Scanning method and scanning device for malicious programs
A malicious program and scanning method technology, applied in the Internet field, can solve the problems of no malicious program scanning method, no malicious program scanning, malicious consumption of traffic, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0093] The embodiment of the present invention provides a malicious program scanning method. The method improves the malicious program scanning device. The malicious program scanning device in this embodiment may be installed on a user client, for example, the client may be a user terminal such as a PC (Personal Computer, personal computer), a mobile phone, or a handheld computer.
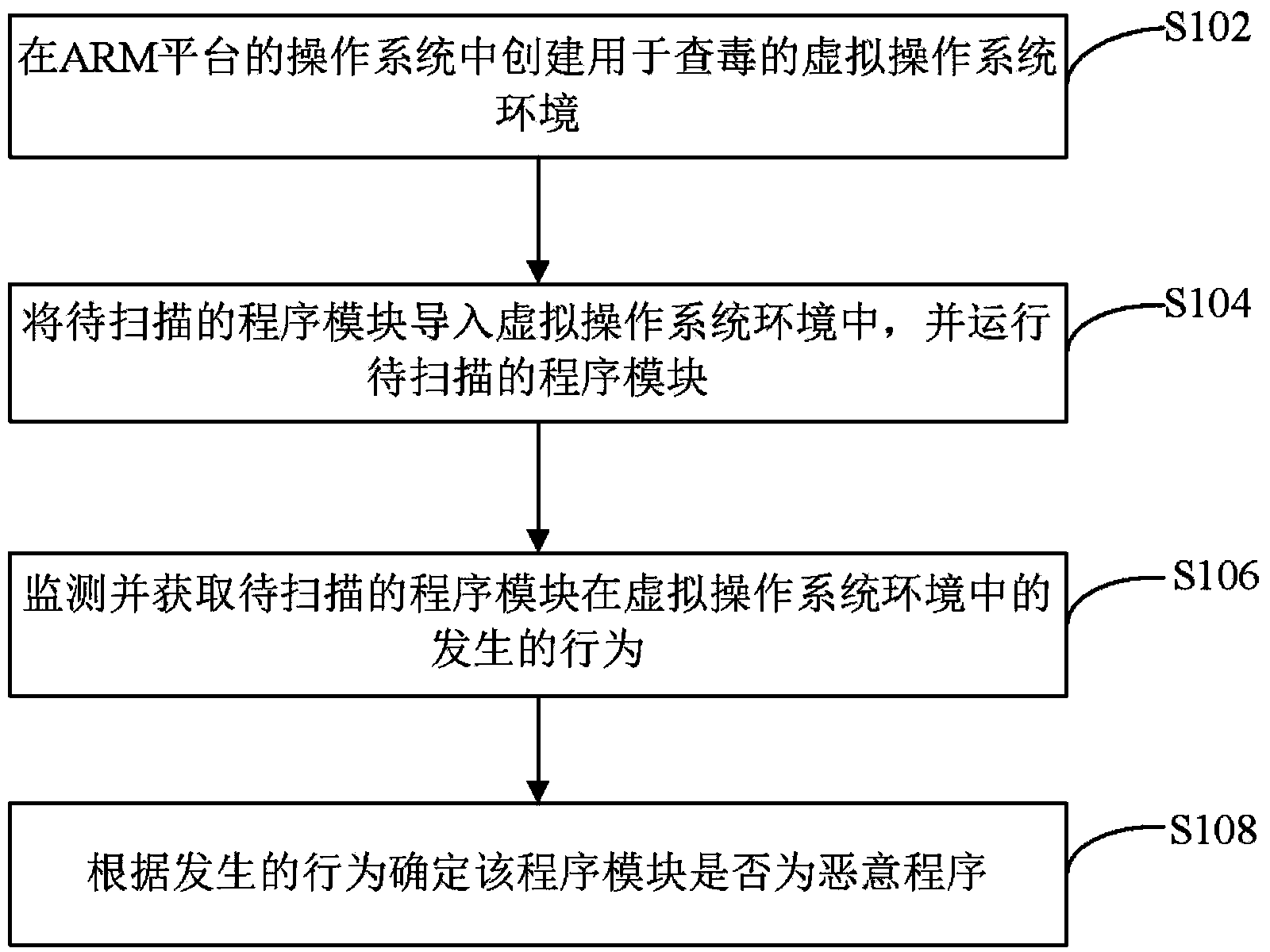
[0094] figure 1 It is a flowchart of a malicious program scanning method according to an embodiment of the present invention, and the method includes steps S102 to S108.
[0095] S102, creating a virtual operating system environment for virus checking in the operating system of the ARM platform.
[0096] S104. Import the program module to be scanned into the virtual operating system environment, and run the program module to be scanned.
