Use web search engines to correct domain names used for social engineering
A search engine, Internet search technology, applied in the field of using web search engines to correct domain names used for social engineering, to reduce security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
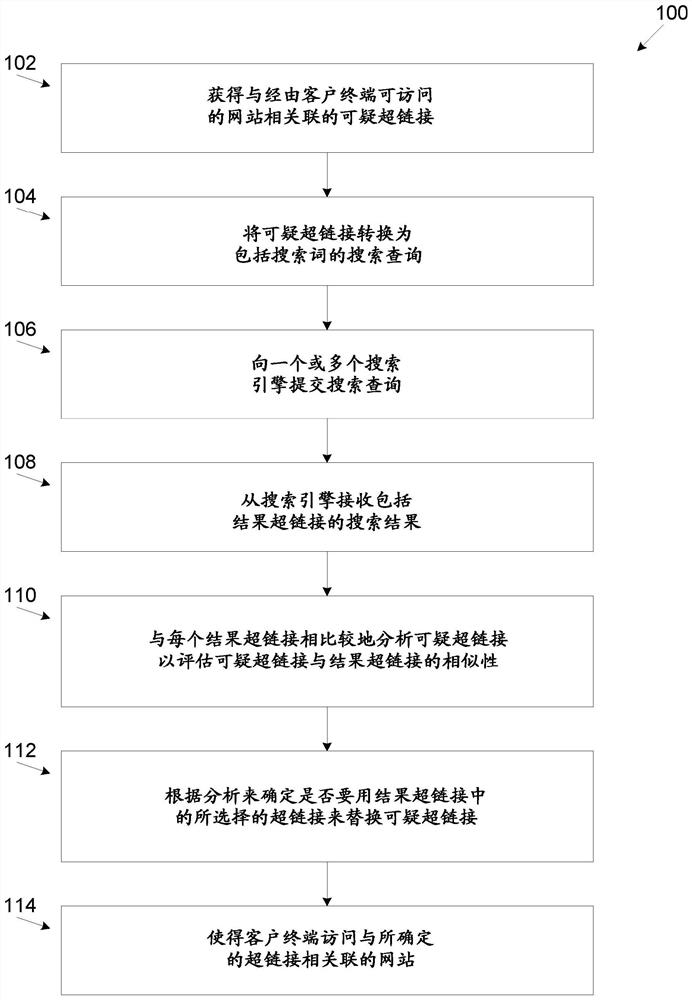
[0018] According to some examples of the present disclosure, there are provided systems, methods, and methods for detecting hyperlinks associated with untrusted web resources using one or more search engines and replacing them with trusted hyperlinks associated with trusted web resources. Software Program Product.
[0019] Before explaining at least one of the illustrative examples in detail, it should be understood that the present disclosure is not necessarily limited to the construction and arrangement of components and / or methods given in the following description and / or illustrated in the drawings and / or examples detail. The disclosure is capable of other examples or of being practiced or carried out in various ways.
