Patents
Literature
258 results about "Base calling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
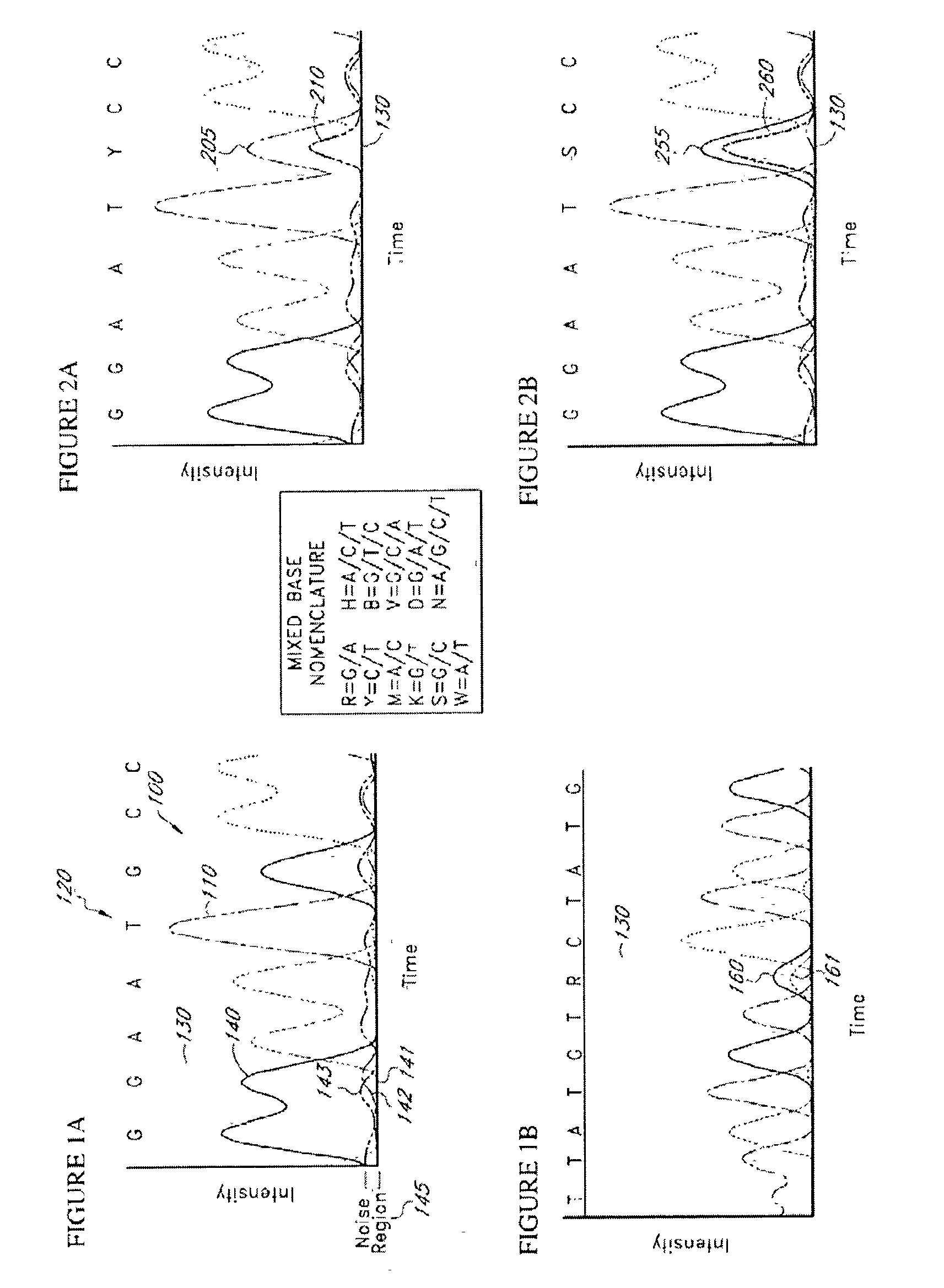
Base calling is the process of assigning nucleobases to chromatogram peaks. One computer program for accomplishing this job is Phred base-calling, which is a widely used basecalling software program by both academic and commercial DNA sequencing laboratories because of its high base calling accuracy.
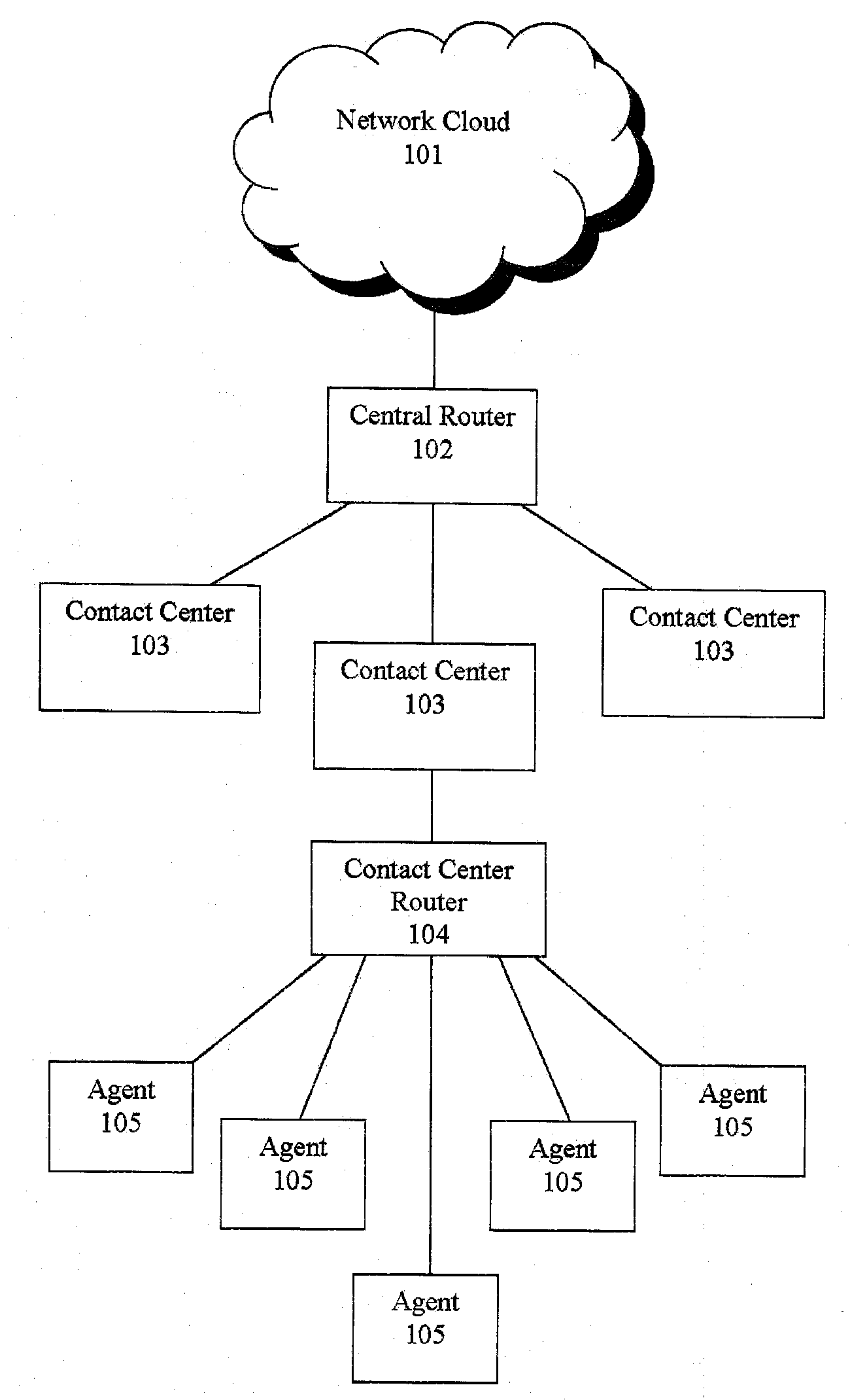
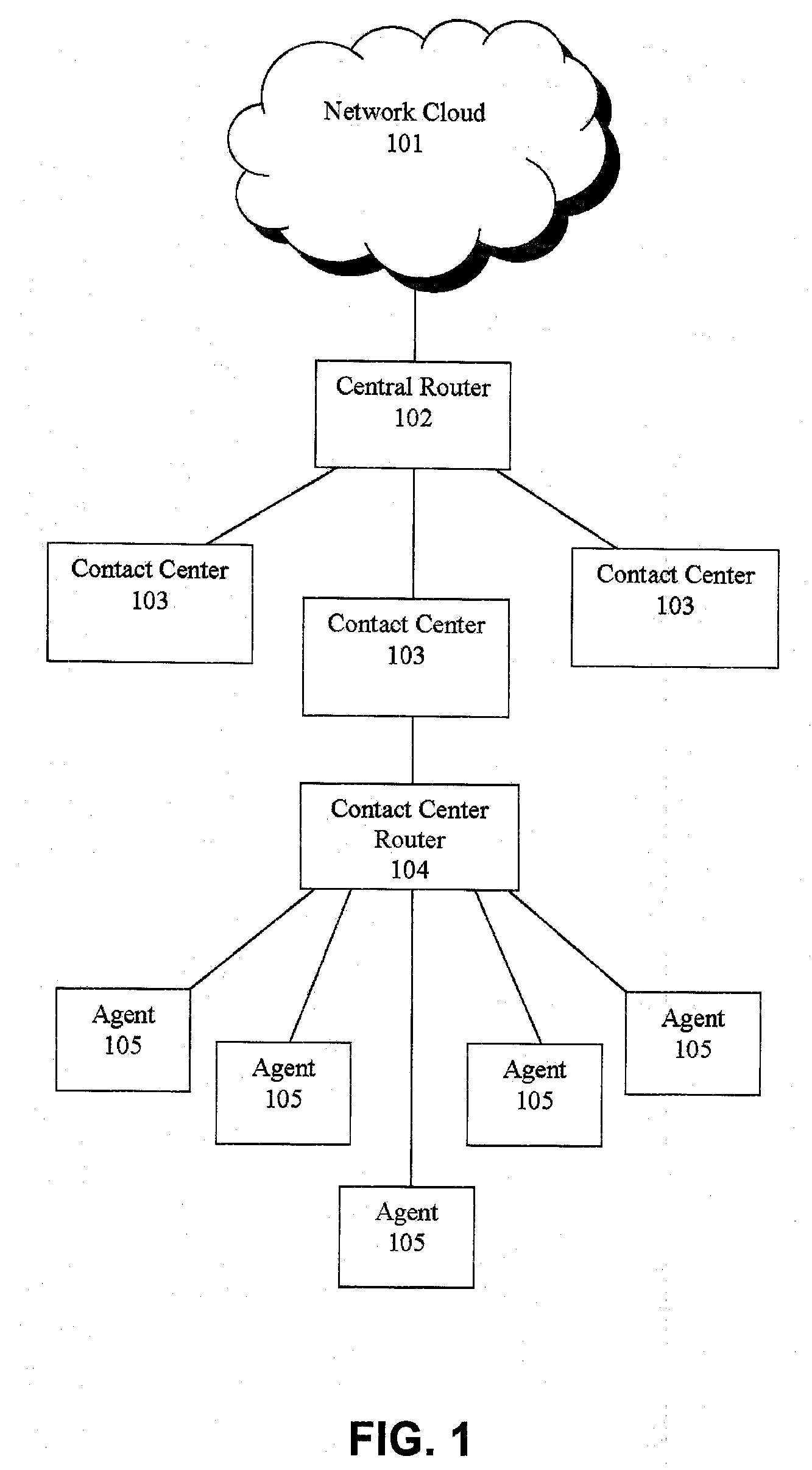
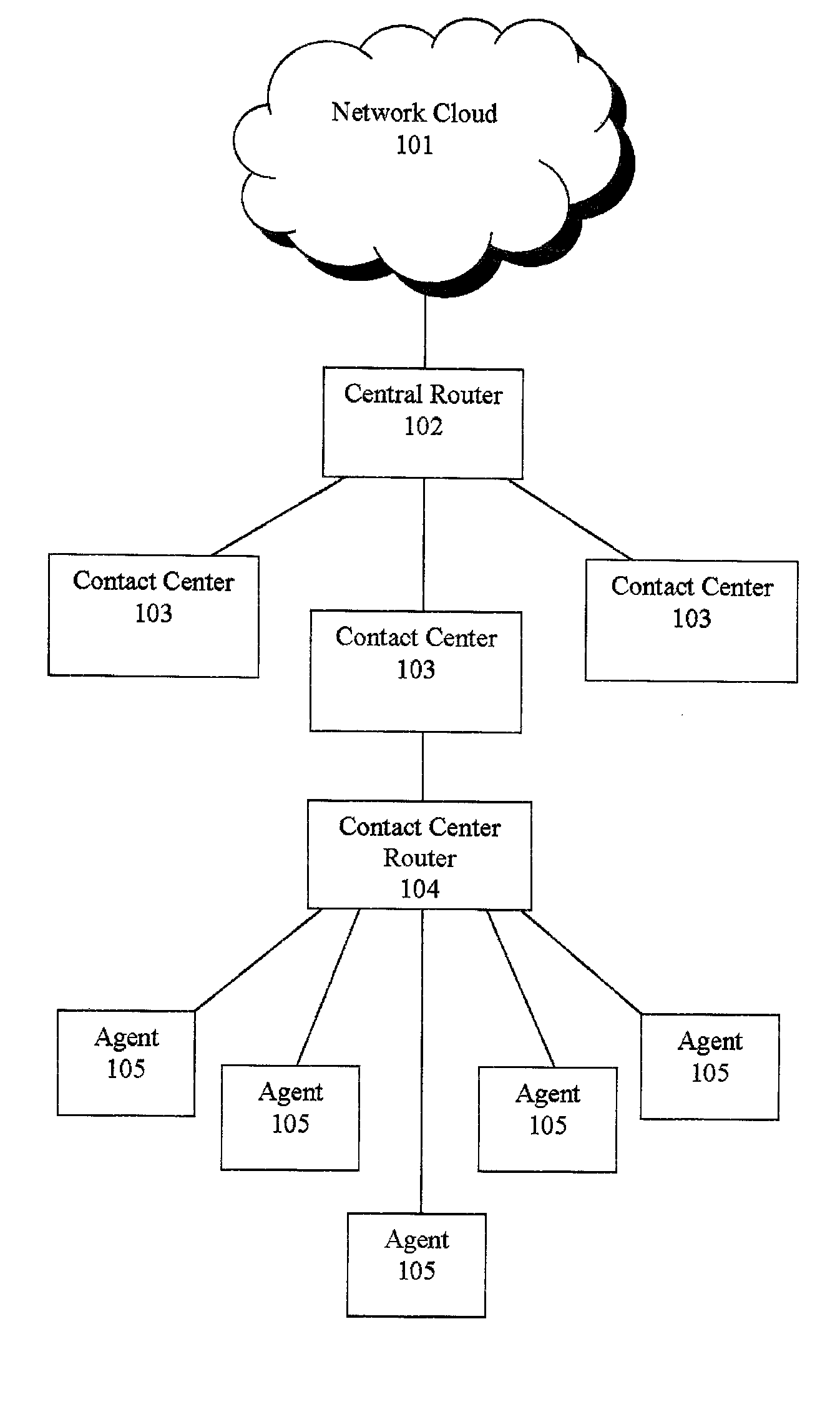
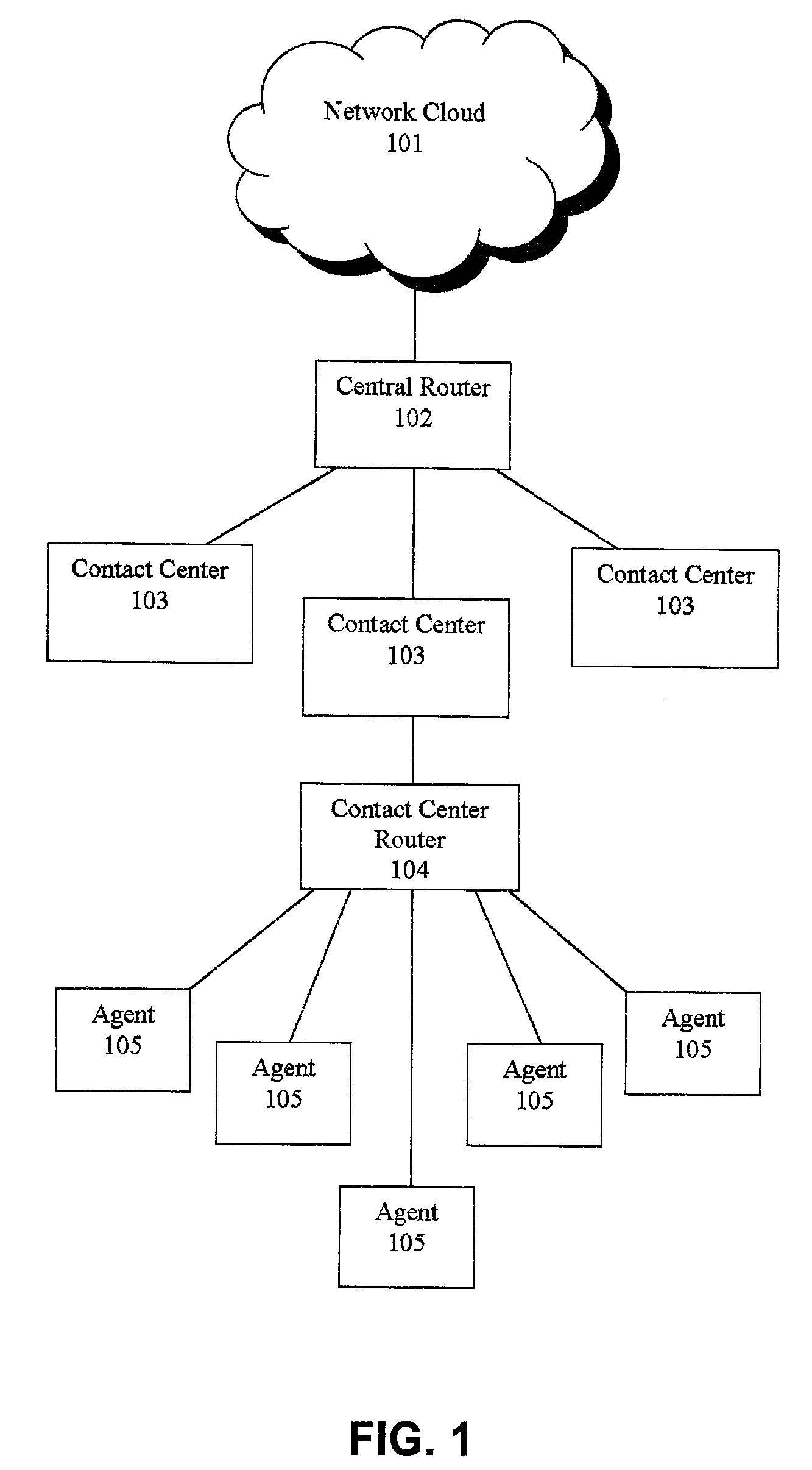
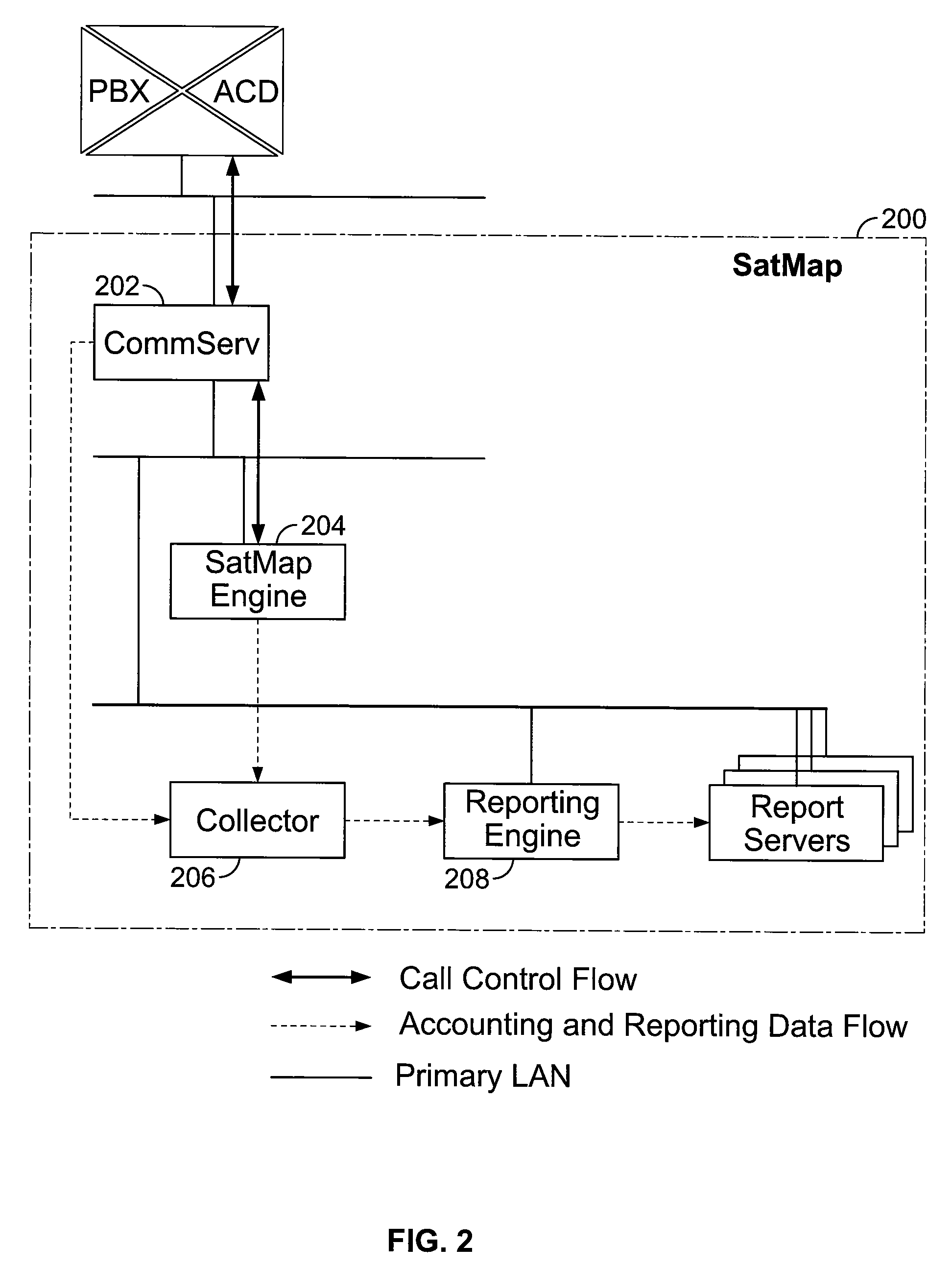
Shadow queue for callers in a performance/pattern matching based call routing system
ActiveUS20100054453A1Increase opportunitiesShorten the construction periodManual exchangesAutomatic exchangesPattern matchingBase calling
Methods and systems are disclosed for routing callers to agents in a contact center, along with an intelligent routing system. A method for routing callers includes routing a caller, if agents are available, to an agent based on a pattern matching algorithm (which may include performance based matching, pattern matching based on agent and caller data, computer models for predicting outcomes of agent-caller pairs, and so on). Further, if no agents are available for the incoming caller, the method includes holding the caller in a shadow queue, e.g., a set of callers. When an agent becomes available the method includes scanning all of the callers in the shadow queue and matching the agent to the best matching caller within shadow queue.
Owner:AFINITI LTD +1
Method and system for conducting customer needs, staff development, and persona-based customer routing analysis
InactiveUS20050187802A1Maximize probabilityMaximize effectivenessFinanceSpecial data processing applicationsThird partyBase calling
Computer-implemented methods and systems for conducting customer needs, staff development, or persona-based call routing analyses in which a recommendation engine receives baseline information regarding a current status and one or more objectives of a subject and generates assumed information about the subject based on a statistical evaluation of current status and objectives of a plurality of third parties having pre-determined characteristics in common with the subject. The recommendation engine determines a gap between the current status and objectives of the subject and generates and prioritizes a recommendation for one or more proposals for the subject based on the gap. Thereafter, the recommendation engine formulates one or more follow-up questions for the subject.
Owner:CITIBANK
Shadow queue for callers in a performance/pattern matching based call routing system
ActiveUS8644490B2Increase opportunitiesShorten the construction periodManual exchangesAutomatic exchangesPattern matchingBase calling
Methods and systems are disclosed for routing callers to agents in a contact center, along with an intelligent routing system. A method for routing callers includes routing a caller, if agents are available, to an agent based on a pattern matching algorithm (which may include performance based matching, pattern matching based on agent and caller data, computer models for predicting outcomes of agent-caller pairs, and so on). Further, if no agents are available for the incoming caller, the method includes holding the caller in a shadow queue, e.g., a set of callers. When an agent becomes available the method includes scanning all of the callers in the shadow queue and matching the agent to the best matching caller within shadow queue.
Owner:AFINITI LTD +1
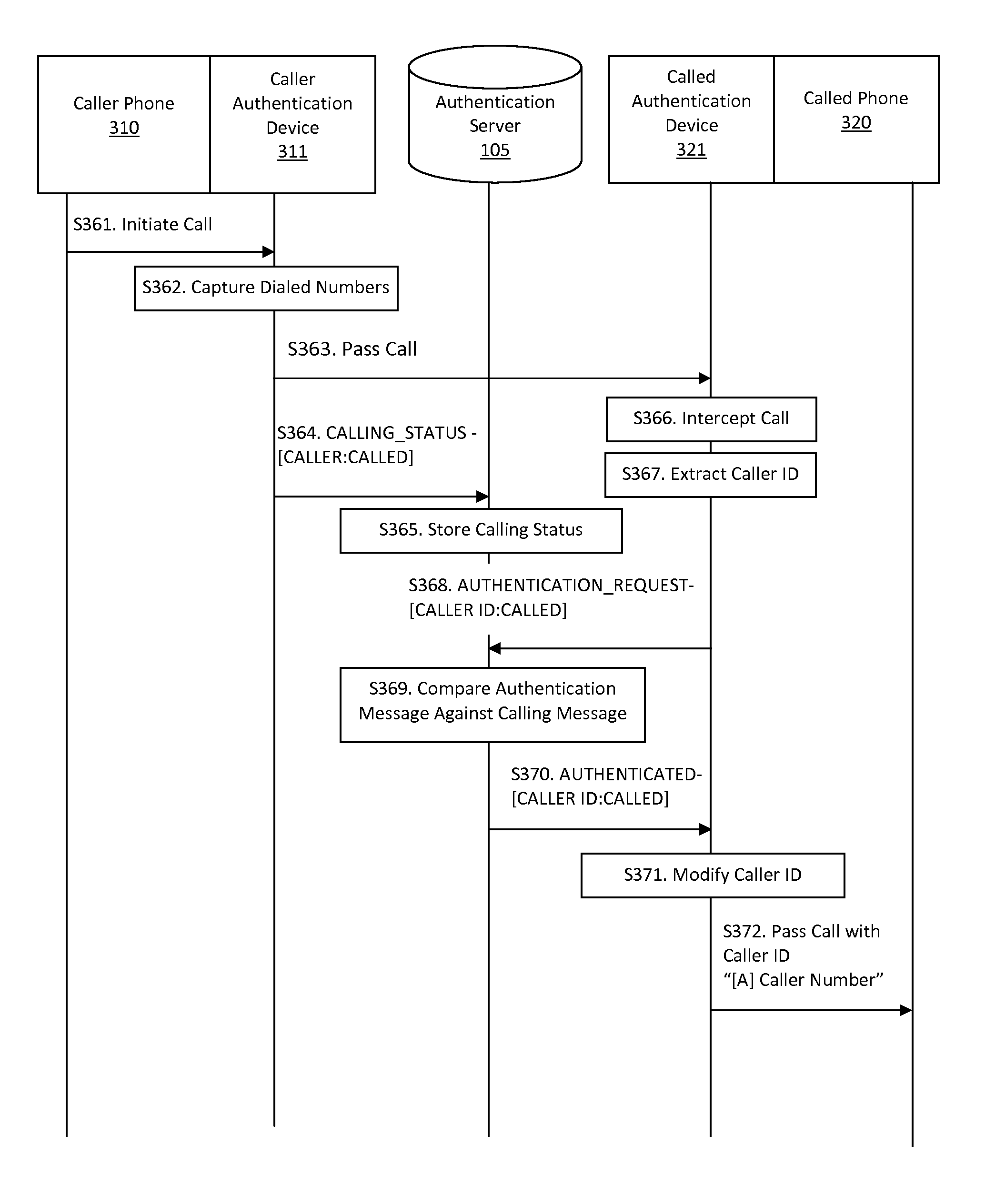
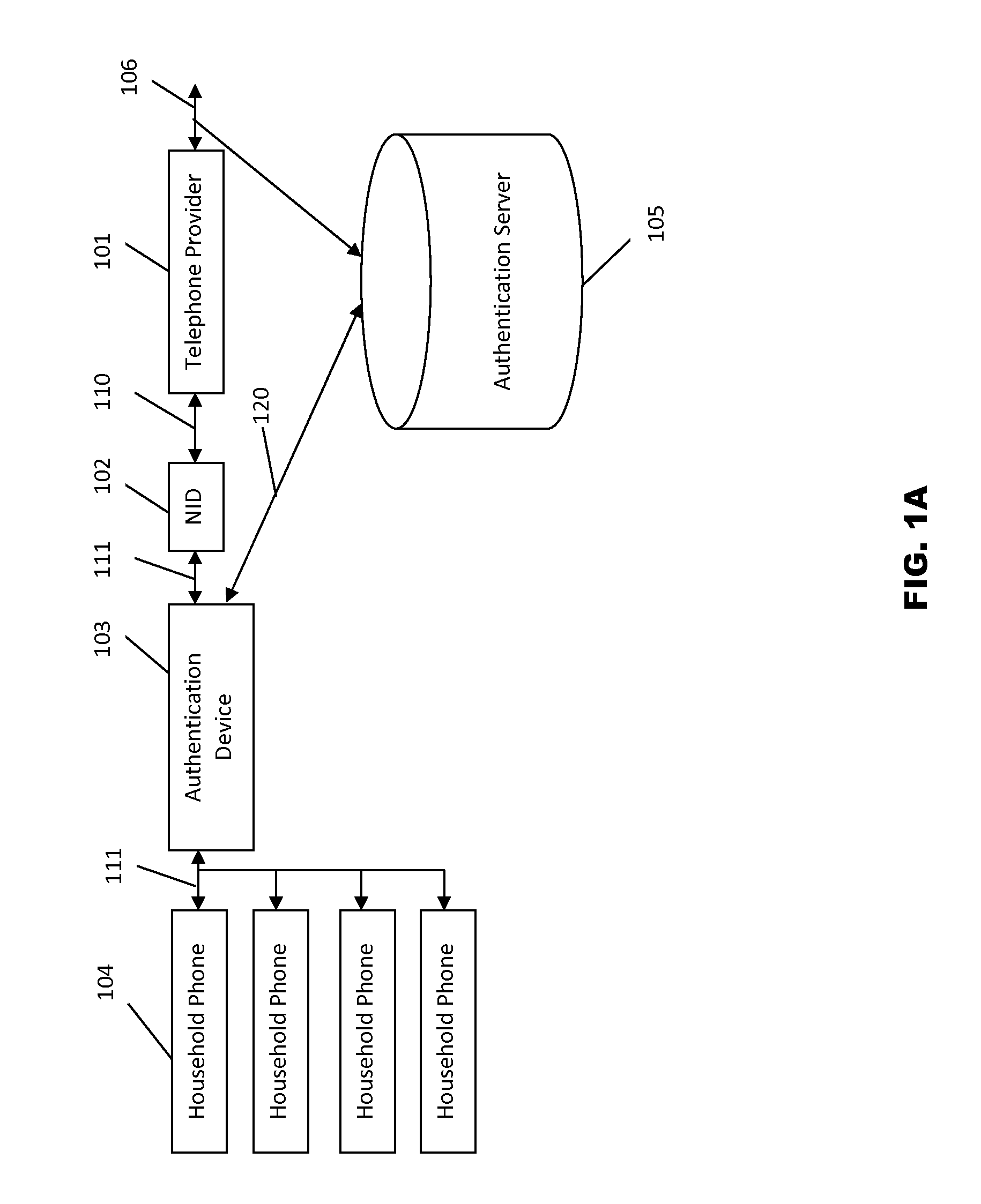
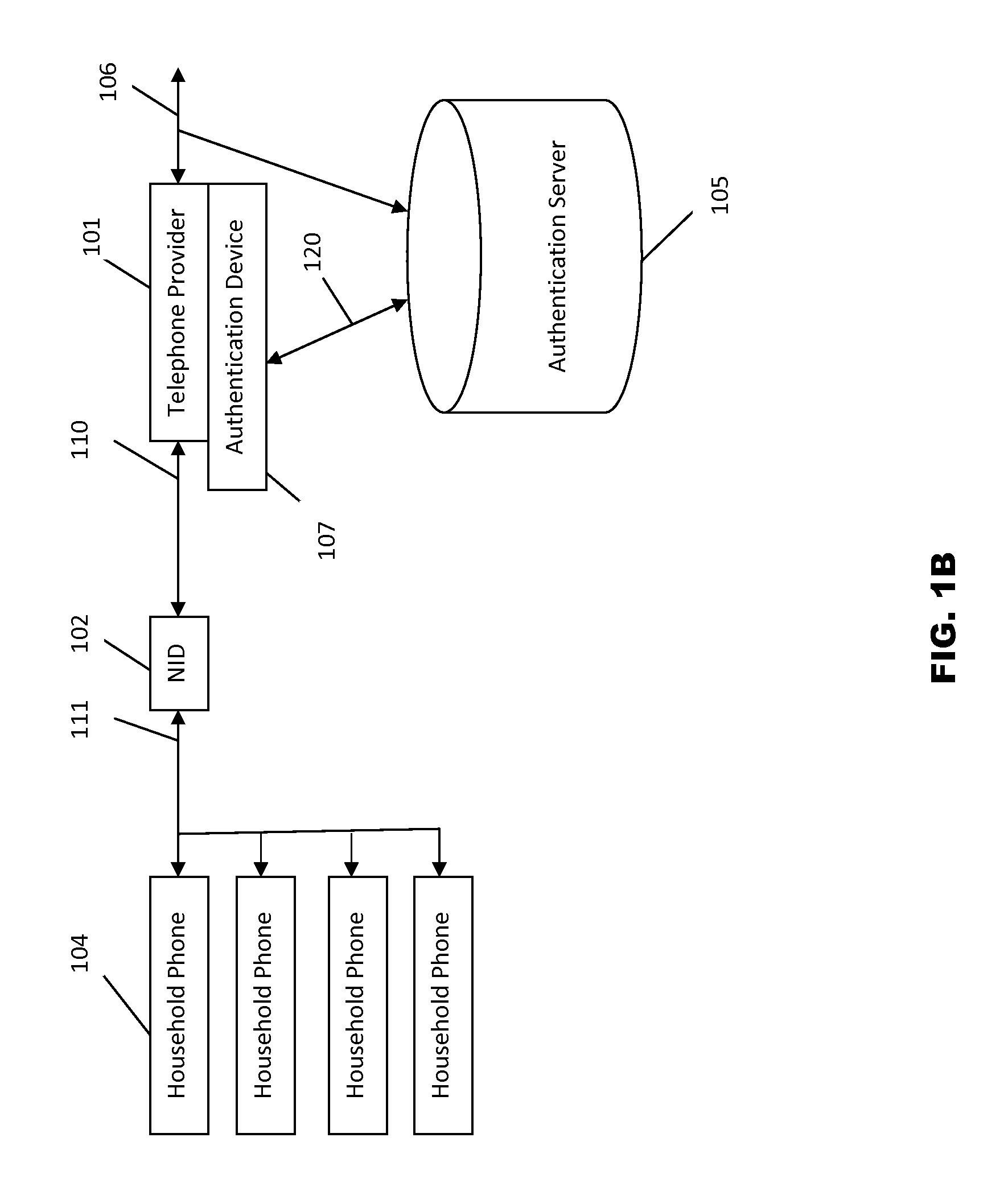
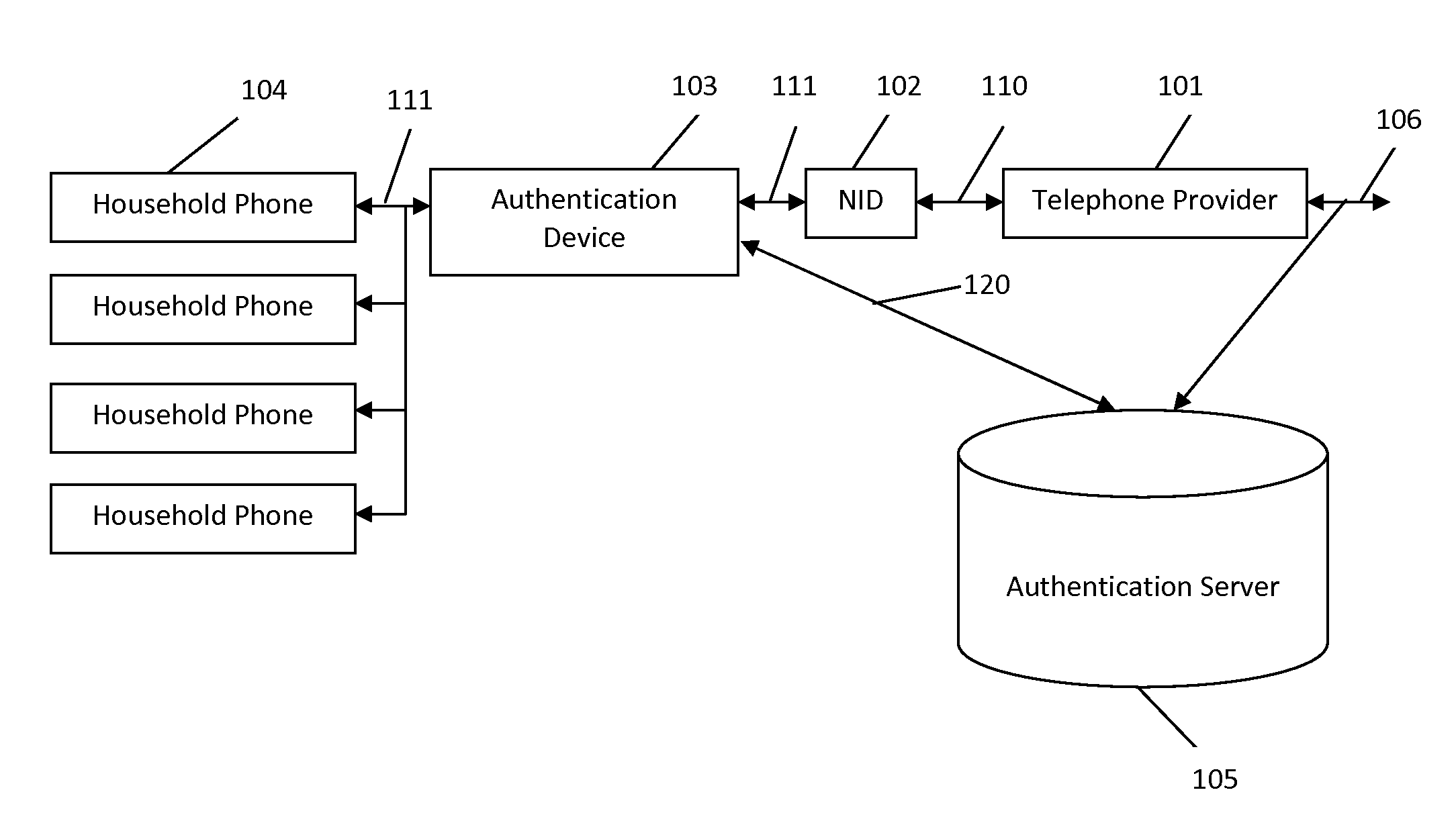
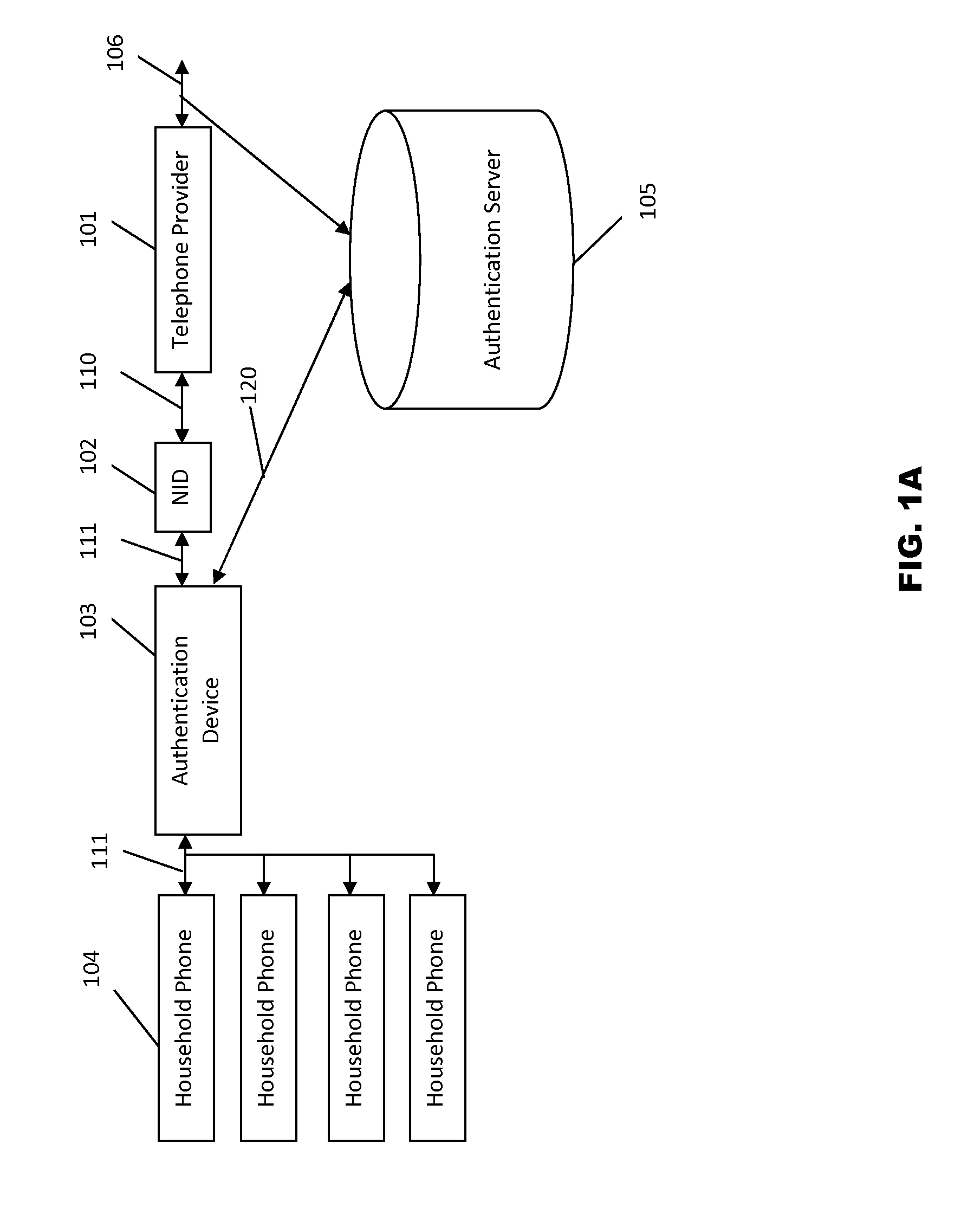
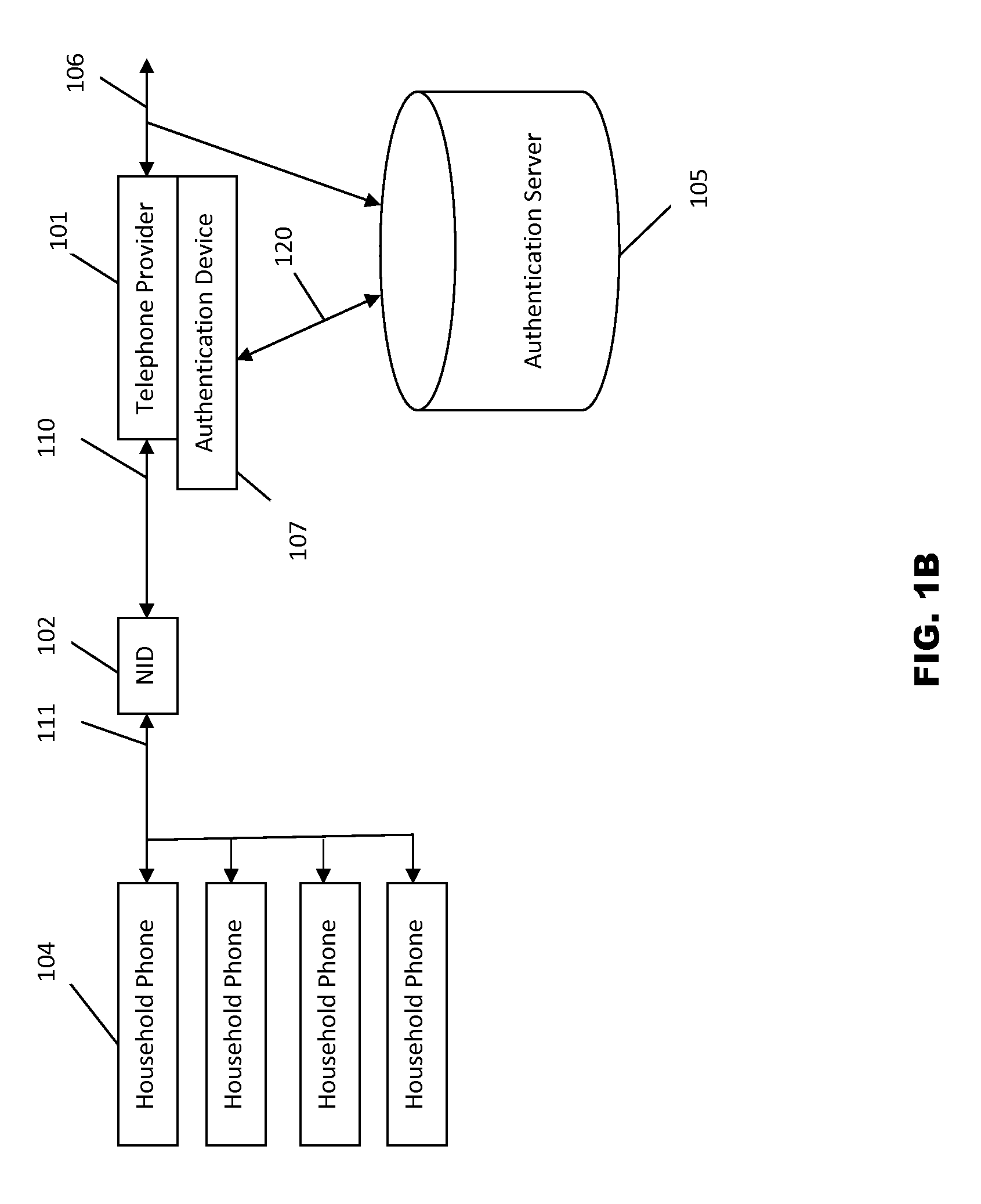
Systems and methods for caller ID authentication, spoof detection and list based call handling
ActiveUS9060057B1Special service for subscribersCalled number recording/indicationBase callingCommunication source
Systems and methods for caller id authentication, spoof detection and list based call handling are disclosed. The caller ID authentication is performed by an authentication device connected to the calling party telephone transmitting the source and destination telephone numbers of the call to an authentication server. The called party authentication device extracts the caller ID of the incoming call and transmits the caller ID of the caller and the telephone number of the called party to the authentication server. The authentication server analyzes the transmitted information from both devices and replies with the authentication status of the caller ID to the called party authentication device. Other embodiments are disclosed where the authentication server is not available and caller ID authentication is performed in a peer-to-peer manner. In another embodiment, the concepts of active and passive certification passwords are used to maintain the integrity of the system. Other embodiments allow for authenticating blocked caller ID's, reveling blocked caller ID's, VoIP implementations, legitimate caller ID spoofing, and placing a blocked caller ID on private white or black lists. Another embodiment combines the described caller ID authentication system within a call handling system utilizing internal, global and private white and black lists. Applications of caller ID authentication methodology to other forms of communication source address authentication, such as email, SMS, and postal mail are envisioned.
