Safety structure of all-around protecting mobile proxy network management application
A mobile agent and security technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of mobile agent fatality and mobile agent attack, and achieve the effect of preventing replay, comprehensive protection and improving flexibility.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
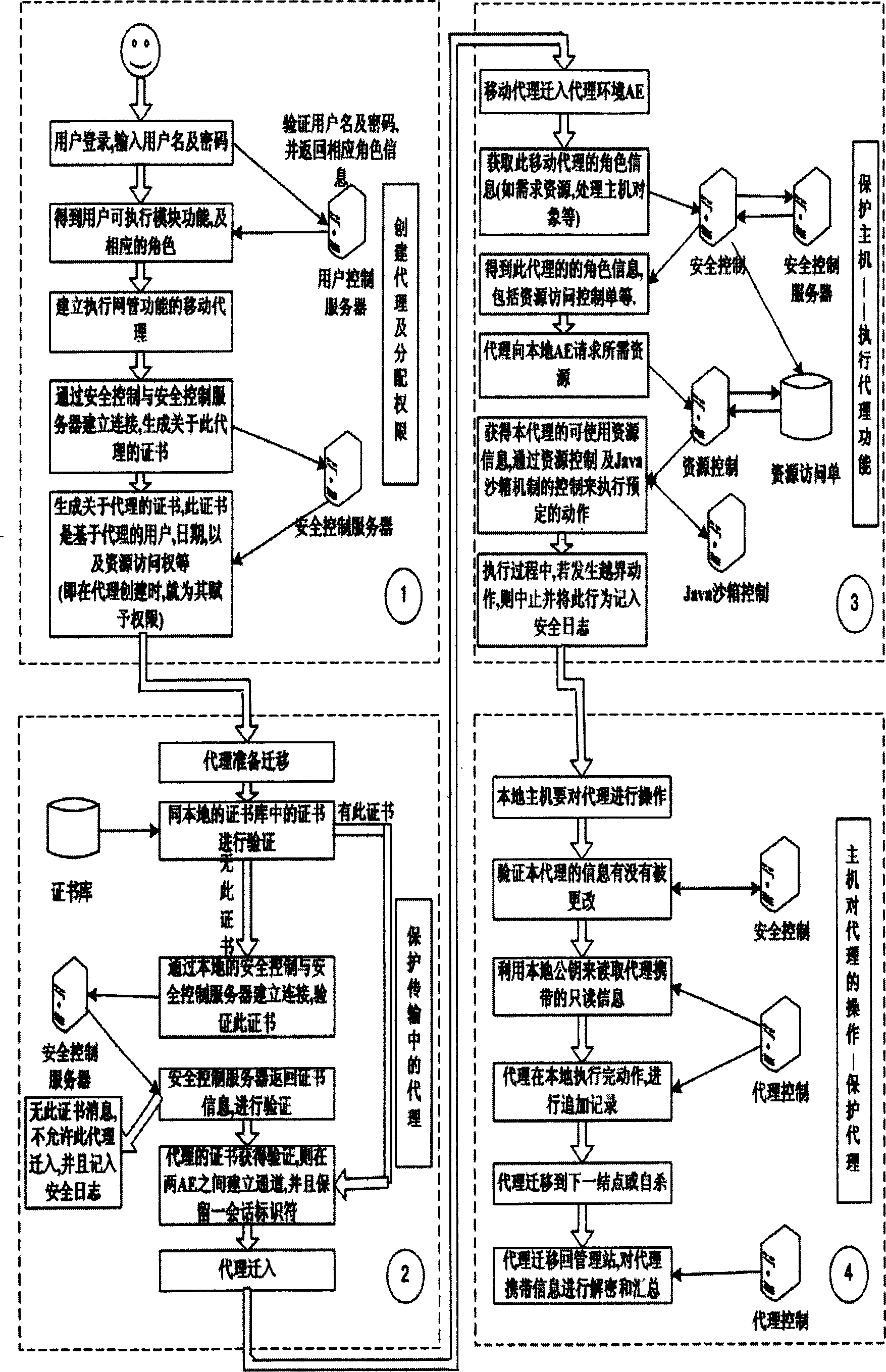
[0074] The present invention will be described in more detail according to the drawings and implementation examples below.