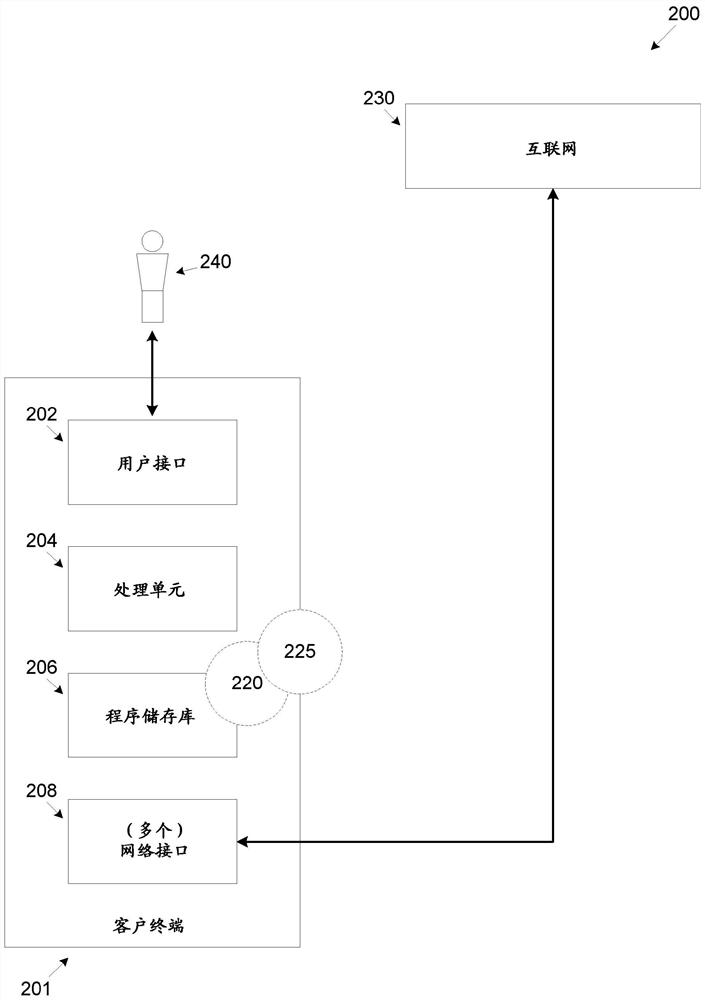
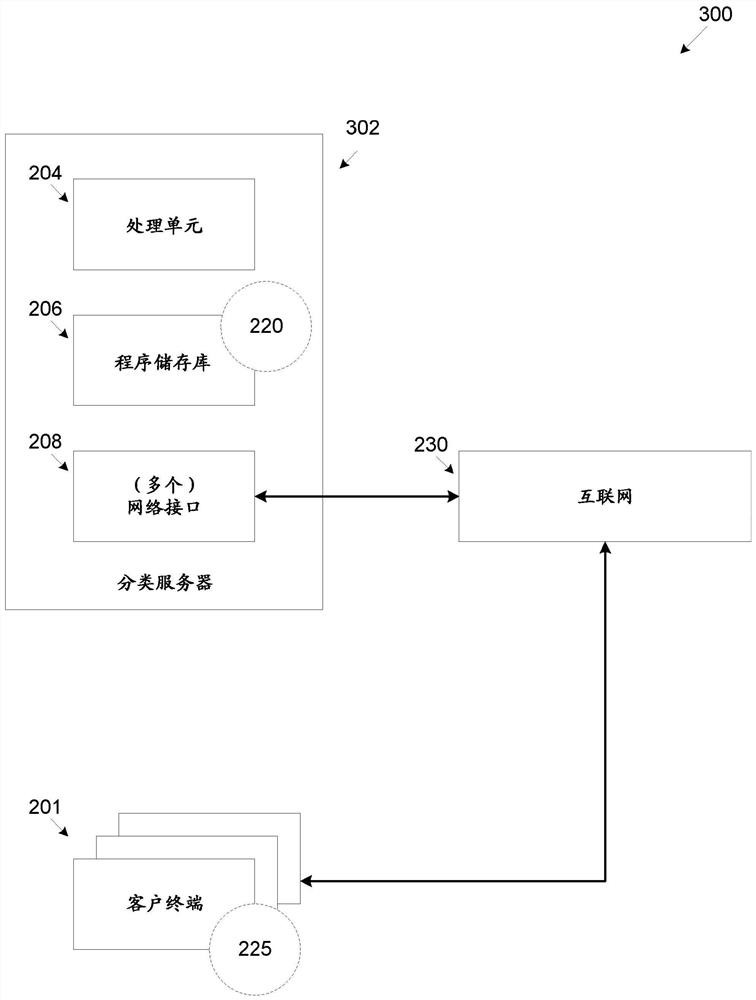
[0020] now refer to figure 1 , figure 1 is an example for detecting hyperlinks associated with untrusted web resources and replacing them with trusted hyperlinks associated with trusted web resources based on analysis of search engine results at a client...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com