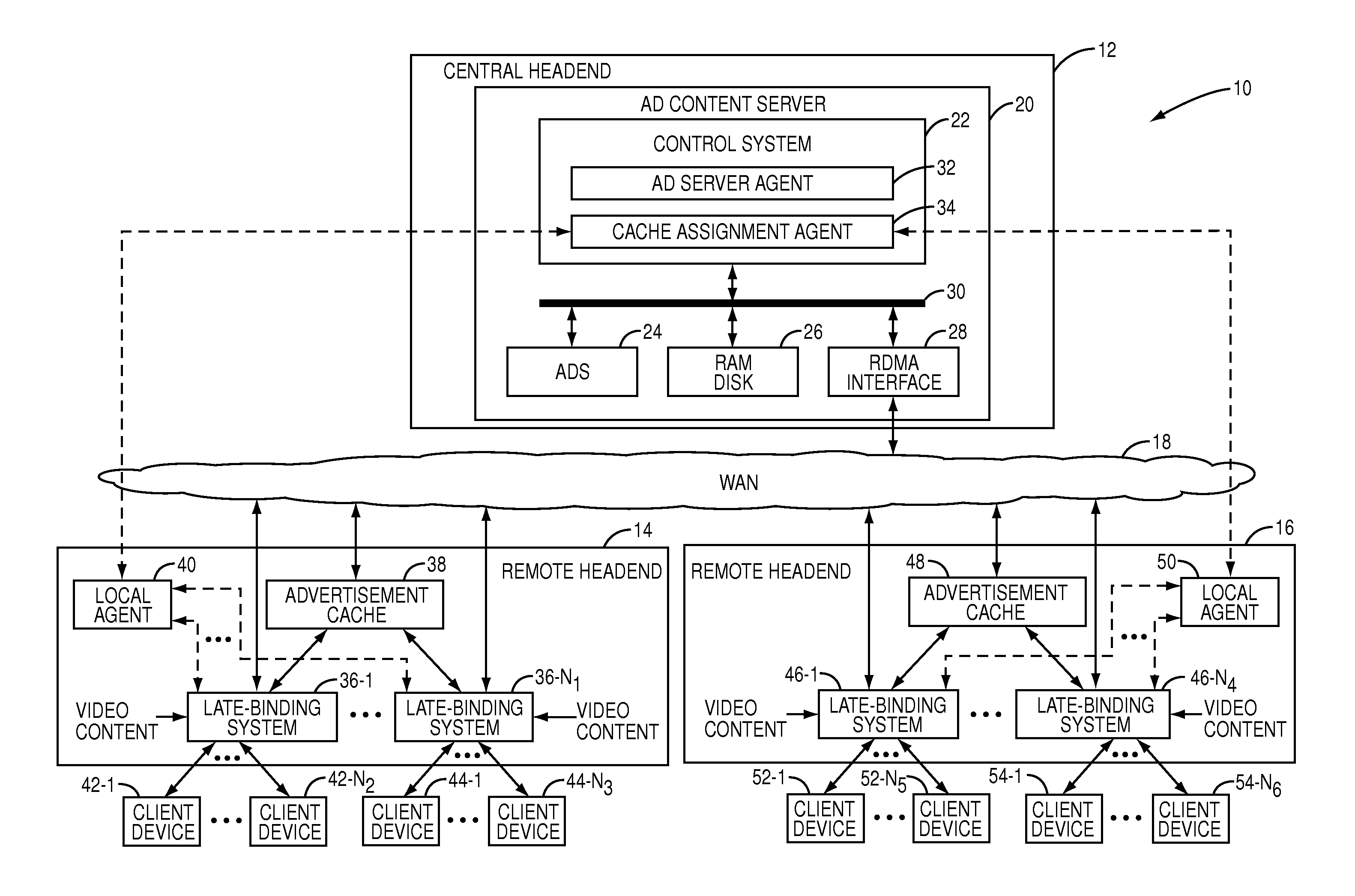
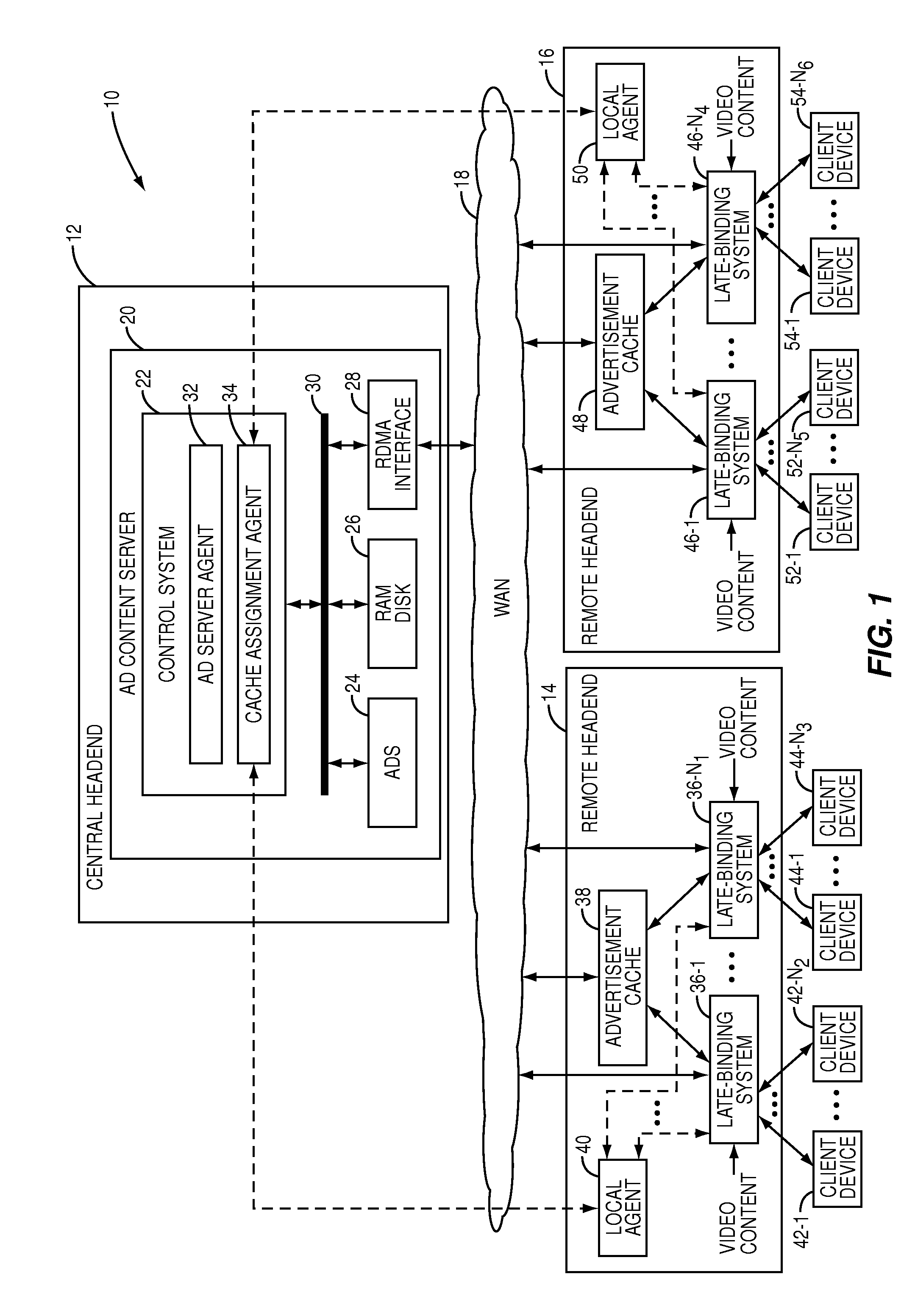
Push-caching scheme for a late-binding advertisement architecture
A system providing late-binding of advertisements to video content and incorporating a push-caching scheme is disclosed. In general, the system includes an advertisement server located at a central location such as a central headend and a number of late-binding systems located at locations such as a number of remote headends. The late-binding systems are connected to the advertisement server via a Wide Area Network (WAN). Each of the late-binding systems is also connected to an associated advertisement cache via a Local Area Network (LAN). A cache assignment agent associated with the advertisement server operates to push advertisements to the advertisement caches associated with the late-binding systems in a predictive fashion based on, for example, historical information for the late-binding systems and / or profiles of users or viewers associated with the client devices served by the late-binding systems.
Owner:QURIO HLDG
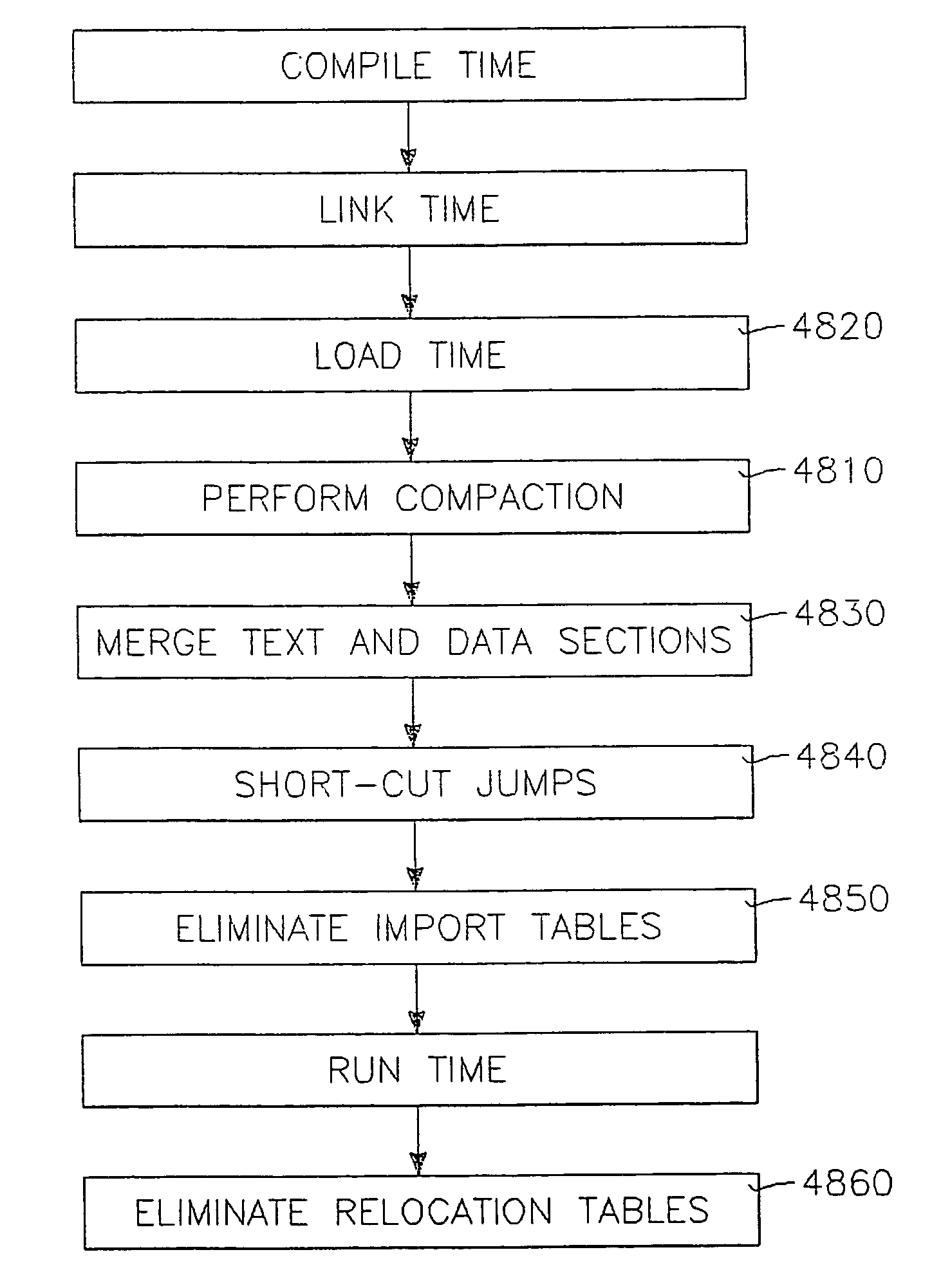
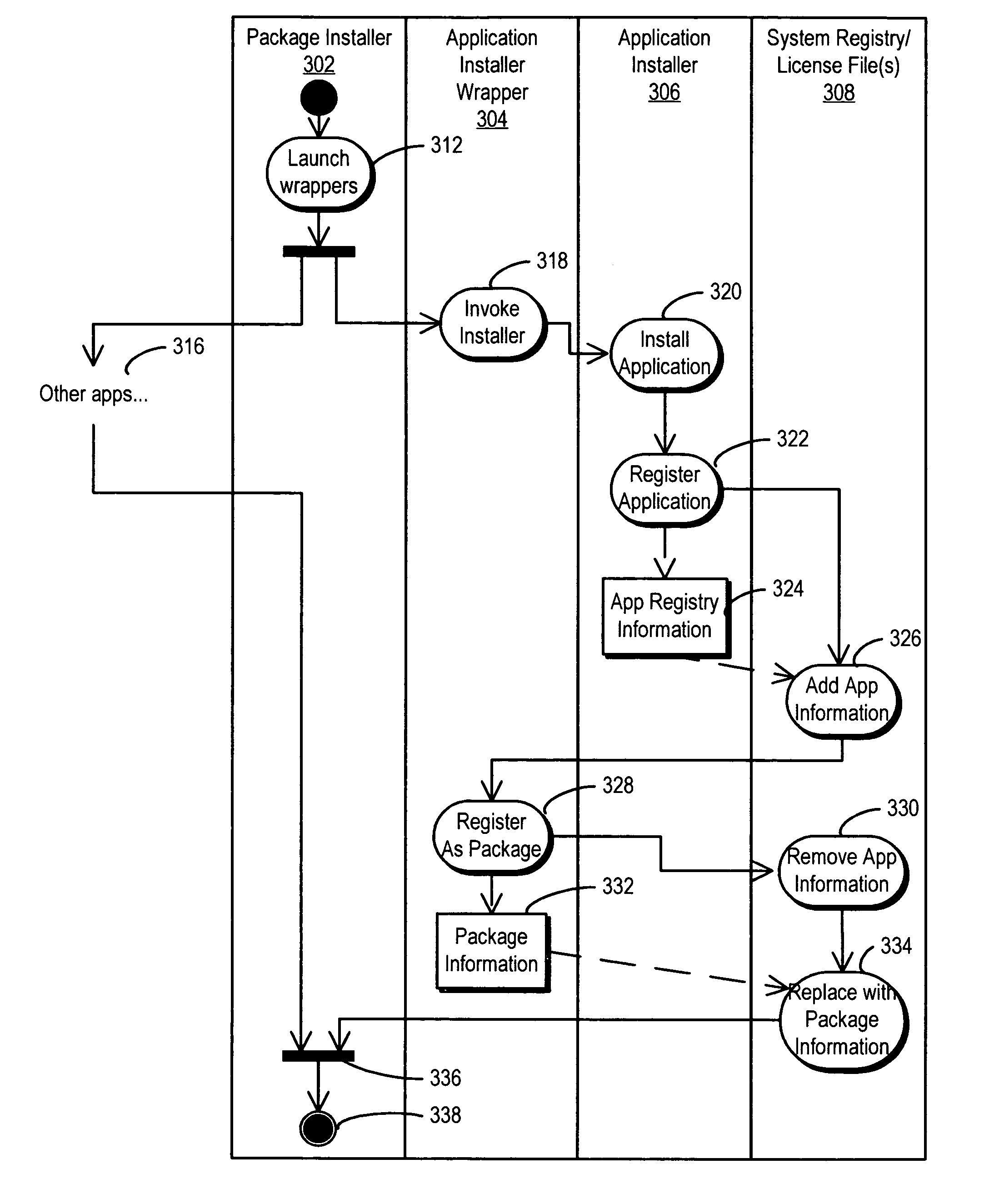
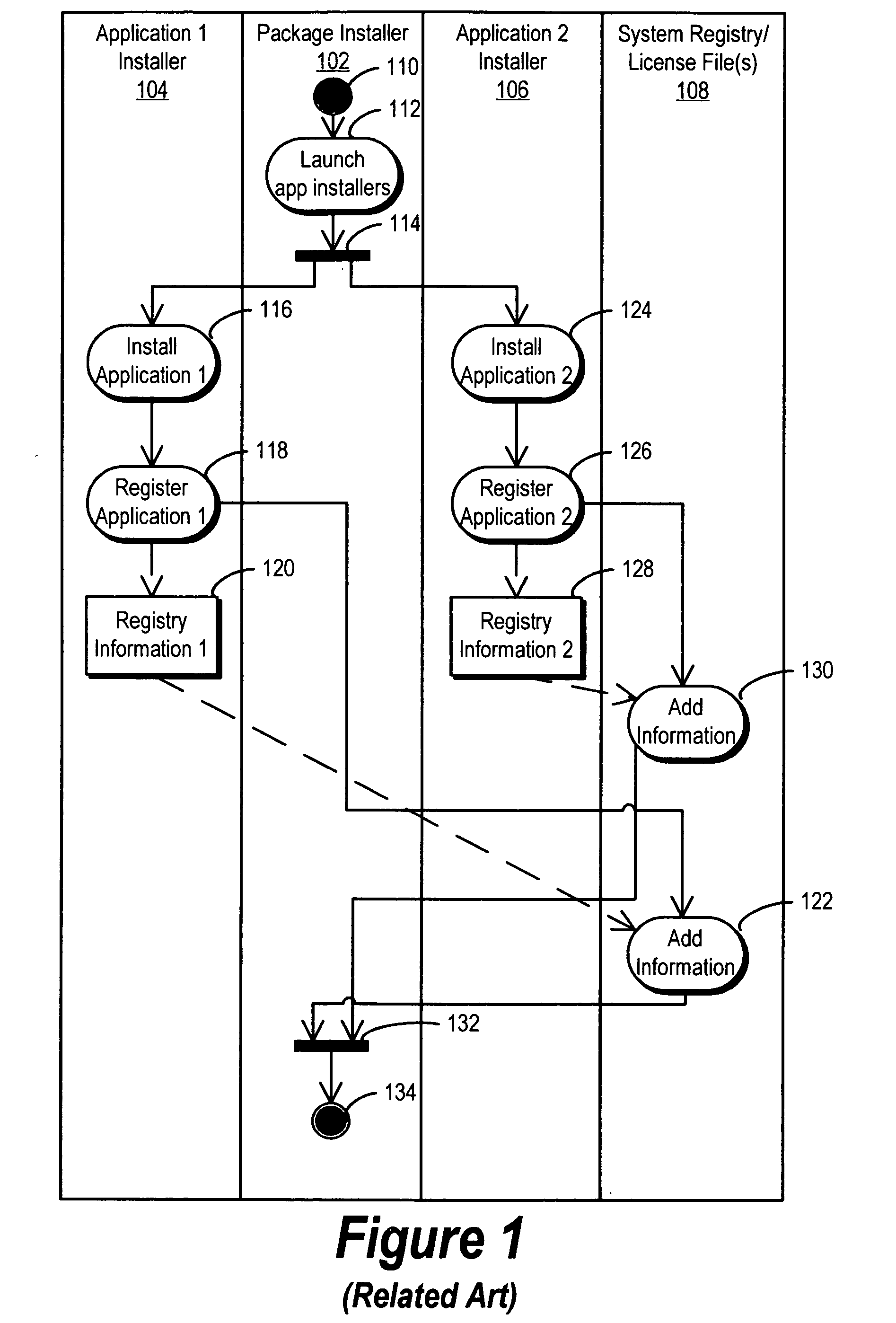
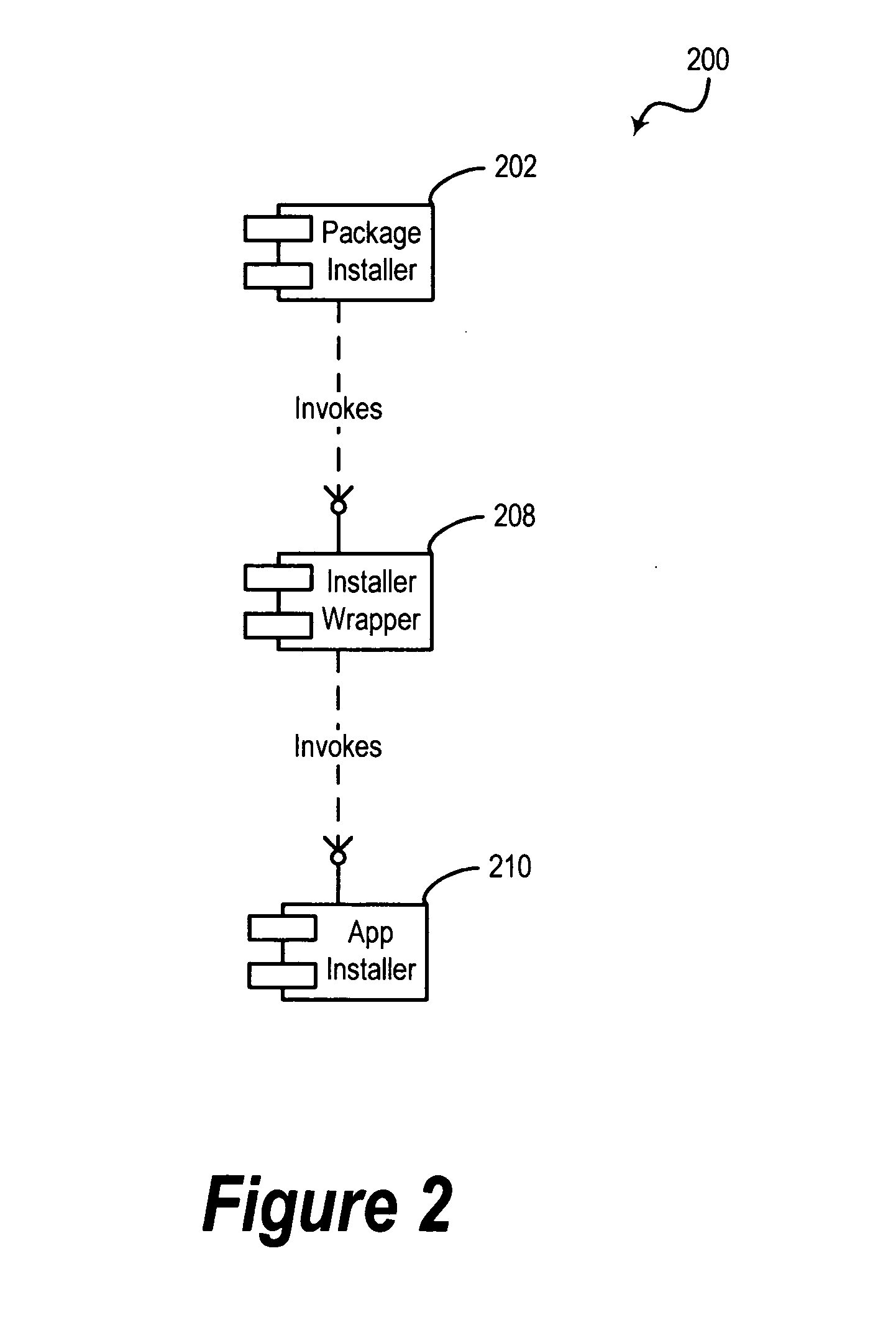
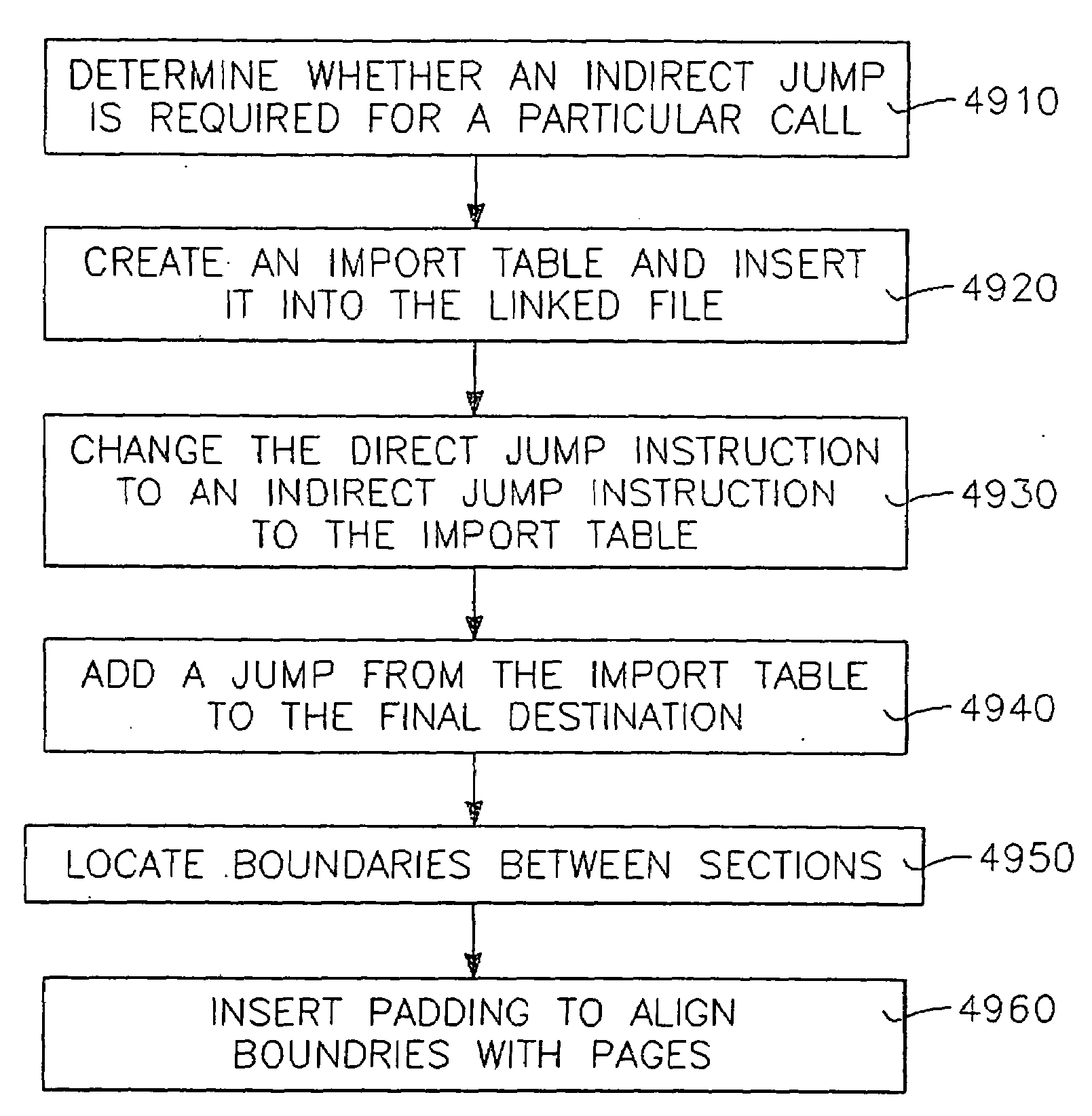
Efficient linking and loading for late binding and platform retargeting
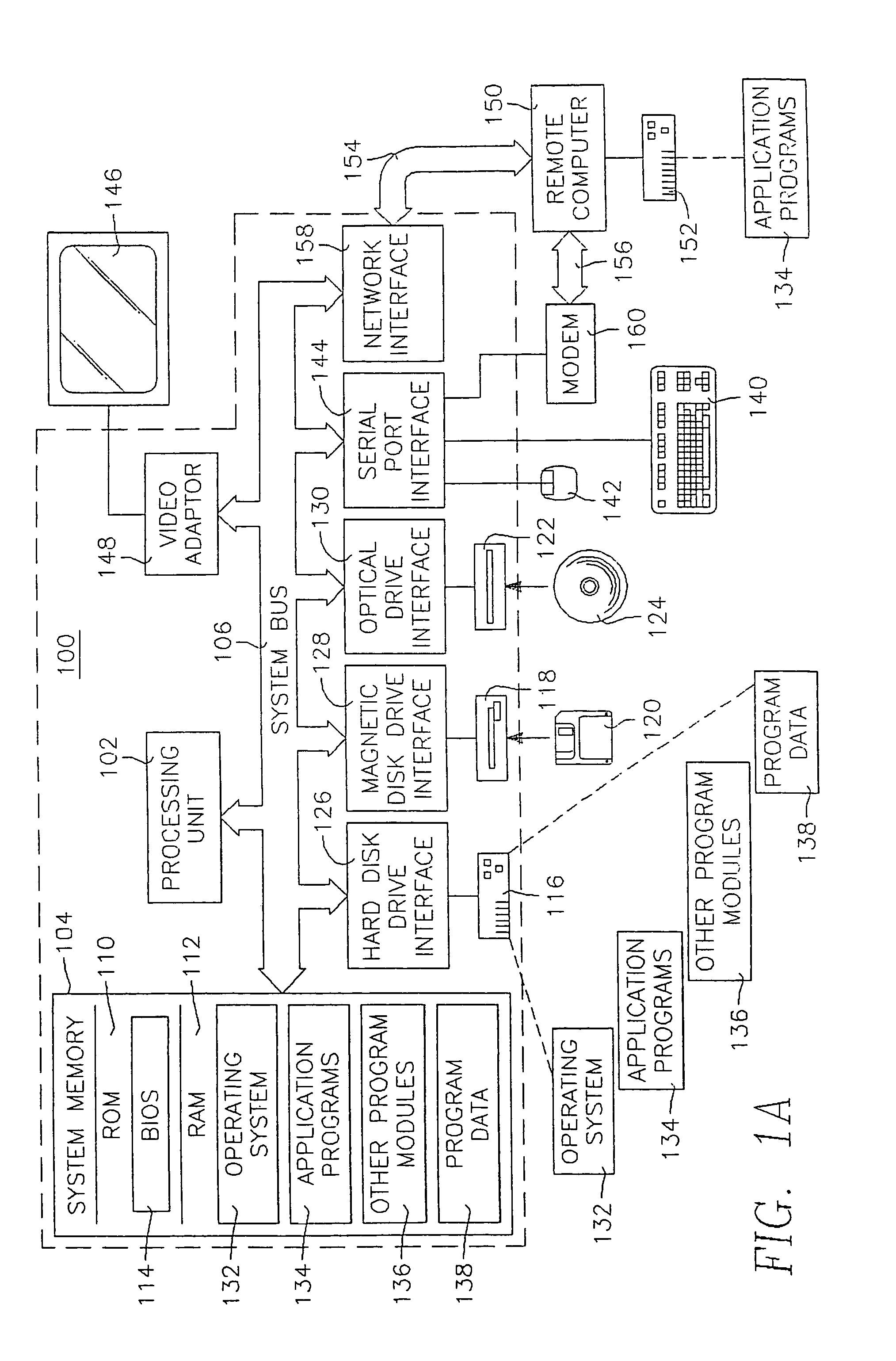
InactiveUS7565665B2Severely restrictedFacilitates version control of versionFinanceDigital data processing detailsVirtual memoryOperational system
A method of producing an executable image from an object file without shared library support from the operating system, wherein the executable image requires a shared library file in order to resolve at least one of the symbols called for in the object file. A method of optimizing the loading of a previously linked file into working memory in a computer for executing in a single address space of the working memory, the file containing an instruction to make an indirect jump to a location in a shared library through an import section of the file. A method for optimizing the loading of a previously linked file into working memory in a computer for executing in a single address space of the working memory, the file containing plural sections with number-filled padding between the end of