Safety storage method for data
A technology for safe storage and data, applied in the redundancy of computing for data error detection, electrical digital data processing, special data processing applications, etc. Safe storage and other issues to achieve the effect of improving data recovery efficiency, high data reading efficiency, and high data recovery efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
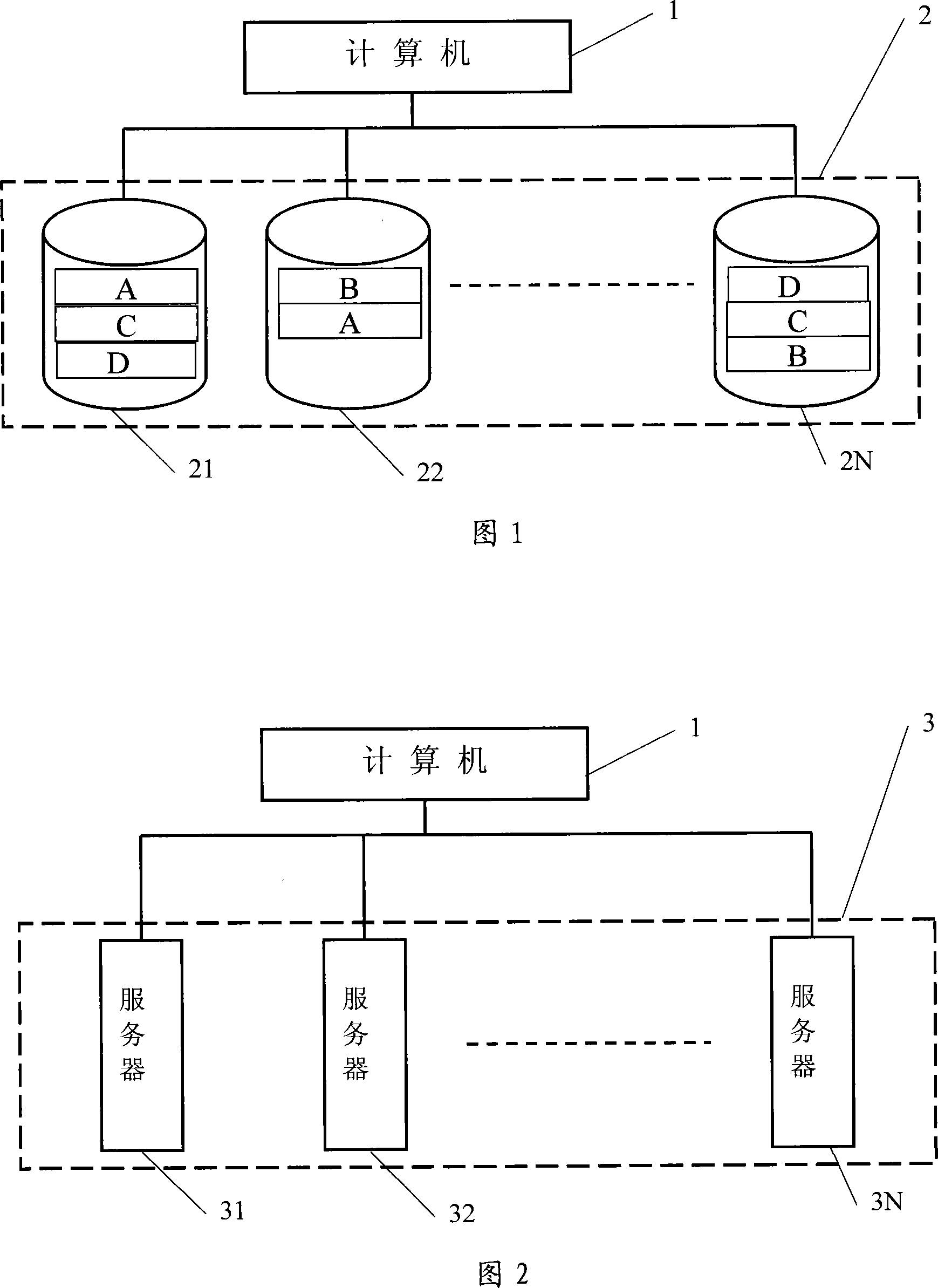
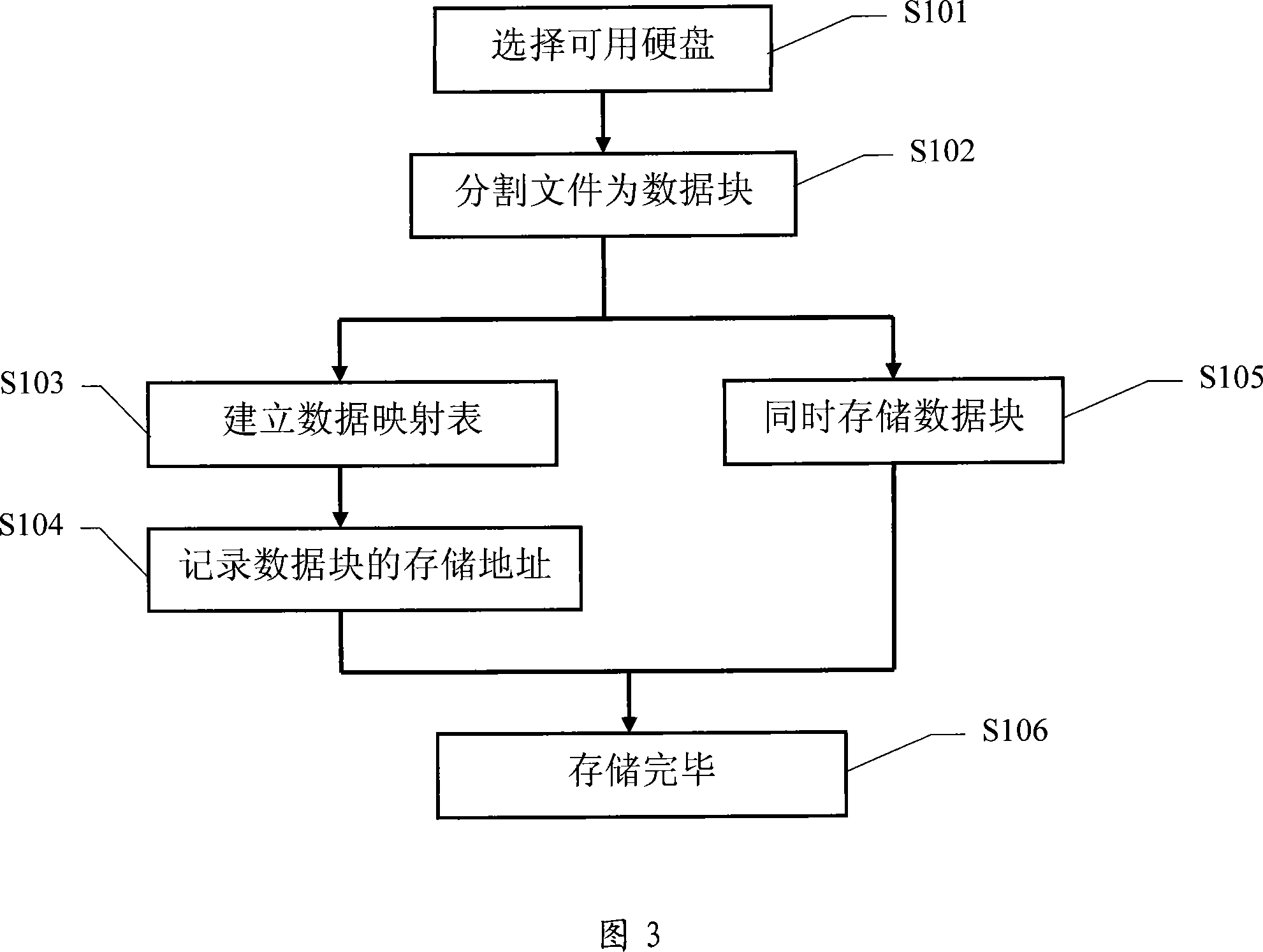
