Patents
Literature
44 results about "Supplier identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
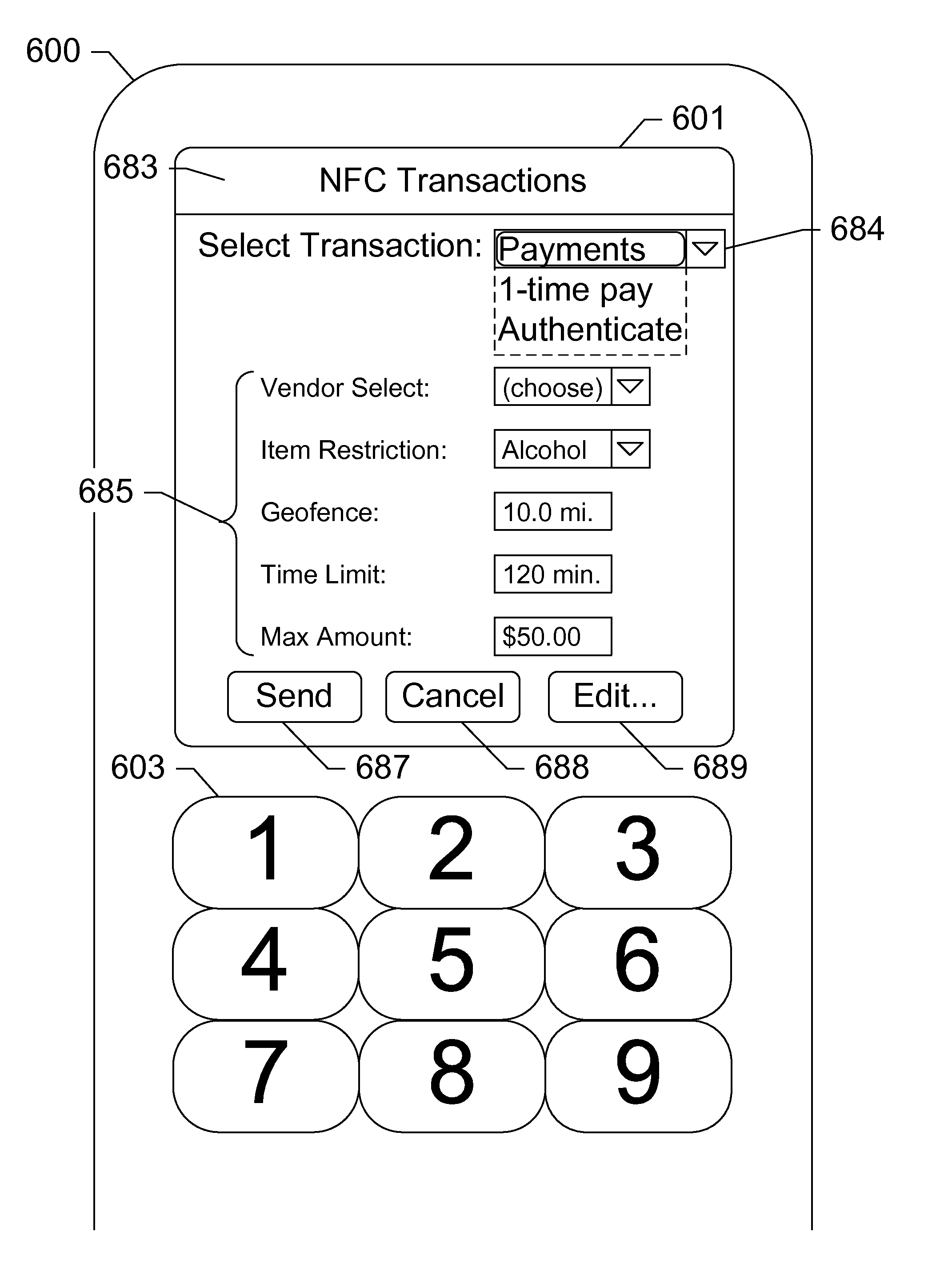
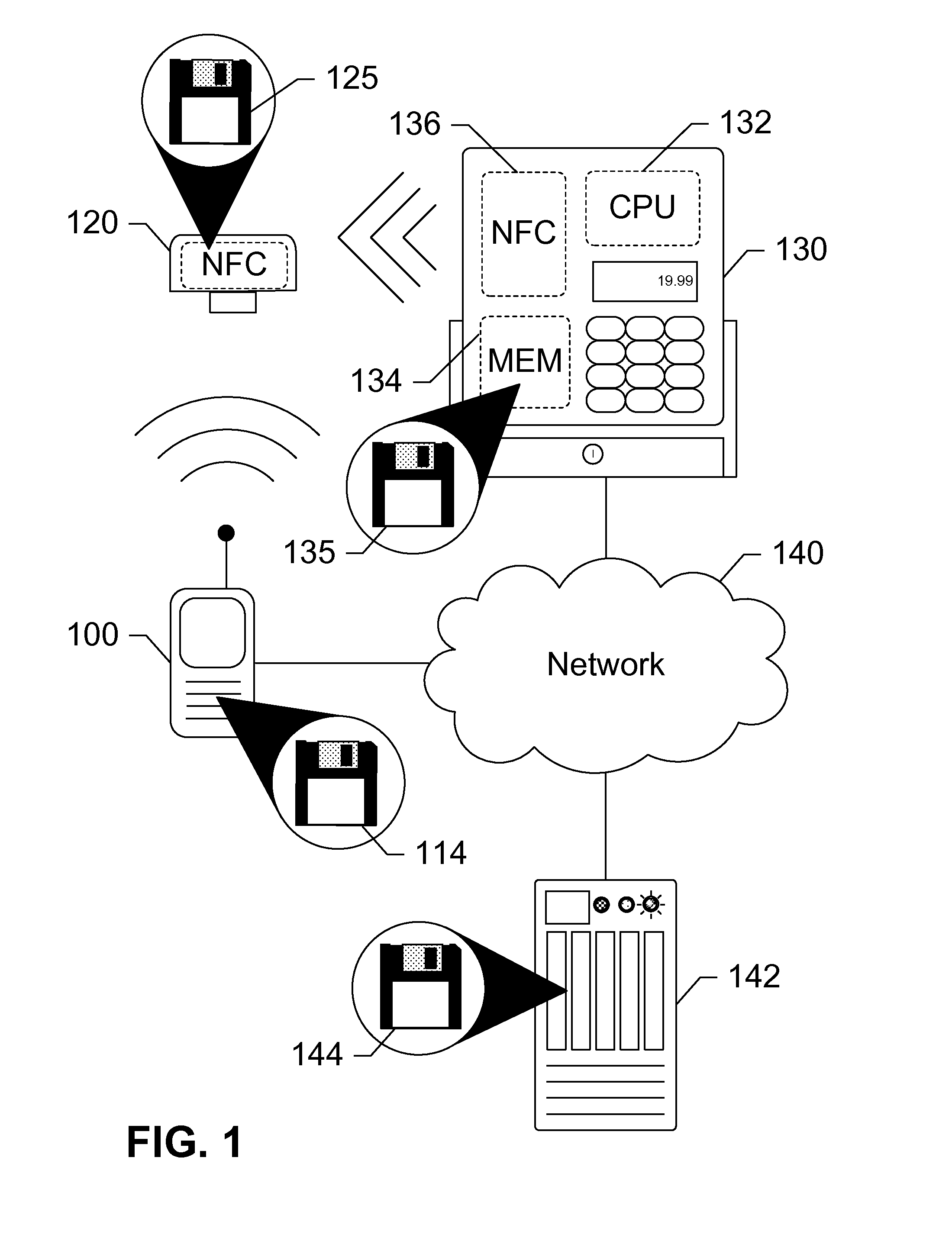
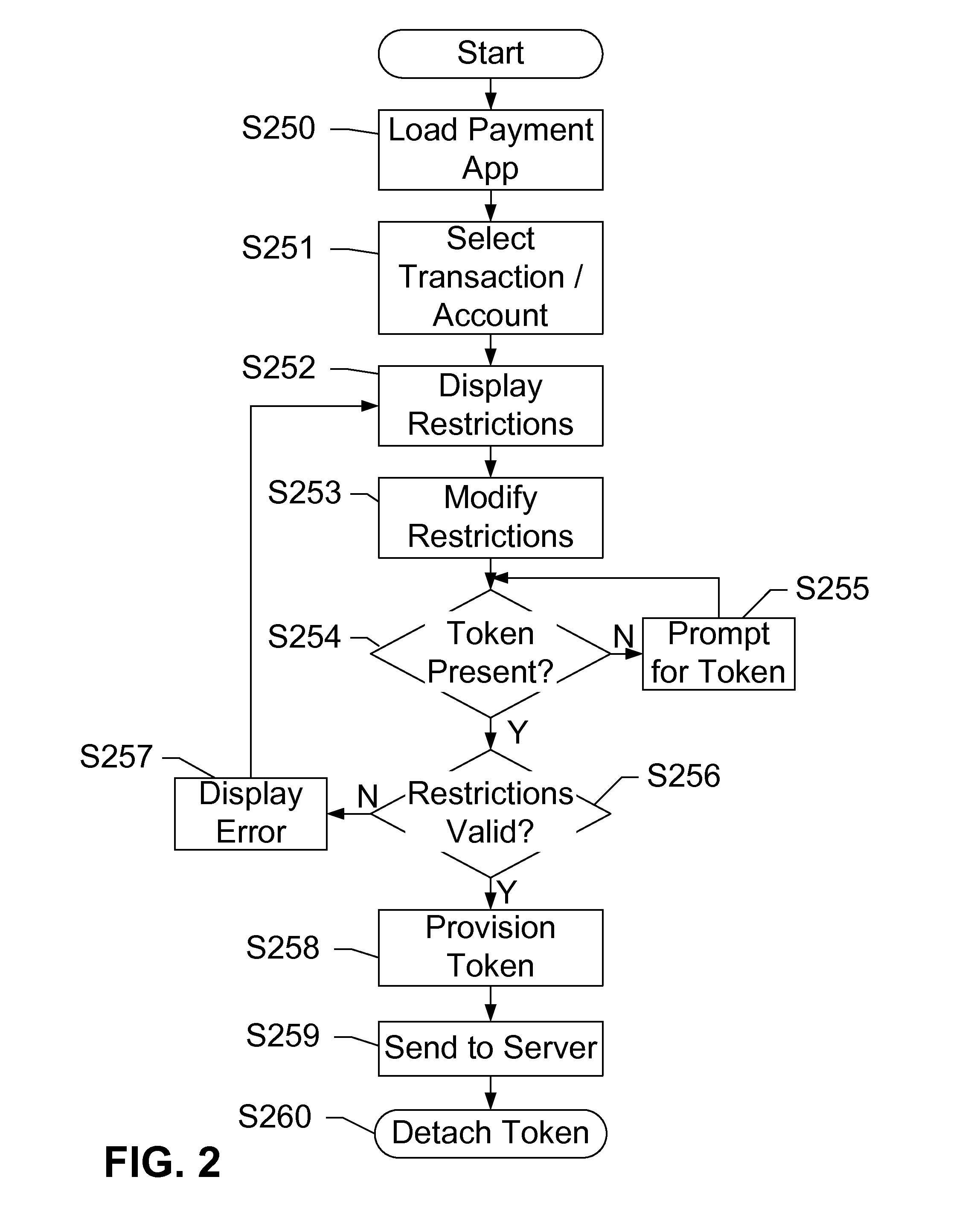
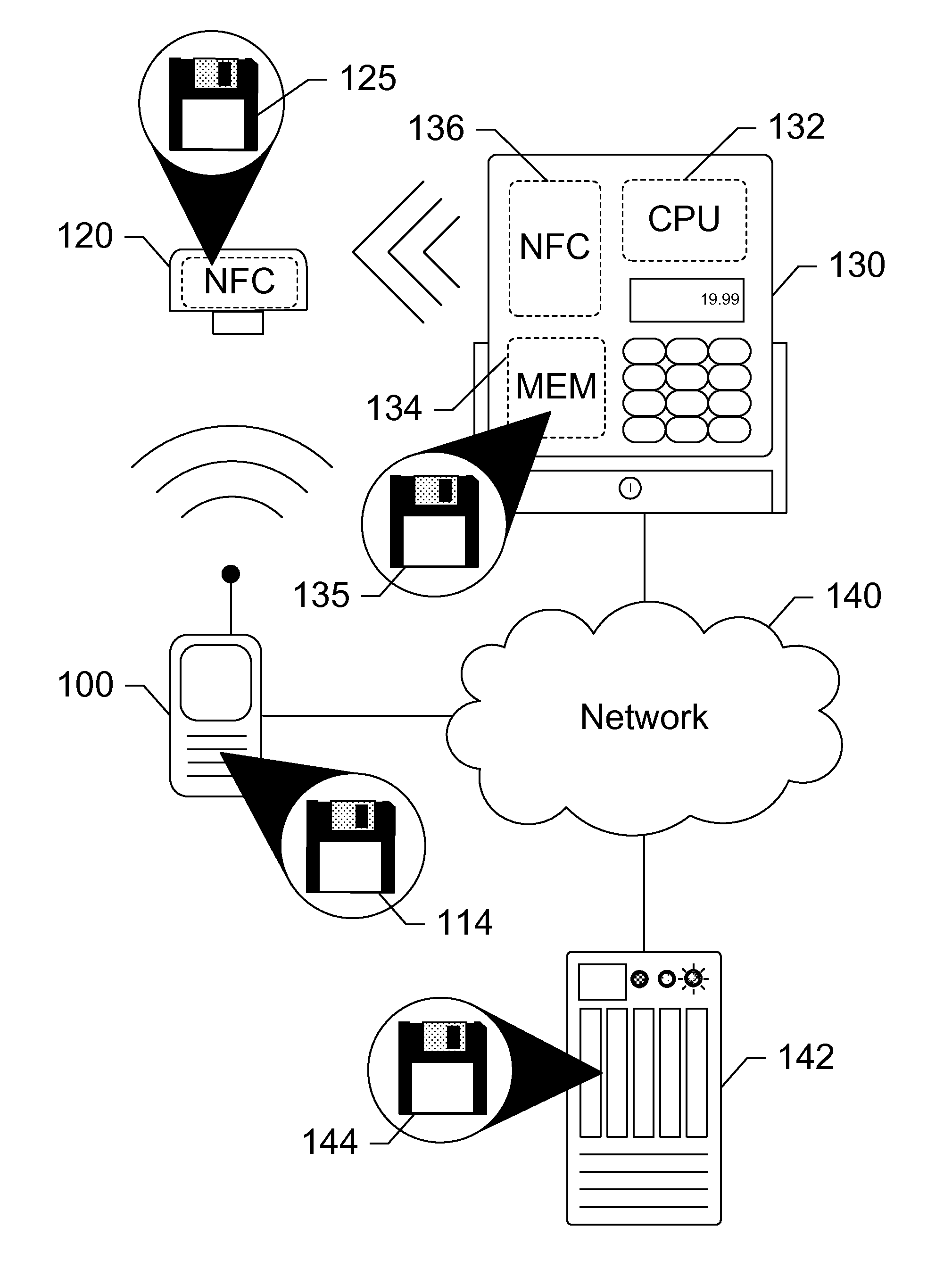
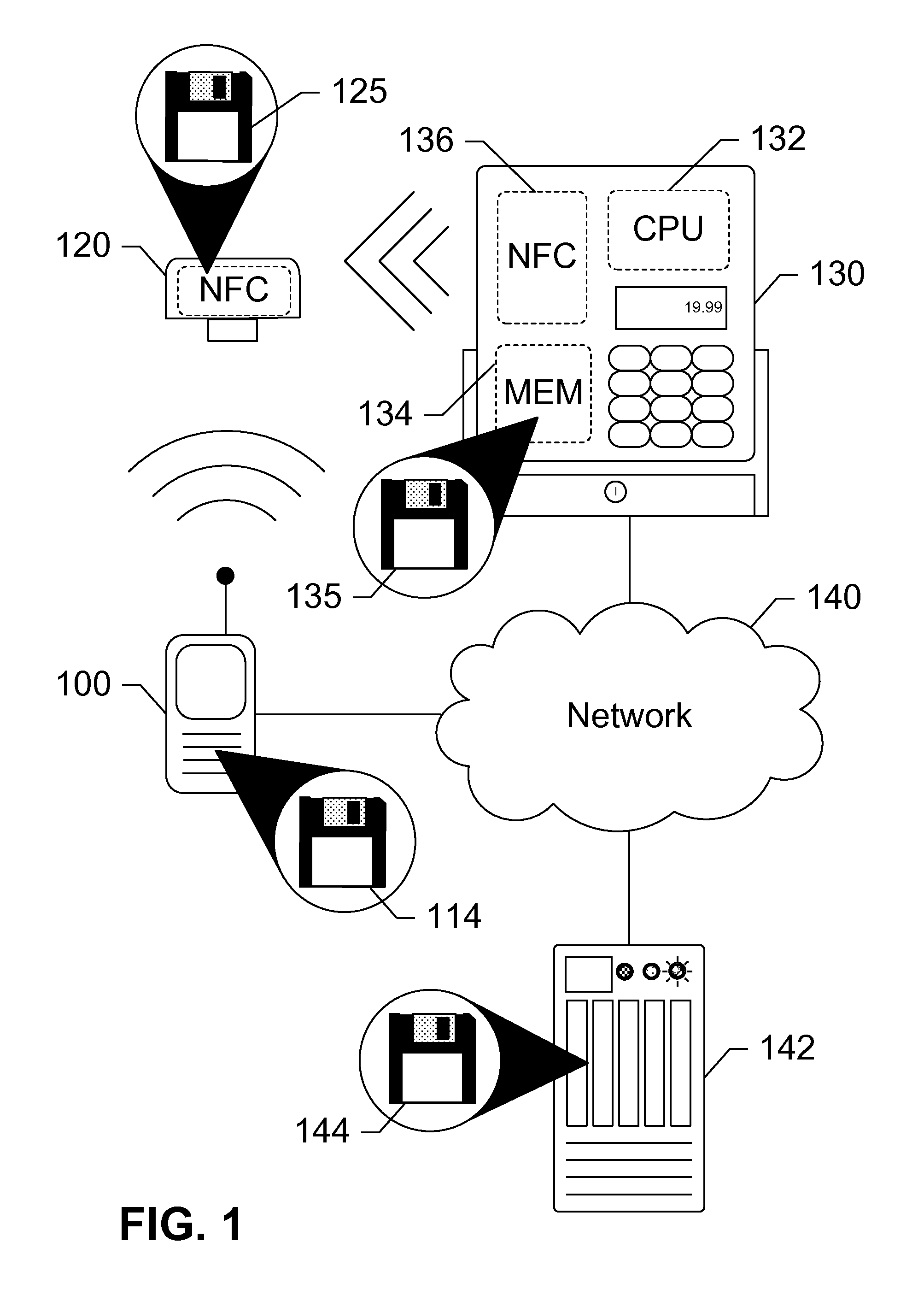
Security token for mobile near field communication transactions
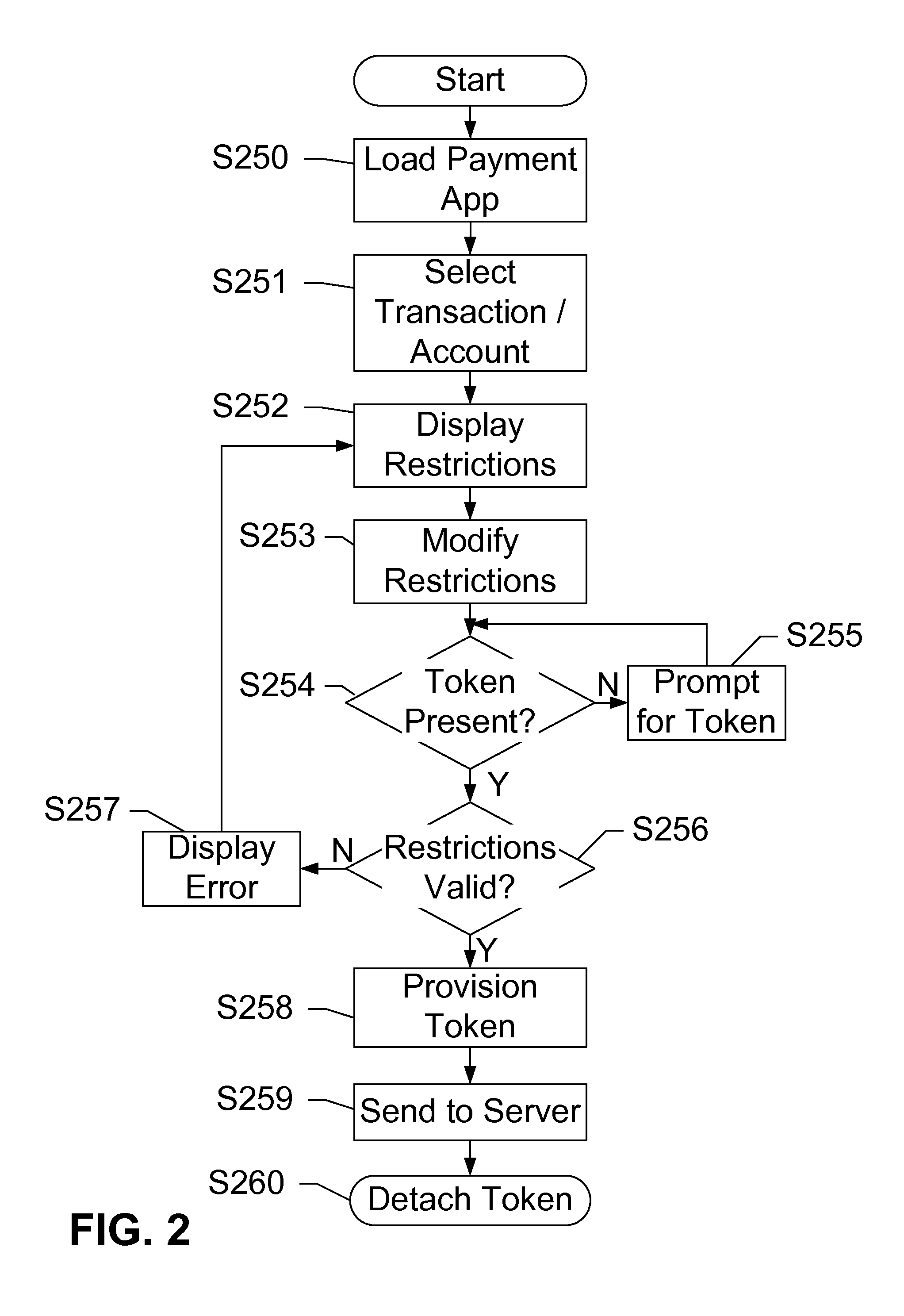
Devices, systems, and methods are disclosed which relate to an NFC-enabled security token that is removably coupled to a mobile device. The security token may be provisioned with the information by the mobile device, then decoupled from the mobile device and used to authenticate the user or perform a transaction at a POS terminal equipped with an NFC reader. The security token includes logic for user-controlled restrictions on allowable purchases, such as payment limits, timeouts, vendor identifiers, allowed purchases, and location-based restrictions. The security token is further equipped with “self destruct” security features, such as deactivating itself or erasing any sensitive information upon being unable to contact the mobile device for a specified duration, or being subject to an unauthorized or restricted transaction, until such time as it is re-coupled to the mobile device.
Owner:AT&T INTPROP I LP
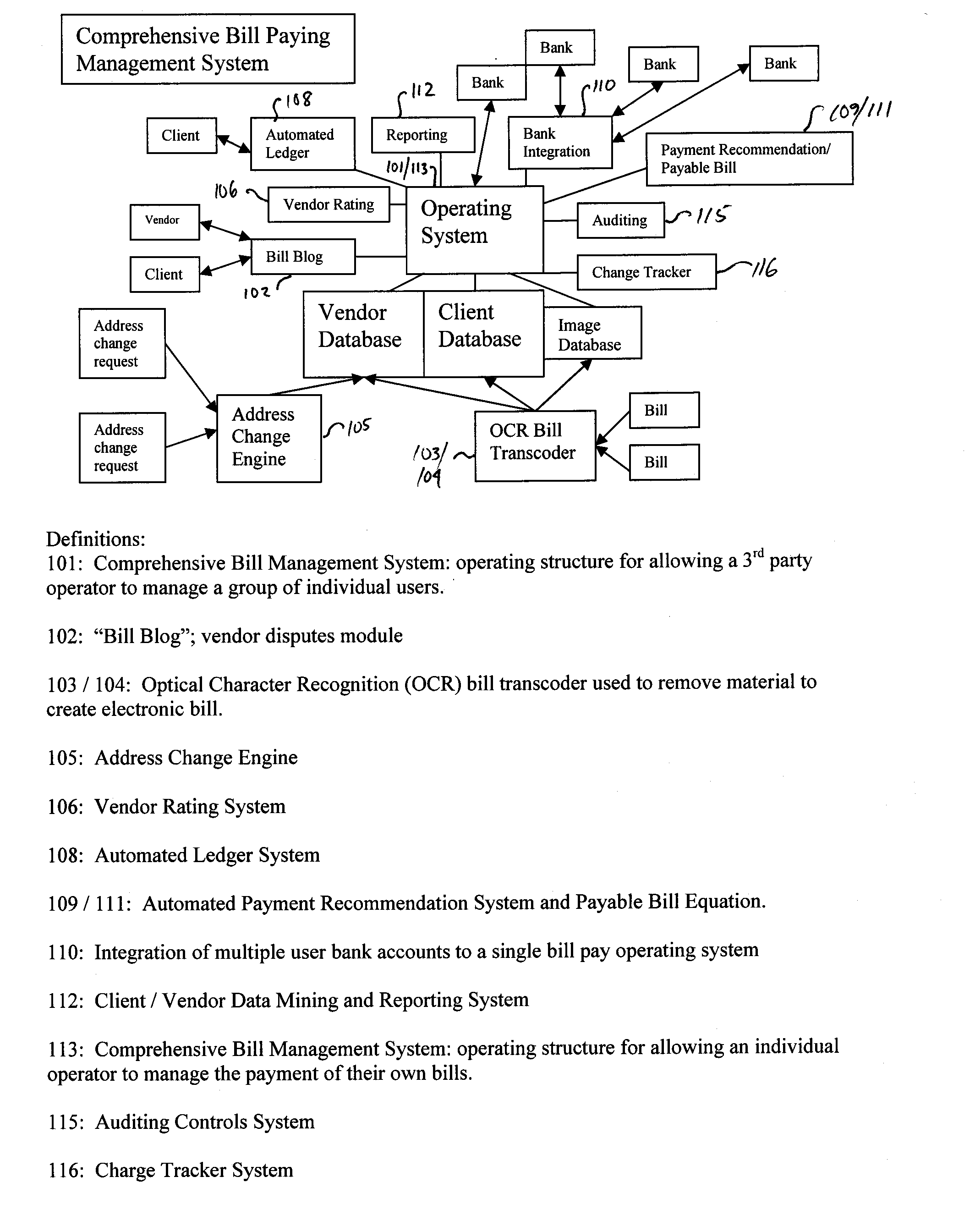
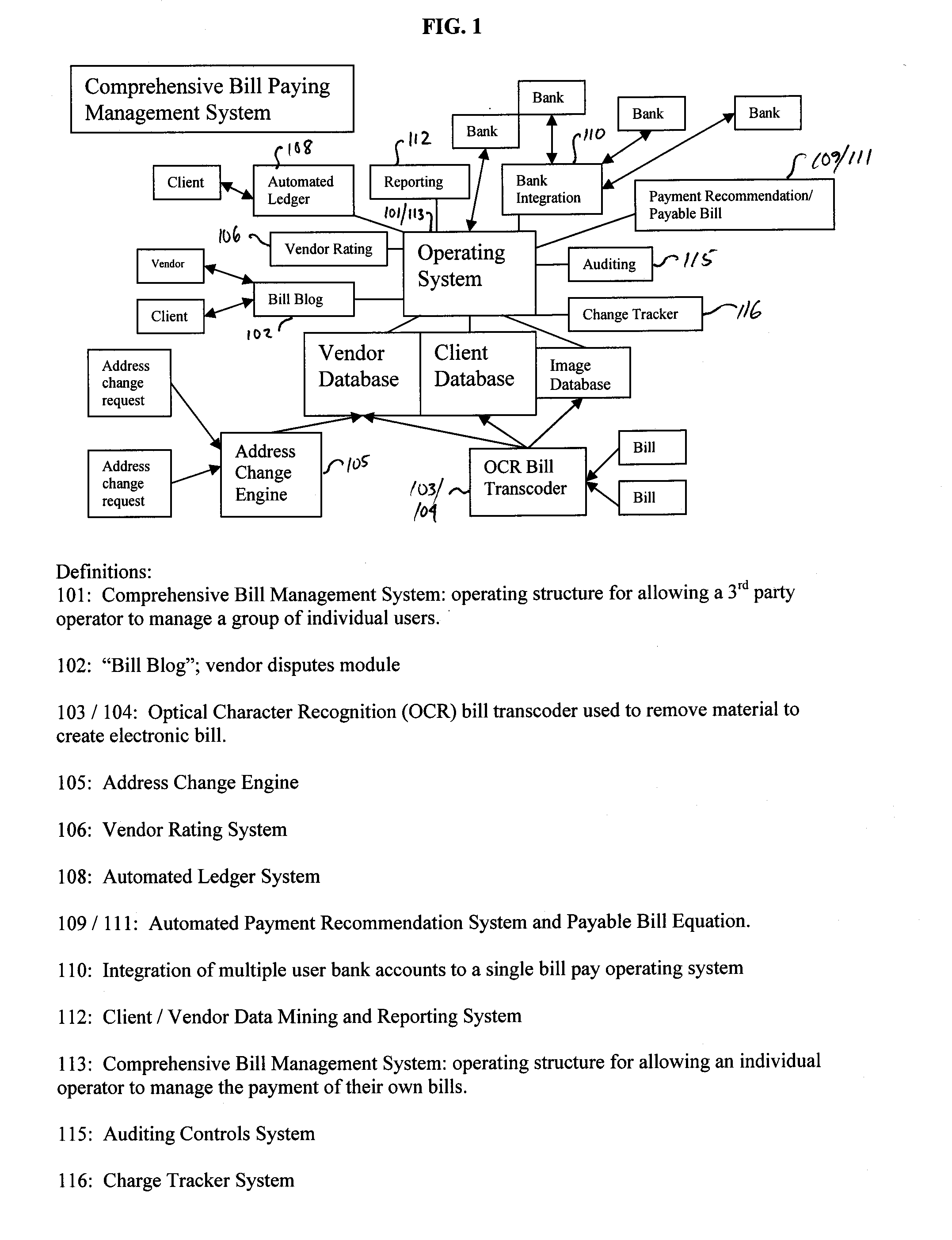
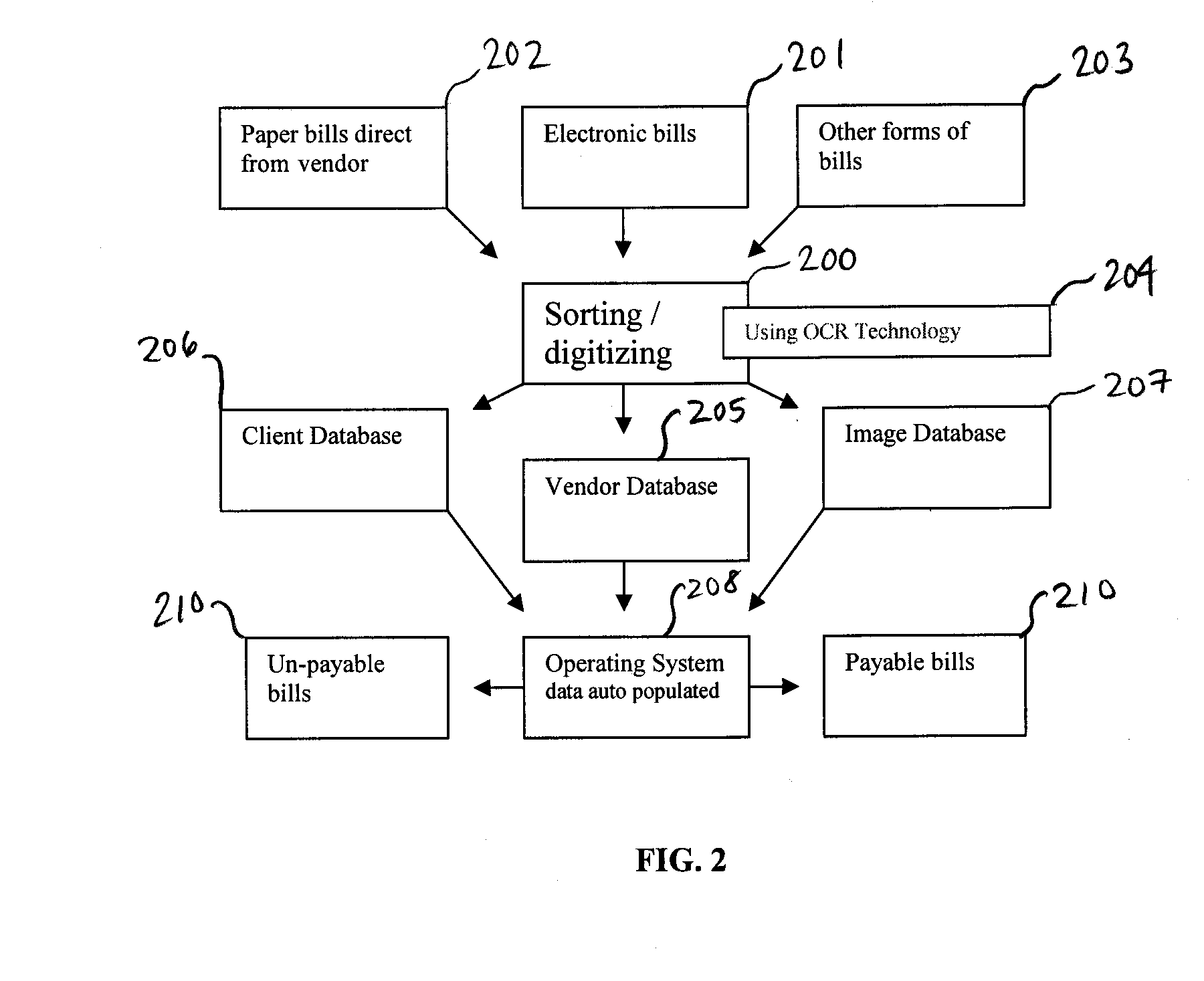
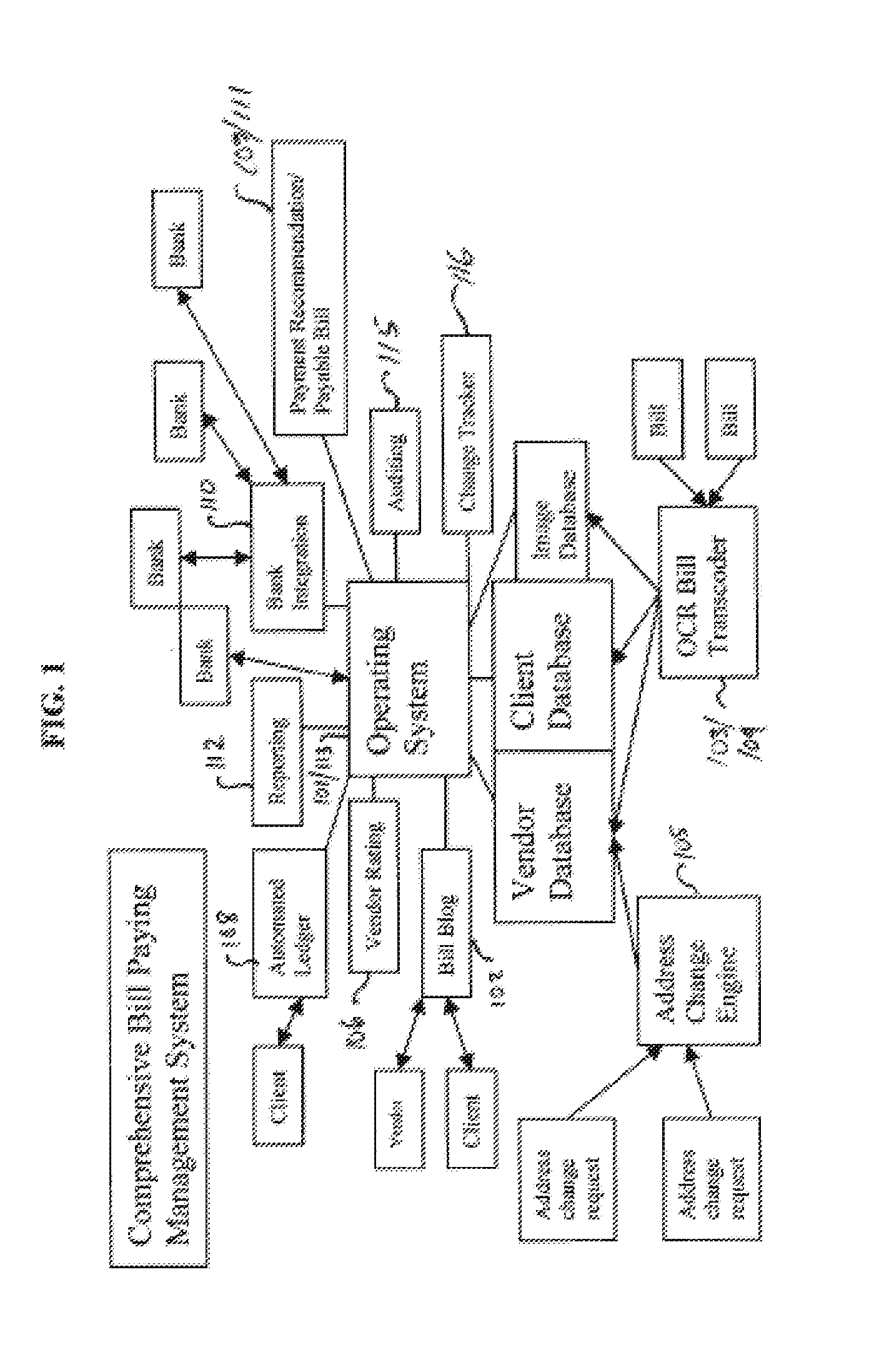
Bill paying systems and associated methods
Methods of paying user bills on behalf of a user are described. In one embodiment, the method includes receiving from a vendor a user bill having a user identifier, a vendor identifier, and a bill amount. The method further includes obtaining the user identifier, the vendor identifier, and the bill amount, associating the bill with the user based on the user identifier, and associating the bill with the vendor based on the vendor identifier. The method further includes determining whether the bill is payable, which includes comparing the bill to stored bill data associated with the user and the vendor. When the bill is payable, the method further includes obtaining funds from an account of the user, dispersing funds to the vendor to pay the bill and storing an indication of the paying of the bill.
