Mobile phone information security management method based on multiple authority modes
A technology for security management and mobile phone information, applied in telephone communication, electrical components, branch office equipment, etc., can solve problems such as malicious peeking, leakage, and misoperation of SMS messages, and achieve the effect of improving information security performance and protecting personal privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
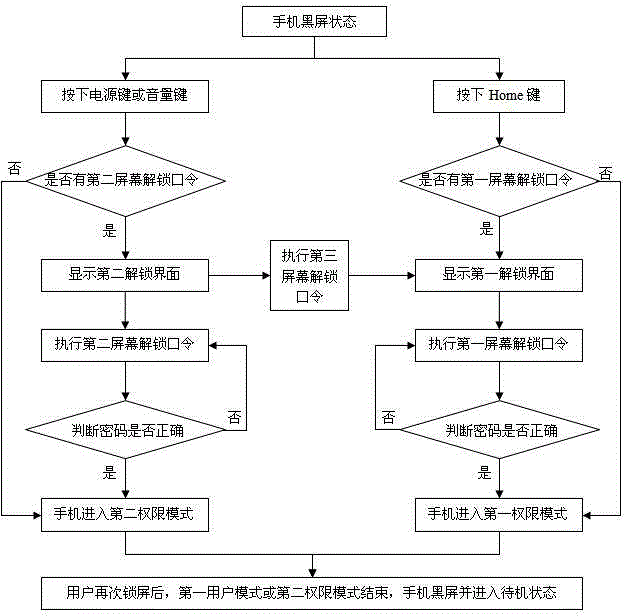
[0034] Such as figure 1 As shown, a mobile phone information security management method based on a multi-authority mode, the authority mode includes a first user mode and a second authority mode, and the second authority mode includes a visitor mode, an elderly mode, a child mode and a power saving mode A combination of one or more of them, the method includes the steps of multi-authority mode security management:
[0035] S1: When the mobile phone is in a black screen state, press the power button or the volume button, light up and activate the mobile phone screen, and the mobile phone automatically loads the preset second permission mode. If the user has not set the second screen unlock password, then perform step S4; if the user If the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com