Mobile client user dynamic secret key encrypted communication method based on HTTP protocol
An HTTP protocol and mobile client technology, applied in the field of mobile Internet, can solve problems such as security risks, secret keys cannot be changed, and no remedial measures, etc., to achieve the effect of ensuring efficiency and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The technical solution of the present invention will be specifically described below in conjunction with the accompanying drawings.
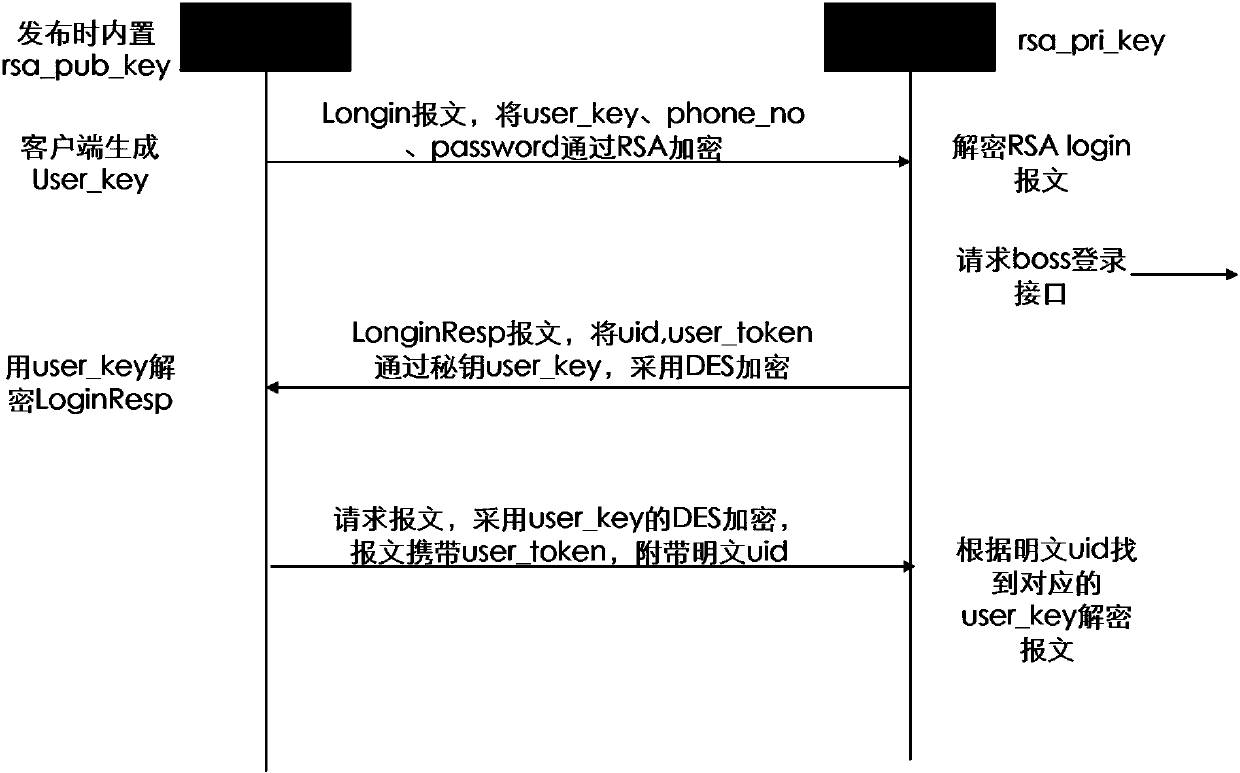
[0020] A kind of mobile client user's dynamic secret key encryption communication method based on HTTP protocol of the present invention comprises the following steps,
[0021] 1. When the client publishes, the general asymmetric encryption public key (rsa_public_key) is pre-built in the client, and the server saves the corresponding private key (rsa_private_key);
[0022] 2. When the user logs in, the client automatically generates a string of random key strings (user_key), and the client uses the public key (rsa_public_key) for the user_key, phone_no (mobile phone number), password (user login password) in the login message Use asymmetric encryption algorithm (RSA) to encrypt and submit to the server --- client user_key should be encrypted and stored properly;
[0023] 3. After receiving the user login request message, the server uses ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com