Owner:PREMIER PAYMENT SERVICES
Security Token for Mobile Near Field Communication Transactions
ActiveUS20130124346A1Cryptography processingBuying/selling/leasing transactionsPaymentFinancial transaction
Devices, systems, and methods are disclosed which relate to an NFC-enabled security token that is removably coupled to a mobile device. The security token may be provisioned with the information by the mobile device, then decoupled from the mobile device and used to authenticate the user or perform a transaction at a POS terminal equipped with an NFC reader. The security token includes logic for user-controlled restrictions on allowable purchases, such as payment limits, timeouts, vendor identifiers, allowed purchases, and location-based restrictions. The security token is further equipped with “self destruct” security features, such as deactivating itself or erasing any sensitive information upon being unable to contact the mobile device for a specified duration, or being subject to an unauthorized or restricted transaction, until such time as it is re-coupled to the mobile device.
Owner:AT&T INTPROP I L P
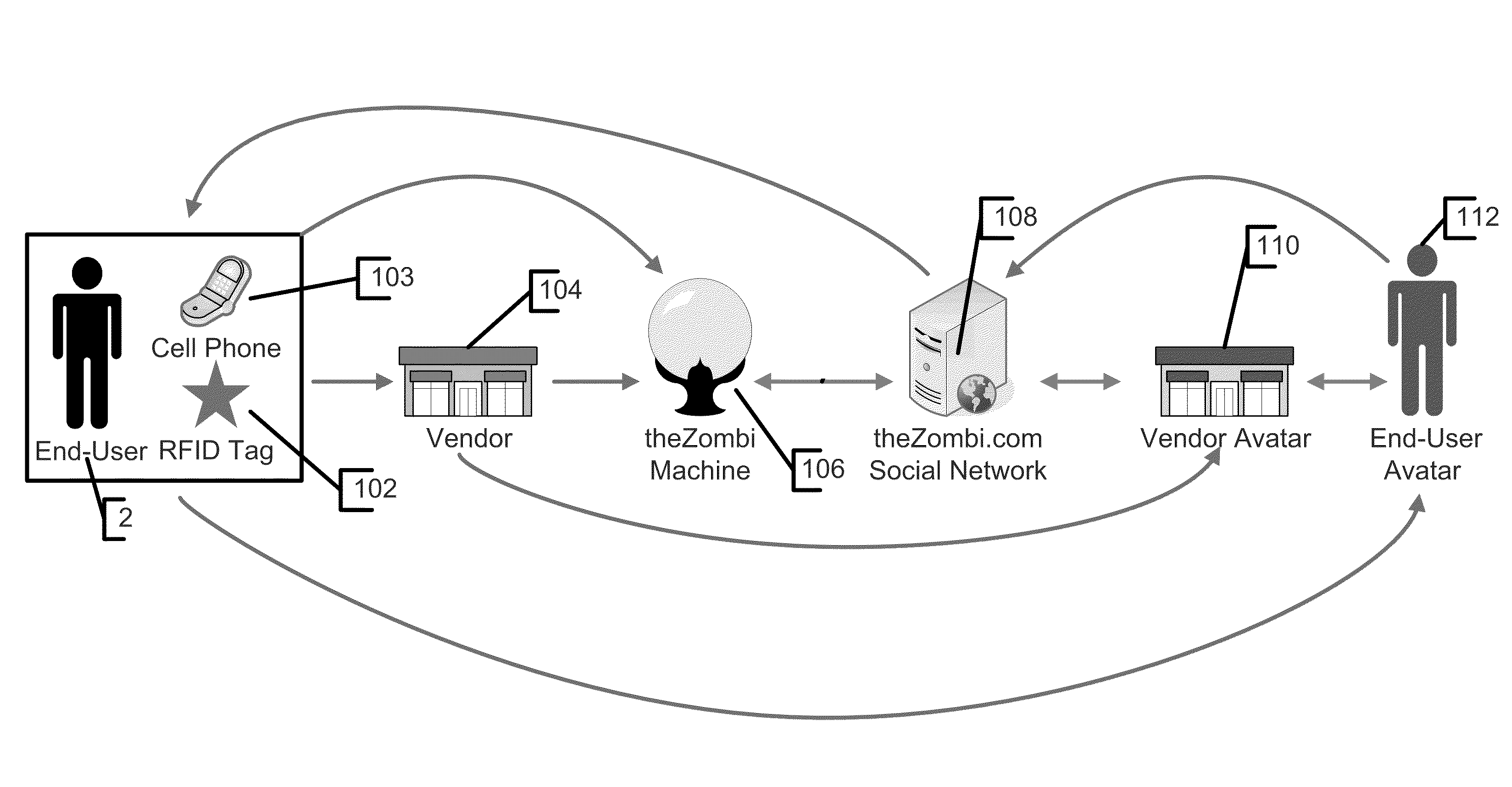
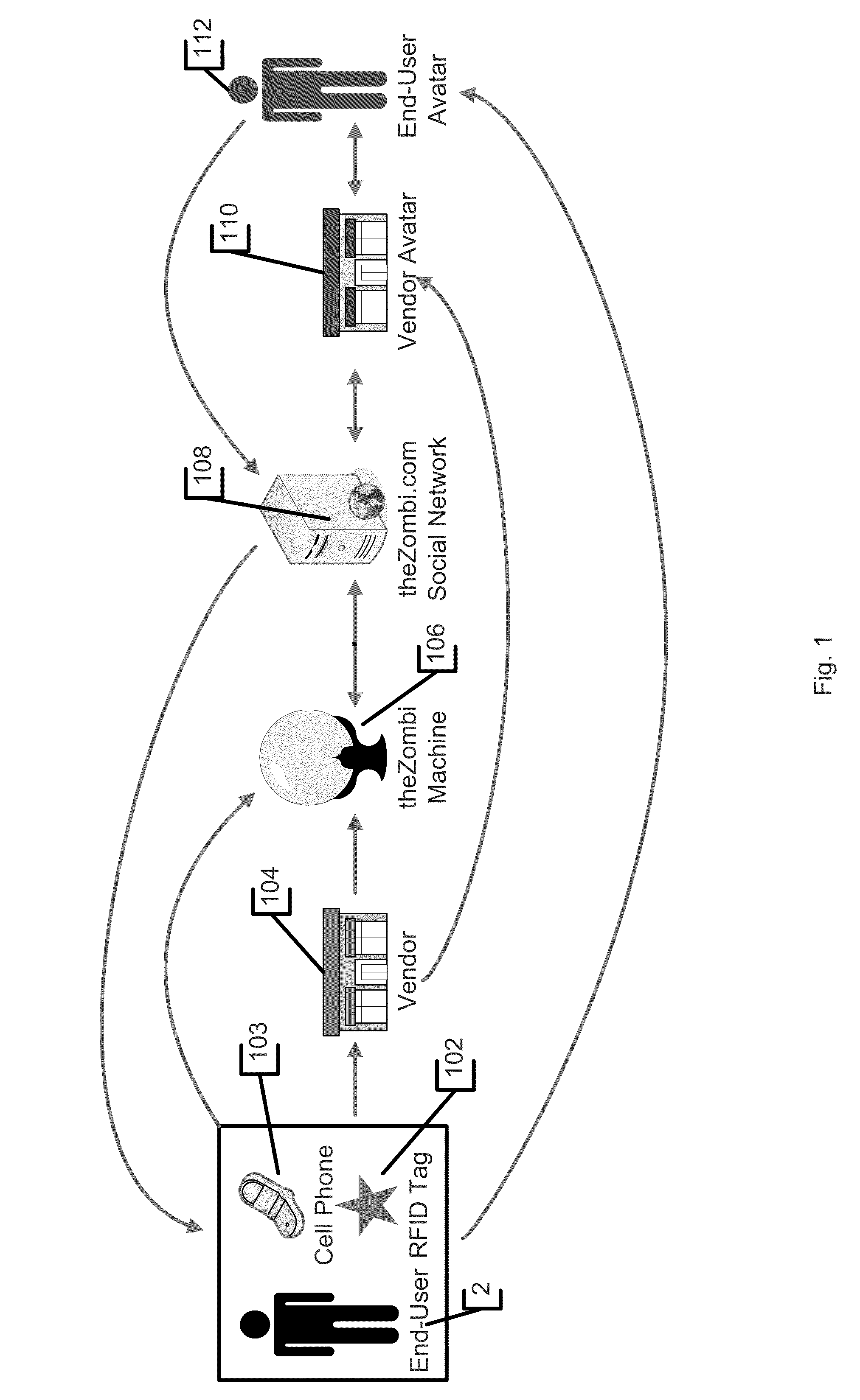
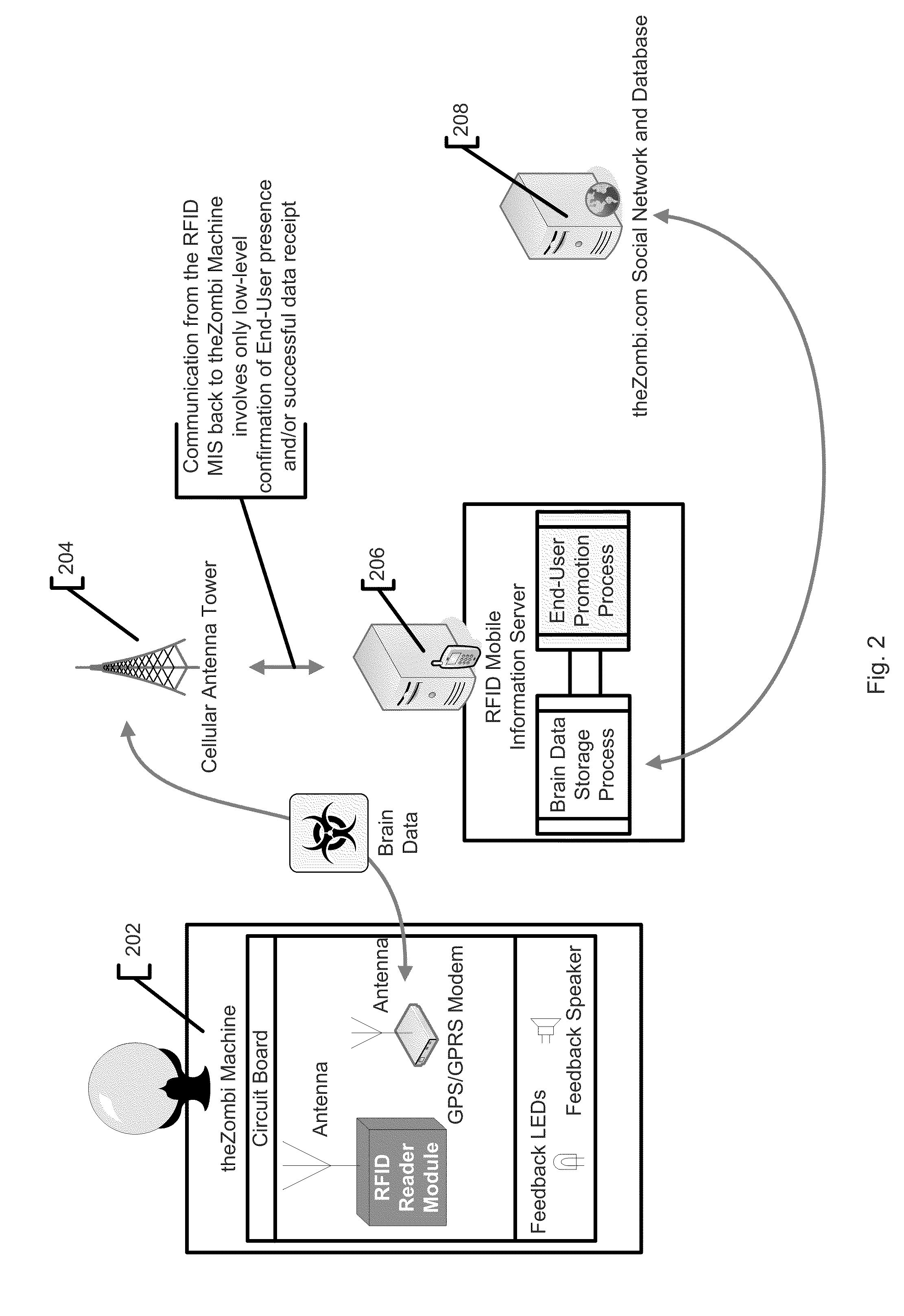
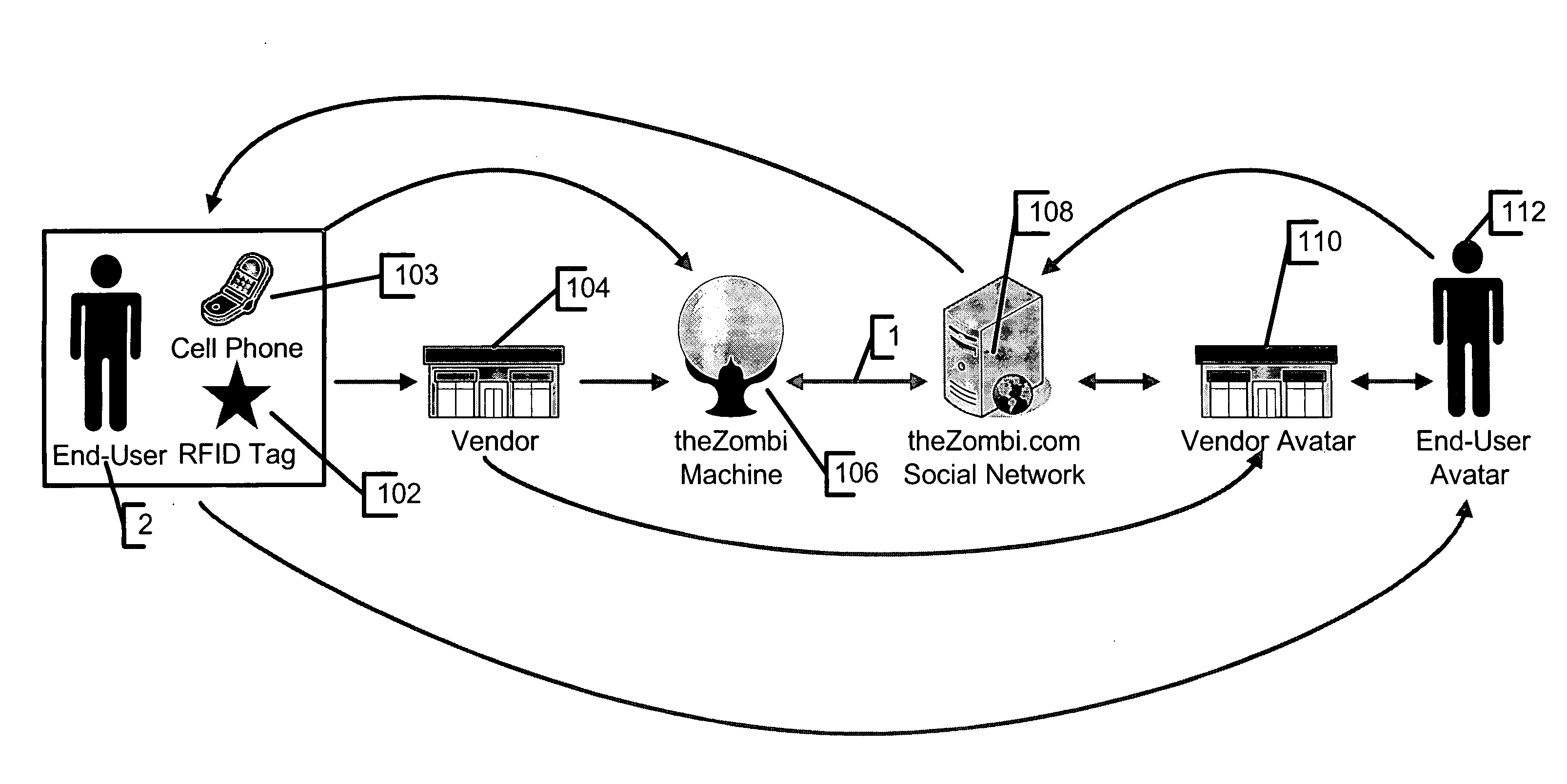
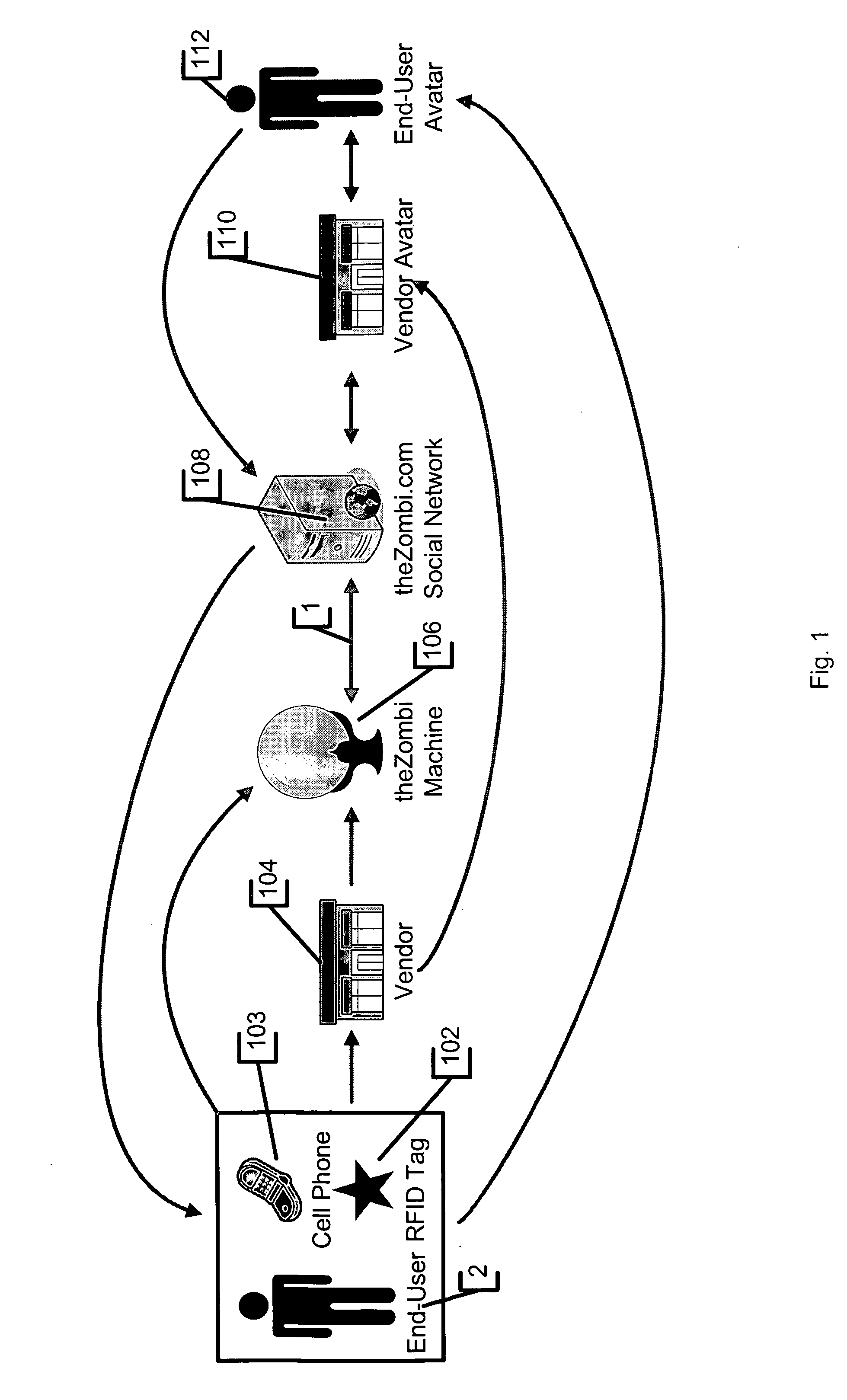
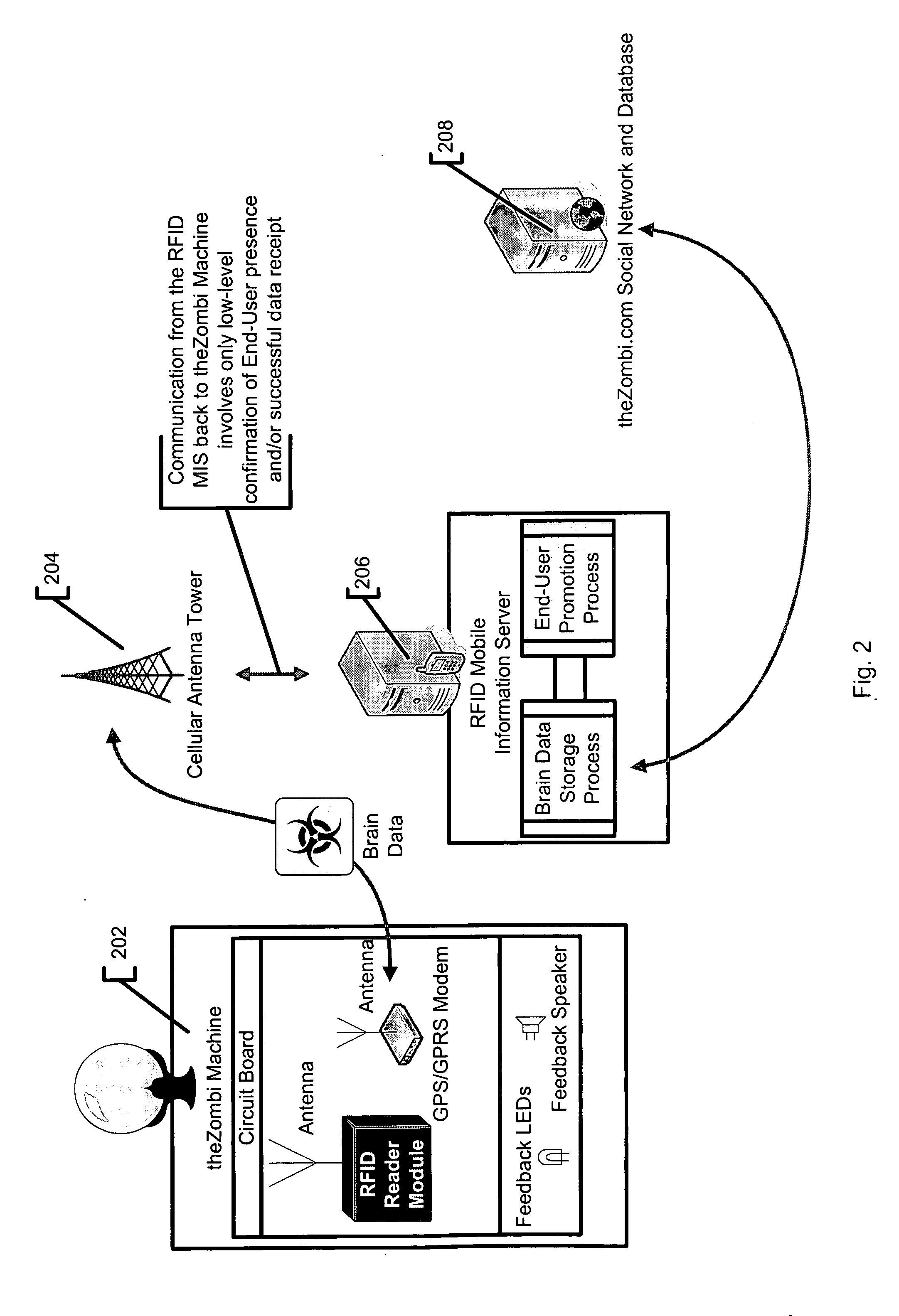
System and method for tracking individuals via remote transmitters attached to personal items
InactiveUS8028905B2Registering/indicating time of eventsVisual presentationSupplier identifierWorld Wide Web
Owner:HOLBERG JORDAN R
System and method for tracking individuals via remote transmitters attached to personal items
InactiveUS20080302867A1Registering/indicating time of eventsVisual presentationSupplier identifierWorld Wide Web
In accordance with an embodiment, a system and method for verifying presence at a vendor location is defined. Preferably, an identification tag is coupled to a device, and the identification tag is operable to transmit a unique user identifier representing the user in possession of the device. The identification tag preferably includes a low frequency RFID device. Further, an identification tag reader is provided that is operable to receive from the identification tag the user identifier. The identification tag reader is preferably placed at a location of a vendor. Further, a computing device is provided that is operable to receive the user identifier from the identification tag reader. The computing device is further operable to receive from the identification tag reader a vendor identifier representing the vendor location, and is still further operable to receive a time identifier representing a time when the identification tag reader received the user identifier from the identification tag. Preferably, a database is also provided that stores the user identifier, the vendor identifier and the time identifiers with a plurality of other user identifiers, other vendor identifiers and other time identifiers. The computing device determines the name of the user and the name of the vendor as a function of the user identifier and the vendor identifier.
Owner:HOLBERG JORDAN R
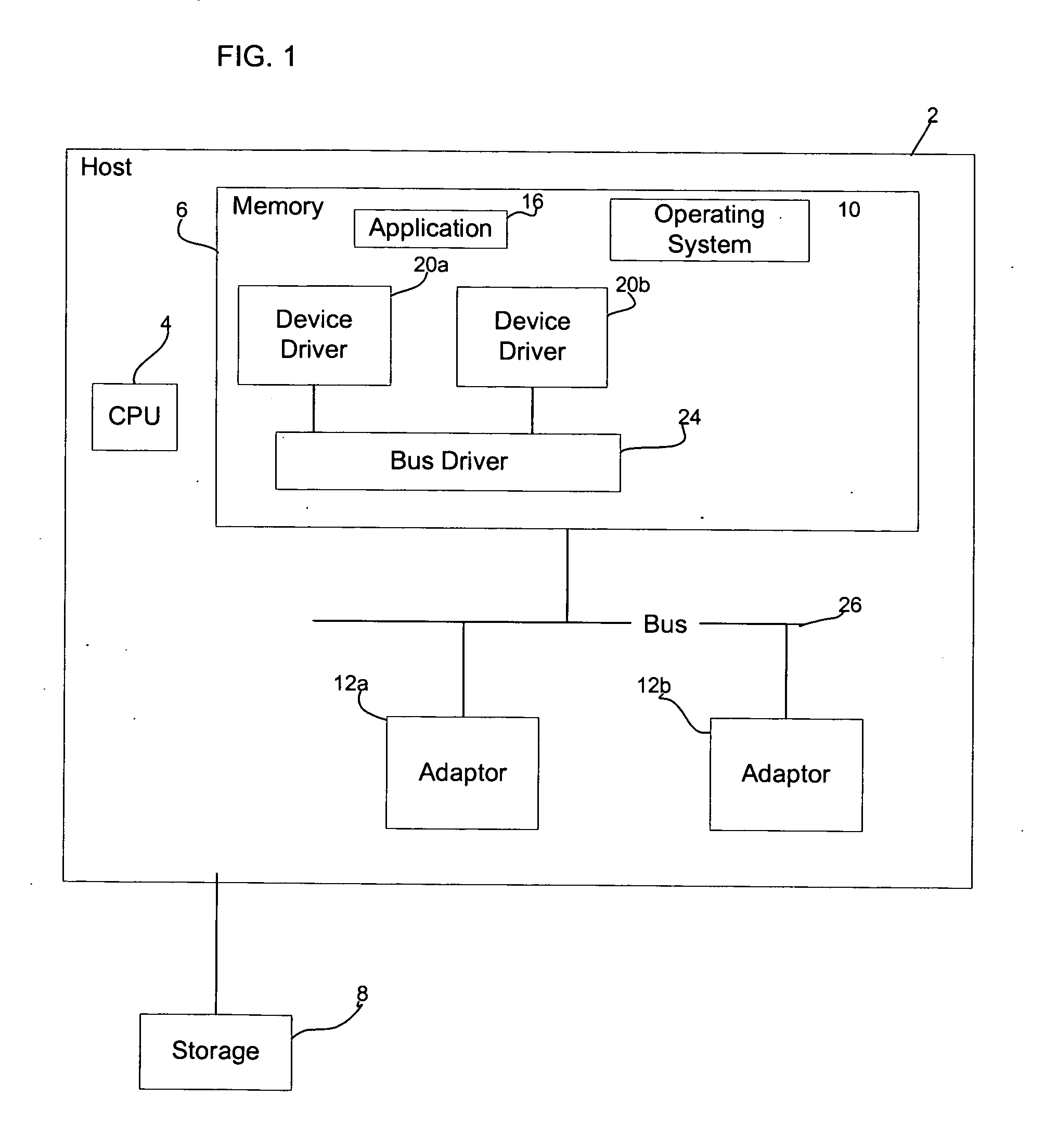
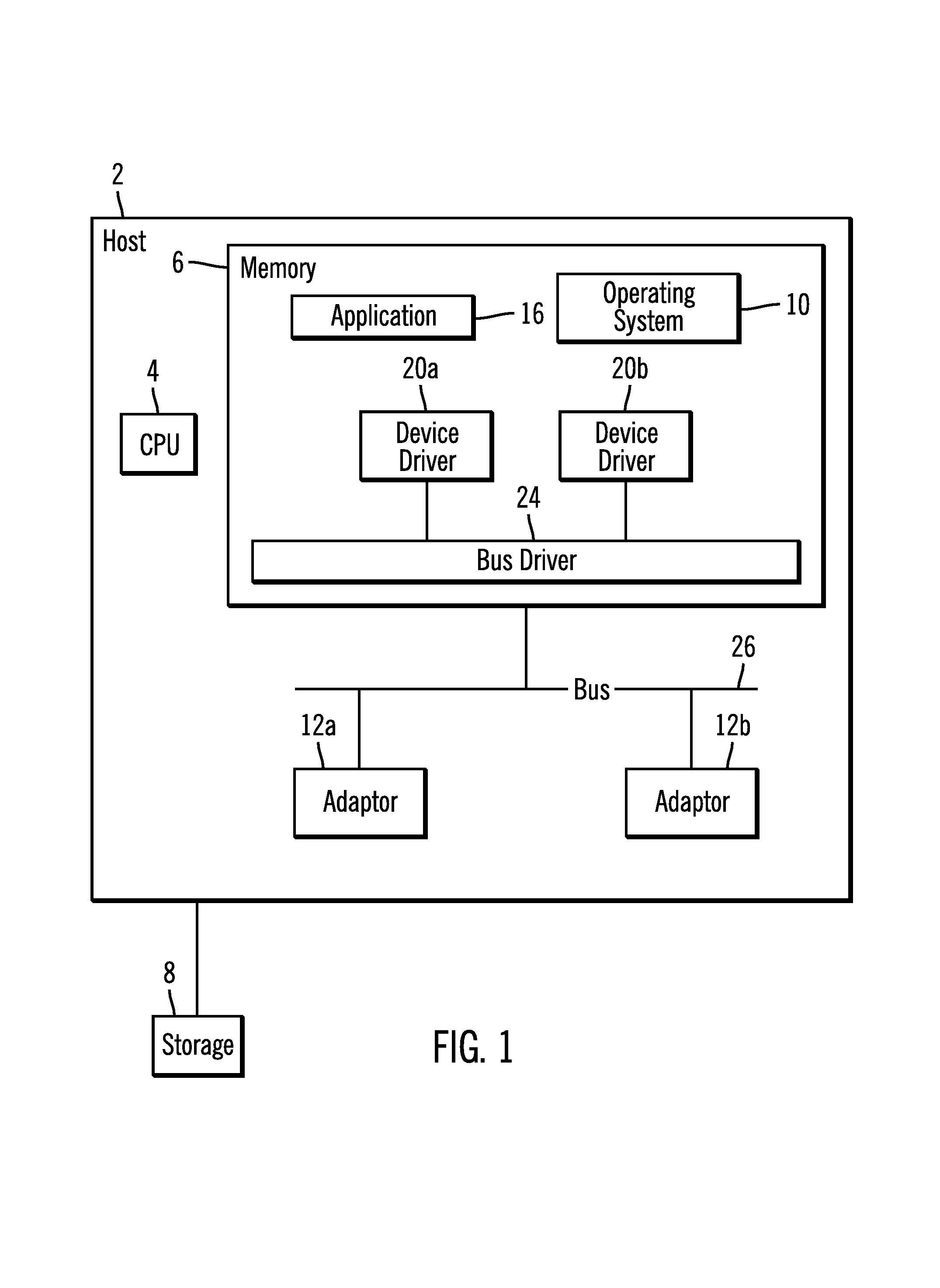
Managing transmissions between devices
InactiveUS20050138261A1Digital computer detailsTime-division multiplexComputer hardwareSupplier identifier
Provided are a method, system, and program for processing a transmission from a first device to a second device. An identification transmission is received including an interface address from the first device. A determination is made as to whether the identification transmission indicates a recognized vendor identifier. An interface address of a third device is returned to the first device in response to determining that the identification transmission includes one recognized vendor identifier, wherein the third device relays transmissions between the first and second devices.