Owner:DANIS SERDAR ARTUN
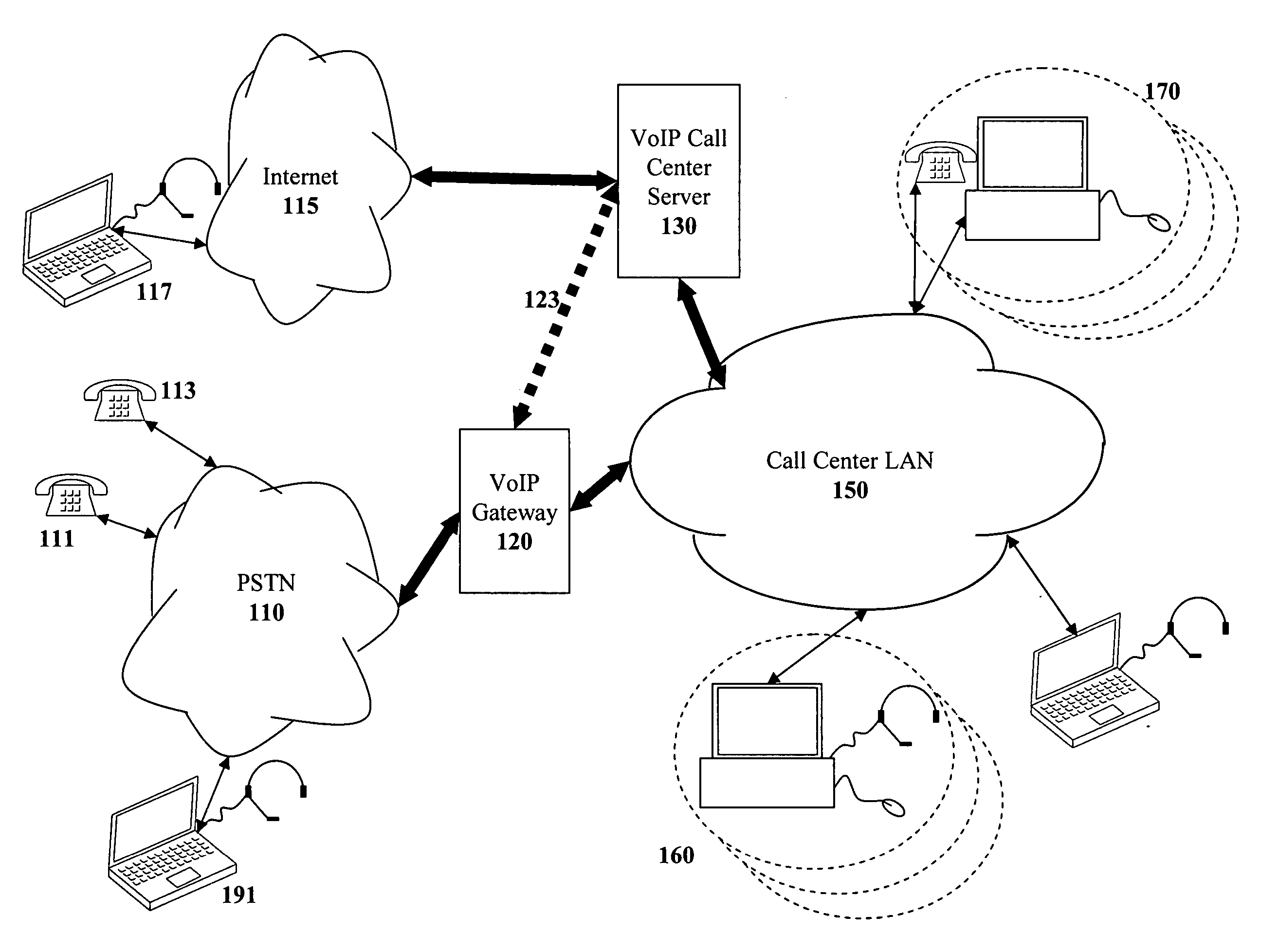
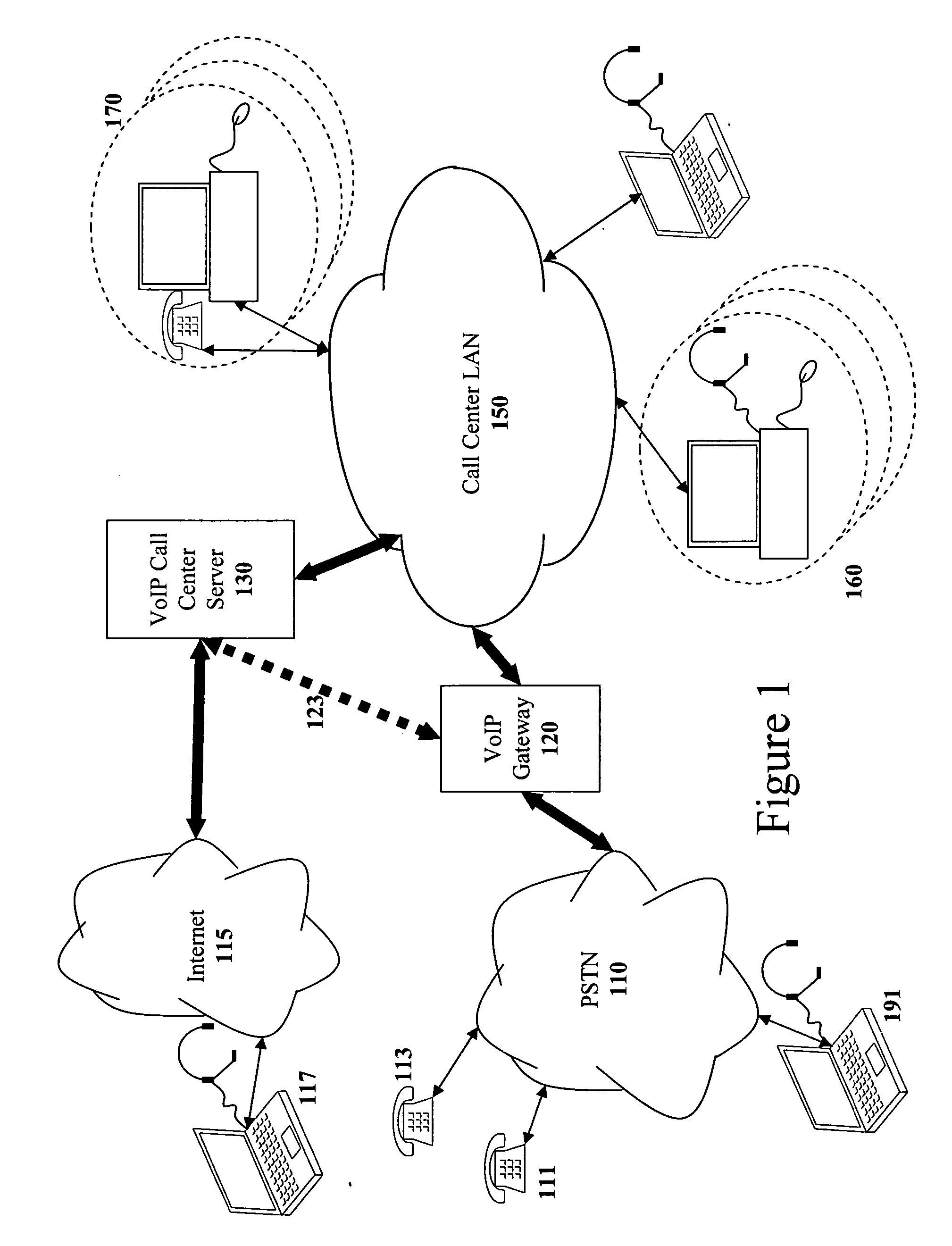
Voice over internet protocol implemented call center
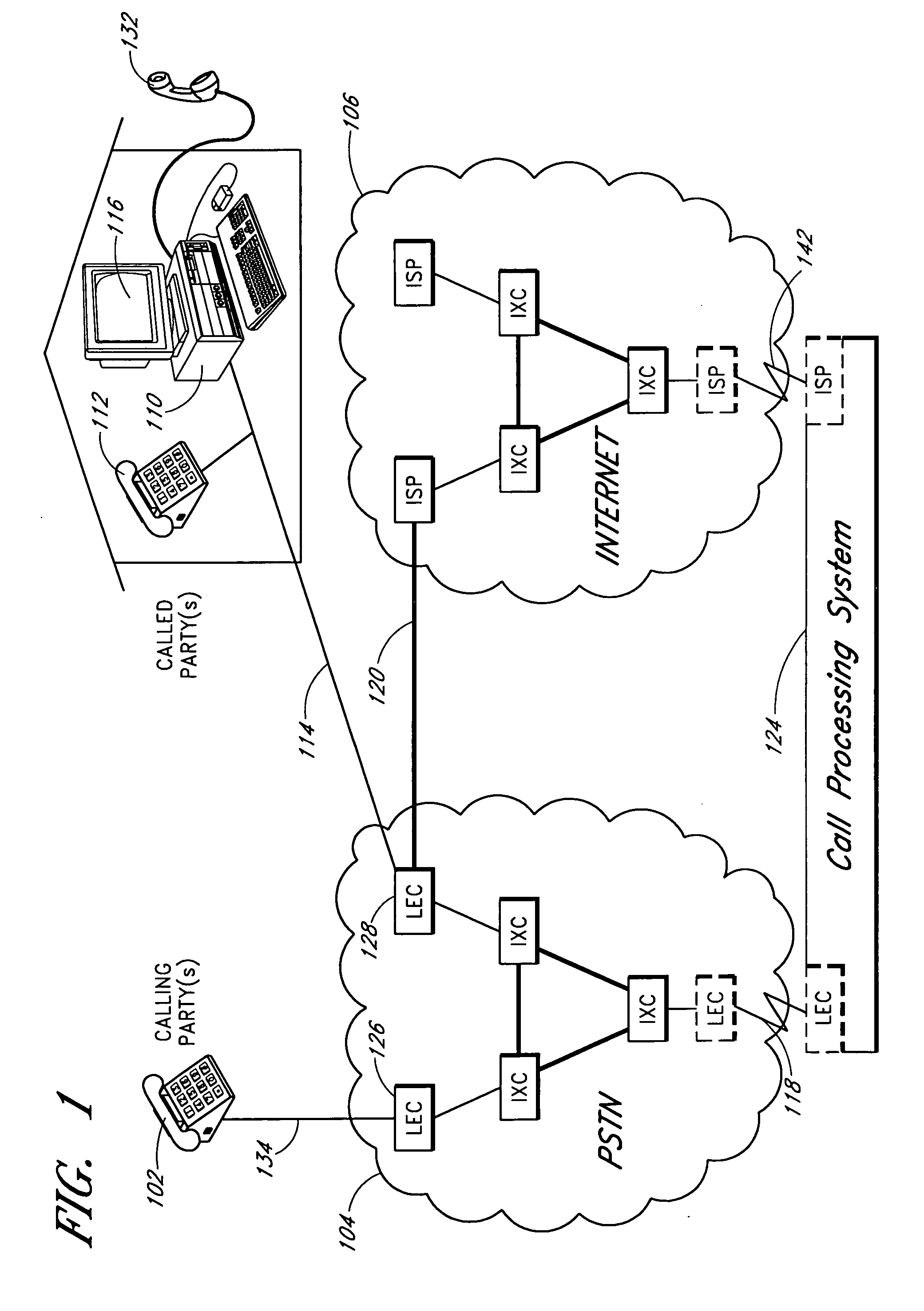
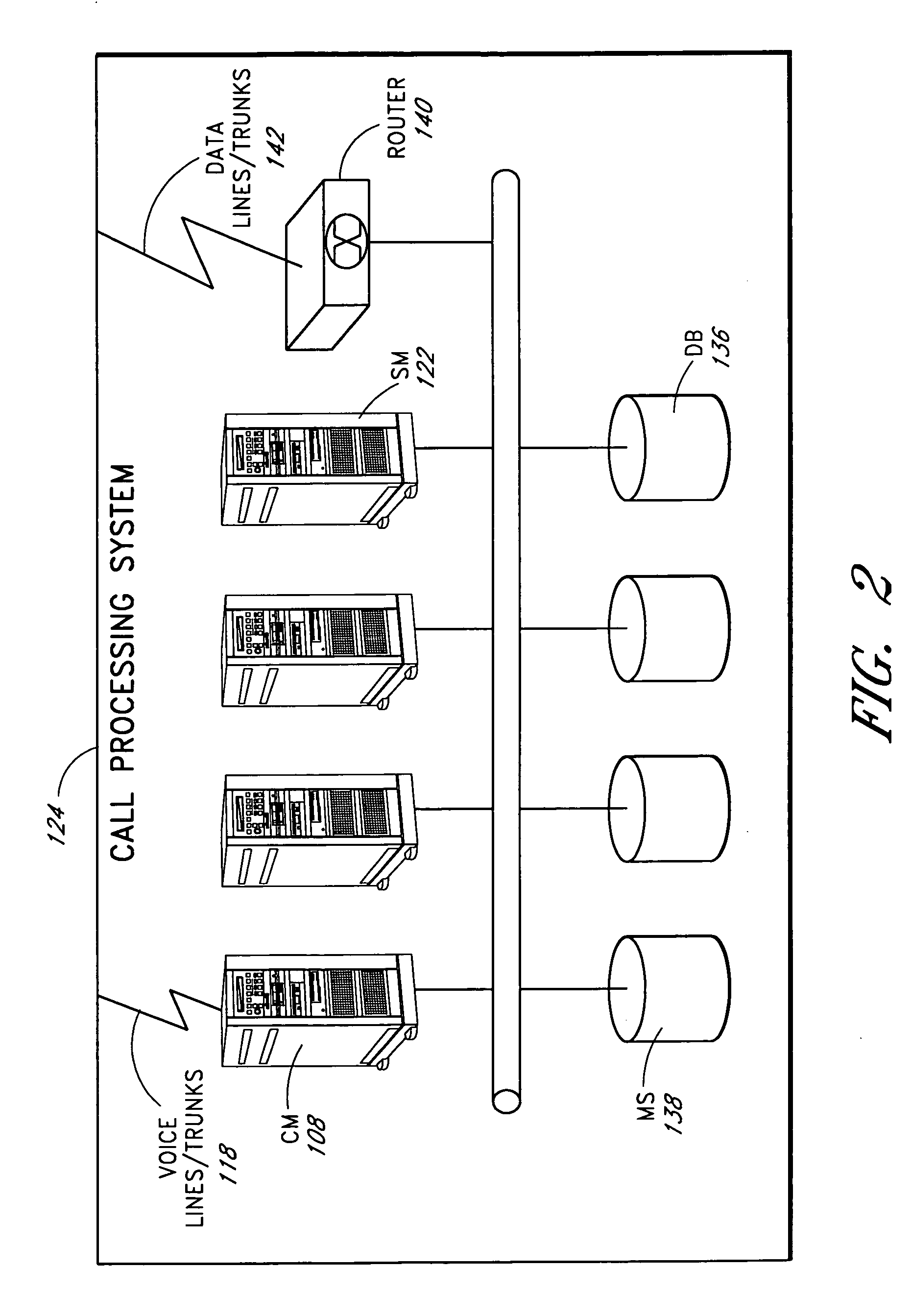
The present invention takes advantage of Voice over Internet Protocol (VoIP) technology by introducing VoIP-based call center telephony equipment that is software-based and runs on inexpensive off-the-shelf personal computer (PC) systems. With the VoIP-based call center system of the present invention, the traditional Public Switched Telephone Network (PSTN) is coupled to a Voice over Internet Protocol (VoIP) gateway in order to convert all incoming traditional telephone communication into VoIP based telephony telecommunication. This is performed using the well-known SIP telephony protocol set forth in RFC 3261. Once converted to the VoIP format, the incoming VoIP-based calls are directed to the VoIP based Call Center Server system. The Call Center Server system provides all the sophisticated call center features that were formerly only available in large call centers created with specialized expensive telephone equipment
Owner:KISHINSKY KONSTANTIN +4
Methods and systems for telephony processing, including location based call transfers
InactiveUS20060142012A1Reduce complexityGood knowledgeSpecial service for subscribersSubstation equipmentCall forwardingBase calling
The present invention provides flexible call processing. In one embodiment, an inbound call from a calling party is received at a call processing system. The inbound call is intended for a called party. A determination is made that a first condition has occurred and / or is occurring. The called party's location is determined via a location based service associated with the mobile device of the called party. Based at least in part on the called party's mobile device location, a phone number stored in computer readable memory is selected. The calling party is connected to a communication device associated with the selected phone number.
Owner:CALLWAVE COMM
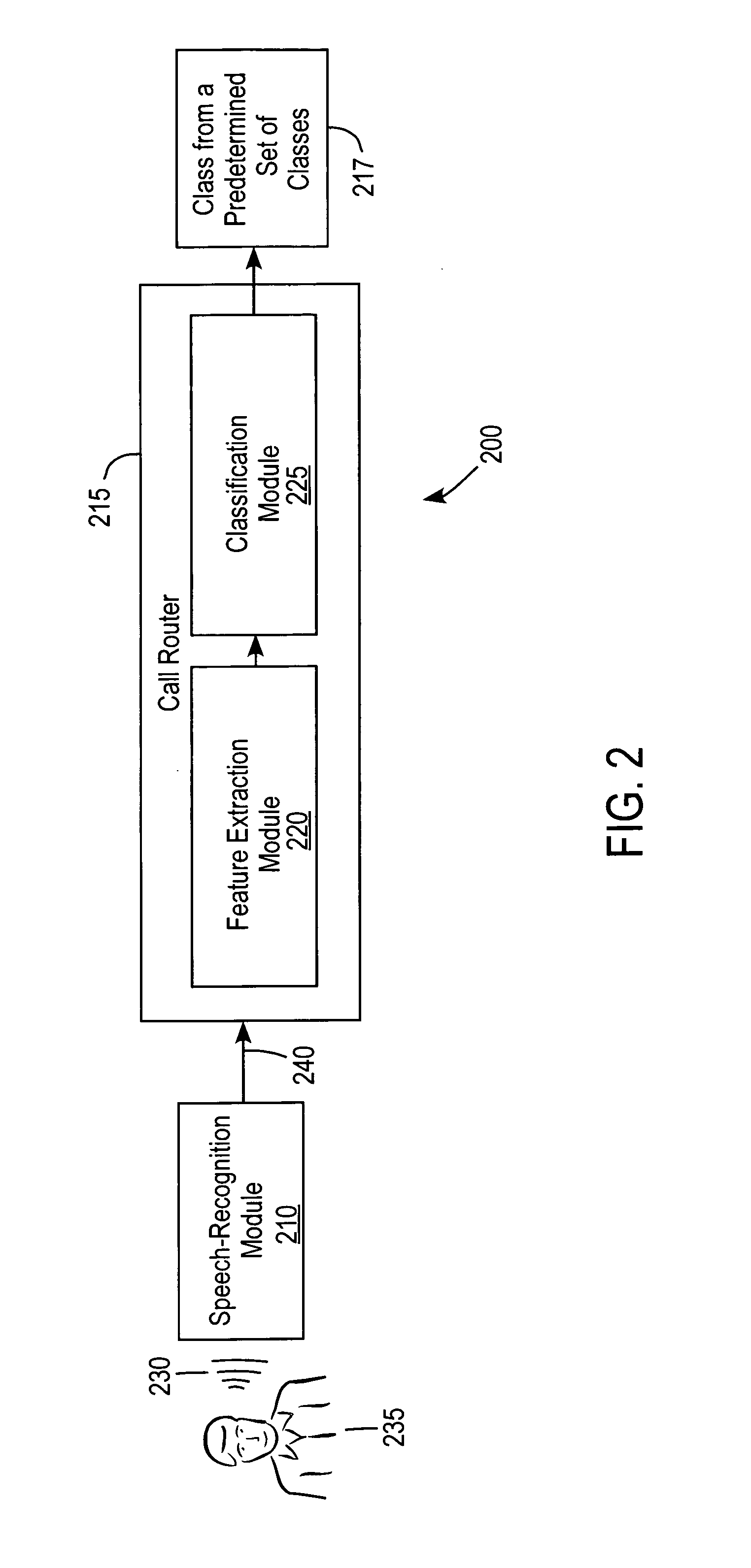
Method and apparatus for generating a speech-recognition-based call-routing system
ActiveUS7206389B1Special service for subscribersAutomatic call-answering/message-recording/conversation-recordingFeature vectorFeature extraction
A computerized method is provided for electronically directing a call to a class, such that an utterance spoken by a speaker and received by a call-routing system is classified by the call-routing system as being associated with the class, such that the call-routing system includes a speech-recognition module, a feature-extraction module, and a classification module. The method includes extracting features from recognized speech; weighting elements of a feature vector with respective speech-recognition scores, wherein each weighting element is associated with one of the features; ranking classes to which the features are associated; and electronically directing the call to a highest-ranking class.