each section and a succeeding page boundary. A method of optimizing the loading of a previously linked file into working memory in a computer for executing in a memory sharable with other executables. This method includes selecting a portion of code in the previously linked file, removing the portion of code from the previously linked file, and constructing a dynamically linked library file containing the portion of the code, the dynamically linked library file being available to plural files including the previously linked file. A method of converting an image which has been previously linked for executing in an unshared memory into an image optimized for use with virtual memory.
Owner:MICROSOFT TECH LICENSING LLC
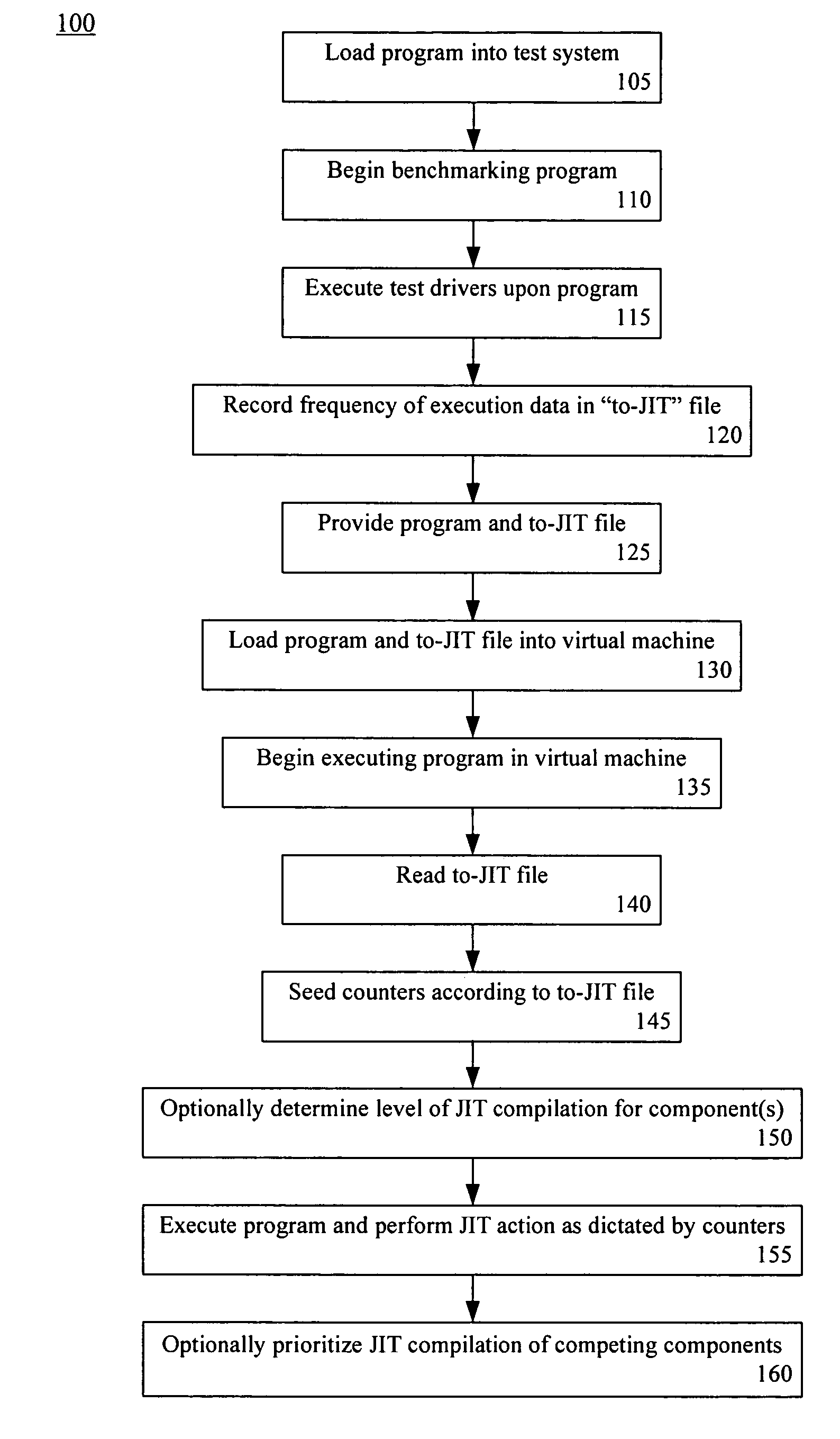
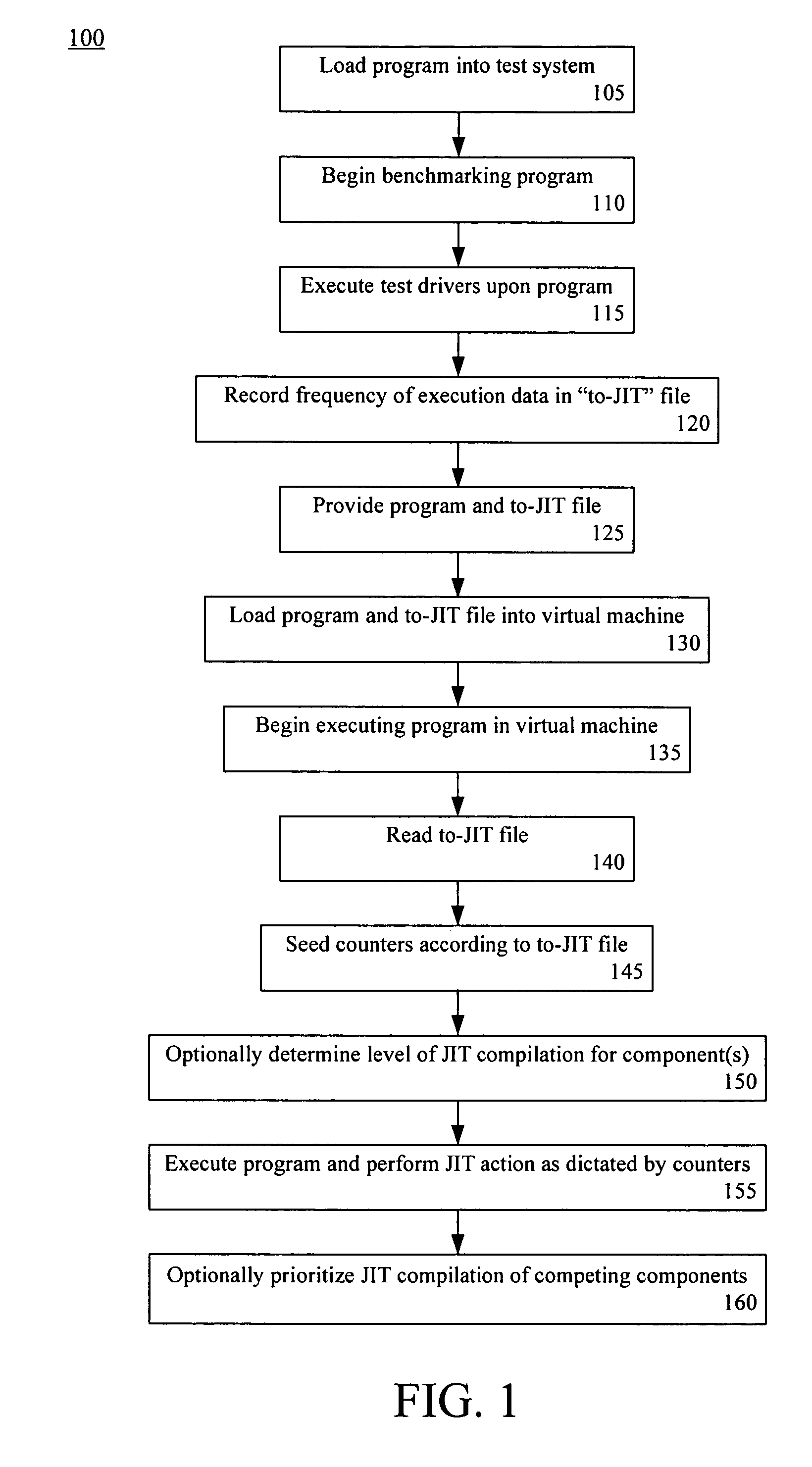
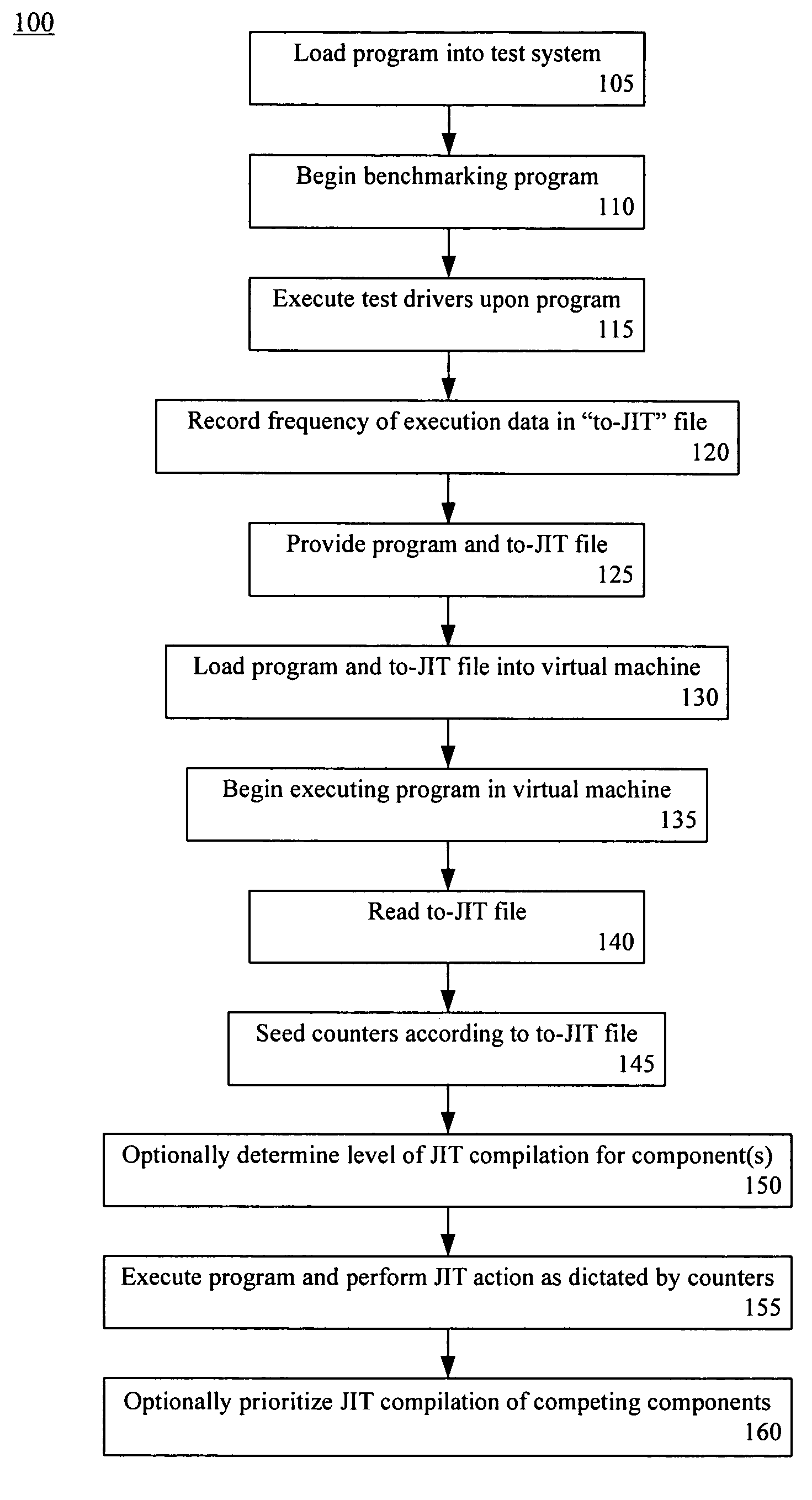
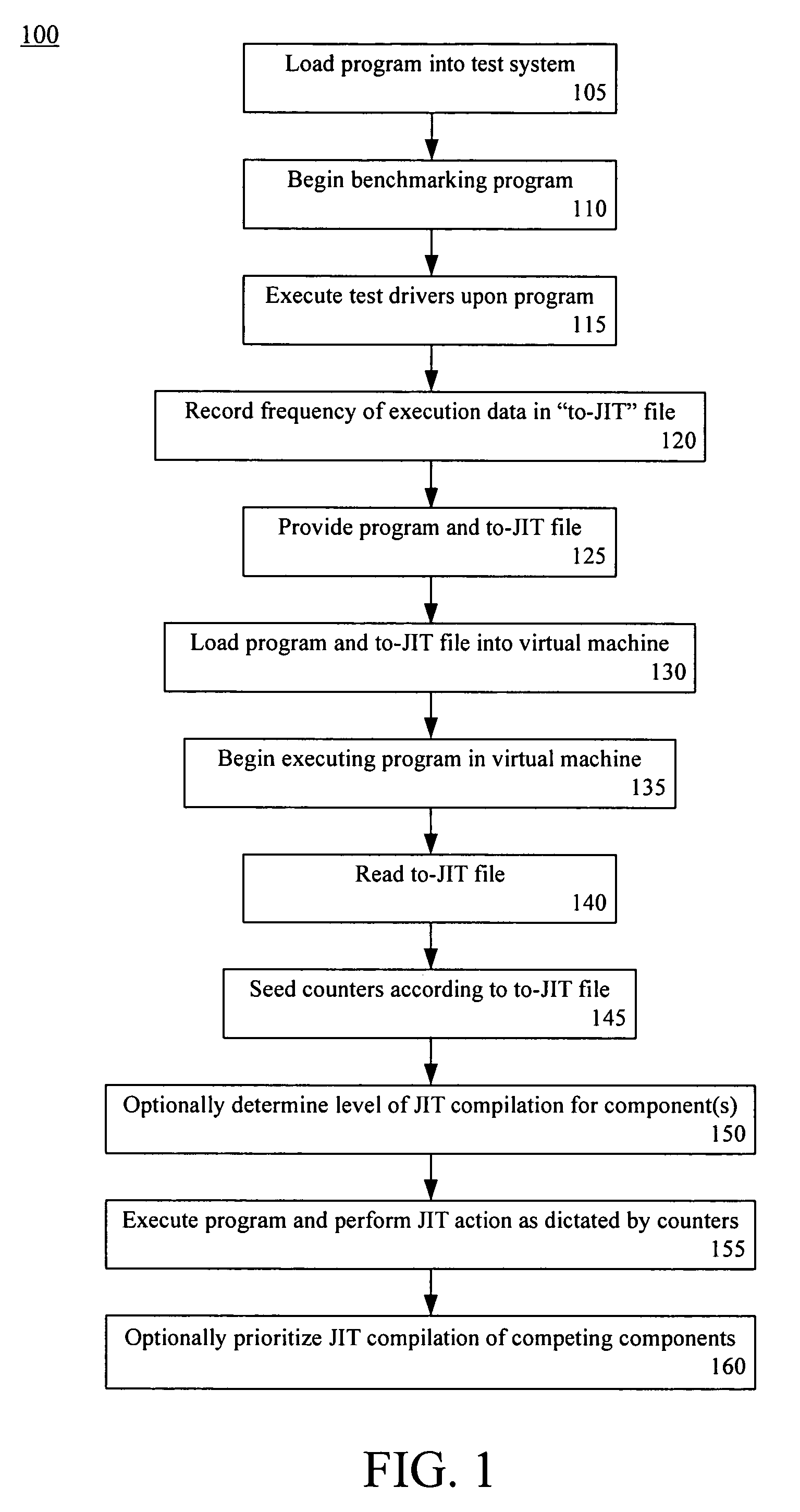
Late binding of optimization information for just in time compilation
InactiveUS20060206884A1Improve computing powerImprove performanceProgram controlMemory systemsJust-in-time compilationParallel computing
A method of optimizing the runtime performance of a program written in an interpreted programming language can include loading, within a virtual machine having a Just In Time (JIT) compiler, the program and a file specifying frequency of execution data for at least one component of the program. The program can be executed. The executing step can include reading the file specifying the frequency of execution data, seeding a counter of the virtual machine associated with the component(s) with a value derived from the frequency of execution data, and performing a JIT action upon the component(s) of the program according to the seeded counter of the virtual machine.
Owner:IBM CORP
Efficient linking and loading for late binding and platform retargeting
InactiveUS20050226406A1Severely restrictedFacilitates version control of versionFinanceDigital data processing detailsVirtual memoryOperational system