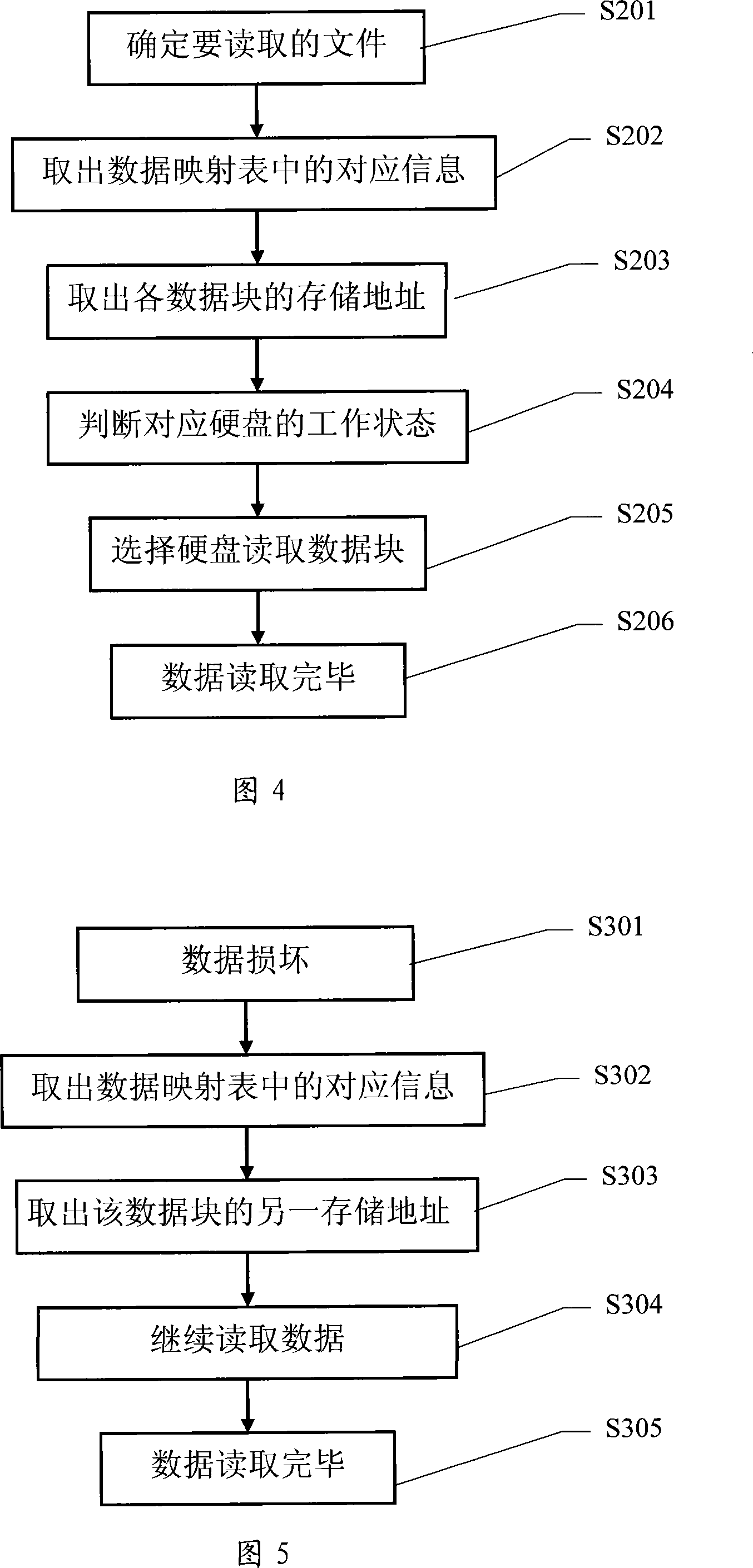
[0051] The basic idea of the present invention is to adopt distributed real-time backup storage, and trade space for safety. Access multiple storage devices in any known way in the computer system, and store any data in two different storage devices at the same time. When the data in a certain storage device is damaged, or the storage device is damaged, the corresponding Other storage devices for data take out data and store them in other storage devices, so as to ensure that any data has available data in the two storage devices at the same time. When reading data, read from one of the two storage devices. If a storage device storing data is damaged, read data directly from the other storage device.
[0052] In order to facilitate the understanding of the present invention, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0053] The hardware structure provided in Fig. 1 and Fig. 2 is the same a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com