Owner:NUANCE COMM INC
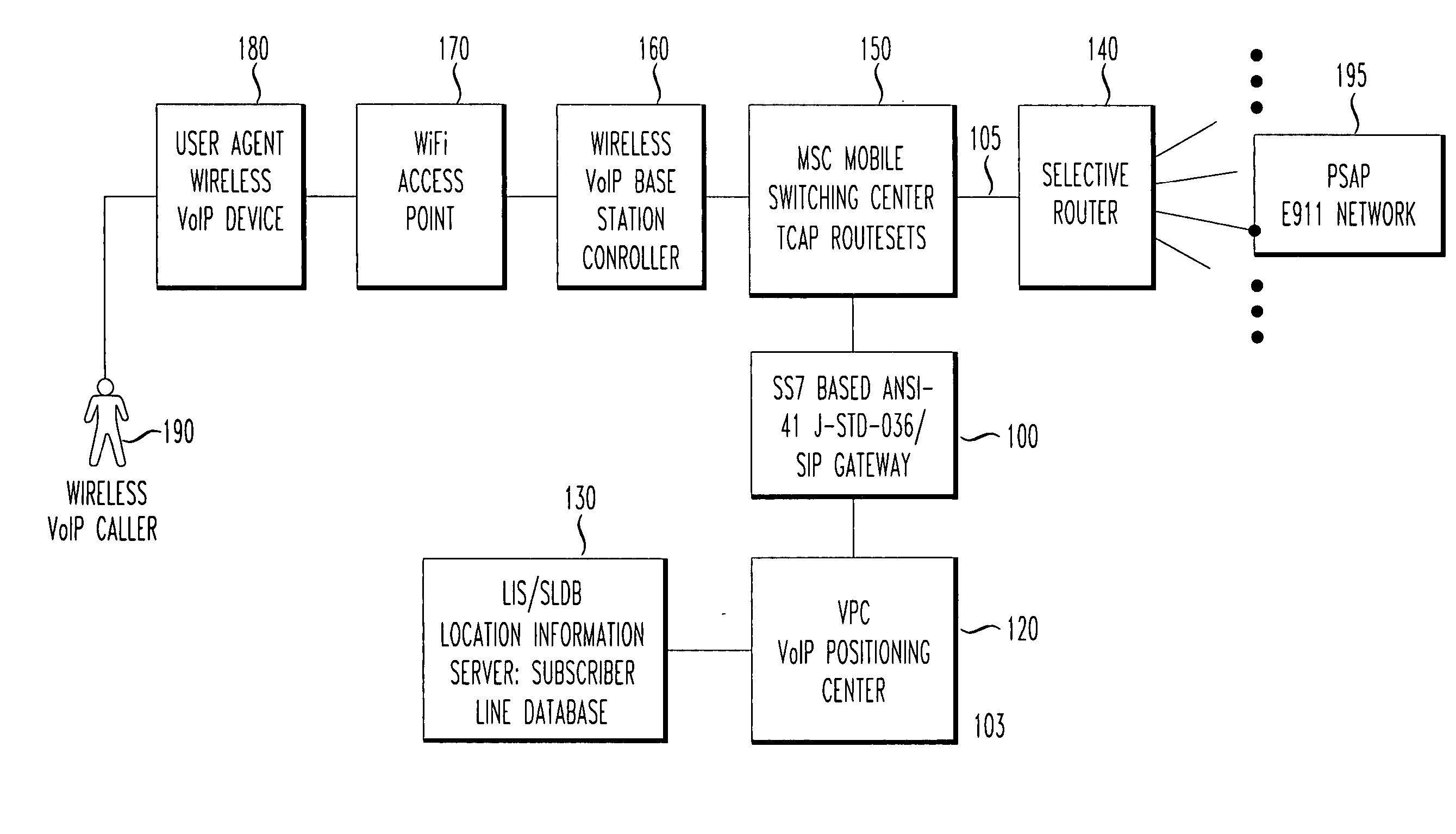
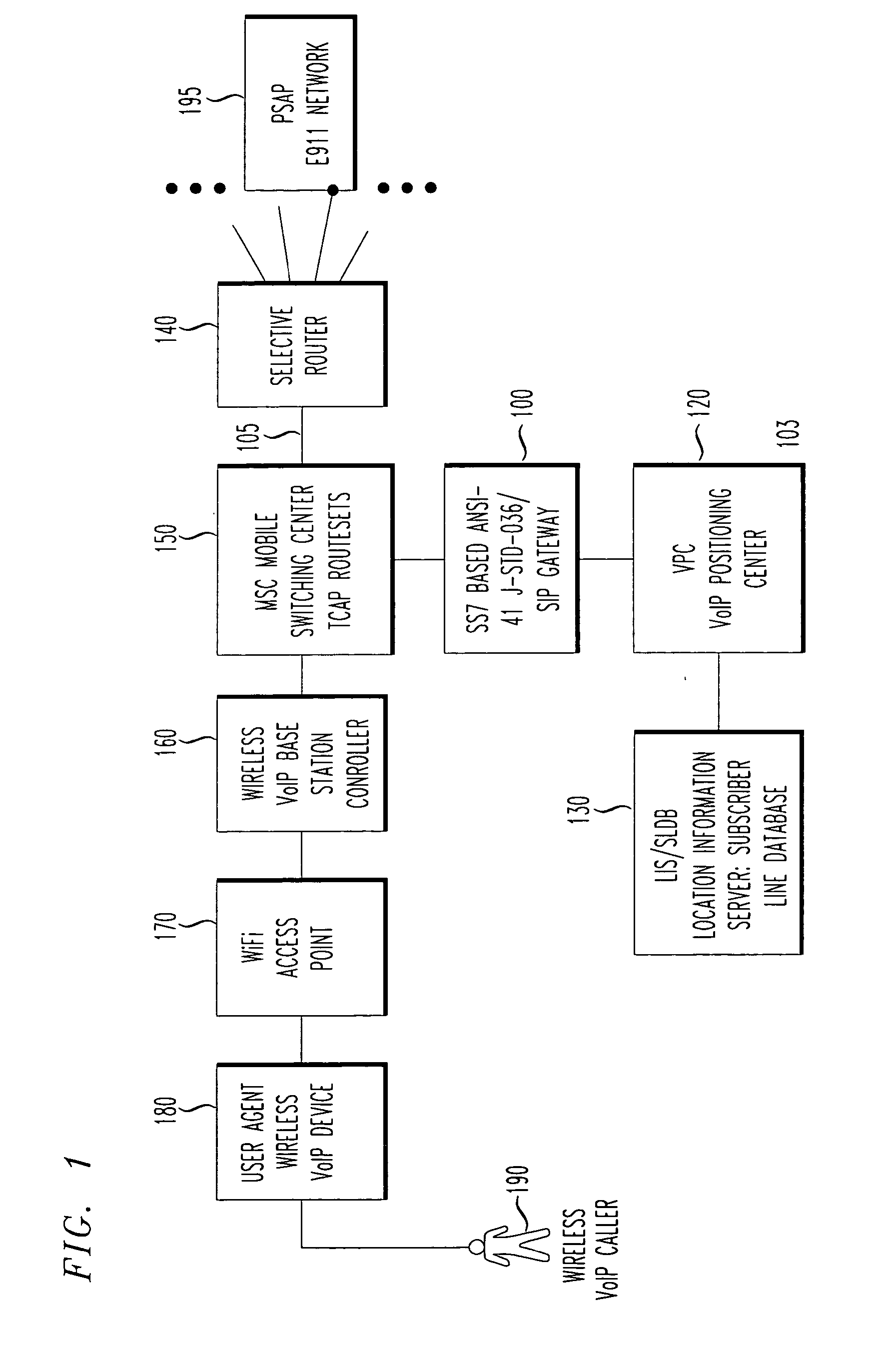
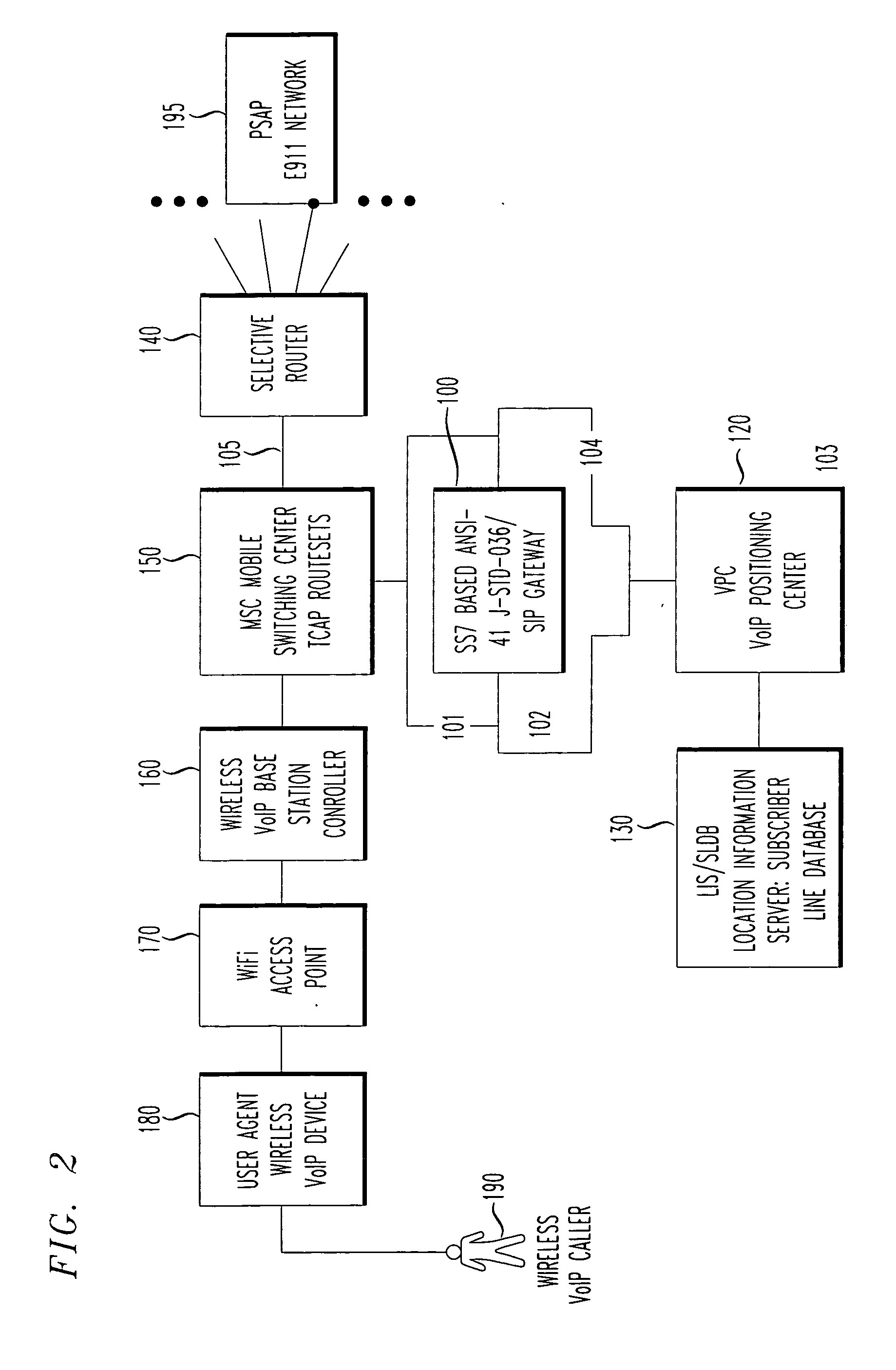
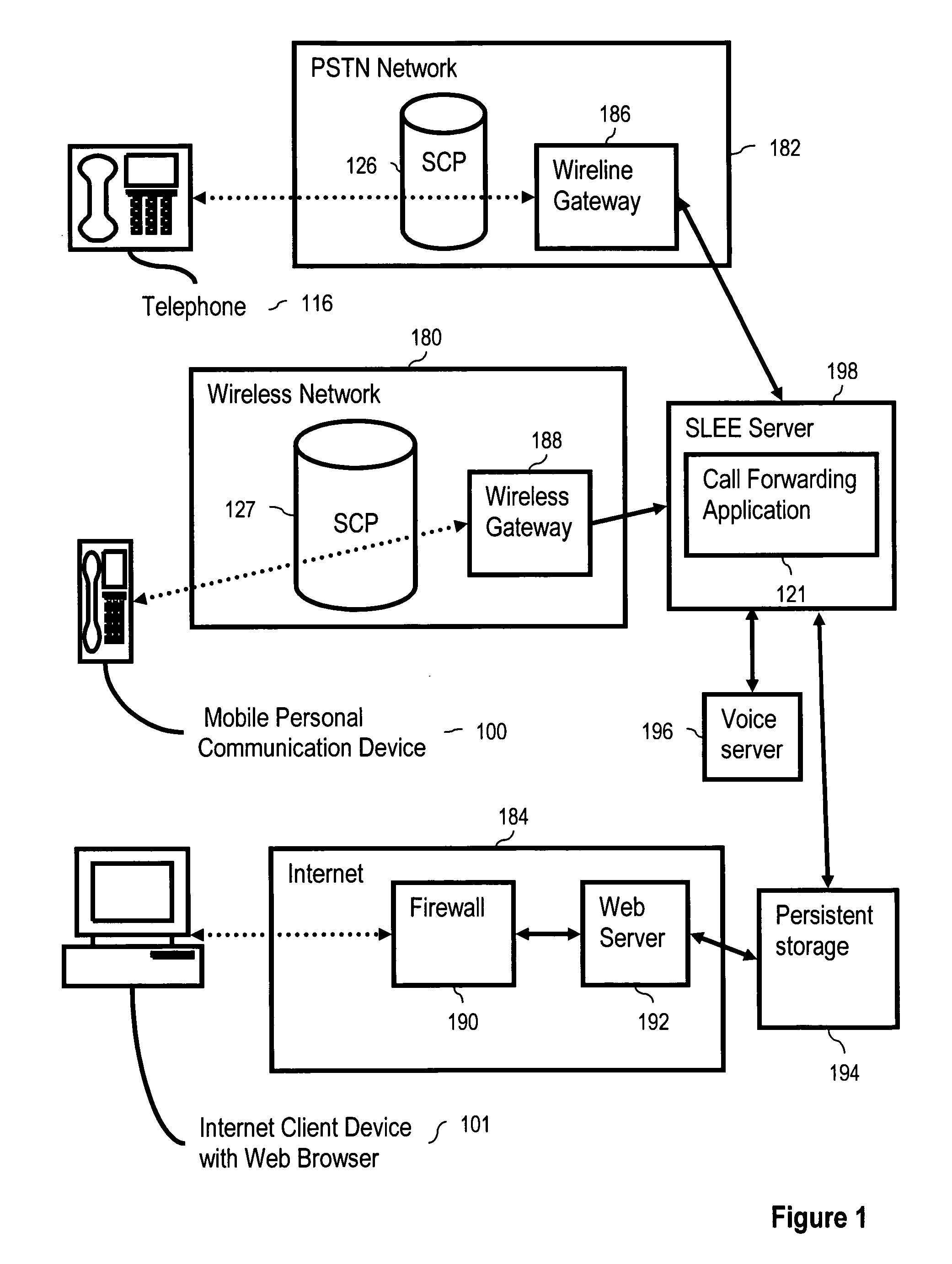
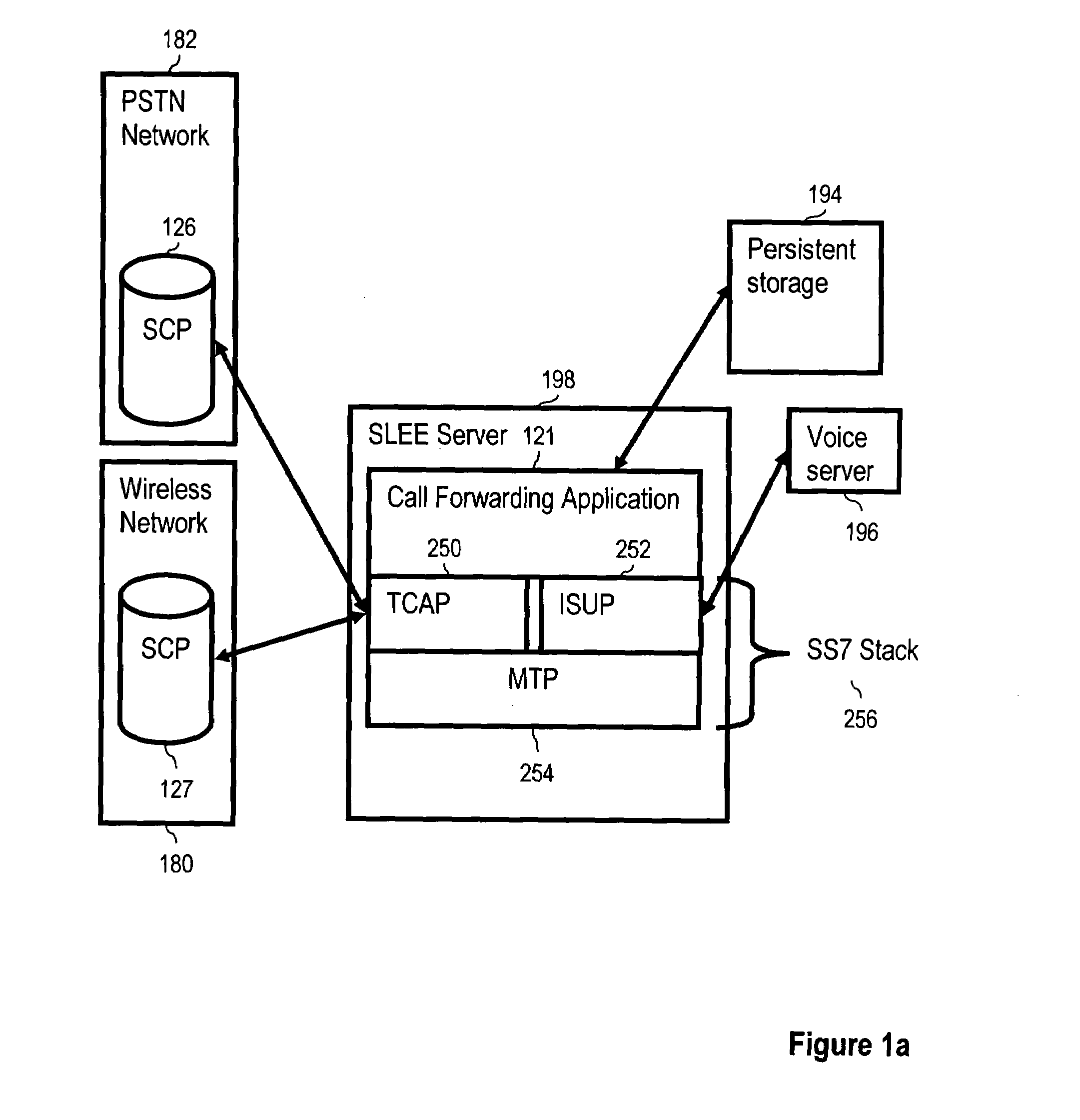
SS7 MAP/Lg+ to SIP based call signaling conversion gateway for wireless VoIP E911
InactiveUS20070263610A1Interconnection arrangementsRadio transmissionSession Initiation ProtocolDual mode
An SS7-based call protocol conversion gateway that translates between circuit-switched SS7 protocols and session initiation protocol (SIP) oriented protocol, allowing an E911 call initiated over a switched network to be routed by a VoIP network. The SS7-based call protocol conversion gateway provides a PSAP with MSAG quality (street address) information about a VoIP dual mode phone user without the need for a wireless carrier to invest in building out an entire VoIP core. Thus, wireless carriers may continue signaling the way they are today, i.e., using the J-STD-036 standard for CDMA and GSM in North America, yet see benefits of a VoIP network core, i.e., provision of MSAG quality location data to a PSAP.
Owner:TELECOMM SYST INC
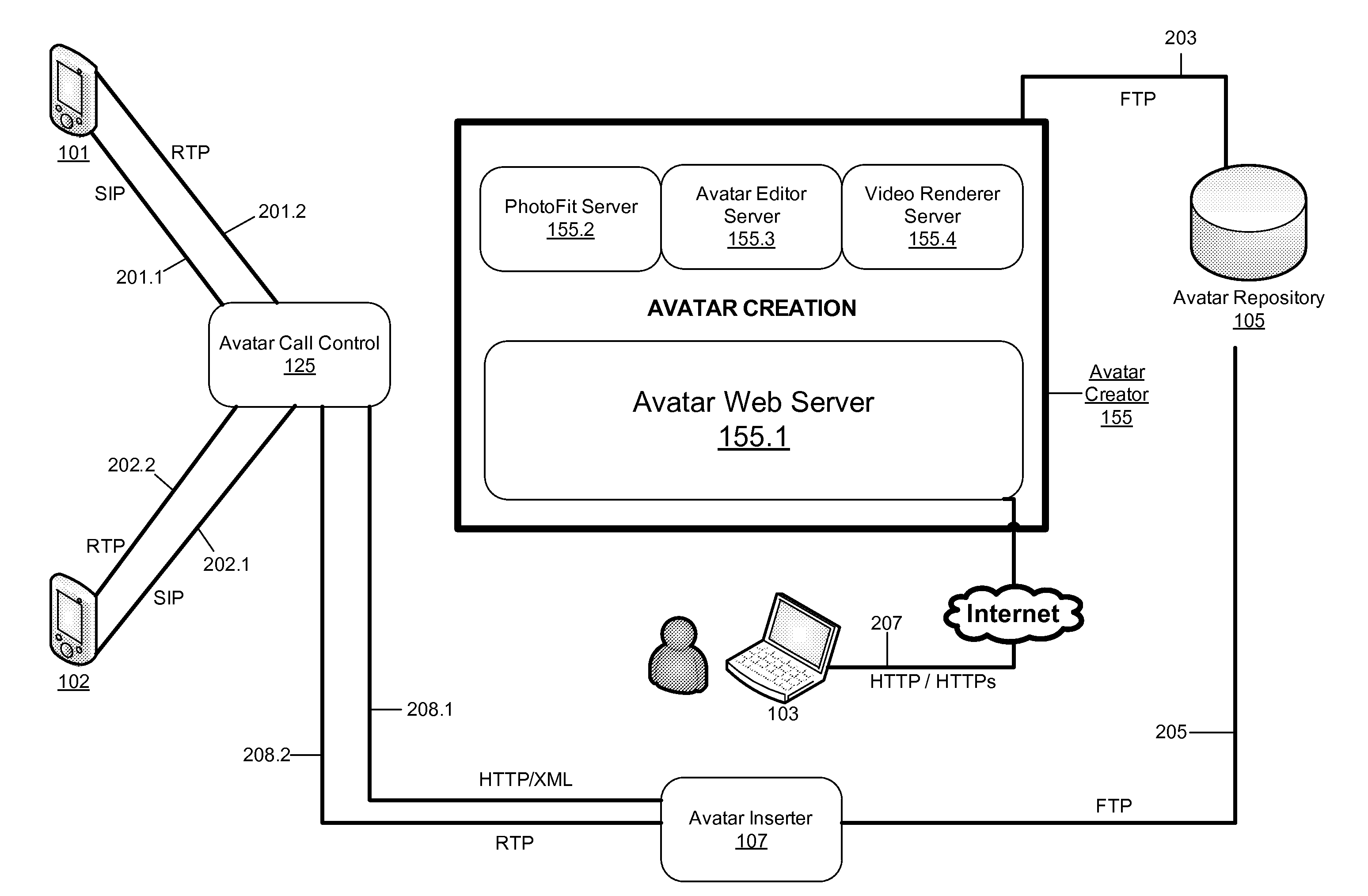
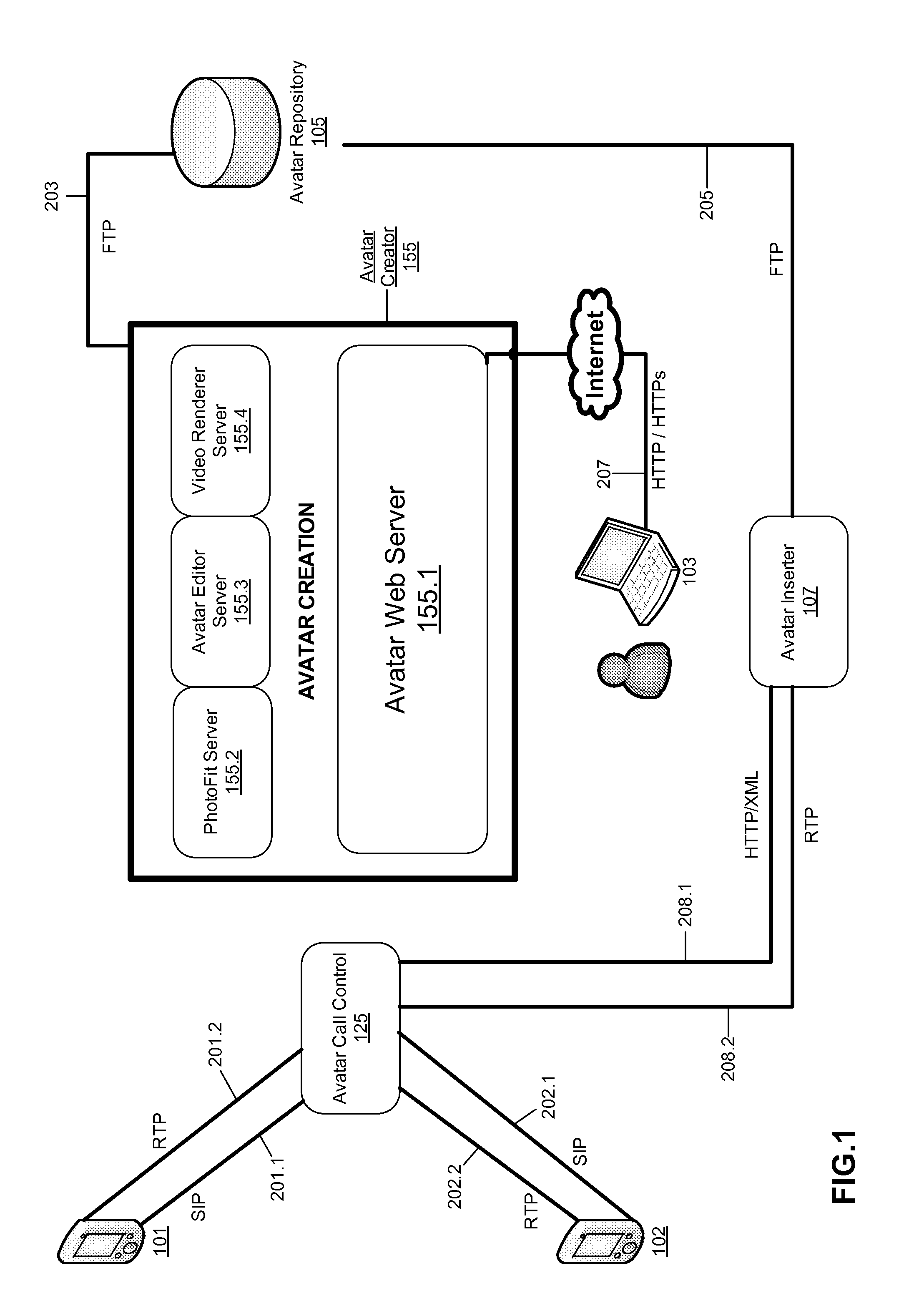
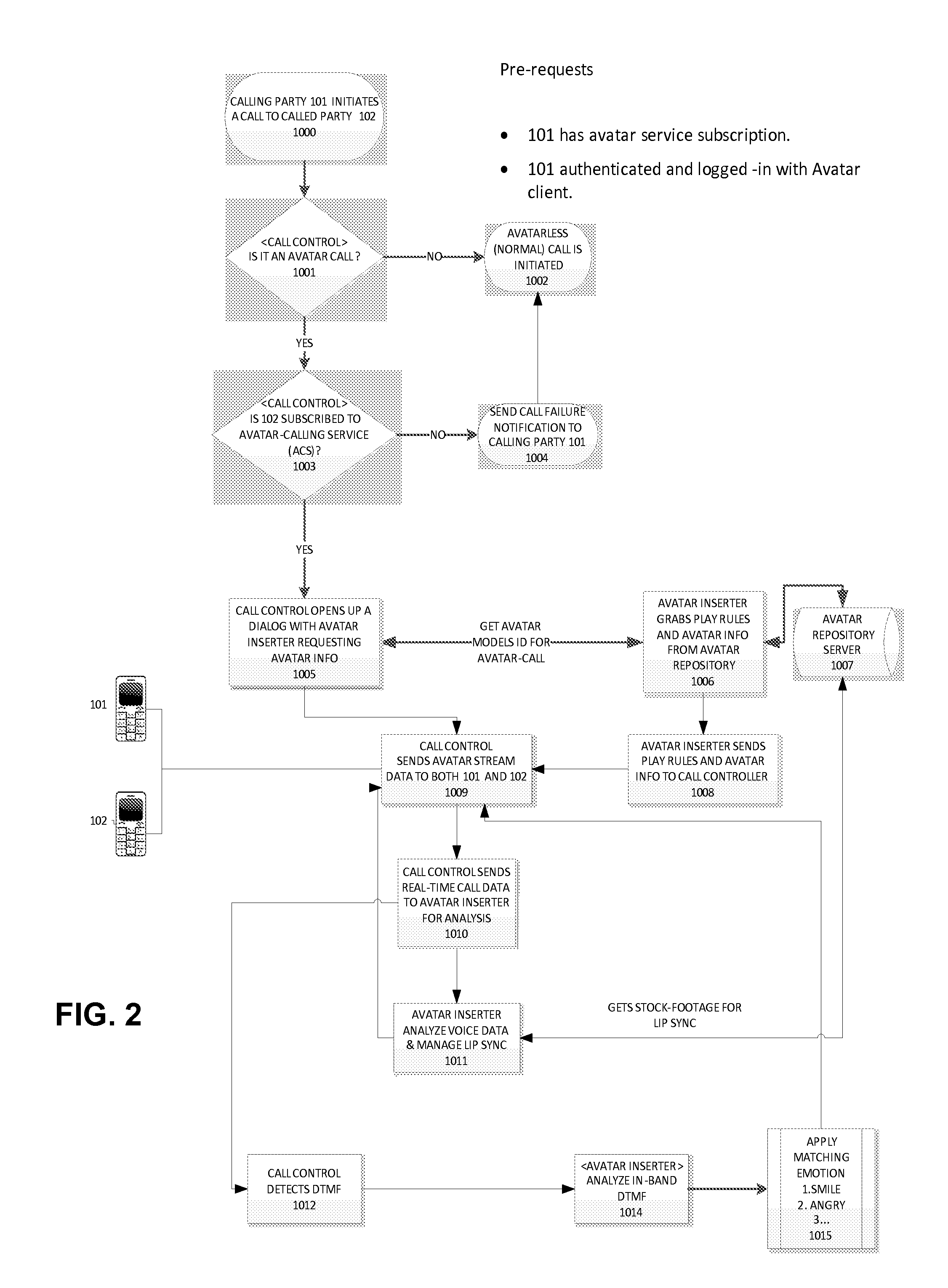
Interactive Avatars for Telecommunication Systems
ActiveUS20130258040A1Facilitate communicationServices signallingAutomatic exchangesSpoken languageBase calling
Owner:ARGELA YAZILIM & BILISIM TEKNOLOJILERI SAN & TIC A S
Systems and methods for caller ID and call destination authentication
ActiveUS9277049B1Special service for subscribersGraded-service arrangementsBase callingCall forwarding
Systems and methods for caller id authentication, caller id spoof detection, call destination authentication and call forwarding detection are disclosed. Embodiments include legitimate caller ID spoofing, authenticating blocked caller ID's and revealing caller ID's to certain parties. Other embodiments utilize caller ID authentication within a list based call handling system. Applications of caller ID authentication methodology to other forms of communication source address authentication, such as email, SMS, and postal mail are described.
Owner:DANIS SERDAR ARTUN
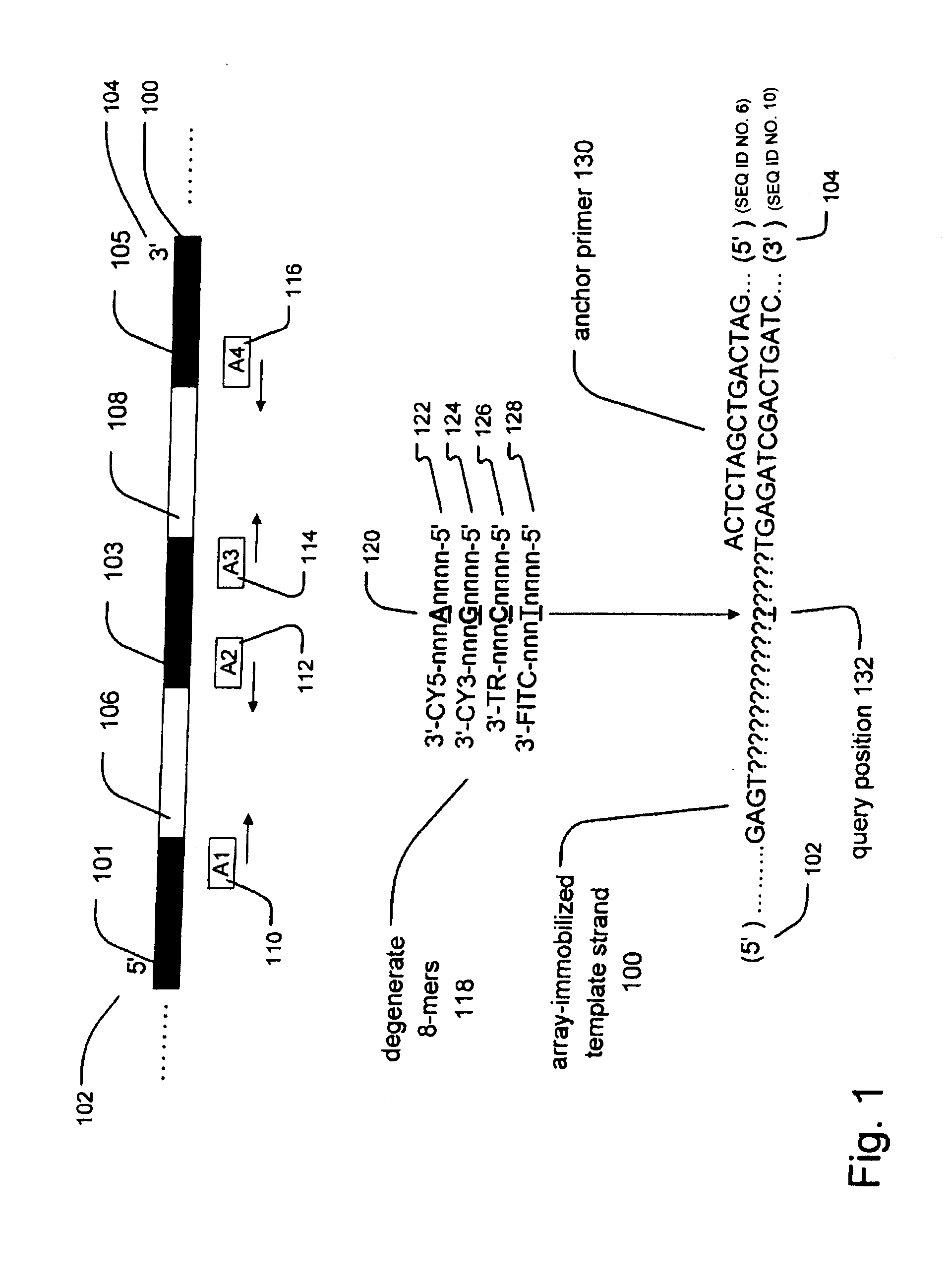
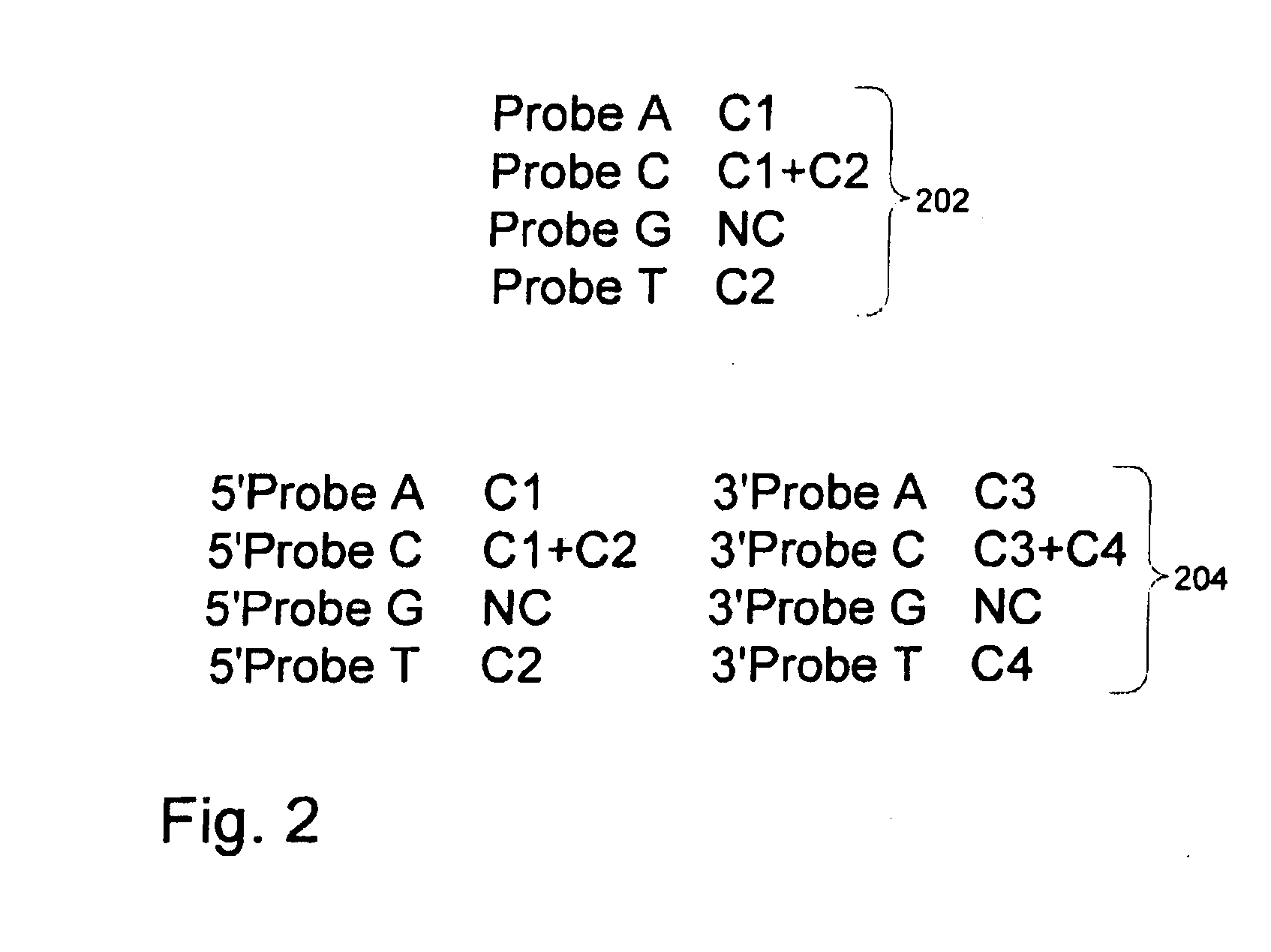
Methods and compositions for efficient base calling in sequencing reactions
ActiveUS20090263802A1Efficient connectionBioreactor/fermenter combinationsBiological substance pretreatmentsBase callingNucleotide sequencing
The present invention is directed to methods and compositions for acquiring nucleotide sequence information of target sequences. In particular, the present invention provides methods and compositions for improving the efficiency of sequencing reactions by using fewer labels to distinguish between nucleotides and by detecting nucleotides at multiple detection positions in a target sequence.
Owner:COMPLETE GENOMICS INC
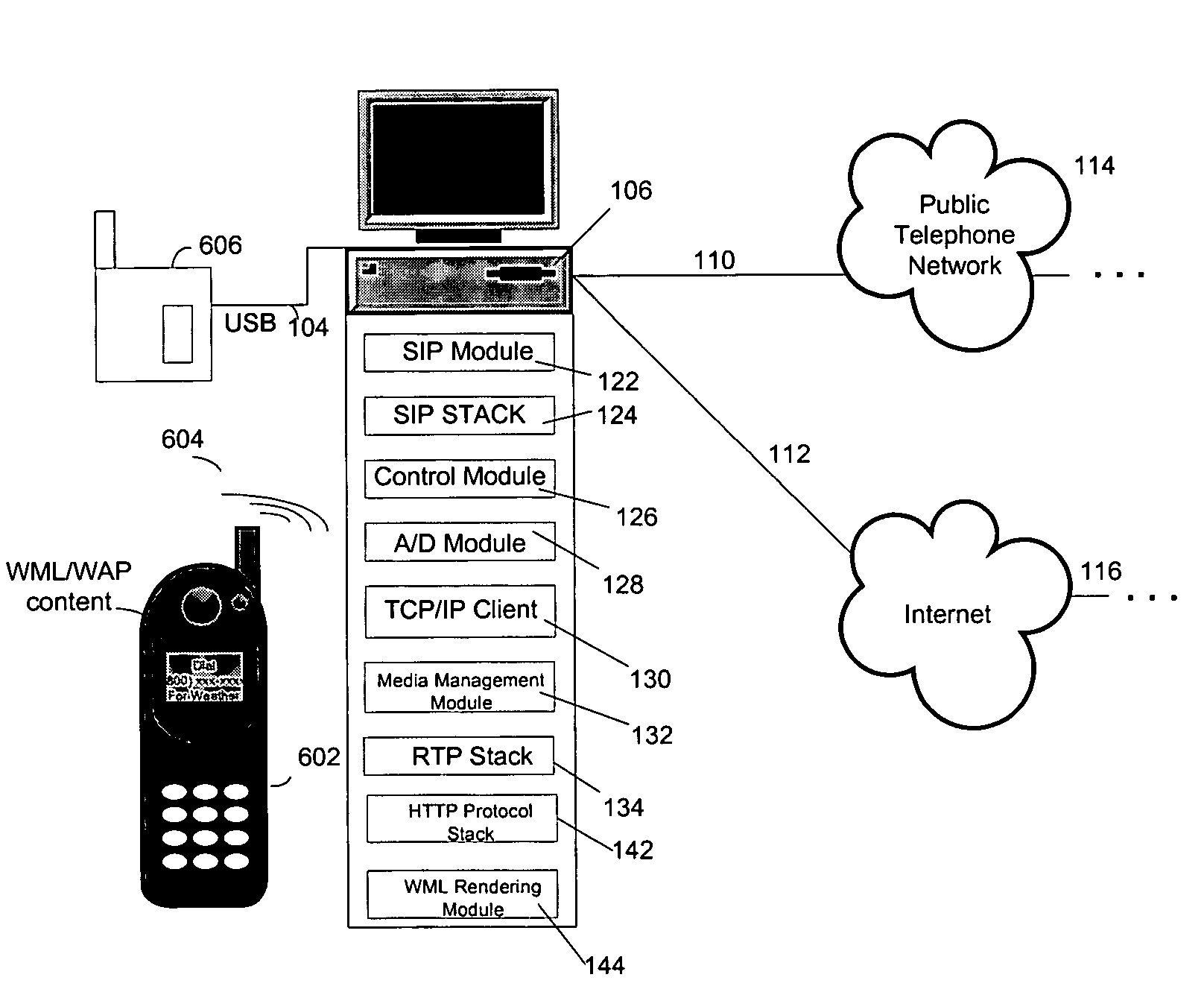
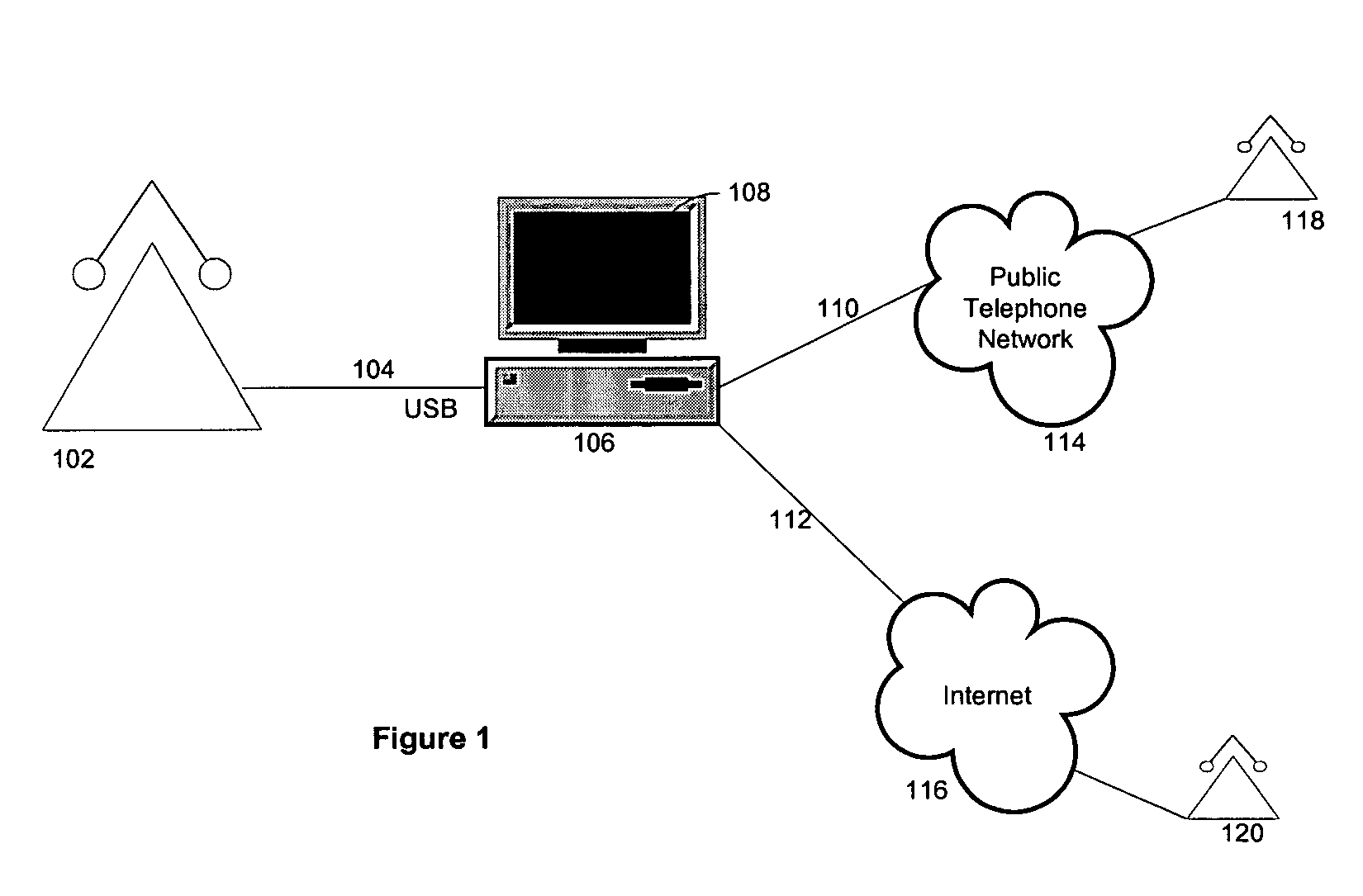
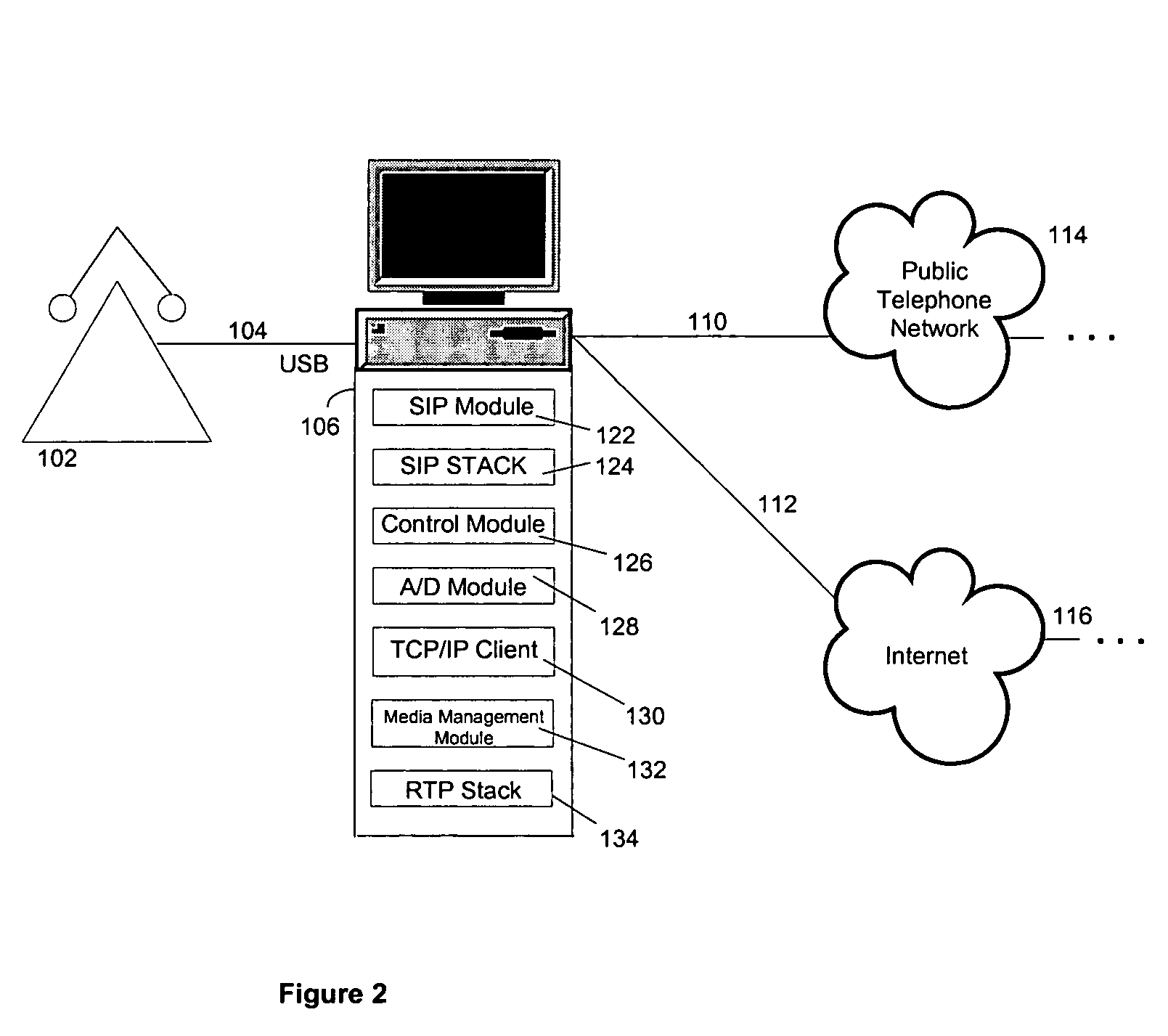
System and method for network phone having adaptive transmission modes
A system for an adaptive network phone includes a SIP-enabled handset or other telephone device to be connected to a host computer, for instance via a USB connection. The host computer may initiate a call event when the user picks up the SIP device and wishes to make a call, in one regard by testing line conditions for a data connection to the Internet or other network to determine if a packet-based call will meet minimum noise, delay or other criteria of the user. If the conditions are satisfactory, the call may proceed as a packet network transmission, otherwise the call may revert to the public switched telephone network for fallback completion. The SIP-enabled handset may also interface to multimedia functions in the host computer, for instance to permit paging, answering machine, cordless operation or other features.