Owner:INTEL CORP
Managing transmissions between devices
Provided are a method, system, and program for processing a transmission from a first device to a second device. An identification transmission is received including an interface address from the first device. A determination is made as to whether the identification transmission indicates a recognized vendor identifier. An interface address of a third device is returned to the first device in response to determining that the identification transmission includes one recognized vendor identifier, wherein the third device relays transmissions between the first and second devices.
Owner:INTEL CORP
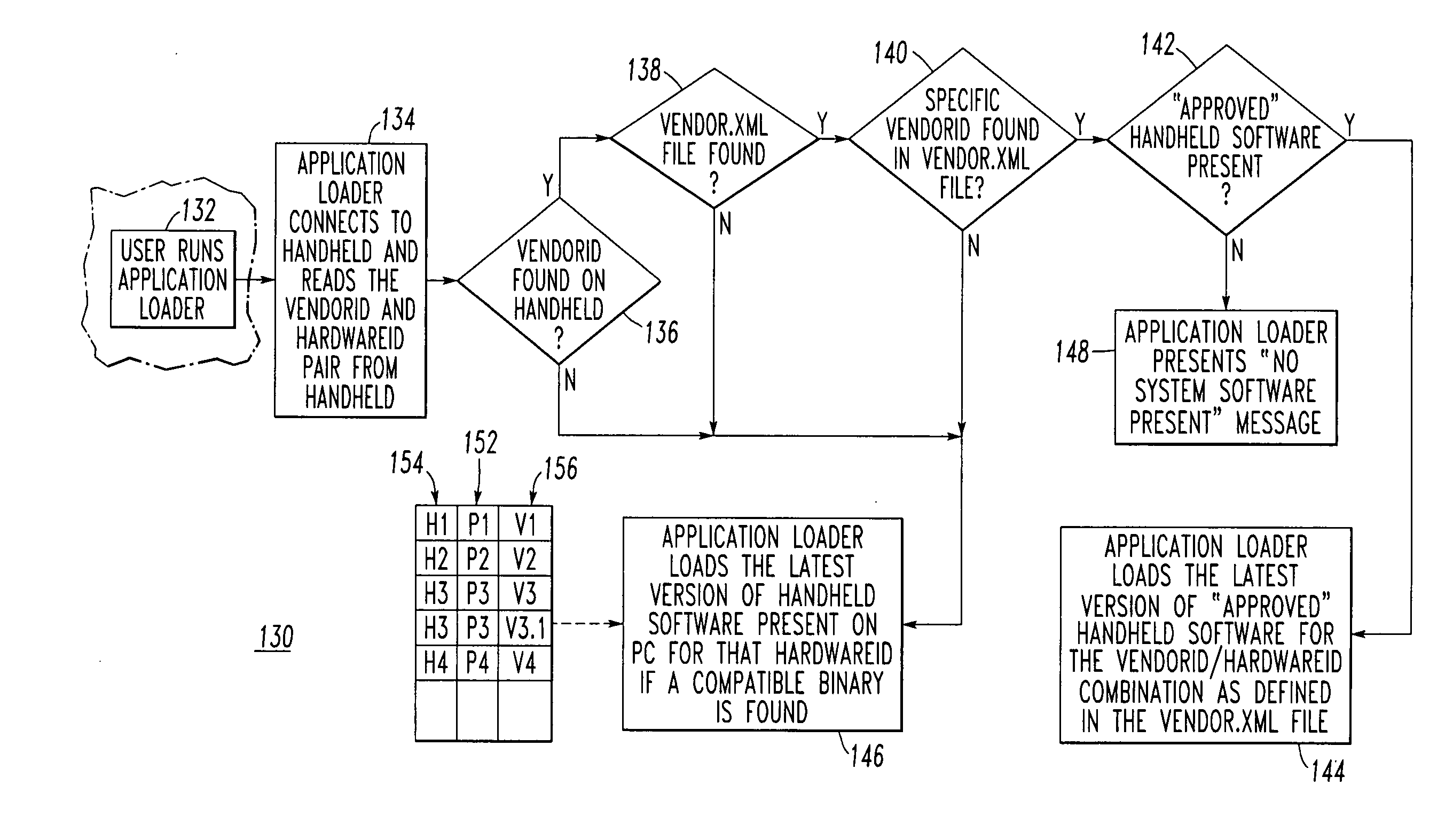
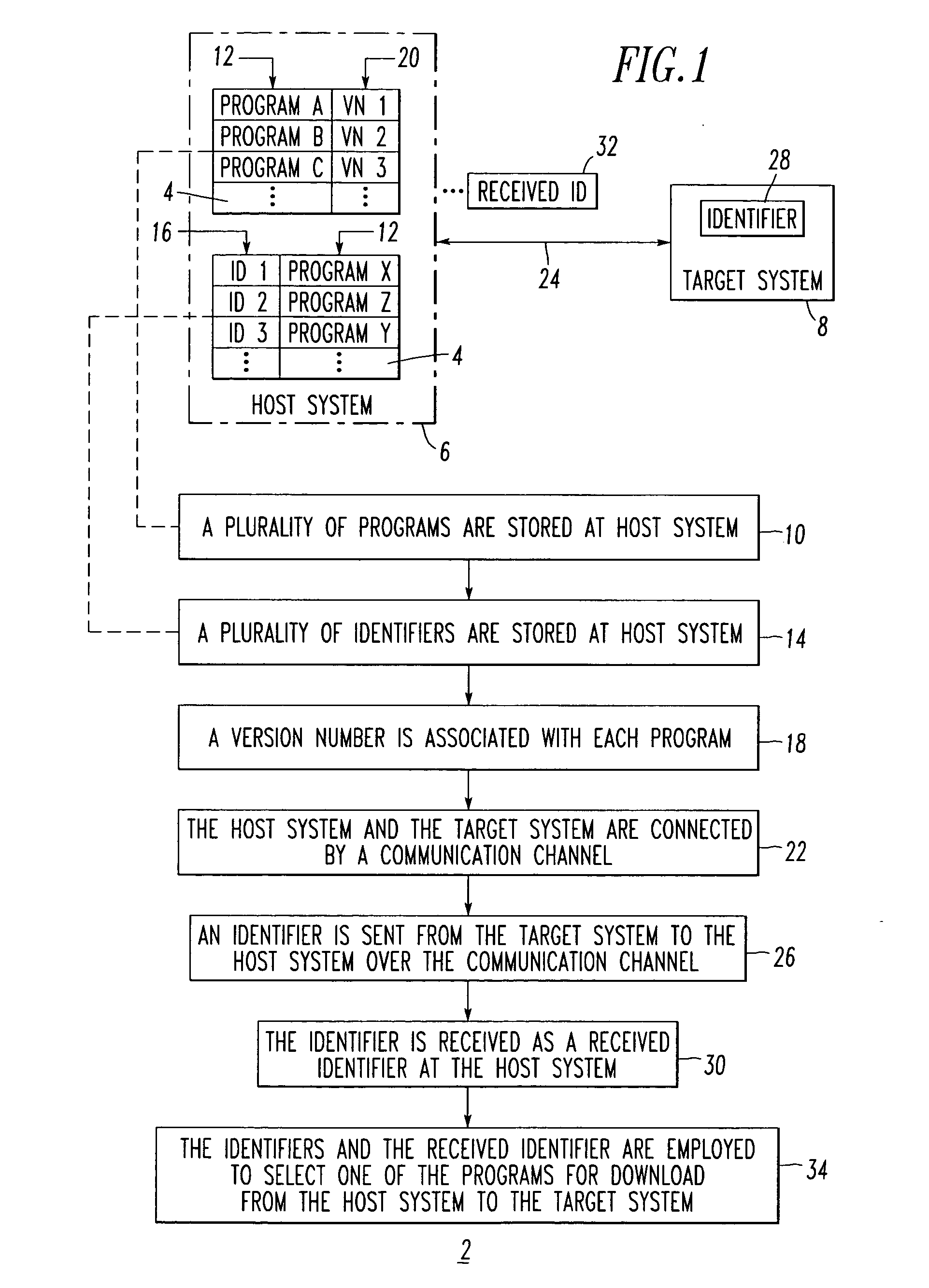
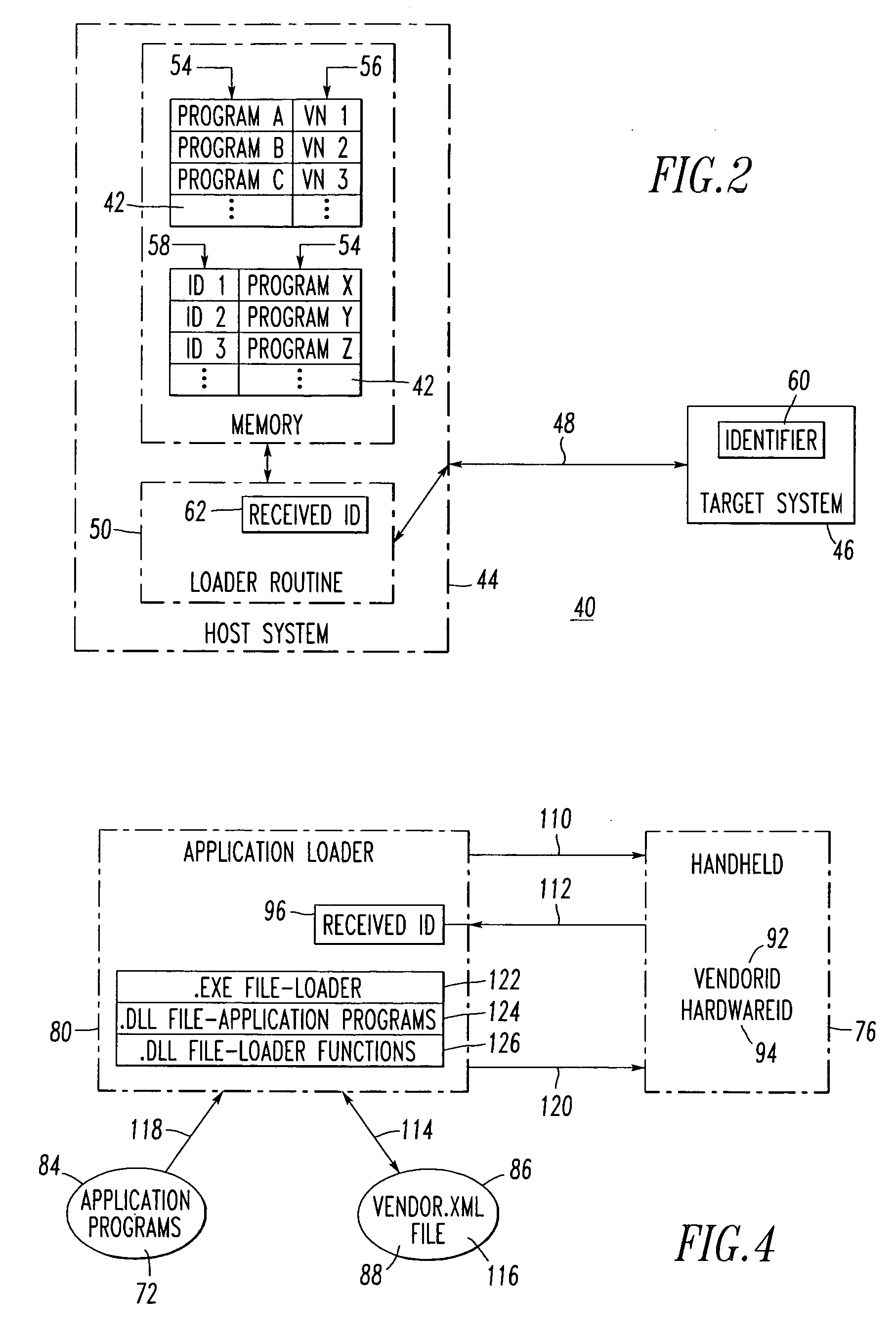
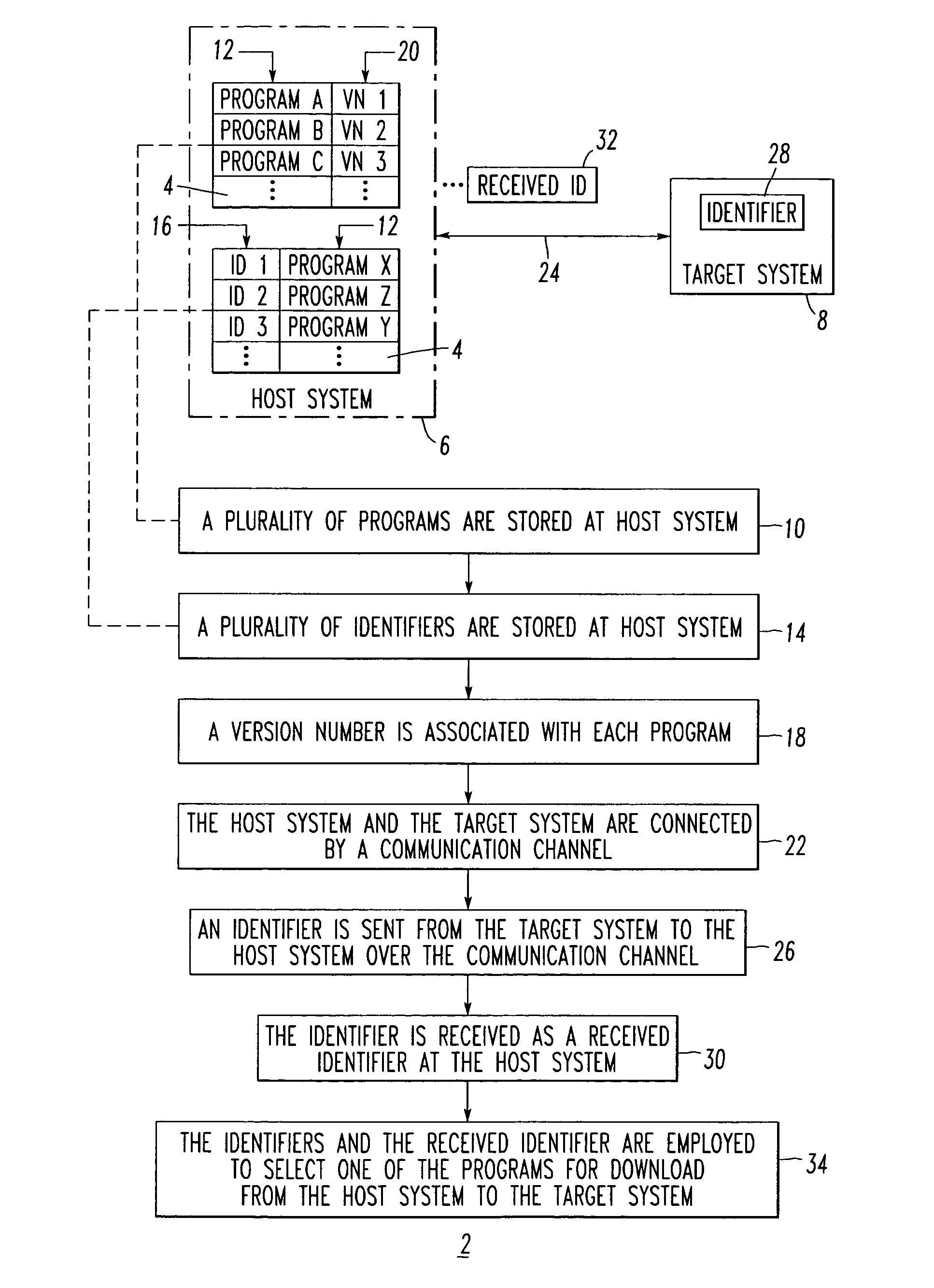
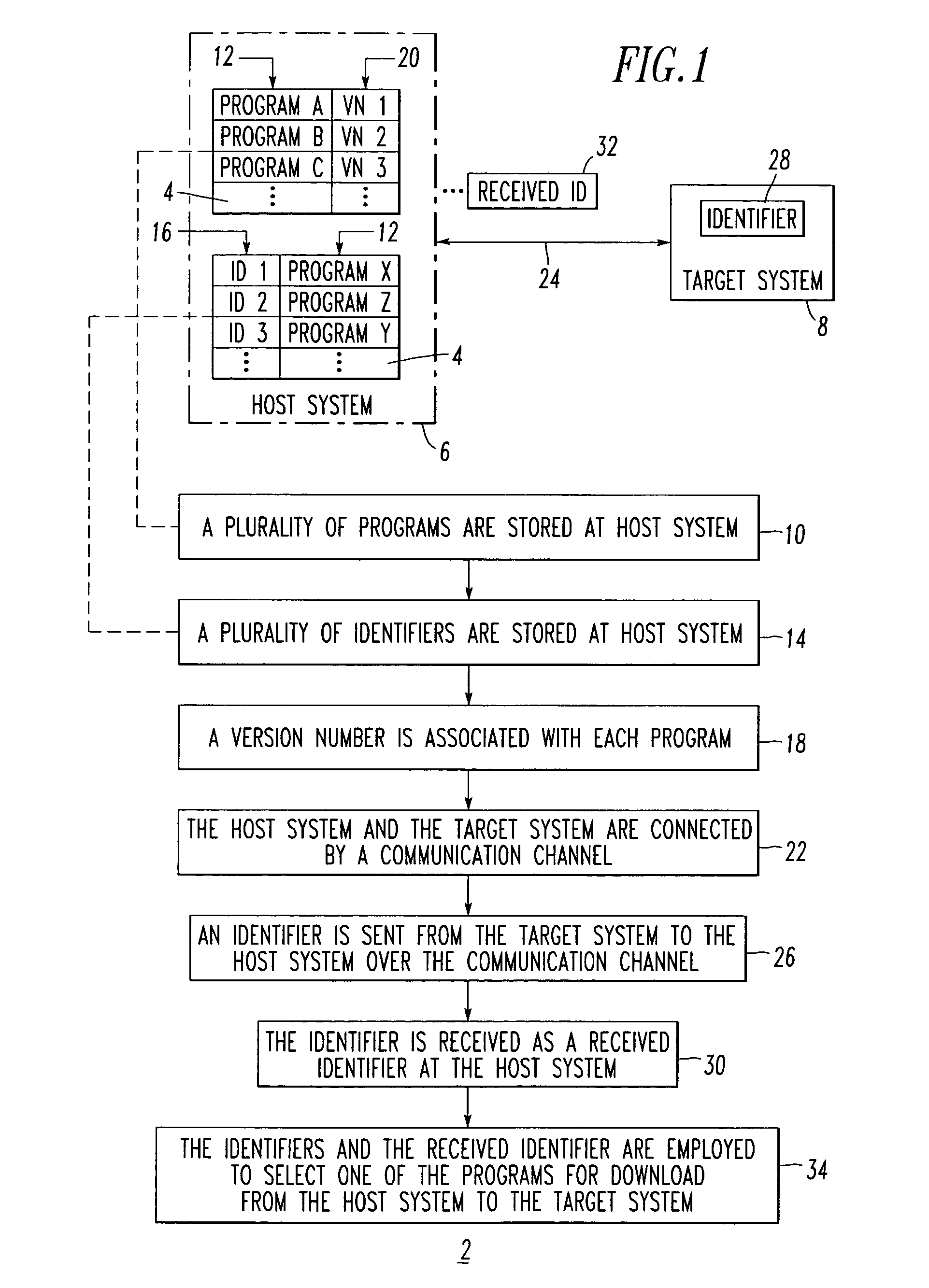
Method and system for selecting a program for download
A system selects an application program for download. The system includes a host system, such as a personal computer, having a disk sub-system storing a plurality of application programs. The disk sub-system includes a file storing a plurality of identifiers, with each of at least some of the identifiers being associated with one or more of the application programs. A target system, such as a wireless handheld electronic device, includes a hardware identifier and a vendor identifier. A communications channel connects the host system and the target system. An application loader routine executes at the host system, communicates with the target system through the communications channel, requests the hardware and vendor identifiers as a received identifier from the target system over the communication channel, and employs the identifiers and the received identifier to select one of the application programs for download from the host system to the target system.
Owner:MALIKIE INNOVATIONS LTD
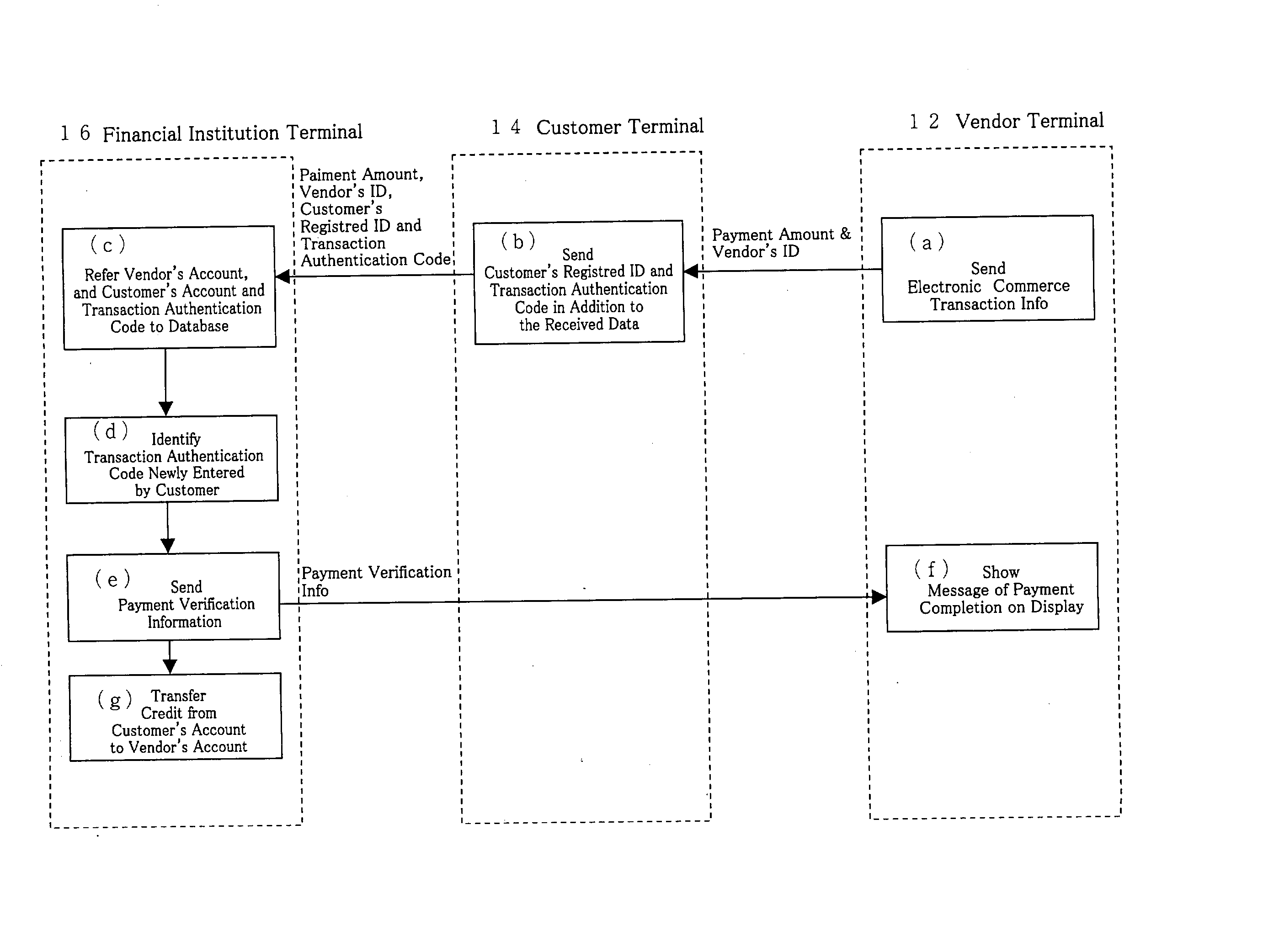
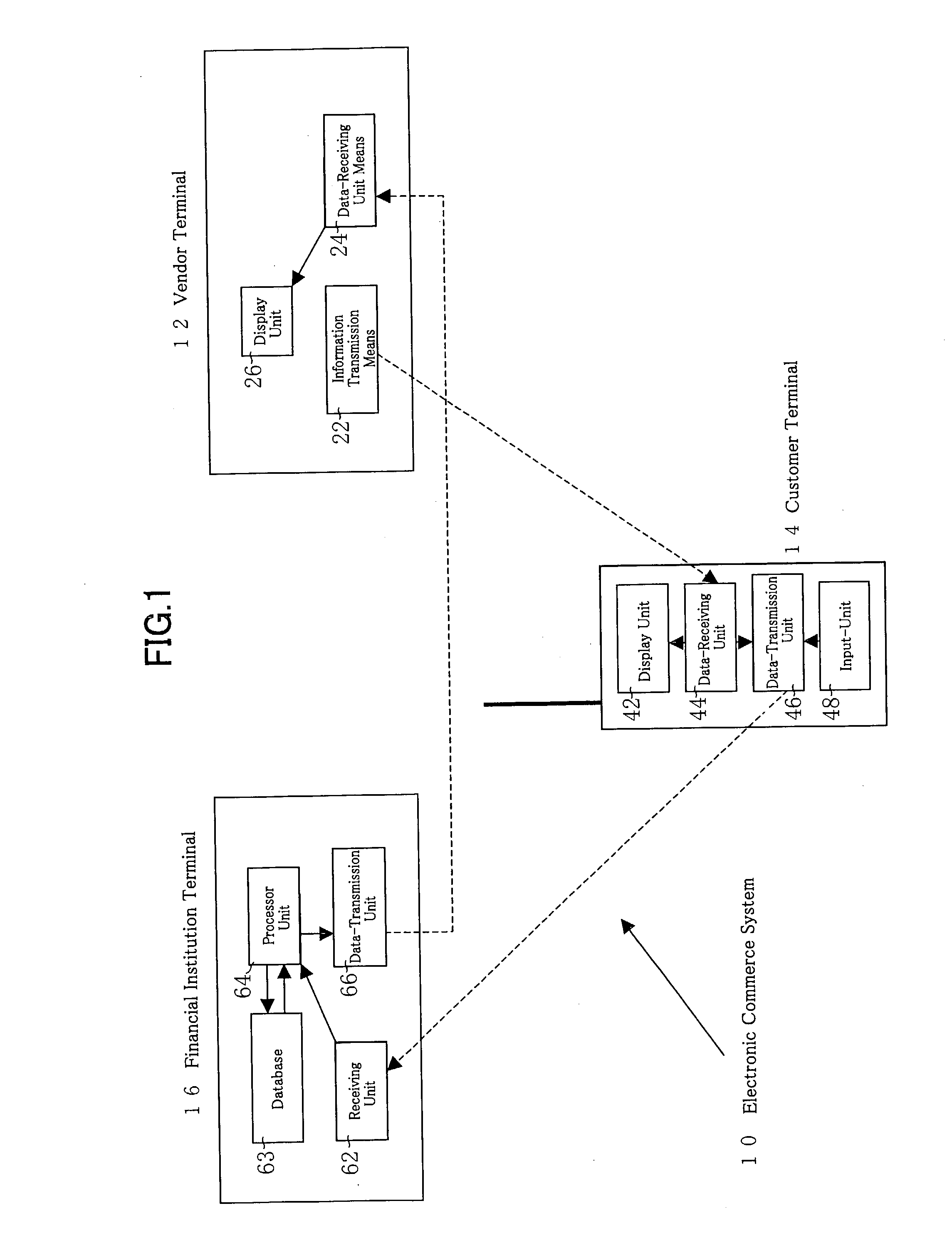
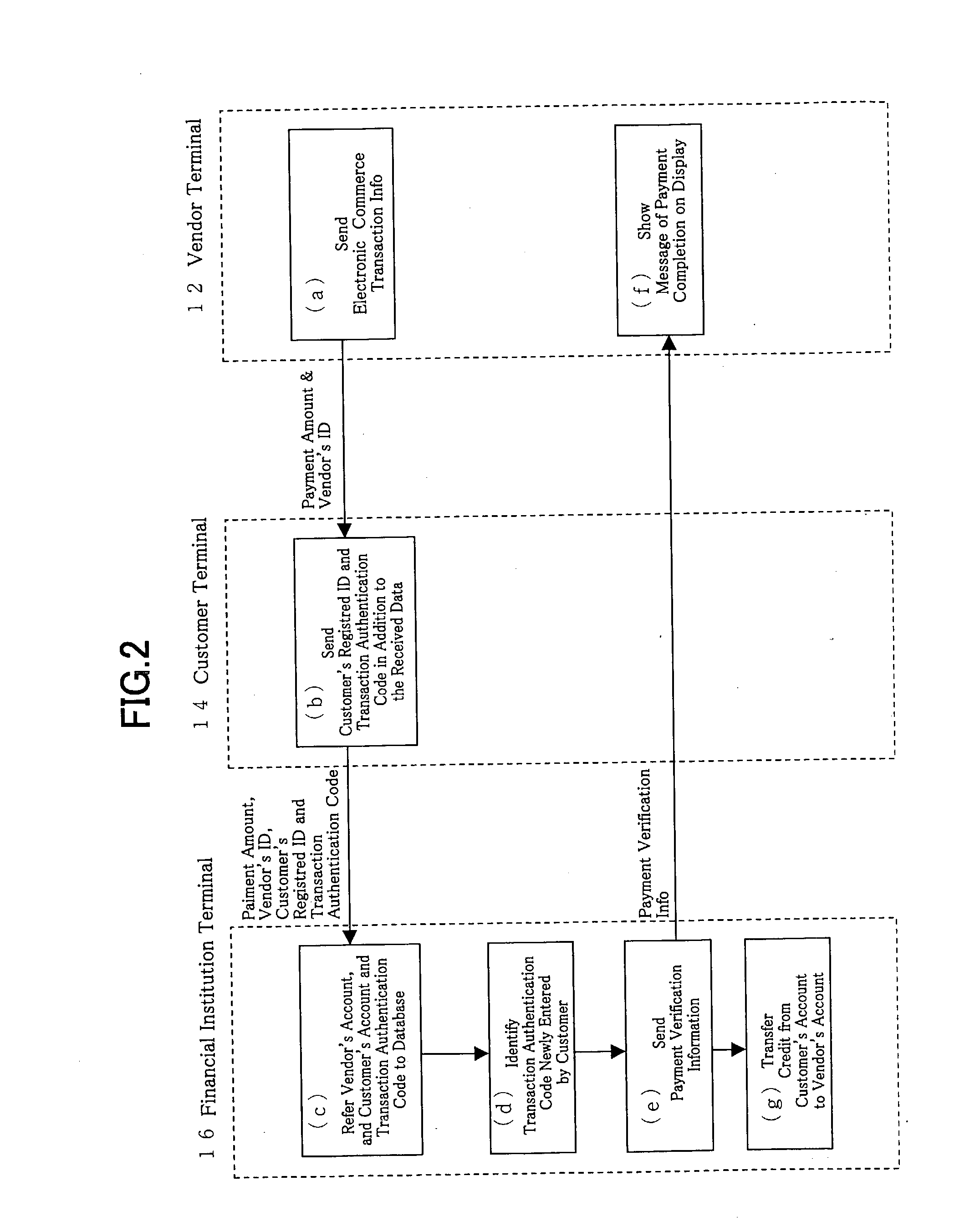
Electronic Commerce Transaction System
The present invention enables a customer to conduct electronic commerce without divulging confidential information to vendors. The present invention is an electronic commerce transaction system comprising a vendor terminal that has an information transmission means that transmits electronic commerce transaction information, including at least information on the amount to be paid and the vendor identifier, a customer terminal used by the customer having a data-receiving unit for receiving said electronic commerce transaction information from said vendor terminal and a data-transmission unit for sending said electronic commerce transaction information, the customer's registered identifier, and a transaction authentication code, and a financial institution terminal prepared in a financial institution with a data-receiving unit for receiving said electronic commerce transaction information, said customer's registered identifier, and transaction authentication code, as well as a database to specify the customer based on the registered identifier and to authenticate the customer based on the received transaction authentication code, and wherein, said vendor terminal transmits electronic commerce transaction information to said customer terminal, said financial institution terminal receives the customer's registered identifier, and a transaction authentication code, and the electronic commerce transaction information from said customer terminal, and said database of said financial institution terminal identifies the customer based on the registered identifier and authenticates the customer based on the received transaction authenticates code using said database, and wherein, said financial institution terminal processes the payment of the payment amount to the vendor based on said electronic commerce transaction information, and withdraws the payment amount from the customer's account or bills the customer for the payment amount.
