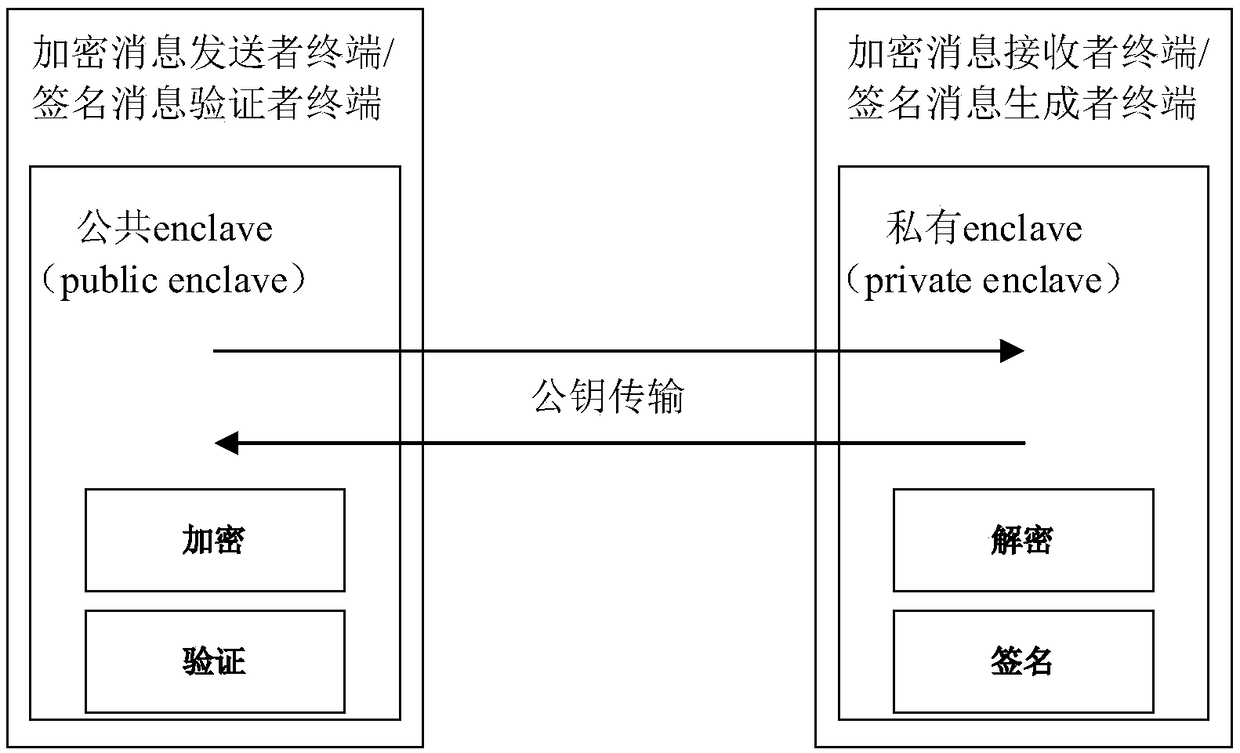
Public key password calculation method and system based on Intel SGX mechanism
A technology of public key cryptography and calculation method, which is applied in the directions of public keys, transmission systems, and digital transmission systems of secure communication, and can solve the problems of low performance and high performance overhead of public key cryptography systems.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] In order to make the objectives, technical solutions, and advantages of the present invention clearer, the present invention will be further described in detail through examples below.