Owner:MALIKIE INNOVATIONS LTD
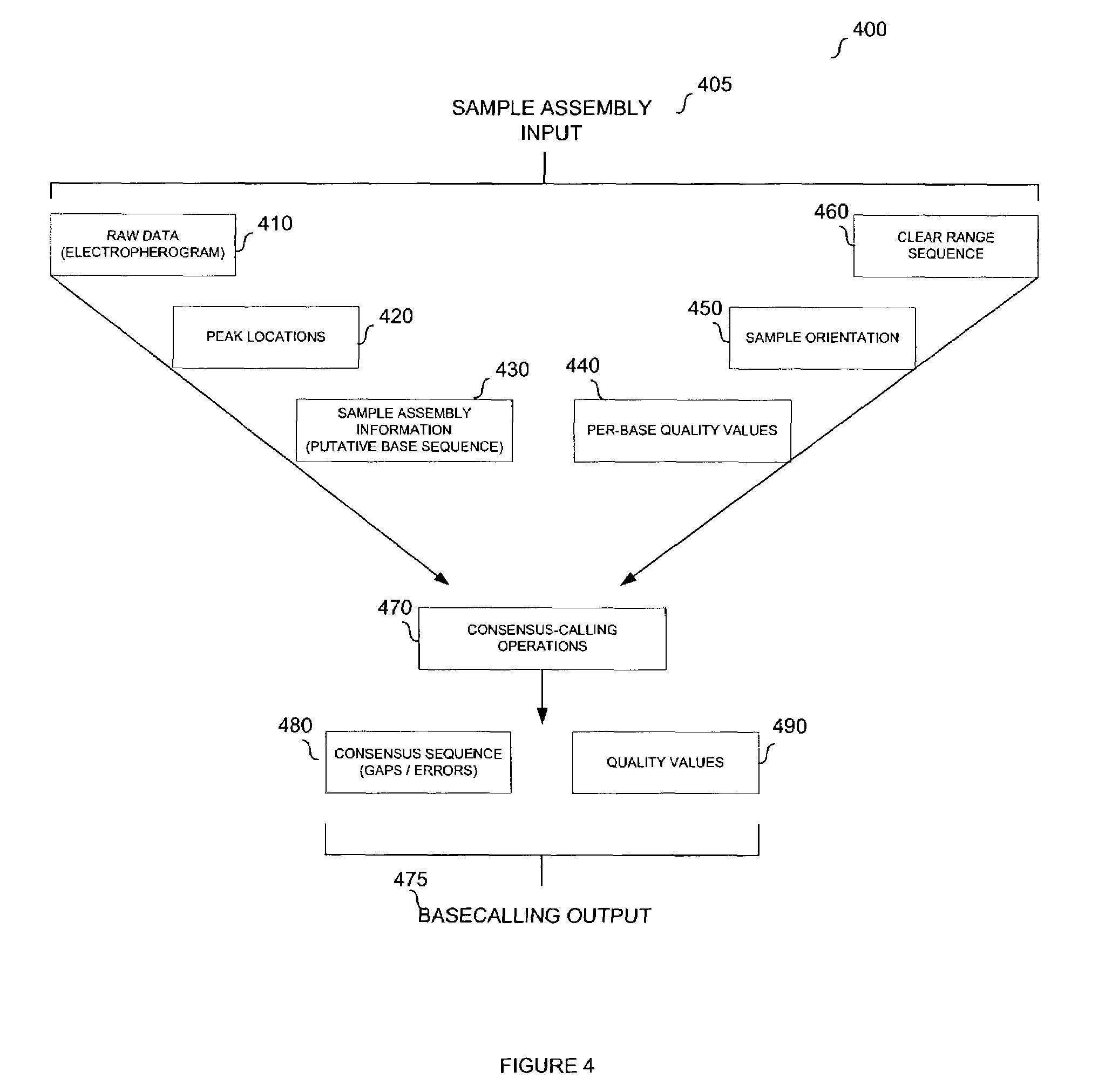
System and method for consensus-calling with per-base quality values for sample assemblies
InactiveUS7406385B2Quality improvementRemove uncertaintyMicrobiological testing/measurementBiological testingSequence analysisNucleotide
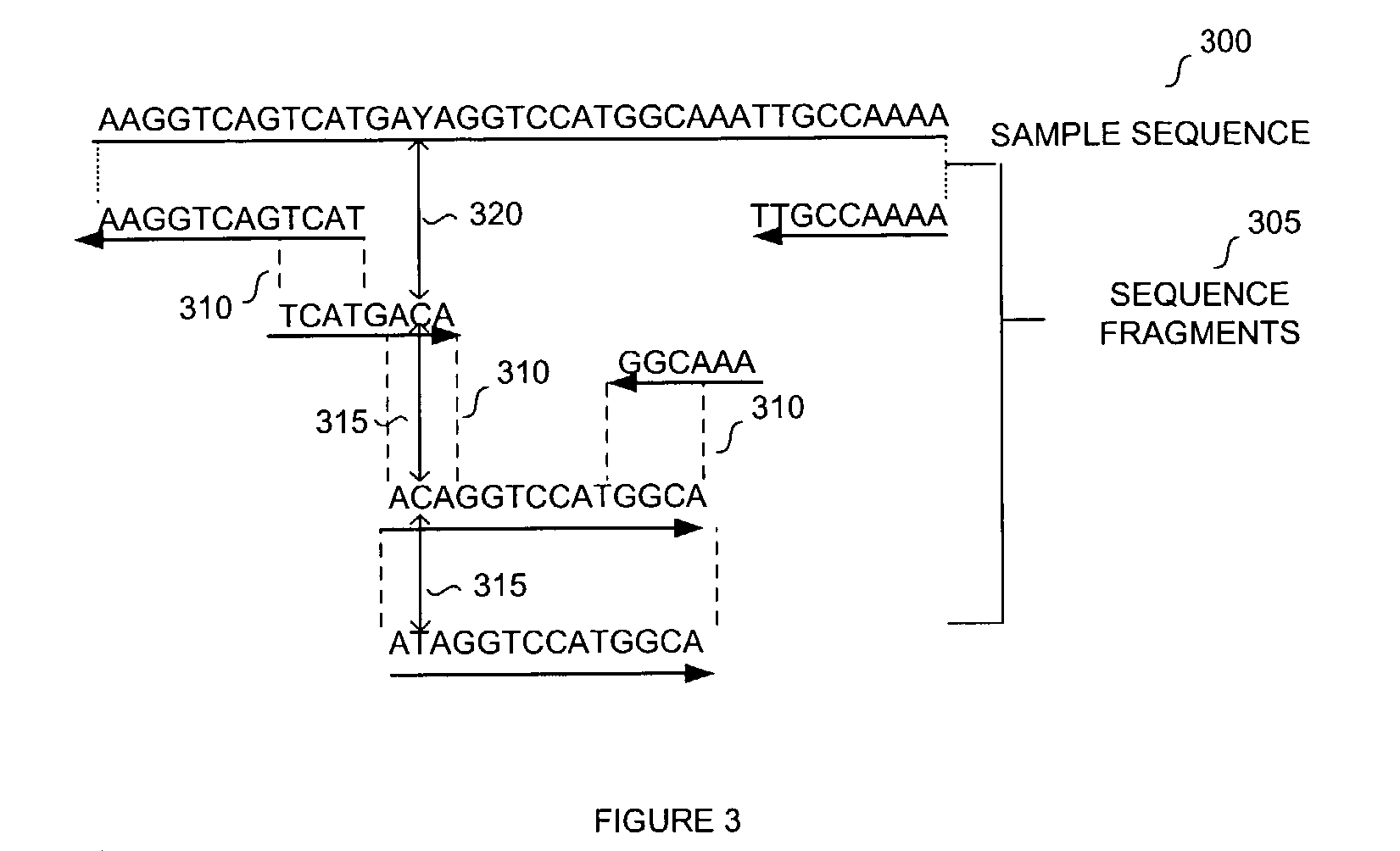
The present teachings disclose a method for evaluation of a polynucleotide sequence using a consensus-based analysis approach. The sequence analysis method utilizes quality values for a plurality of aligned sequence fragments to identify consensus basecalls and calculate associated consensus quality values. The disclosed method is applicable to resolution of single nucleotide polymorphisms, mixed-based sequences, heterozygous allelic variants, and heterogeneous polynucleotide samples.
Owner:APPL BIOSYSTEMS INC
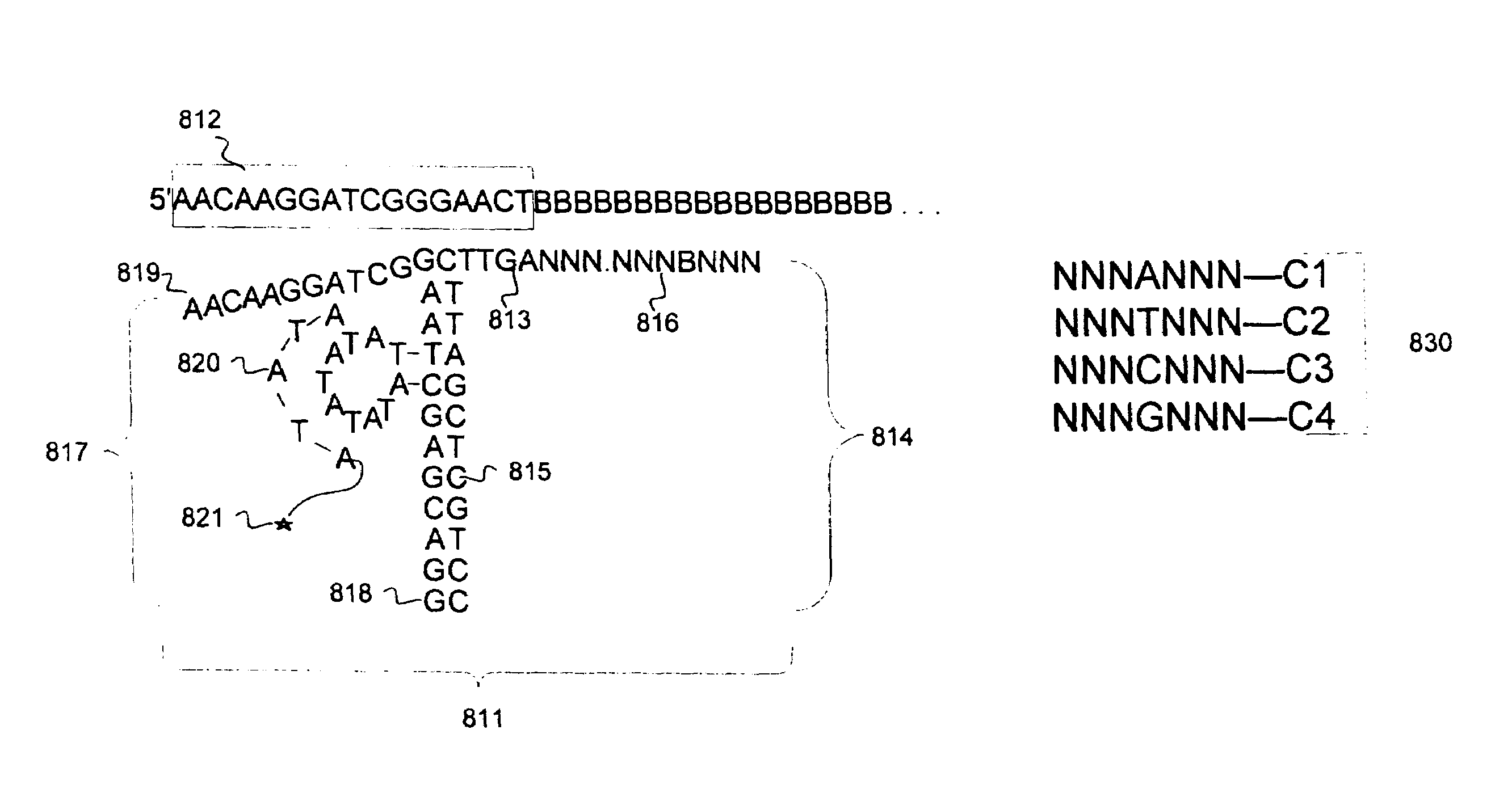
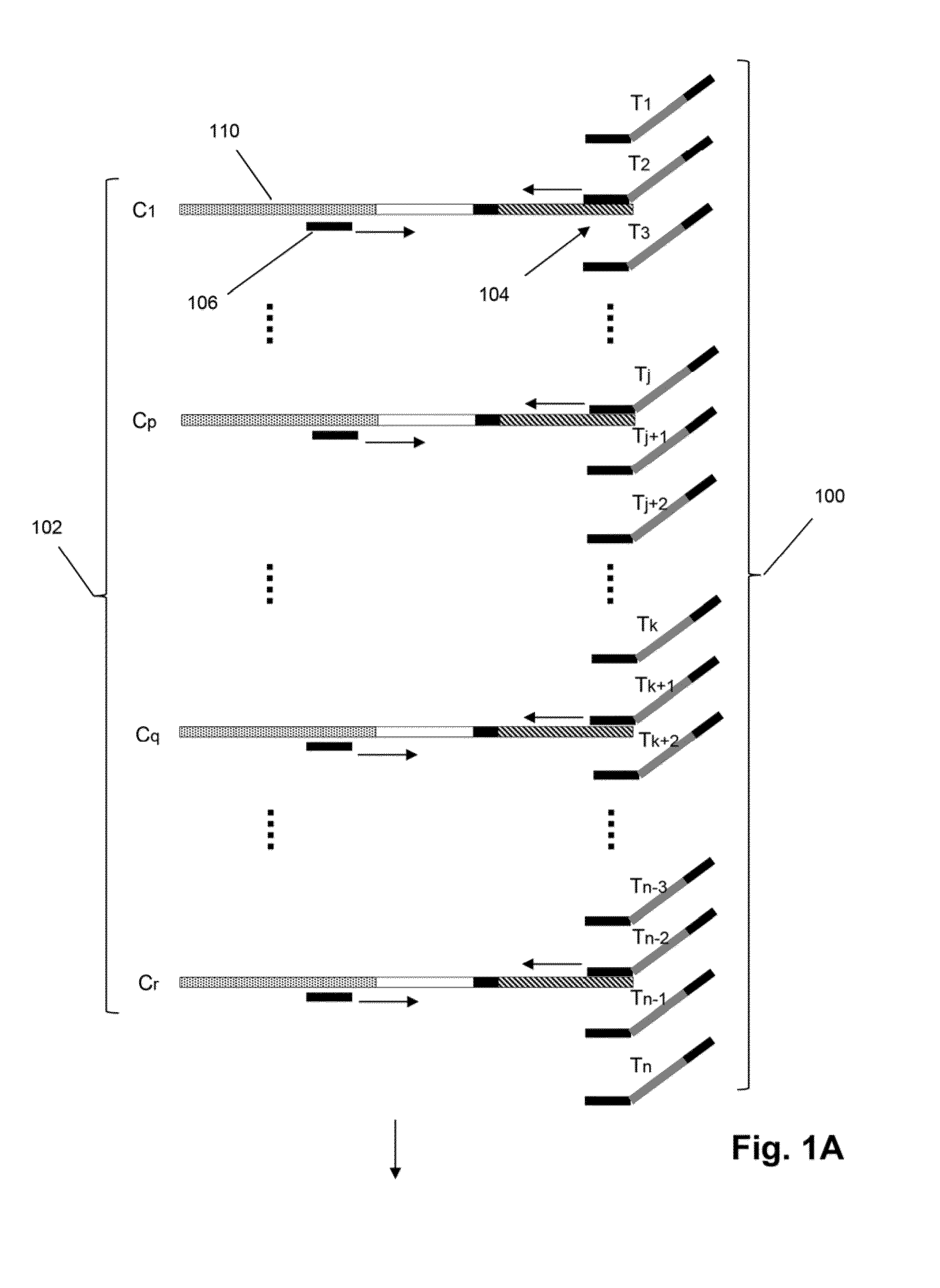
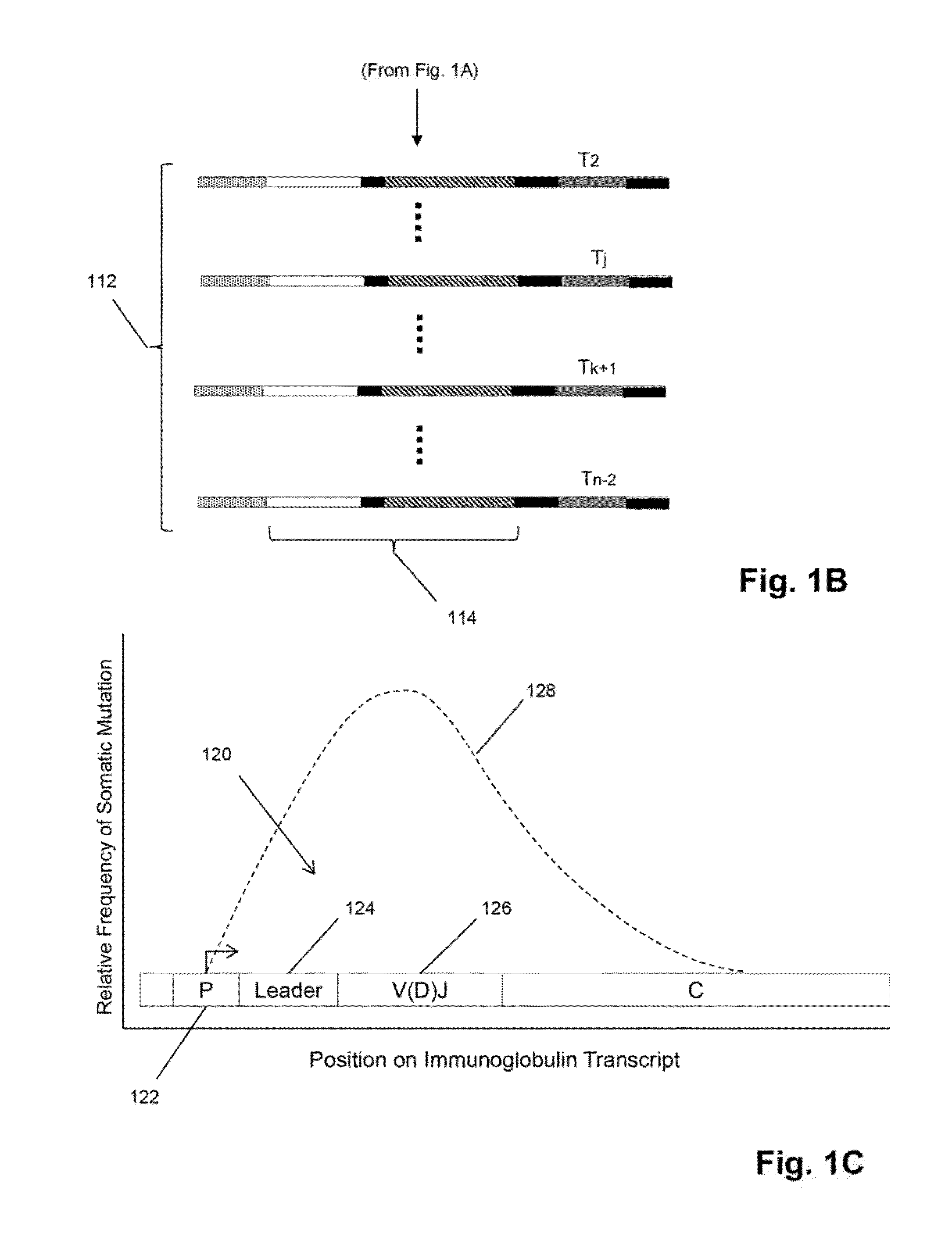
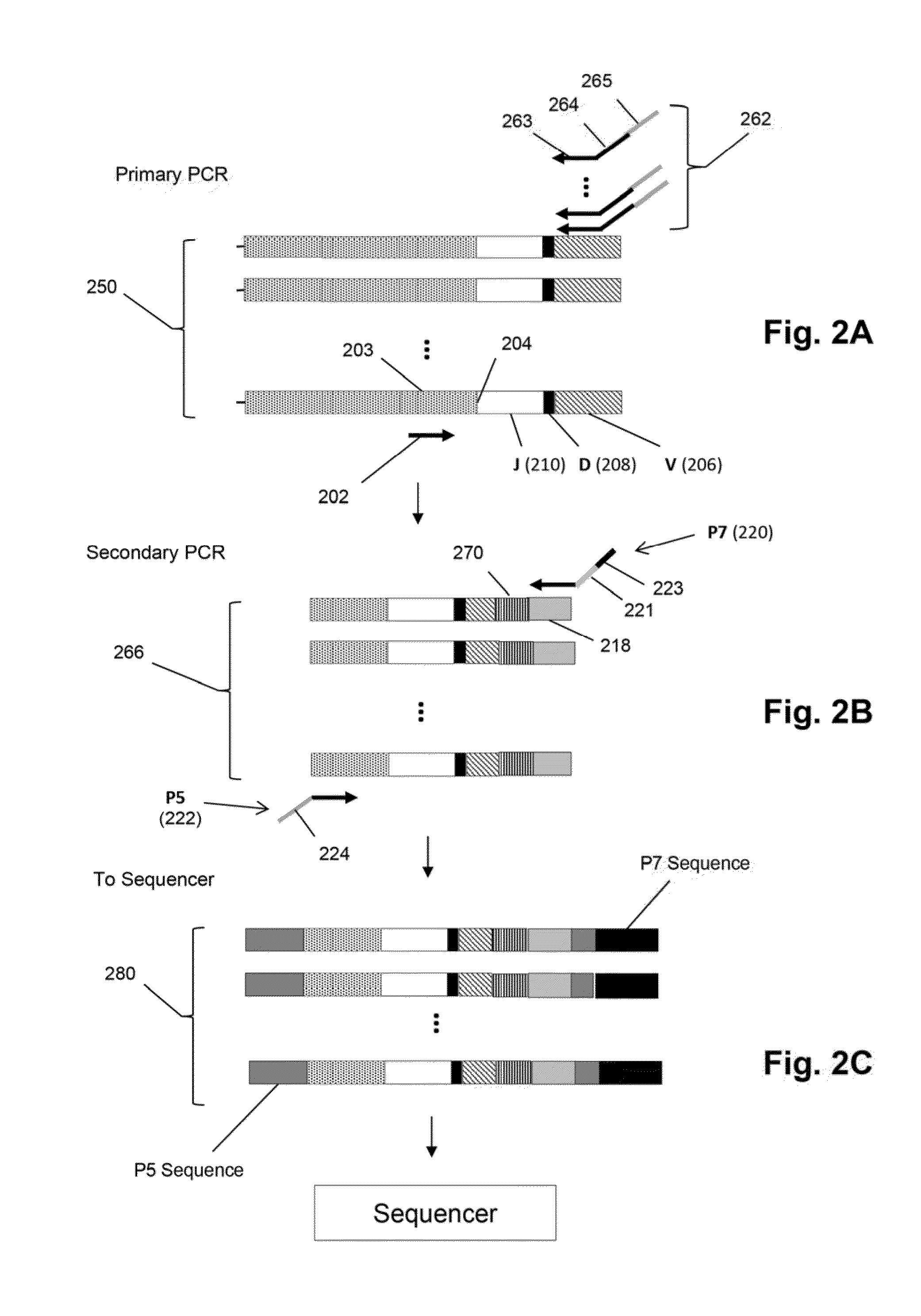
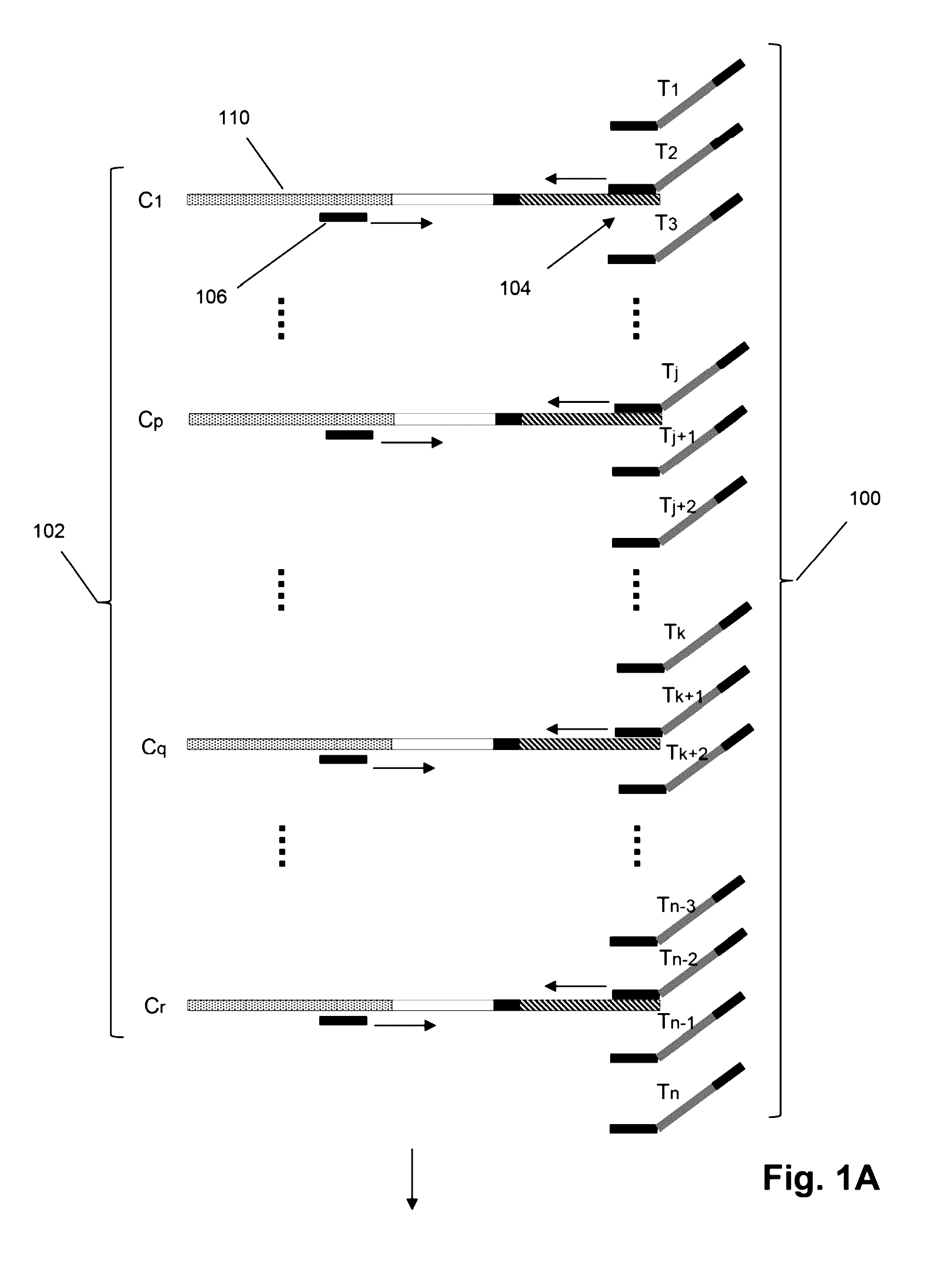
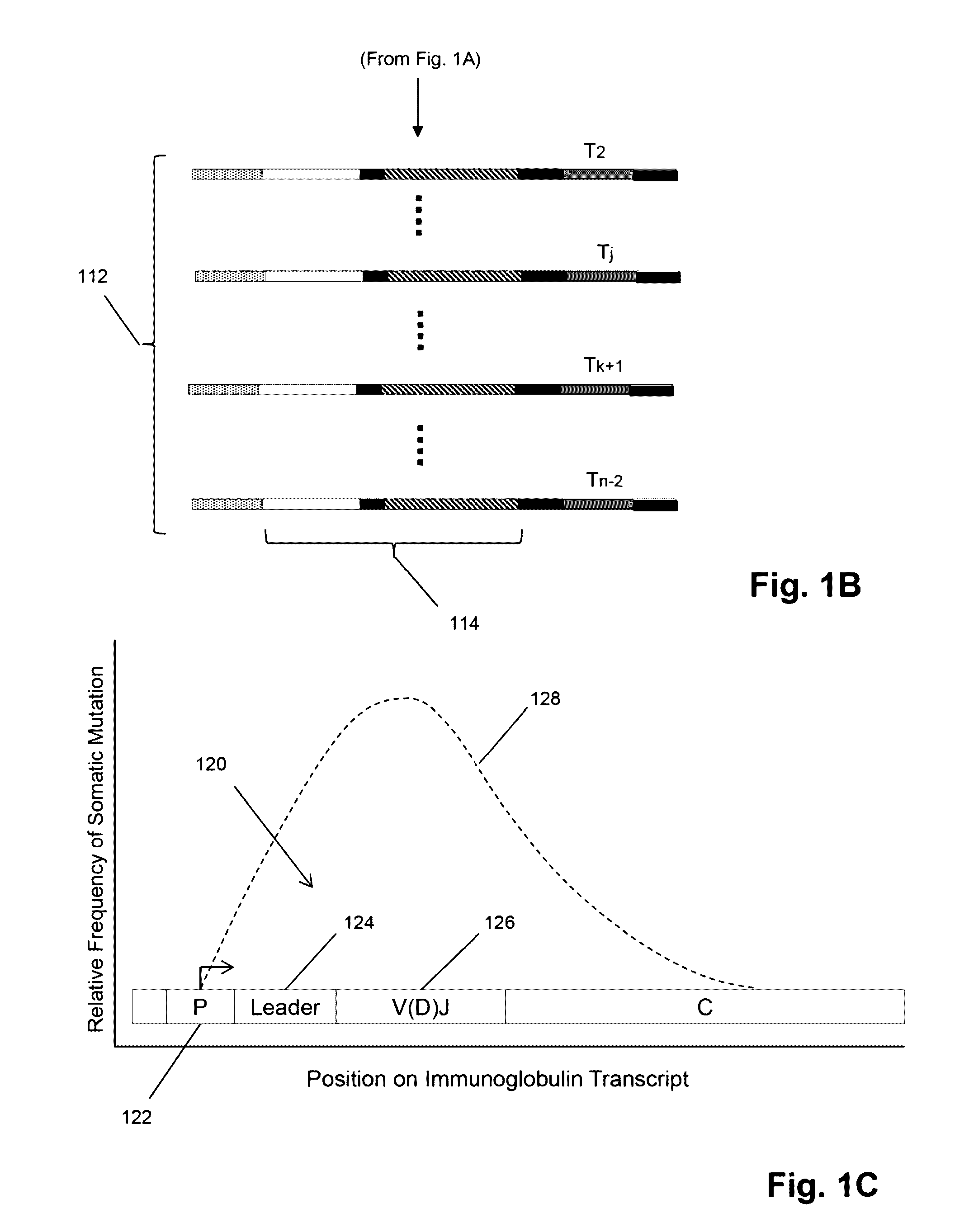
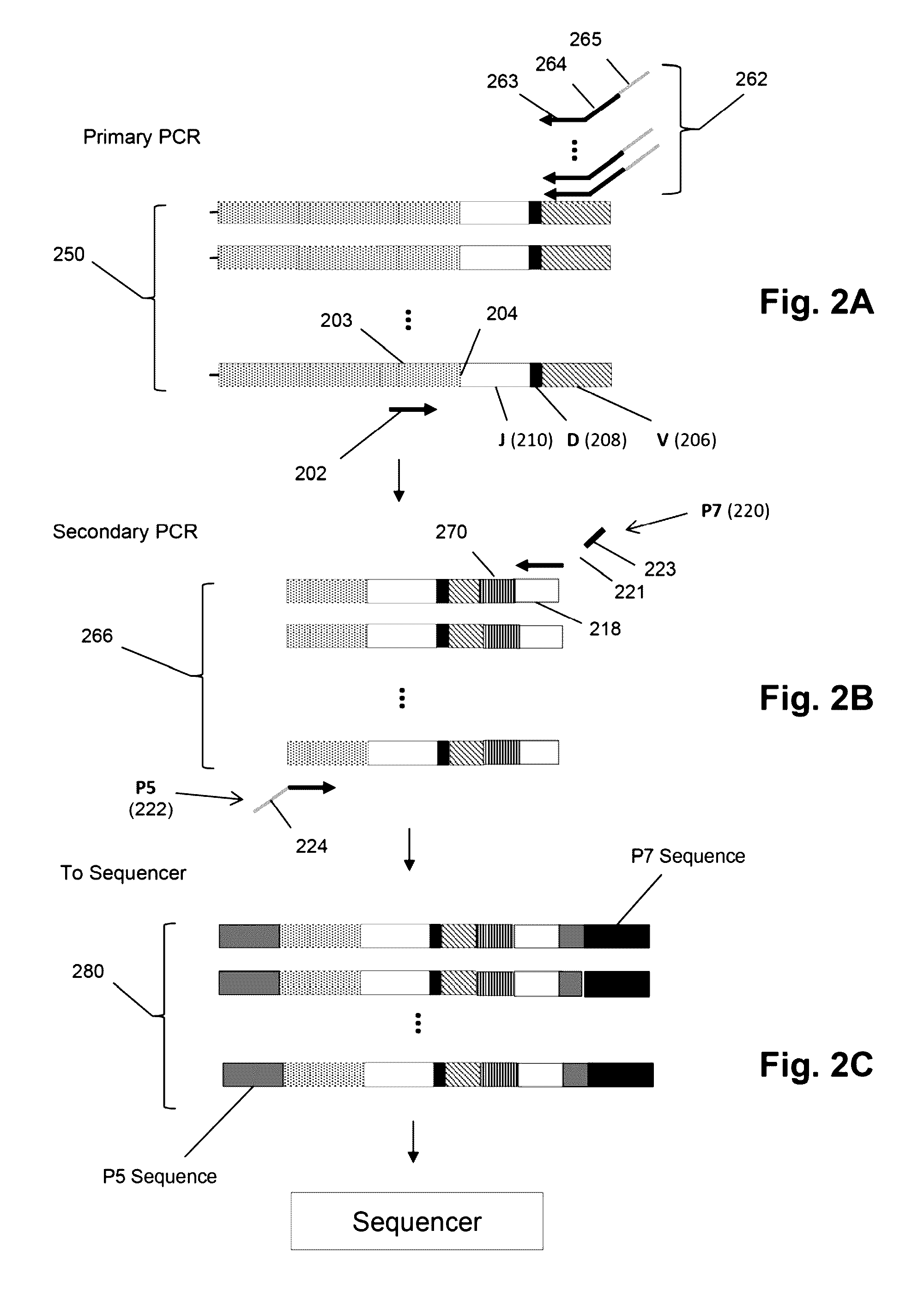
Method of sequence determination using sequence tags
The invention is directed to the use of sequence tags to improve sequence determination of amplicons of related sequences, particularly large and complex amplicons, such as those comprising recombined nucleic acids encoding immune receptor molecules. In one aspect, sequence reads having the same sequence tags are aligned after which final base calls are determined from a (possibly weighted) average base call from sequence read base calls at each position. Similarly, in another aspect, sequence reads comprising series of incorporation signals are aligned by common sequence tags and base calls in homopolymer regions are made as a function incorporation signal values at each “flow” position.
