Data security control method and data security control platform
A technology of data security and management and control platform, which is applied in the field of data security, and can solve the problems of inability to know the security protection situation, irrationality, lack of linkage of security protection products, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
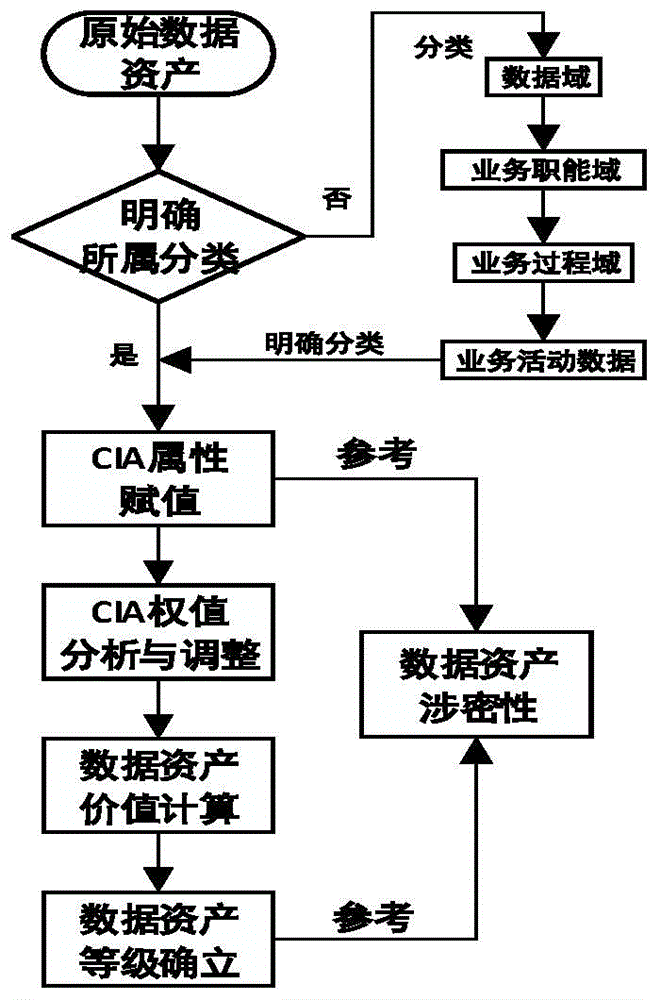
[0064] Embodiment 1 of the present invention: a data security management and control method, such as figure 1 shown, including the following steps:
[0065] 1. Divide data according to data category and confidentiality level
[0066] The data categories are divided according to the following methods: According to the content, type, department, business activity or business system relationship of the data itself, the data is divided into data categories, data subcategories, data subcategories and data, data categories , data subclass, data subclass and data respectively correspond to data domain, business function domain, business process domain and business activity.
[0067] Automatic classification and grading technology can be used, that is, natural language processing and text classification algorithms are used to associate data with one or more predefined categories according to the semantic characteristics and format of data content, and automatically assign specified d...
Embodiment 2
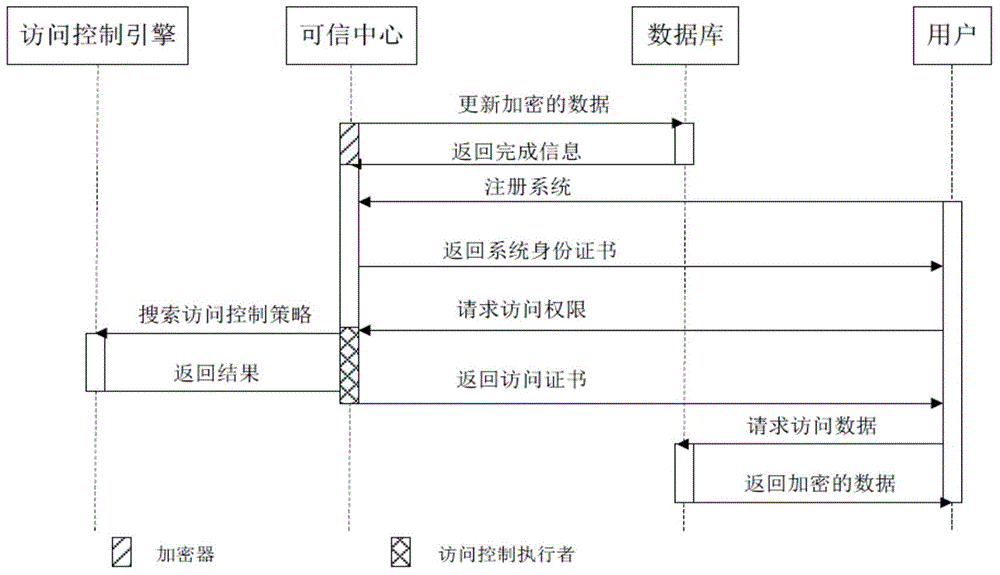
[0134] Embodiment 2 of the present invention: a data security management and control platform that implements the aforementioned method, such as Figure 5 shown, including:
[0135] Data classification and grading module 1, used to classify data according to data category and confidentiality level;
[0136] The security protection tool allocation module 2 is used to allocate corresponding security protection tools and carry out security protection for data encryption, identity authentication, access control, security audit, tracking and evidence collection according to the data division results;
[0137] The log collection and processing module 3 is used to collect log information generated by security protection tools and perform normalization processing to establish a security view of the full life cycle of data.
[0138] The data classification and grading module 1 includes a data classification module 11, which is used to classify data into major data categories, data sub...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com