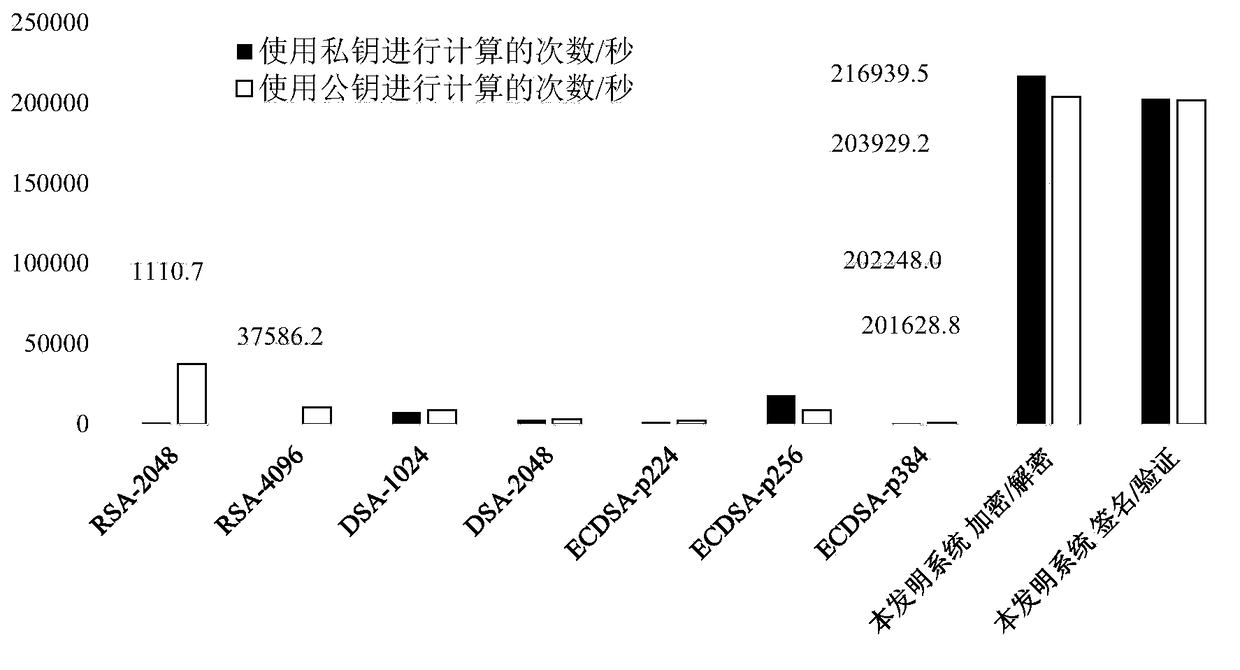
[0055] This example uses the AES-256-GCM algorithm to encrypt and decrypt, and the HMAC-SHA256 algorithm to sign and verify.
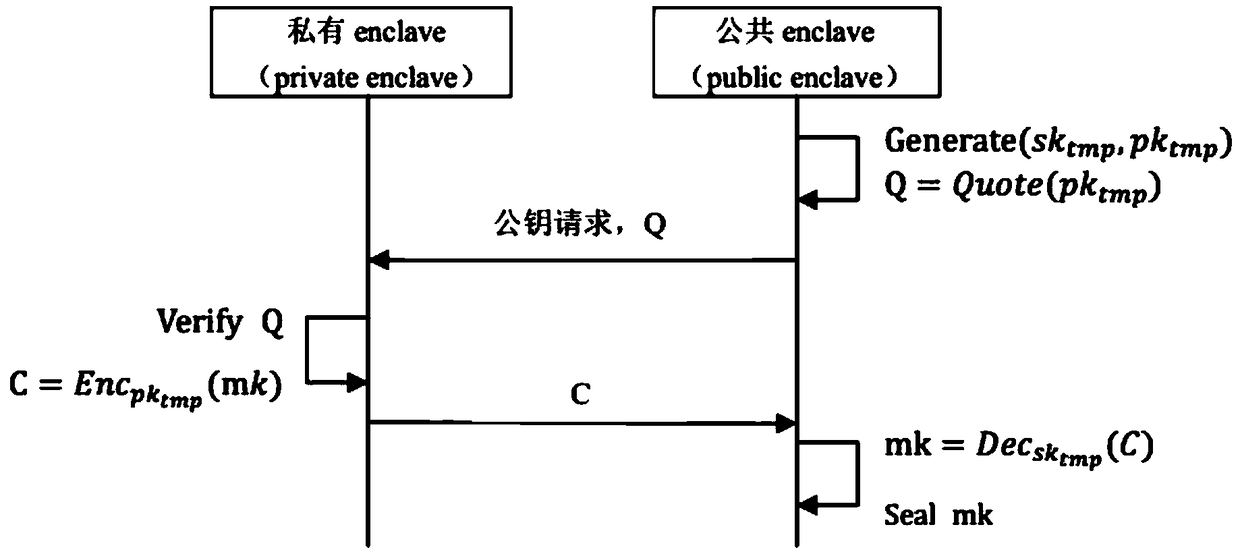
[0056] The Private enclave is launched for the first time, and a 256-bit private key mk is randomly generated.
[0057] Private enclave calls SGX sealed API to encrypt and store mk.
[0058] The Public enclave is launched for the first time, and it performs SGX remote authentication to request the public key from the Private enclave. Send a public key request to the Private enclave to generate a temporary key pair (sk tmp ,pk tmp ), issue SGX remote assertion proof Q=Quote(pk tmp ).
[0059] After receiving Q, Private enclave calls the enclave authentication API provided by Intel for verification. If the verification passes, use pk tmp The public key, namely mk, is e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com