Owner:SKINNER JAMES JAY
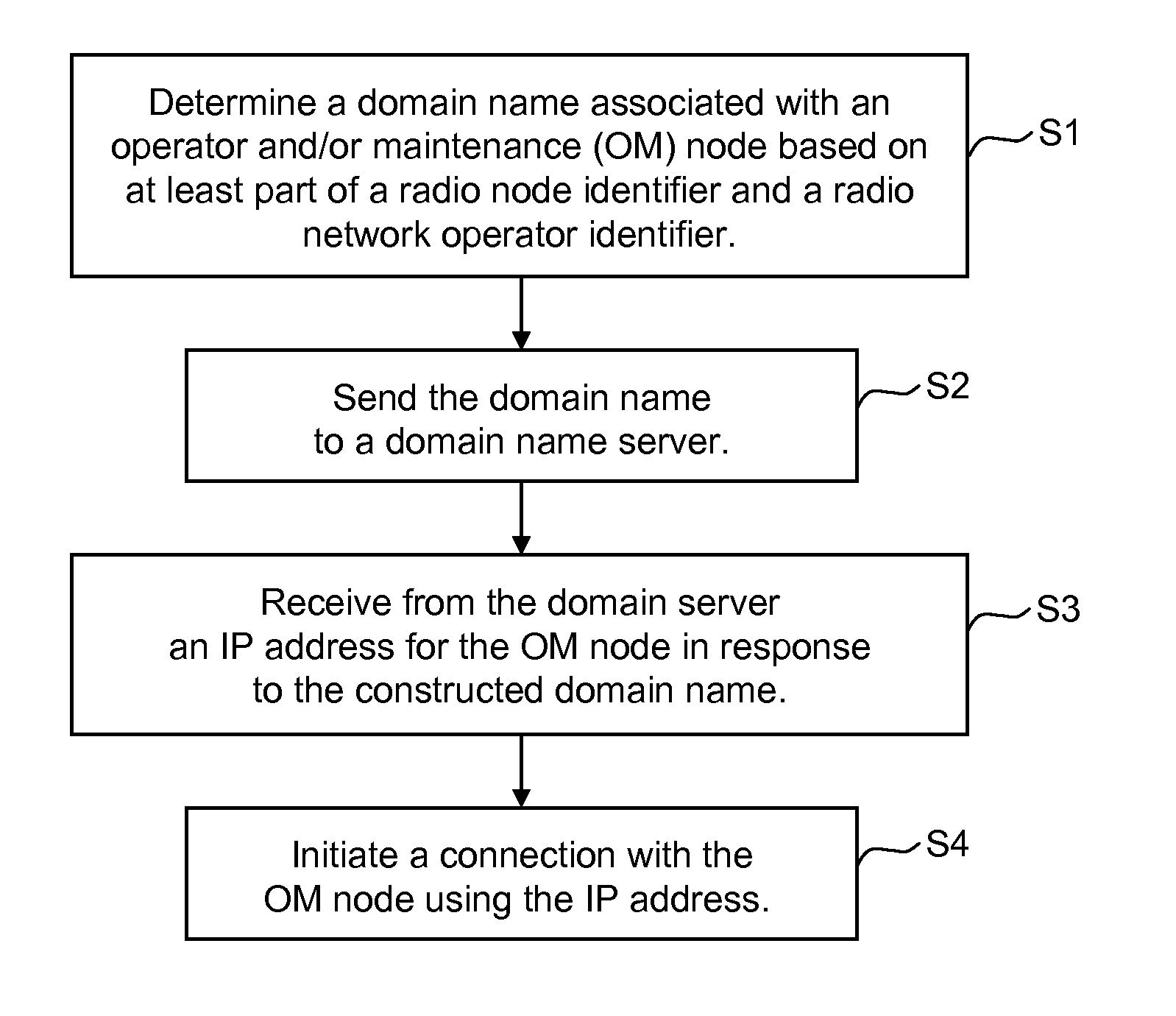
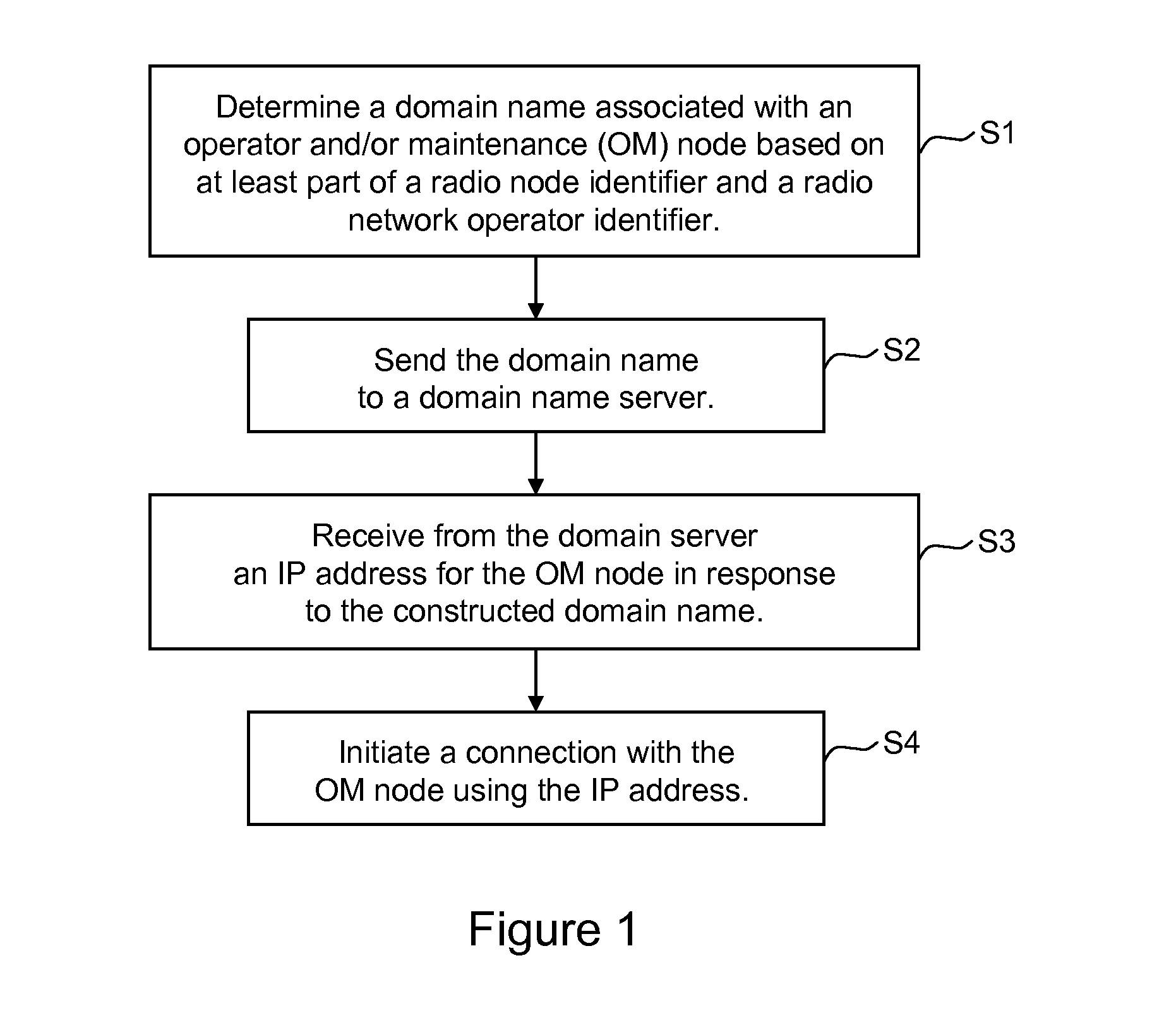
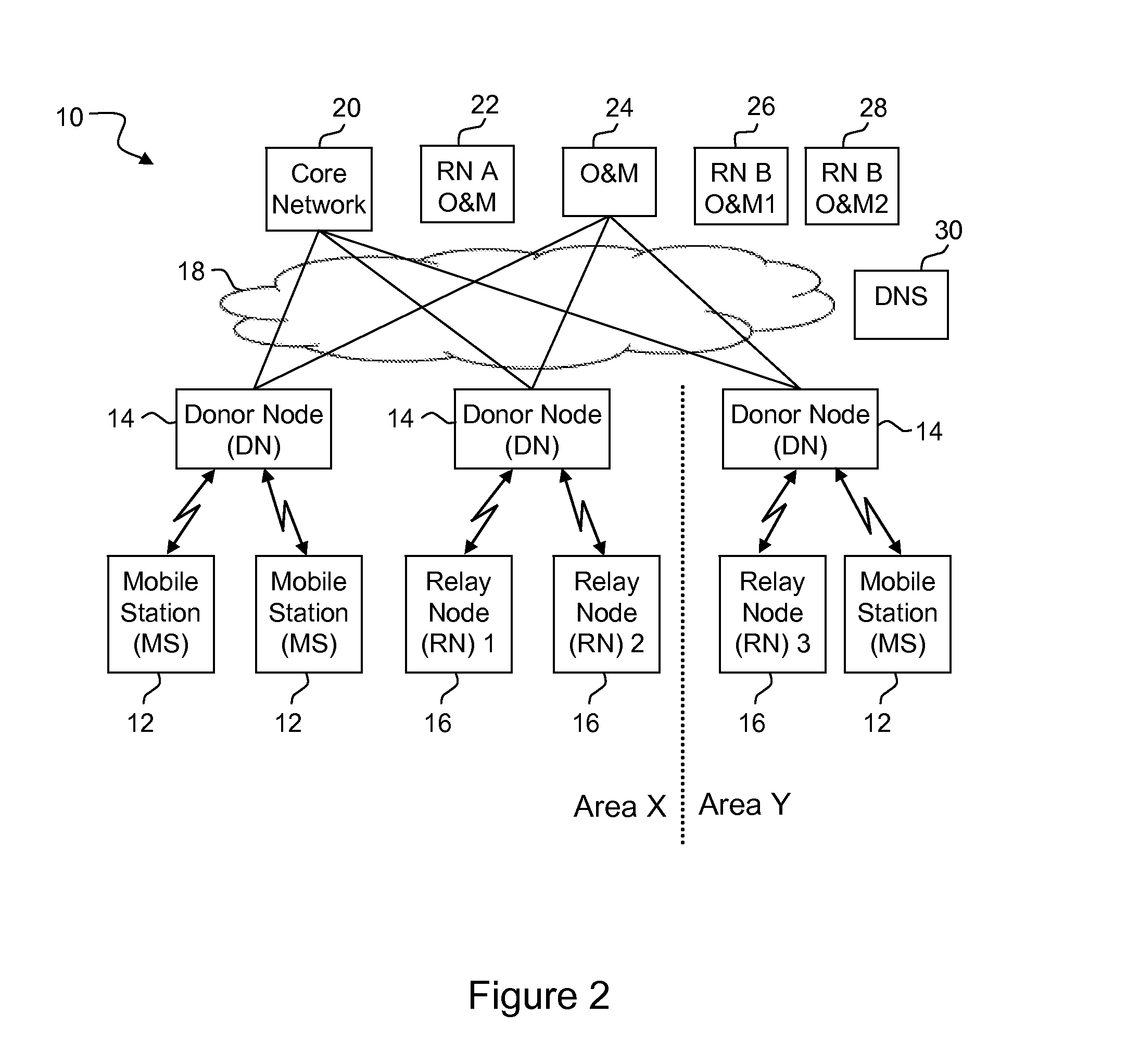
Radio network node discovery of operations node
A domain name associated with a radio network node's operator or maintenance (OM) node is determined based on at least part of a radio node identifier and a radio network operator identifier. The radio network node sends the domain name to a domain name server. In response to sending the constructed domain name, the radio network node receives from the domain server an IP address for the OM node. The radio network node then initiates a connection with the OM node using the IP address. In one non-limiting example embodiment, the part of the radio node identifier is a radio network node vendor identifier.
Owner:TELEFON AB LM ERICSSON (PUBL)
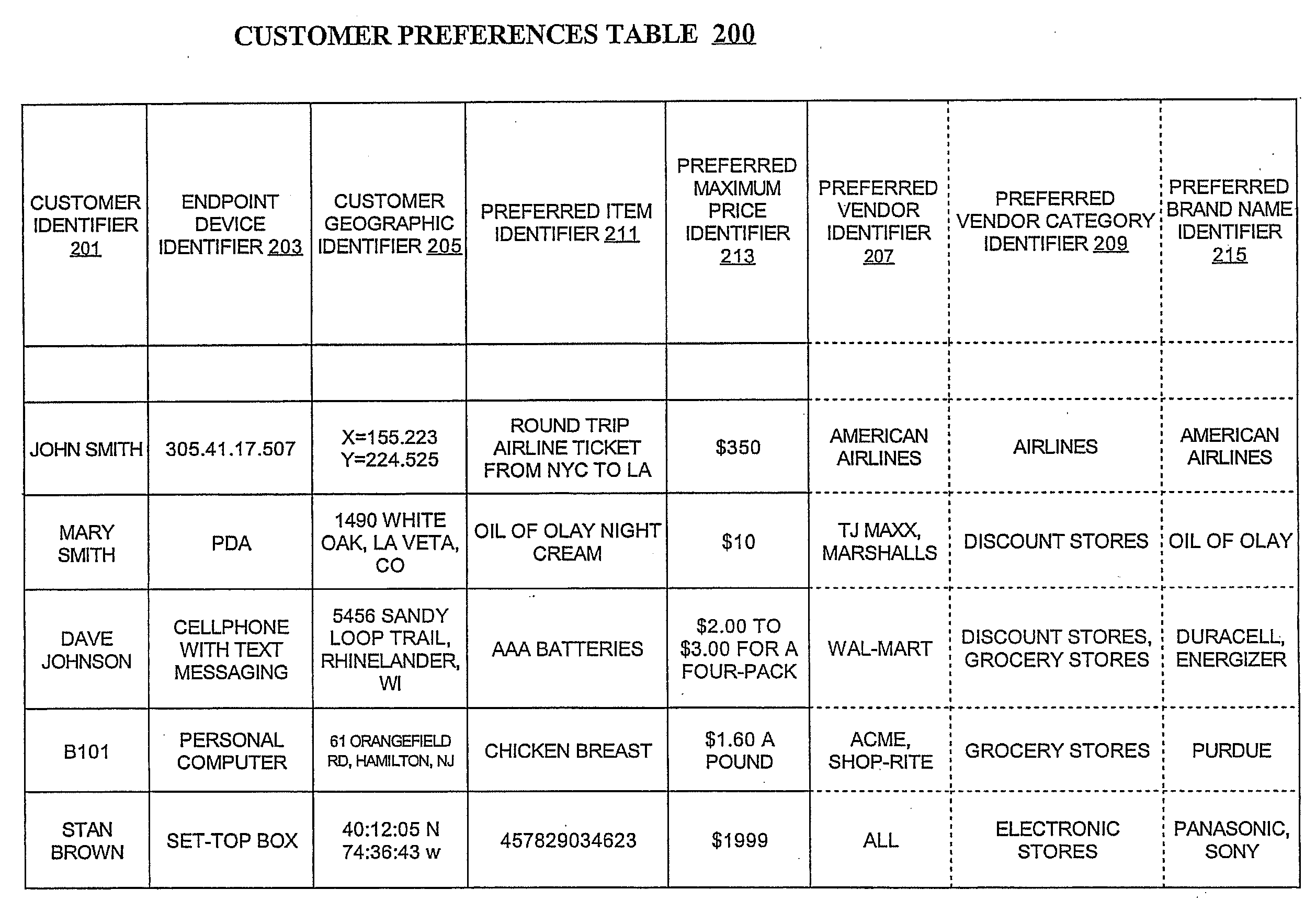
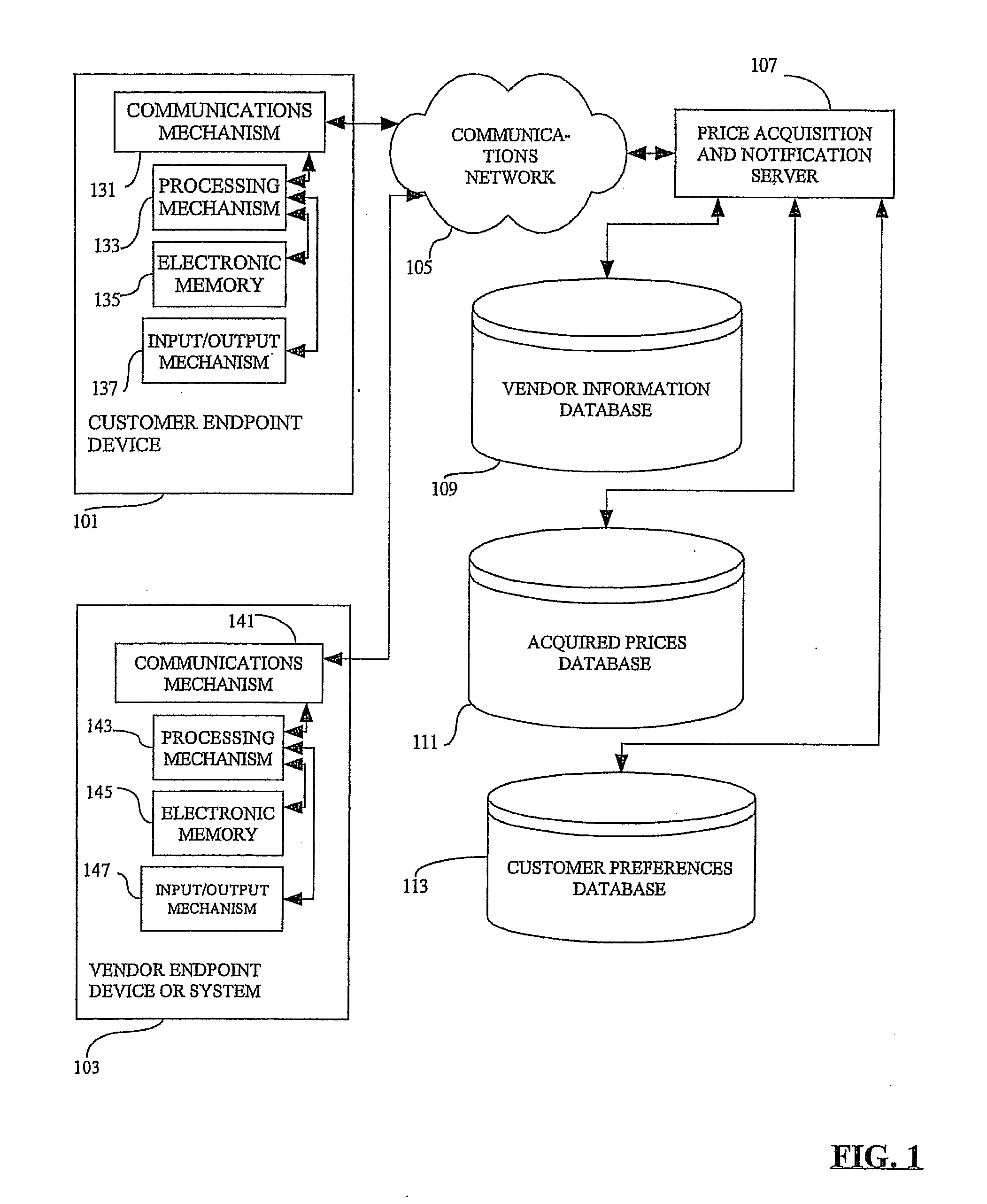
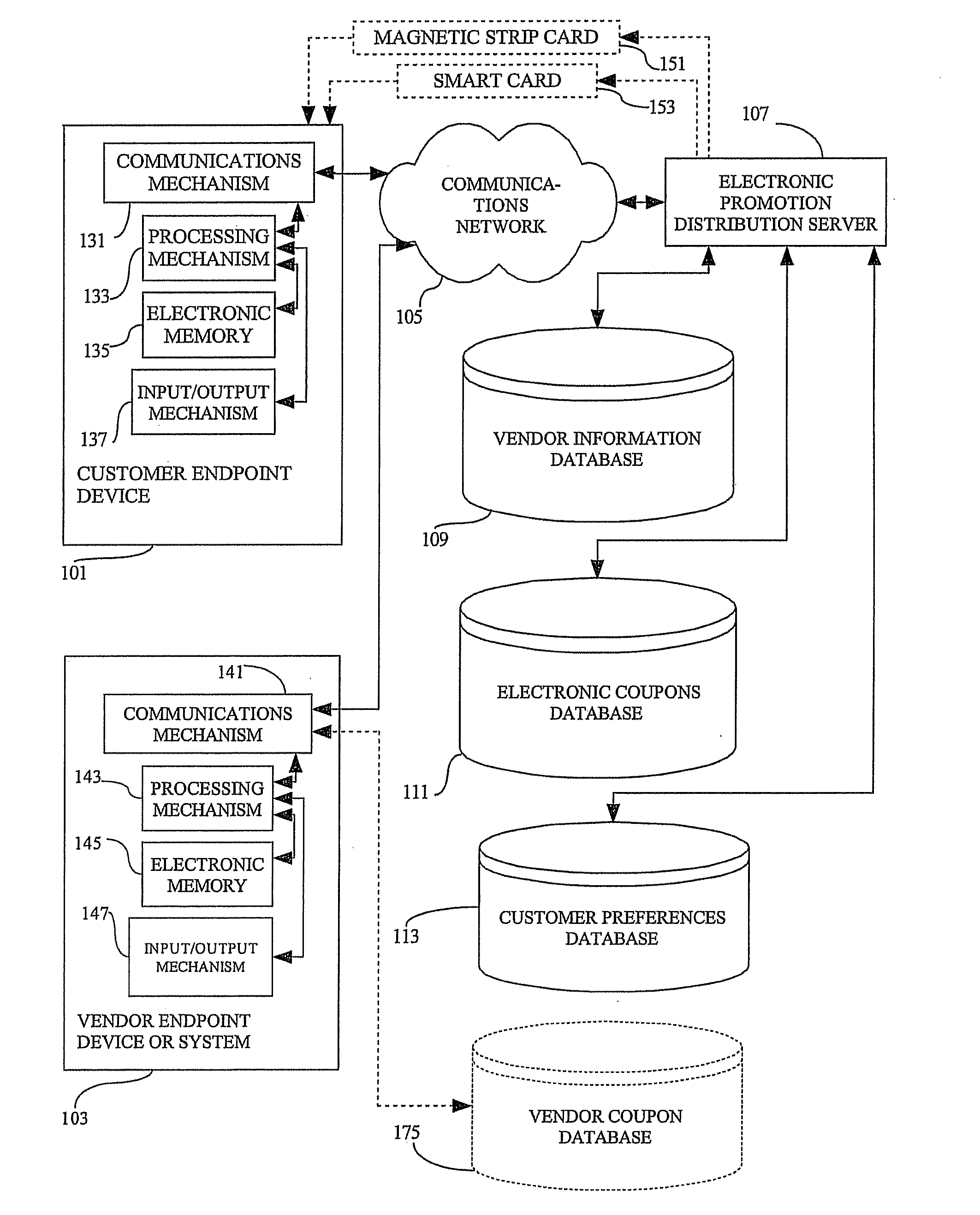
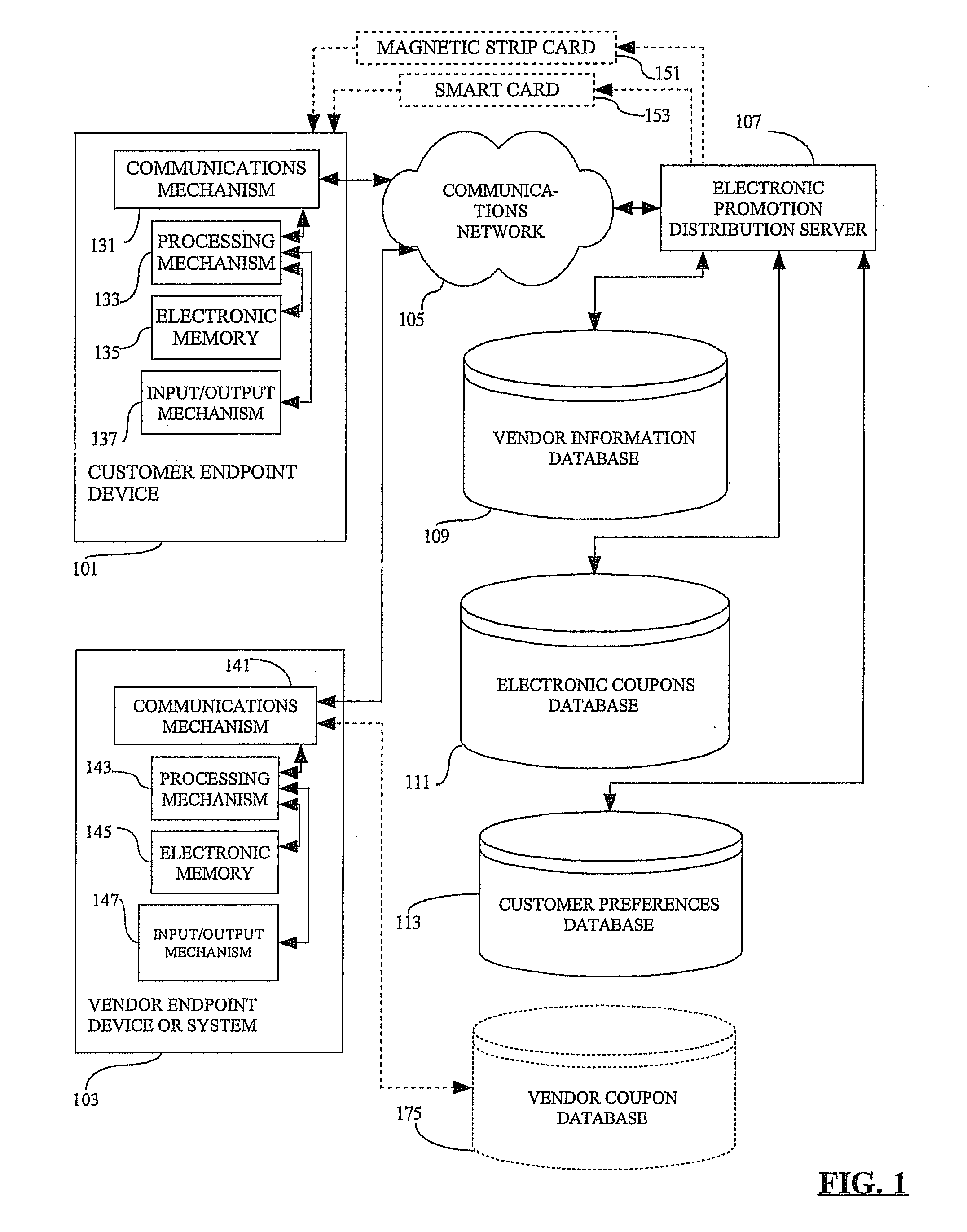
Methods, devices, systems, and computer program products for locating items offered by vendors at customer preferred prices
Methods, devices, systems, and computer program products for locating items offered by vendors at customer preferred prices are provided. The methods comprise receiving customer preferences including a customer identifier associated with a preferred item identifier and a preferred maximum price identifier. Vendor information is received which includes a vendor identifier associated with an offered item identifier and an offered item price identifier. The customer preferences and vendor information are stored, wherein the stored customer preferences include one or more stored preferred item identifiers and the stored vendor information includes one or more stored offered item identifiers. The stored preferred item identifiers are compared with the stored offered item identifiers. If a preferred item identifier matches an offered item identifier, the offered item price identifier associated with the matching offered item identifier is retrieved, and the preferred maximum price identifier associated with the matching preferred item identifier is retrieved. If the offered item price identifier is less than or equal to the preferred maximum price identifier, a matching price record is generated.
Owner:AT&T DELAWARE INTPROP INC
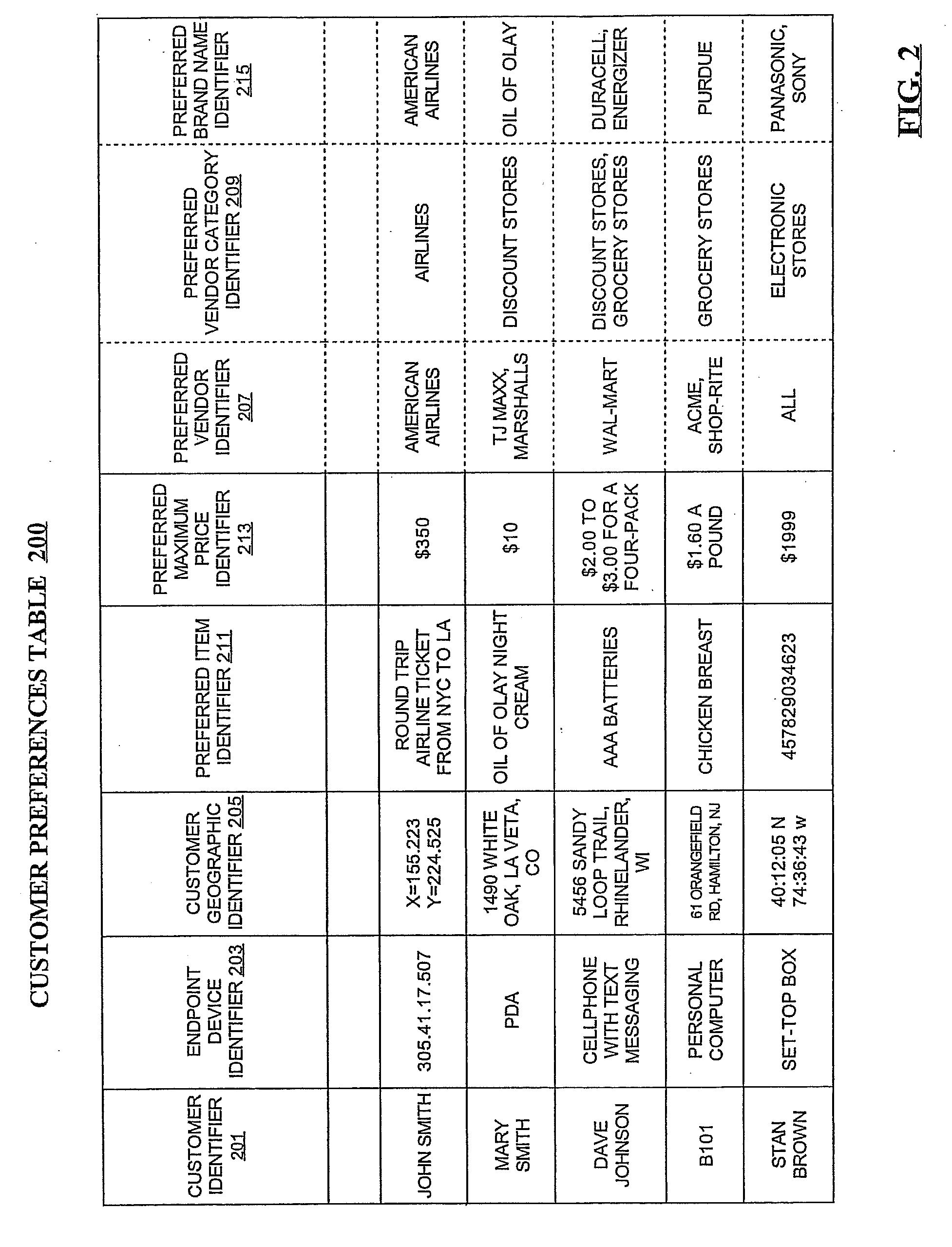
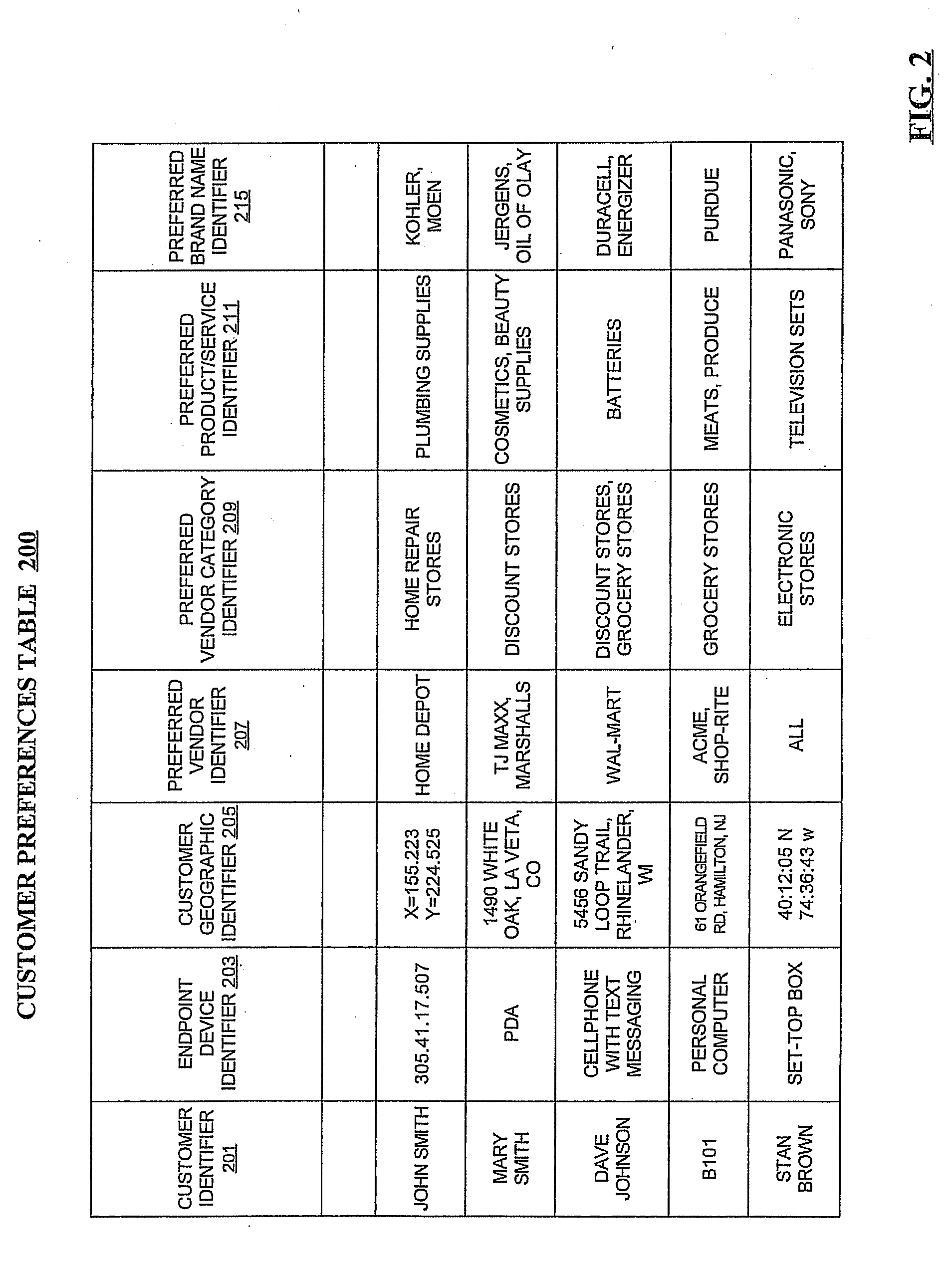
Methods, devices, systems, and computer program products for distributing electronic coupons
Electronic coupons are distributed by receiving customer preferences including a customer identifier associated with a preferred vendor identifier, a preferred vendor category identifier, a preferred product / service identifier, or a preferred brand name identifier. Vendor information is received which includes a vendor identifier, a vendor category identifier, a vendor product / service identifier, a brand name identifier, or a promotional offer discount parameter. The customer preferences are compared with the vendor information to determine whether or not a match exists between the customer preferences and the vendor information. If a match exists, an electronic coupon is generated that includes information indicative of the preferred vendor identifier, the preferred vendor category identifier, the preferred product / service identifier, the preferred brand name identifier, or the promotional offer discount parameter. The generated electronic coupon is distributed to a customer associated with the customer identifier.