A method of producing an executable image from an object file without shared library support from the operating system, wherein the executable image requires a shared library file in order to resolve at least one of the symbols called for in the object file. A method of optimizing the loading of a previously linked file into working memory in a computer for executing in a single address space of the working memory, the file containing an instruction to make an indirect jump to a location in a shared library through an import section of the file. A w method for optimizing the loading of a previously linked file into working memory in a computer for executing in a single address space of the working memory, the file containing plural sections with number-filled padding between the end of each section and a succeeding page boundary. A method of optimizing the loading of a previously linked file into working memory in a computer for executing in a memory sharable with other executables. This method includes selecting a portion of code in the previously linked file, removing the portion of code from the previously linked file, and constructing a dynamically linked library file containing the portion of the code, the dynamically linked library file being available to plural files including the previously linked file. A method of converting an image which has been previously linked for executing in an unshared memory into an image optimized for use with virtual memory.
Owner:MICROSOFT TECH LICENSING LLC
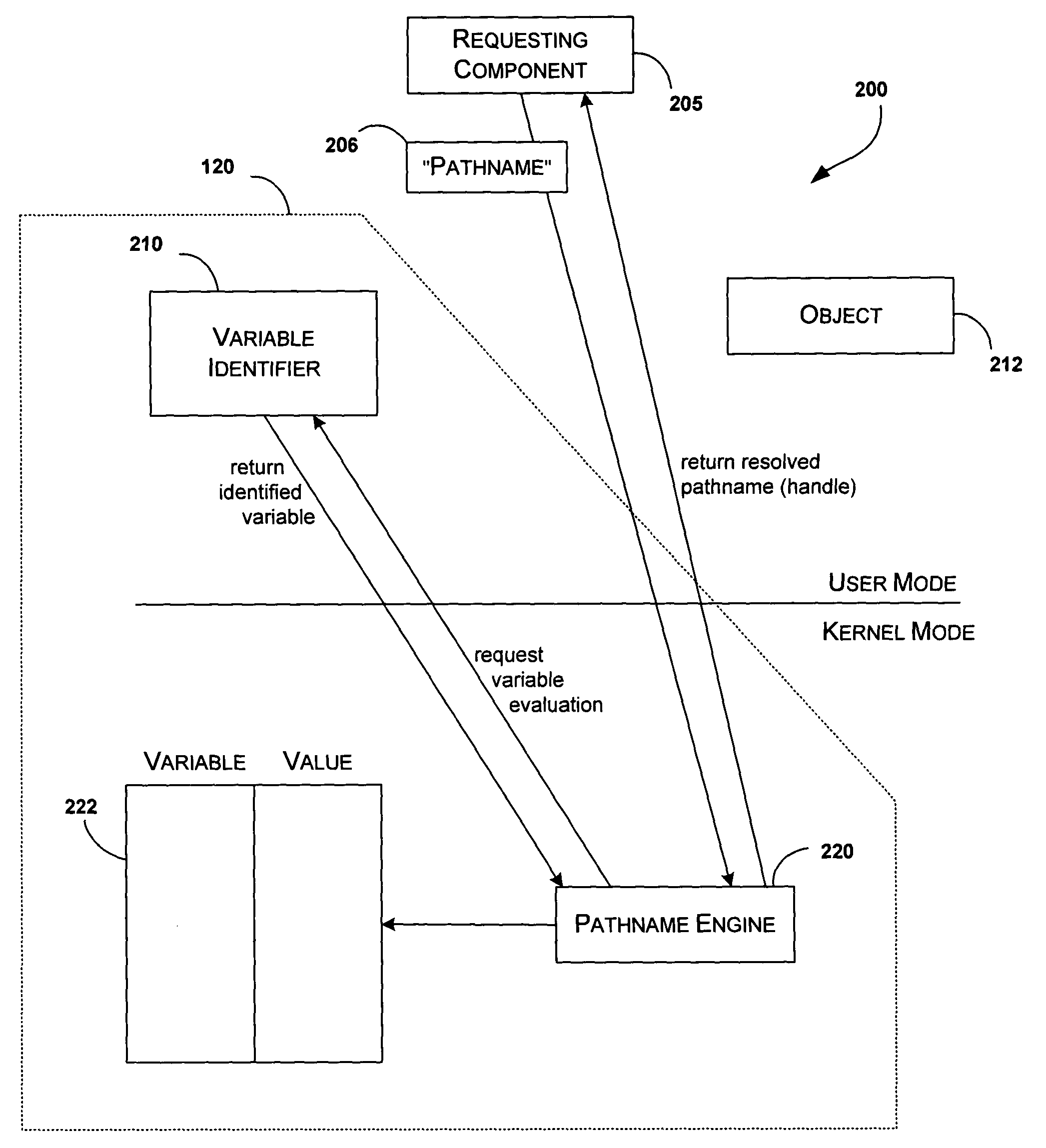
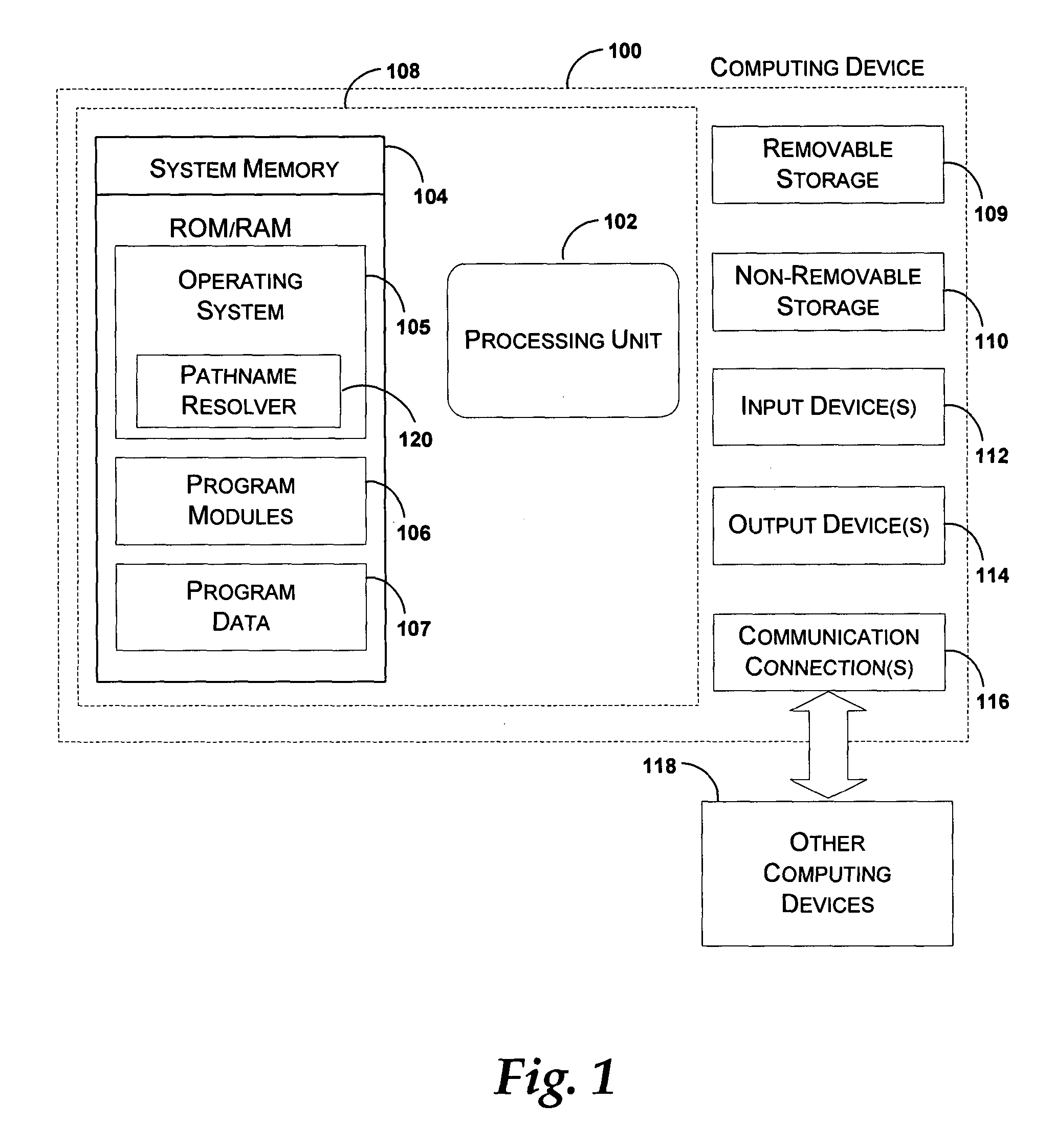
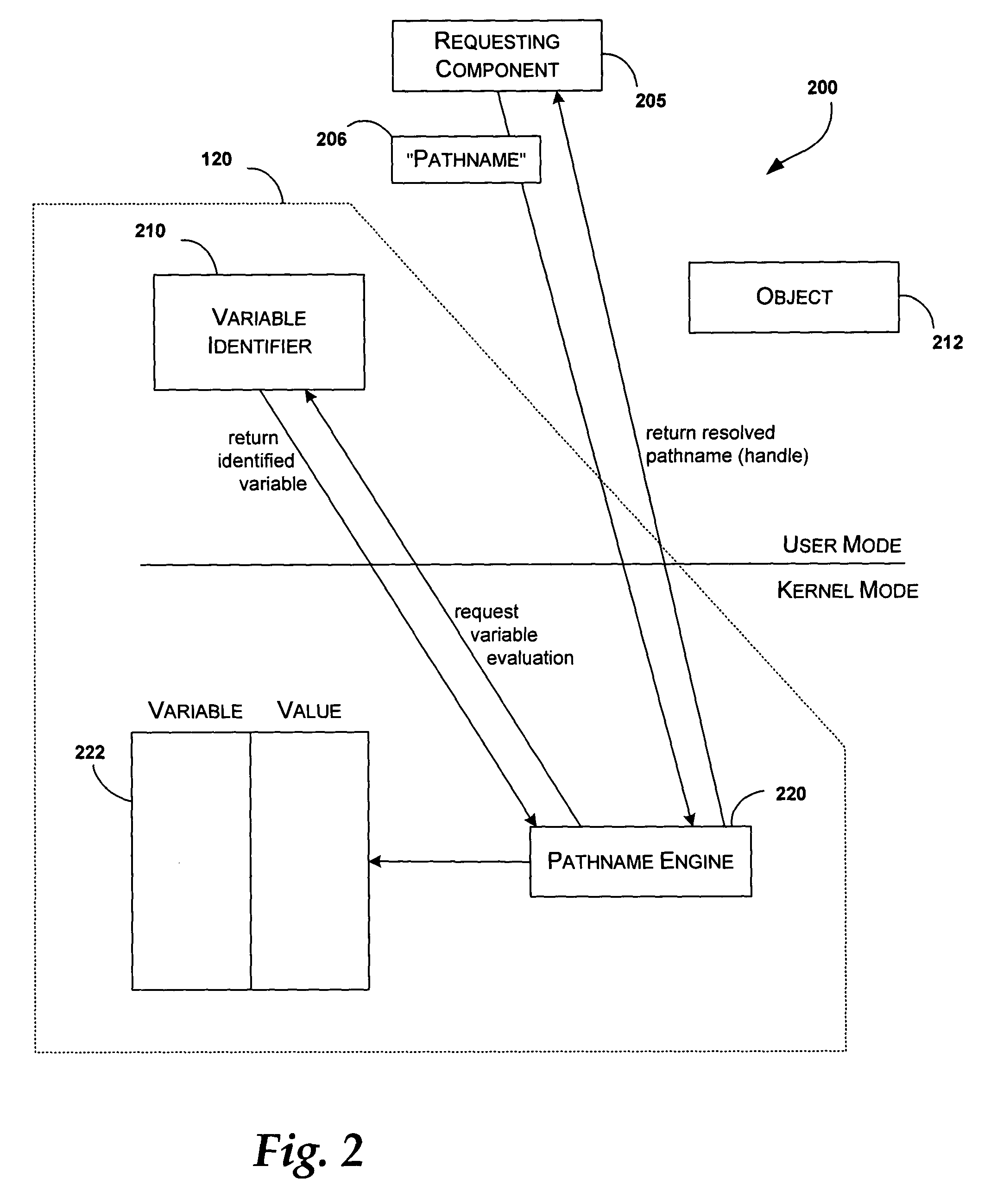
Method and apparatus for late-binding/dynamic pathname resolution
InactiveUS20050044075A1Digital data processing detailsSpecial data processing applicationsTheoretical computer scienceLate binding
Late-binding / dynamic pathname resolution can be performed by a variable identifier operating in user or kernel mode, and a pathname engine and a data structure operating in kernel mode. The variable identifier identifies a variable in a pathname. The pathname engine evaluates the variable by converting the variable into a character string such that a path to an object file is established. The pathname engine determines a scope of potential character string values for the variable by mapping the variable to corresponding values stored in the data structure. Each variable has a well-defined scope of values because the only values available are the values selected for storage in the data structure. The mechanism for establishing values is extensible such that variable / value pairs can be implemented in the data structure at any time.