Owner:ADAPTIVE BIOTECH
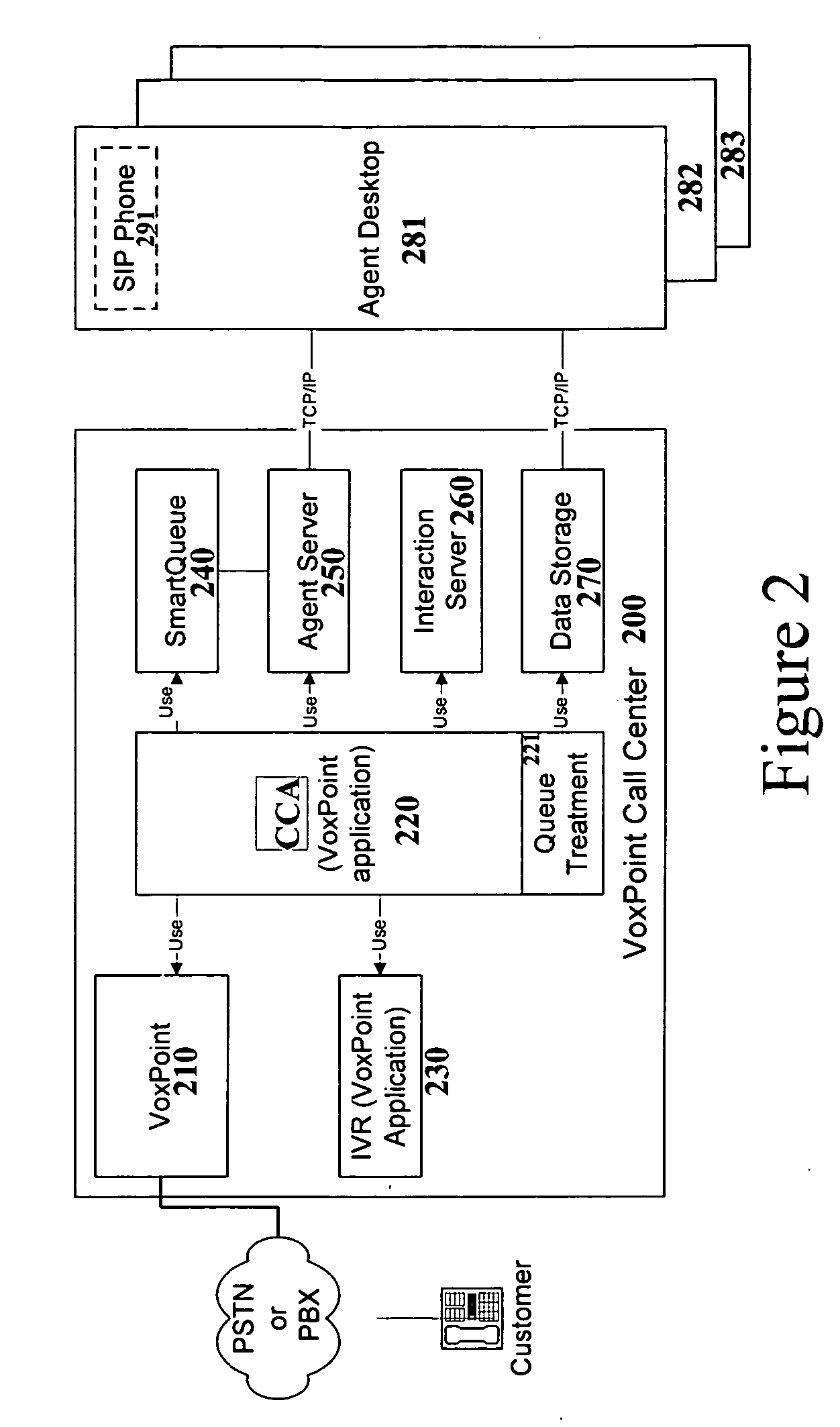
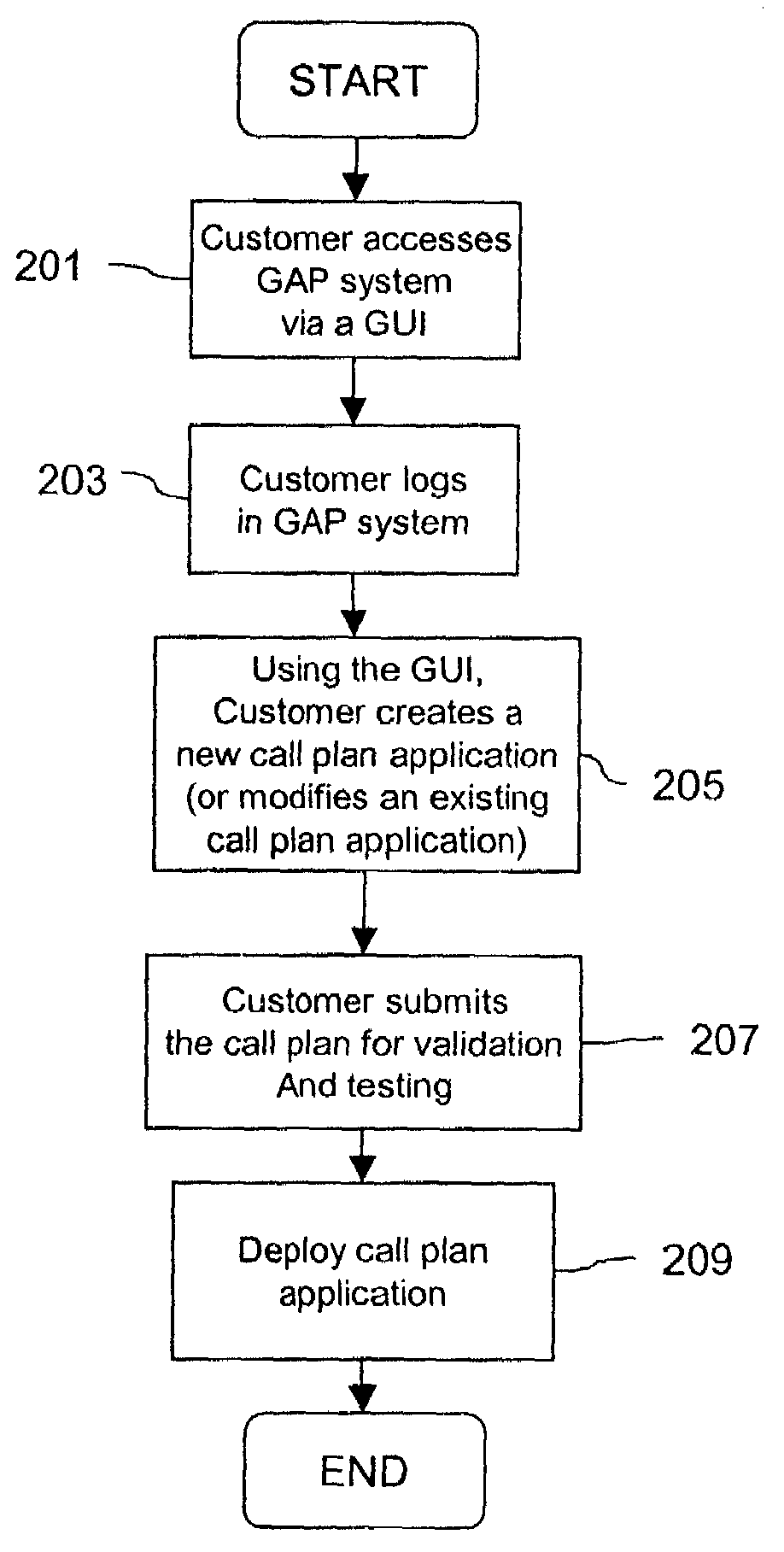
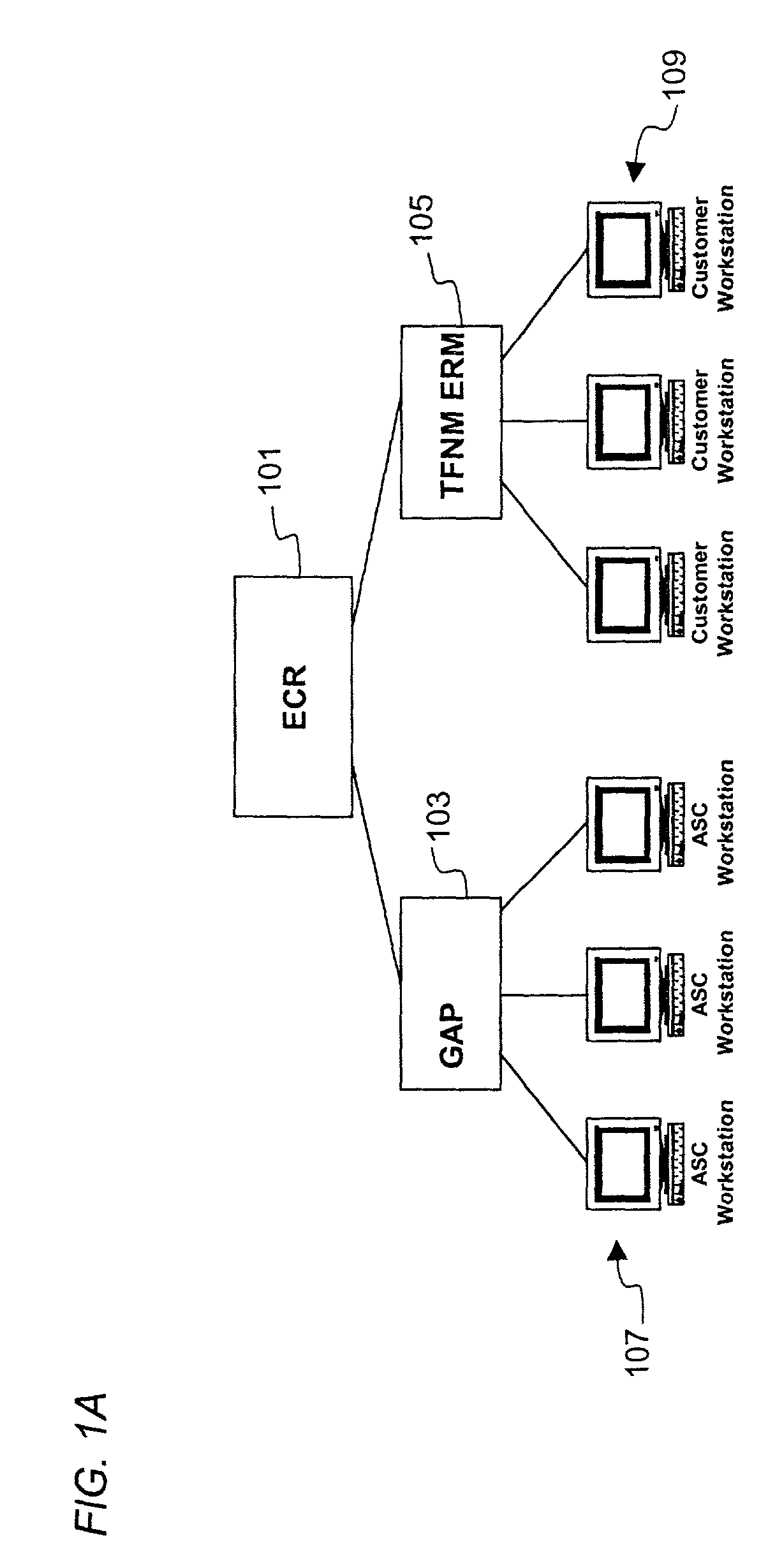
Graphical user interface (GUI) based call application system
ActiveUS7117447B2Special service for subscribersSupervisory/monitoring/testing arrangementsFeature setBase calling
An approach for providing self-service call plan application development is disclosed. A graphical system includes a computing system that is configured to cause a graphical user interface (GUI) to be present for automated creation of an application for controlling call flow logic. The application supports a predefined feature set. Additionally, the system includes a database that is coupled to the server and configured to store the application. The server is further configured to determine whether the application is valid and to initiate deployment of the application. The deployment may be performed on a real-time basis.
Owner:VERIZON PATENT & LICENSING INC
Methods and apparatus for facilitating the interaction between multiple telephone and computer users
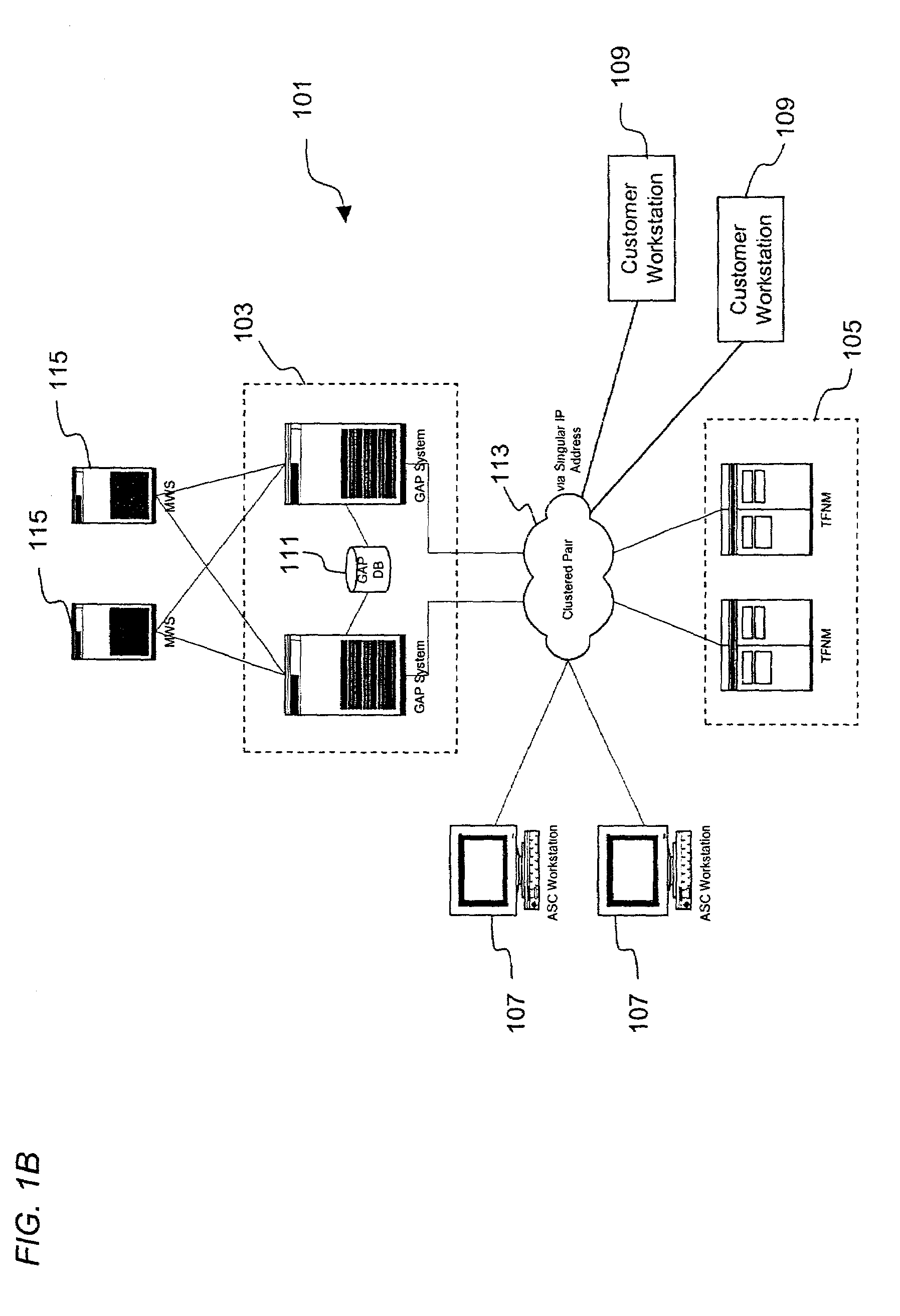
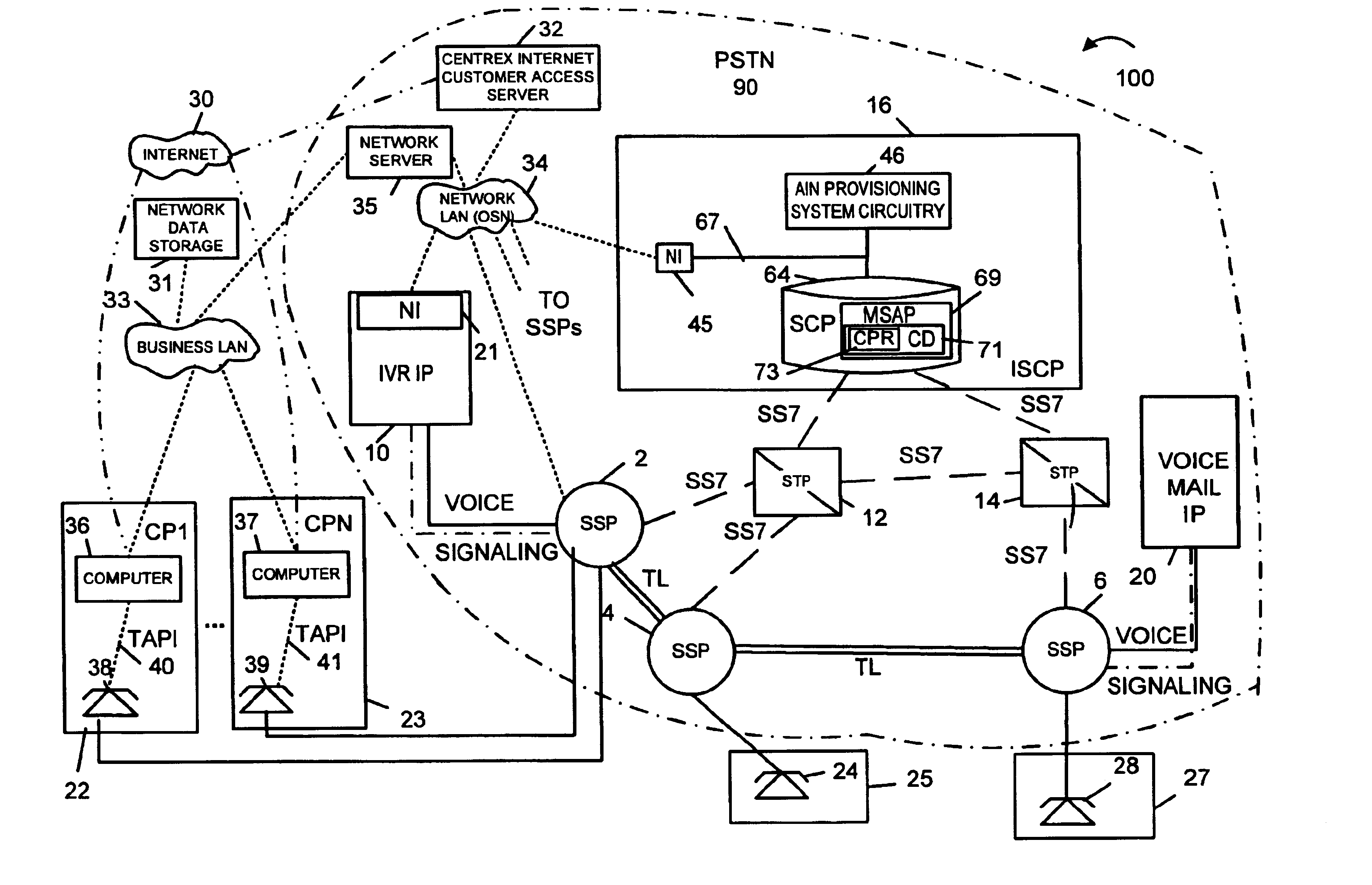
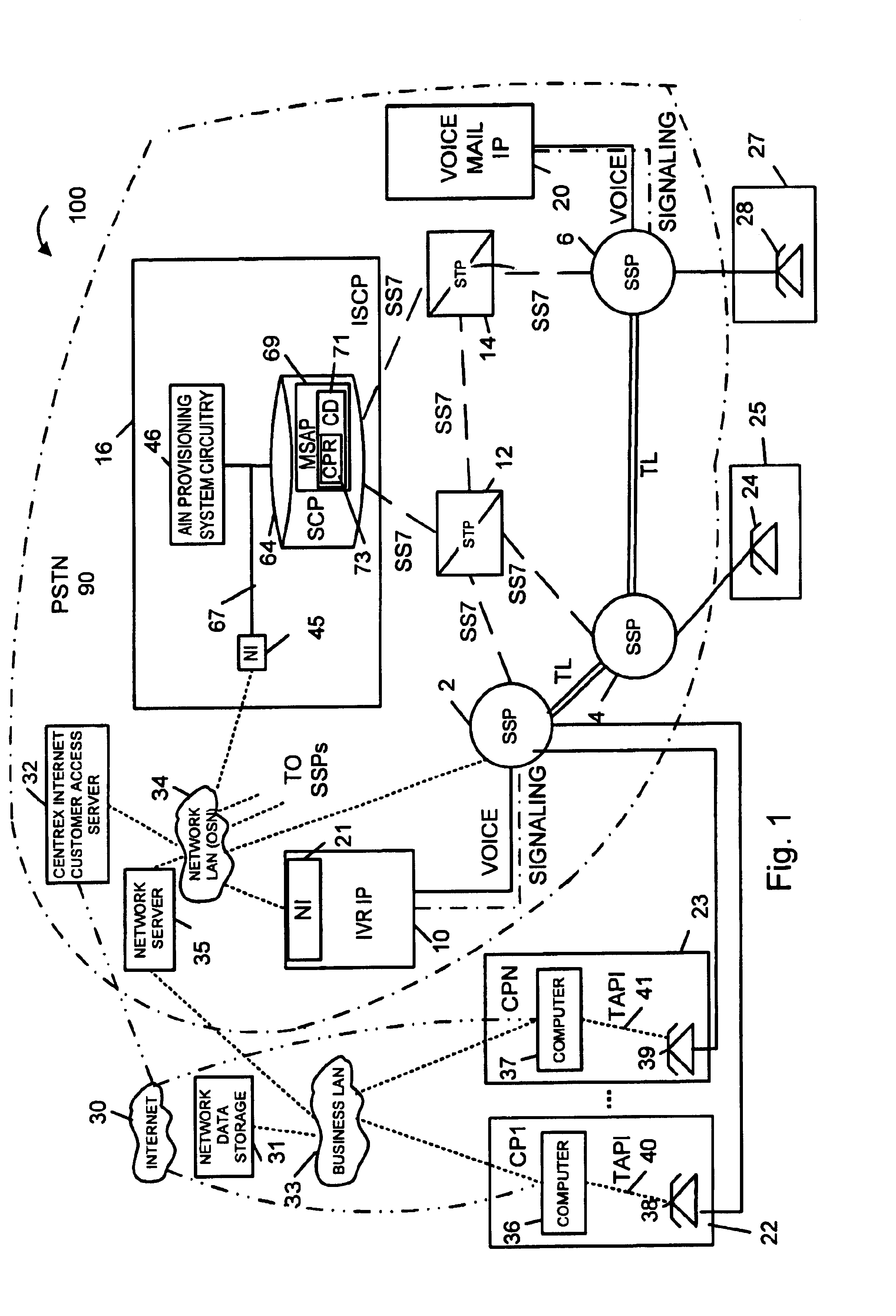
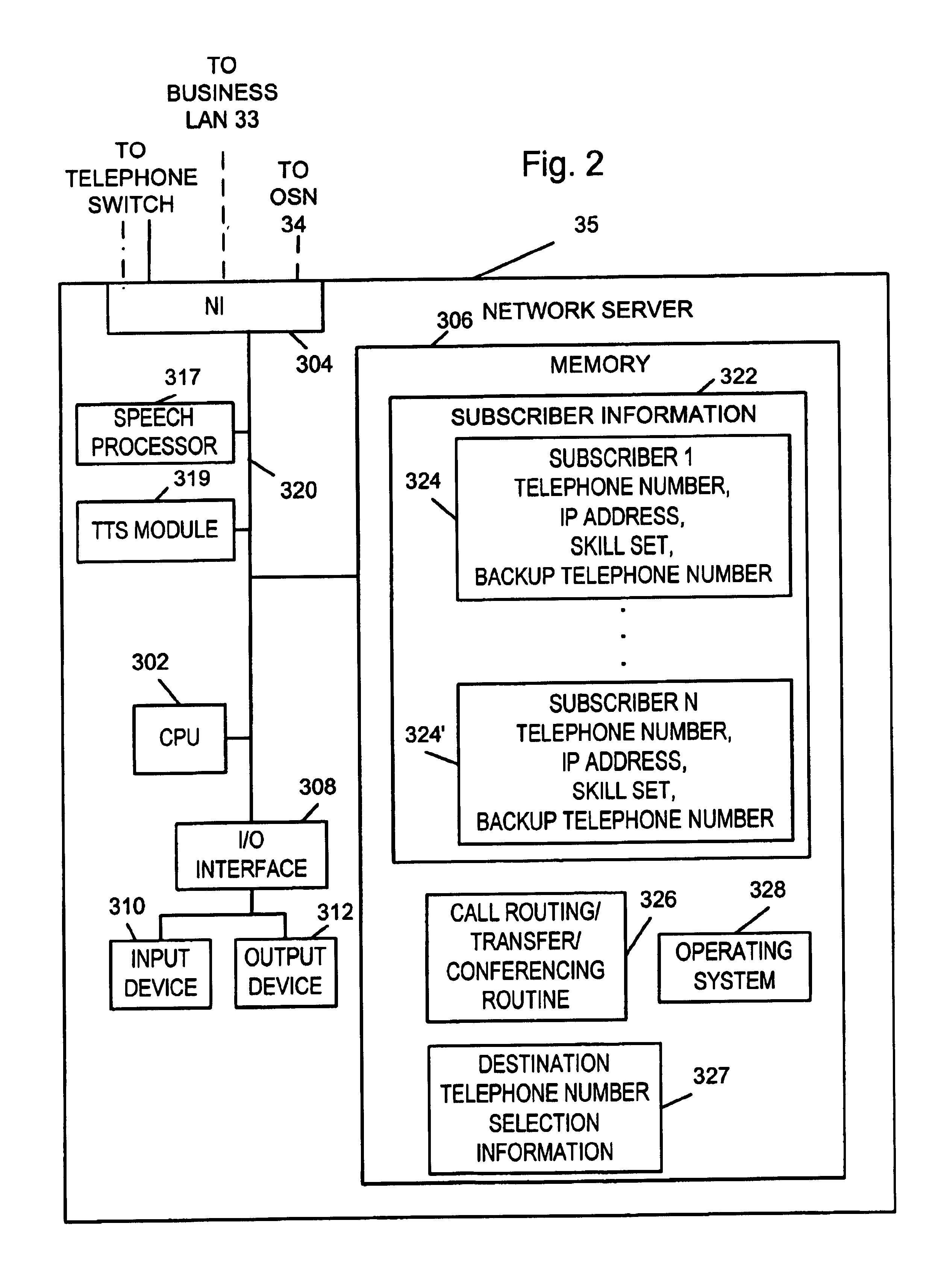
InactiveUS6920213B2Telephone data network interconnectionsIntelligent networksComputer usersBase calling
AIN based call routing, transfer and conferencing methods and apparatus are disclosed. In various embodiments initial call routing is based on the availability of a party to service a call as determined from a computer system associated with the party selected to service the call. The party's computer system supports a telephone programming application interface (TAPI) which allows a telephone network server to determine the availability of the party selected to service the call from, in part, TAPI obtained telephone line status information. The network server supplies call related data to the computer system of the party assigned to service the call. Call transfer and conferencing operations along with the transfer of call related data are also supported. AIN mid-call triggers are used in some embodiments to support call transfer and conferencing operations.
Owner:VERIZON PATENT & LICENSING INC
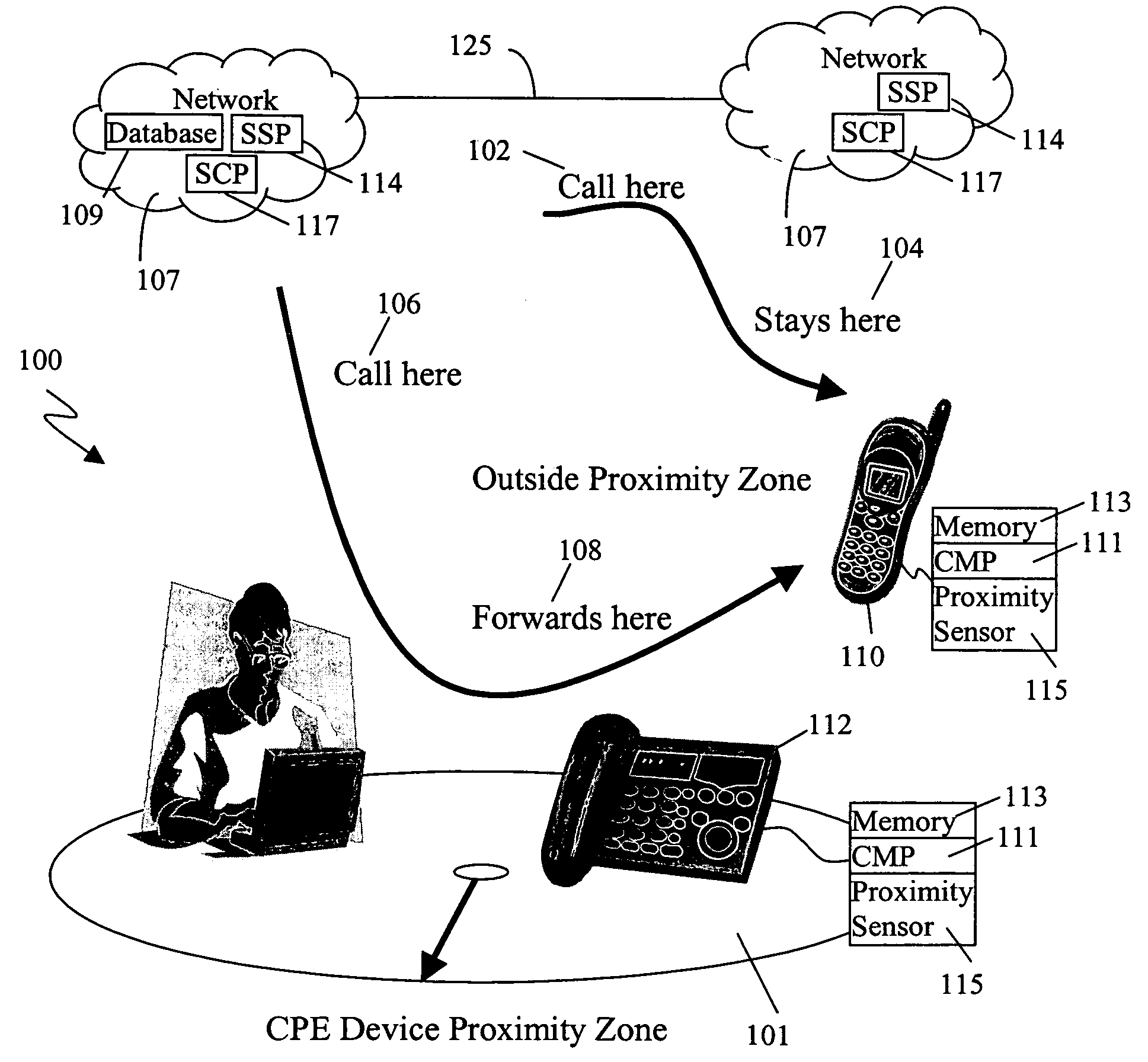
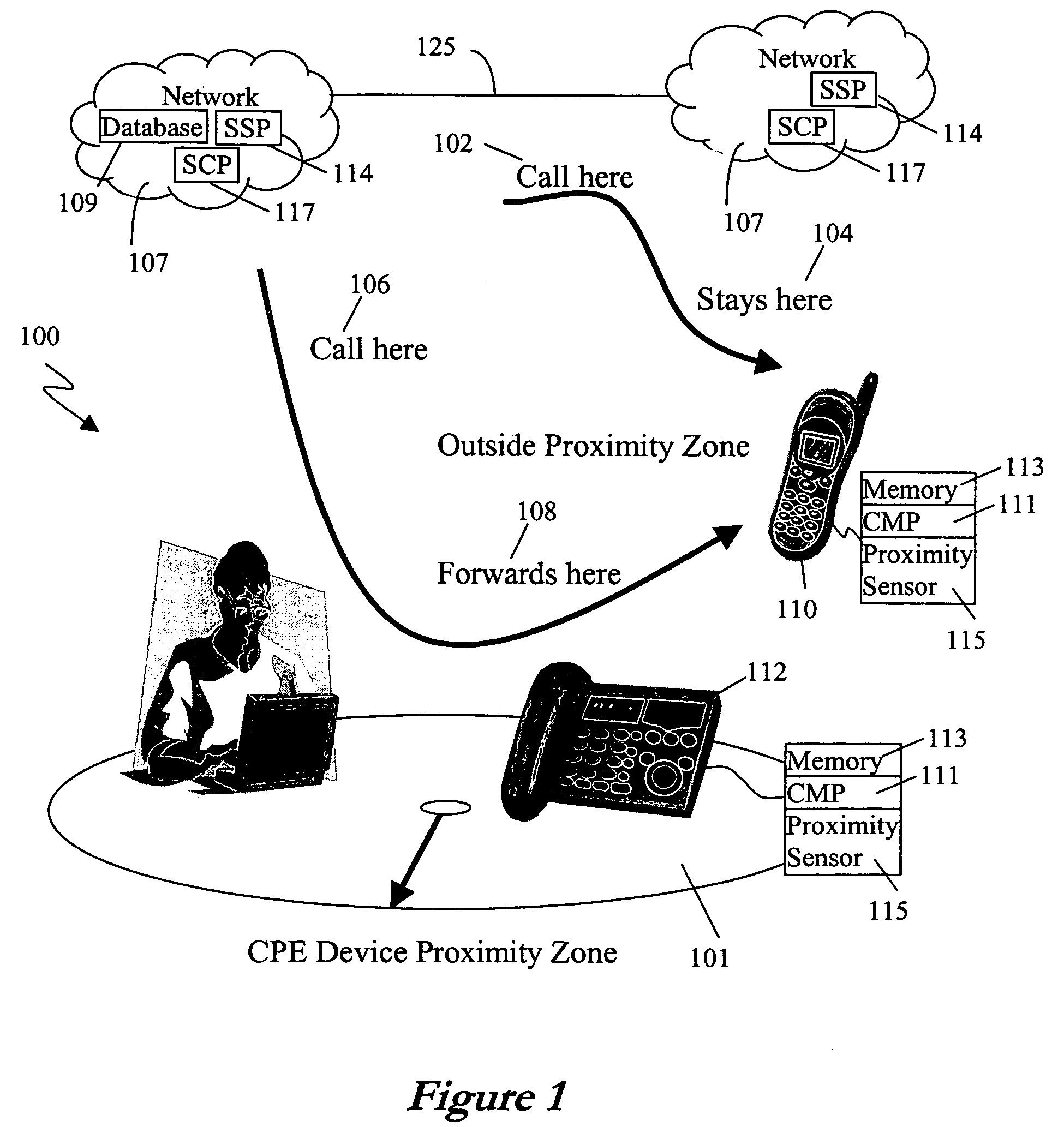
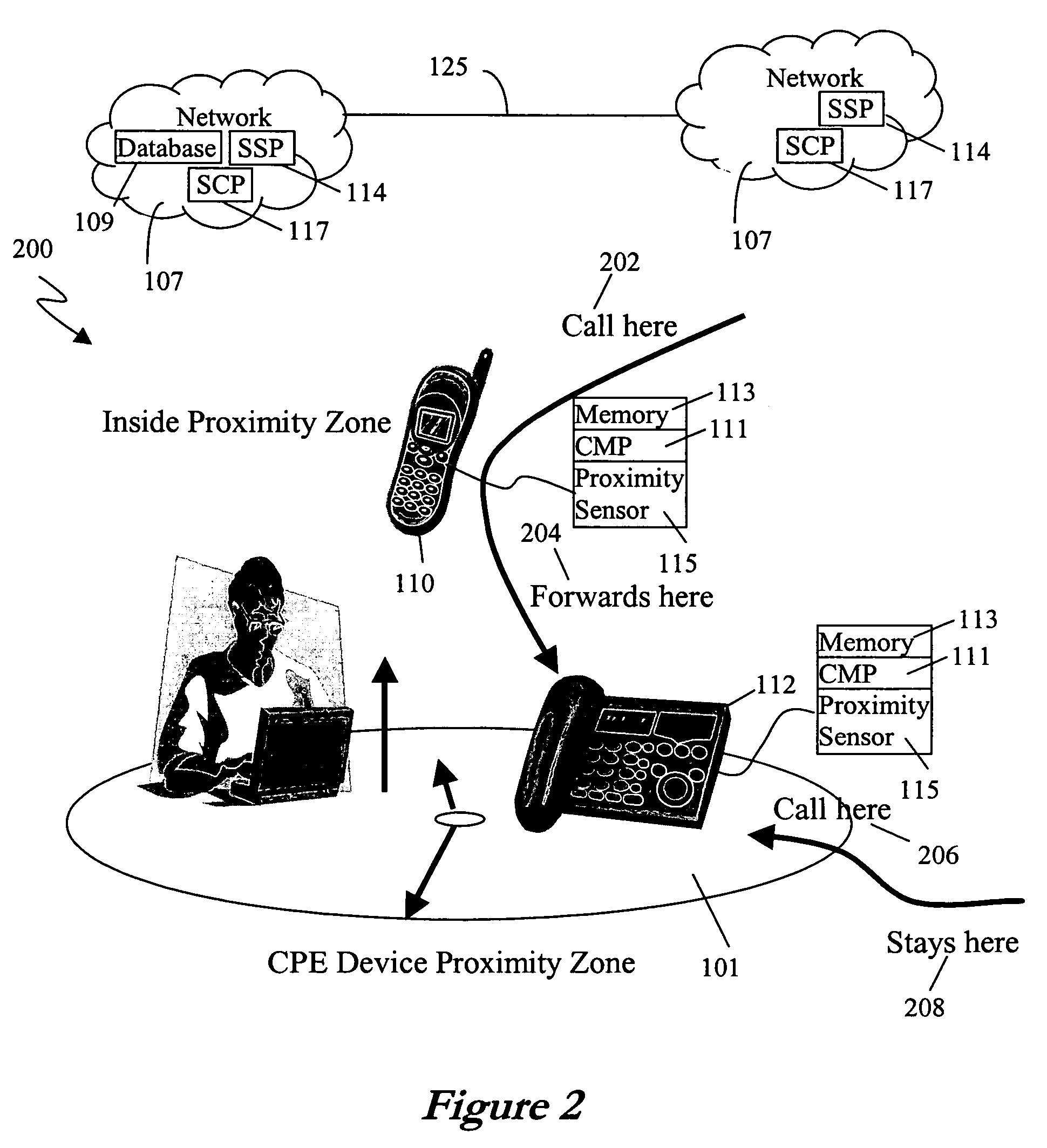
Proximity based call management
ActiveUS20080004002A1Special service for subscribersConnection managementProximity sensorBase calling
A method is disclosed for proximity-based call management that includes sensing a proximity event between a first device associated with a first network and a second device associated with a second network, sending a first communication address for the first device from the first device to the second device over a wireless communication path between the first device and the second device, and signaling the second network from the second device to establish a conference call between the first device and the second device. A proximity based call management apparatus is disclosed including a processor coupled to a memory, a proximity sensor in data communication with the processor, a network interface in data communication with the processor, and a computer program stored in the memory for execution by the processor, the computer program comprising instructions proximity-based call management.