Owner:AT&T DELAWARE INTPROP INC
Bill paying systems and associated methods
Methods of paying user bills on behalf of a user are described. In one embodiment, the method includes receiving from a vendor a user bill having a user identifier, a vendor identifier, and a bill amount. The method further includes obtaining the user identifier, the vendor identifier, and the bill amount, associating the bill with the user based on the user identifier, and associating the bill with the vendor based on the vendor identifier. The method further includes determining whether the bill is payable, which includes comparing the bill to stored bill data associated with the user and the vendor. When the bill is payable, the method further includes obtaining funds from an account of the user, dispersing funds to the vendor to pay the bill and storing an indication of the paying of the bill.
Owner:MILLER DEVIN +2
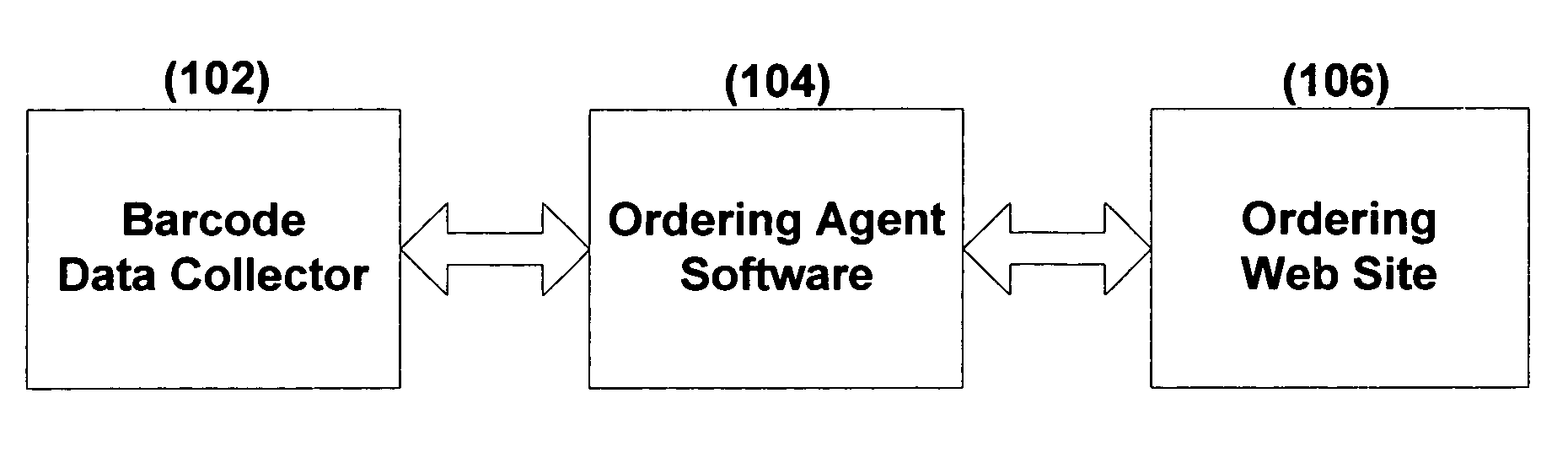
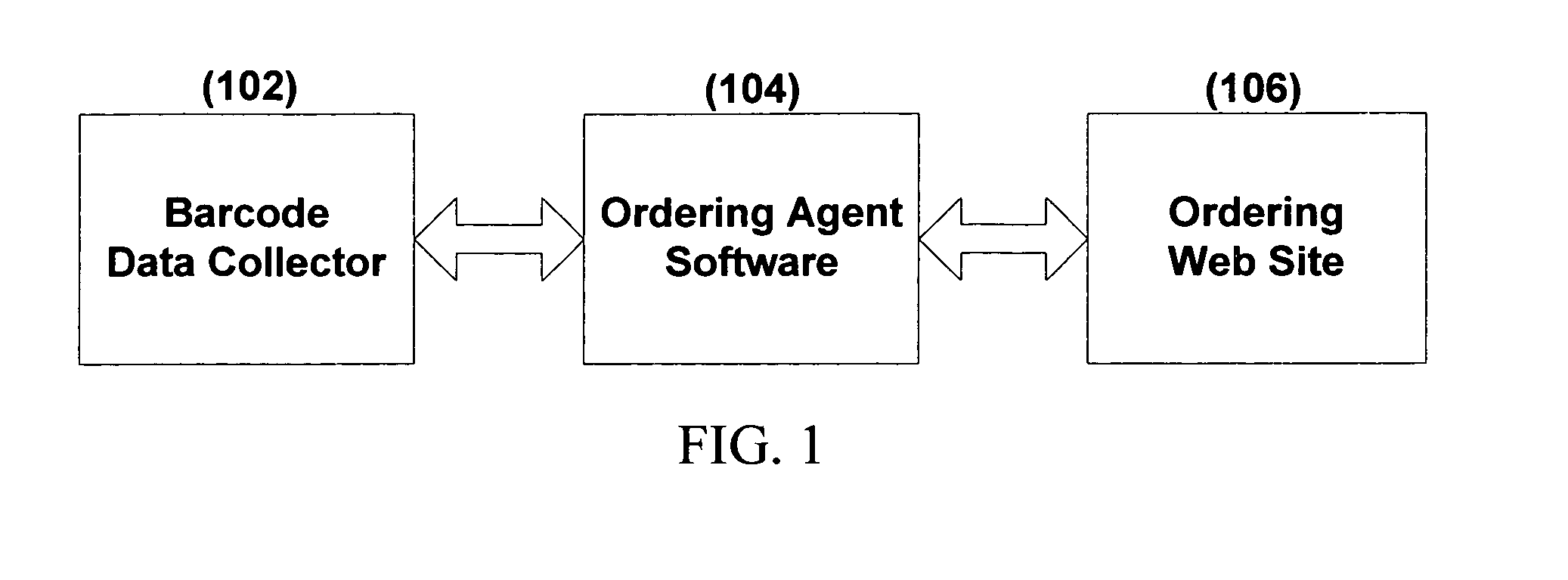
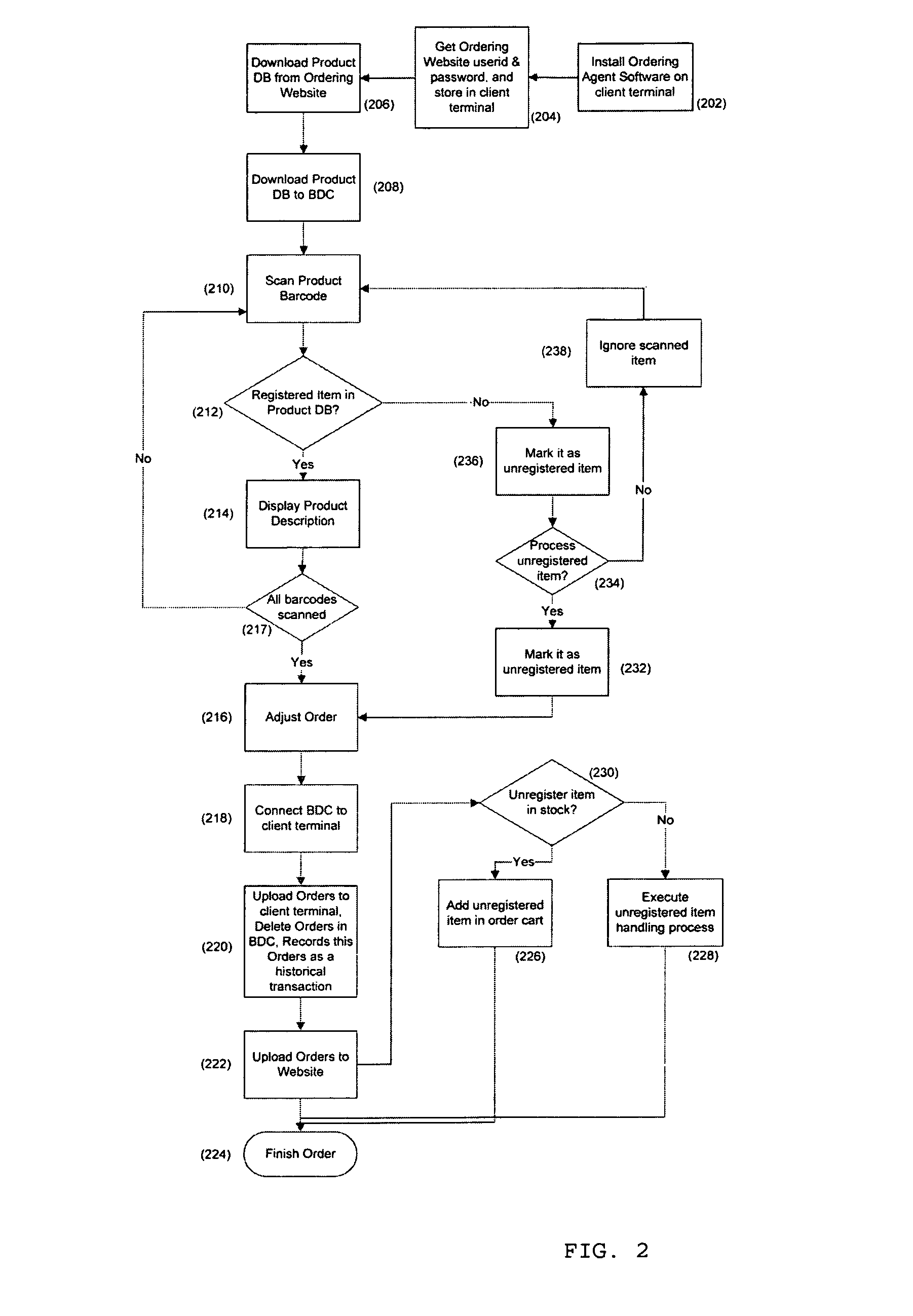
System and method for ordering using barcode data collector and online services
ActiveUS7954710B1Facilitate business transactionFacilitate information exchangeVisual presentationCommerceWeb siteBarcode
The present invention allows a user to place an order on an internal computer system or through a web site automatically by scanning UPC / EAN or product ID barcodes, without the need to modify supplier or other party websites. As such, a compact optical code reader with associated software is disclosed having multiple functions and is capable of performing various data processing functions involving scanned data. The system includes user and supplier identifiers which are employed to facilitate sales transactions.
Owner:KOAMTAC
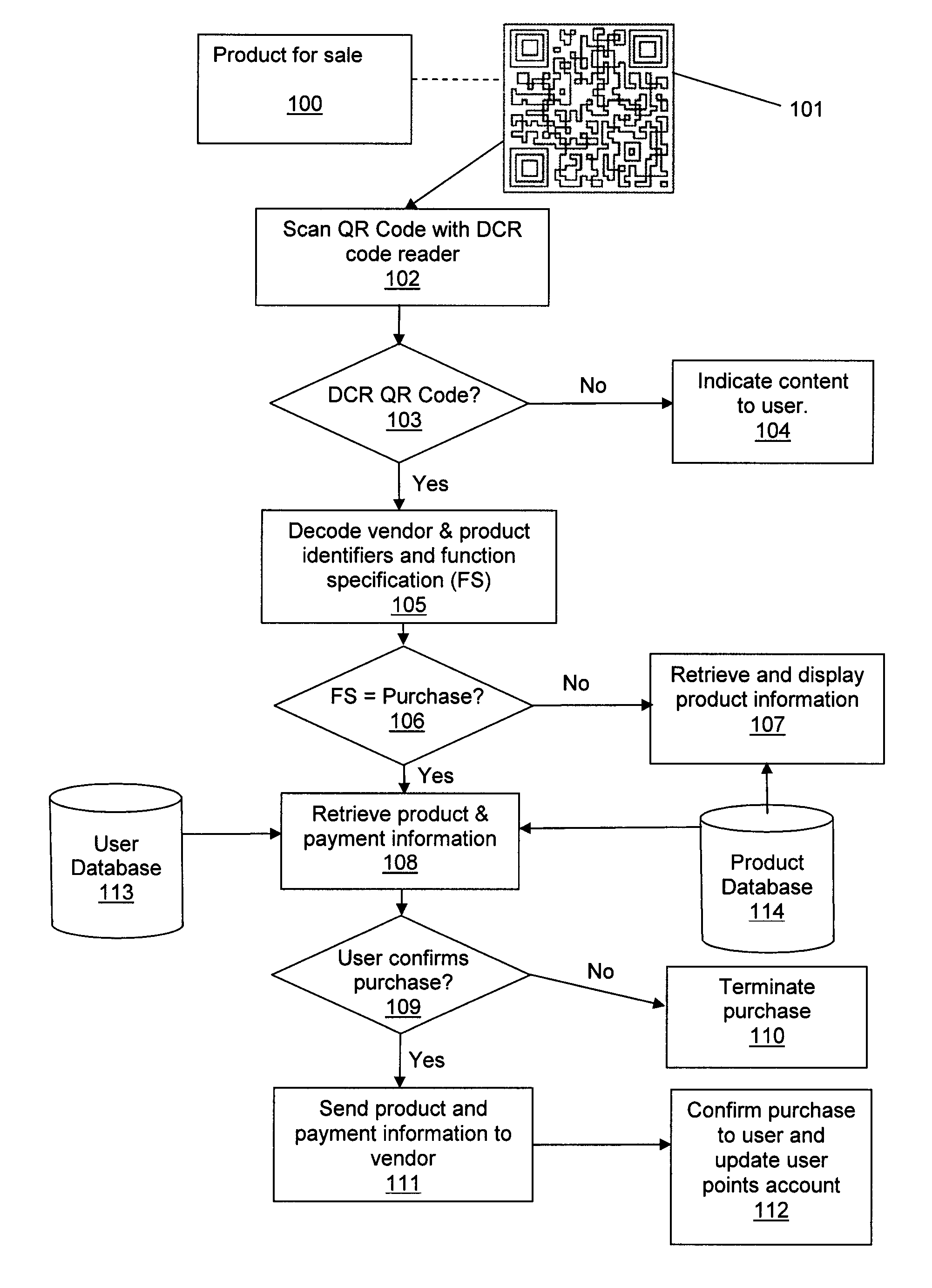
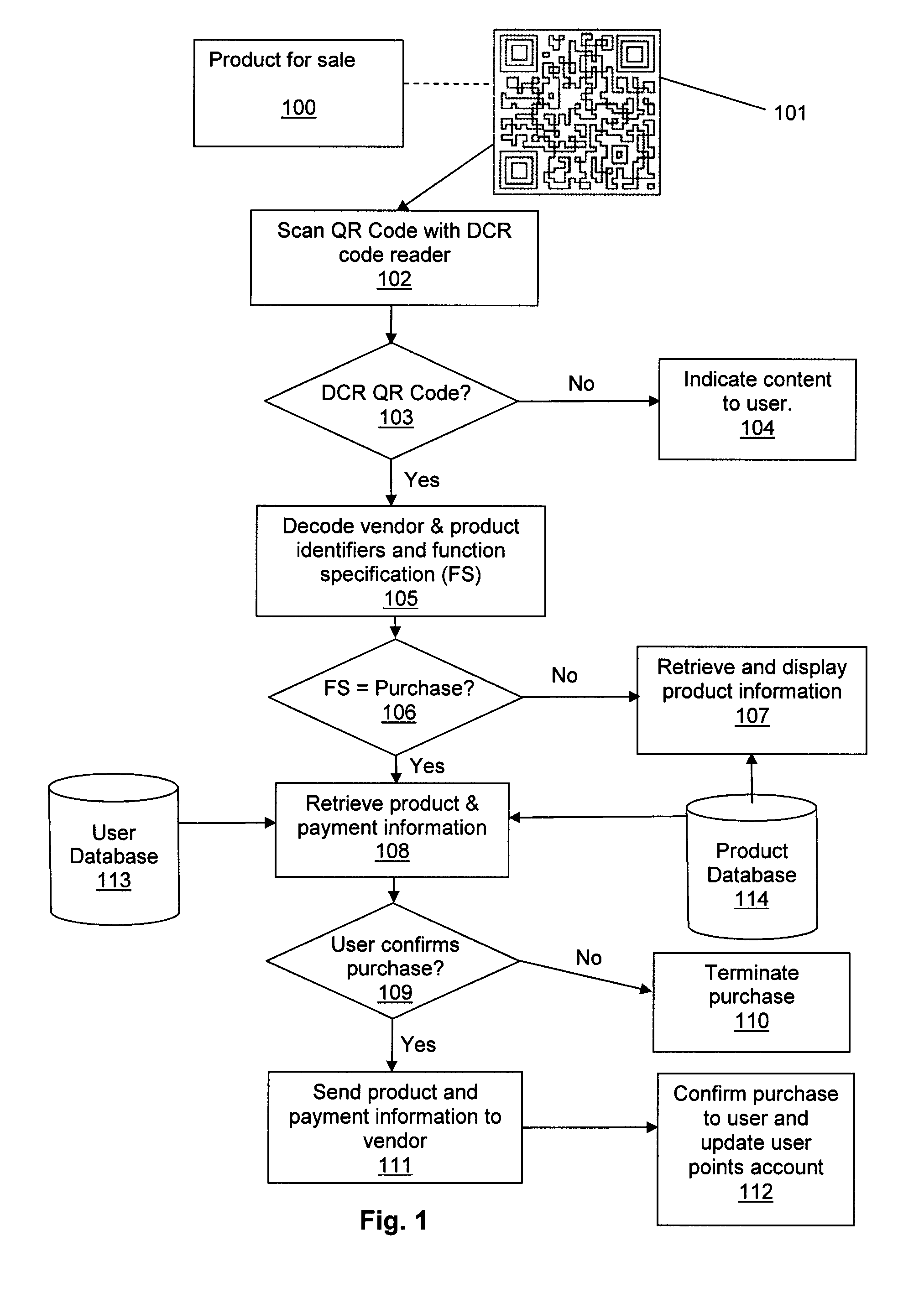
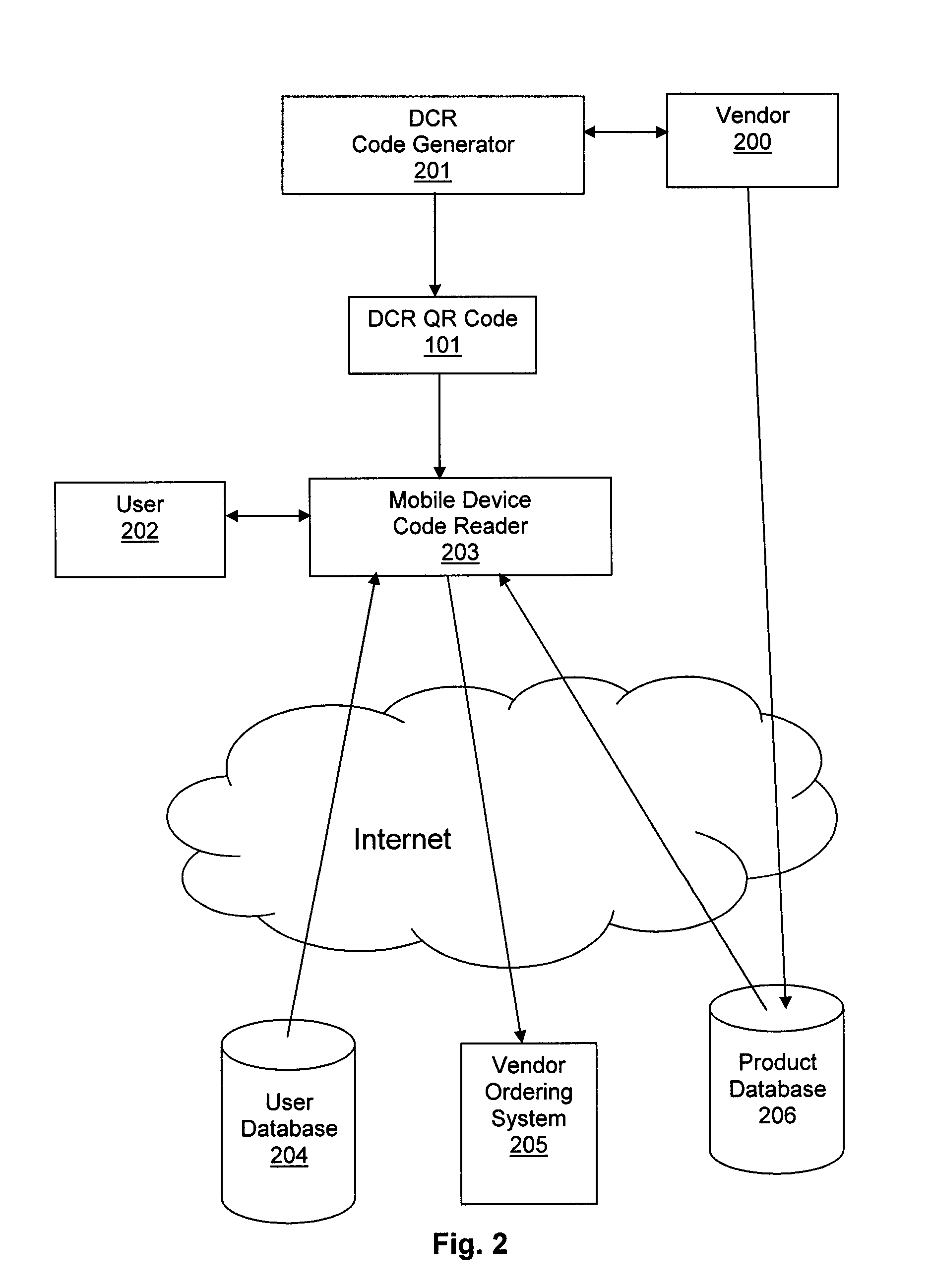
Product information and payment system using scanable codes
InactiveUS20150213434A1Acutation objectsCharacter and pattern recognitionProduct IdentifierCentral database
The present invention is a computer-based system for retrieving and displaying product information, and for purchasing products, by scanning a customized optical machine-readable representations of data, such as a QR code. The system supports products from multiple vendors and maintains a central database in which a user accumulates points by purchasing products associated with the customized codes. The customized codes contain a known identifier to indicate that they are special codes for processing by the system, as well as a product identifier and a vendor identifier.
Owner:DCR STRATEGIES
Distributing secret keys for managing access to ECUs
ActiveCN105490803AKey distribution for secure communicationSecurity arrangementSupplier identifierAuthorization
A system and method of controlling access to electronic control units (ECUs) includes: receiving, at an ECU supplier computer, a supplier encryption key derived from a master encryption key using a supplier identifier that identifies an ECU supplier; issuing an ECU identifier that identifies an ECU and includes the supplier identifier; generating for the ECU an ECU unlock authorization key using the supplier encryption key and the ECU identifier; and storing the ECU unlock authorization key and the ECU identifier in the ECU.
Owner:GM GLOBAL TECH OPERATIONS LLC
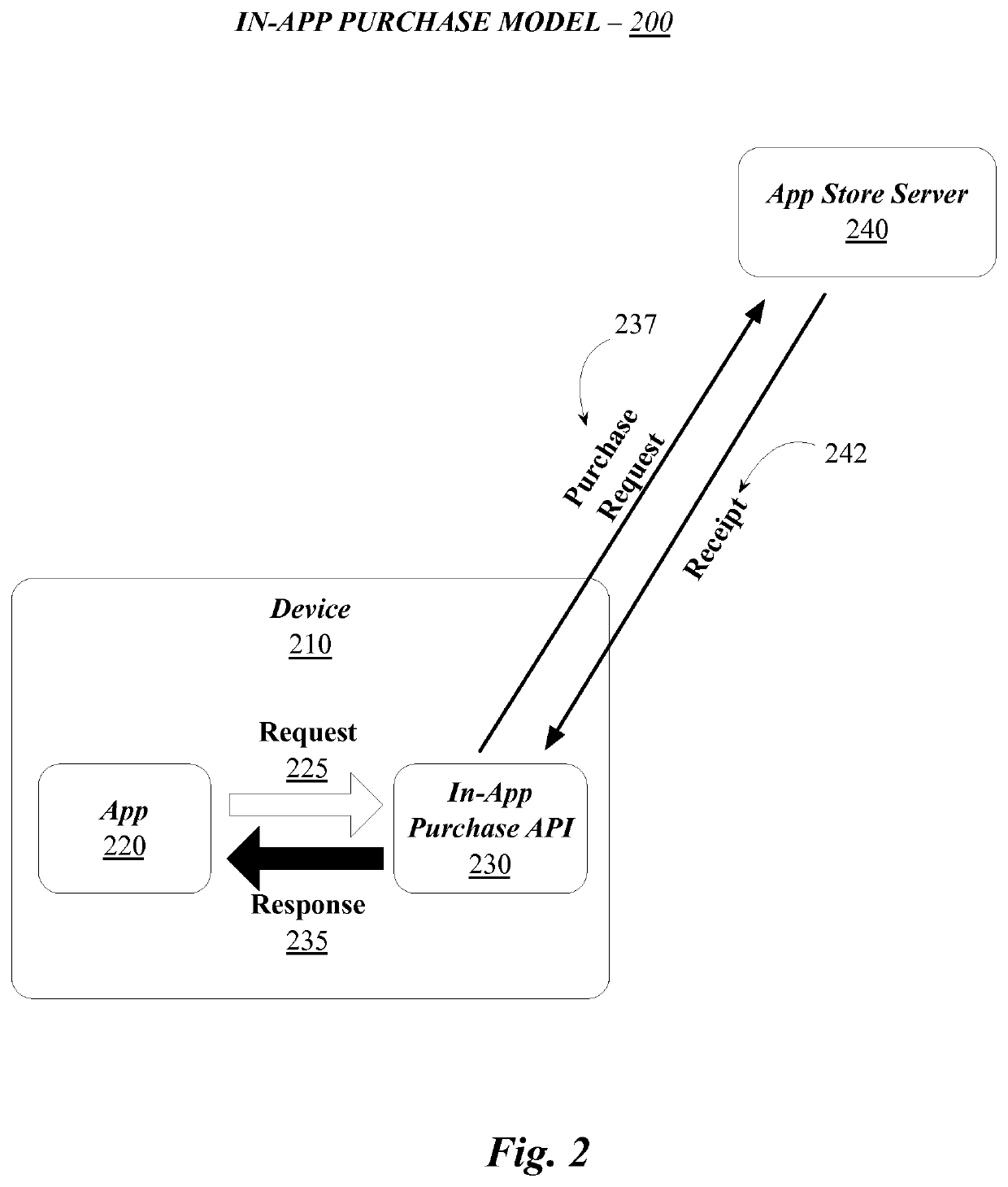
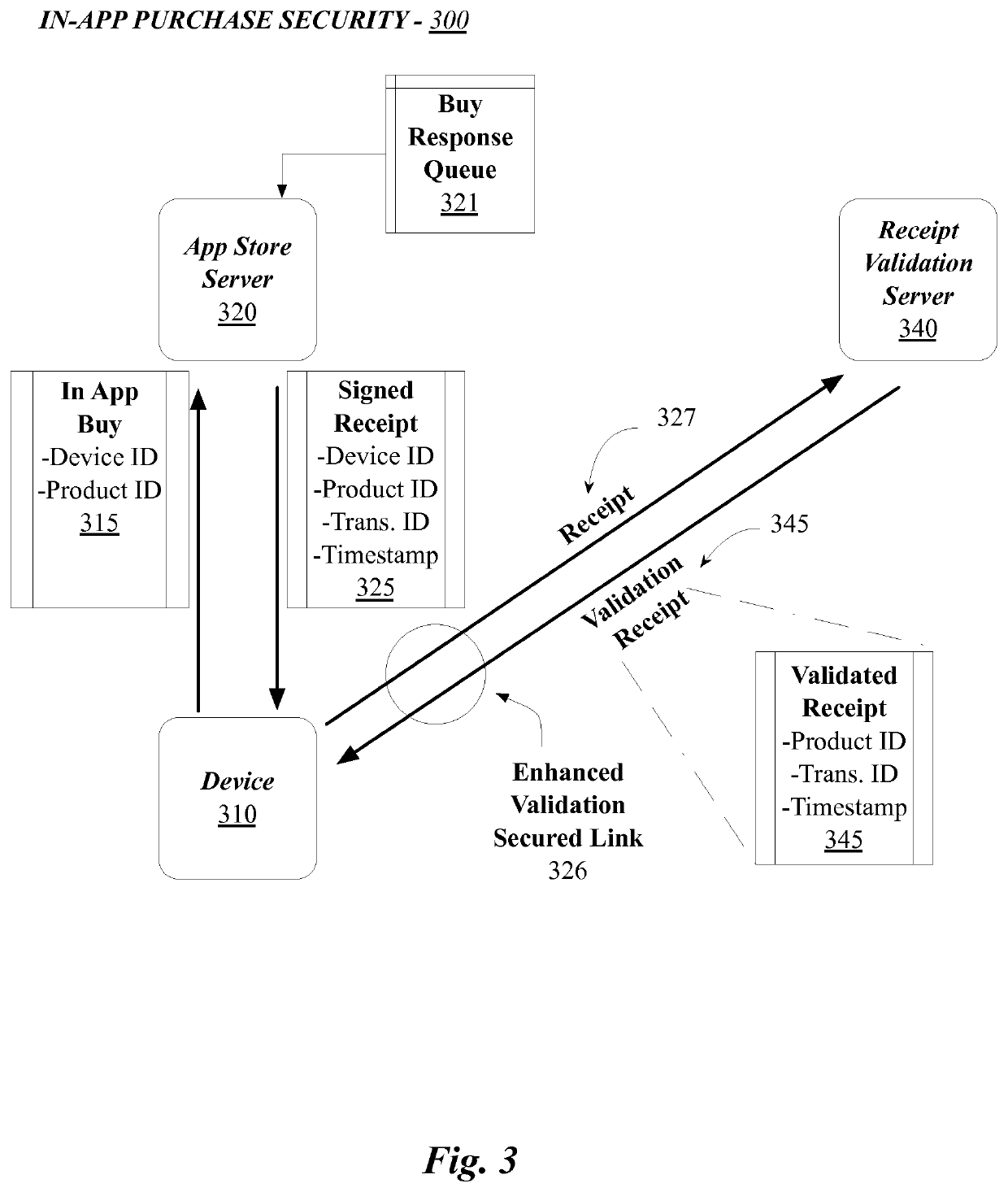
Securing in-app purchases
In one embodiment, a unique (or quasi unique) identifier can be received by an application store, or other on-line store, and the store can create a signed receipt that includes data desired from the unique identifier. This signed receipt is then transmitted to a device that is running the application obtained from the on-line store and the device can verify the receipt by deriving the unique (or quasi-unique) identifier from the signed receipt and comparing the derived identifier with the device identifier stored on the device, or the vendor identifier assigned to the application vendor.
