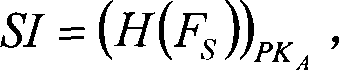Software real name authentication system and its safe checking method
A technology of real-name authentication and software, applied in computer security devices, instruments, electrical digital data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be described in detail below through specific embodiments and accompanying drawings.
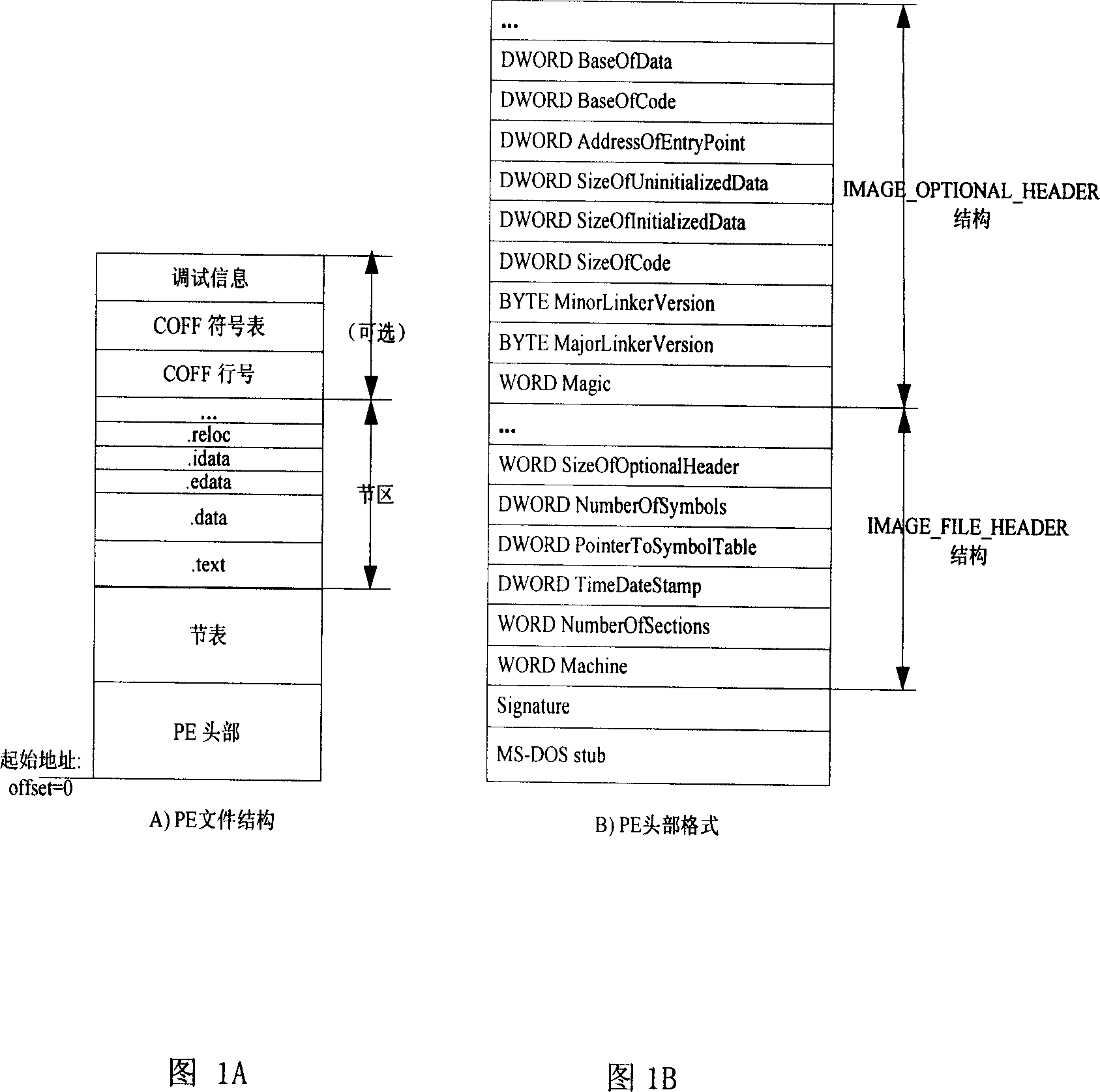
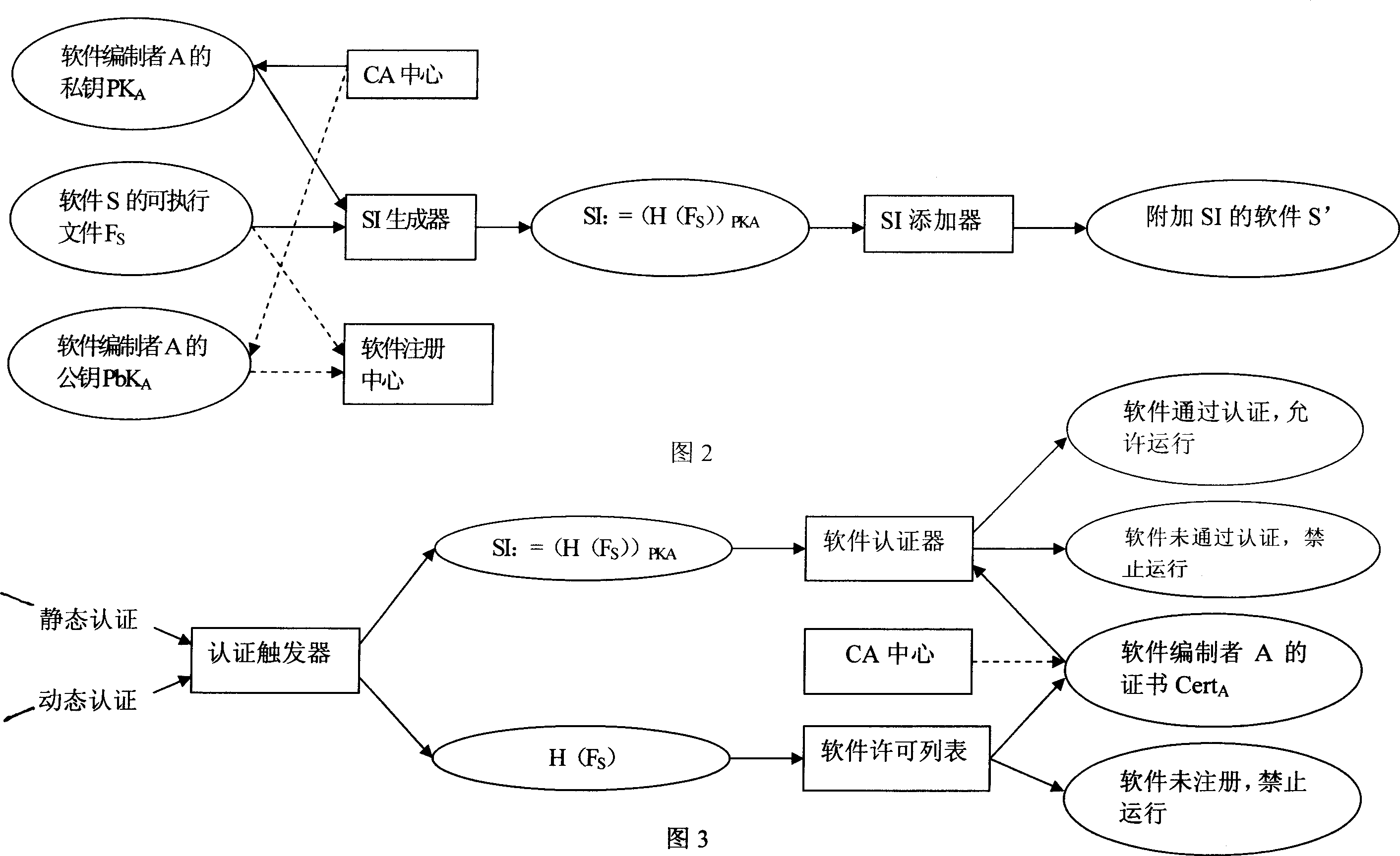
[0040] The first thing to explain is that in a modern computer system, the source program is processed by a compiler and an assembler to generate an object file, and multiple object files are then combined into an executable file by a linker. PortableExecutable (PE) is the object file format used by Windows NT technology. Windows executable files (.exe) or dynamic link library files (.dll) are stored in PE format, so this manual mainly proposes A software real-name mechanism realization scheme for Windows operating system, and the system security is analyzed and discussed. As shown in FIGS. 1A and 1B , the loader of the operating system will process the PE file during execution, so as to load the code, data, and resources of the program into the memory. Therefore, to implement a security mechanism based on software authentication in the Windows operating s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com