[0097] S106, monitor and acquire the behavior of the program module to be scanned in the virtual operating system environment.
[0098] S108. Determine whethe...
Embodiment 2
[0101] This embodiment is a specific application scenario of the first embodiment above. Through this embodiment, the method provided by the present invention can be described more clearly and specifically.
[0102] Wherein, the method provided in this embodiment can be implemented in the mobile terminal based on the ARM platform in the form of driver or antivirus software.
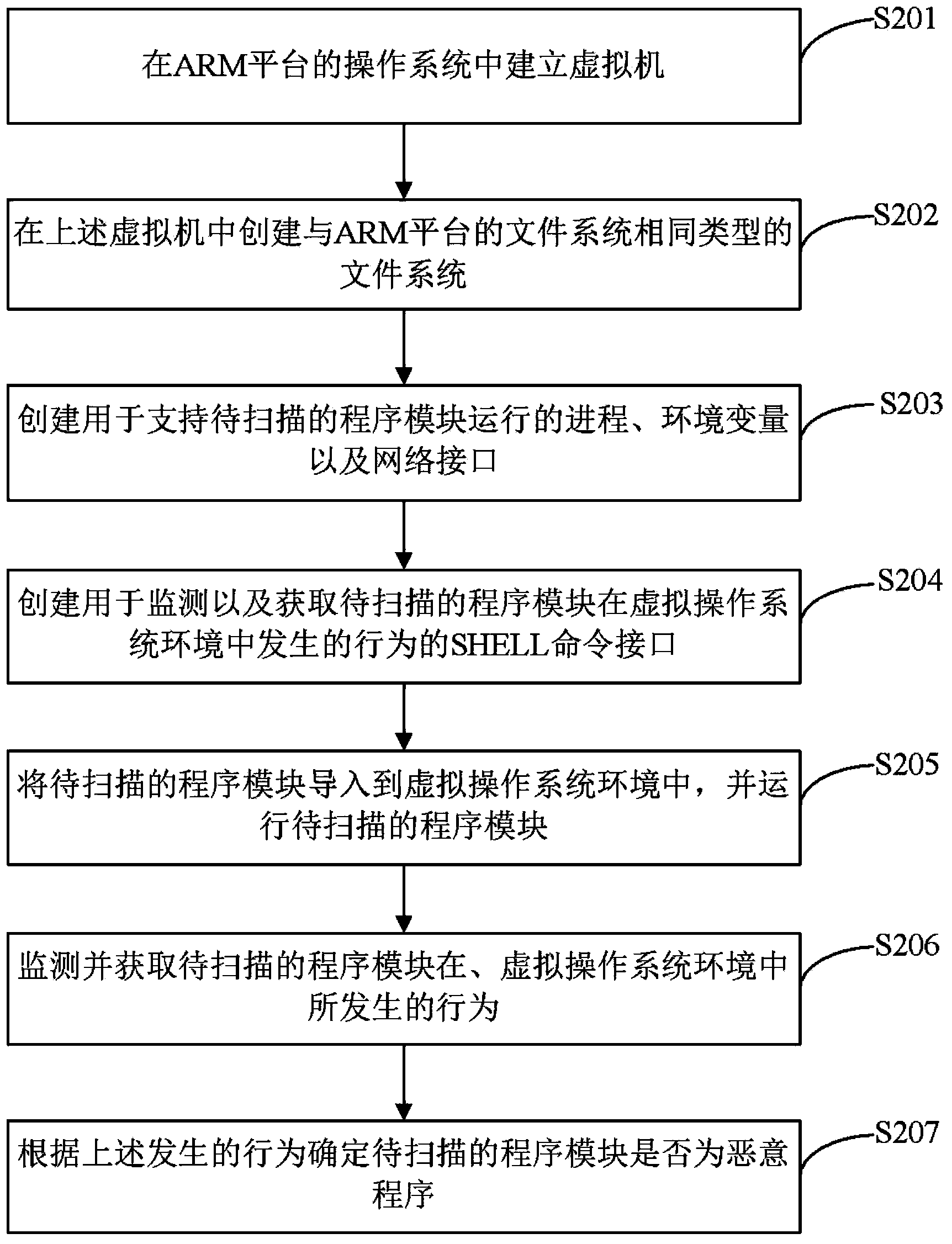
[0103] figure 2 It is a flowchart of a specific scanning method for a malicious program according to an embodiment of the present invention, and the method includes steps S201 to S207.
[0104] S201. Establish a virtual machine in the operating system of the ARM platform.
[0105] Taking a mobile phone running the Android system as an example, this step is to create a virtual machine in the Android system running on the mobile phone. The virtual machine can be a complete system, which simulates a complete hardware system function and runs in a completely isolated environment. A complete computer system...
