SM9 joint digital signature method and SM9 joint digital signature device
A digital signature and pre-signature technology used in digital transmission systems, secure communication devices, key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0079] It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
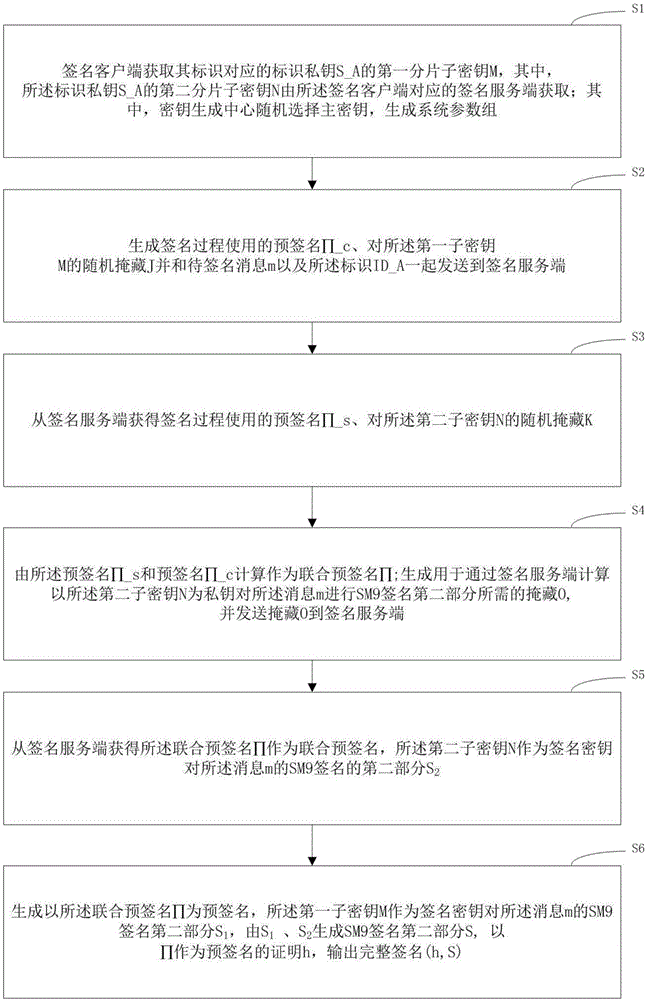
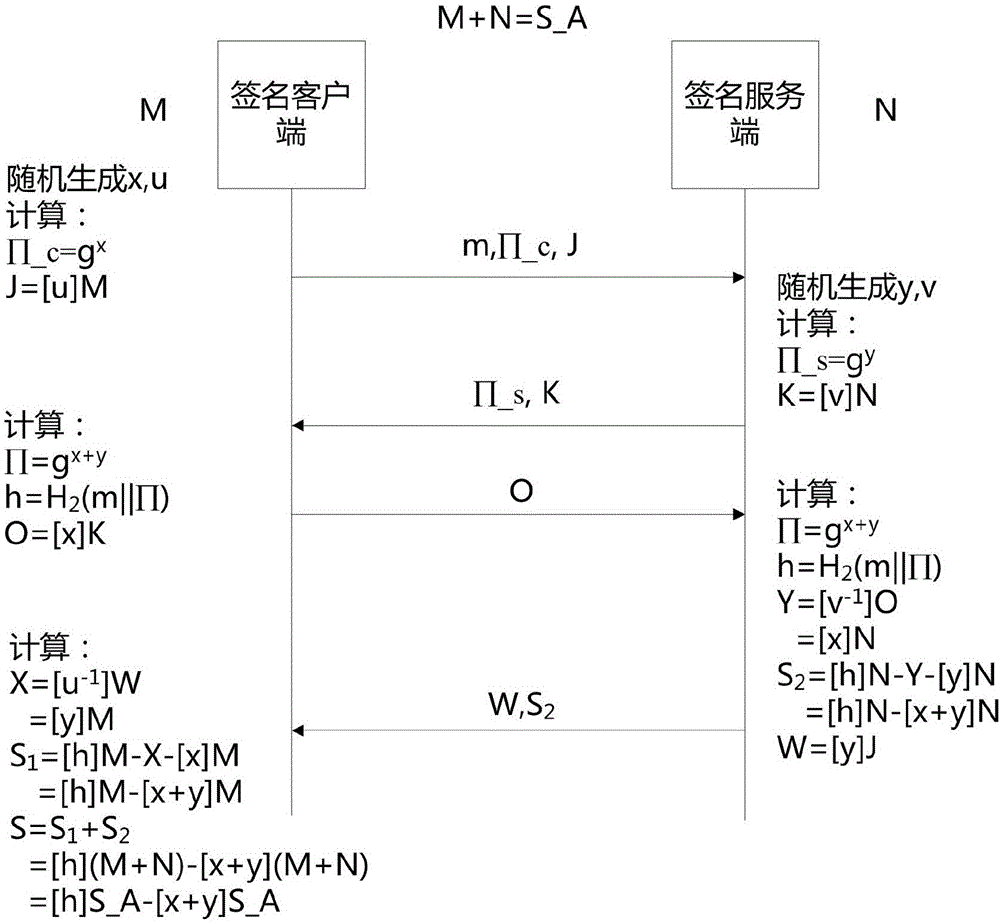
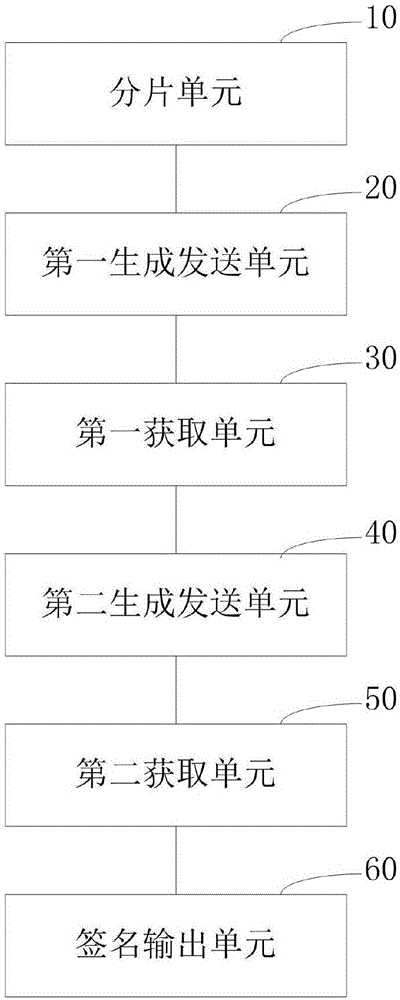
[0080] refer to figure 1 and figure 2 , an embodiment of the present invention provides a SM9 joint digital signature method, including the steps:
[0081] S1. The signature client obtains the first fragmented sub-key M of the identification private key S_A corresponding to its identification, wherein the second fragmented sub-key N of the identification private key S_A is obtained by the signature server corresponding to the signature client Obtain; wherein, the key generation center randomly selects the master key to generate the system parameter group. .
[0082] In step S1, the above-mentioned system parameter group includes 1 , P 2 , [s]P 1 , g=e(P 1 , [s]P 2 ), H>, where E is an elliptic curve, and e represents a binary mapping e:G 1 ·G 2 →G t , G 1 and G 2 are two point groups on the elliptic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com