Information security management and control method, system and device and readable storage medium
A technology of information security and security control, applied in the field of systems, devices, computer-readable storage media, and information security control methods, can solve problems such as theft of sensitive information, human instability, and enterprise hazards, and achieve information security and difficulty in internal intrusion high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
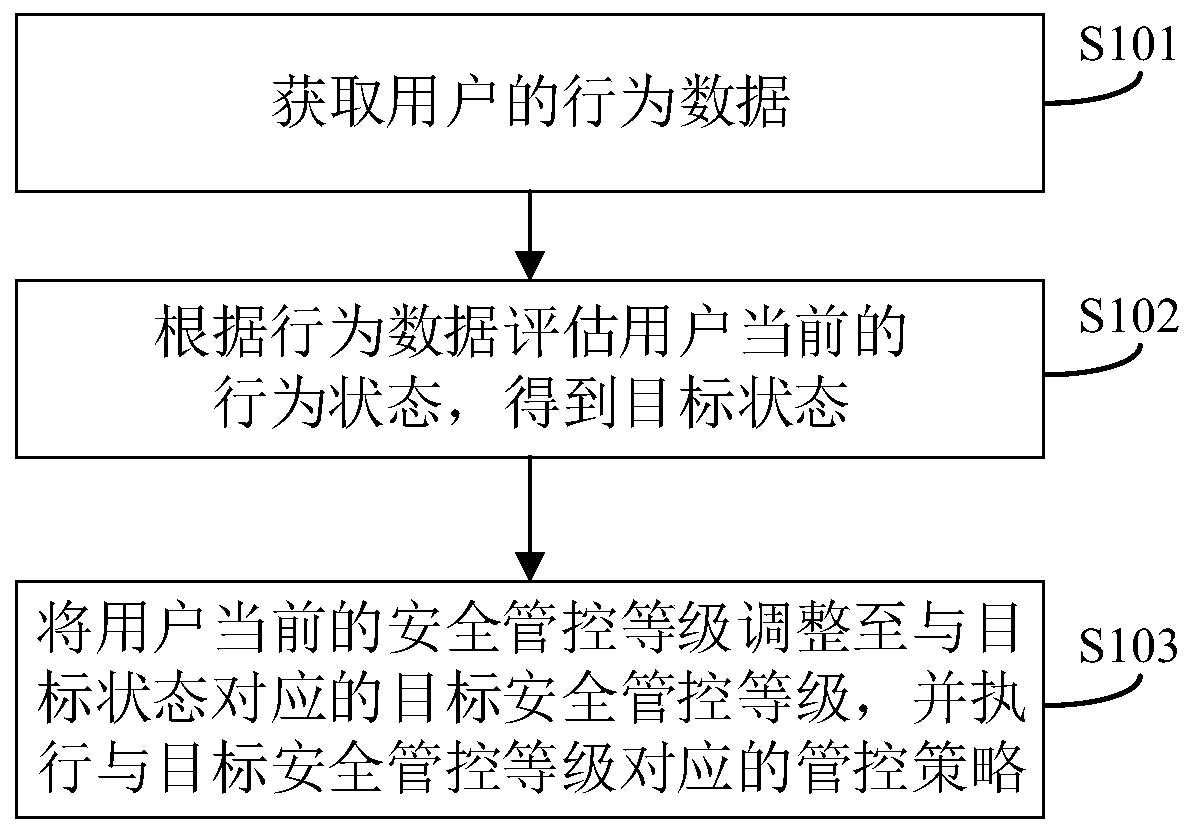
[0063] See figure 1 , figure 1 A flowchart of an information security management and control method provided in the embodiment of the present application, which includes the following steps:
[0064] S101: Obtain the behavior data of the user;
[0065] The purpose of this step is to obtain various behavior data performed by internal employees in the internal network of the enterprise that can represent some behavior data performed by users in accordance with their own will, such as modification operations on local device security items, various operations performed on sensitive data, The location information of the login file system, the time spent browsing the recruitment website, the number of local attachments uploaded, etc. Since the types of data given above and other data with the same meaning are all direct feedback of actions taken by users in accordance with their own will, this application will use behavioral data as the data of the same or similar data mentioned a...
