Telecommunication method for securely exchanging data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048]Like numbered elements in these figures are either equivalent elements or perform the same function. Elements which have been discussed previously will not necessarily be discussed in later figures if the function is equivalent.
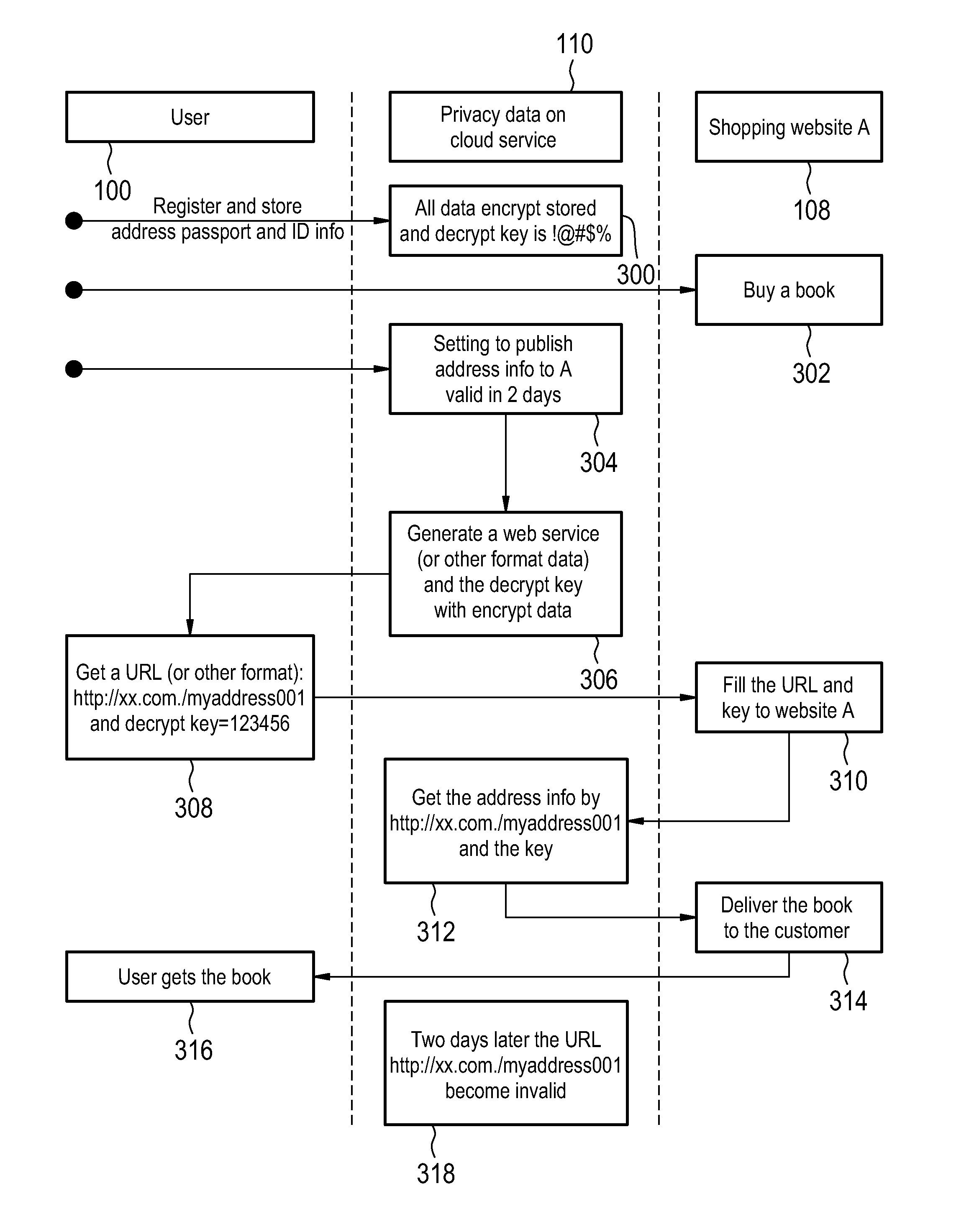
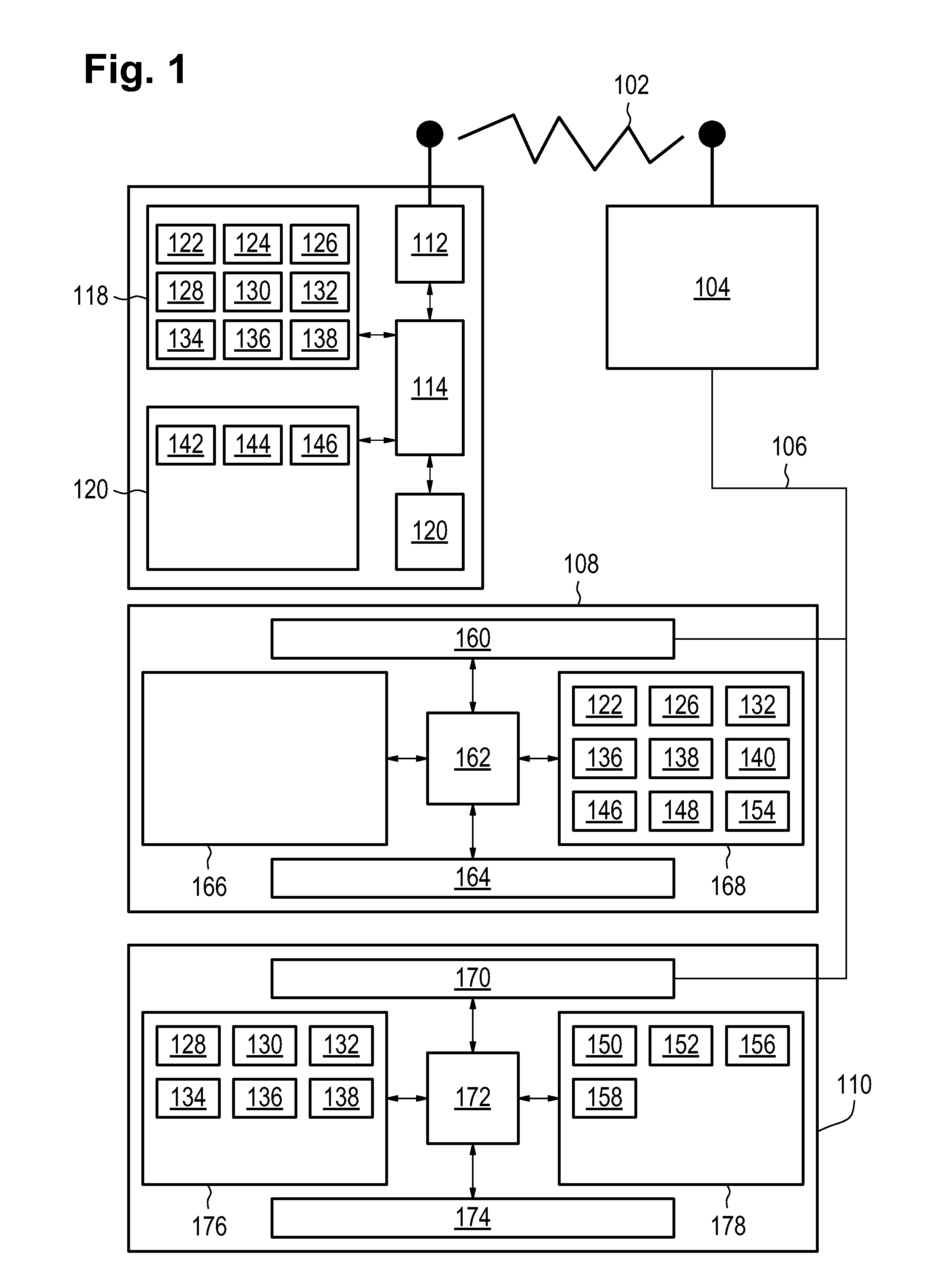
[0049]FIG. 1 shows an example of a telecommunications system. The system comprises a telecommunications device 100 which is connected via a wireless telecommunications connection 102 to a base station 104. For instance the telecommunications device could be a mobile telephone or a smart phone. The base station 104 is connected via a wired network connection 106 to a first server 108 and a second server 110. The first server 108 and the second server 110 may be computer processing devices for computer systems.
[0050]The telecommunications device 100 is shown as comprising a transceiver 112, a processor 114 and a battery 120, storage 118, and memory 120. The storage 118 is shown as containing unencrypted data 122, an encryption key 124, an order request 12...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com