Owner:MICROSOFT TECH LICENSING LLC
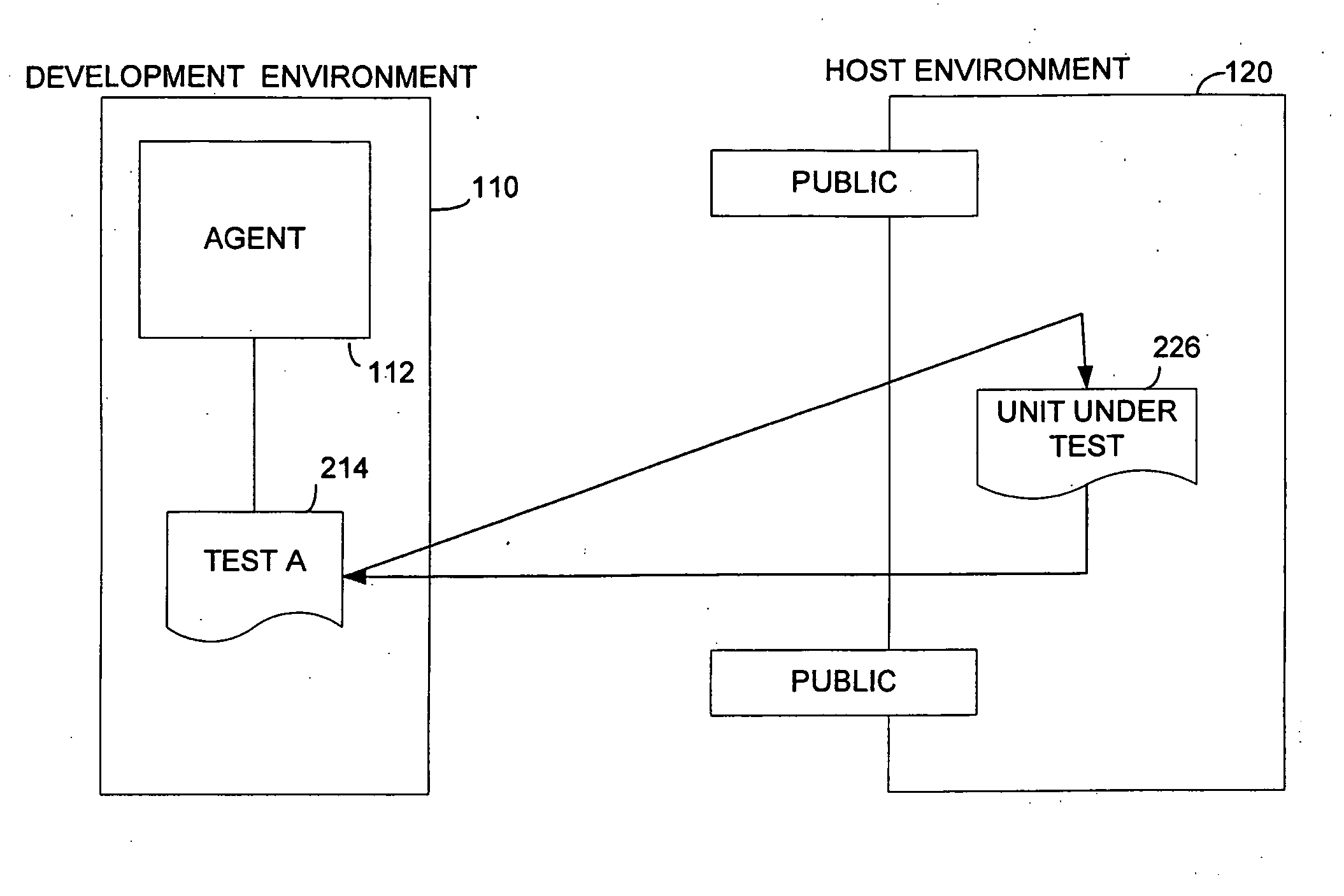
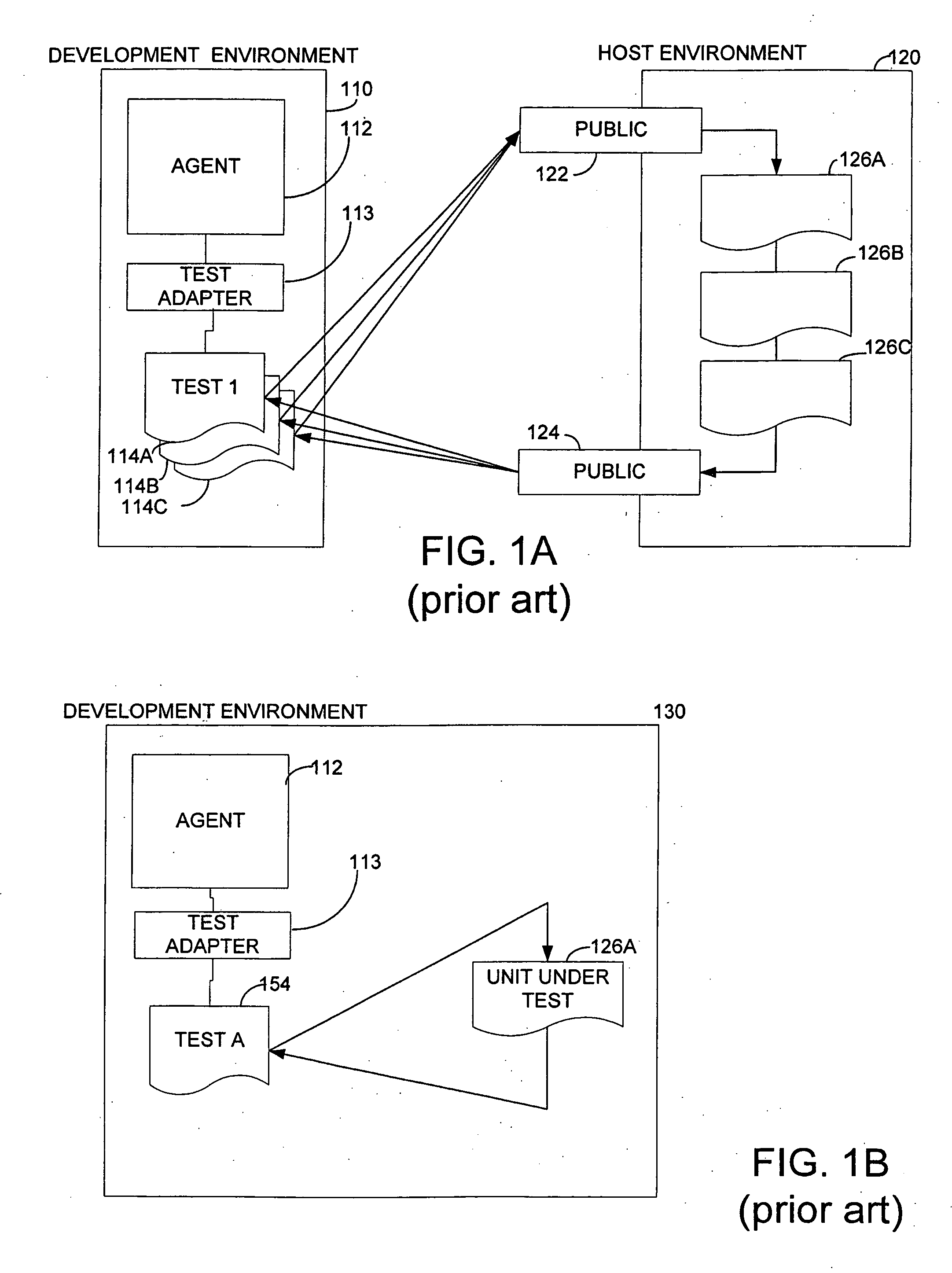
Method and apparatus for executing unit tests in application host environment
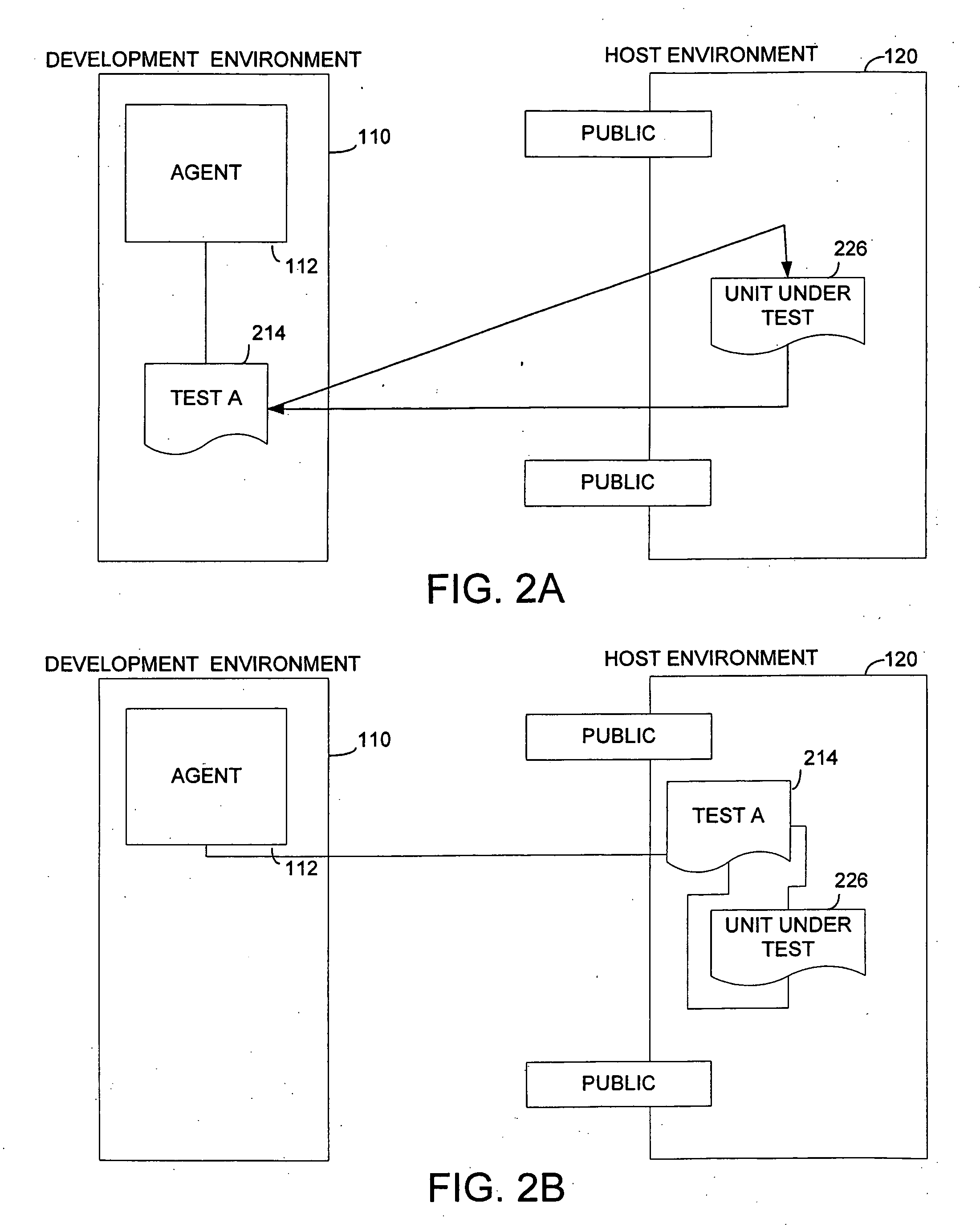
InactiveUS20060218446A1Available for useDetecting faulty computer hardwareSpecific program execution arrangementsSpecific testHosting environment
A development environment in which unit tests are prepared. The unit tests run in a host environment for more complete and accurate testing of program units. The development environment uses a test execution shim to access an adapter running in the host environment. The host adapter may invoke other program objects that run specific tests. Such objects may late bind to the unit under test. An accessor class may facilitate late binding to the specific unit under test while allowing tests authored in the development environment to use context sensitive information needed to access the unit under test.
