A digital anti-counterfeiting method for multiple security cigarettes
A digital and cigarette technology, applied in the field of multi-security cigarette digital anti-counterfeiting, can solve the problems of cigarette manufacturers such as catastrophic impact, difficulty in making timely response, inconsistent packaging, etc., to achieve mutual detection and custom upgrade or adjustment, elimination Invalidation of Cigarette Digital Anti-counterfeiting Query and Prevention of Sequential Exhaustive Attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
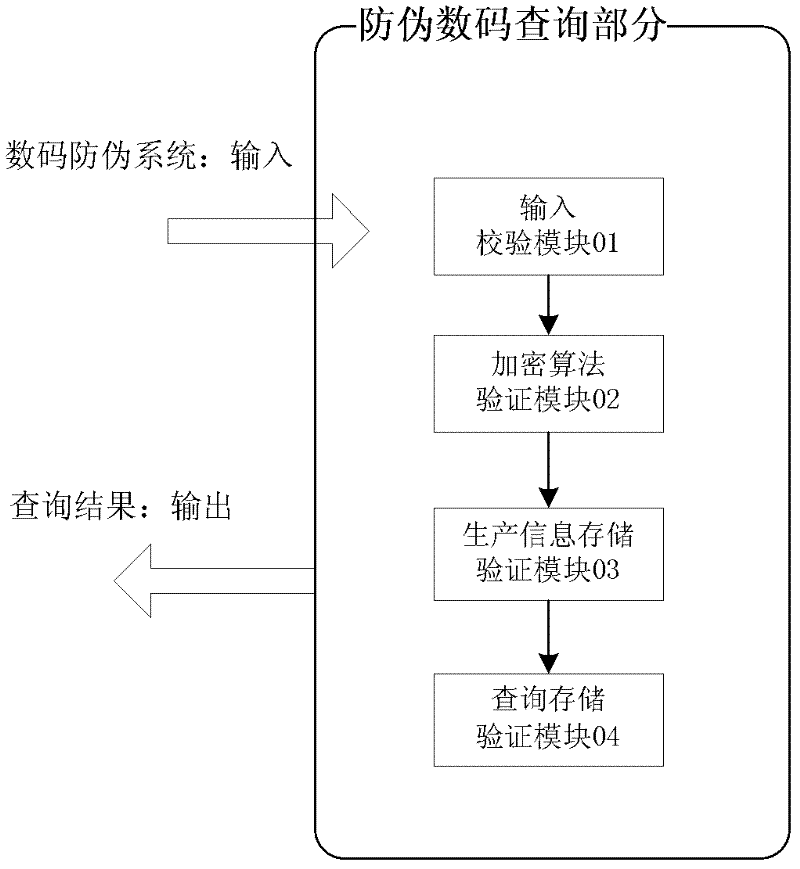
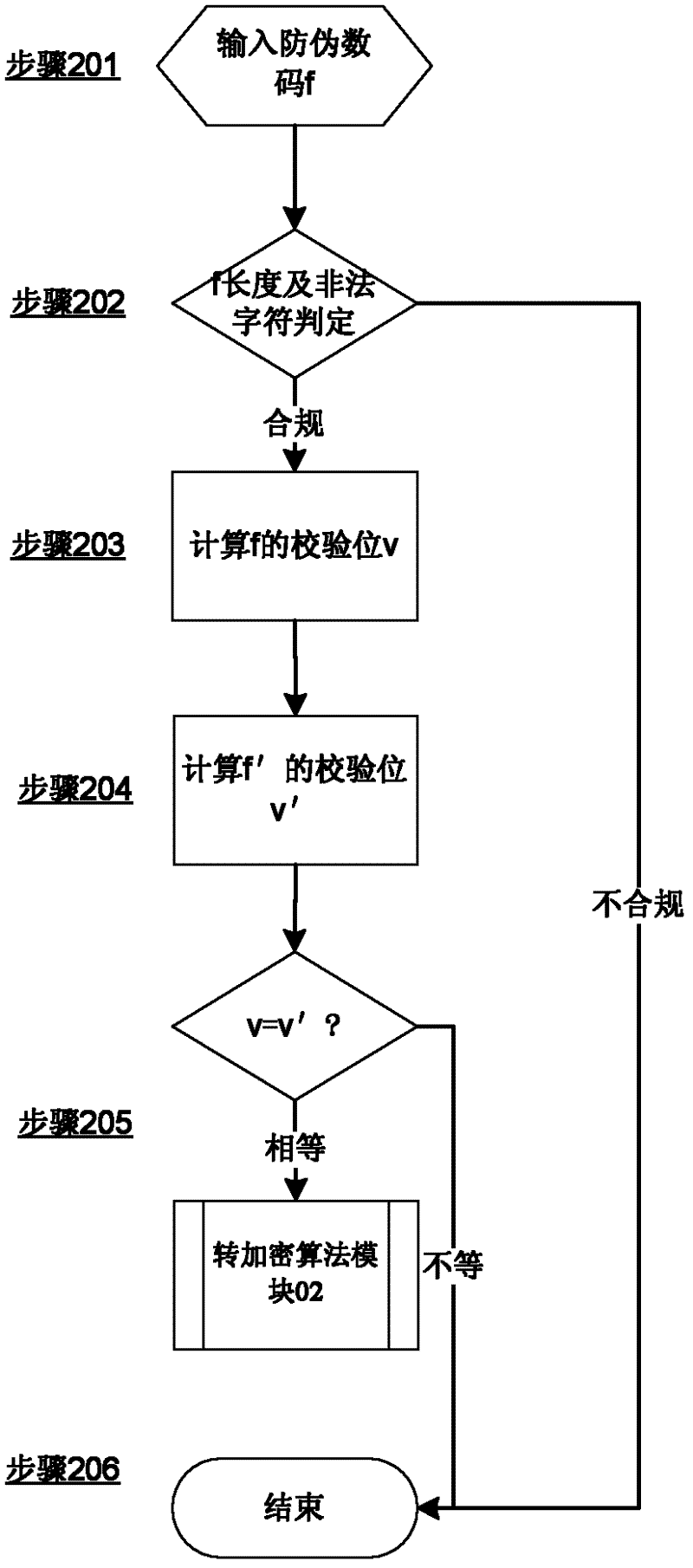
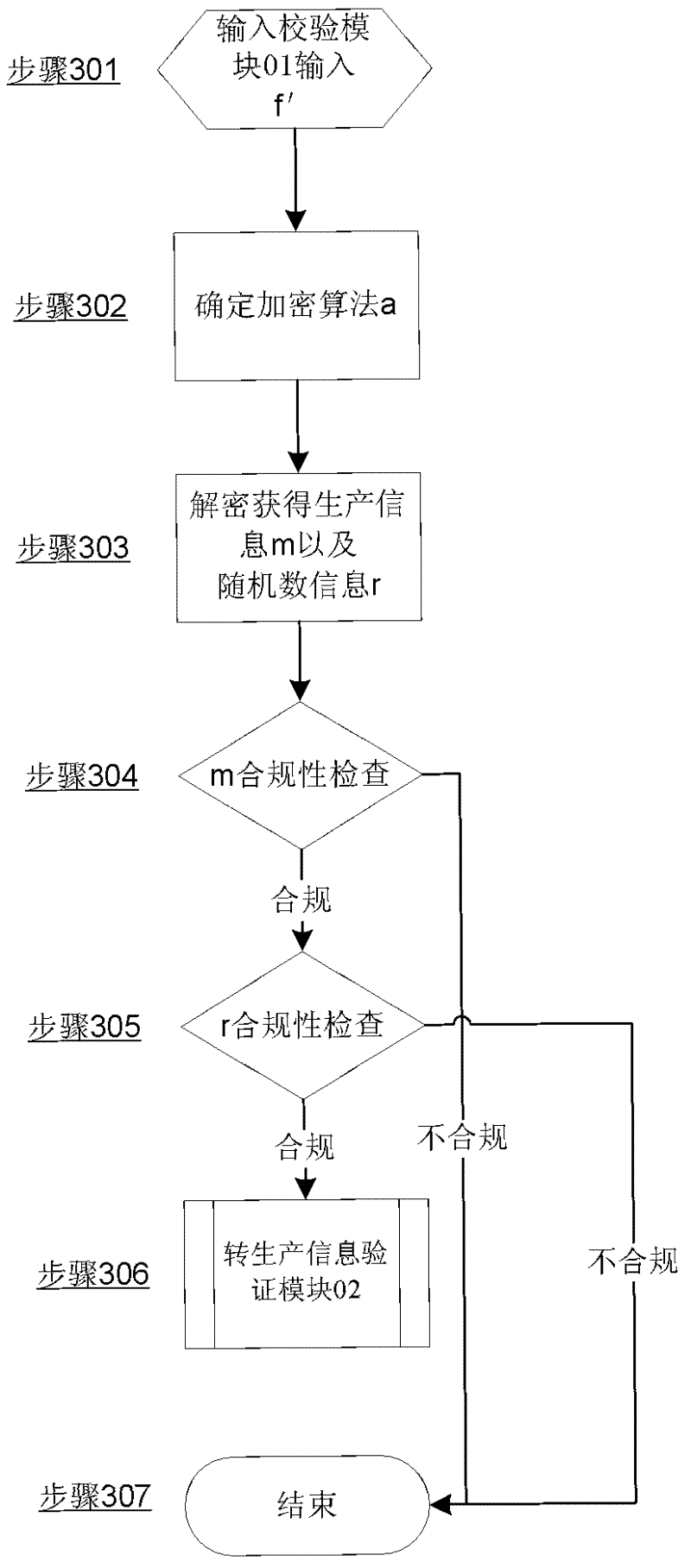
[0043] The method of the present invention strips off the digital anti-counterfeiting query from the whole digital anti-counterfeiting system, and adopts a modular design; the method has designed multiple security modules, each security module can be upgraded independently or corrective measures can be taken, and any security module fails (leaking secrets) ) will not affect the security of the entire digital anti-counterfeiting inquiry part. Such as figure 1 As shown, the anti-counterfeiting method is designed with four security modules: input verification module 01, encryption algorithm verification module 02, production information storage verification module 03, query storage verification module 04.
[0044] (1) Input verification module 01
[0045] The input checking module 01 of this embodiment is implemented by using redundancy checking. In communications, redundancy checks refer to data appended to messages for error detection and error correction. In this embodiment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com