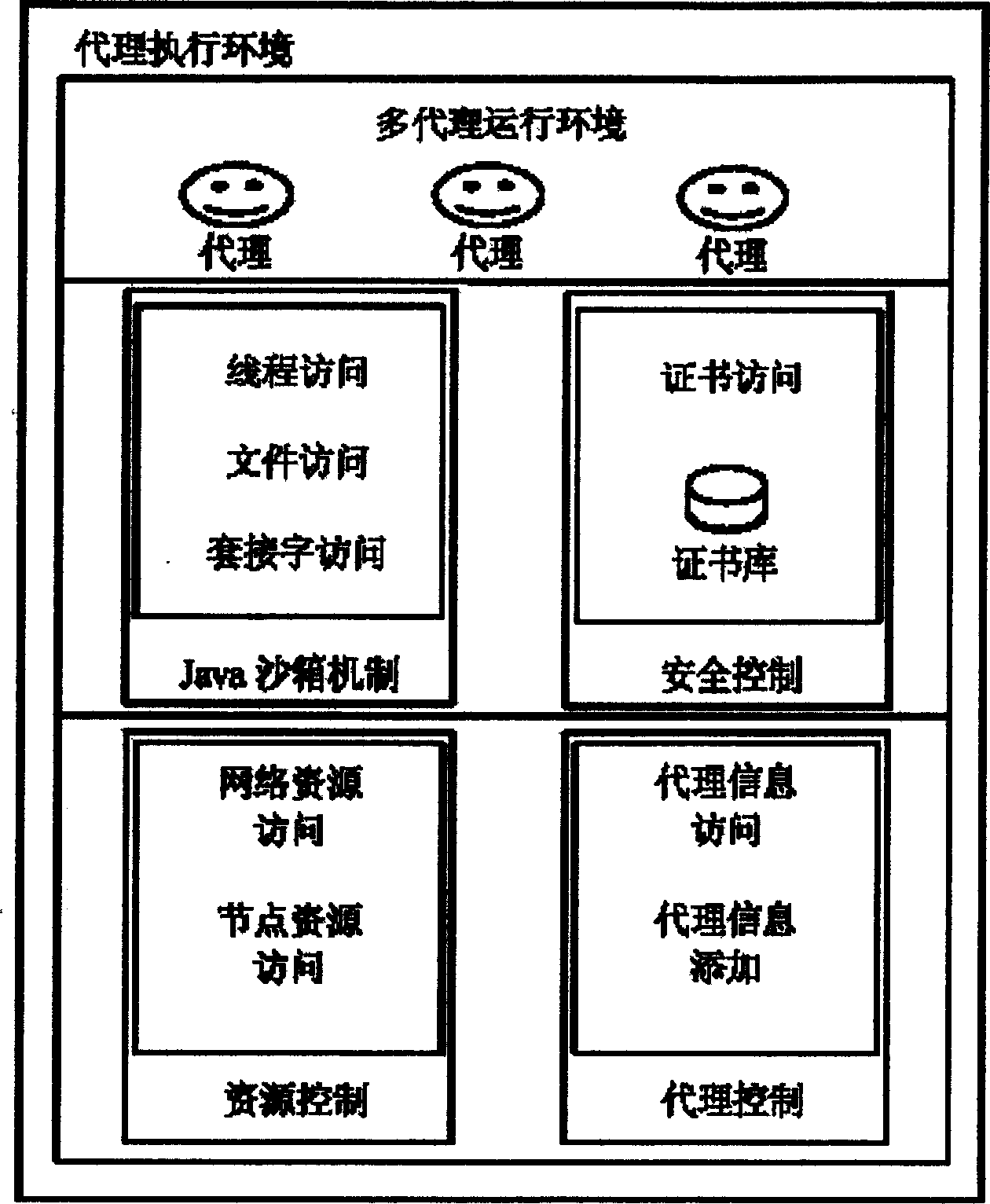
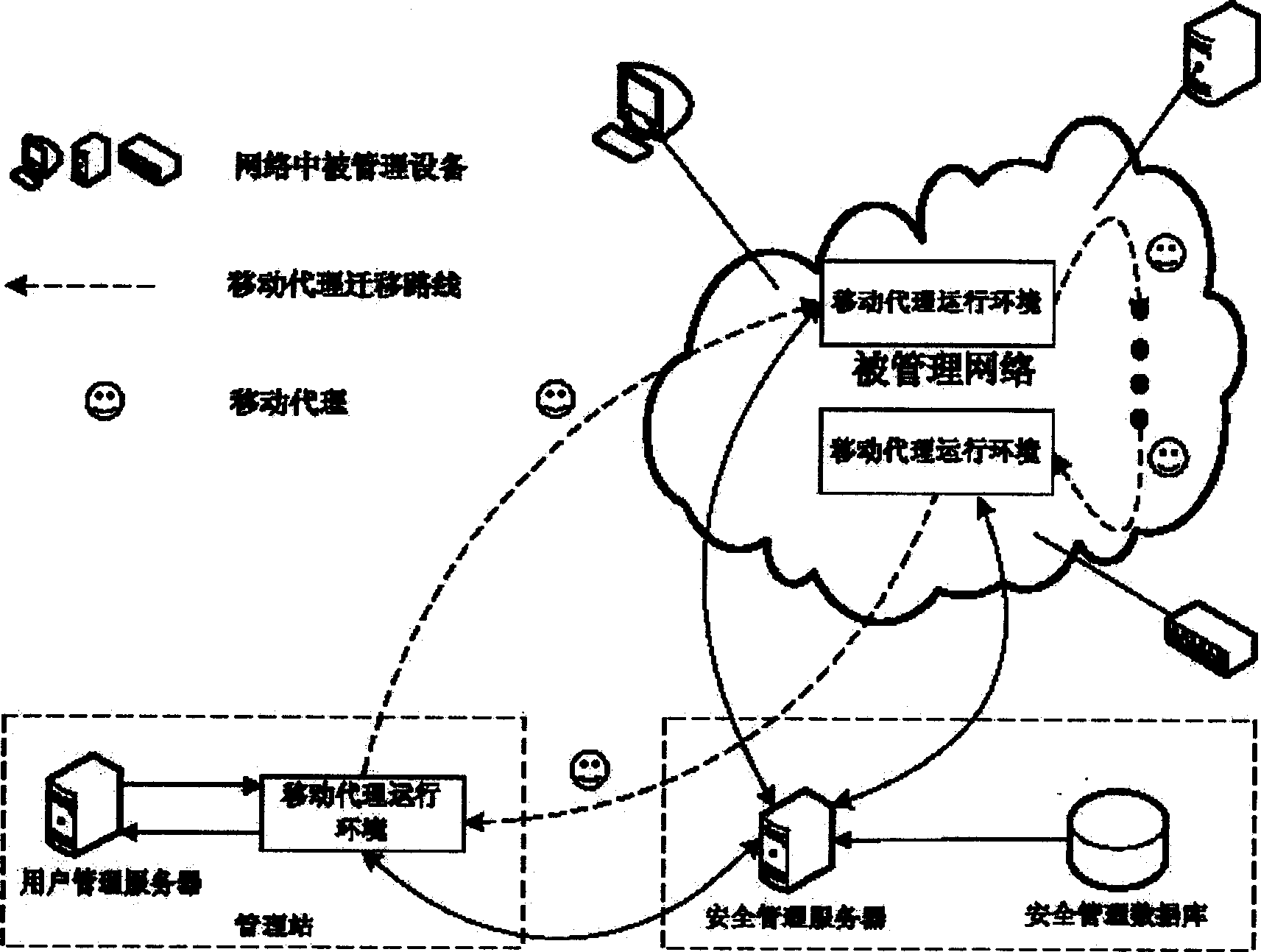
[0075] (1) Protect the transmission of the mobile agent
[0076] When an AE (Agent Environment, Agent Execution Environment) is to be sent to a mobile agent before it is sent to other AEs, we hope that the two AEs will authenticate each other and establish a secure channel, and this secure channel can also be used in future communications , there is no need to repeat the authentication process again.
[0077] And it is hoped that the two channels adopt the same security mechanism so as to facilitate implementation. Therefore, a secure channel is established using the SSL3.0 (Secure Socket Layer, a secure communication protocol) model in which both parties are authenticated.
[0078] The SSL3.0 protocol uses public key certificates to authenticate each other, establishes a common session key, and uses symmetric encryption algorithms to encrypt and prote...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com