Data encryption method based on password book
A technology of data encryption and codebook, applied in the field of computer data security, can solve problems such as insufficient security, and achieve the effect of improving efficiency and reducing algorithm complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The technical scheme of the present invention is described in detail below in conjunction with accompanying drawing:
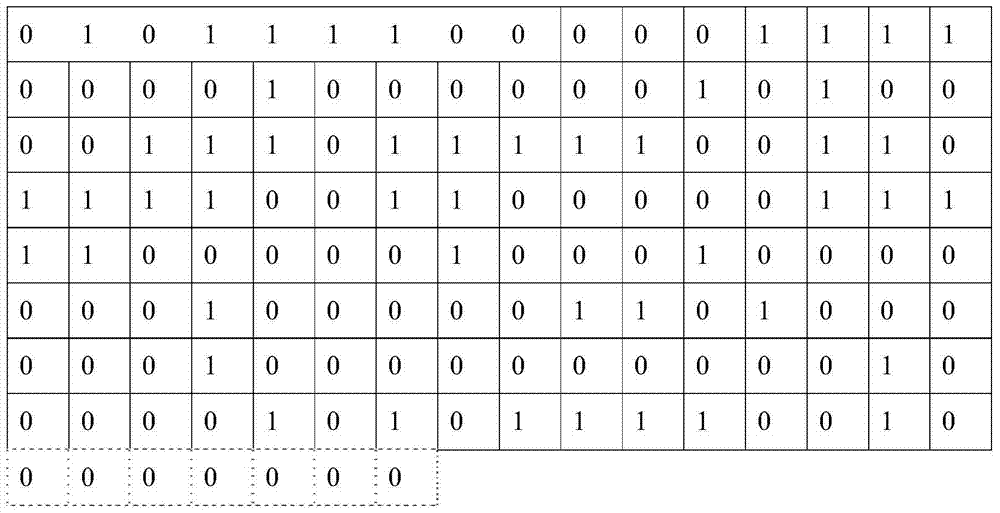
[0027] The idea of the present invention is to use user-defined cipherbooks to encrypt data, make full use of the sequence formed by the stored data itself, and do not need to "disrupt" the original data by extracting part of the bit data or inserting data between specific bits Instead of storing the sequence, the original data sequence is "segmented by a fixed length". This "fixed length" generally exceeds 8 bits, which makes the ciphertext display simpler and more concise, and greatly increases the difficulty for users to illegally decrypt.
[0028] The data encryption method based on codebook of the present invention comprises the encryption and decryption of data, and the encryption of data is specifically as follows:
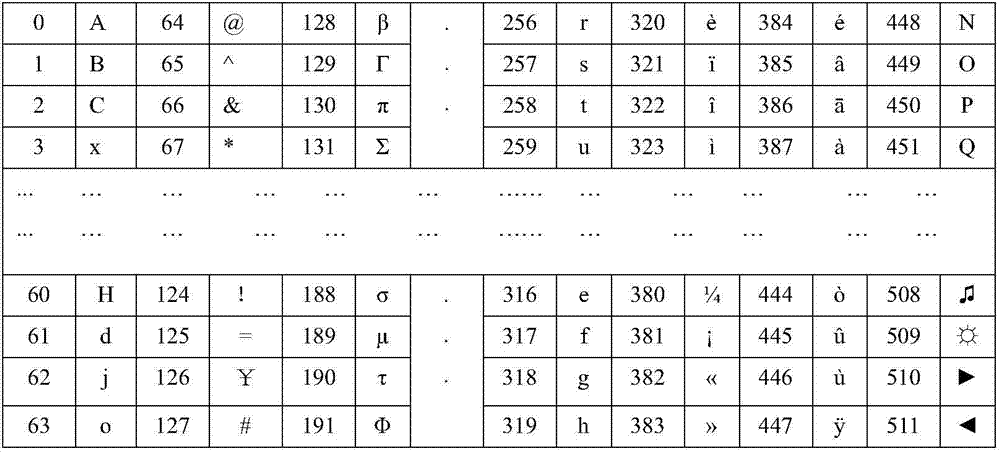
[0029] Step 1, choose 2 N different characters, and combine the 2 N characters and 0~(2 N The decimal numbers of -1) correspon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com