Multi-receiver encryption method based on biological characteristics
A biometric and encryption method technology, applied in the field of network security technology, can solve the problems of safe storage of each user, and achieve the effects of improving security and reliability, avoiding security problems, and avoiding key abuse.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
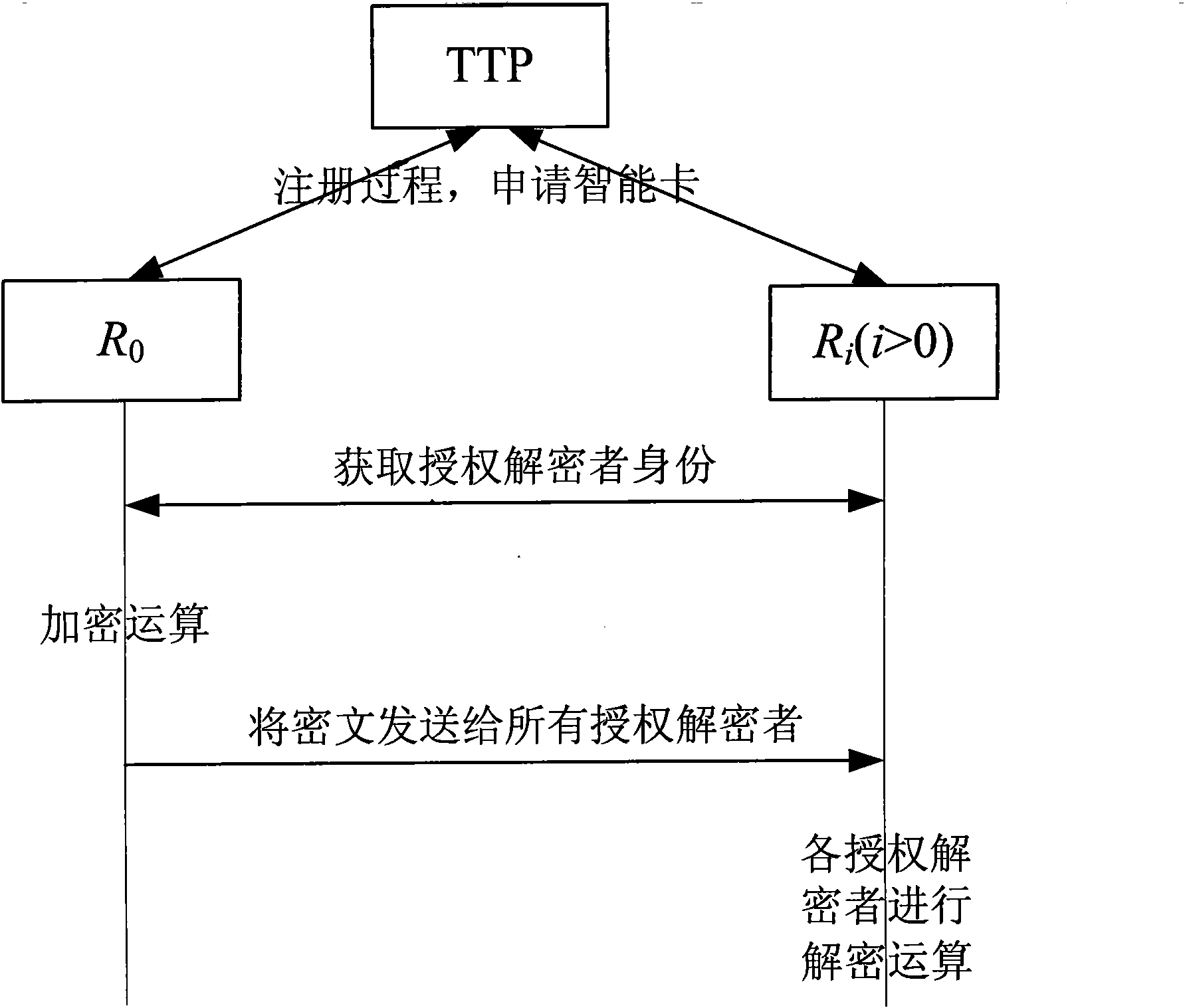
[0052] attached figure 1 The specific flow of the multi-recipient encryption method based on biometric features (such as fingerprints, irises, faces, etc.) of the present invention is given. Combine below figure 1 A complete biometric-based encryption and decryption process will be described.
[0053] Step 1: TTP establishes system parameters. The system parameters are selected by a trusted third-party TTP, including: two p-order cyclic groups (G 1 , +) and (G 2 , ·), where p is a prime number; P is G 1 Generator of ; let e be G 1 and G 2 The bilinear transformation on , that is, e: G 1 ×G 1 →G 2 ;TTP randomly selects its own private key Its corresponding public key is Q TTP = S TTP P∈G 1 ;Let H( ) be a one-way cryptographic hash function;
[0054] Step 2: Registration process. All users in the system, including: CryptoR 0 and n decryptors R 1 , R 2 ,...,R n , register with the trusted third party TTP, and apply for your own smart card. Encryptors need to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com