IMA processor system information security management method
A technology of security management and system information, which is applied in the field of information security management of IMA processor system, and can solve the problems of information security storage and access, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
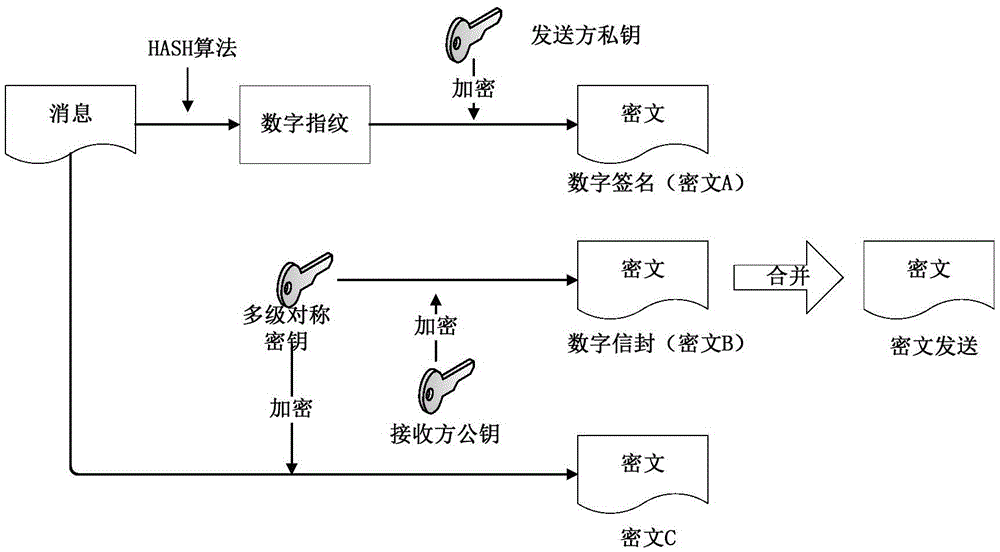
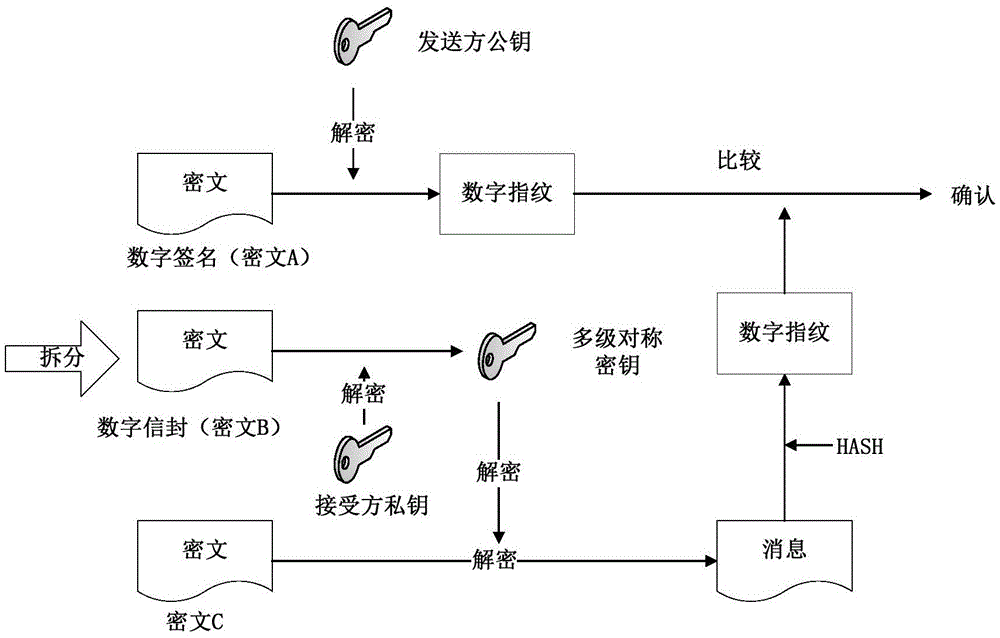
[0032] The present invention proposes an information security management method for an IMA processor system, which divides the information of the IMA processor system into four security levels of top secret, confidential, secret, and common for management. It can be stored in the processor system, but the top secret and confidential information are prohibited from being stored in the processor system in total, and only temporarily loaded through the data loader; top secret information, confidential information, and secret information are identified and encrypted according to the level; system applications are classified according to the corresponding security level To manage and control information access rights, high security level users can access low security level information, and low security level users are prohibited from accessing high security level information. The secret information stored in the IMA processor system is automatically encrypted by hardware, and the el...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com