Embodiment 3
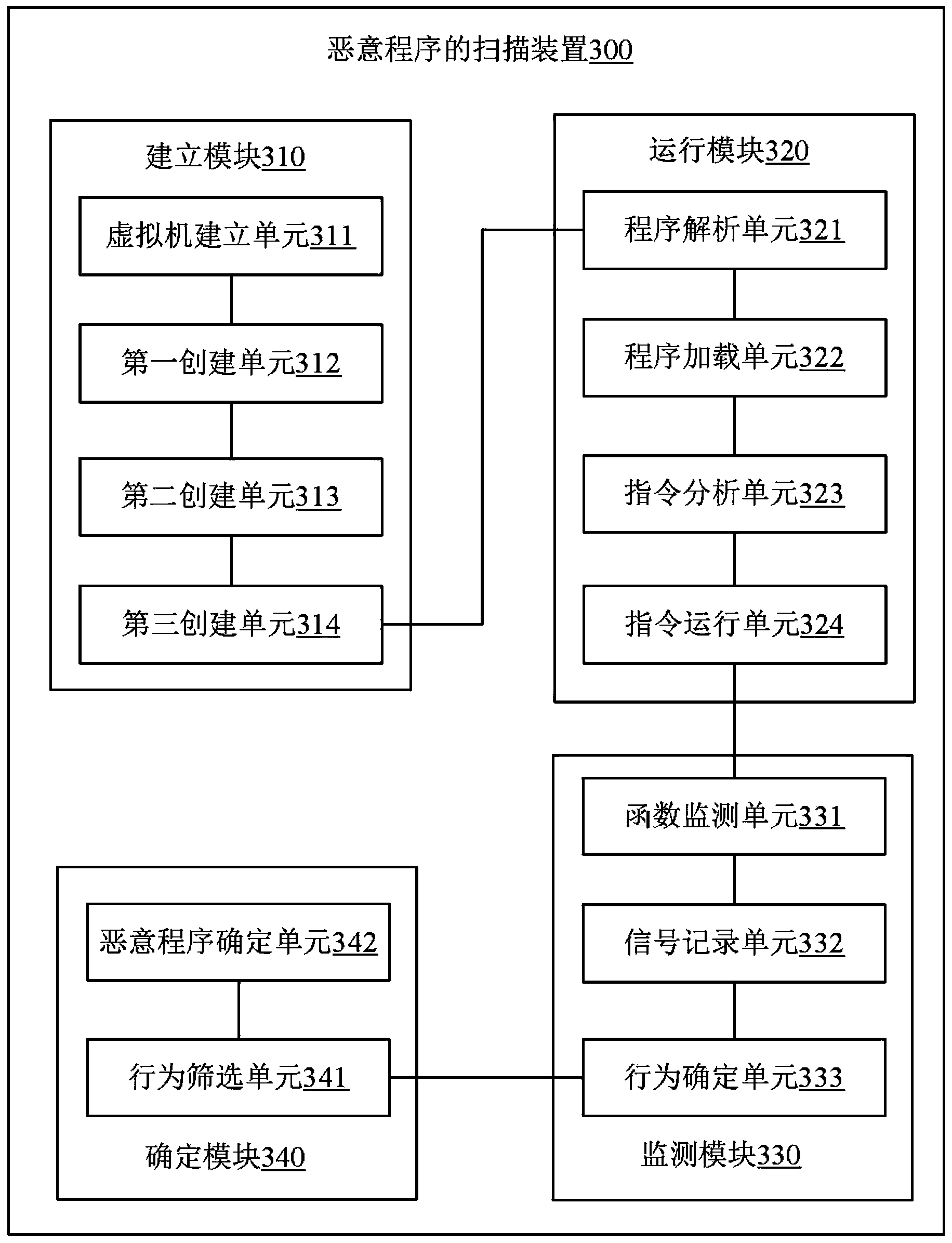
[0167] image 3 It is a structural block diagram of a malicious program scanning device provided by an embodiment of the present invention, and the device 300 includes:
[0168] Build a module 310, configured to create a virtual operating system environment for virus checking in the operating system of the ARM platform;
[0169] The running module 320 is configured to import the program module to be scanned into the virtual operating system environment, and run the program module to be scanned;
[0170] The monitoring module 330 is configured to monitor and obtain the behavior of the program module to be scanned in the virtual operating system environment;
[0171] The determination module 340 is configured to determine whether the program module is a malicious program according to the occurred behavior.
[0172] Optionally, the establishment module 310 includes:
[0173] The virtual machine establishment unit 311 is configured to establish a virtual machine in the operatin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com