Owner:SBC KNOWLEDGE VENTURES LP
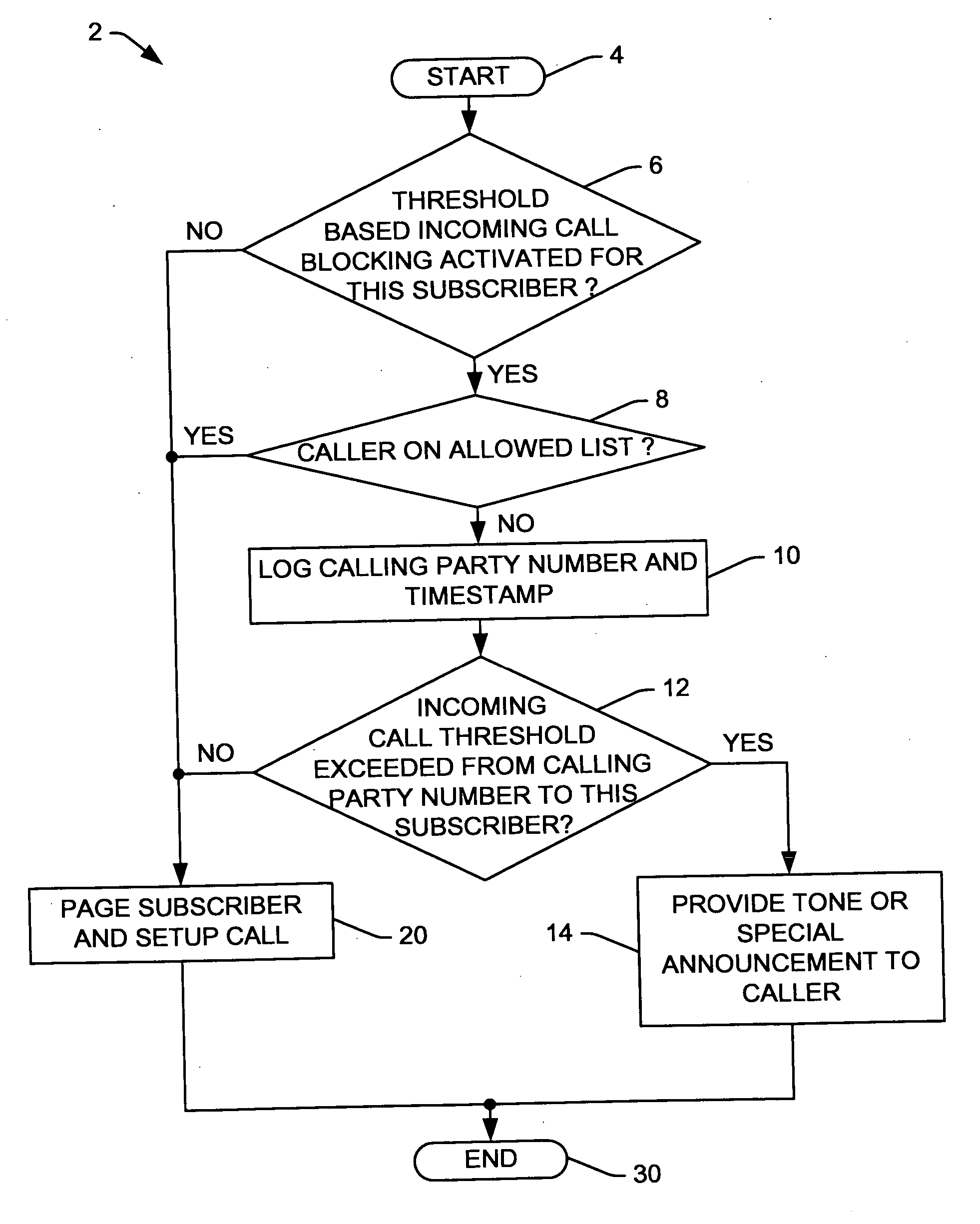
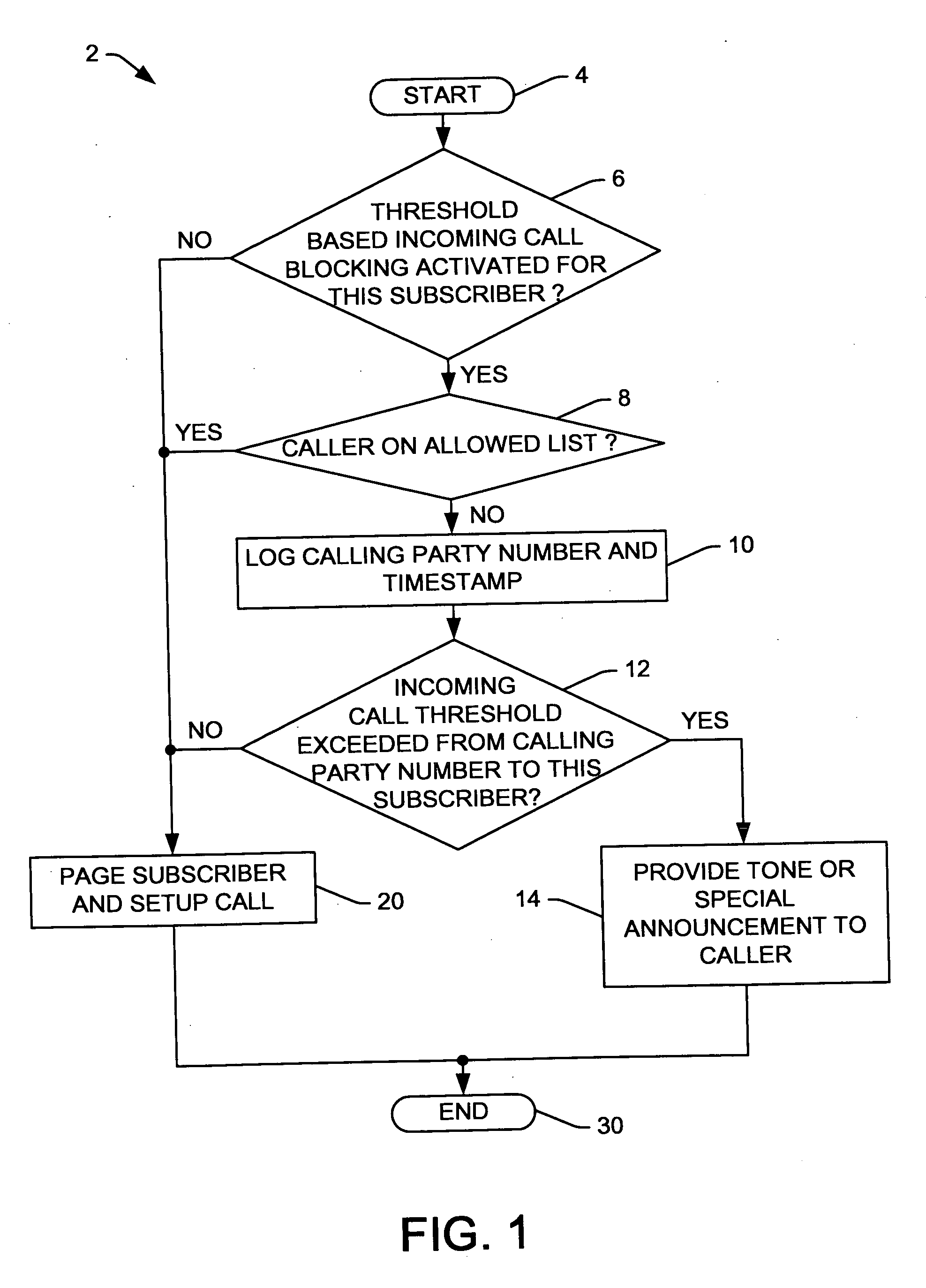
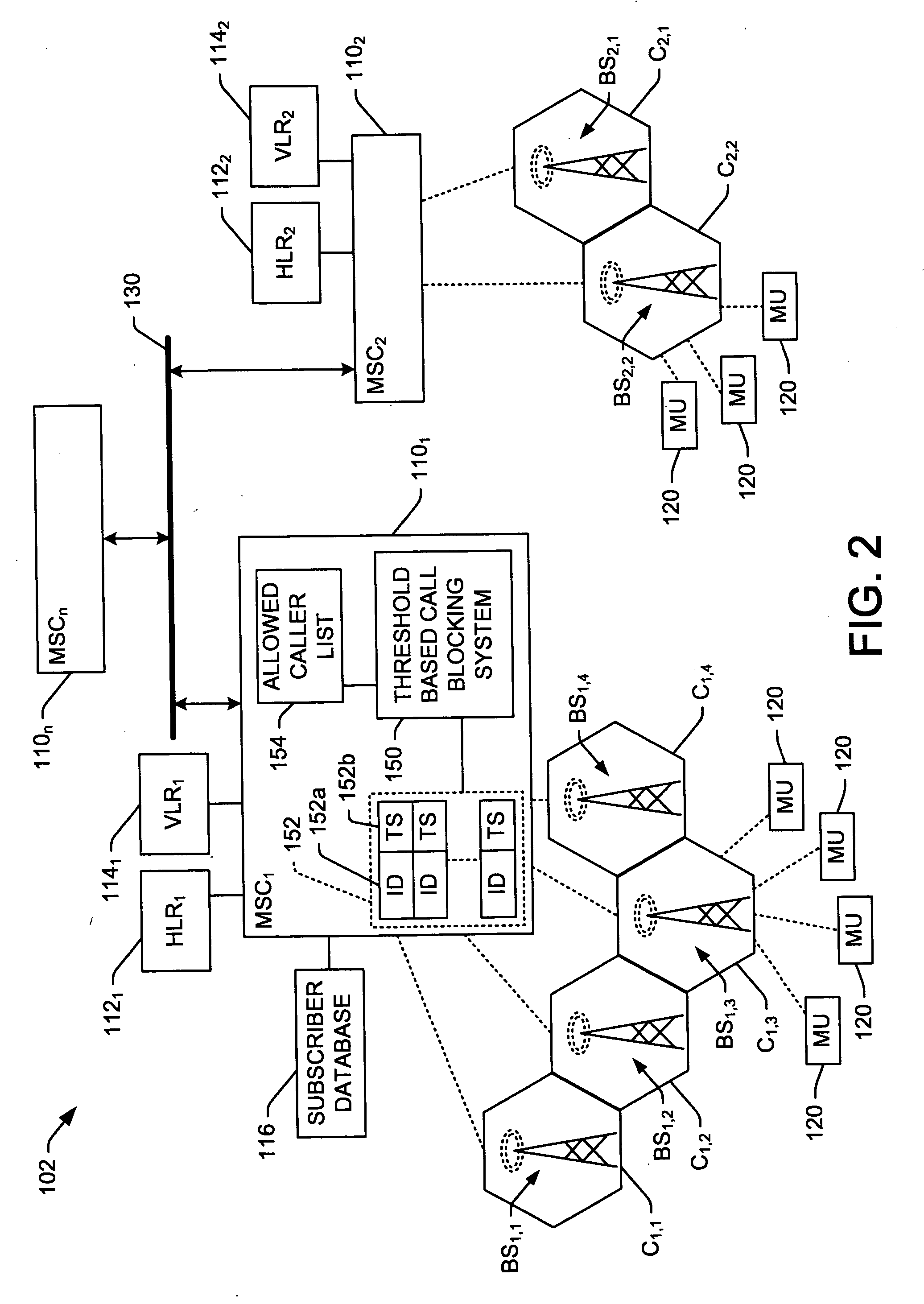
Methods and systems for selective threshold based call blocking
InactiveUS20060291641A1Easy to understandWell formedSpecial service for subscribersTelecommunicationsCommunication unit
Systems and methods are presented for blocking nuisance calls to communications devices, in which incoming calls are selectively blocked if the caller has made a threshold number of attempts to call a communications unit within a specified interval of time. The nuisance call blocking service may be selectively performed only for communications customers subscribing to the service, and the service may include the ability to designate a list of allowed callers who can make unlimited call attempts, with non-designated calling parties being limited to the threshold number of call attempts within the specified time period before being blocked.
Owner:LUCENT TECH INC
Method of sequence determination using sequence tags
Owner:ADAPTIVE BIOTECH
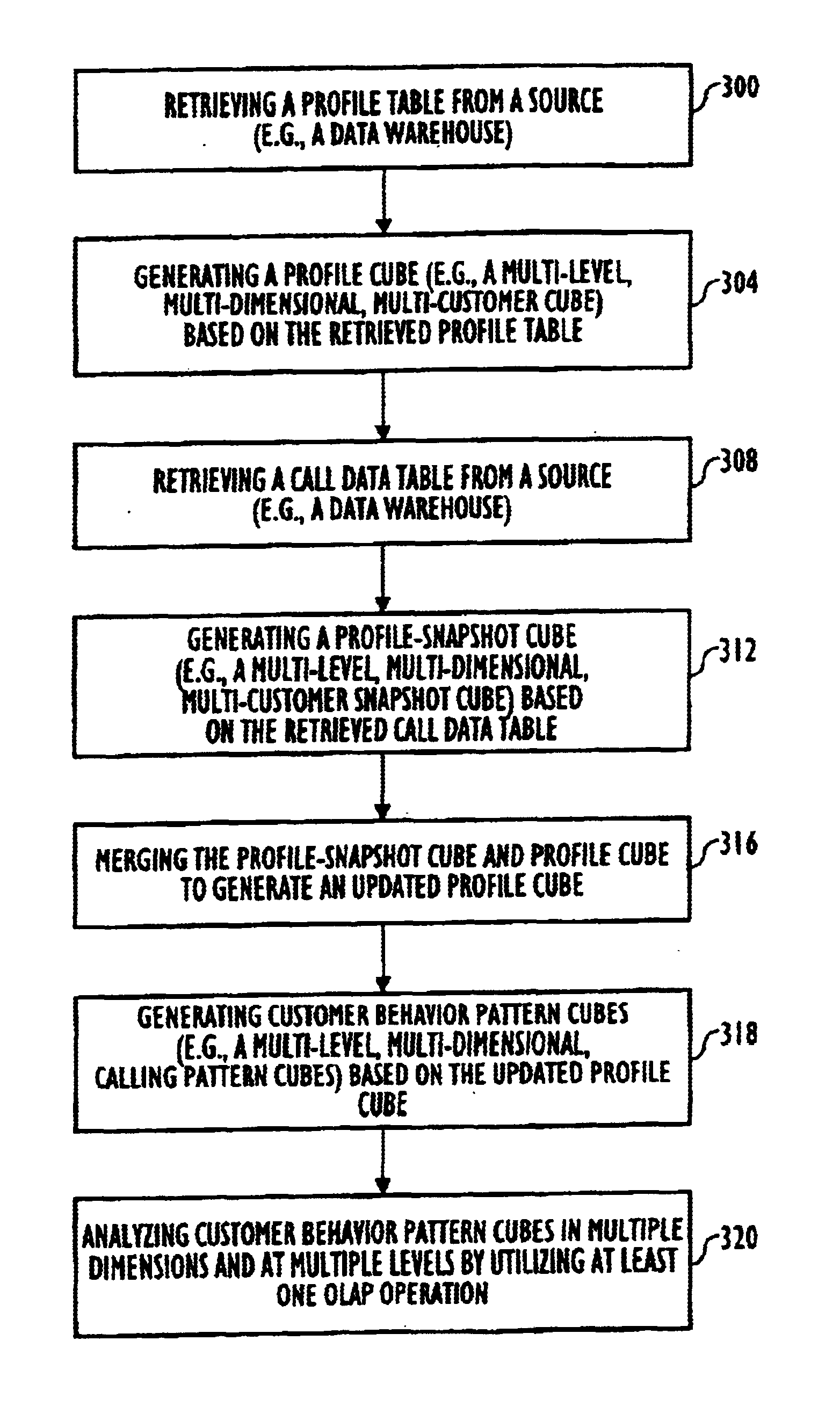
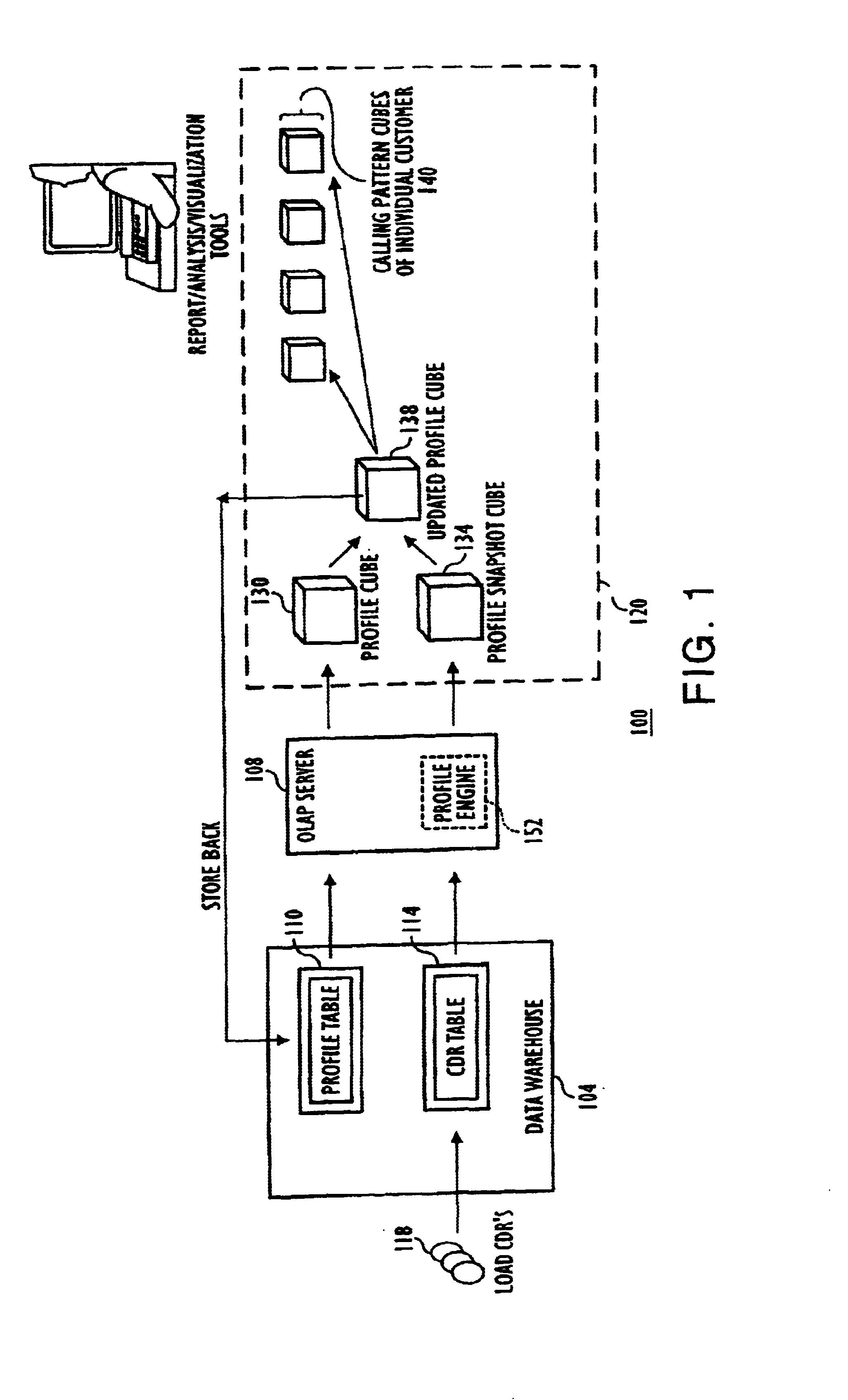
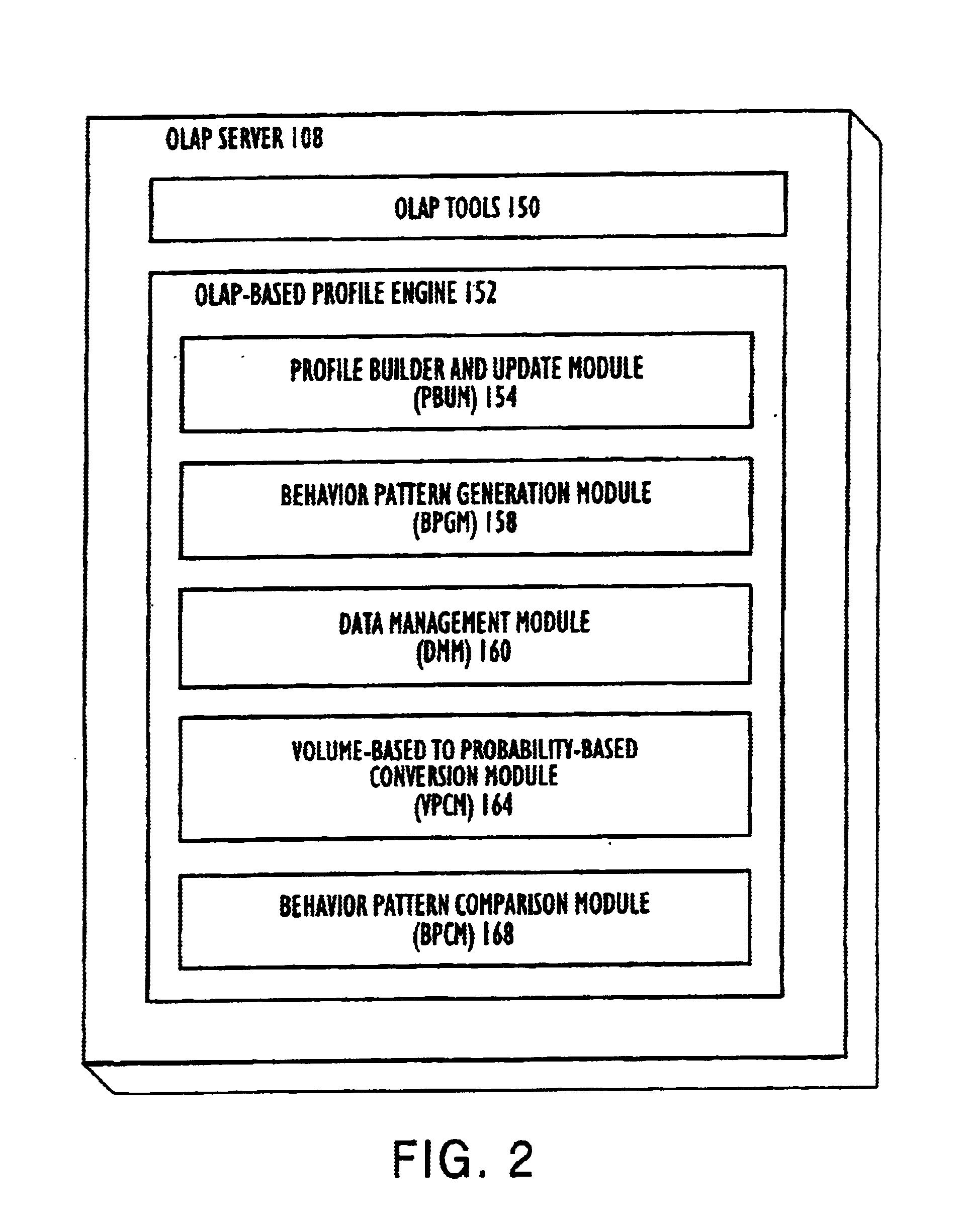
Olap-based customer behavior profiling method and system
InactiveUS6917940B1FinanceSupervisory/monitoring/testing arrangementsBehavioral analyticsBase calling
An OLAP-based method and system for profiling customer behavior that can be utilized to detect telecommunication fraud. First, call records are received. Next, a calling profile cube (e.g., a multi-customer profile cube) is generated based on the call records. A volume-based calling pattern cube (e.g., a calling pattern cube for each individual customer) is then generated based on the multi-customer profile cube. The volume-based calling pattern cube is then compared with known fraudulent volume-based calling patterns. If the similarities generated by the comparison reaches or exceeds a predetermined threshold, then the particular caller with the calling pattern being analyzed is considered suspicious. In this manner, suspicious calling activity can be detected, and appropriate remedial actions, such as further investigation or the cancellation of telephone services, can be taken.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
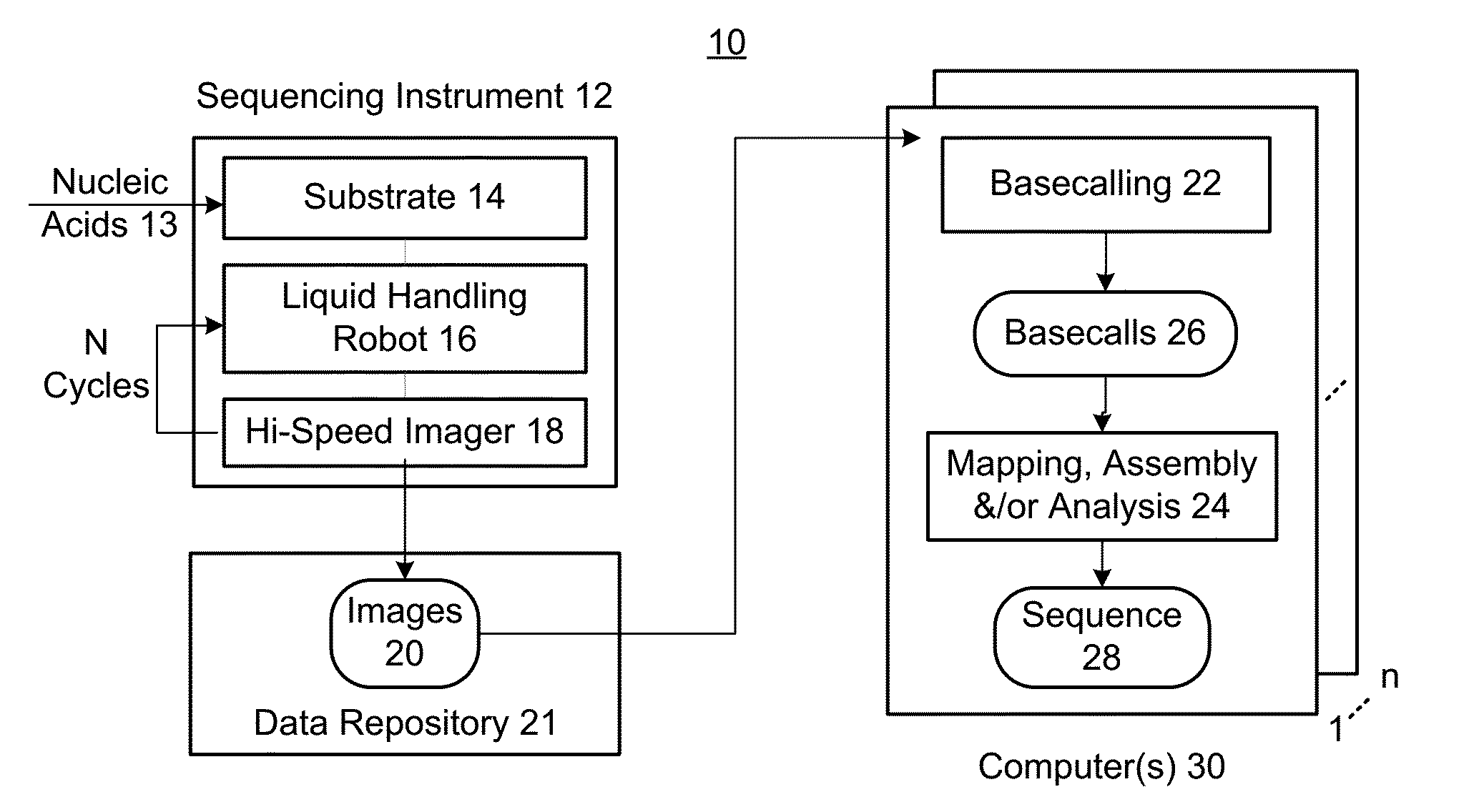
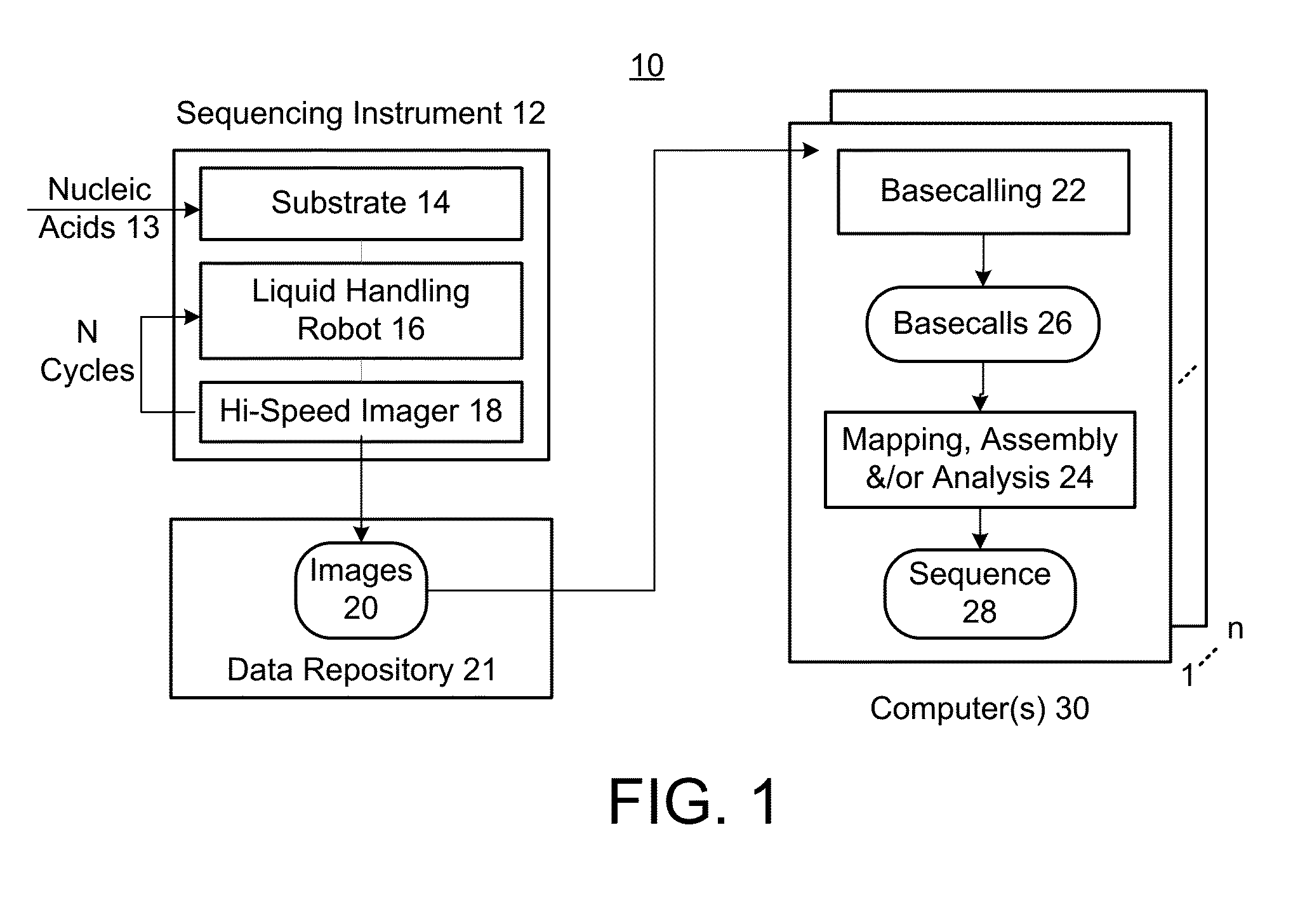
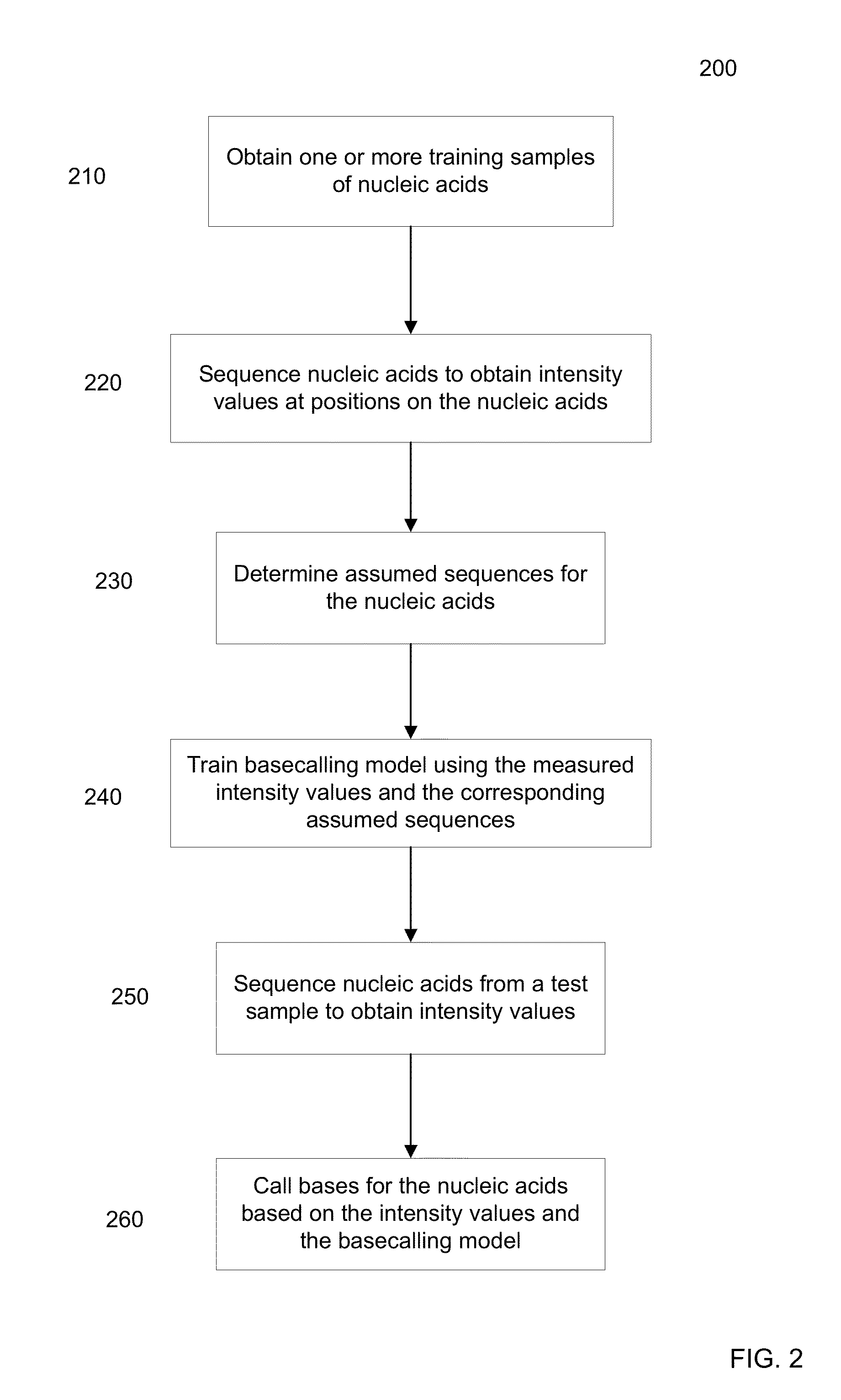
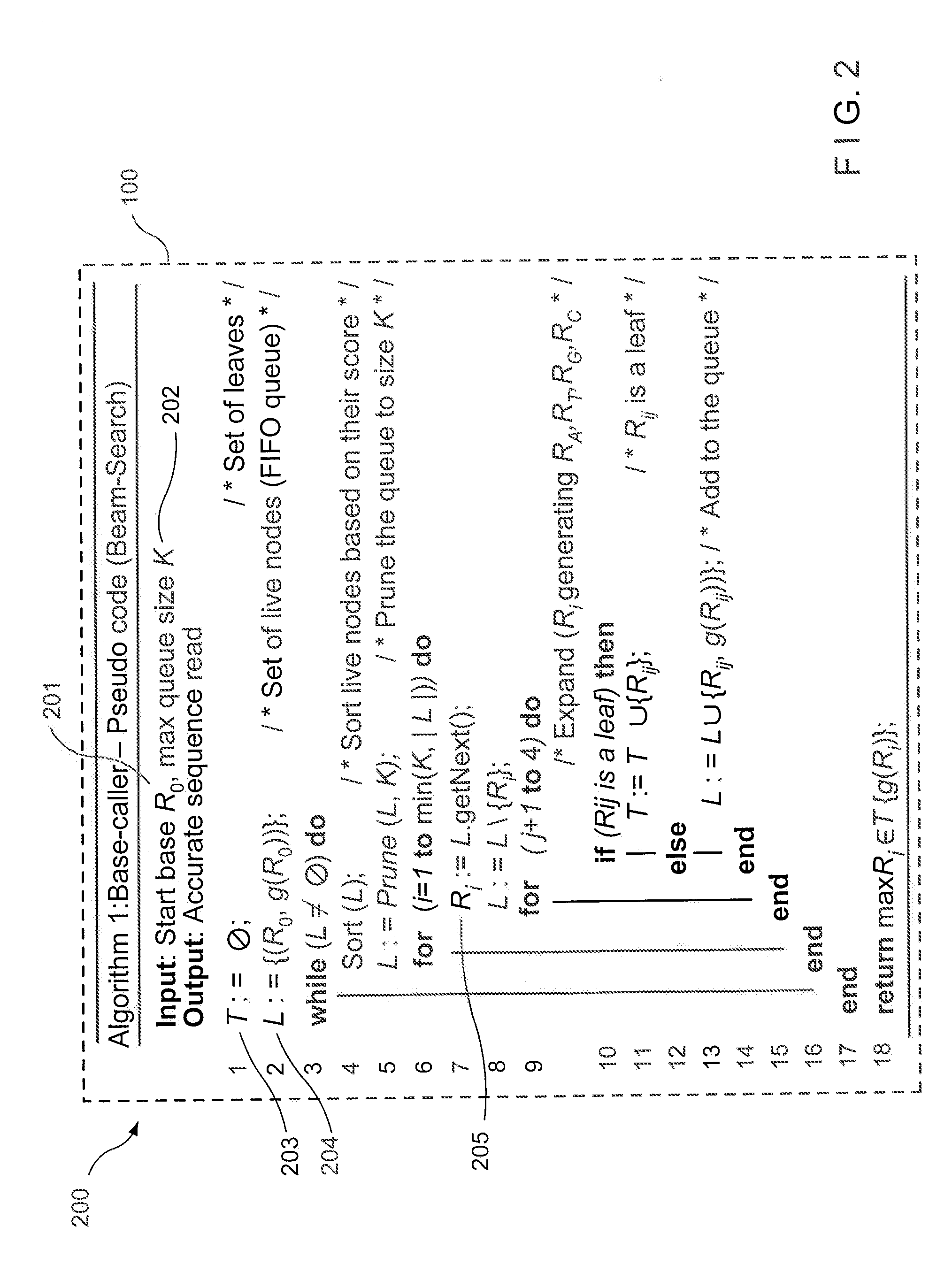
Basecaller for DNA sequencing using machine learning
ActiveUS20150169824A1Reduce contributionBiostatisticsBiological testingBase callingArtificial intelligence
Methods, systems, and apparatuses are provided for creating and using a machine-leaning model to call a base at a position of a nucleic acid based on intensity values measured during a production sequencing run. The model can be trained using training data from training sequencing runs performed earlier. The model is trained using intensity values and assumed sequences that are determined as the correct output. The training data can be filtered to improve accuracy. The training data can be selected in a specific manner to be representative of the type of organism to be sequenced. The model can be trained to use intensity signals from multiple cycles and from neighboring nucleic acids to improve accuracy in the base calls.