Owner:MICROSOFT TECH LICENSING LLC
Dynamically extensible rule-based expert-system shell for database-computing environments
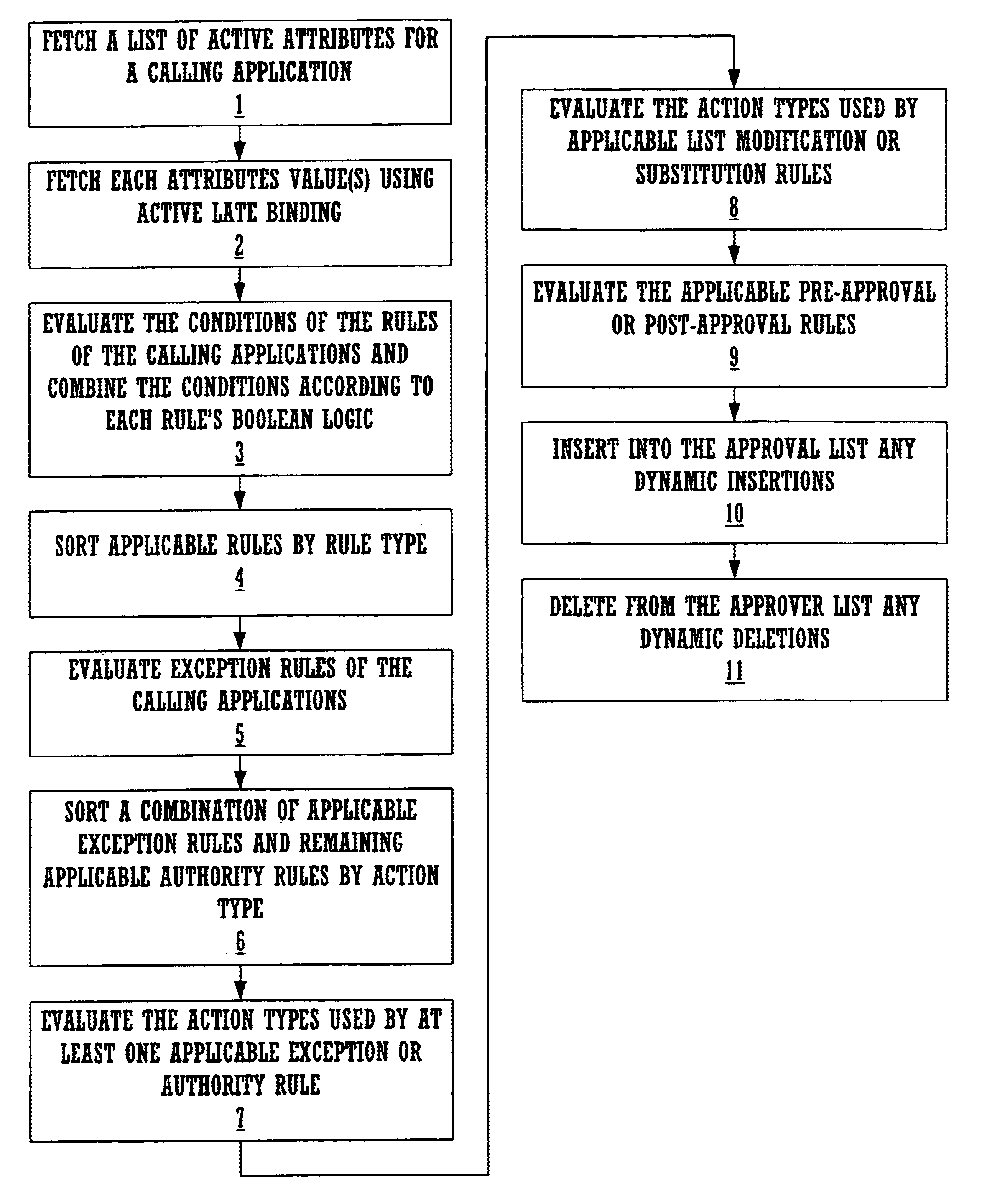
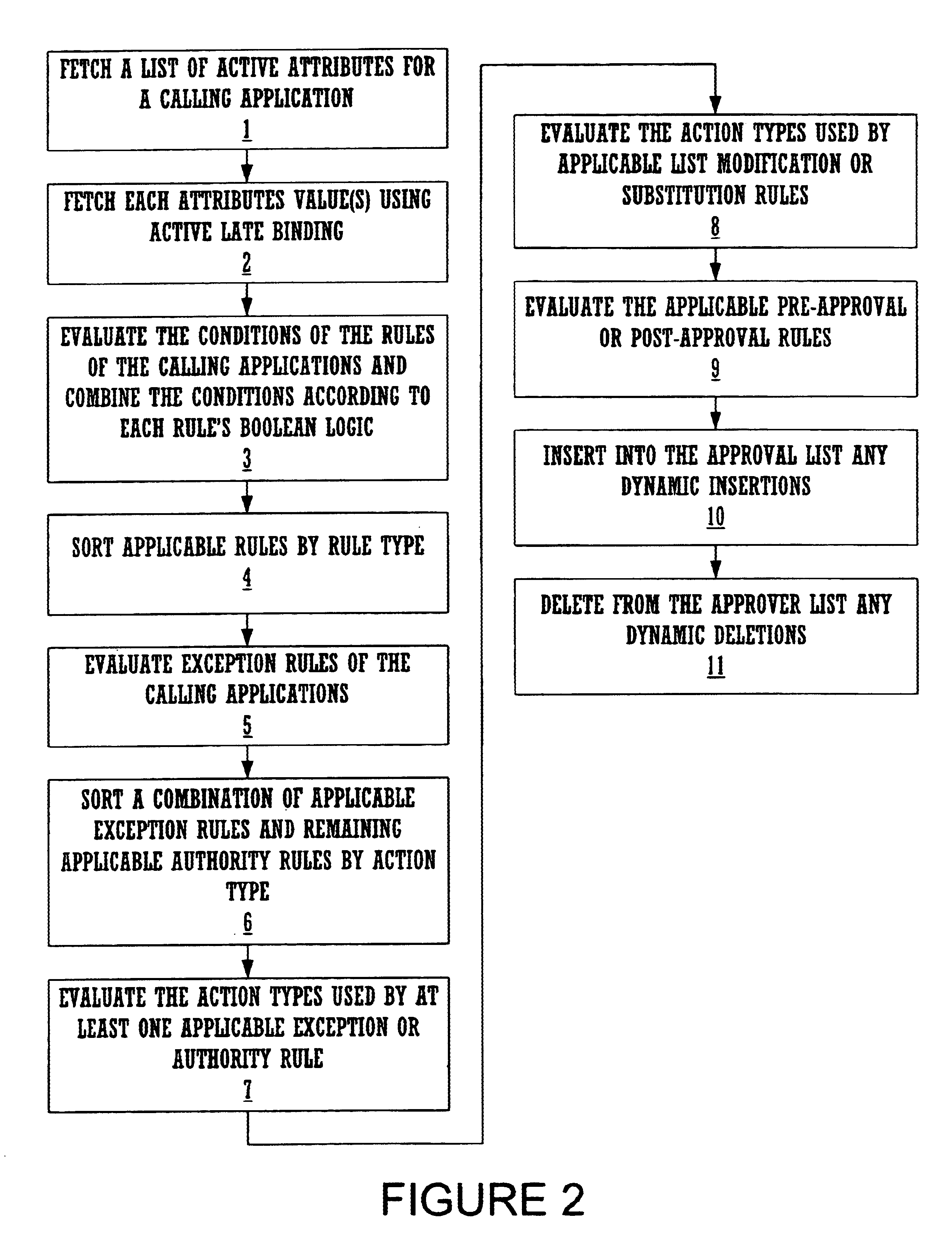
InactiveUS6847957B1Office automationKnowledge representationRule based expert systemRelational database management system
A computer-implemented method for flexibly and efficiently representing and applying business rules in a transaction-processing relational database management system (RDBMS) environment. The method includes providing a deterministic rule-based expert-system shell. A late-binding mechanism within the RDBMS environment is also provided. An extensible data-maintenance mechanism is created for the rule-based expert-system shell. The extensible data-maintenance mechanism maintains sets of approval rules governing business transactions generated by other transaction-processing applications. The data-maintenance mechanism uses late binding to make the sets of rules and rule components stored in the data-maintenance mechanism arbitrarily extensible. A rule-processing engine applies the sets of approval rules stored in the extensible data-maintenance mechanism to business transactions originating in transaction-processing applications. The method provides for a plurality of approval-rule types, each making a qualitatively different contribution to the list of approvers required for any given business transaction. The method calculates the list of approvers required for a given business transaction by applying the appropriate set of approval rules to the transaction.
Owner:ORACLE INT CORP
Real-time messaging method and apparatus
ActiveUS9178916B2Lower capability requirementsMultiple digital computer combinationsOffice automationReal-time Transport ProtocolMessage passing
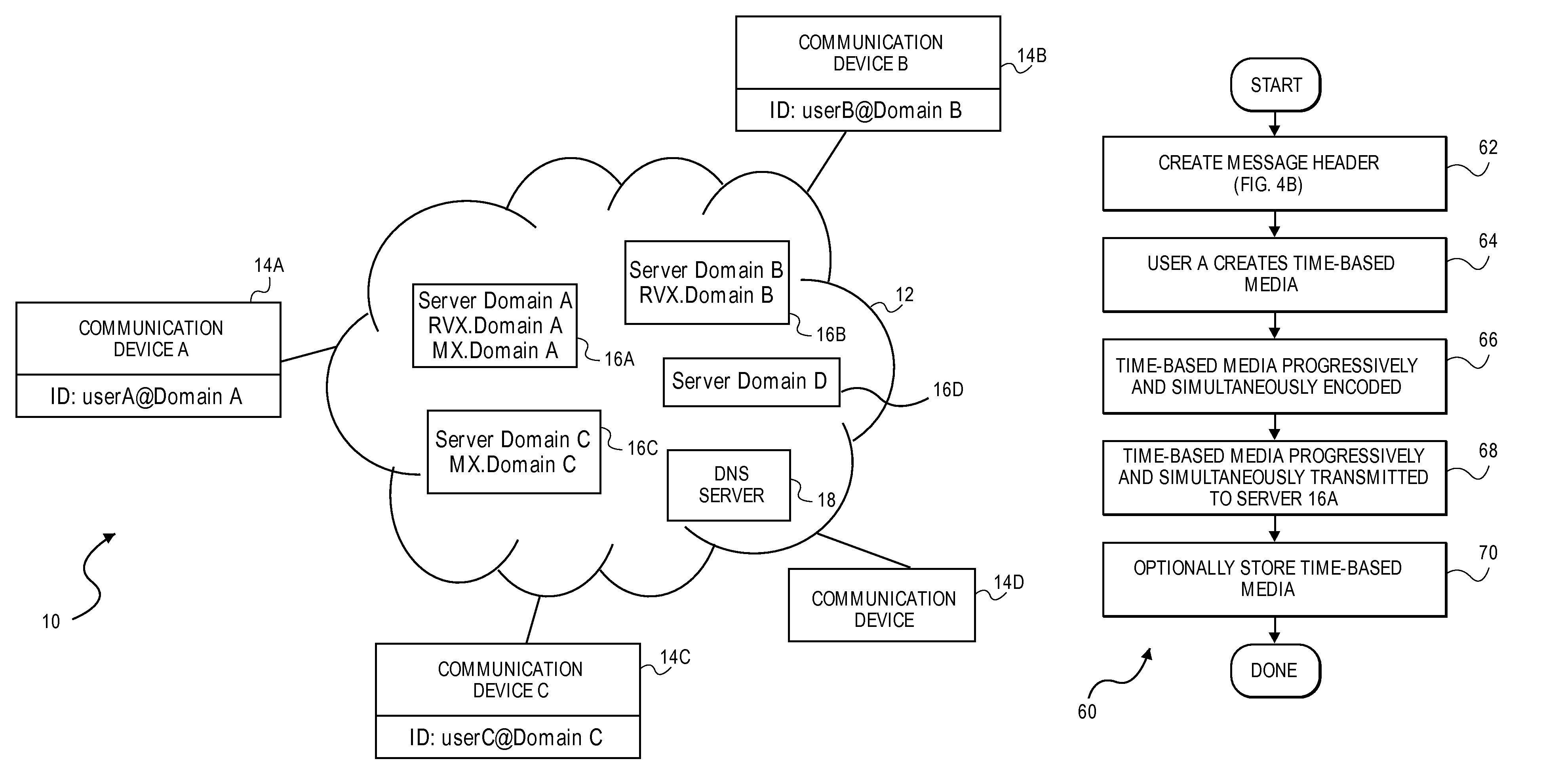
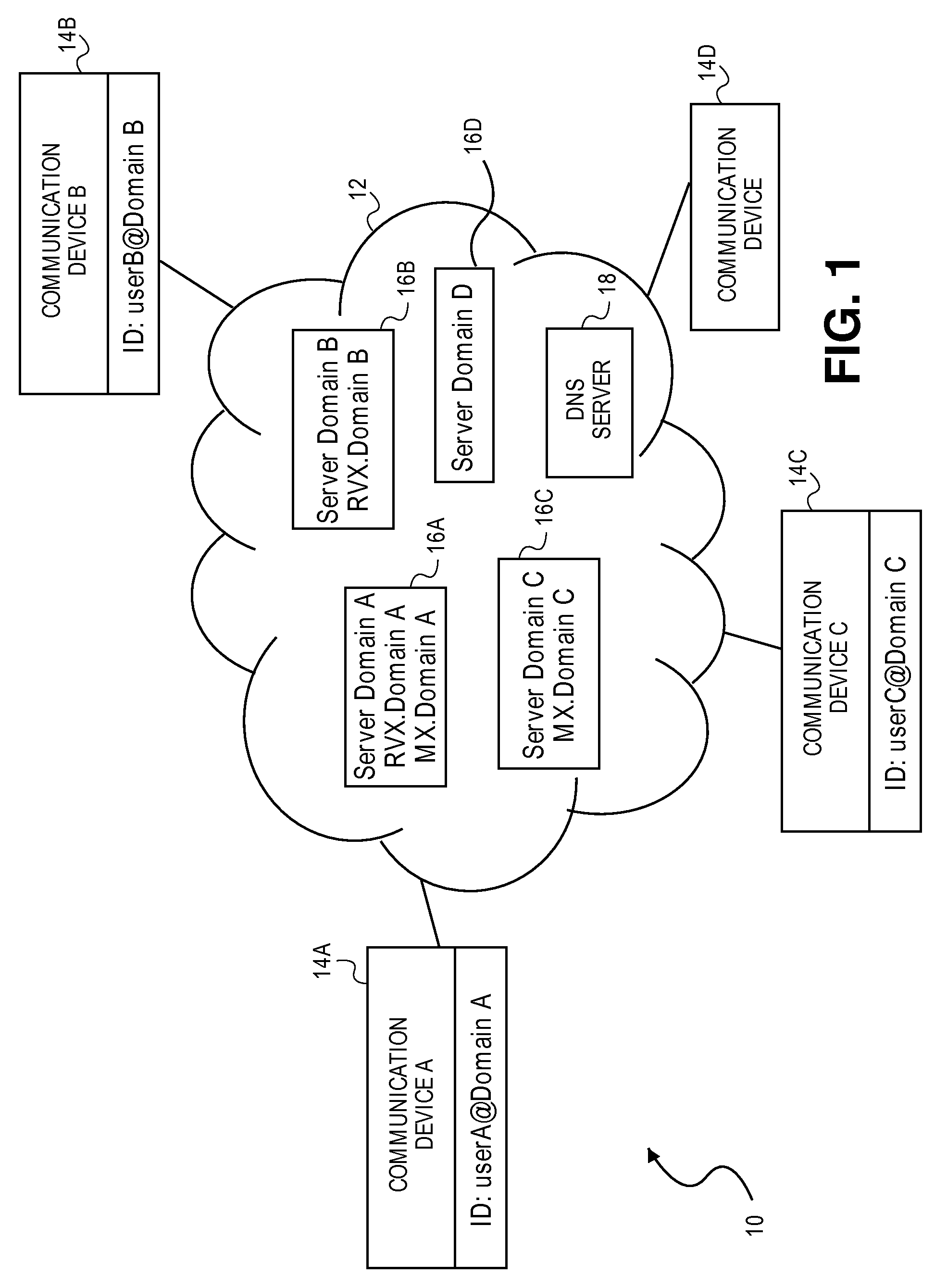
A system and method for the late-biding of time-based media in real-time With late binding, the sender may create time-based media before or at the same time an active delivery route to the recipient is discovered. As soon as the route becomes available, the media is transmitted. The existing DNS and email infrastructure is possibly used for route discovery, while any real-time transmission protocol may be used for the actual delivery of the media. “Progressive” emails may also be used for the real-time delivery of time-based media.