Owner:APPLE INC
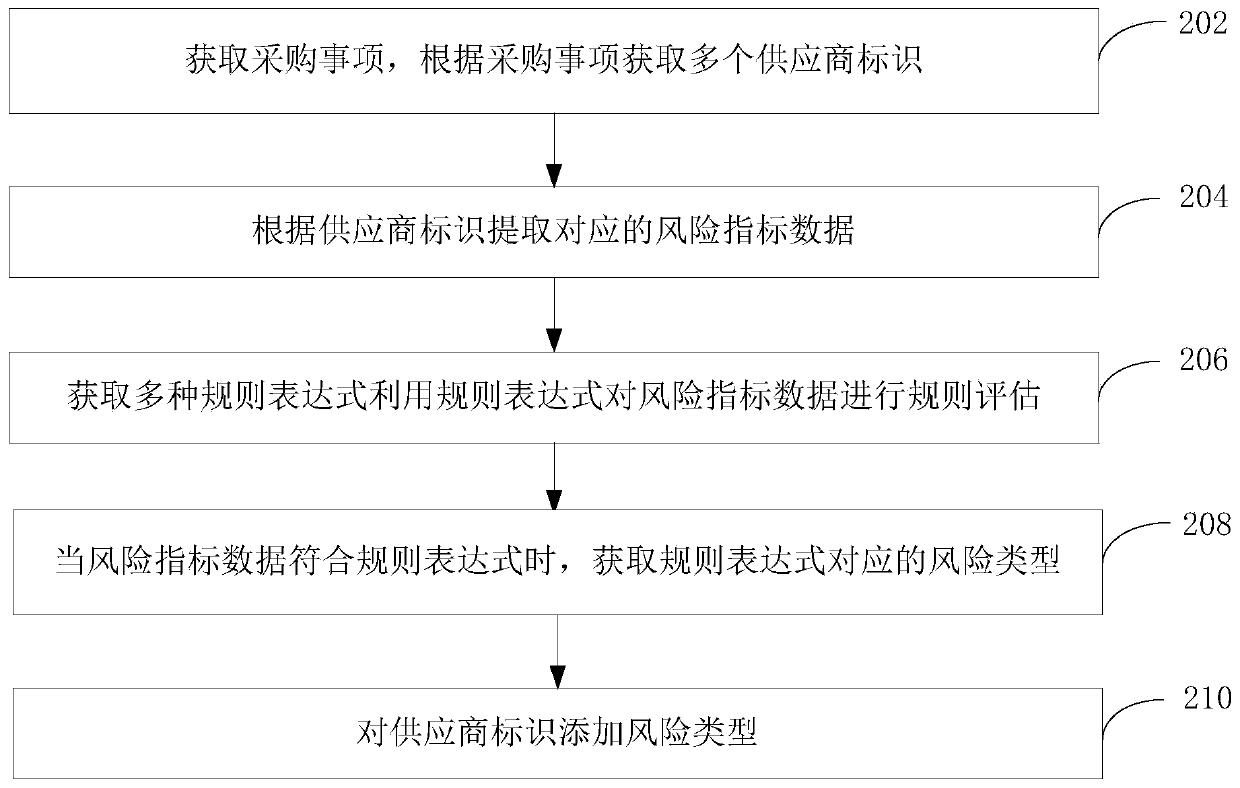
Supplier risk assessment processing method and device, computer equipment and storage medium
PendingCN109872050AImprove accuracyAccurate identificationResourcesDecision takingSupplier identifier
The invention relates to a supplier risk assessment processing method and device based on intelligent decision in the field of artificial intelligence, computer equipment and a storage medium. The method comprises the steps of obtaining purchase items, and obtaining a plurality of supplier identifiers according to the purchase items; Extracting corresponding risk index data according to the supplier identifier; Obtaining a plurality of rule expressions, and performing rule evaluation on the risk index data by utilizing the rule expressions; When the risk index data conforms to a rule expression, obtaining a risk type corresponding to the rule expression; And adding the risk type to the supplier identifier. By adopting the method, the accuracy of risk assessment on the supplier can be effectively improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
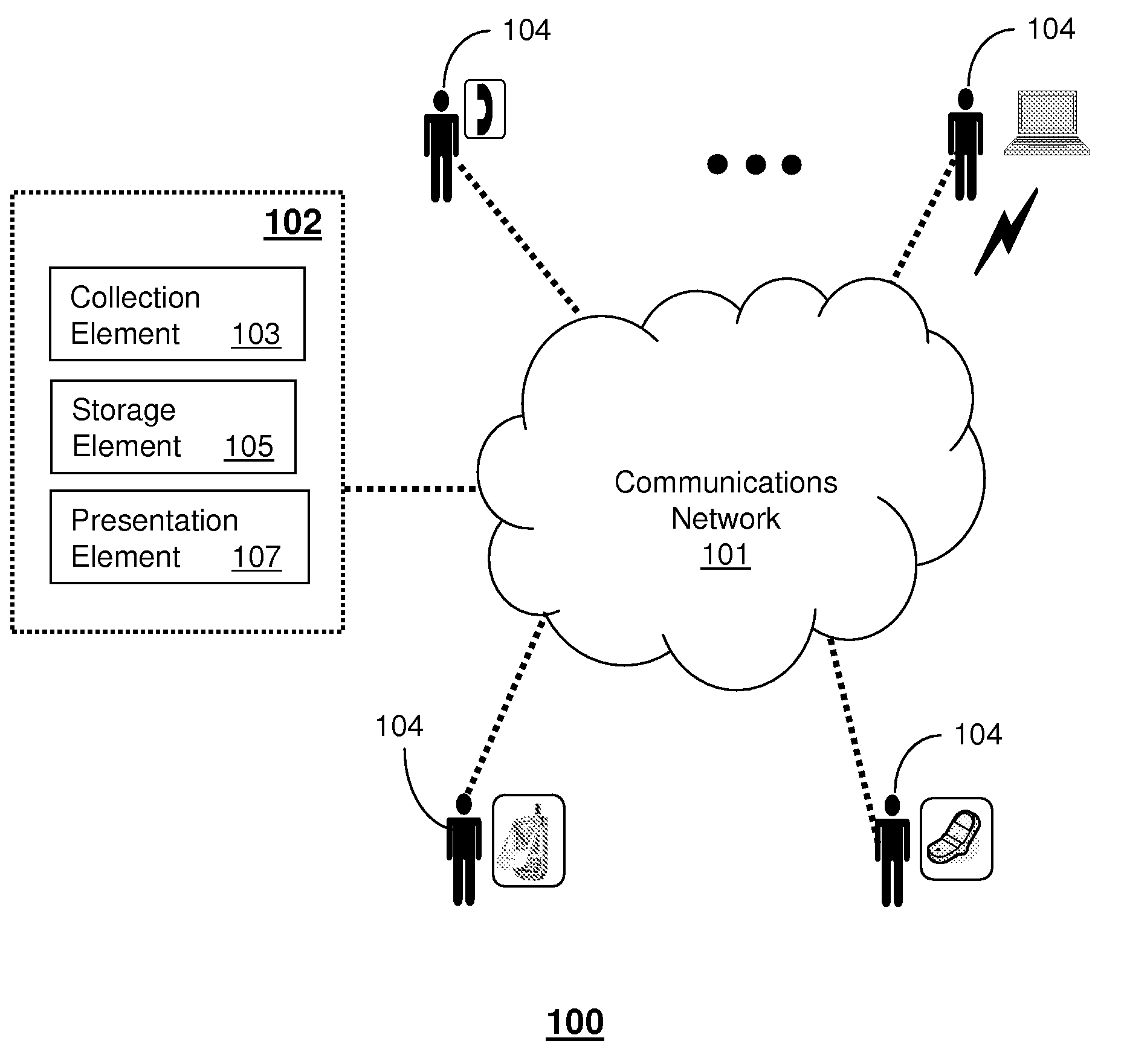
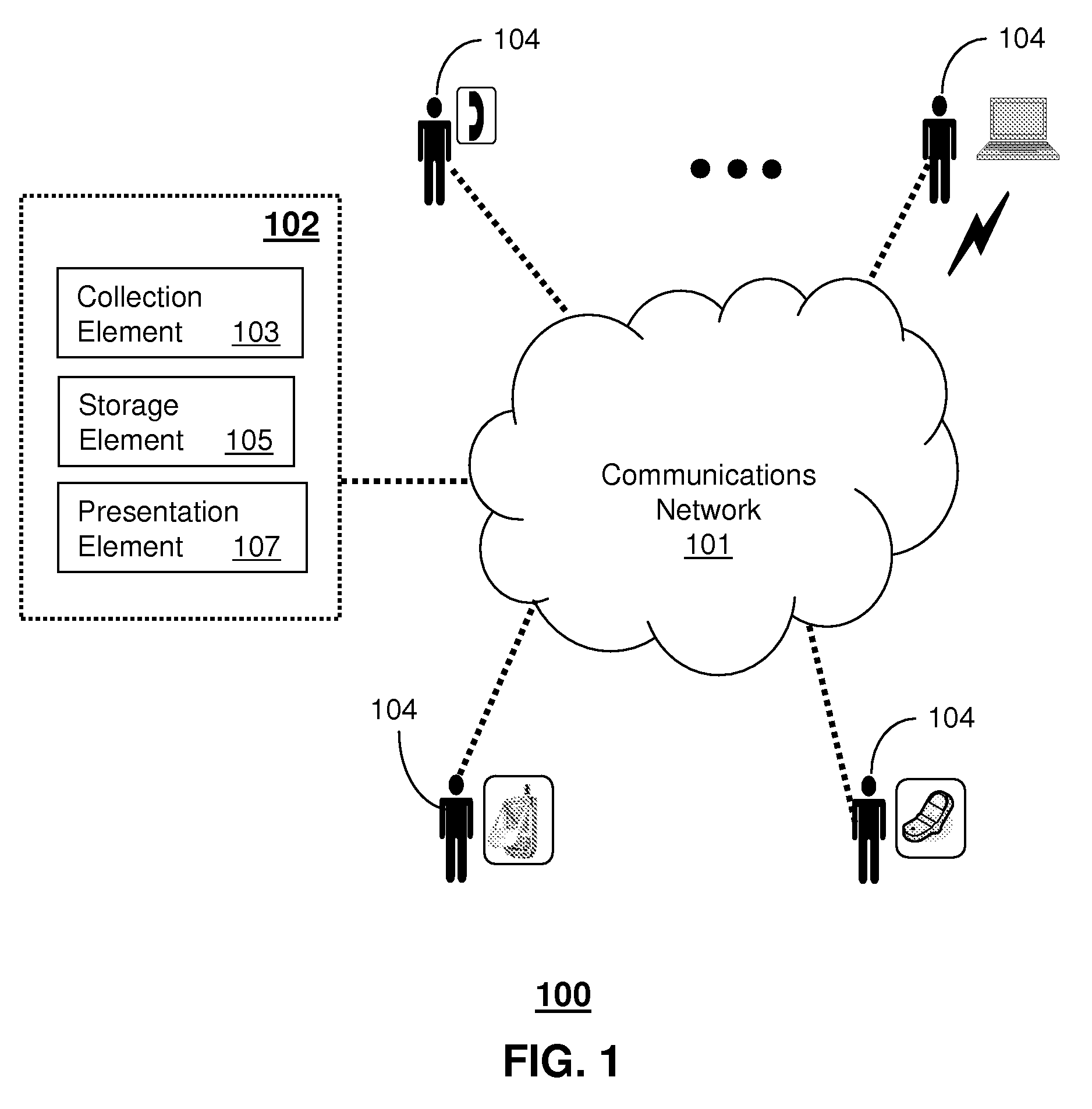
Method and apparatus for sharing end user feedback
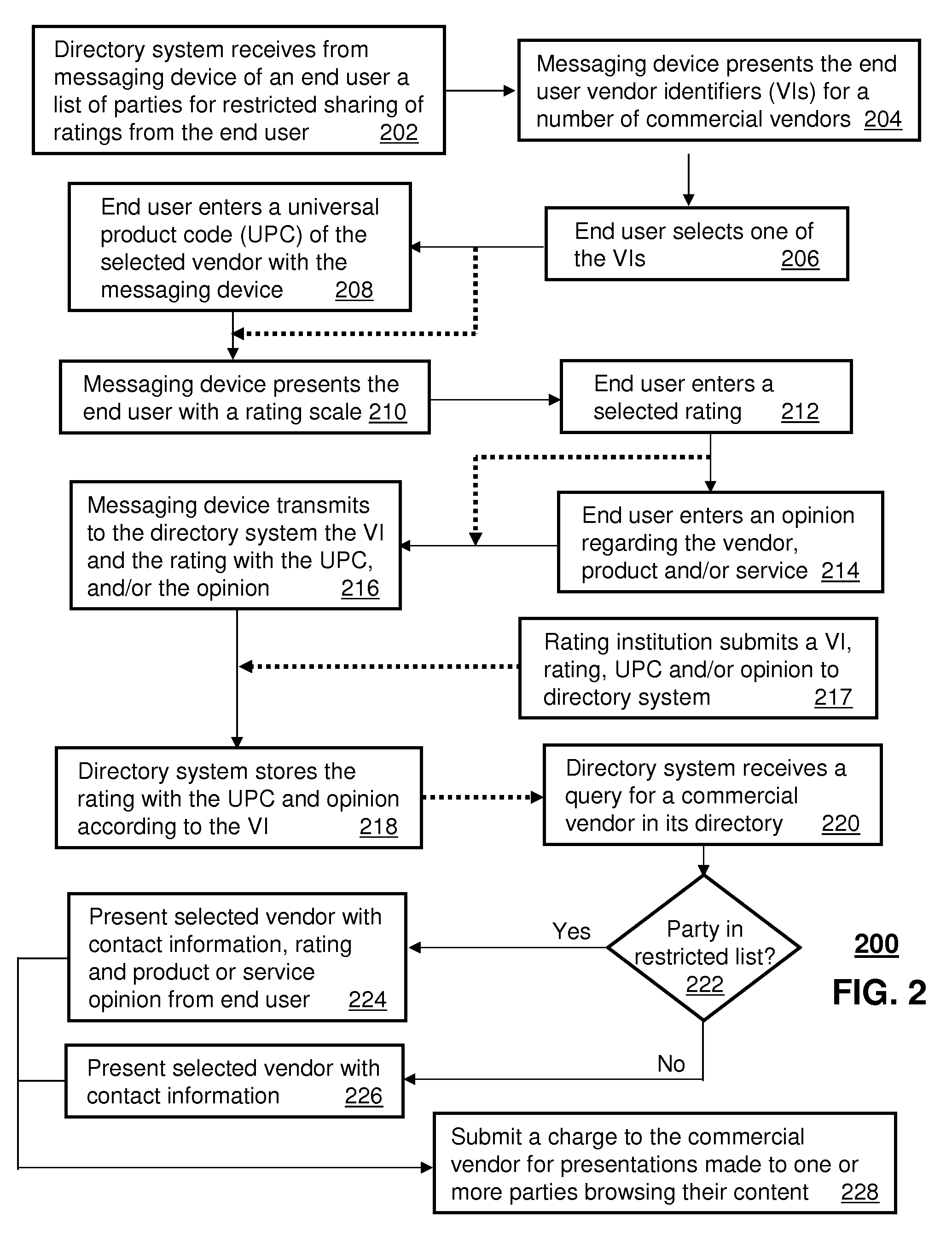
A method and apparatus for sharing end user feedback is disclosed. An apparatus that incorporates teachings of the present disclosure may include, for example, a system can have a collection element that receives a vendor identifier and a measure of satisfaction associated therewith, and a storage element that stores the measure of satisfaction in a telephone directory of commercial vendors according to the vendor identifier. Additional embodiments are disclosed.
Owner:AT&T INTPROP I L P
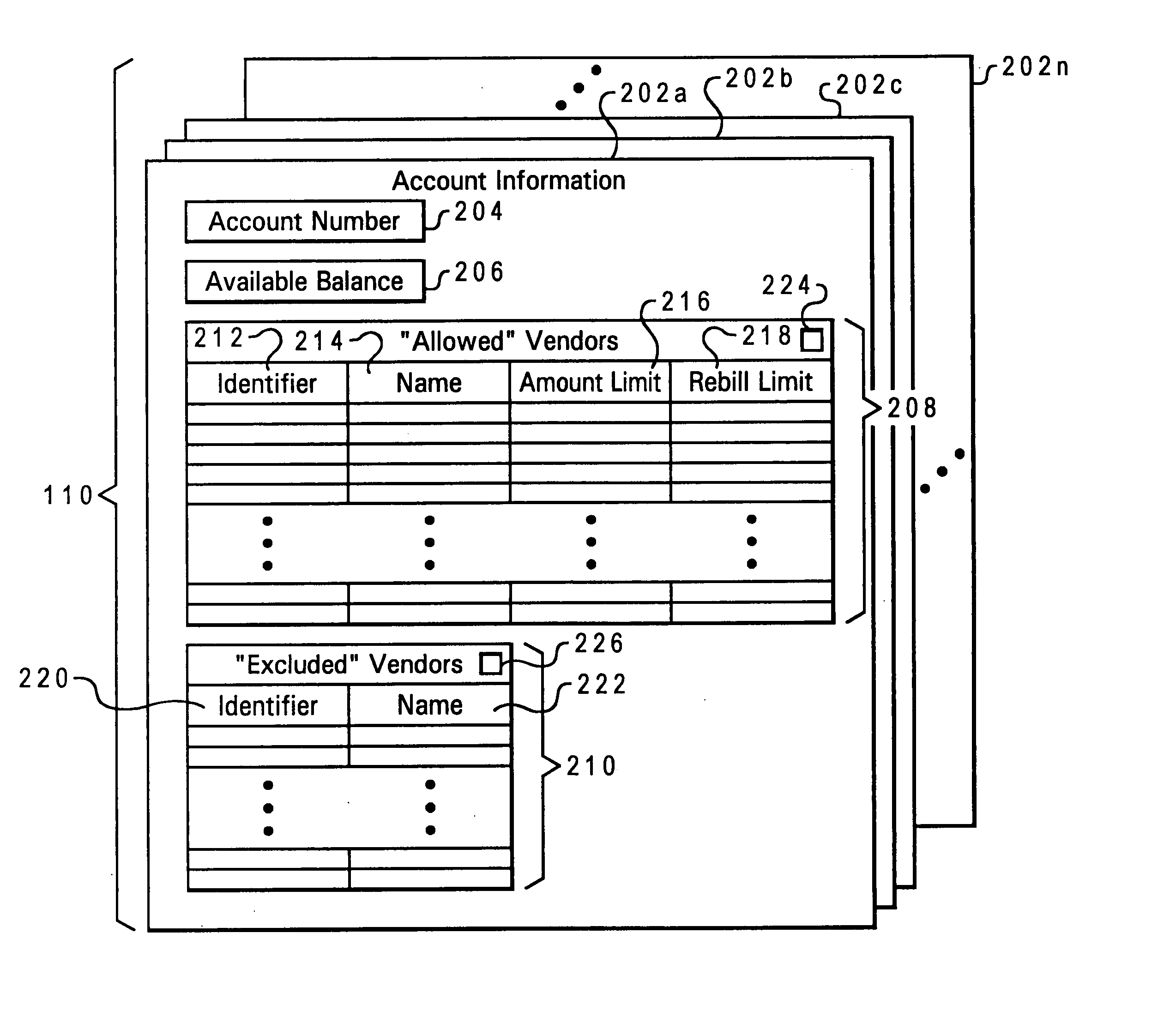
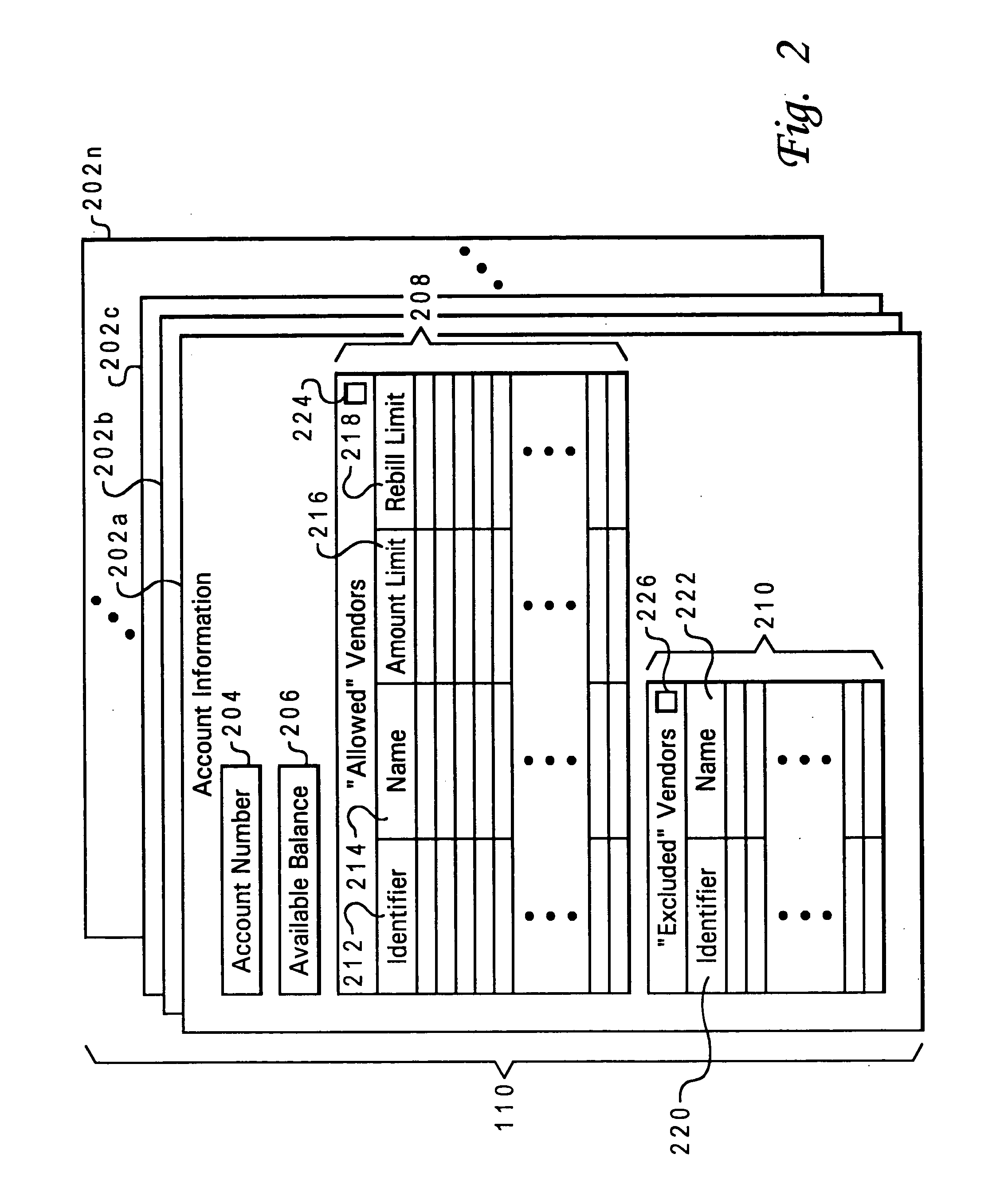
Personally customizable credit card accounts
InactiveUS20050144123A1Increase costImproved security of and controlFinanceCredit schemesCredit cardUnique identifier
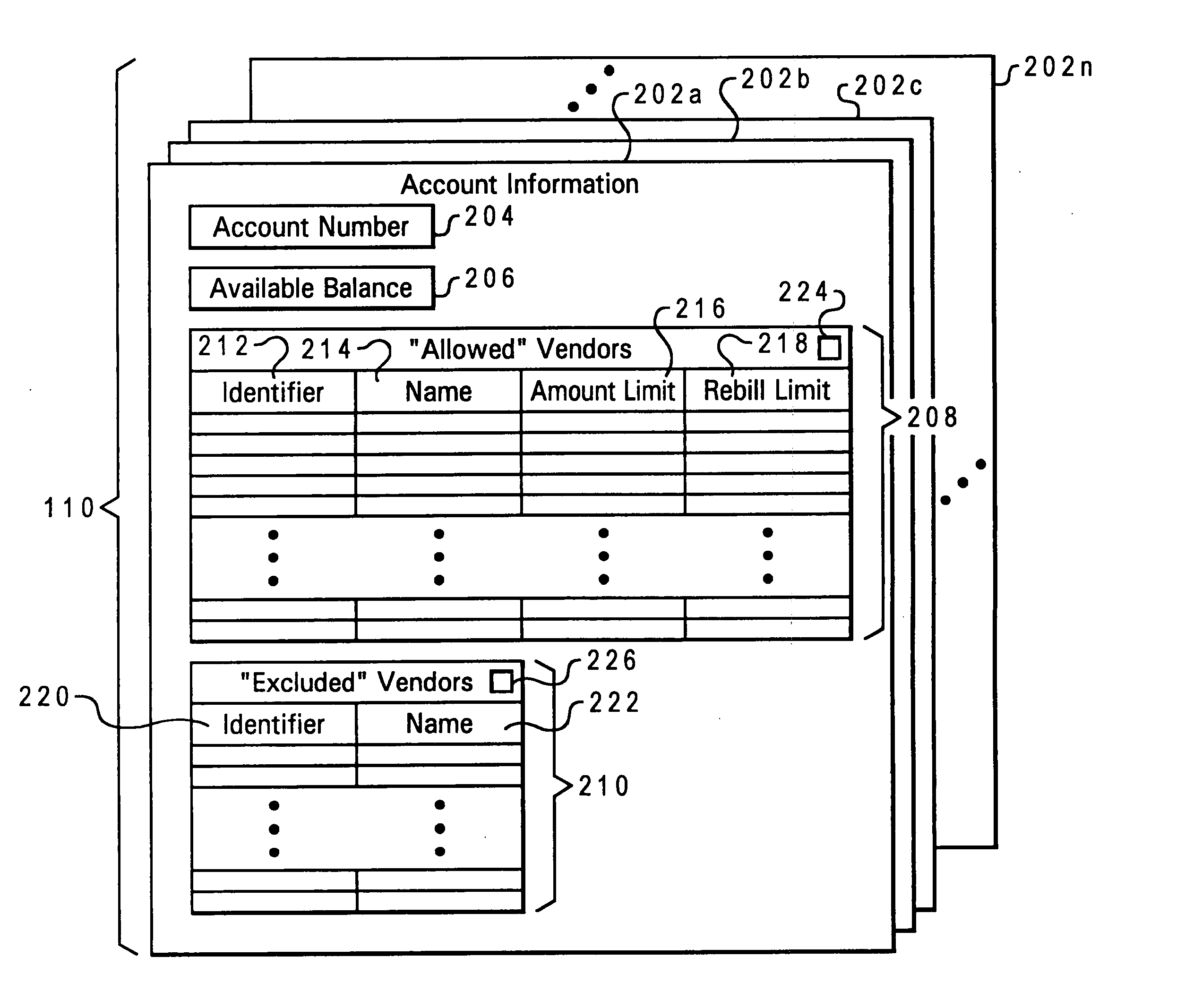
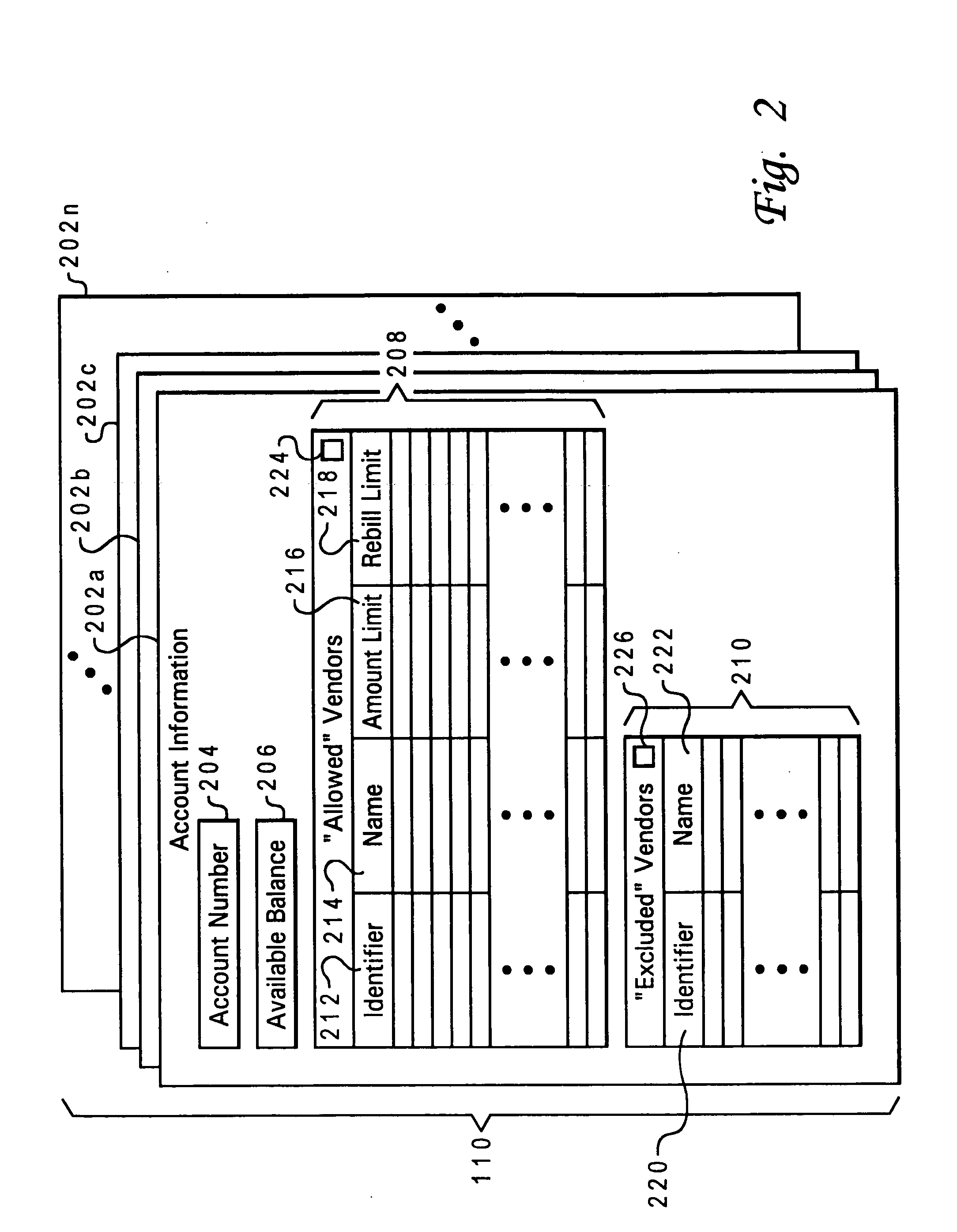
Account holders may specify vendor-specific charge restrictions for charging transactions against their accounts, where each vendor-specific charge restriction includes a unique identifier for the corresponding vendor to which the charge restriction is applicable. The charge restriction may be an exclusion from approval of all charge authorization requests, an amount limit on charge authorization requests which may be approved, a “rebill” limit on the number of times subsequent charge authorization requests may be approved, or a combination of such restrictions and / or other restrictions. When a charge authorization request is received for a charge against an account having vendor-specific charge restrictions set by the account holder, the vendor identifier is extracted from the charge authorization request and employed to determine whether any charge restrictions are applicable to the requesting vendor. The vendor-specific charge restrictions for a particular vendor may be specified by the account holder either before or after an initial charge transactions involving that vendor, with the vendor identifier either manually entered by the account holder or automatically extracted from an account transaction record.
