A method to realize a global network real name system based on ID authentication
A technology of identification authentication and global network, which is applied in the field of global network real-name system, can solve problems such as insufficient scale of management users, influence on authentication efficiency, and inability to meet technical requirements, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
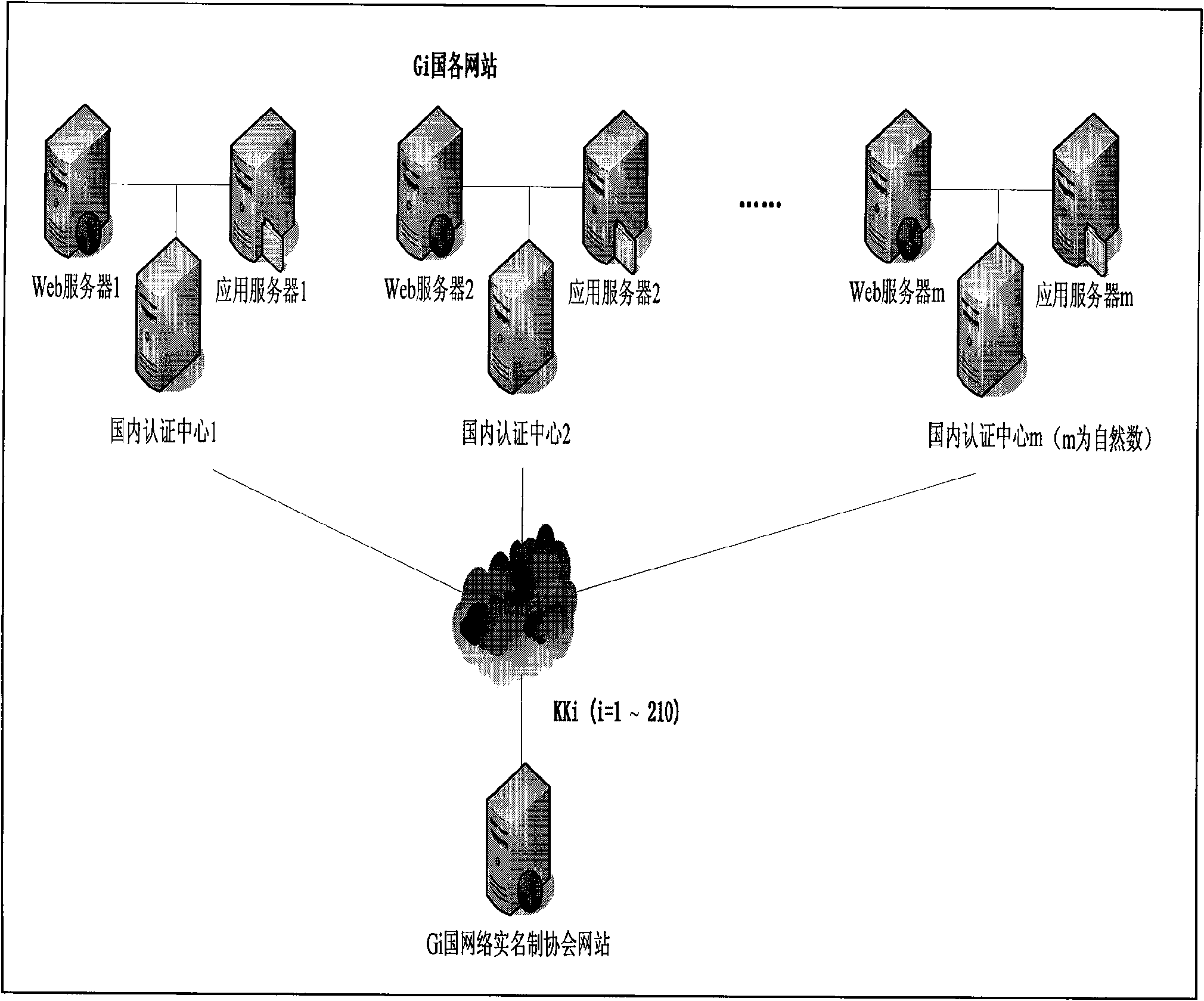