Owner:MGI TECH CO LTD
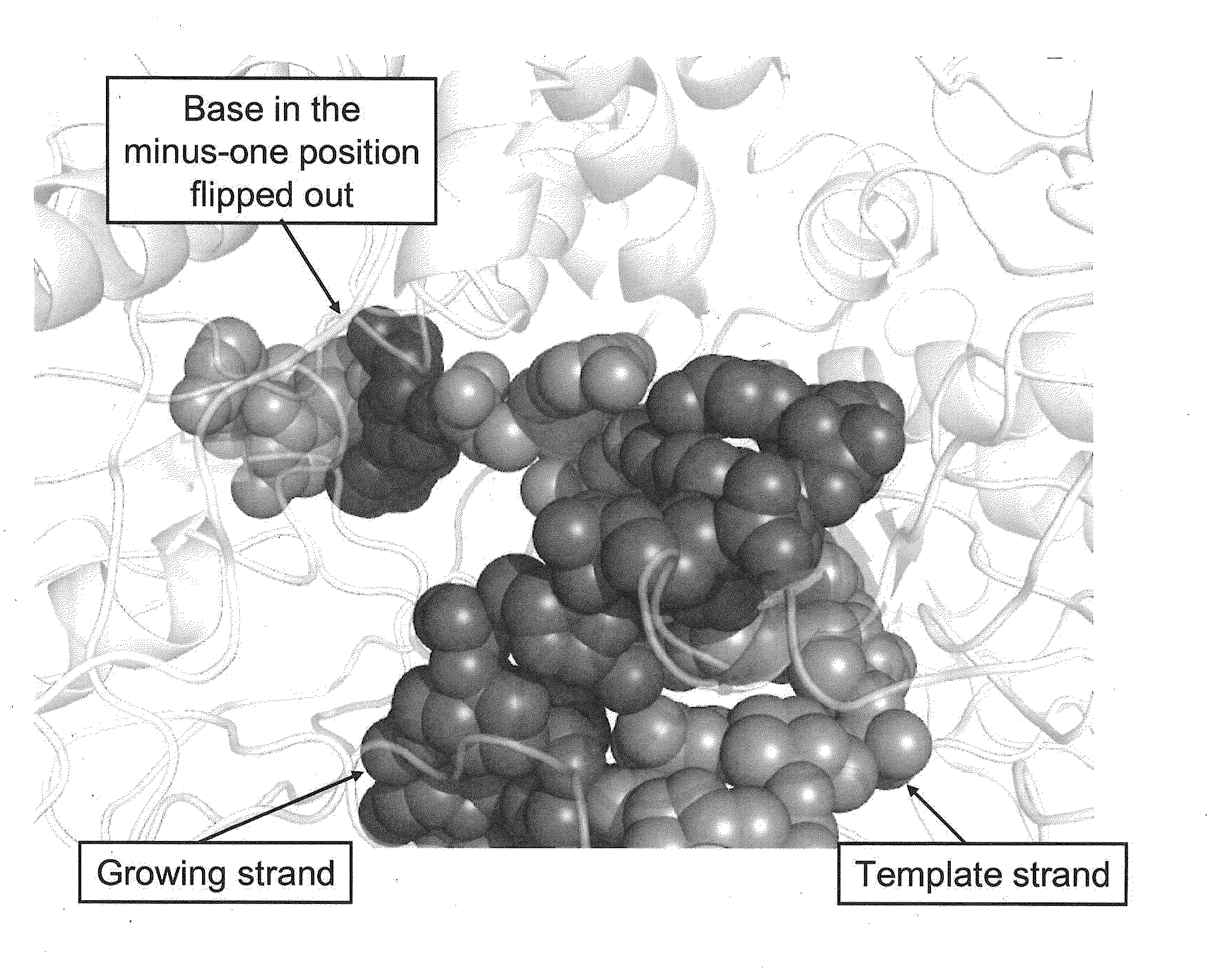
Sequencing methods using enzyme conformation
Systems and methods are provided for single-molecule sequencing of template nucleic acids in which the signal from a label attached to a polymerase enzyme is used to monitor conformational changes in the polymerase which occur while labeled nucleotides or nucleotide analogs are added to a growing nucleic acid chain which is complementary to the template nucleic acid. The signal indicative of the conformational state of the enzyme is used to determine with higher confidence when true nucleotide or nucleotide analog incorporation events occur, allowing for the improved quality of base calls and sequence determination.
Owner:PACIFIC BIOSCIENCES
Method, computer-accessible medium and system for base-calling and alignment
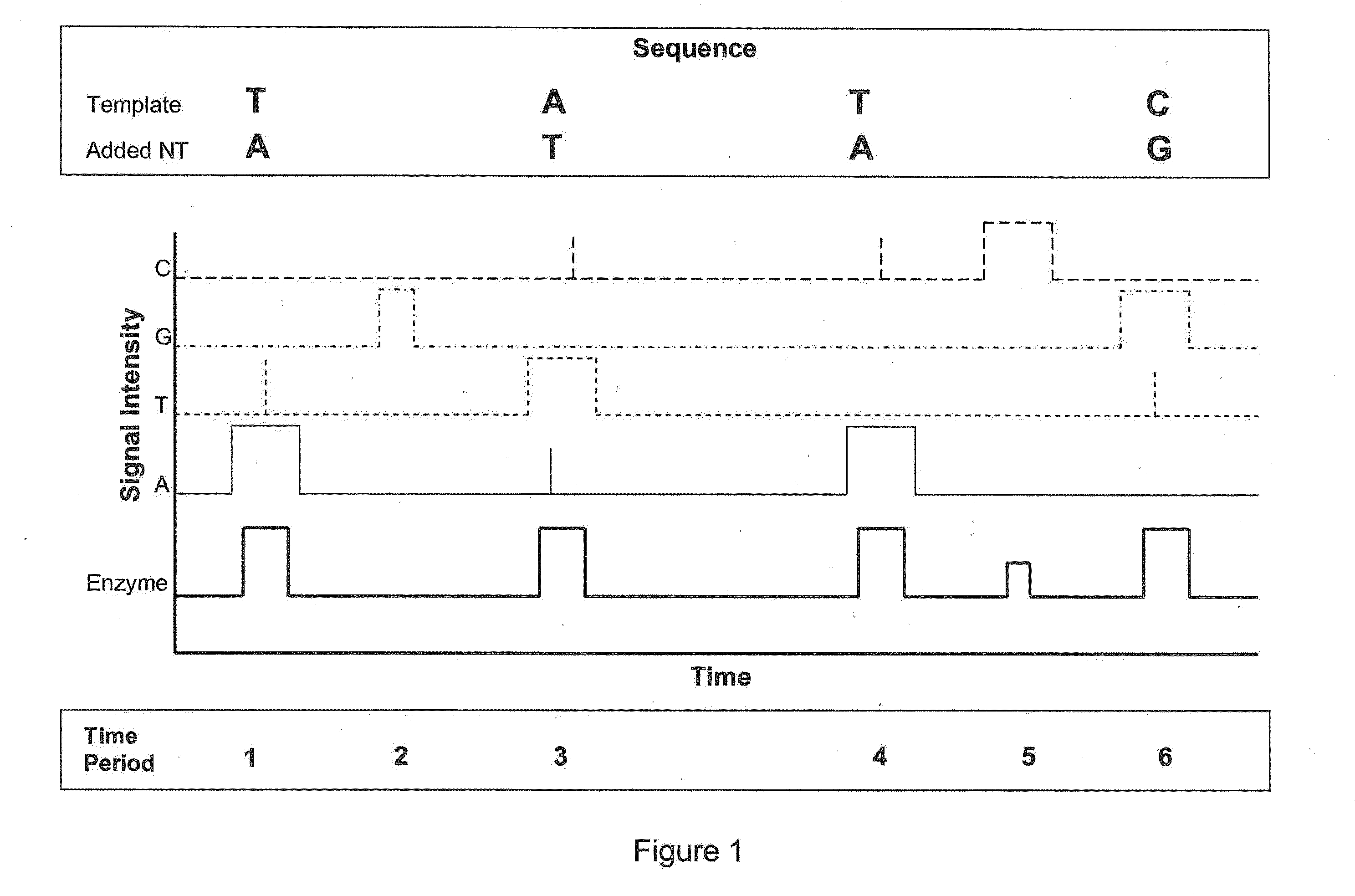
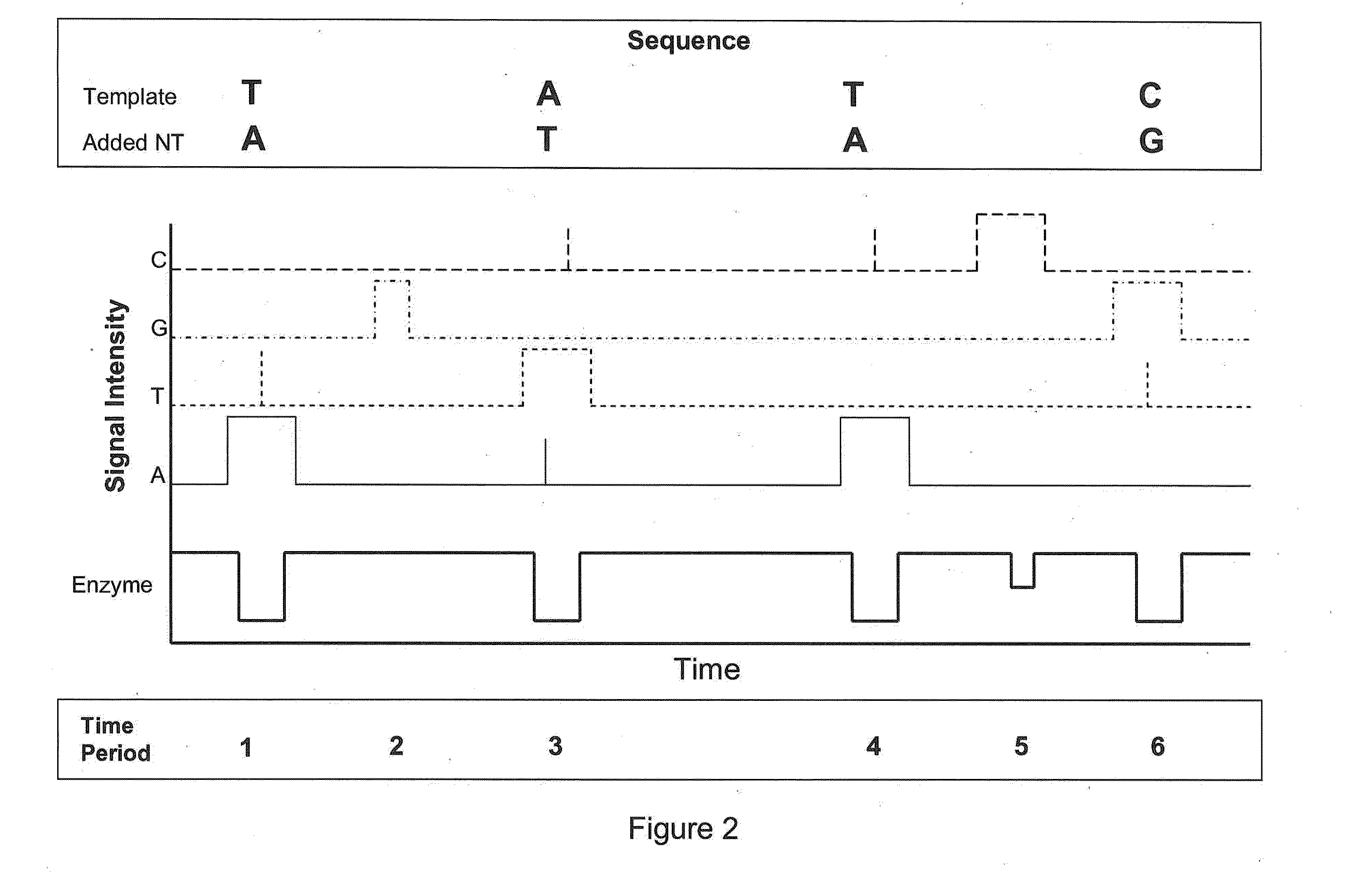
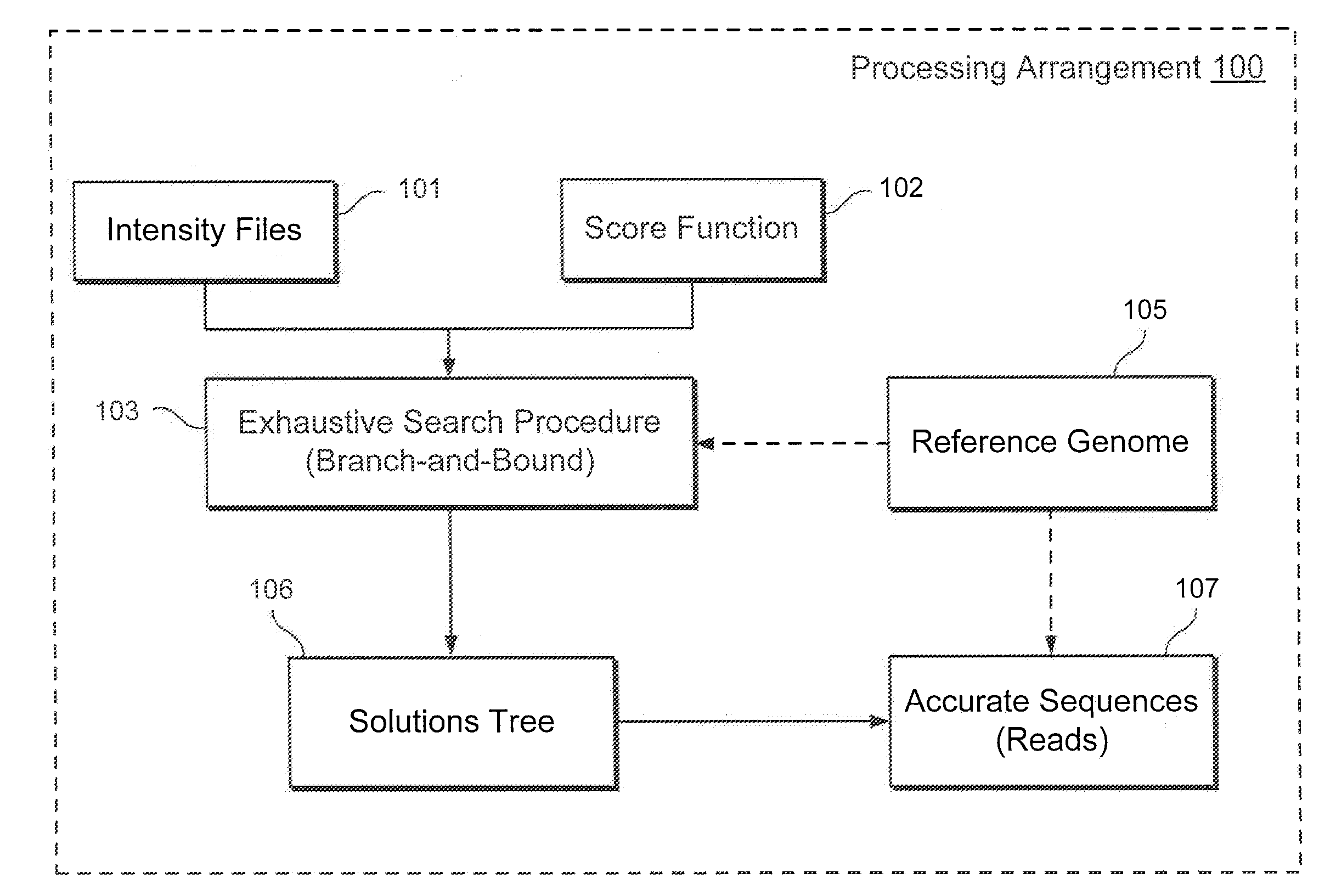
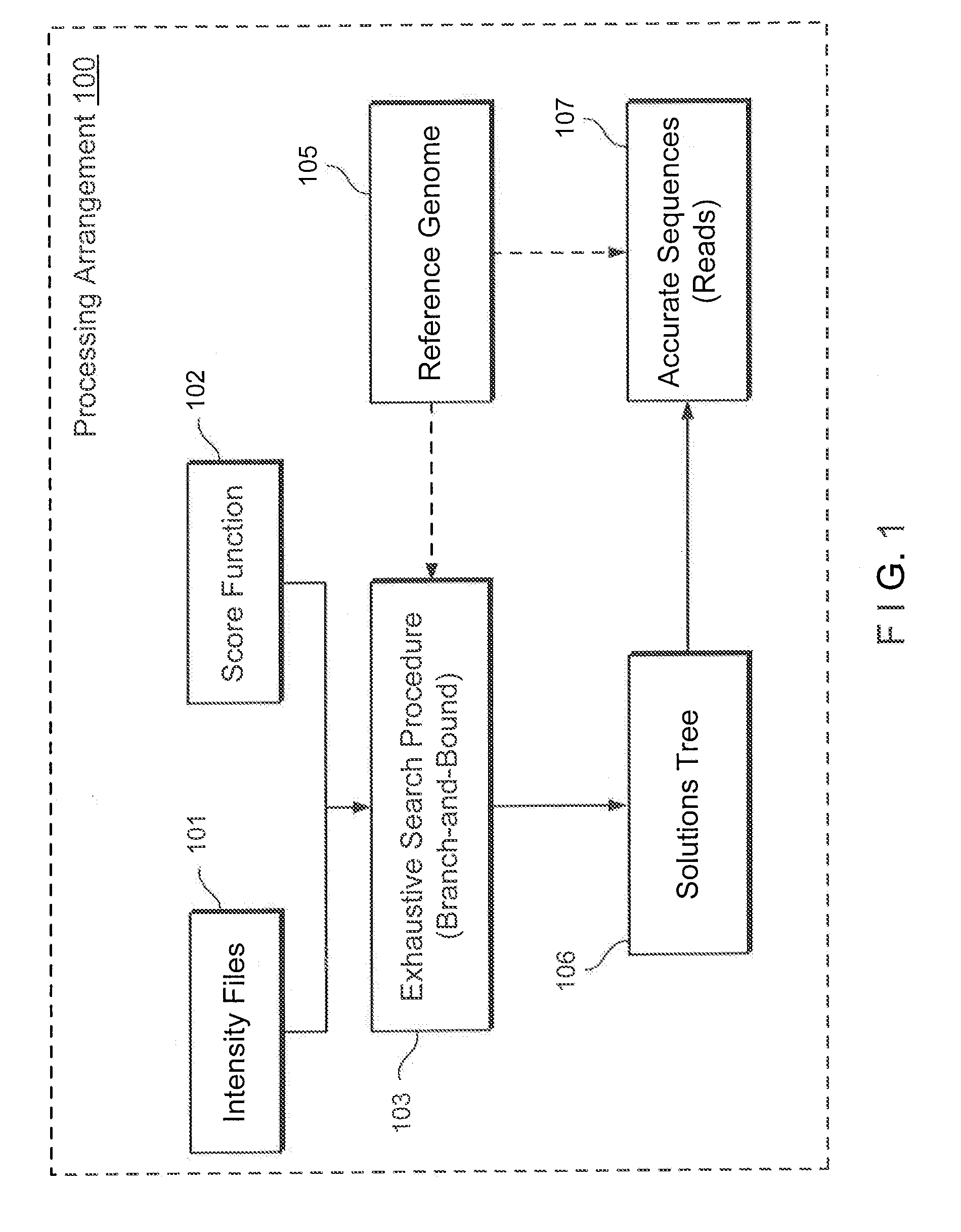
Exemplary methods, procedures, computer-accessible medium, and systems for base-calling, aligning and polymorphism detection and analysis using raw output from a sequencing platform can be provided. A set of raw outputs can be used to detect polymorphisms in an individual by obtaining a plurality of sequence read data from one or more technologies (e.g., using sequencing-by-synthesis, sequencing-by-ligation, sequencing-by-hybridization, Sanger sequencing, etc.). For example, provided herein are exemplary methods, procedures, computer-accessible medium and systems, which can include and / or be configured for obtaining raw output from a sequencing platform configured to be used for reading fragment(s) of genomes, obtaining reference sequences for the genomes obtained independently from the raw output, and generating a base-call interpretation and / or alignment using the raw output and the reference sequences. For example, a score function can be determined based on information associated with the sequencing platform that can be used to analyze polymorphisms based on the base-call interpretation and / or alignment.
Owner:NEW YORK UNIV
History-based call stack construction
InactiveUS20080209406A1Error detection/correctionSpecific program execution arrangementsCall stackDefined Procedure
In a computing system environment, methods and apparatus relate to constructing a call stack for a software program based upon a comprehensive recording of an execution history of the software program. Upon defining procedure calls and returns in the execution history, a call stack is constructed for the procedure calls having no corresponding returns, but without reading or otherwise examining allocated stack memory or registers, such as return addresses. In this manner, an accurate call stack can be constructed despite stack memory or registers being erased or corrupted or despite various compiler optimizations eliminating convenience or otherwise complicating the construction. Nuances for defining procedure calls and returns as well as stack pointer values for same are also contemplated. Still other embodiments relate to stand-alone computer program products (on computer-readable media or as a download, or other) or those working in conjunction with other programs.
Owner:RPX CORP
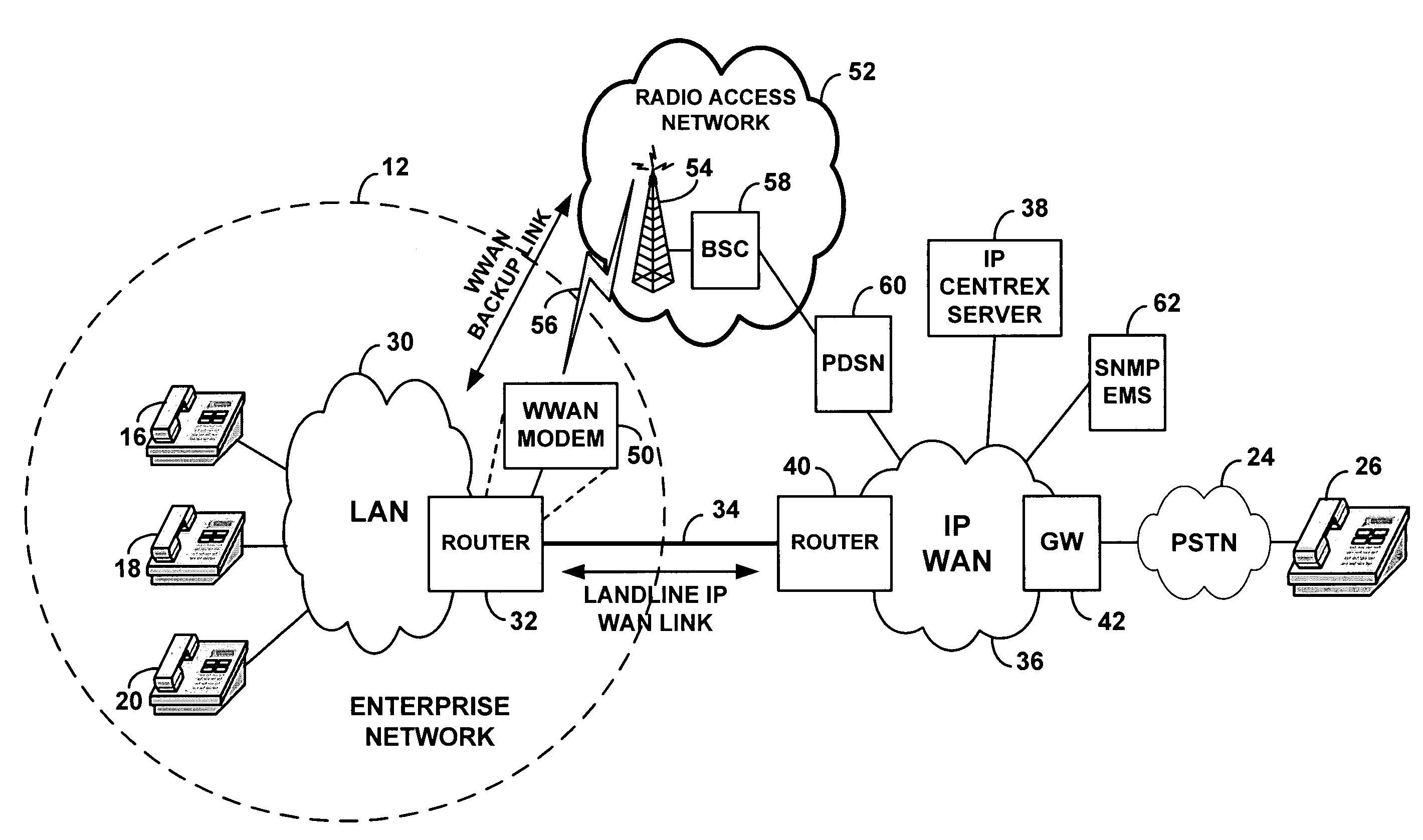
Method and system to support internal calling upon loss of connection with IP Centrex server
A method and system for facilitating calling within an enterprise network upon failure of a landline connection between the enterprise network and an outside call server such as an IP Centrex server. Upon failure of the landline connection, an enterprise router switches over to a backup wireless packet-data link, such as a 3G cellular link for instance. Thus, packet-based call signaling can continue to flow between the enterprise network and the call server so as to continue setting up inside calls between enterprise telephone stations. The backup wireless packet-data link can also be used to carry a limited extent of outside calls, such as emergency calls for instance.
Owner:SPRING SPECTRUM LP
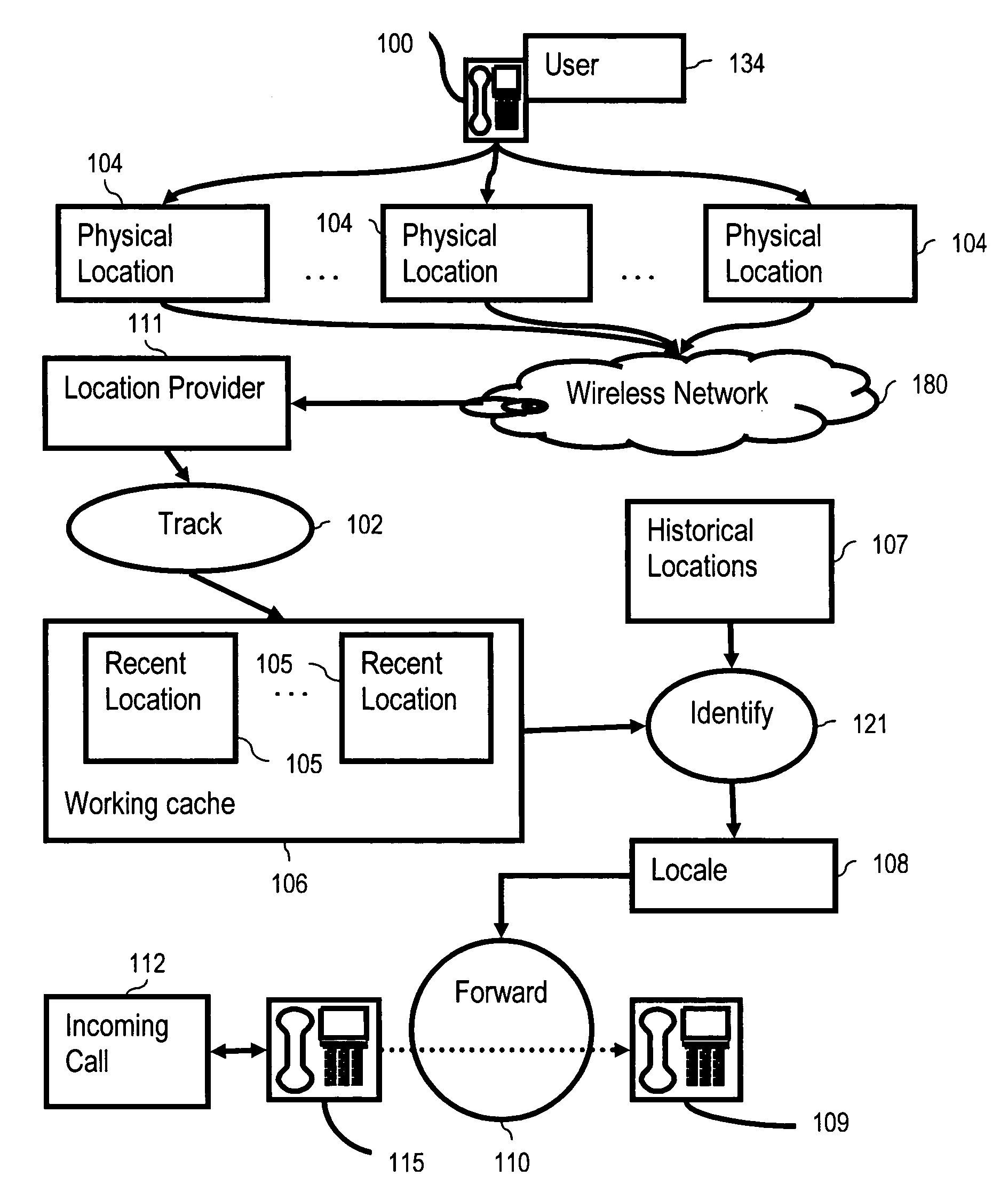
Locale based call forwarding
InactiveUS7082192B2Special service for subscribersCommmunication supplementary servicesTelecommunications networkCall forwarding
Call forwarding a telephone number, including tracking recent locations of a user with the user's mobile personal communications device and a wireless telecommunications network; identifying a locale for the user in dependence upon the recent locations and upon historical location records for the user; and forwarding a telephone number in dependence upon the locale. In many embodiments, identifying a locale further comprises comparing historical location records and recent locations, wherein the historical location records are related to the locale through a locale identification field used as a foreign key.
Owner:IBM CORP
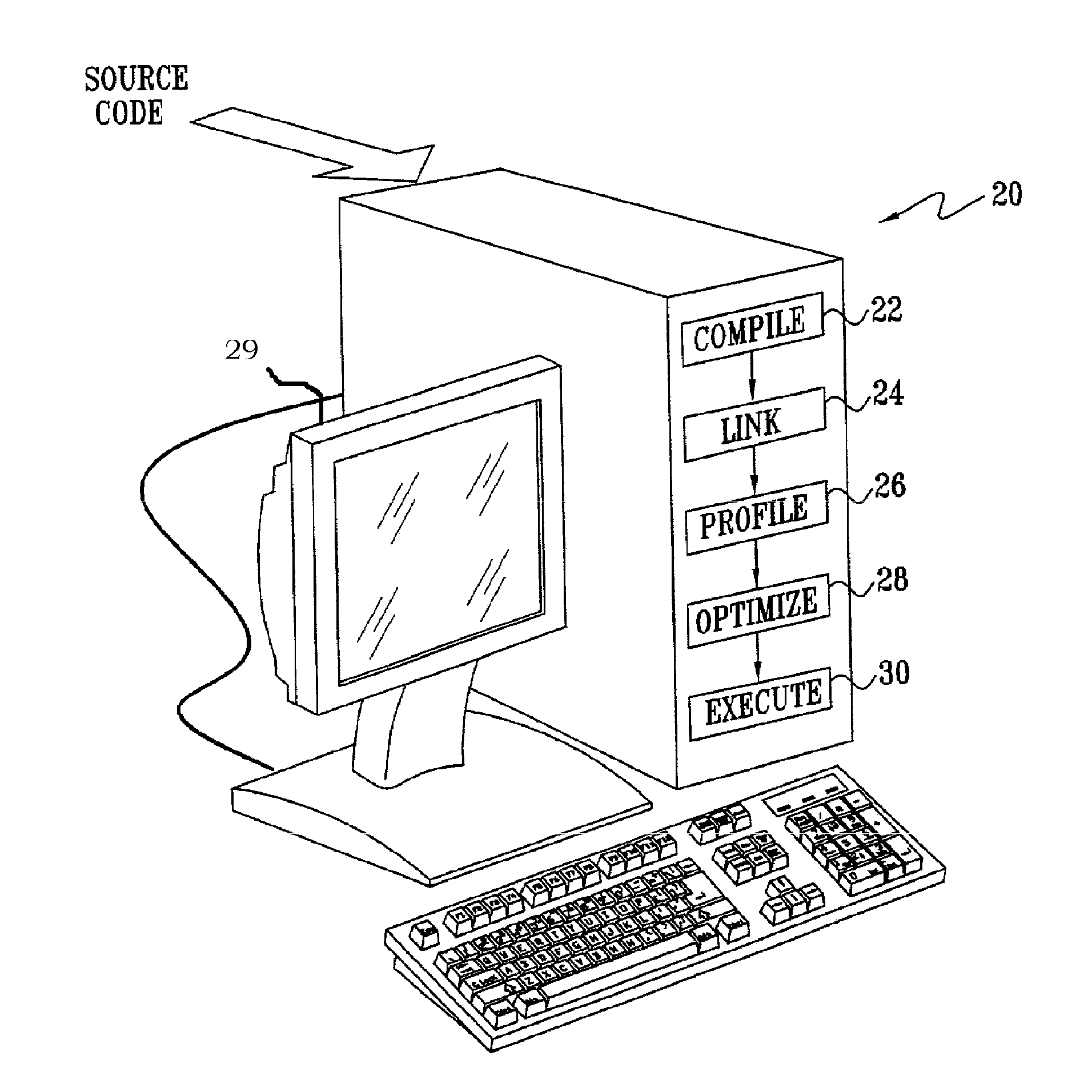
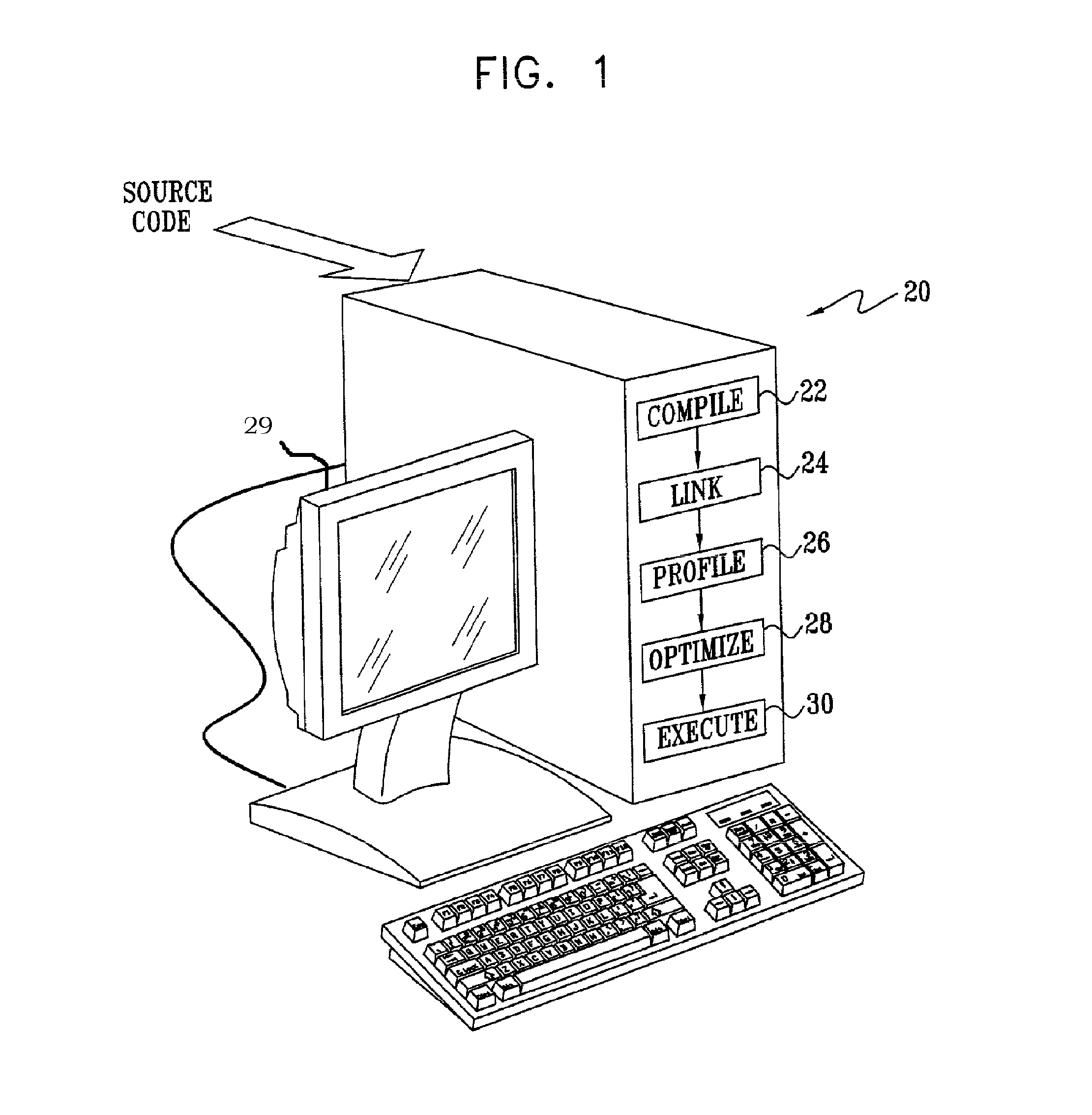
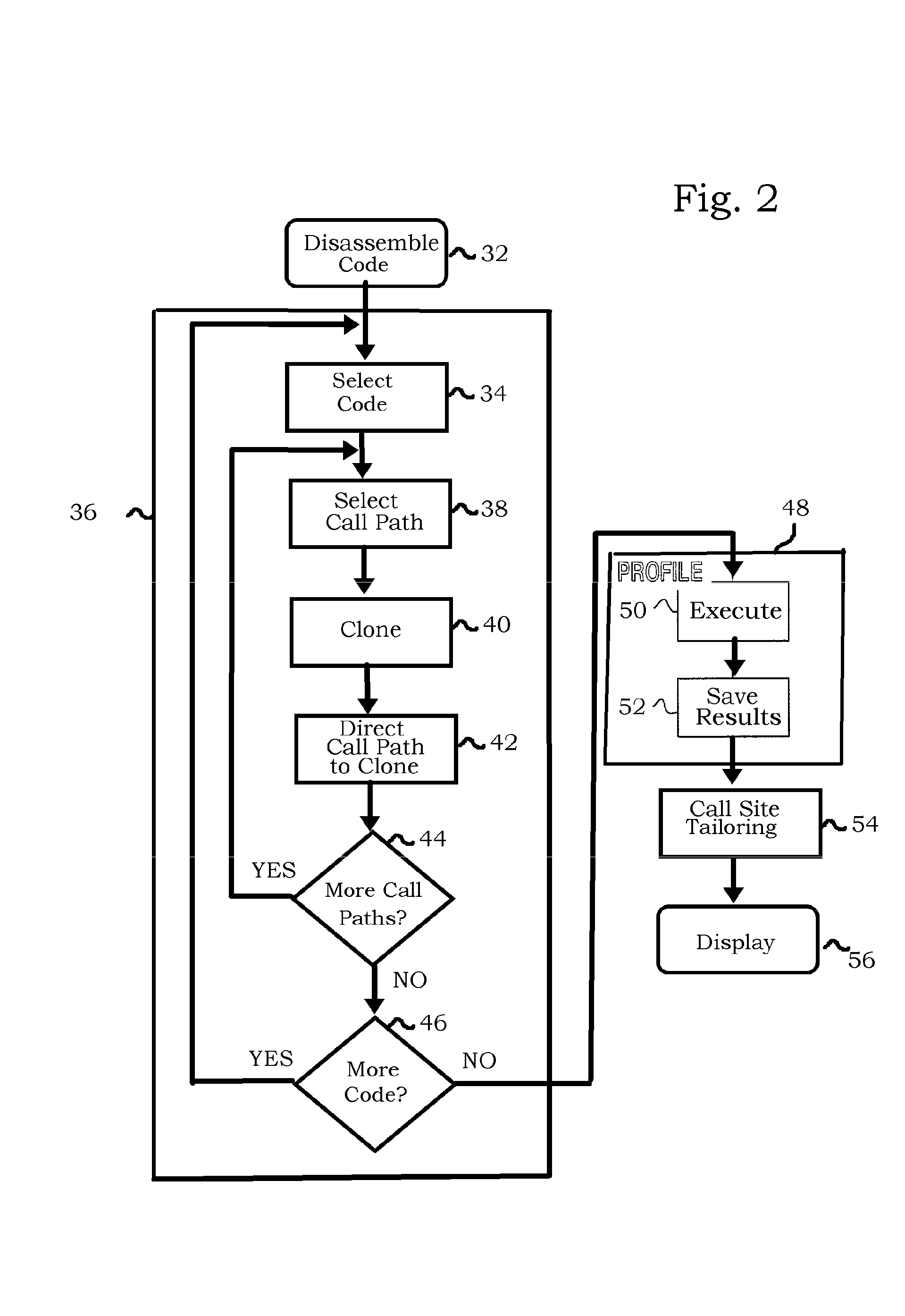
Method for Enabling Profile-Based Call Site Tailor-ing Using Profile Gathering of Cloned Functions
Methods and systems for computer program optimization utilize function cloning in program code, such as post-linked code. Each function call is directed to a different cloned version of the called function. Conventional profiling methods such as hardware event sampling, basic block profiling, and edge profiling may then be applied to the modified program code to obtain call path-based, clone-specific profile data. The profile data can be further exploited to optimize the program code.