Owner:PAYPAL INC
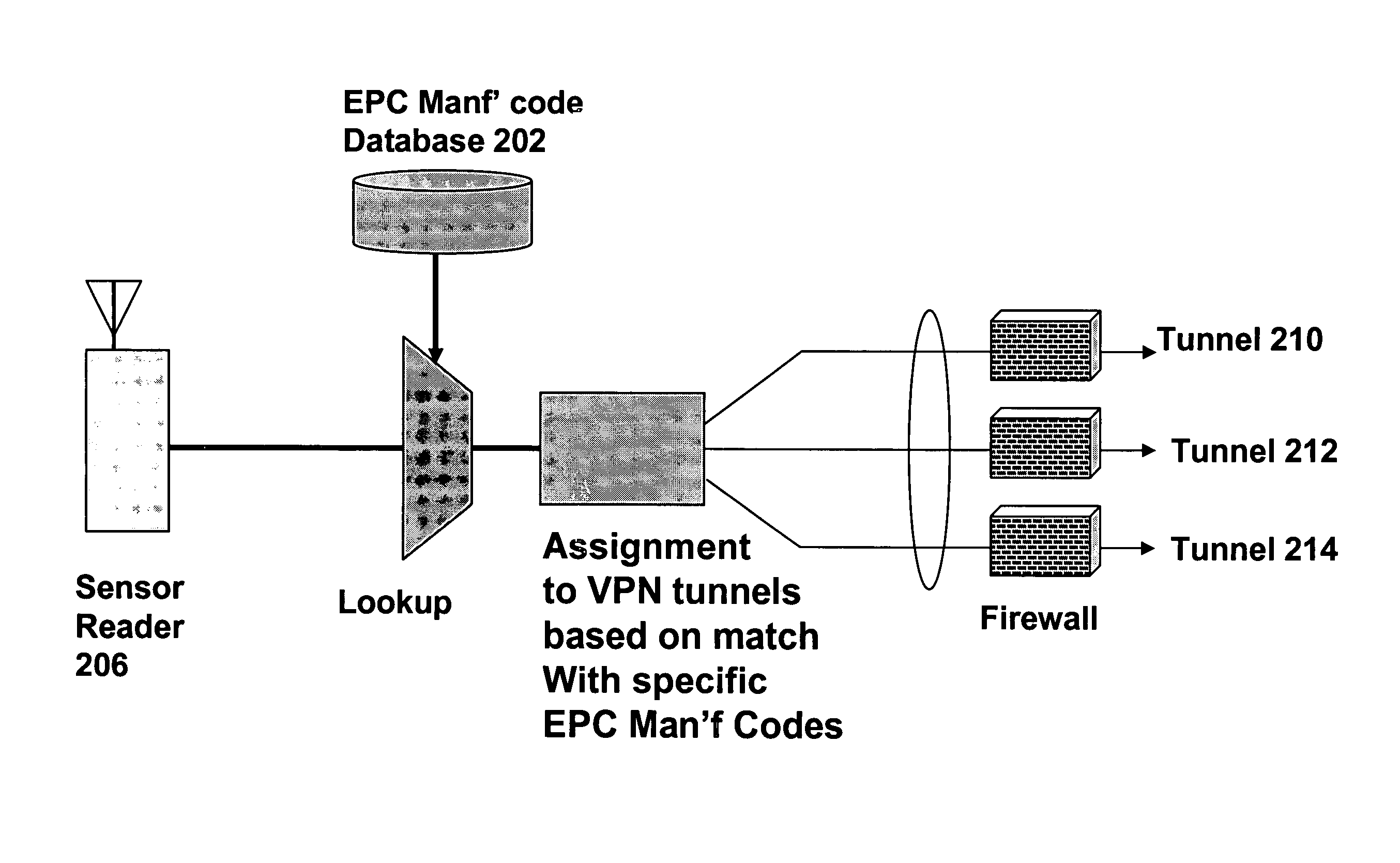
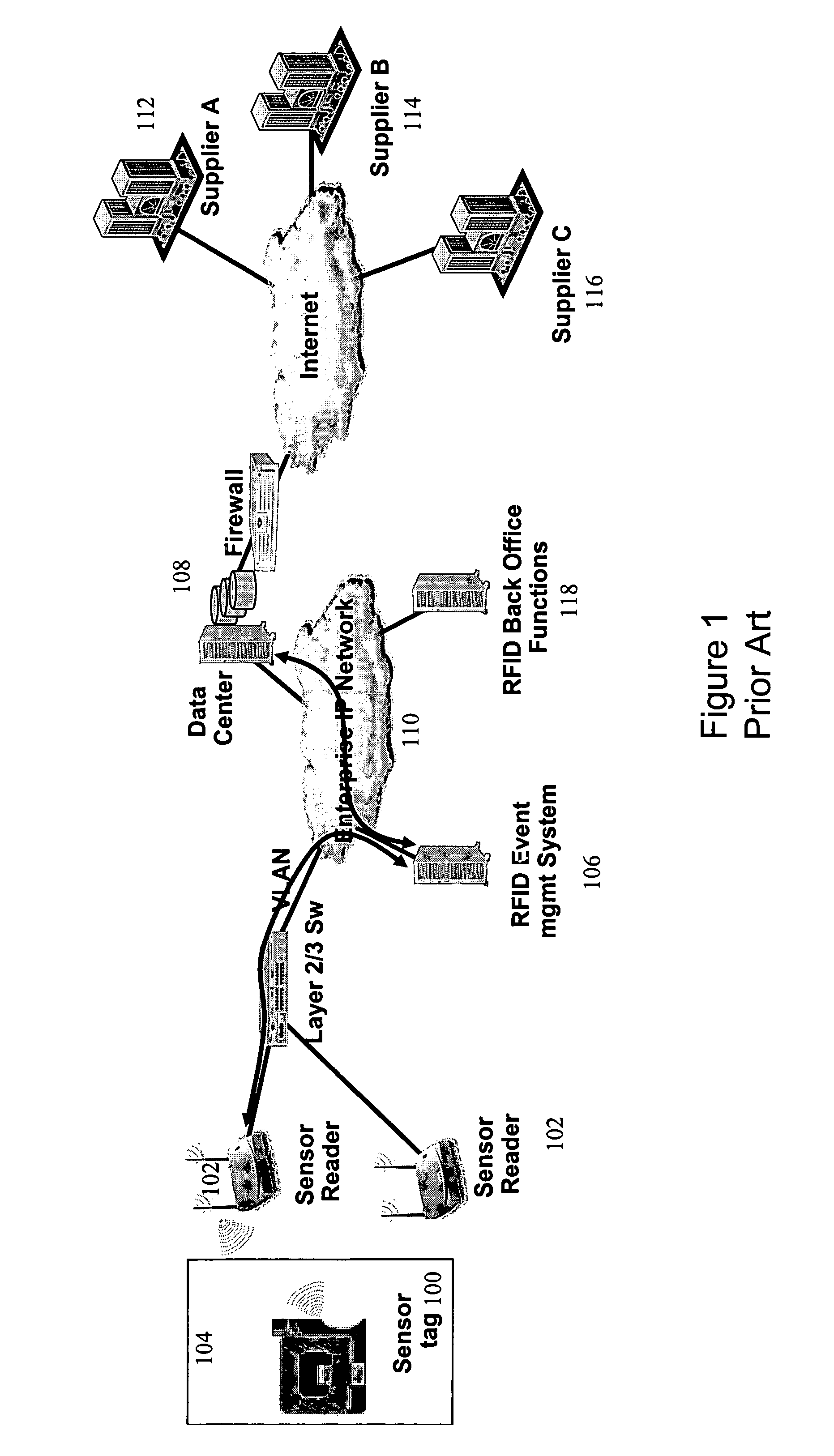
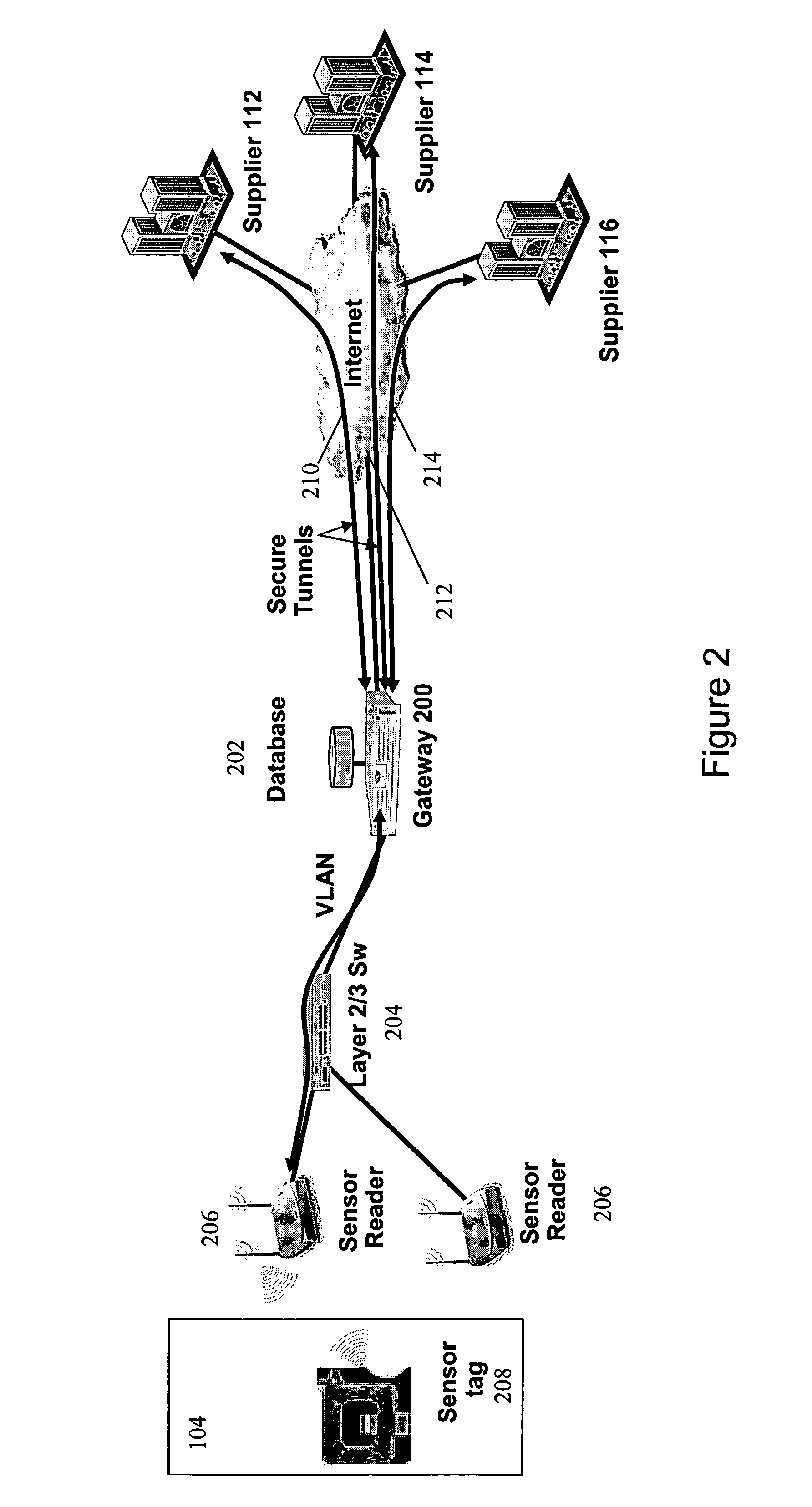
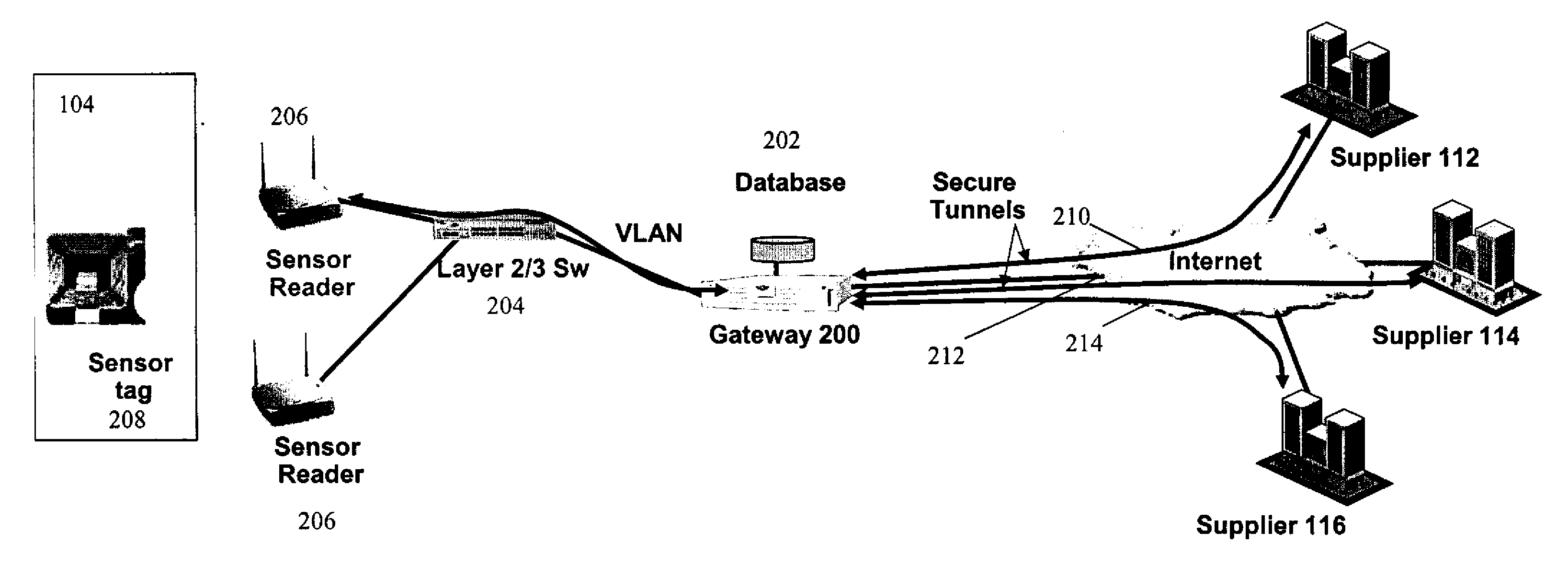
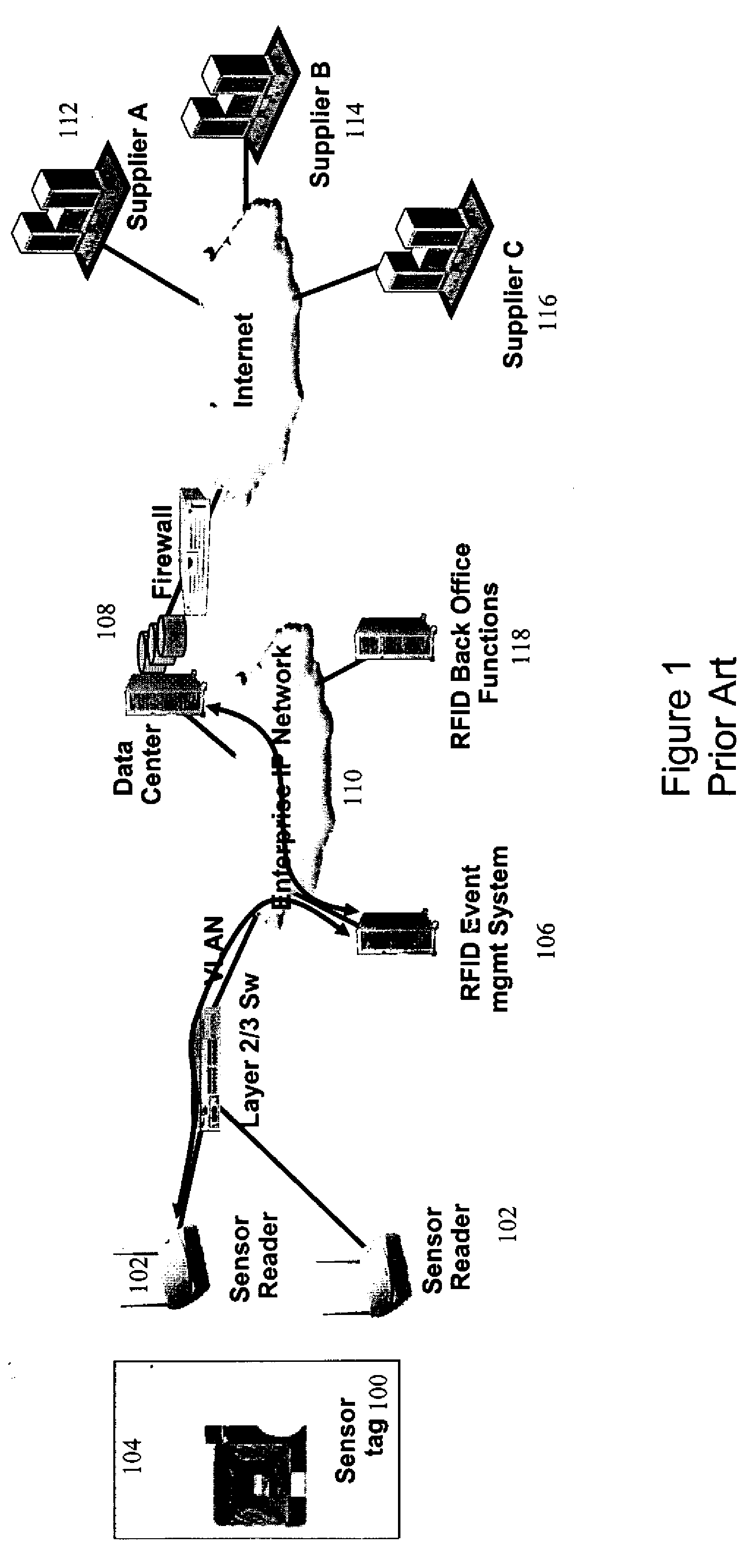
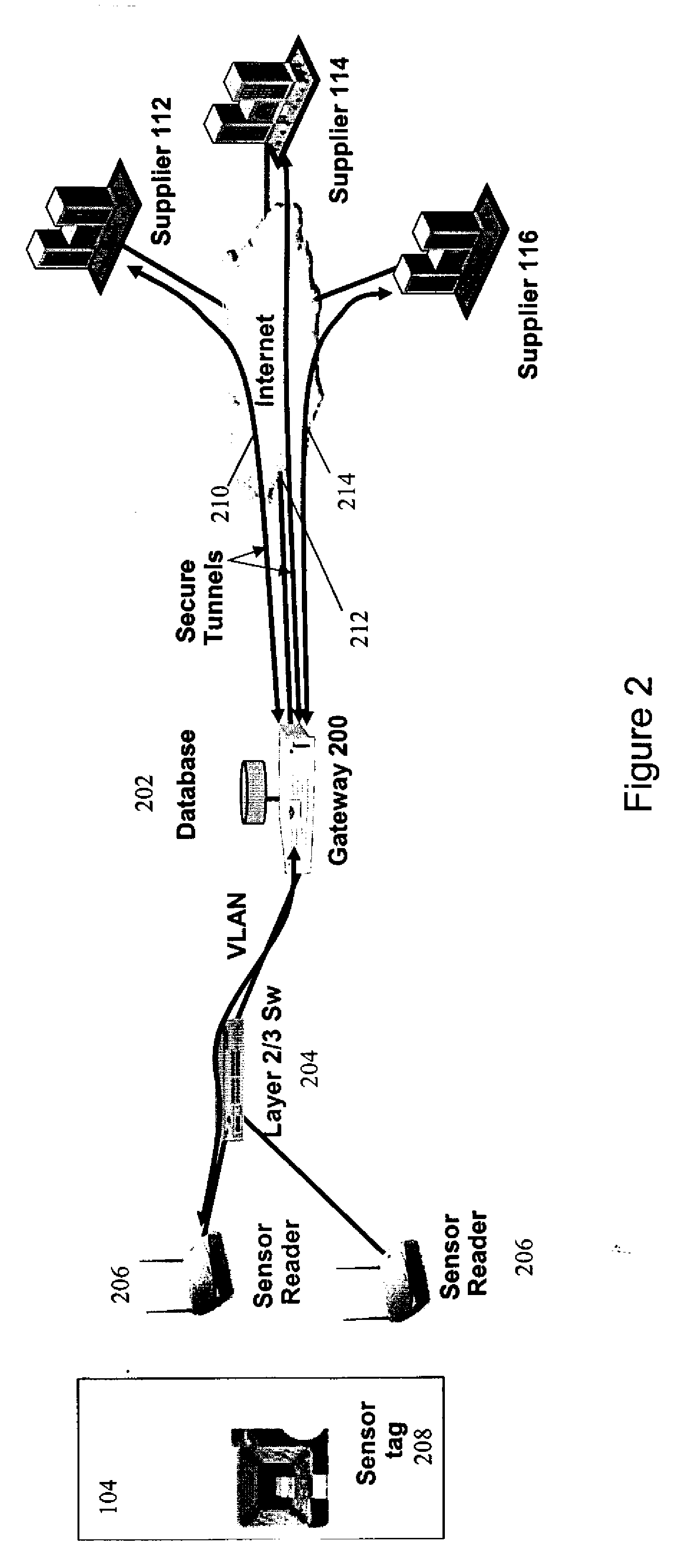
Secure, differentiated reading of sensors and RFID tags
Secure access to inventory data concerning a supplier's product located at a seller's premises is provided by tagging units of product with a supplier identifier and a product identifier. The identifiers may be embedded in RFID tags or EPC labels. A secure VPN tunnel is established between a supplier and a seller. The VPN tunnel is associated with a particular supplier identifier such that only inventory data associated with the supplier identifier that matches the supplier is transmitted on the VPN tunnel, and inventory data associated with supplier identifiers that do not match the supplier are filtered out. Hence, the seller can provide the supplier with access to inventory data without exposing sensitive information related to the seller and other suppliers.
Owner:RPX CLEARINGHOUSE
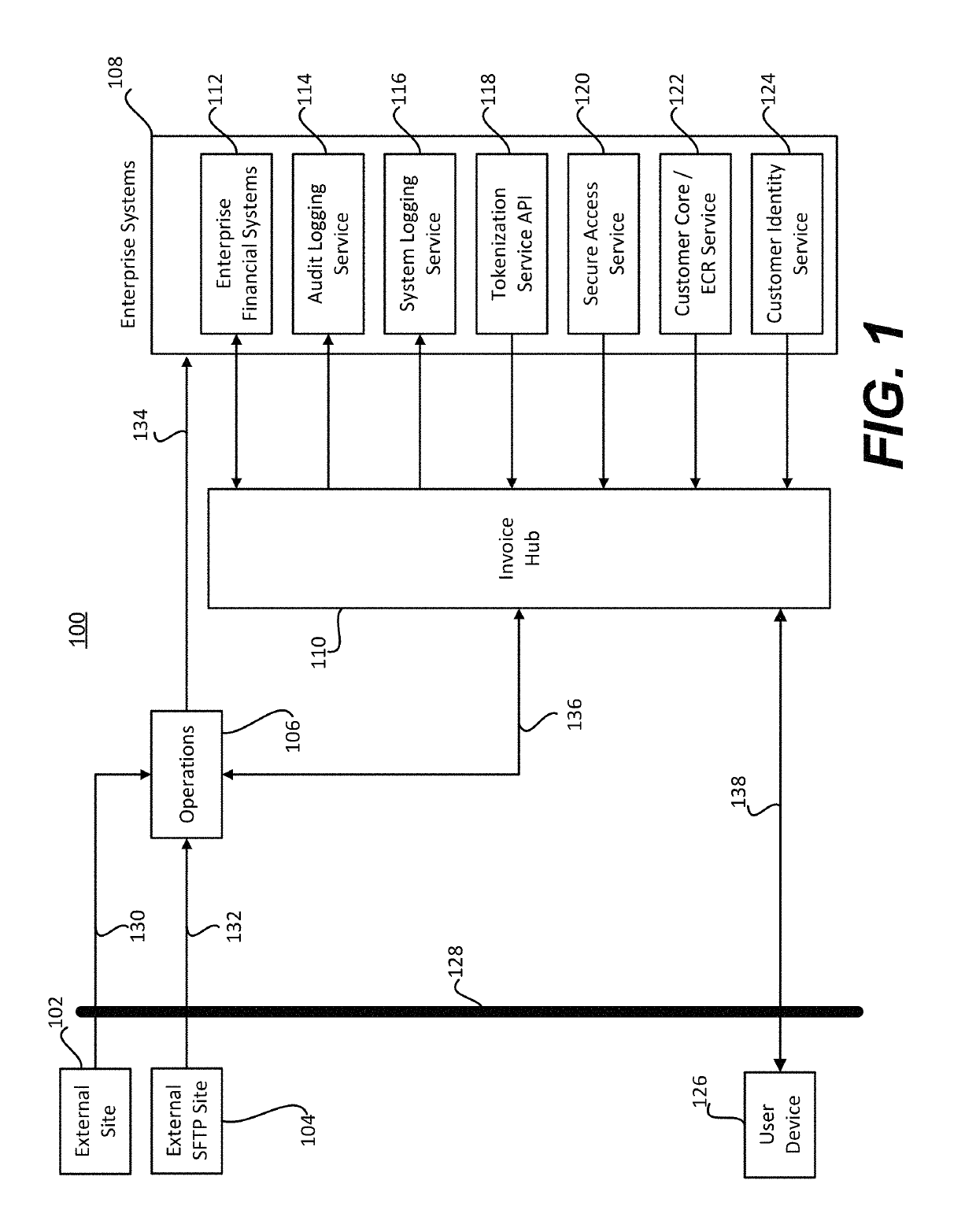
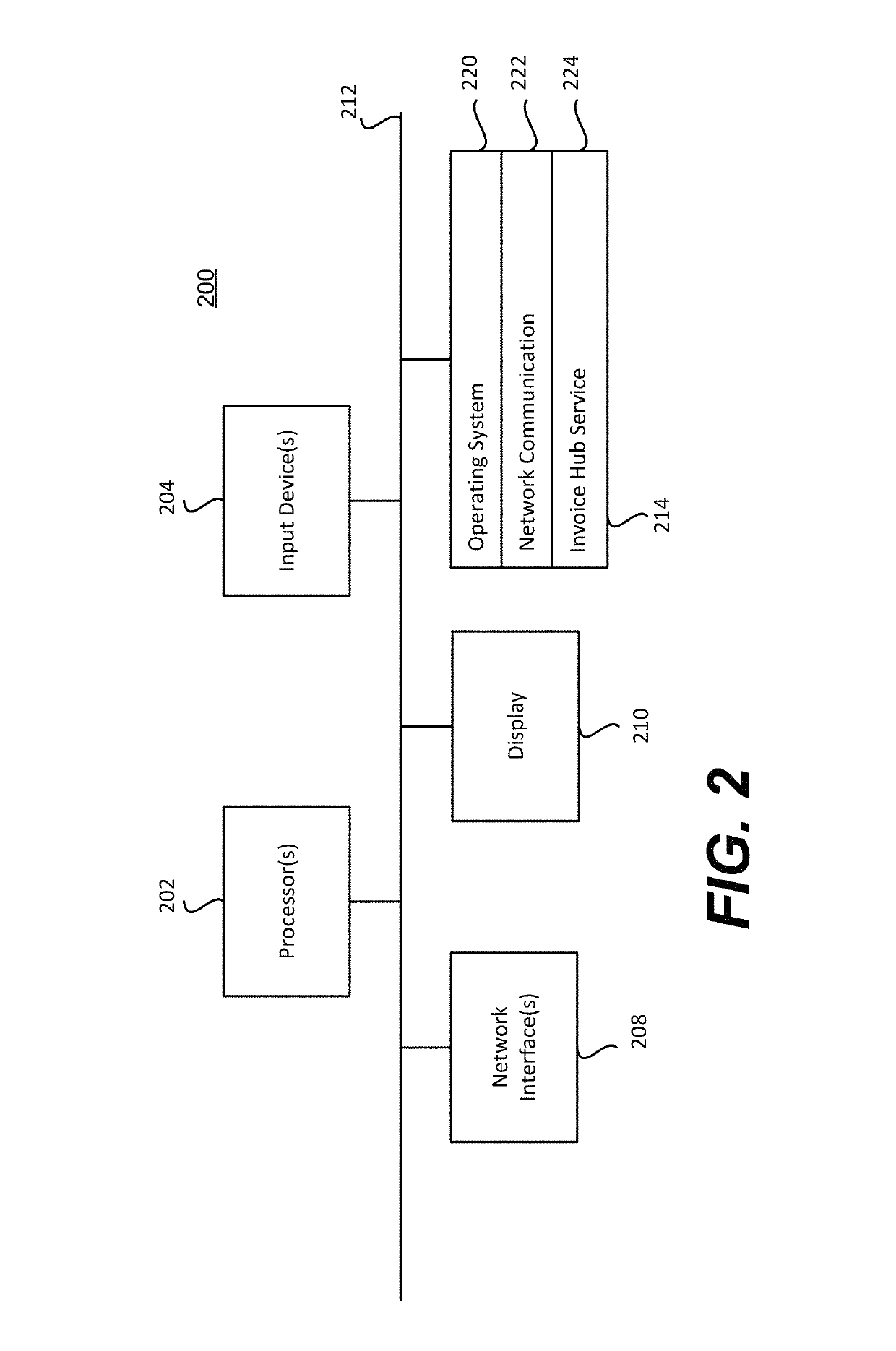
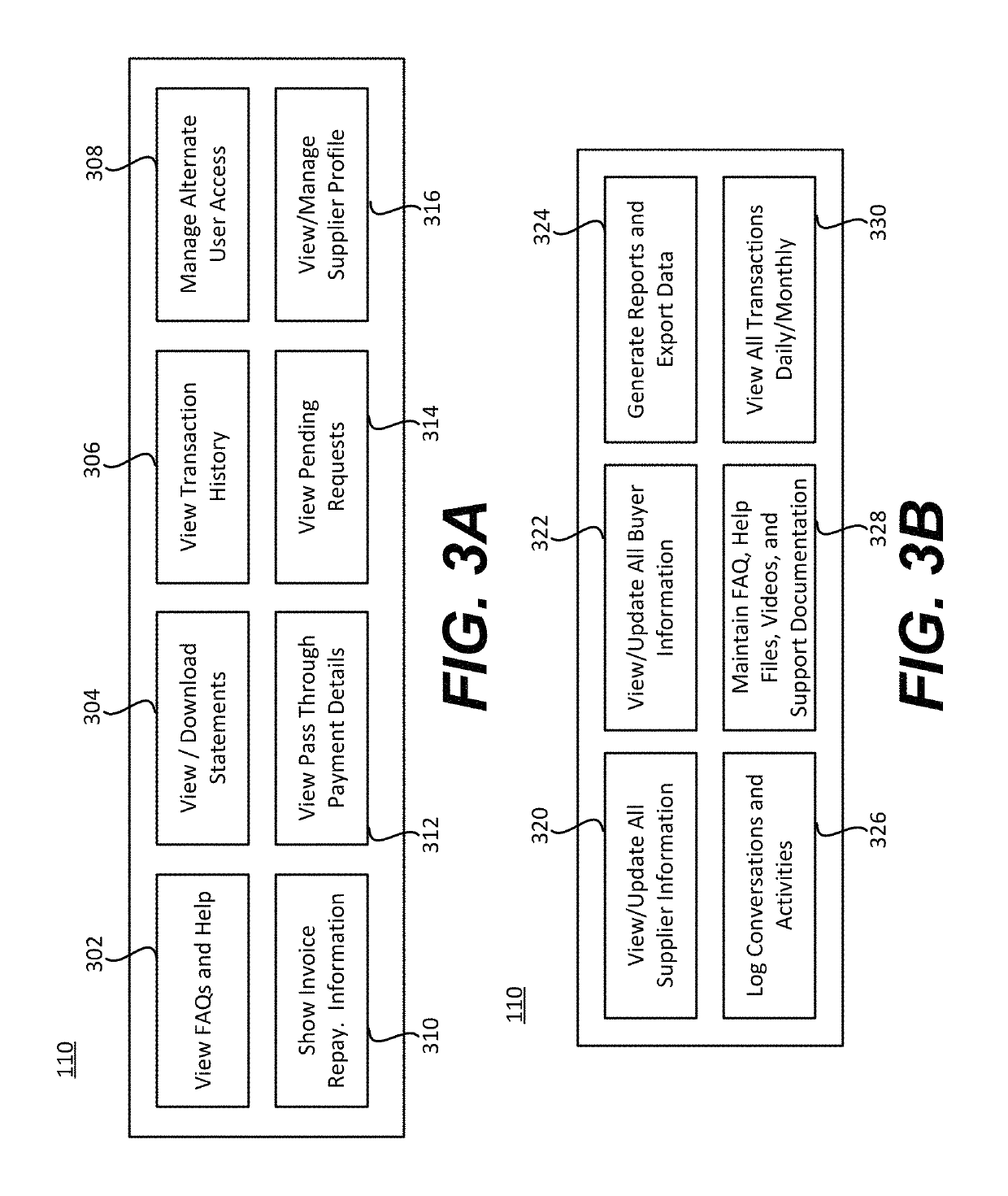
Systems and methods for improving invoice management using enhanced analytical insight
ActiveUS20190378183A1Easy to analyzeEasy to processFinanceVisual data miningInvoiceSupplier identifier
An improved invoice management product may include an invoice hub server and an invoice database, and may receive data including one or more invoices, transmit one or more invoice records to an invoice database, identify one or more invoice records for expedited processing, transmit a request to issue an advance payment to a supplier associated with one or more supplier identifiers associated with the one or more invoice records, and transmit a notice to a customer. An Invoice Hub server may receive data comprising one or more invoices, create one or more invoice records based on the one or more invoices, transmit the one or more invoice records to an invoice database, identify one or more invoice records for expedited processing, transmit a request to issue an advance payment to a supplier, and transmit a notice to a customer associated with the one or more invoice records.
Owner:CAPITAL ONE SERVICES
Systems and methods for improving invoice management using enhanced analytical insight
An improved invoice management product may include an invoice hub server and an invoice database, and may receive data including one or more invoices, transmit one or more invoice records to an invoice database, identify one or more invoice records for expedited processing, transmit a request to issue an advance payment to a supplier associated with one or more supplier identifiers associated with the one or more invoice records, and transmit a notice to a customer. An Invoice Hub server may receive data comprising one or more invoices, create one or more invoice records based on the one or more invoices, transmit the one or more invoice records to an invoice database, identify one or more invoice records for expedited processing, transmit a request to issue an advance payment to a supplier, and transmit a notice to a customer associated with the one or more invoice records.
Owner:CAPITAL ONE SERVICES
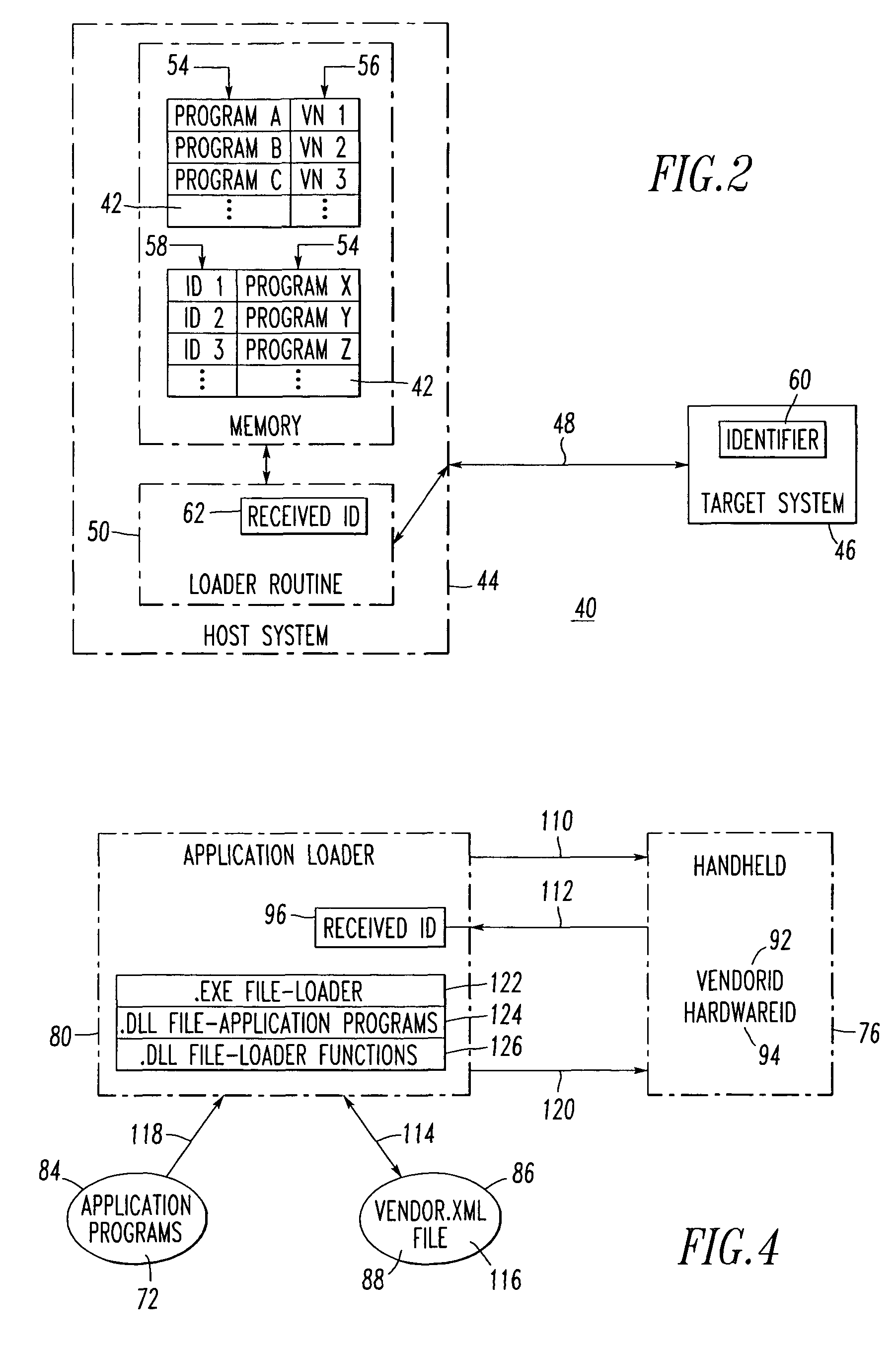
Method and system for selecting a program for download
A system selects an application program for download. The system includes a host system, such as a personal computer, having a disk sub-system storing a plurality of application programs. The disk sub-system includes a file storing a plurality of identifiers, with each of at least some of the identifiers being associated with one or more of the application programs. A target system, such as a wireless handheld electronic device, includes a hardware identifier and a vendor identifier. A communications channel connects the host system and the target system. An application loader routine executes at the host system, communicates with the target system through the communications channel, requests the hardware and vendor identifiers as a received identifier from the target system over the communication channel, and employs the identifiers and the received identifier to select one of the application programs for download from the host system to the target system.
