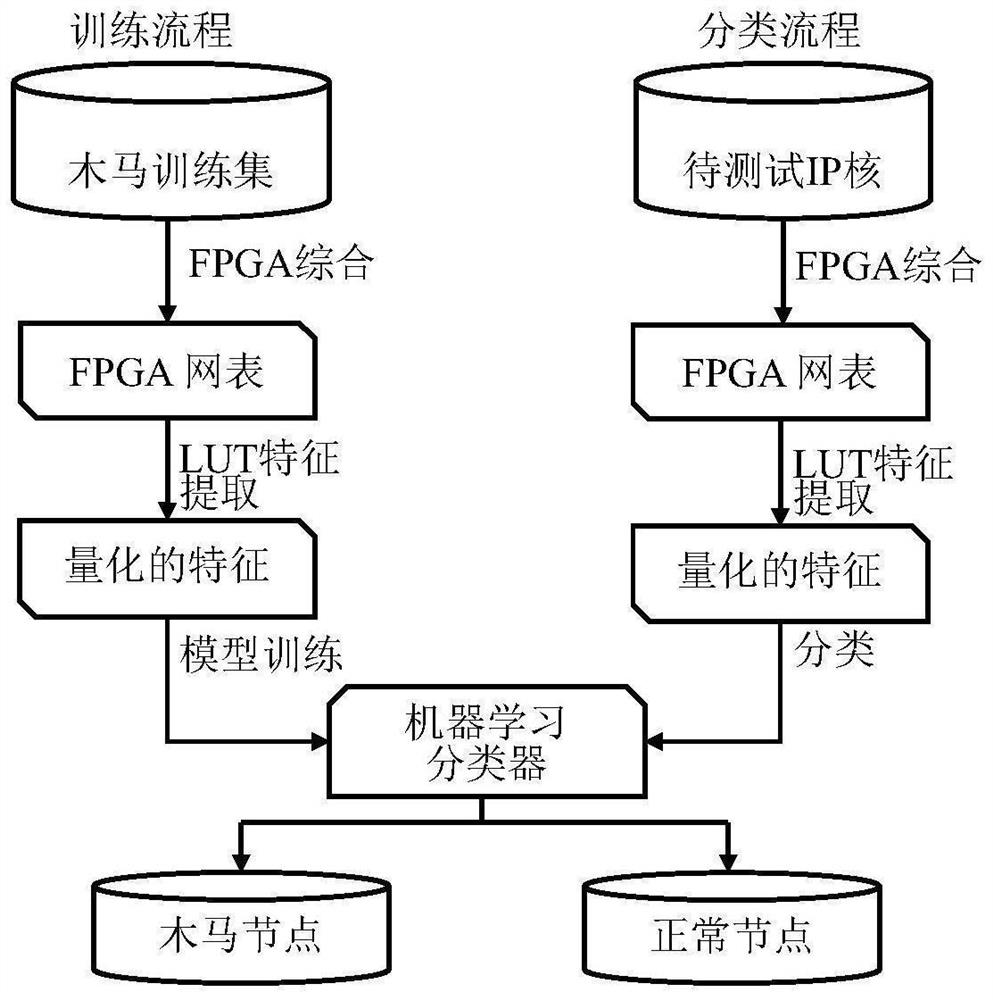
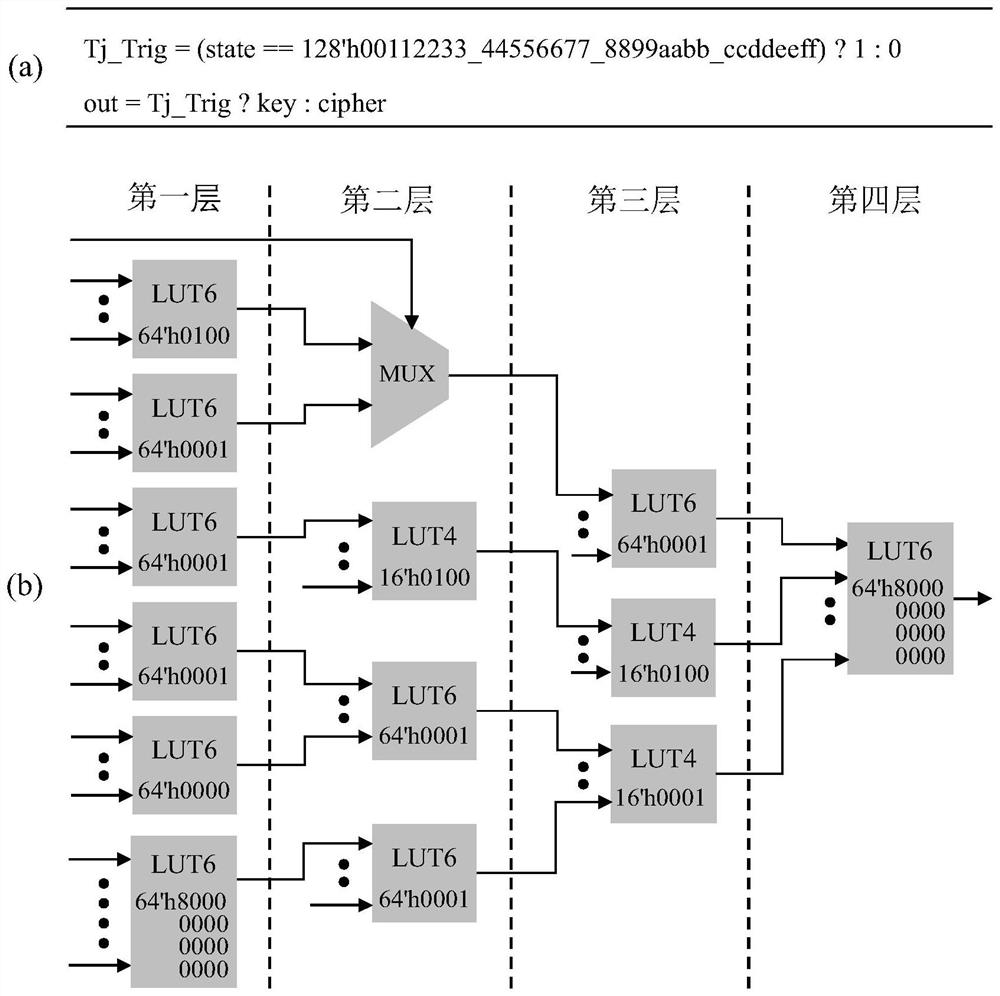
Hardware Trojan horse detection method based on LUT feature extraction and machine learning
A hardware Trojan detection and machine learning technology, applied in computer parts, instruments, computer-aided design, etc., can solve problems such as low detection accuracy and false positives, and achieve the effect of getting rid of dependence, low cost, and eliminating security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
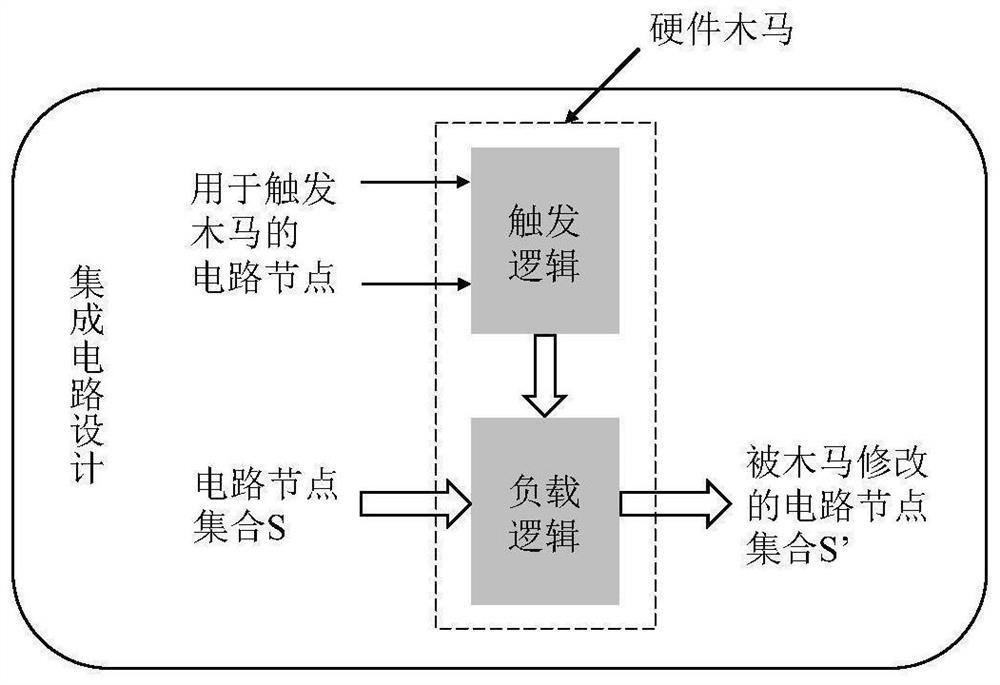
[0036] like figure 2 The IC design shown includes a hardware Trojan embedded by an untrusted third party. The hardware Trojan can be divided into two parts: trigger logic and load logic. The trigger logic is responsible for controlling whether the Trojan circuit is idle or triggered. Before being triggered, the Trojan does not affect the function of the original circuit. When the trigger conditions are met and the Trojan is activated, the load logic is responsible for implementing malicious effects on circuit functions, such as leaking sensitive information or causing system failure. Hardware Trojan designers try to hide Trojan circuits to avoid integrated circuit verification and testing. To achieve this, the designer needs to make the trojan effect appear only in rare cases, preferably after a long run to activate the trojan. In an embodiment of the present invention, the integrated circuit design to be tested is input in the form of register transfer level code.
[003...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com