Frequentness measuring method and system for security and privacy protection facing cloud data issuing
A technology for data release and measurement methods, which is applied in the research field of privacy protection to achieve the effect of convenient protection of privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
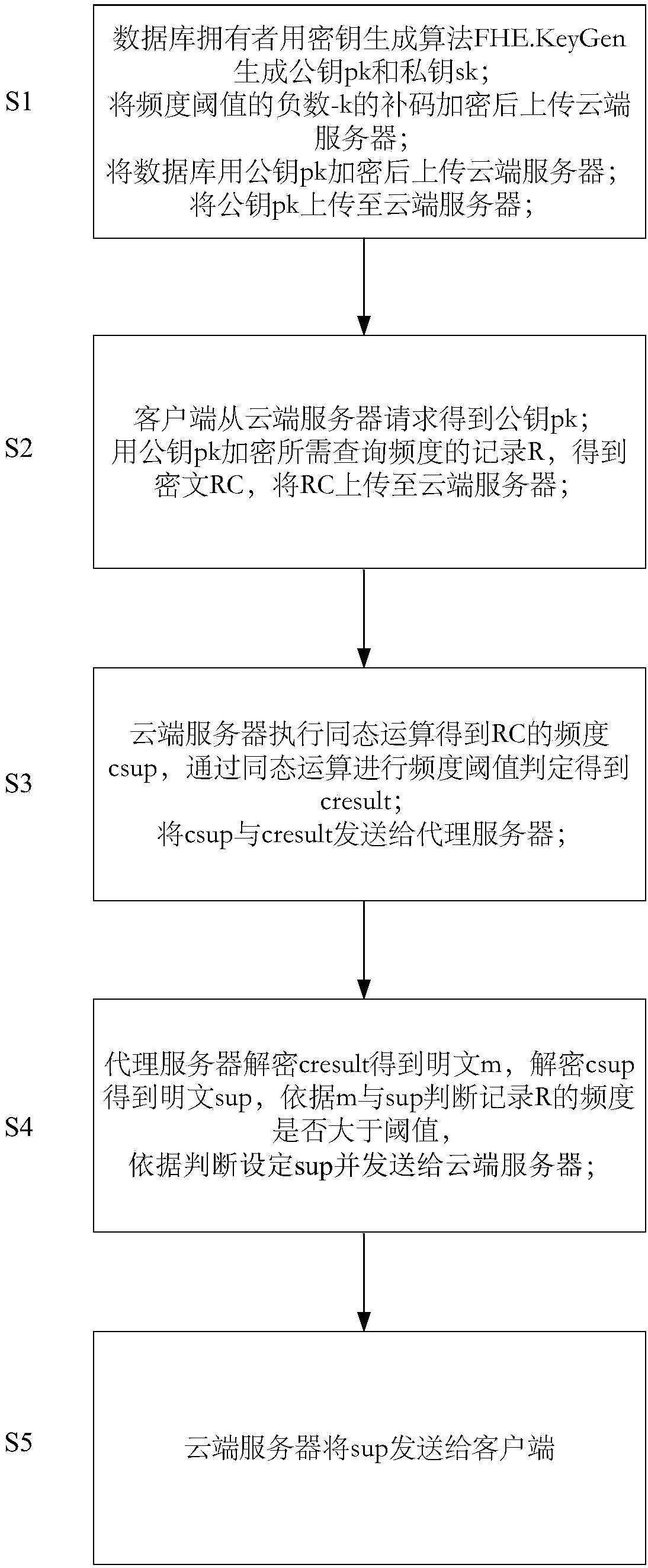
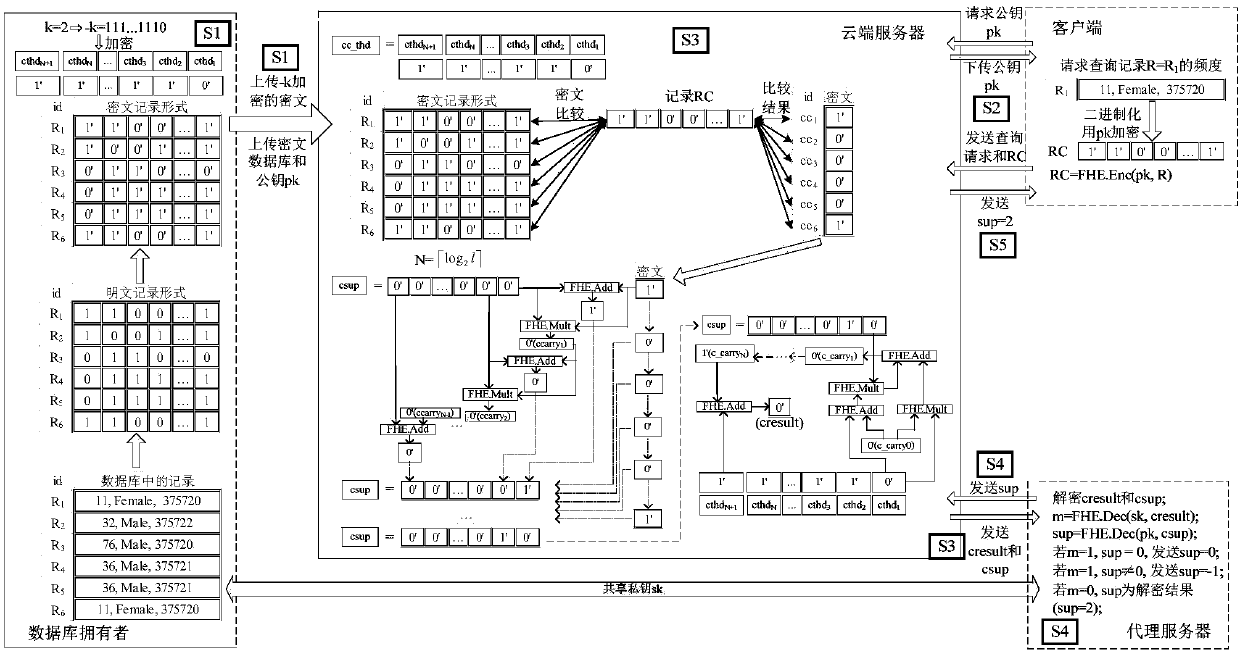
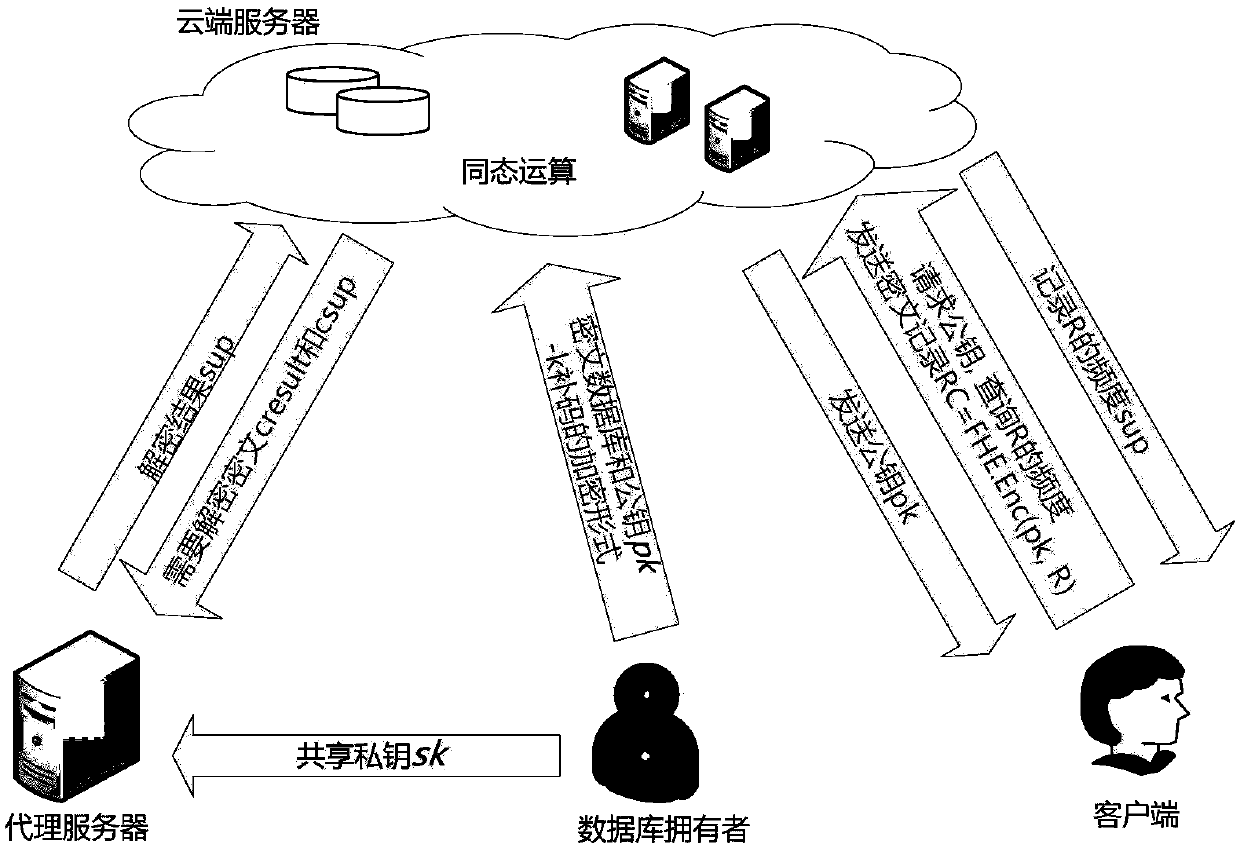
[0026] Before introducing the specific implementation method, first introduce some basic knowledge of fully homomorphic encryption. The homomorphic encryption scheme includes four probabilistic time polynomial algorithms HE={KeyGen, Encrypt, Decrypt, Evaluate}. The functions and processes of these four algorithms are as follows, and λ is a security parameter:
[0027] KeyGen is the key algorithm for generating schemes. Input the security parameter λ, and output the public key pk, private key sk and public evaluation key evk, evk is the public key information required to operate the Boolean circuit. (pk,evk,sk)←HE.KeyGen(1 λ ).
[0028] Encrypt is a ciphertext generation algorithm. Input the public key pk and single-bit information m∈{0,1}, and output a ciphertext c. c←HE.Enc pk (m).
[0029] Decrypt is to decrypt the ciphertext. Input the private key sk and a ciphertext c, and output the information m * ∈{0,1}. m * ←HE.Dec sk (c).
[0030] Evaluate is used to ensur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com