Owner:VOXER IP
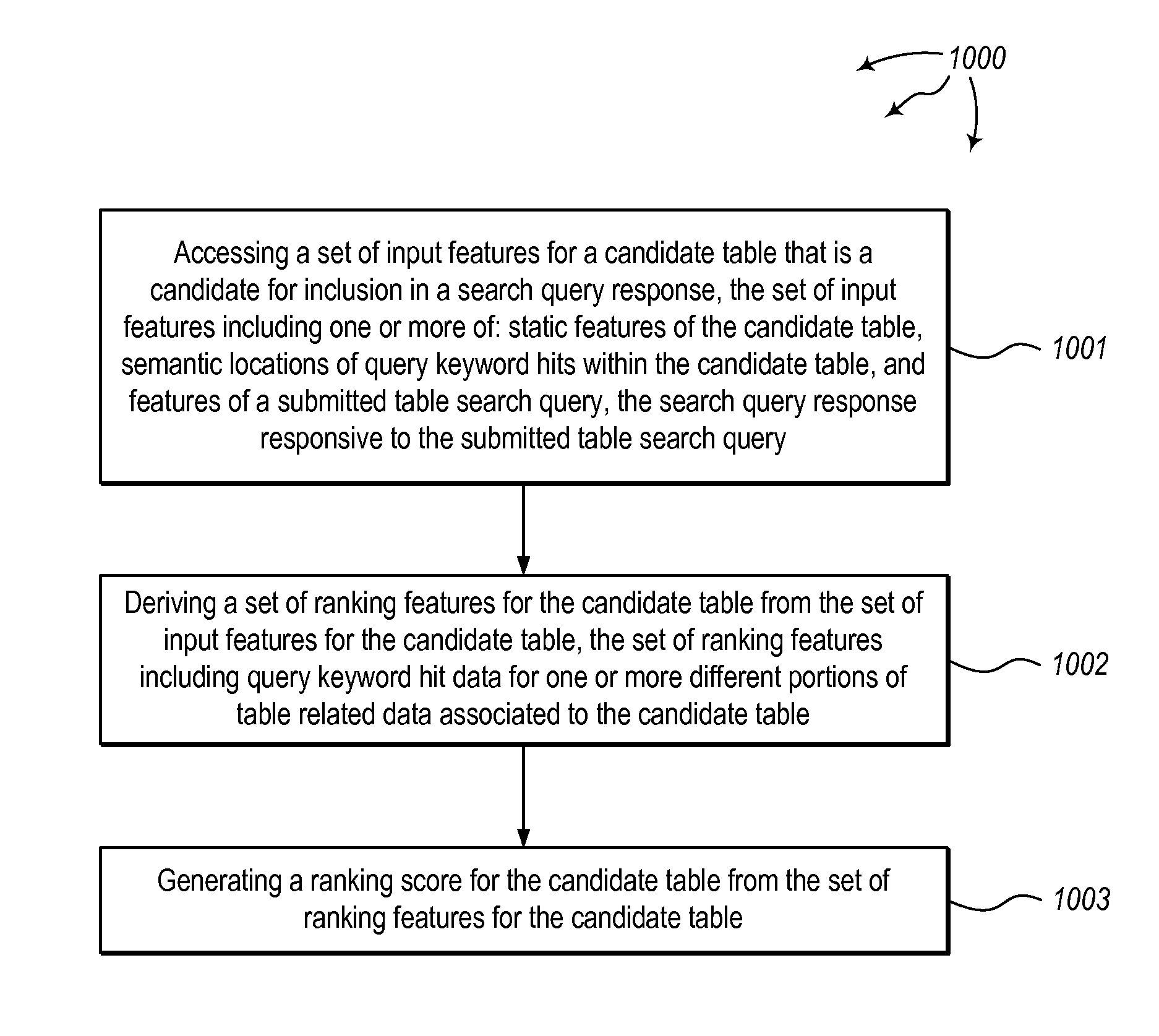
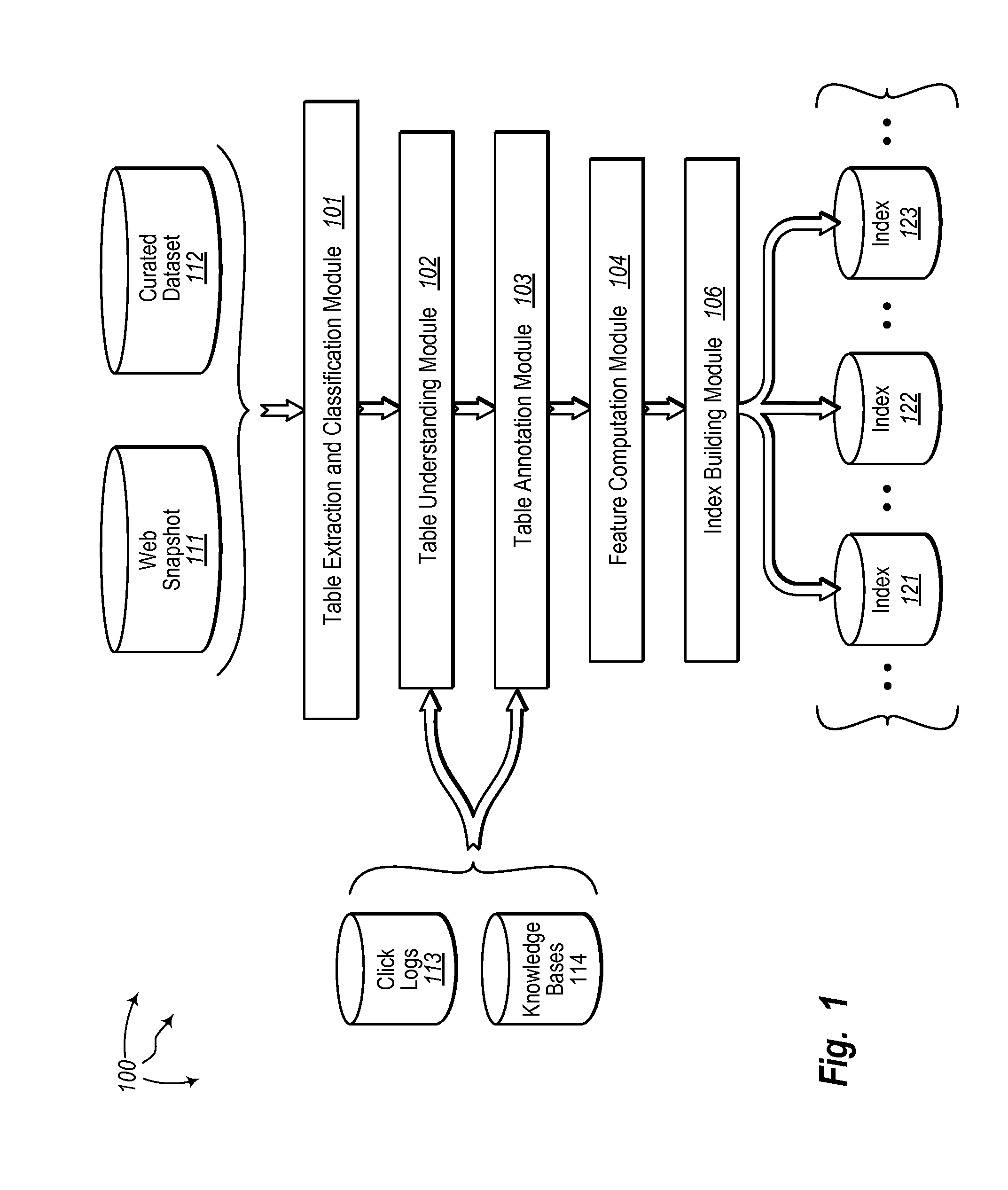
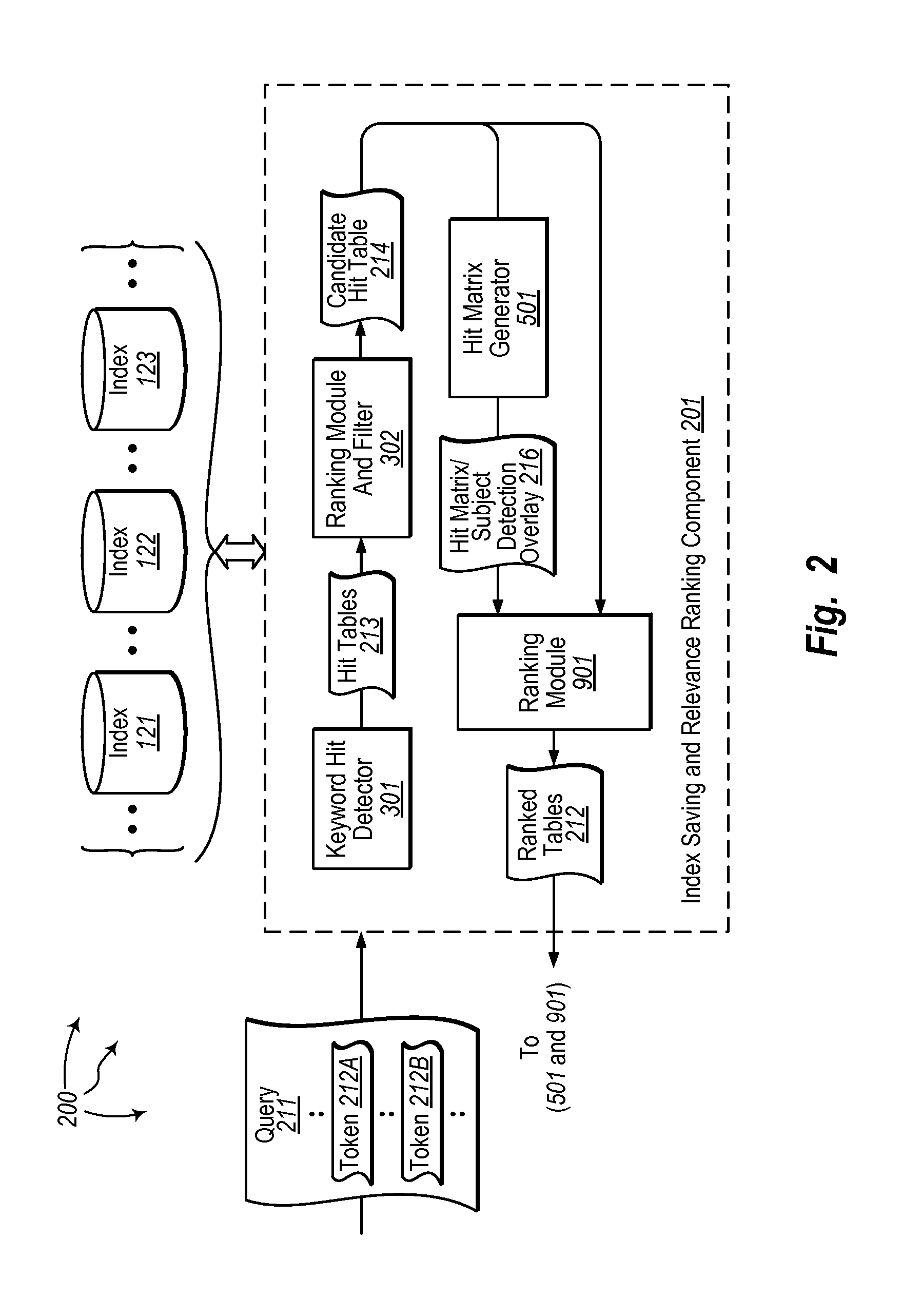
Ranking tables for keyword search
The present invention extends to methods, systems, and computer program products for ranking tables for keyword search. Aspects of the invention include generating lists of candidate tables for inclusion in a search query response, computing table hit matrices, retrieving content from fields of candidate tables having keyword hits, generating ranking features of tables, and computing ranking scores for tables. Aspects of the invention can be used to match keywords against column names, to match keywords against values in subject and non-subject columns, and to match keywords against table descriptions like page titles, table captions, cell values, nearest headings and surrounding text. Which keywords are matched against which fields can depend on the table and / to the query (referred to as “late binding”).
Owner:MICROSOFT TECH LICENSING LLC
Semantic note taking system
ActiveUS20100191807A1Multiple digital computer combinationsWebsite content managementUser inputUser interface
A semantic note taking system and method for collecting information, enriching the information, and binding the information to services is provided. User-created notes are enriched with labels, context traits, and relevant data to minimize friction in the note-taking process. In other words, the present invention is directed to collecting unscripted data, adding more meaning and use out of the data, and binding the data to services. Mutable and late-binding to services is also provided to allow private thoughts to be published to a myriad of different applications and services in a manner compatible with how thoughts are processed in the brain. User interfaces and semantic skins are also provided to derive meaning out of notes without requiring a great deal of user input.
Owner:APPLE INC
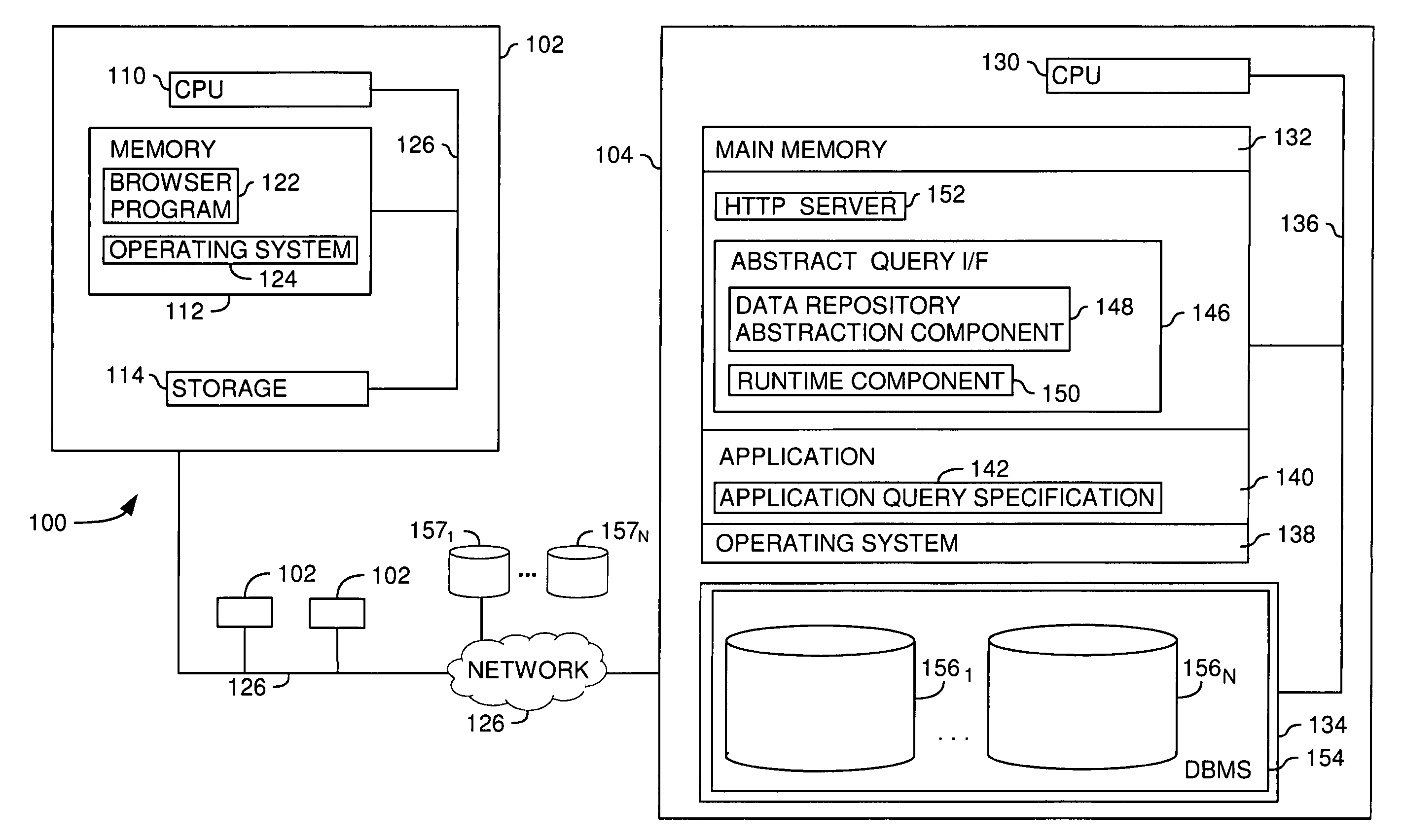
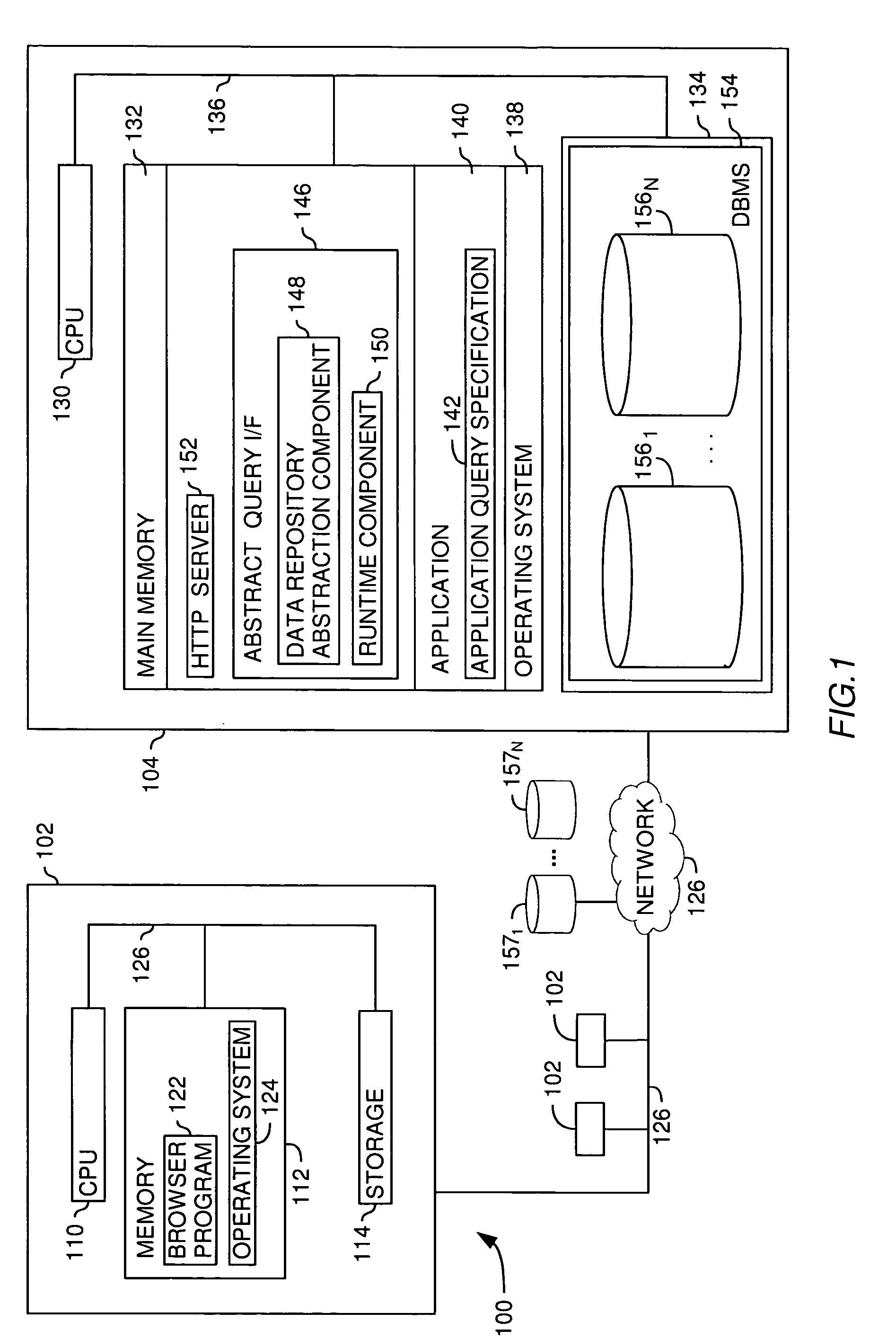
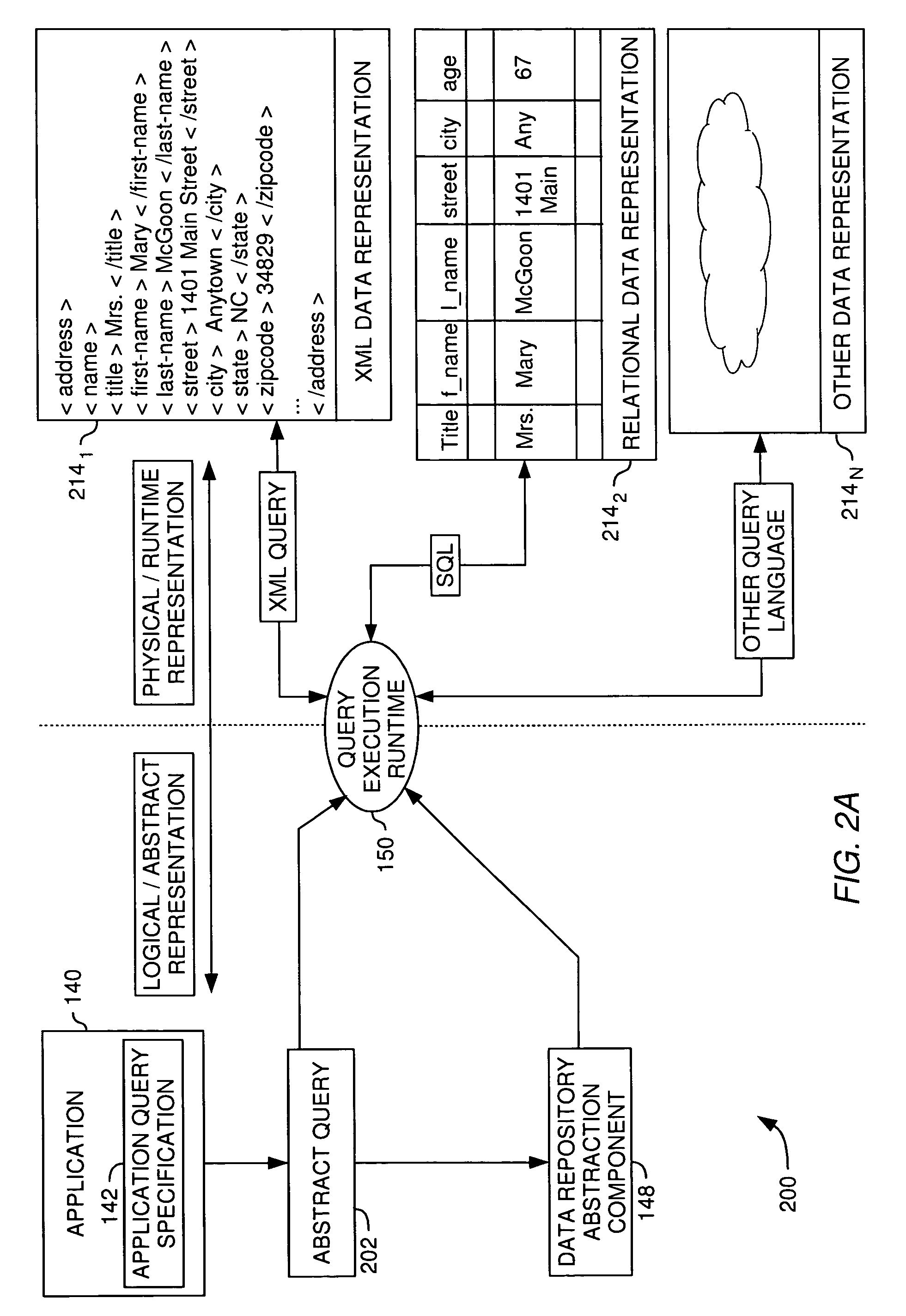
Extending data access and analysis capabilities via abstract, polymorphic functions
InactiveUS20060074873A1Digital data information retrievalSpecial data processing applicationsFunction definitionData access
An abstract database is an effective way to reduce the complexity of a large database management system. Abstract databases allow a user to compose queries based on the logical relationships among data items, without requiring a user to understand the underlying database schema used to store the data in the database system. Embodiments of the invention generally provide methods, systems, and articles of manufacture that extend the capabilities of an abstract database to include “late bound” polymorphic functions in an abstract data layer. Abstract functions are “late bound” because the function definition (i.e., the execution logic) is not determined until the function is actually invoked. They are polymorphic because same function may operate using many different many data input types. Additionally, abstract functions are generally transparent to the end user. That is, they are presented to the user as an additional object that may be used to compose queries of data represented by the abstract data layer undifferentiated from other data elements used to compose an abstract query.