Owner:IBM CORP
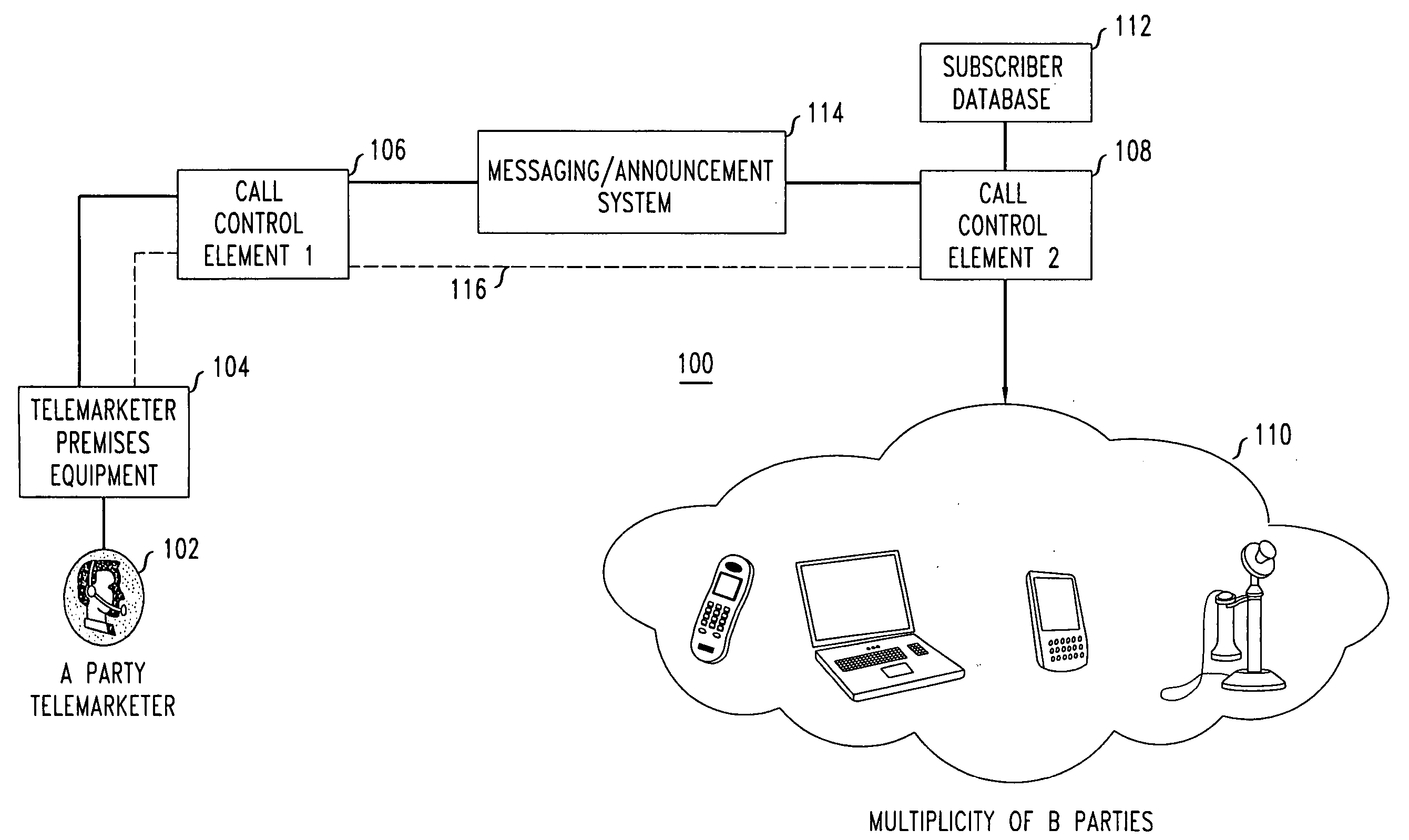
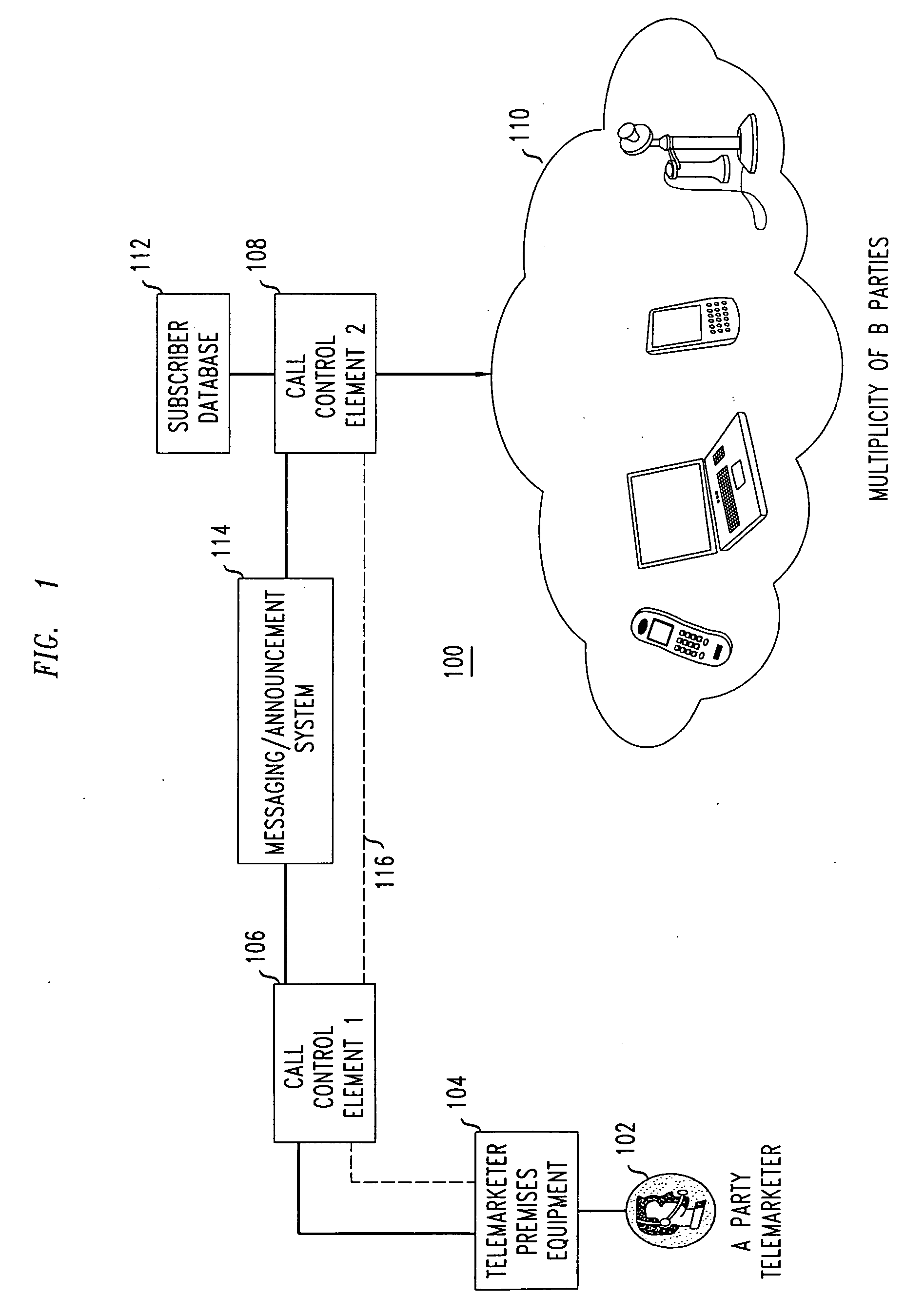
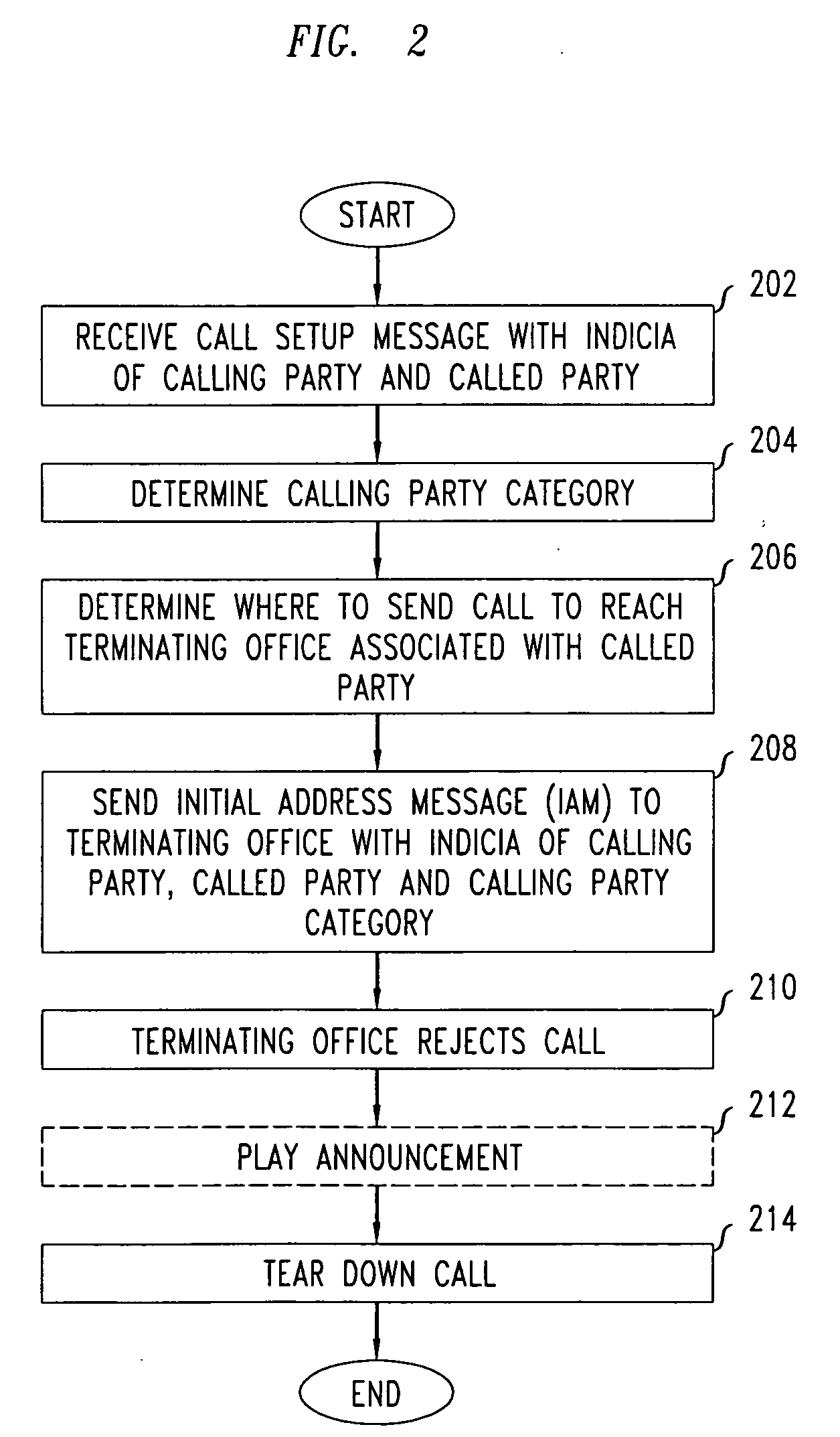
Network support for blocking calls based on calling party category
Network support for blocking certain categories of calls, such as telemarketer calls, is disclosed. One or more network-based call control elements such as may reside within a mobile switching center or central office switch, effects blocking of calls based at least in part on the calling party category. A first call control element receives indicia of a prospective call and determines the calling party category. The first call control element sends a message including indicia of the calling party category to a second call control element, which blocks the prospective call based at least in part on the calling party category. Blocking may occur at the second call control element substantially independently (i.e., without regard to called party preferences) or after querying a subscriber database to determine called party preferences.
Owner:LUCENT TECH INC
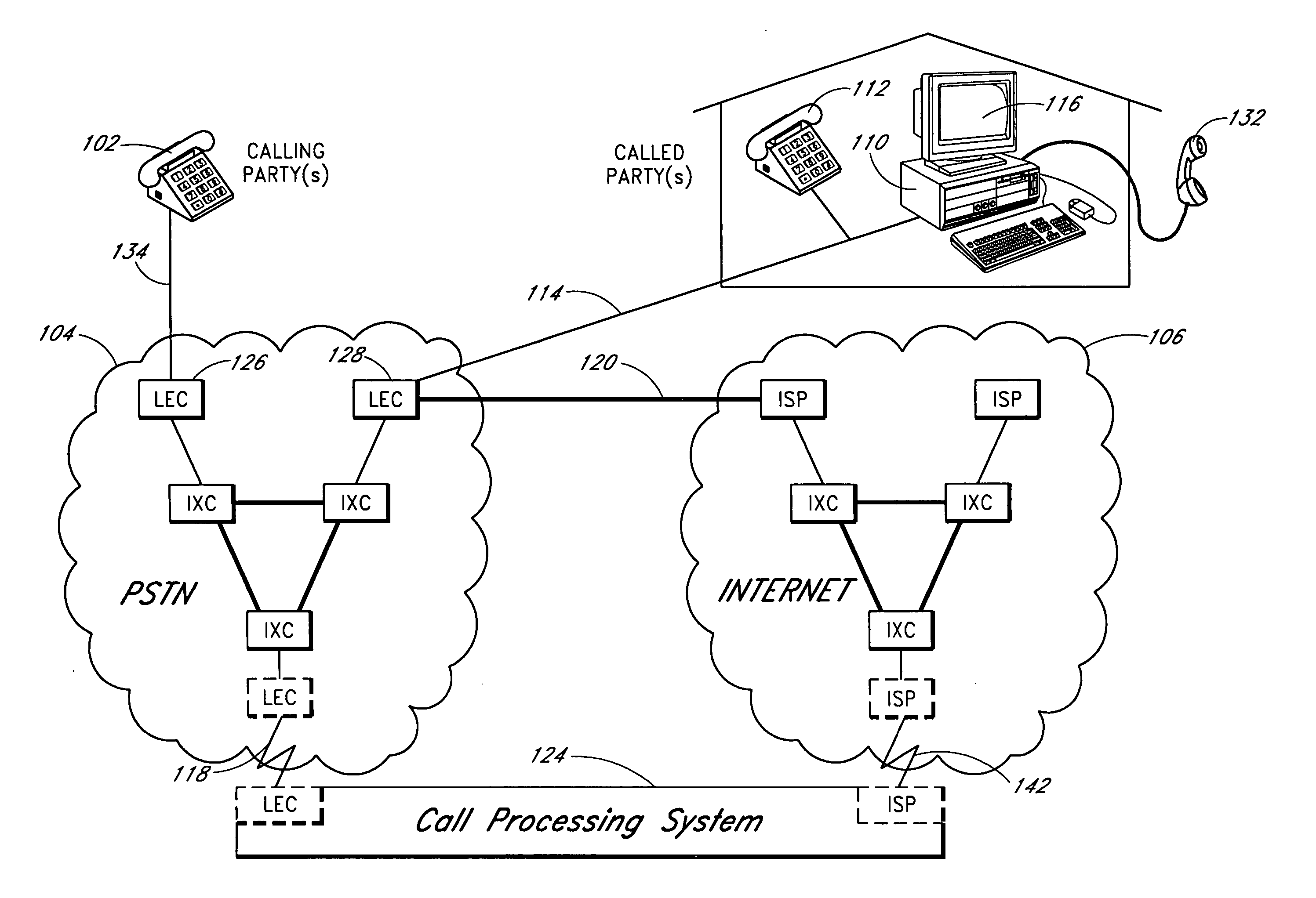
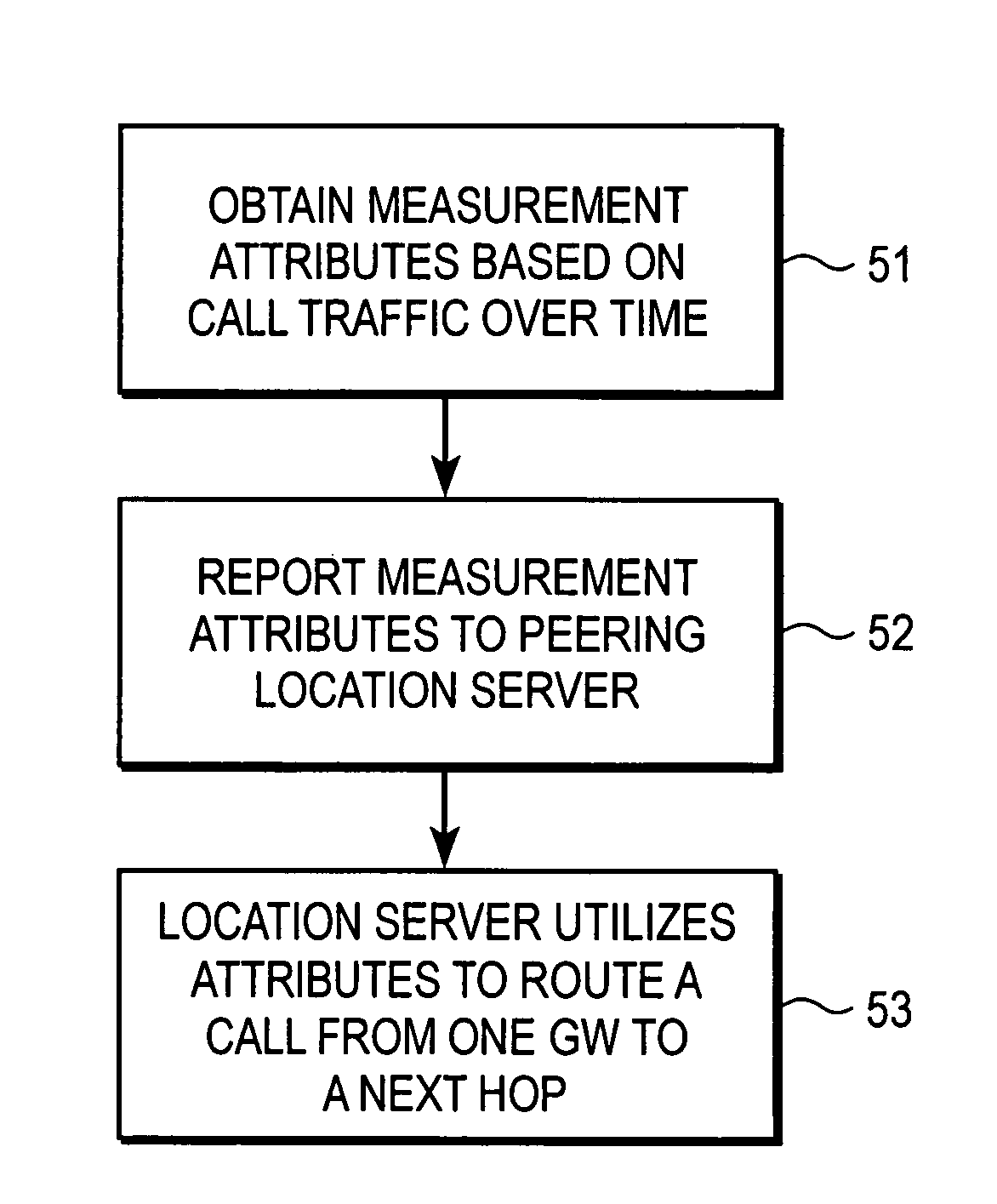
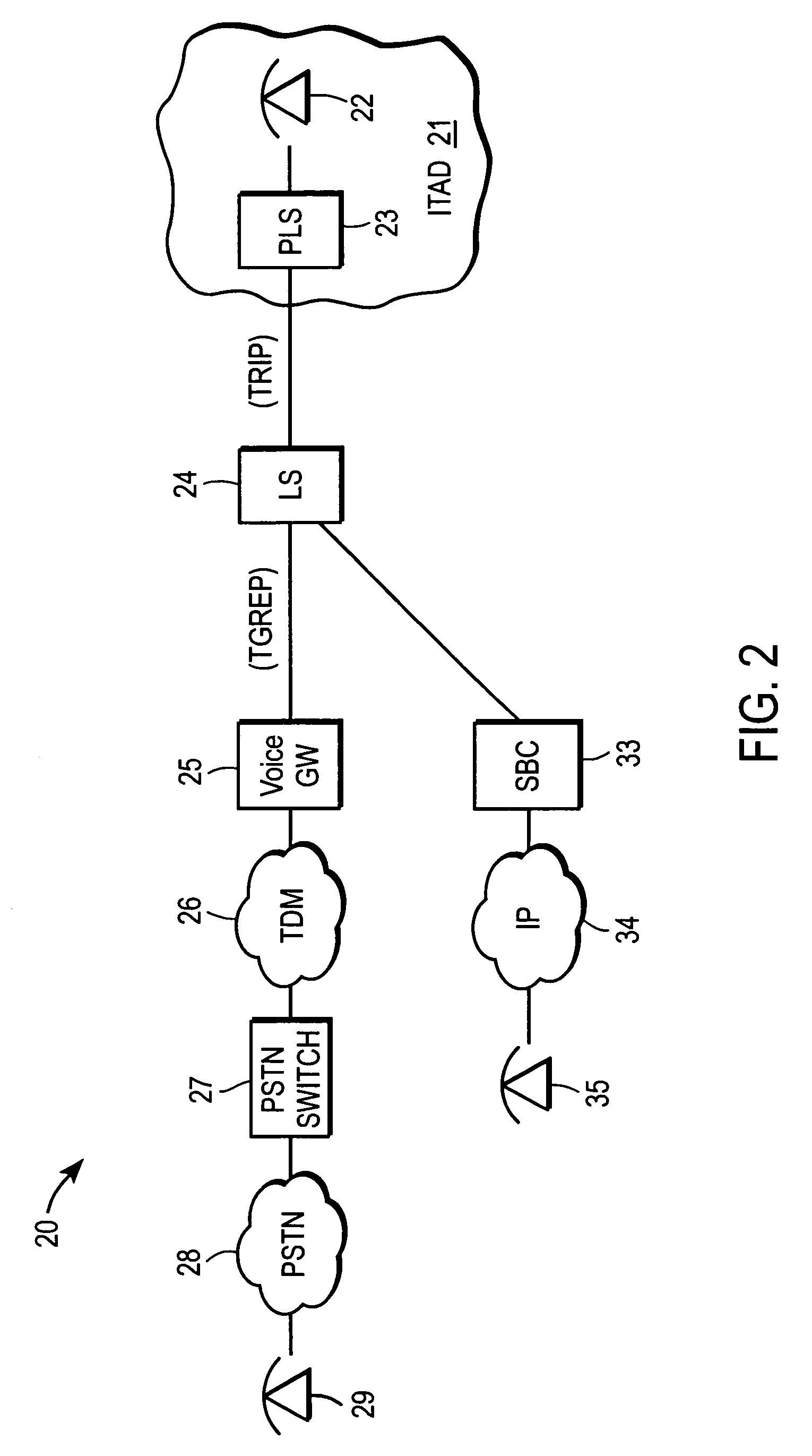
Routing protocol with packet network attributes for improved route selection
A node for routing of calls in a network has an interface coupled to the network and at least one processor operable to route a packet-based call to a telephony destination in accordance with a protocol that includes a set of attributes that describe packet-network routing characteristics of one or more Internet Protocol (IP)-IP gateway devices in the network. The attributes are used by the at least one processor to specify a call route through an IP-IP gateway device for the packet-based call. The set of attributes include a first attribute that identifies a total administratively provisioned bandwidth capacity available on a given call route to accommodate application traffic, and a second attribute that identifies a current bandwidth that is available on the given call route to accommodate the application traffic at a given point in time. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72 (b).
Owner:CISCO TECH INC
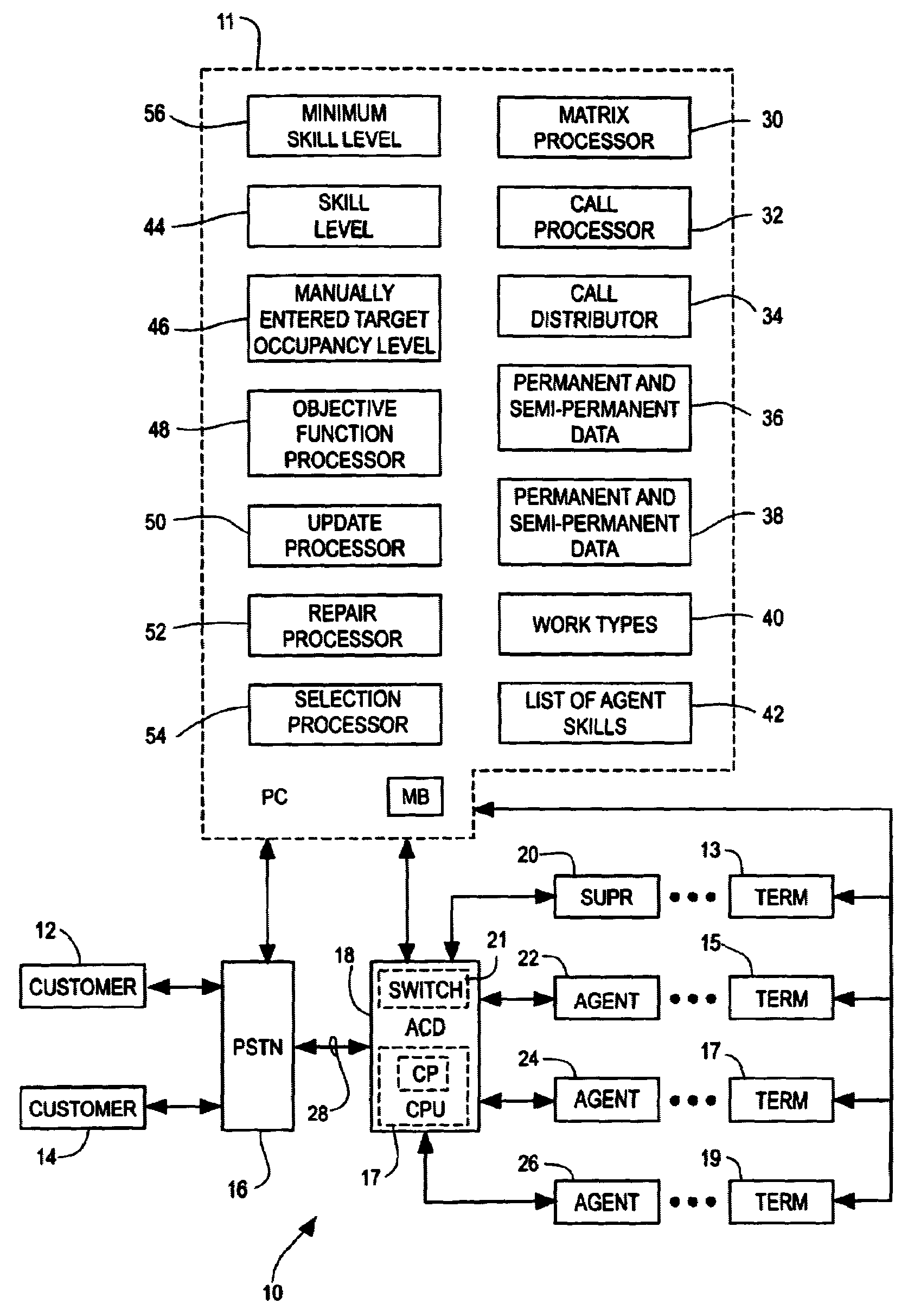
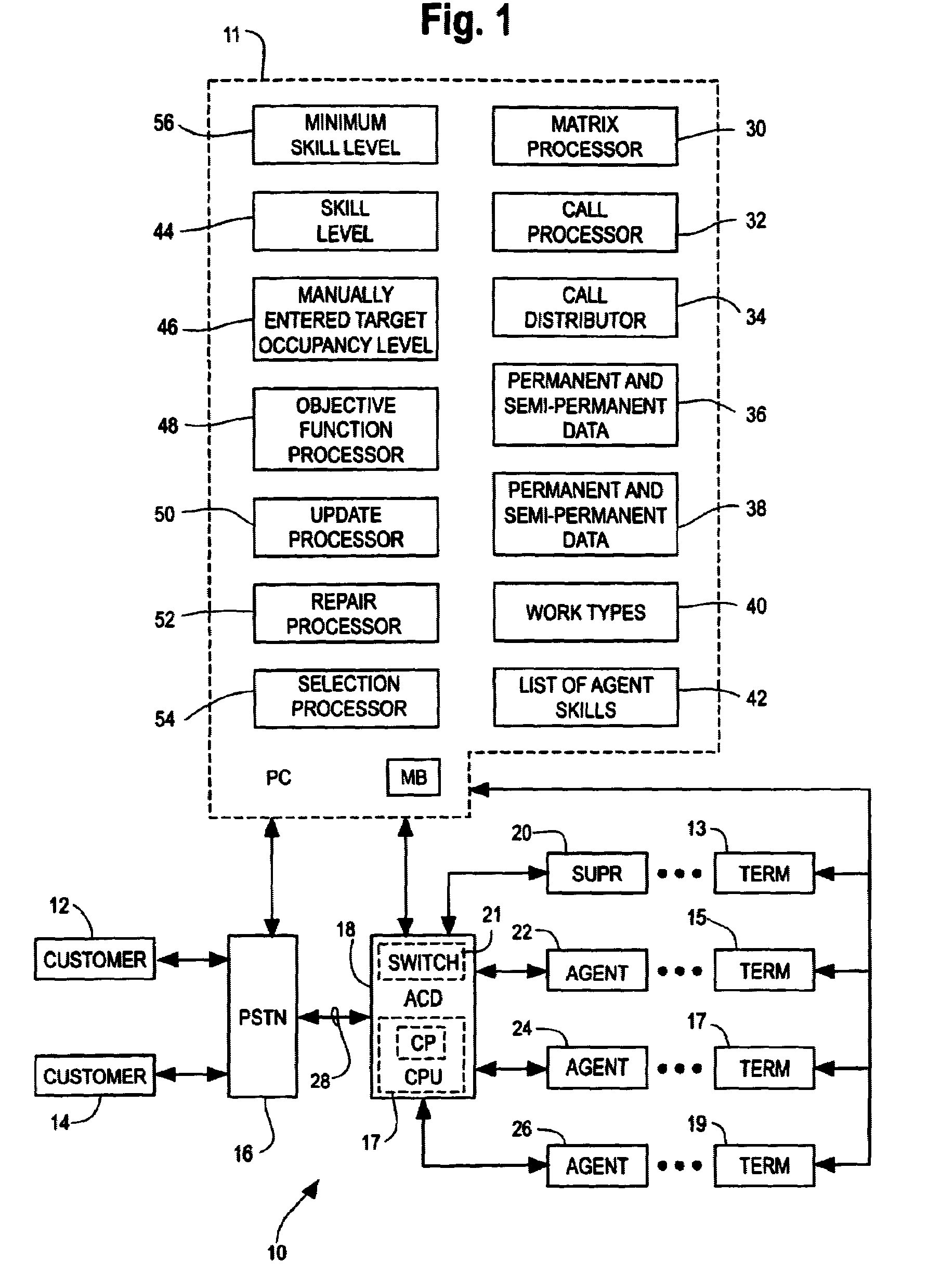
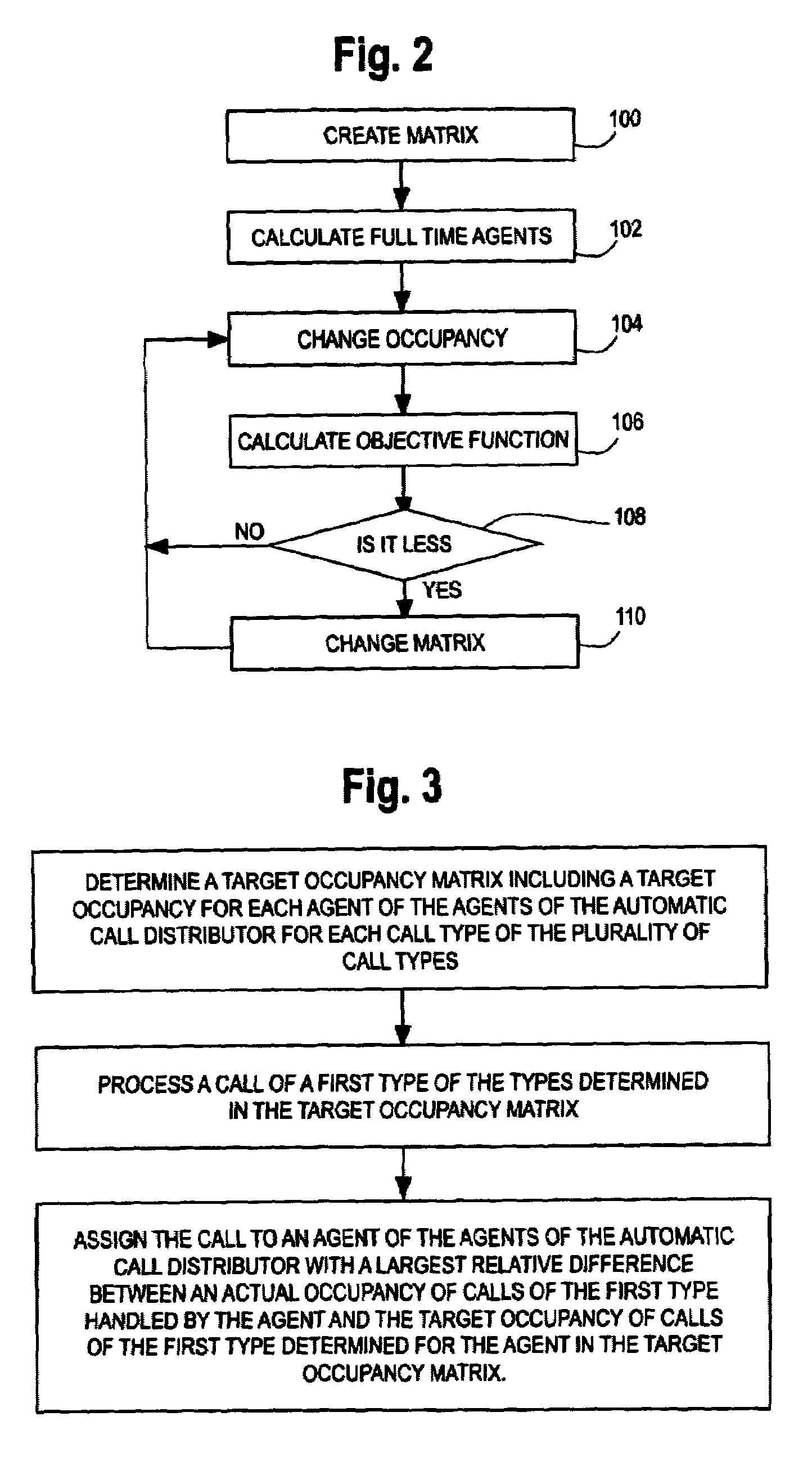
Dynamic skill-based call routing
InactiveUS7133520B1Semi-automatic systemsSupervisory/monitoring/testing arrangementsBase callingSkill sets
A method and apparatus are provided for assigning agents of an automatic call distributor to incoming calls of a plurality of call types handled by the automatic call distributor. The method includes the steps of determining a target occupancy matrix including a target occupancy for each agent of the agents of the automatic call distributor for each call type of the plurality of call types. The method further includes the steps of processing a call of a first type of the types determined in the target occupancy matrix and assigning the call to an agent of the agents of the automatic call distributor with a largest relative difference between an actual occupancy of calls of the first type handled by the agent and the target occupancy of calls of the first type determined for the agent in the target occupancy matrix.
Owner:FIRSTPOINT CONTACT TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com