Method, device and system of distributing network safety strategies
A security strategy and network security technology, applied in transmission systems, electrical components, etc., can solve problems such as difficulty in achieving overall defense and failure to eliminate network security threats, and achieve the effect of eliminating network security threats and improving the effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
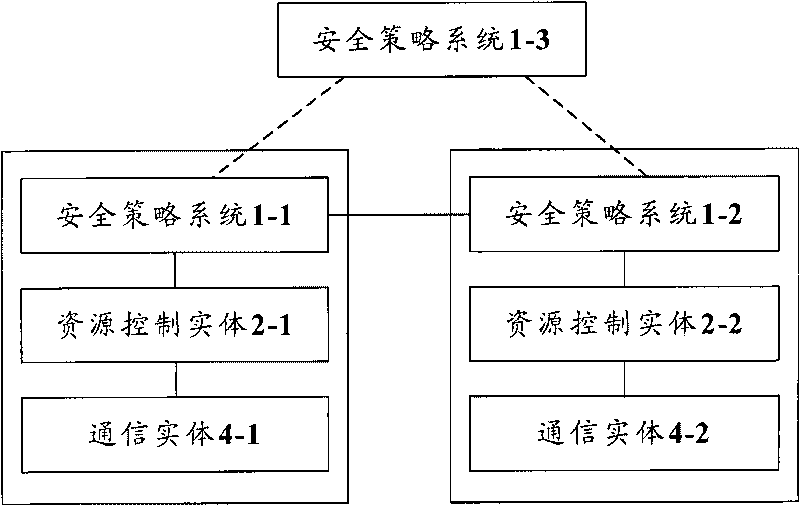
[0060] In this embodiment, the communication entity A and the communication entity B belong to different resource control entities A and B respectively, and the resource control entity A and the resource control entity B belong to the same security domain A (that is, belong to the same security policy system A ).
[0061] Image 6 It is a schematic flowchart of the network security policy distribution method in this embodiment. Such as Image 6 As shown, the network security policy distribution in this embodiment mainly includes the following steps (step S601-step S617):
[0062] Step S601: Communication entity A sends a communication request to resource control entity A, requesting to communicate with communication entity B;
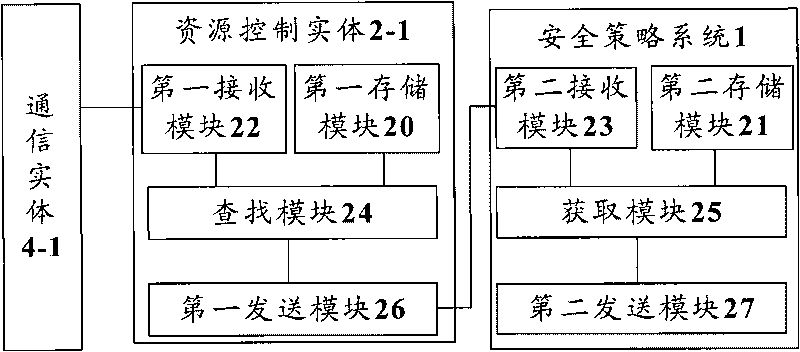
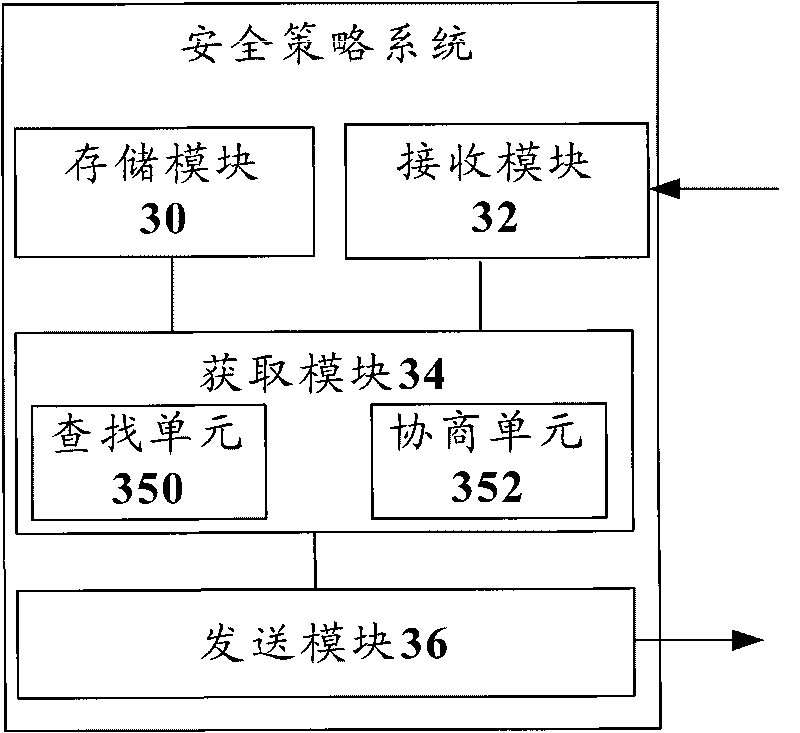
[0063] Step S603: The resource control entity A checks its locally stored security policy information, and if there is no security policy information that matches the communication request of the communication entity A, it requests the security polic...
Embodiment 2
[0072] In this embodiment, communication entity A and communication entity B belong to different resource control entities A and B respectively, resource control entity A and resource control entity B belong to different security domains (that is, belong to different security policy systems), Wherein, the resource control entity A belongs to the security domain A (that is, belongs to the security policy system A), and the resource control entity B belongs to the security domain B (that is, belongs to the security policy system B).
[0073] Figure 7 It is a schematic flowchart of the network security policy distribution method in this embodiment. Such as Figure 7 As shown, the network security policy distribution in this embodiment mainly includes the following steps (step S701-step S719):
[0074] Step S701: The communication entity A in the security domain A sends a communication request to the resource control entity A, requesting to communicate with the communication enti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com