Embodiment 2
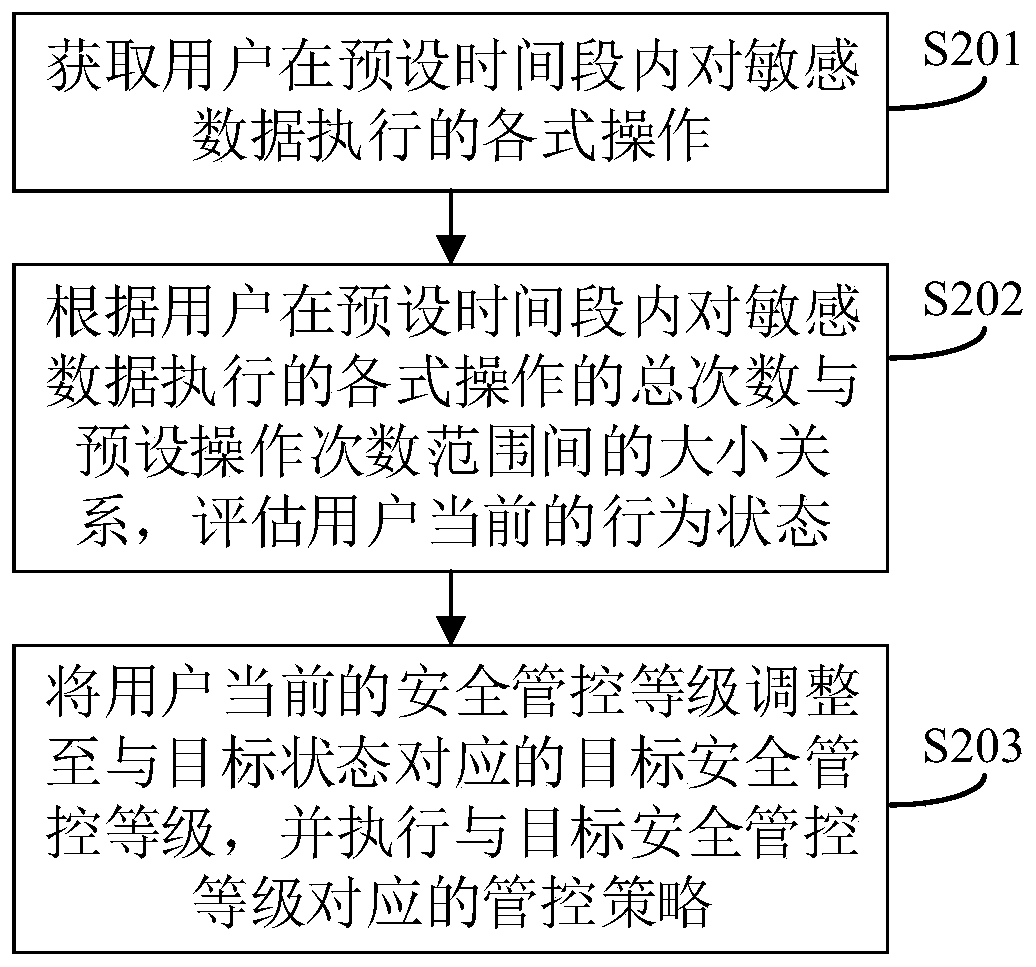
[0082] See figure 2 , figure 2 A flow chart of a method for implementing information security management and control according to the number of operations on sensitive data provided by the embodiment of the present application, on the basis of the first embodiment, this embodiment aims to perform operations on sensitive data according to the user's operations on the sensitive data within a preset time period. The behavior data of the dimension of times is used to give a specific information security management and control method, including the following steps:
[0083] S201: Acquire various operations performed by a user on sensitive data within a preset time period;
[0084] Since sensitive data leakage operations are often performed during non-working hours, and it is often inconvenient to perform operations during working hours due to the presence of surrounding colleagues, the preset time period may preferably be the off-get off work and after-get off work hours of the ...
Embodiment 3
[0096] See Figure 4 , Figure 4 A flowchart of a method for implementing information security management and control according to the number of login location changes provided in the embodiment of the present application, on the basis of the first embodiment, this embodiment is based on the behavior data of the dimension of the location information of the user logging in to the file system. To give an information security management and control method, including the following steps:
[0097] S301: Determine a common login location according to the location information of the user logging in to the file system each time;
[0098] The common login location is a location where the number of logins exceeds the preset number of logins when the user logs in to the file system.
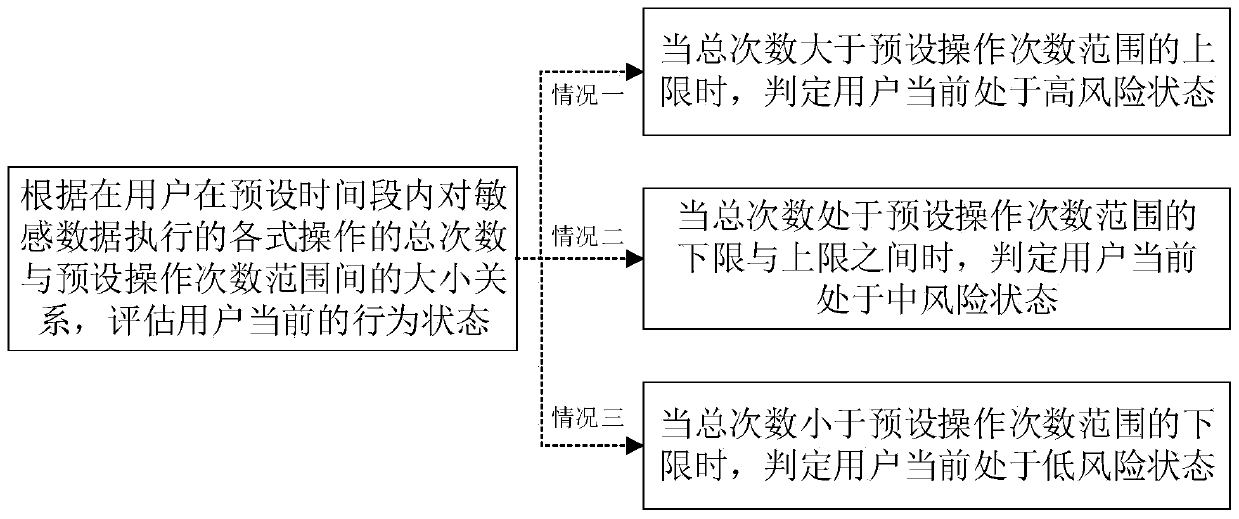
[0099] S302: Evaluate the current behavior status of the user according to the magnitude relationship between the number of new landing positions different from the common landing positions and the number...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com