Owner:MALIKIE INNOVATIONS LTD
Method and apparatus for sharing end user feedback
Owner:AT&T INTPROP I LP
Personally customizable credit card accounts
Owner:PAYPAL INC
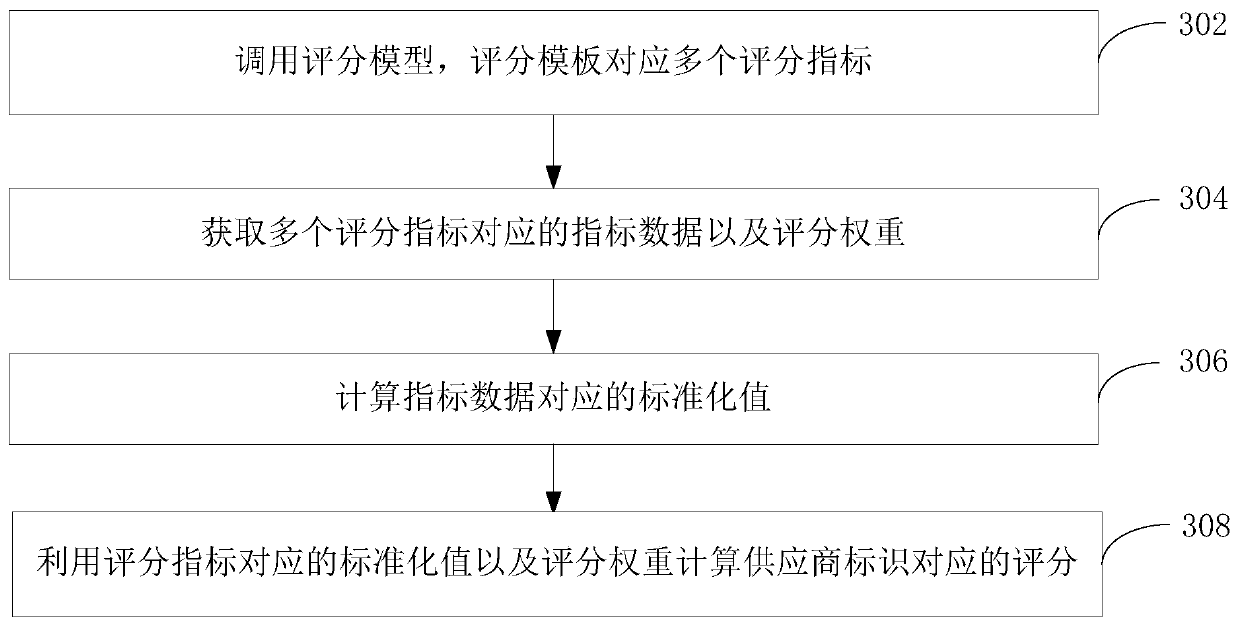
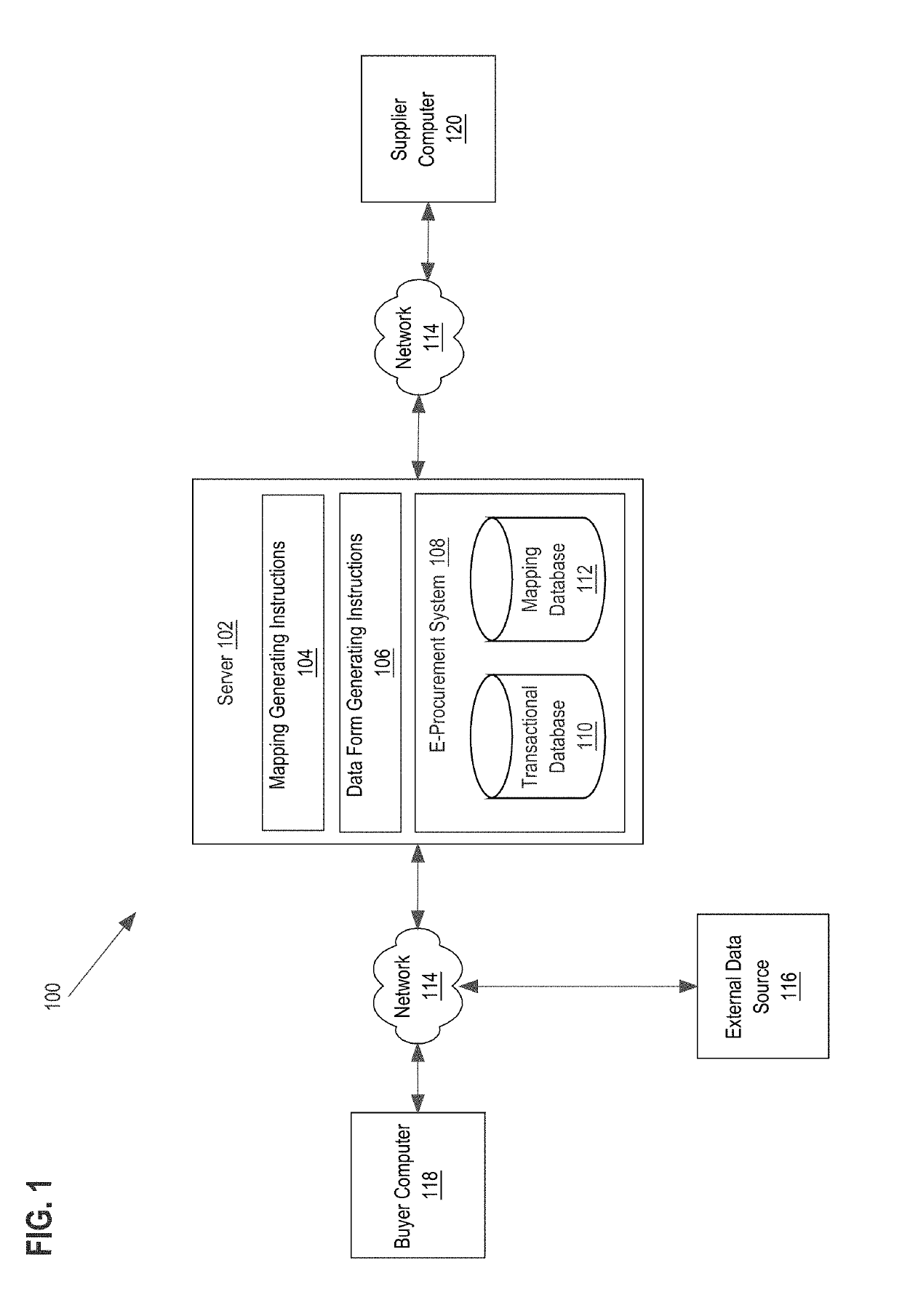
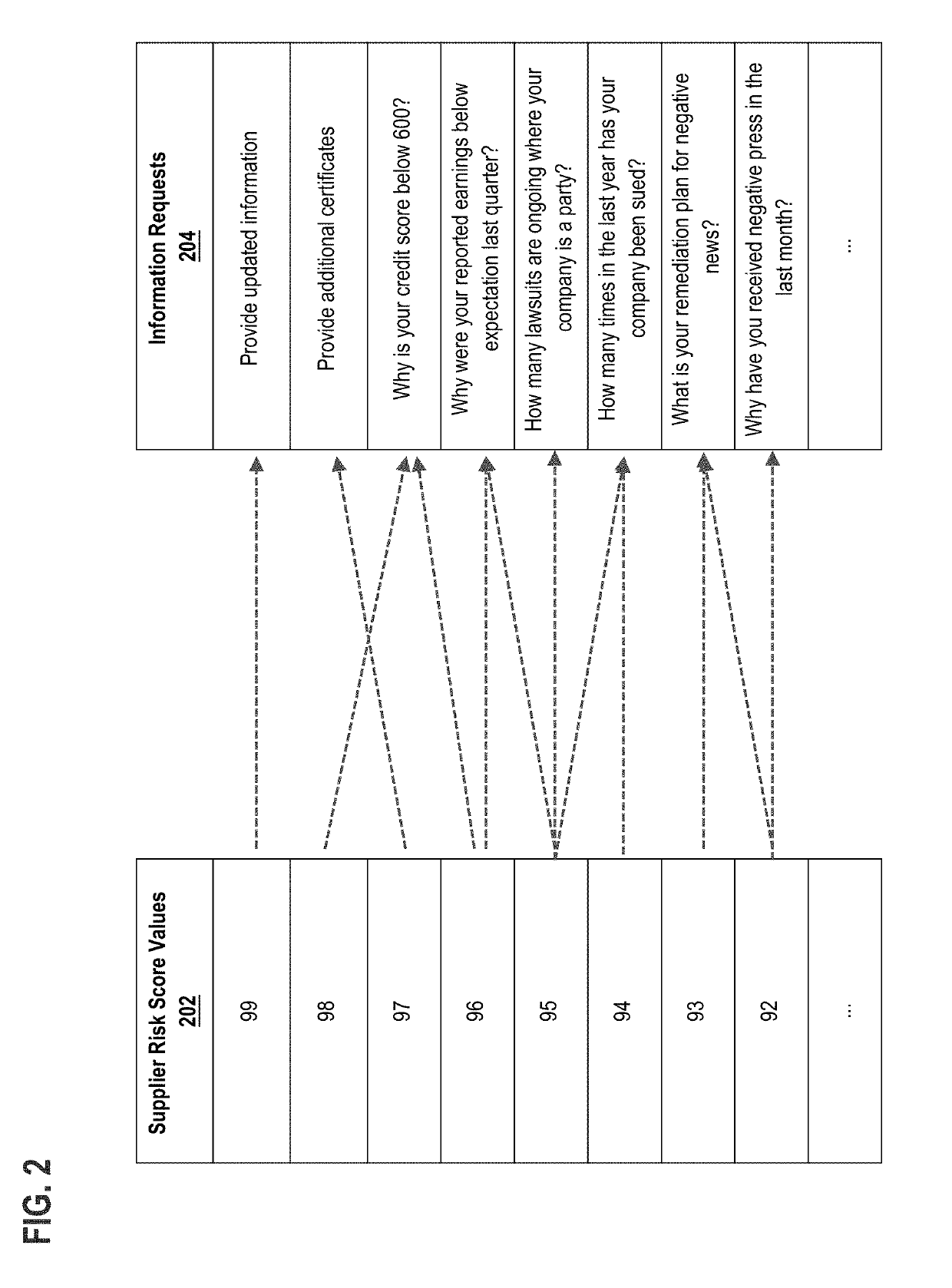
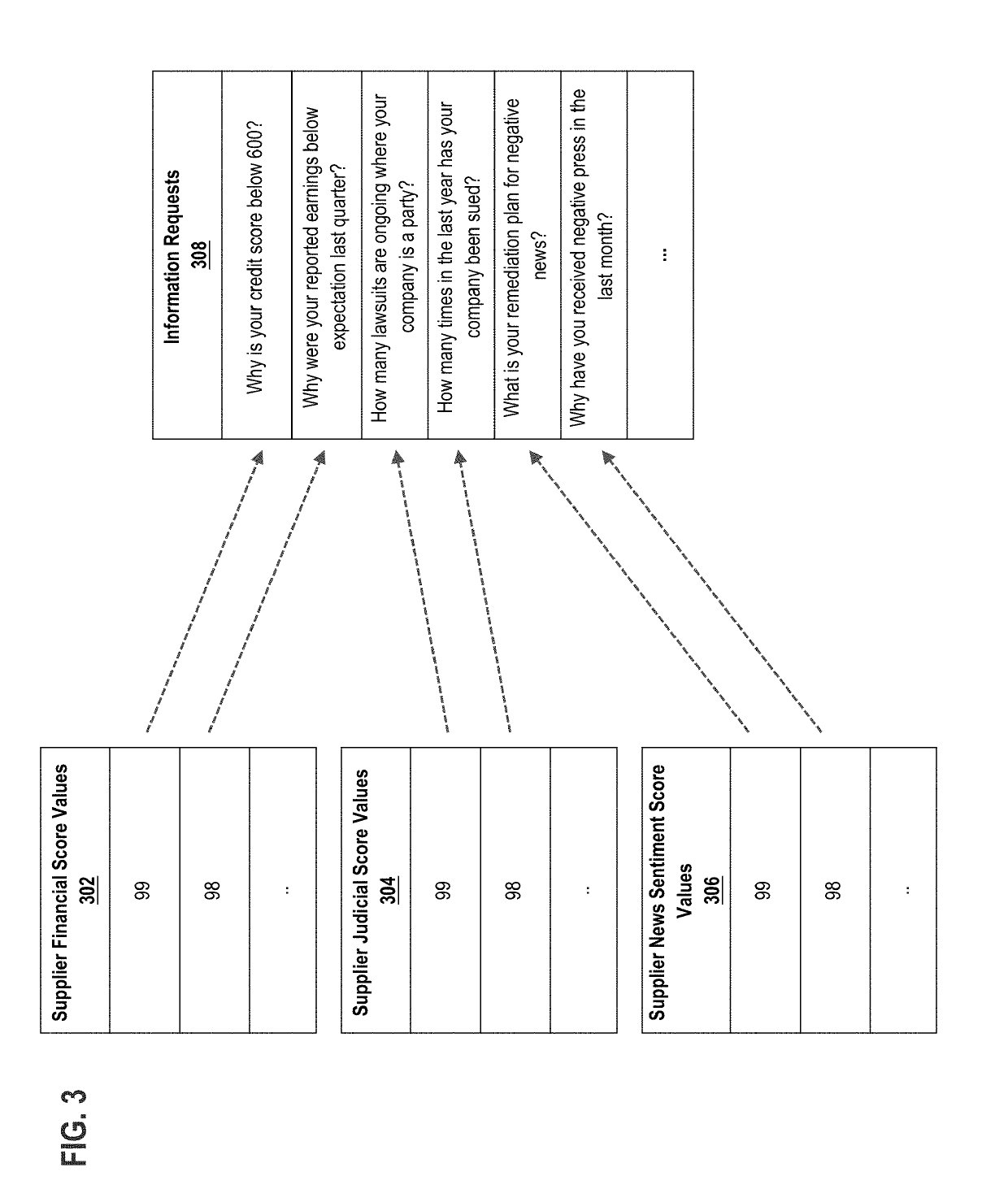
Automated information retrieval based on supplier risk
Techniques are provided for automated information retrieval based on supplier risk. In an embodiment, a selection of a supplier identifier value that identifies a supplier during a supplier onboarding process in an e-procurement system is received. A digital data repository of the e-procurement system is queried to seek a data record matching the selected supplier identifier value. In response to determining that the data repository has a record matching the selected supplier identifier value, a risk score value associated with the selected supplier identifier value is identified from a dataset of risk score values that is stored in the data repository. A unique mapping table is generated that maps each supplier risk score value of one or more supplier risk score values to one or more information request identifiers, the one or more supplier risk score values including the risk score value associated with the selected supplier identifier value. A custom digital data entry form is generated that comprises one or more information request fields that are mapped to the risk score value associated with the selected supplier identifier value. The custom data entry form is transmitted to a computer associated with the supplier corresponding to the selected supplier identifier value, the custom data form prompting the supplier to take action, respond, or contribute information back to the server computer.
Owner:COUPA SOFTWARE
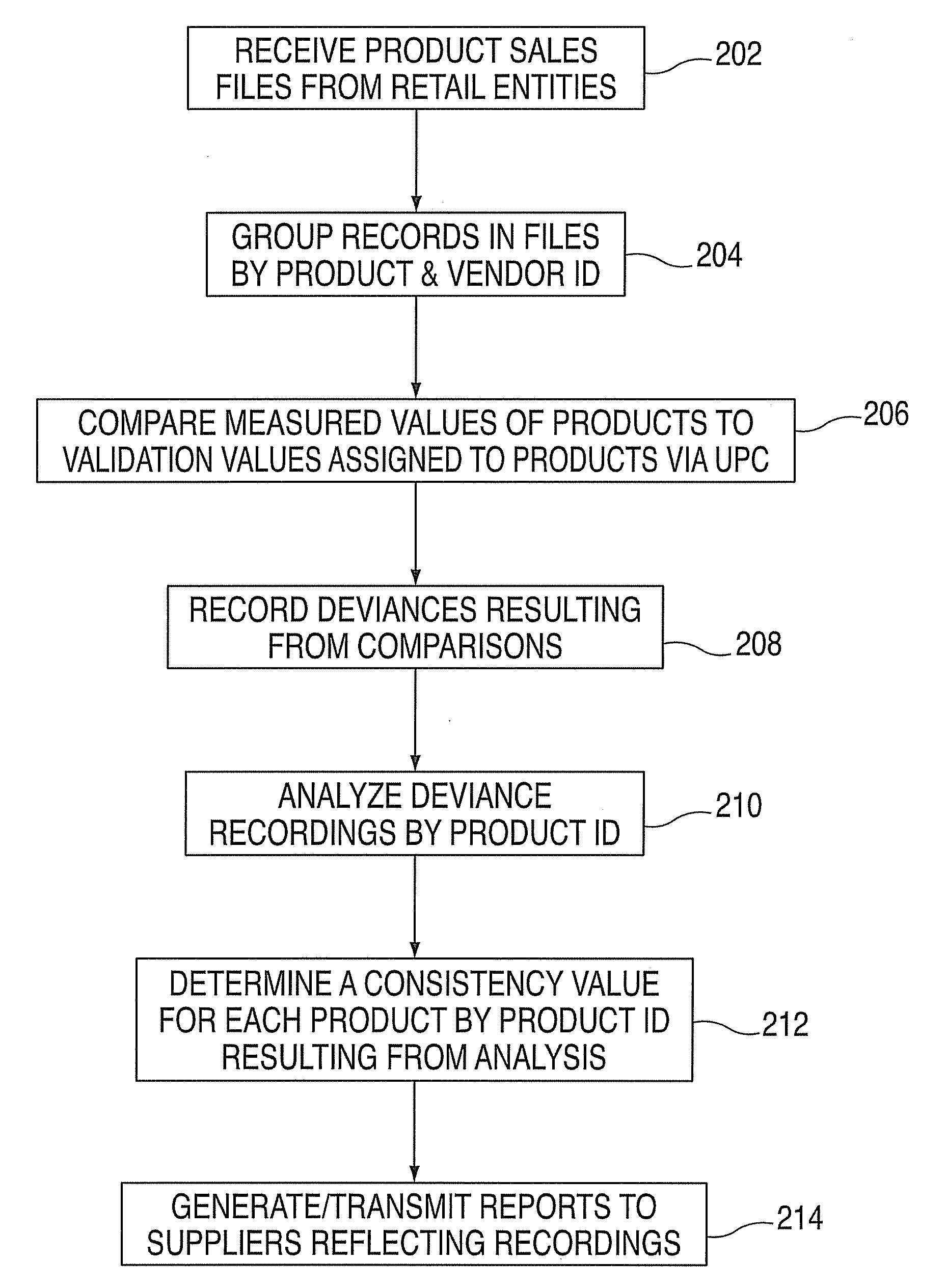
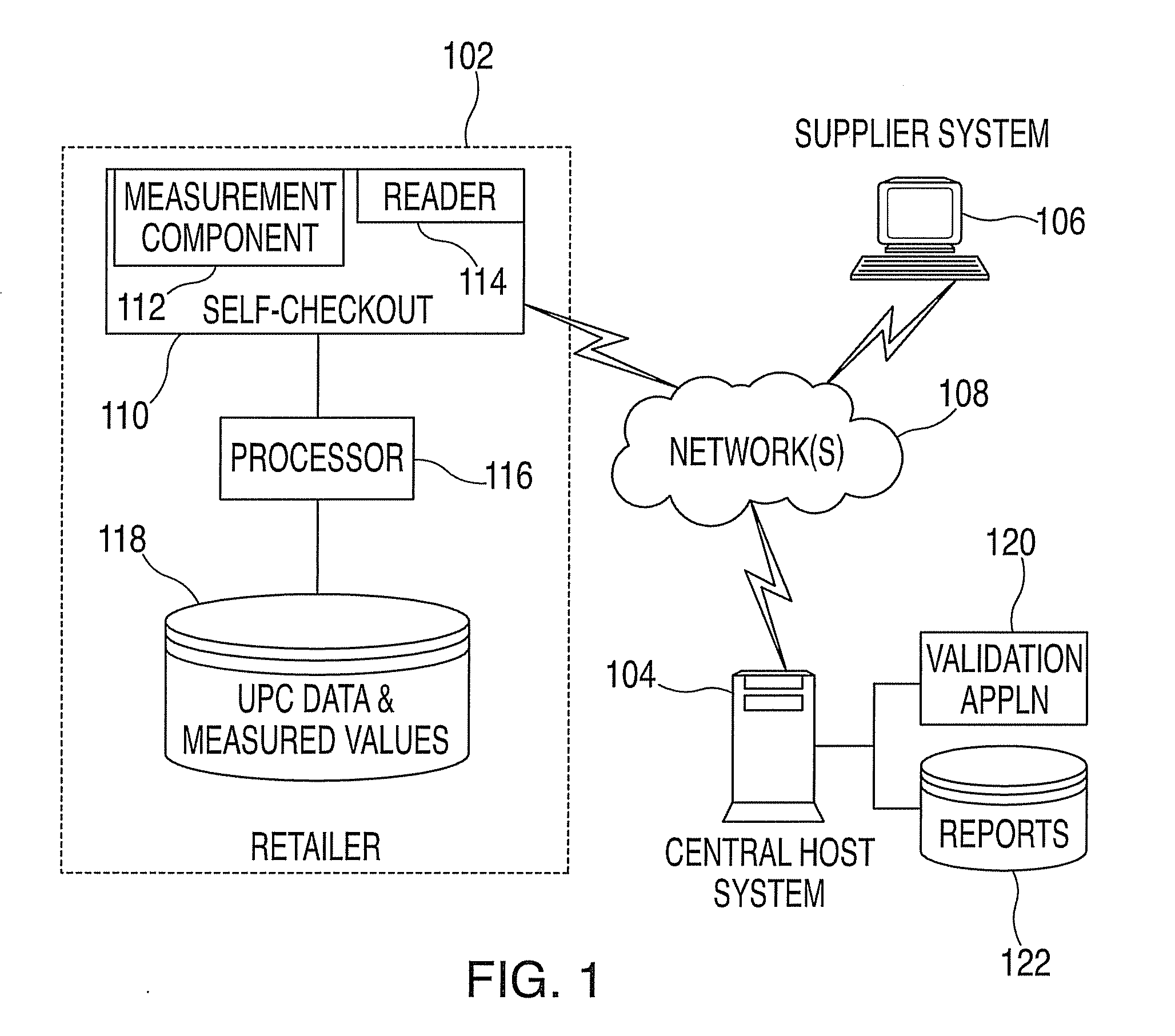
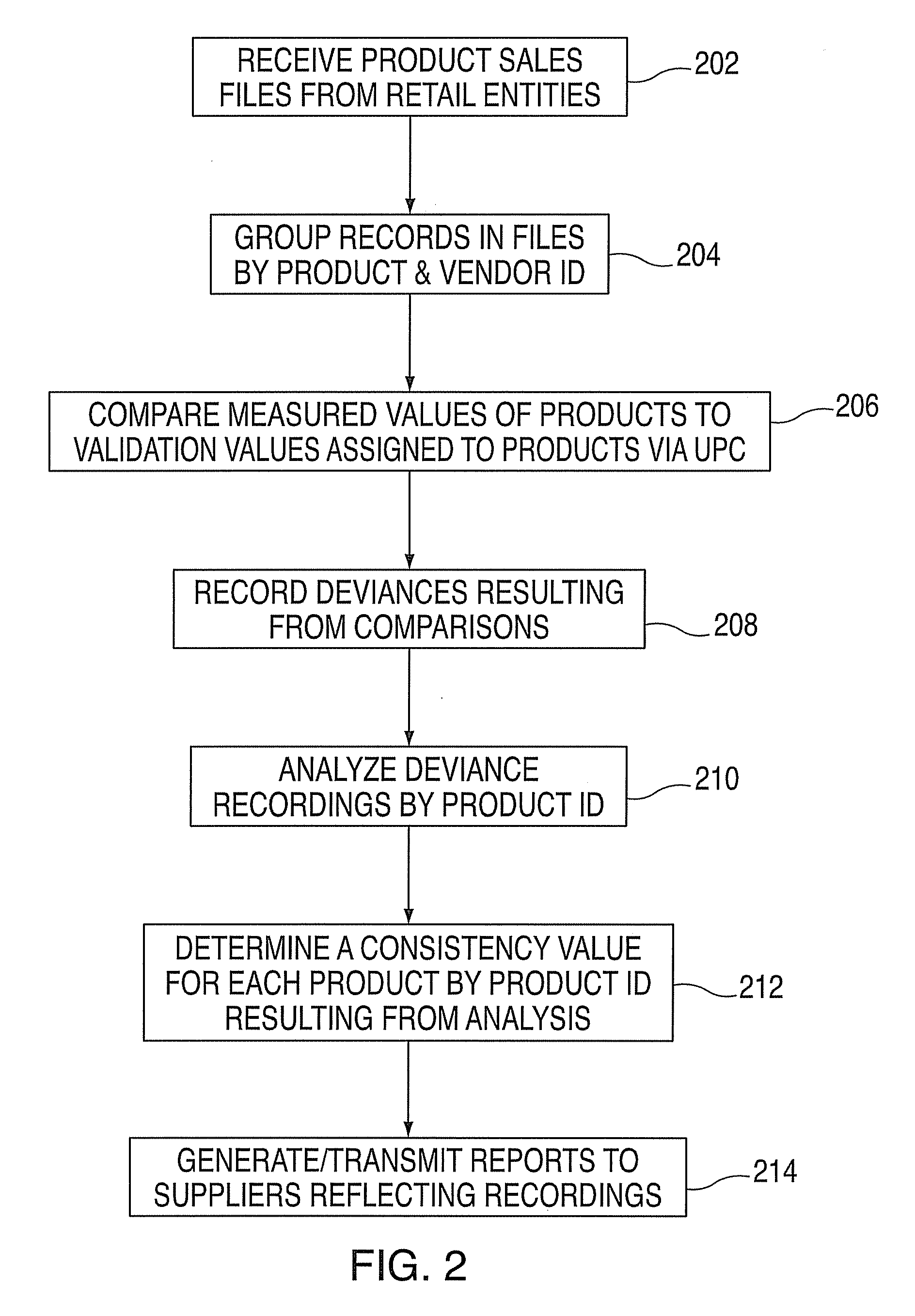
Method and system for product measurement validation
InactiveUS20080033782A1Special data processing applicationsMarket data gatheringUniversal Product CodeProduct Identifier
A method and system for product measurement validation is provided. The method includes receiving a product sales file from a number of retail entities, the product sales file including records of universal product code (UPC) data and measured values of products. The method also includes grouping the records in each of the product sales files by product and supplier identifiers and determining a consistency value for each product. The consistency value is determined by comparing the measured value of the product to a validation value assigned to the product via the UPC, the validation value representing a target measurement for the product. The consistency value is further determined by graphing measurement values and identifying any deviance resulting from the comparing and analyzing results of the graphing by product identifier and supplier identifier to determine whether the measured values of a product provided by a supplier are consistent with the validation value.
Owner:IBM CORP
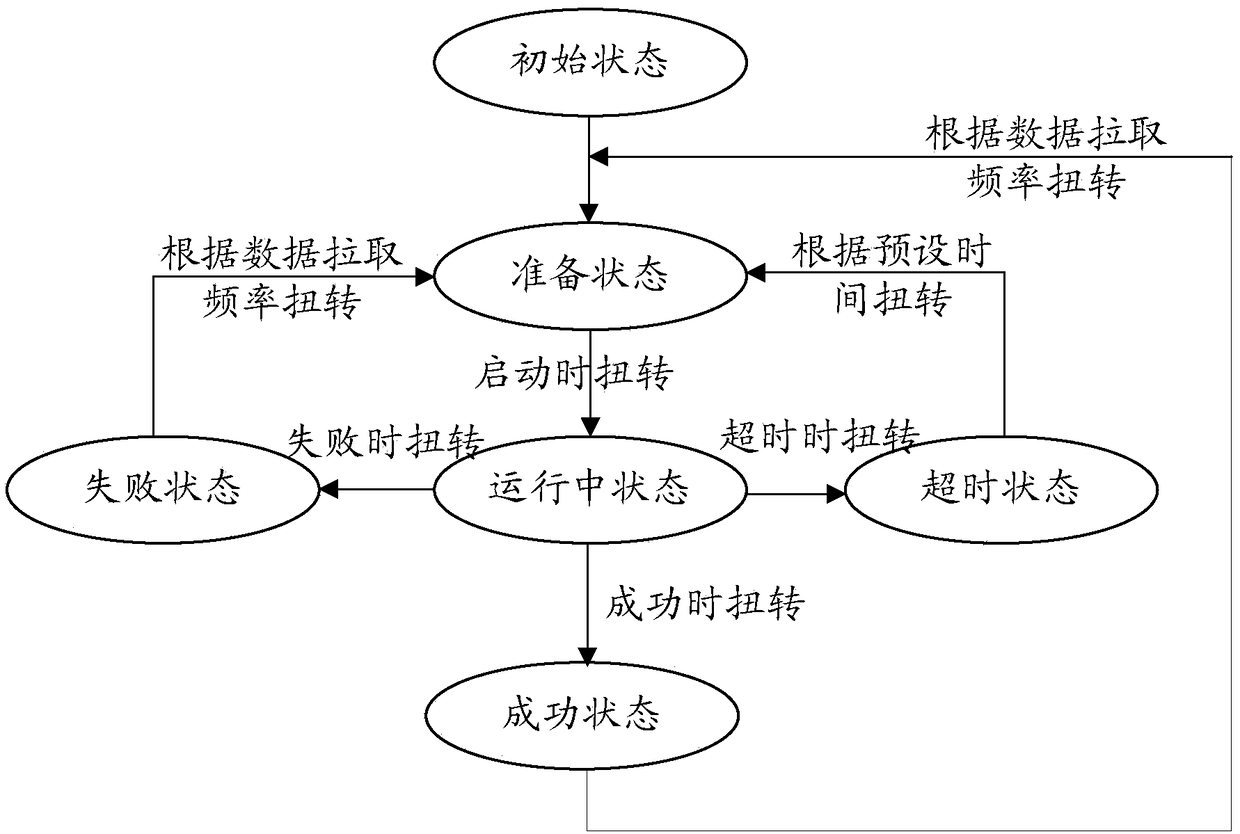
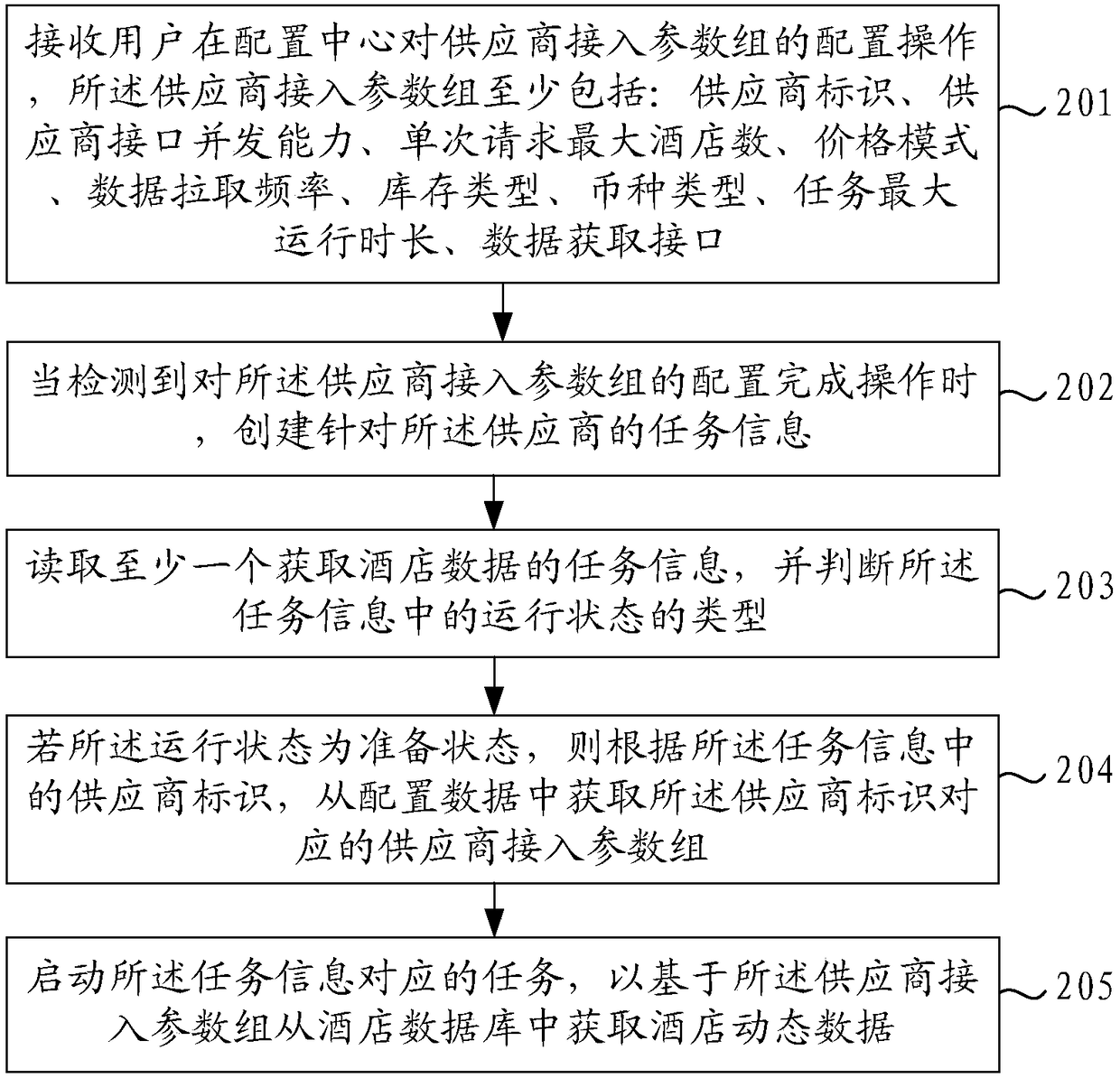
Hotel dynamic data obtaining method and apparatus, electronic device and readable storage medium
ActiveCN108549652ASimplify complexityImprove access efficiencyData processing applicationsSpecial data processing applicationsSupplier identifierDynamic data
The invention provides a hotel dynamic data obtaining method and apparatus, an electronic device and a readable storage medium. The method comprises the steps of reading at least one piece of task information for obtaining hotel data, and judging the type of a running state in the task information; if the running state is a preparation state, obtaining a supplier access parameter group corresponding to supplier identifiers from configuration data according to the supplier identifiers in the task information; and starting a task corresponding to the task information, and obtaining the hotel dynamic data from a hotel database based on the supplier access parameter group. The problems of complex process and relatively low efficiency of supplier access in the prior art are solved; the complexity of the access process can be simplified; and the access efficiency can be improved.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
Secure, differentiated reading of sensors and RFID tags
InactiveUS20120030071A1Expand accessDirect accessLogisticsCommerceProduct IdentifierSupplier identifier
Secure access to inventory data concerning a supplier's product located at a seller's premises is provided by tagging units of product with a supplier identifier and a product identifier. The identifiers may be embedded in RFID tags or EPC labels. A secure VPN tunnel is established between a supplier and a seller. The VPN tunnel is associated with a particular supplier identifier such that only inventory data associated with the supplier identifier that matches the supplier is transmitted on the VPN tunnel, and inventory data associated with supplier identifiers that do not match the supplier are filtered out. Hence, the seller can provide the supplier with access to inventory data without exposing sensitive information related to the seller and other suppliers.
Owner:RPX CLEARINGHOUSE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com