[0033] The implementation steps of the international network real-name system are described below in conjunction with the accompanying drawings:
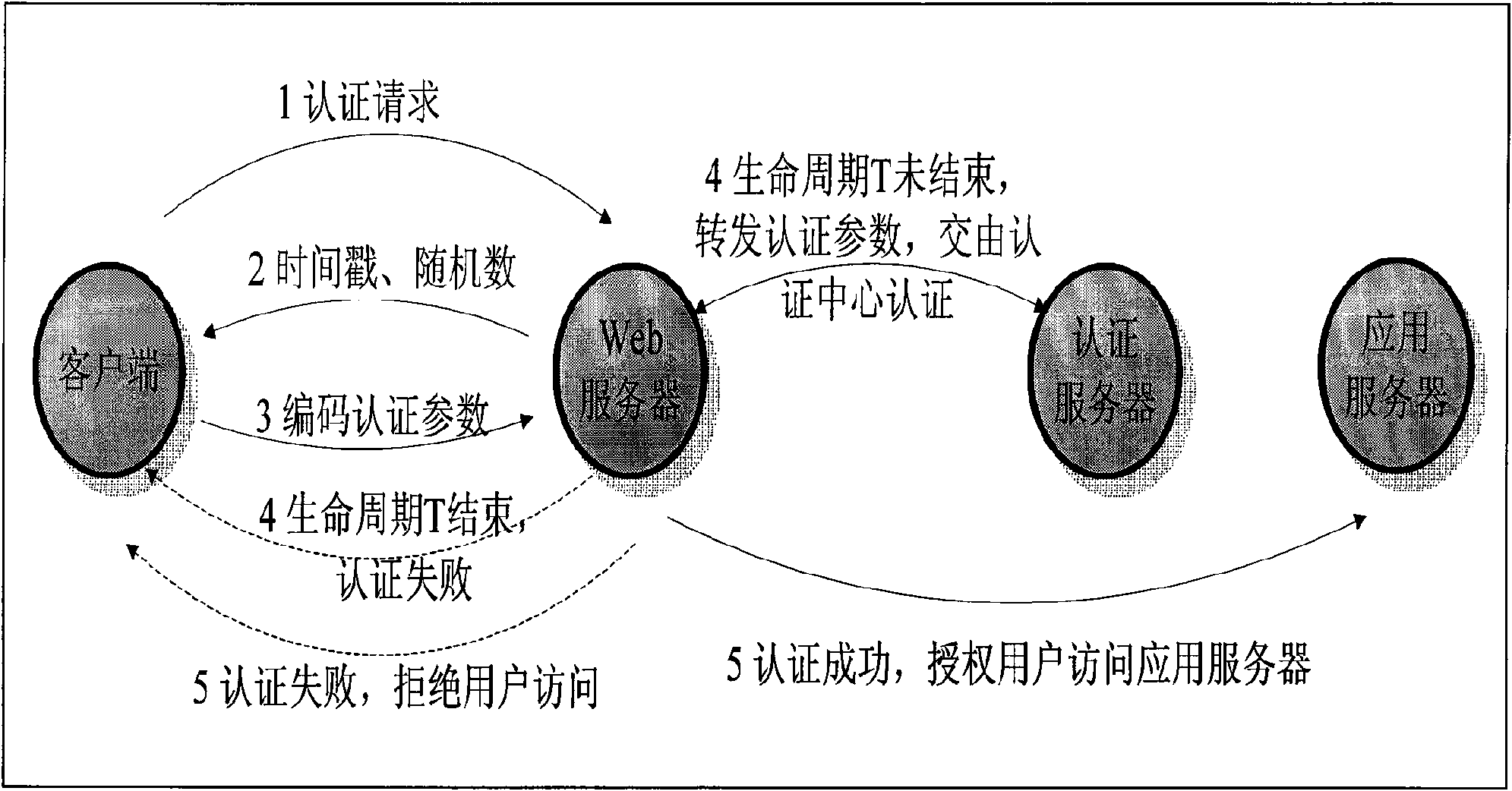
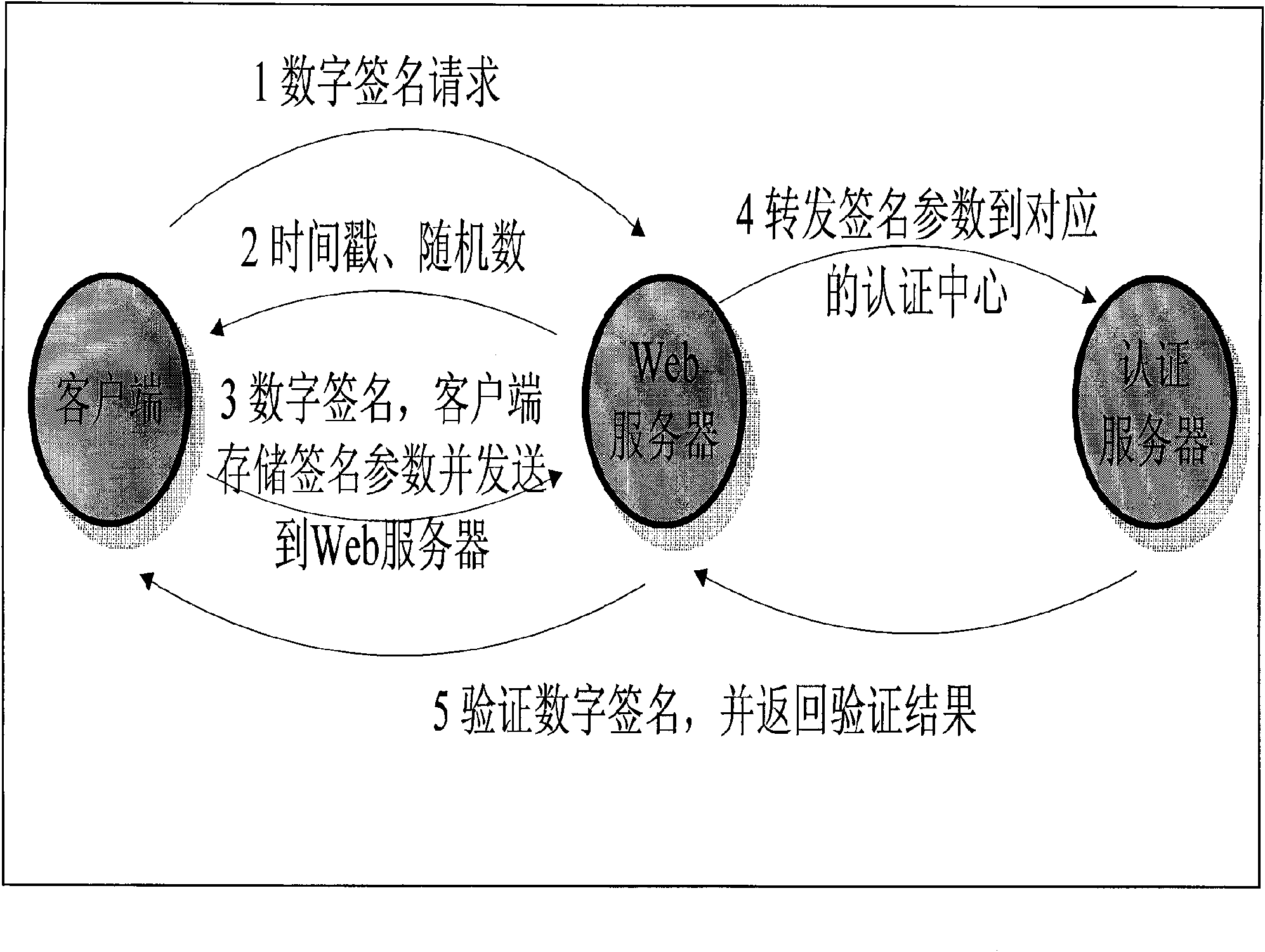
[0034] figure 1 : Explain that the implementation process of the identity authentication protocol in the network real-name system technology is as follows:
[0035] (1) An authentication request is issued by the client side;
[0036] (2) The time stamp and random number are generated by the WEB server and sent to the client, and the authentication life cycle T is calculated at the same time;
[0037] (3) After receiving the time stamp and random number, the client computer transmits it to the chip of the client-side hardware device, and selects the elements of the "key seed" table KK according to the symmetric key generation algorithm composed of time stamp and random number , select a group of symmetric key 1, use the symmetric key 1 to encrypt timestamp and random number to generate authentication password 1, and pass authentica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com