Owner:IBM CORP
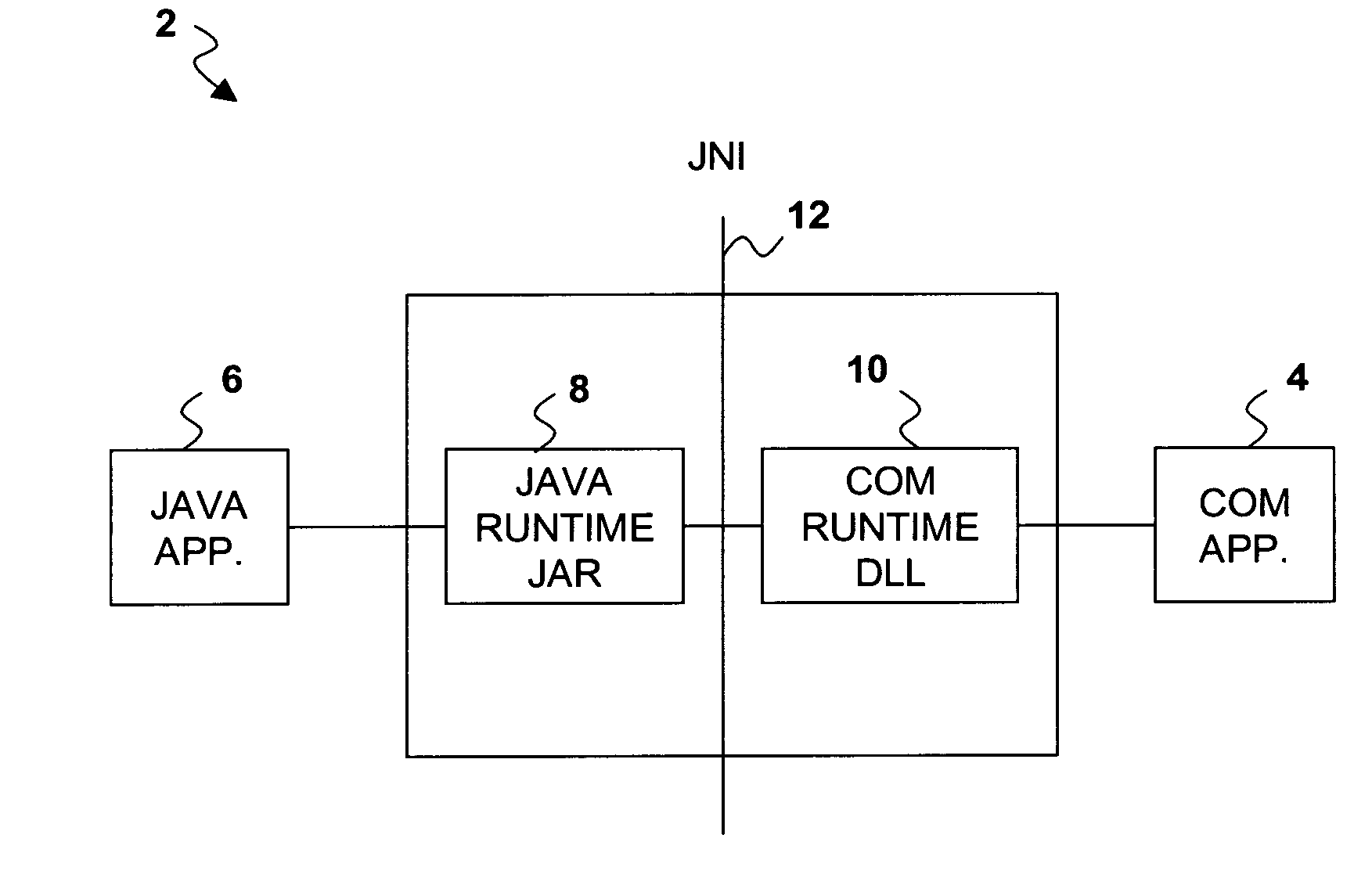
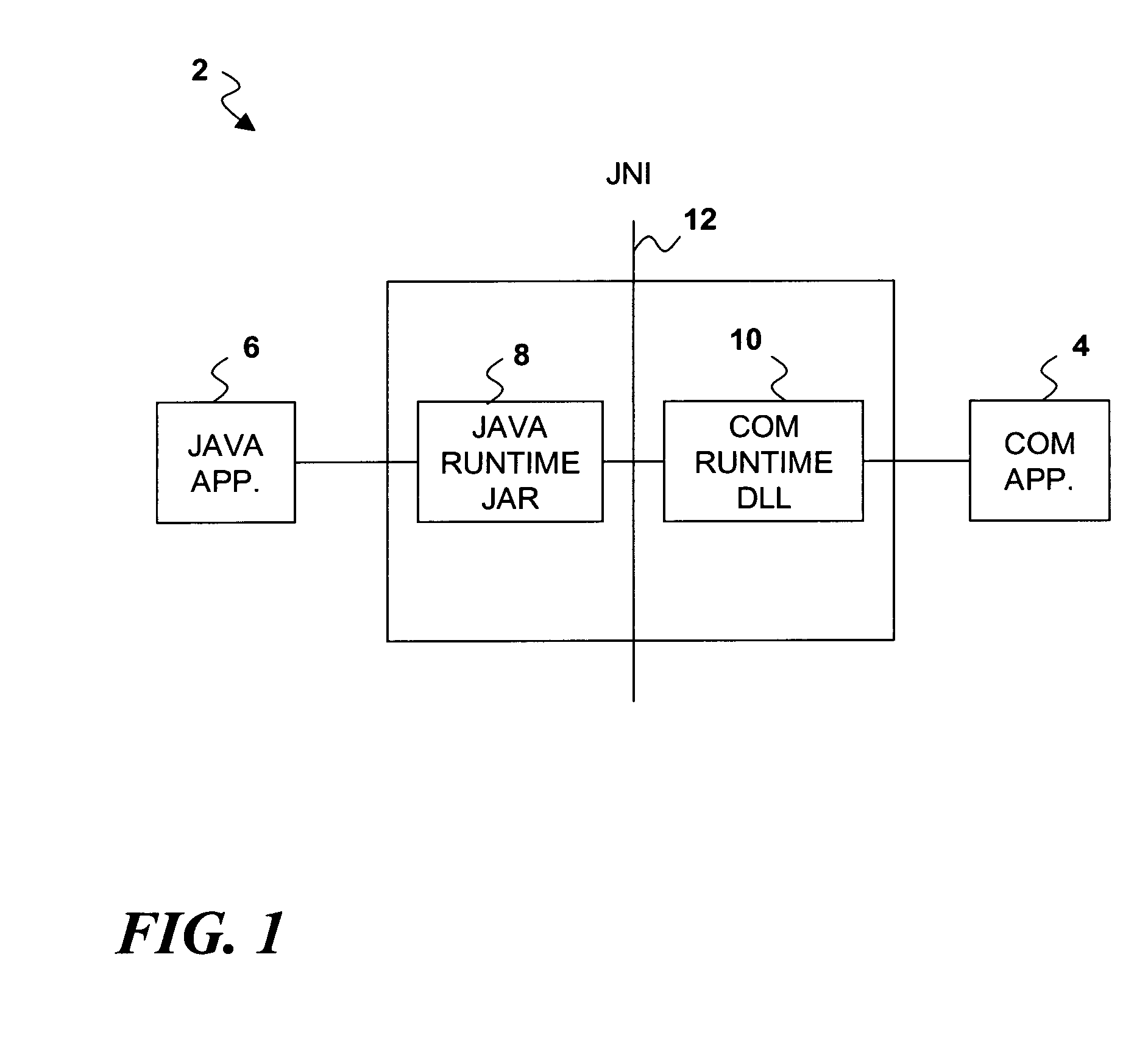
Automation of Java application using enhanced late-bound support
InactiveUS20070038986A1Enhanced late-bound COM-to-Java supportProgram controlMemory systemsJava classesApplication software
A Java / COM bridge provides enhanced late-bound COM-to-Java support. The Java / COM bridge allows a COM application to make a late bound call to a Java class in a Java application wherein the late bound call contains a parameter indicating that the Java class should not be instantiated. The Java / COM bridge returns to the COM application a static COM proxy representing the Java class without instantiating the Java class. Using the static COM proxy, the COM application can call static methods and reference static variables of the Java class. The COM application can also call constructors of the Java class that take parameters by passing the parameters without specifying a method. The Java / COM bridge will identify the Java class constructor based on the specified parameters and instantiate a Java object by calling the identified constructor with the specified parameters.
Owner:IBM CORP
Late binding of optimization information for just in time compilation
InactiveUS7568190B2Improve computing powerImprove performanceProgram controlMemory systemsJust-in-time compilationLate binding
A method of optimizing the runtime performance of a program written in an interpreted programming language can include loading, within a virtual machine having a Just In Time (JIT) compiler, the program and a file specifying frequency of execution data for at least one component of the program. The program can be executed. The executing step can include reading the file specifying the frequency of execution data, seeding a counter of the virtual machine associated with the component(s) with a value derived from the frequency of execution data, and performing a JIT action upon the component(s) of the program according to the seeded counter of the virtual machine.
Owner:INT BUSINESS MASCH CORP
Semantic note taking system
ActiveUS8096477B2Digital data processing detailsCharacter and pattern recognitionUser inputUser interface
Owner:APPLE INC
Efficient linking and loading for late binding and platform retargeting
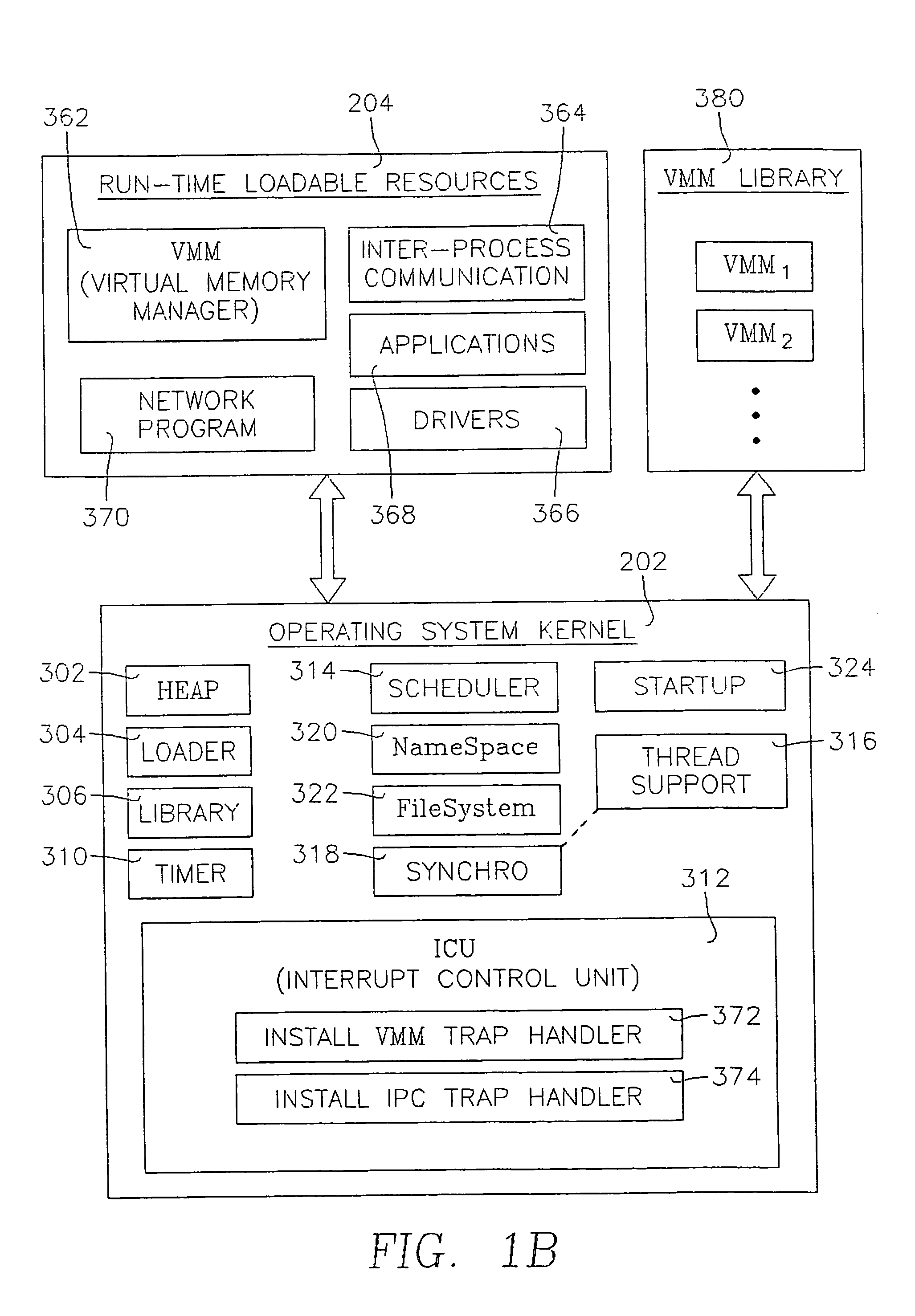
InactiveUS20090133042A1Severely restrictedMultiprogramming arrangementsCode compilationOperational systemWork memory
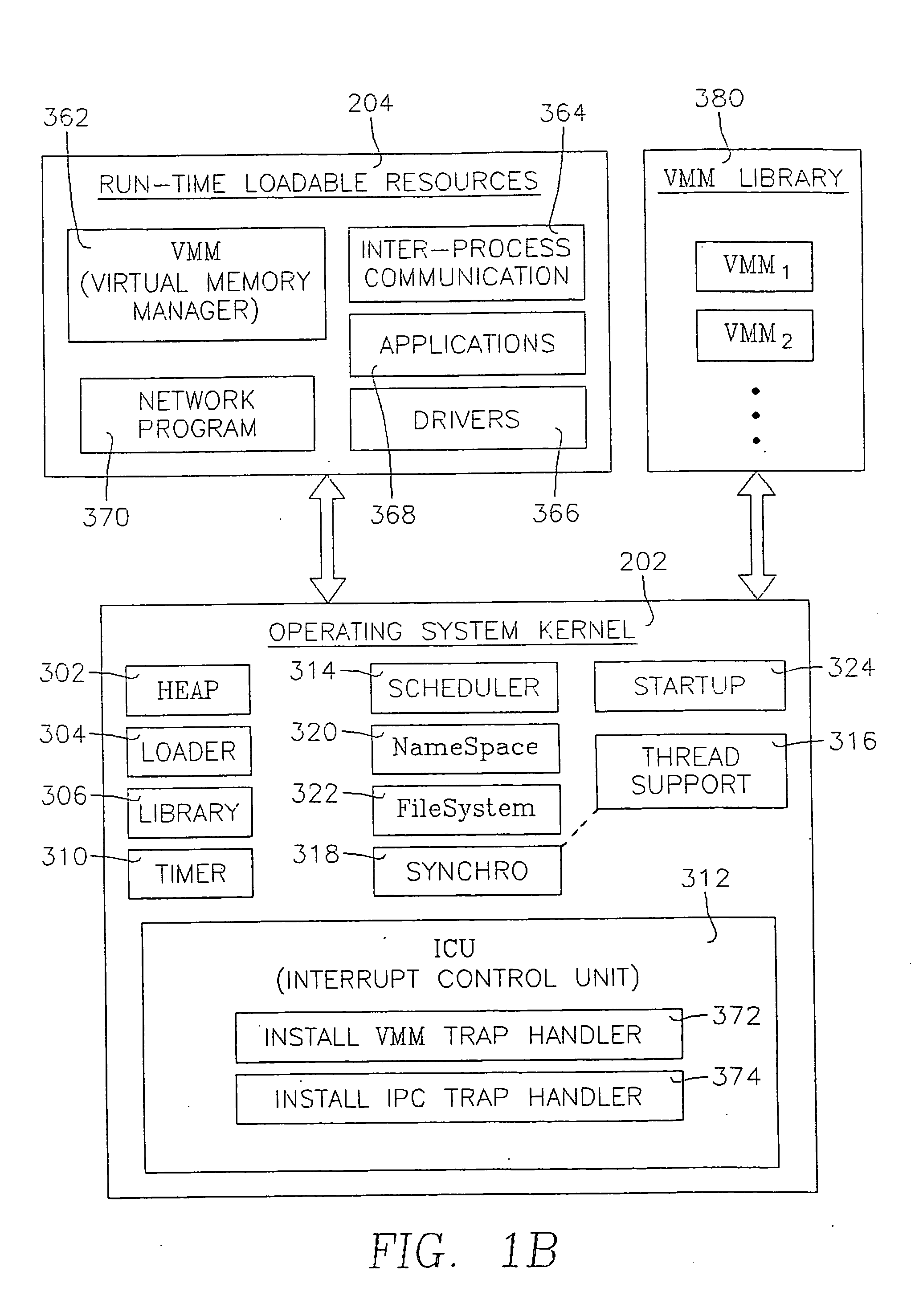
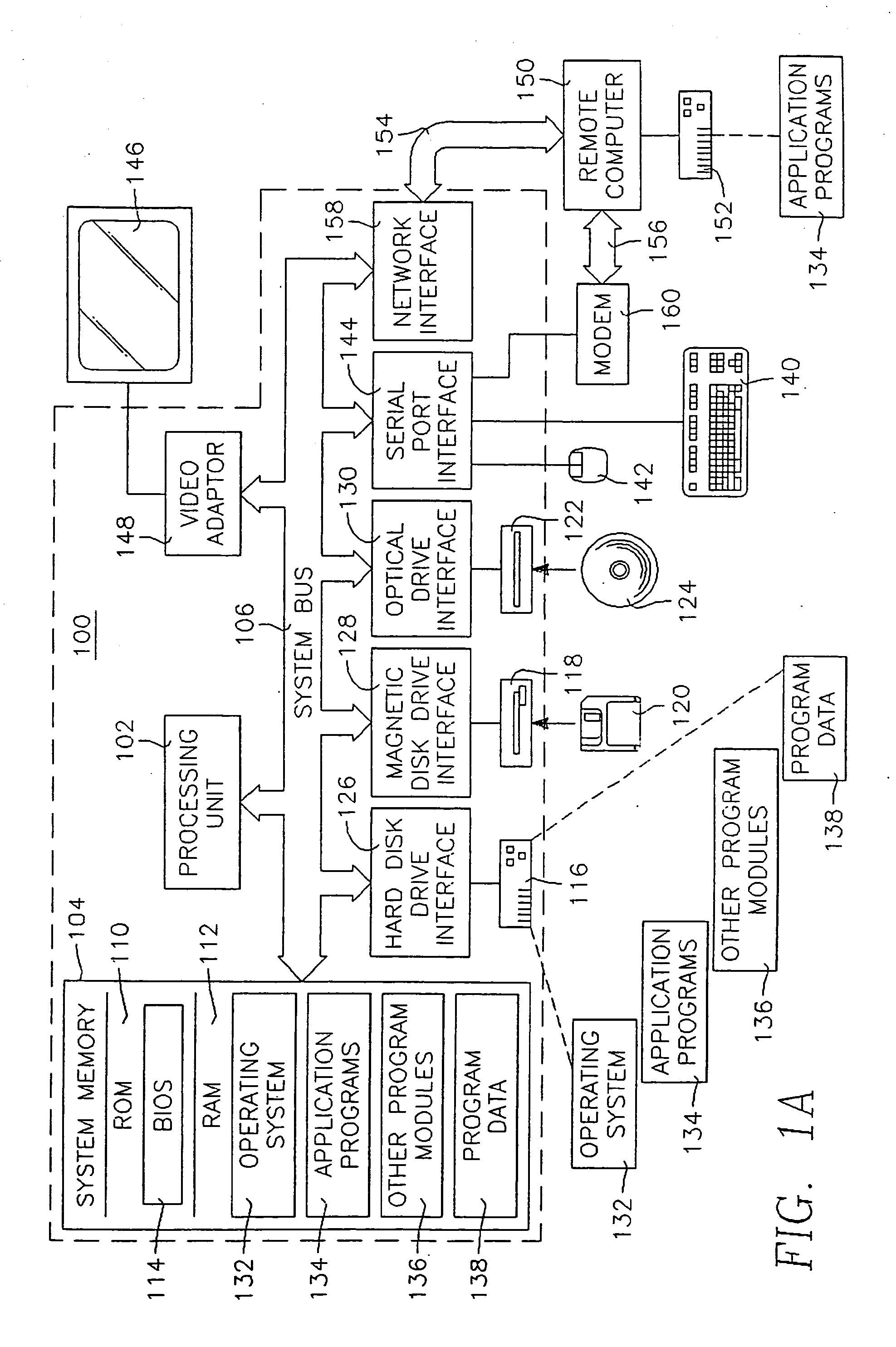
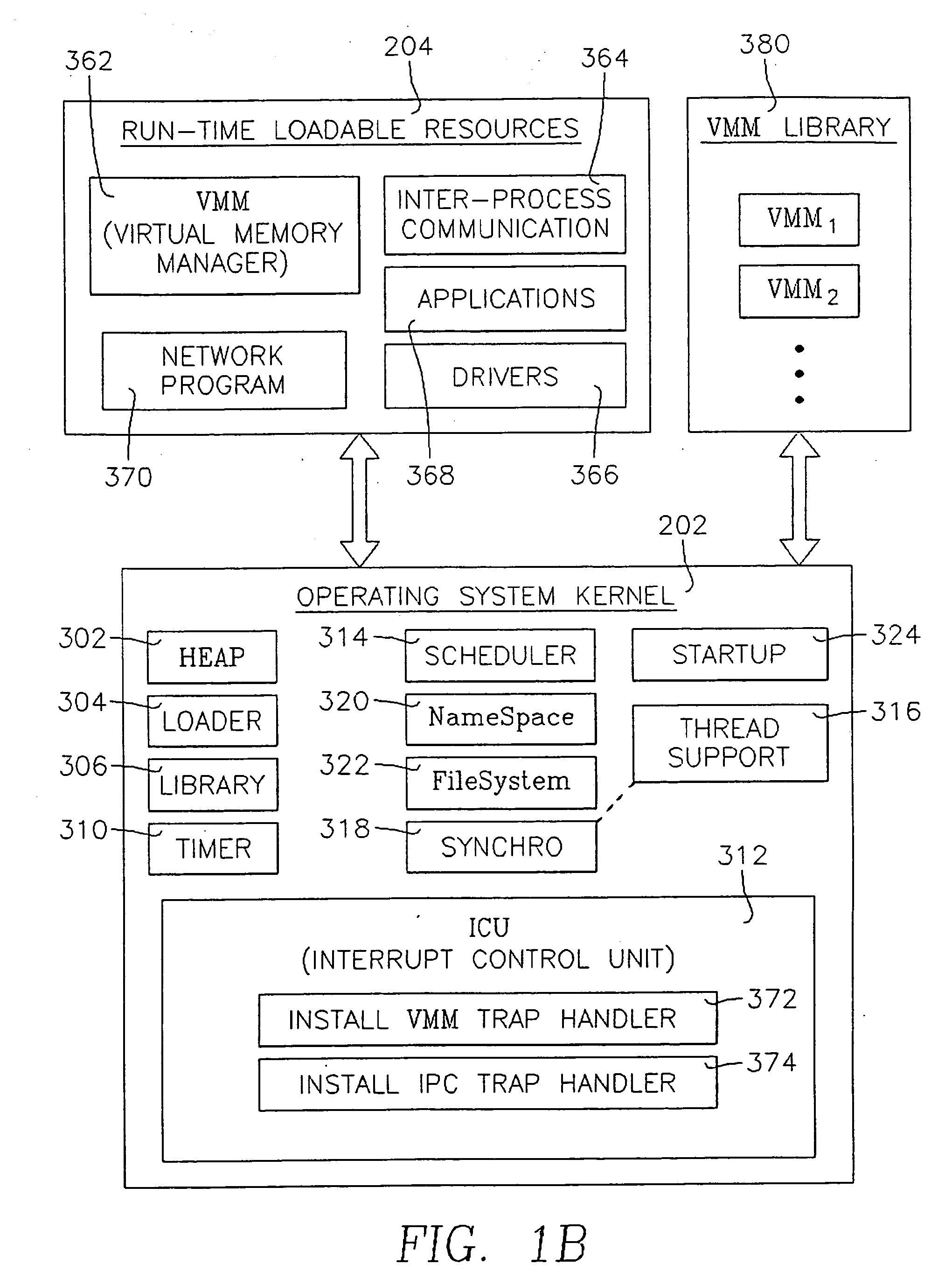
