Private key management method and apparatus for bastion host
A technology of private key management and bastion machine, applied in the computer field, can solve the hidden danger of private key storage of bastion machine and other problems, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0025] refer to figure 1 , shows a flow chart of steps of a method for managing a private key of a bastion machine according to Embodiment 1 of the present invention.
[0026] The embodiment of the present invention bastion machine private key management method comprises the following steps:
[0027] Step 101: Obtain the first private key parameter set in the process file of the bastion host when the bastion host starts.
[0028] Wherein, the first private key parameter includes: a first shared key decryption code parameter. The first private key parameter is preset in the process file of the bastion host. In the embodiment of the present invention, it is assumed that the first private key parameter has been set in the process file of the bastion machine, and the second private key parameter has been set in the private key management platform. The generation of the first private key parameter and the second private key parameter may be generated by the bastion host, or may ...
Embodiment 2
[0040] refer to figure 2 , shows a flow chart of steps of a method for managing a private key of a bastion machine according to Embodiment 2 of the present invention.
[0041] The bastion machine private key management method in the embodiment of the present invention specifically includes the following steps:
[0042] Step 201: Generate the first private key parameter and the second private key parameter, and correspondingly add the first private key parameter and the second private key parameter to the process file of the bastion machine and the private key management platform.
[0043] The first private key parameters include, but are not limited to: the first shared key decryption code, the private key management platform domain name parameter, and the bastion host ID. The second private key parameter includes: a second shared key decryption code, a ciphertext private key, and a private key encryption algorithm.
[0044] A preferred method of generating and uploading th...
Embodiment 3
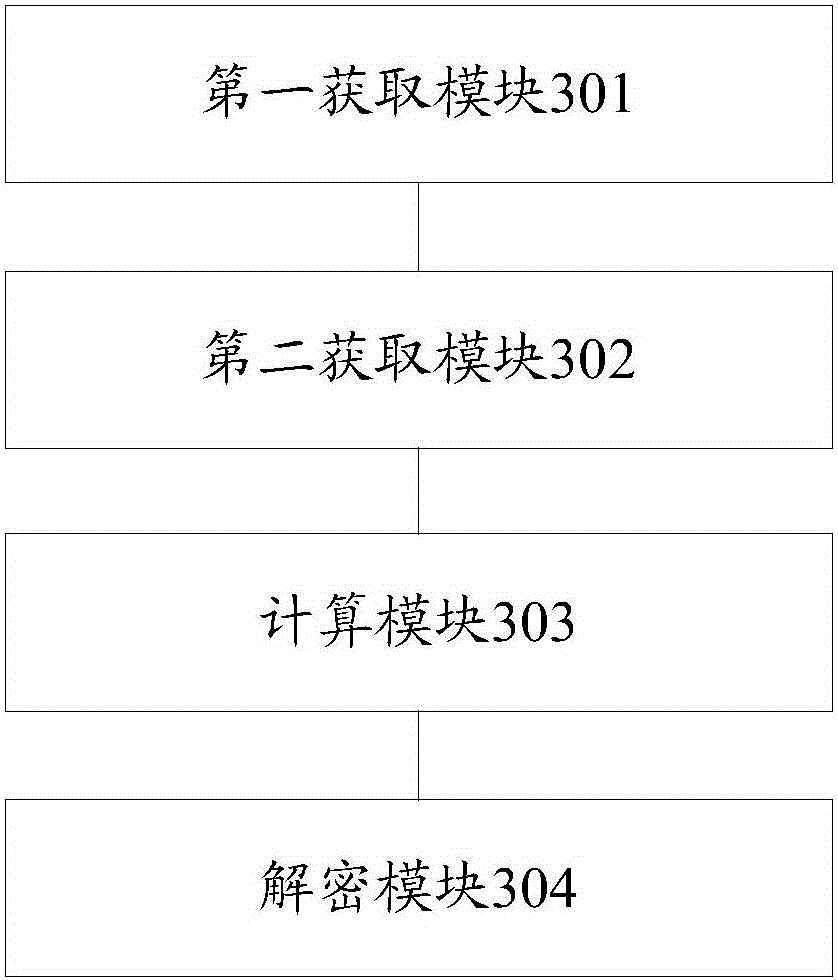
[0067] refer to image 3 , shows a schematic structural diagram of a bastion machine private key management device according to Embodiment 3 of the present invention.
[0068] The bastion machine private key management device in the embodiment of the present invention includes: a first acquisition module 301, which is used to acquire the first private key parameter set in the bastion machine process file when the bastion machine is started; wherein, the first private key parameter Including: the first shared key decryption code; the second acquisition module 302, configured to obtain the second private key parameter from the private key management platform; wherein, the second private key parameter includes: the second shared key decryption code, Ciphertext private key and private key encryption algorithm; Calculation module 303 is used to calculate the first shared key decryption code and the second shared key decryption code according to the shared key algorithm to obtain th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com