The present invention is directed to a loadable virtual memory manager, and generally to a computer operating system capable of supporting application programs running in a computer having a working memory, the computer operating system including a kernel resident in the working memory at run time, and a loadable virtual memory manager resident at link time outside of the working memory and dynamically loadable into the working memory at run time upon demand of one of the application programs. The kernel includes a loader for loading the virtual memory manager into the working memory in response to a demand from one of the application programs. The computer is able to access a storage memory separate from the working memory, the loadable virtual memory manager residing at link time in the storage memory. The loader loads the virtual memory manager from the storage memory to the working memory. The loadable virtual memory manager is removable from the working memory upon lack of demand therefor by the application programs.
Owner:MICROSOFT TECH LICENSING LLC
Extensible method for obtaining an historical record of data backup activity (and errors) and converting same into a canonical format
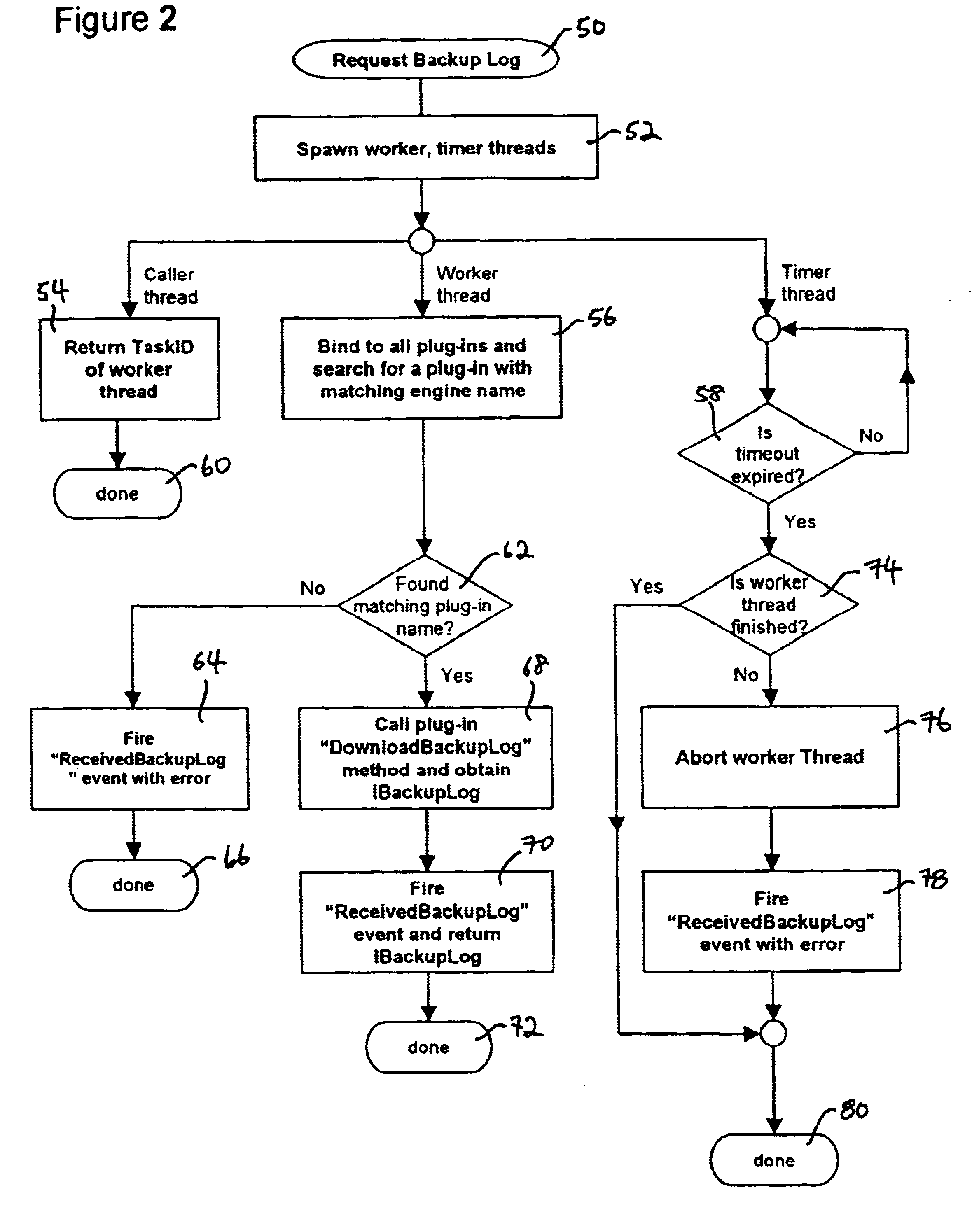
InactiveUS6708188B1Digital data information retrievalData processing applicationsExtensibilityLate binding
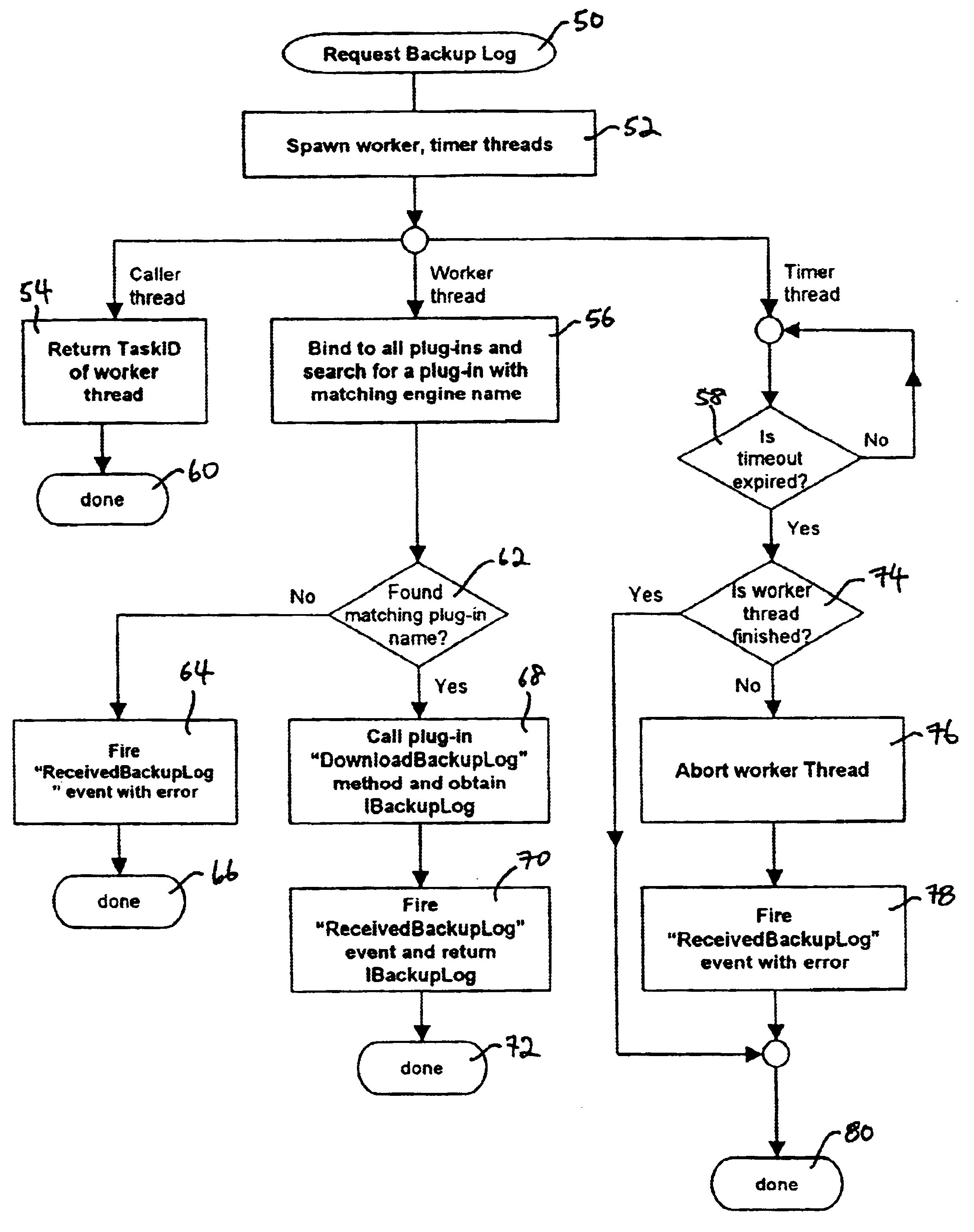
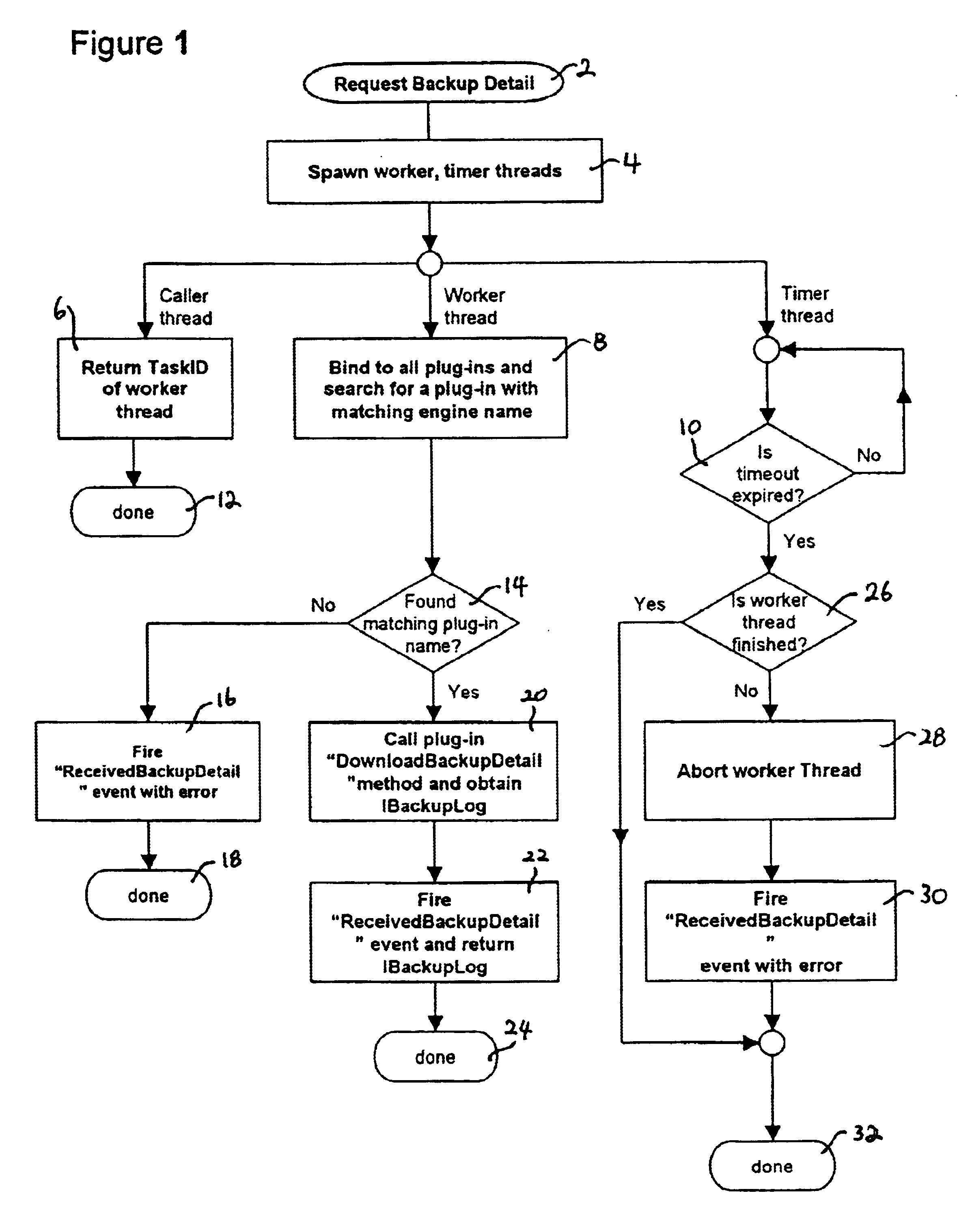
An extensible method and system for obtaining an historical record of data backup activity (and errors) from a plurality of data backup software devices, and converting the same into a canonical format, is disclosed. In the first aspect, a method comprises the steps of providing a late-binding mechanism that provides the invention with extensibility so that it can be made to inter-operate with an arbitrary variety of backup software devices. In the second aspect, an interface for requesting and returning a canonical backup activity log is disclosed. In the third aspect, an interface for requesting and returning a canonical backup error log is disclosed. In the fourth aspect, the use of a canonical format enables the data to be cross-referenced, consolidated and compared.
Owner:BOCADA LLC
Content management system using sources of experience data and modules for quantification and visualization
ActiveUS8645383B2Expand accessData processing applicationsDigital data processing detailsUser inputContent management
A semantic note taking system and method for collecting information, enriching the information, and binding the information to services is provided. User-created notes are enriched with labels, context traits, and relevant data to minimize friction in the note-taking process. In other words, the present invention is directed to collecting unscripted data, adding more meaning and use out of the data, and binding the data to services. Mutable and late-binding to services is also provided to allow private thoughts to be published to a myriad of different applications and services in a manner compatible with how thoughts are processed in the brain. User interfaces and semantic skins are also provided to derive meaning out of notes without requiring a great deal of user input.
Owner:APPLE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com