Active defense method based on cloud platform
An active defense and cloud platform technology, applied in the field of information security, can solve problems such as user infection, inability to analyze new samples in real time, large consumption of client resources, etc., to achieve effective protection, avoid confrontation analysis, and protect security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] Some technical terms in the present invention are defined below:
[0022] Cloud: the server side.
[0023] Characteristic value of a program file: a value that can uniquely identify a file, such as MD5 value, SHA1 Secure Hash Algorithm (Secure Hash Algorithm, SHA1 for short) value, and key instructions of the program.
[0024] Commands in program files: Refers to program instructions.
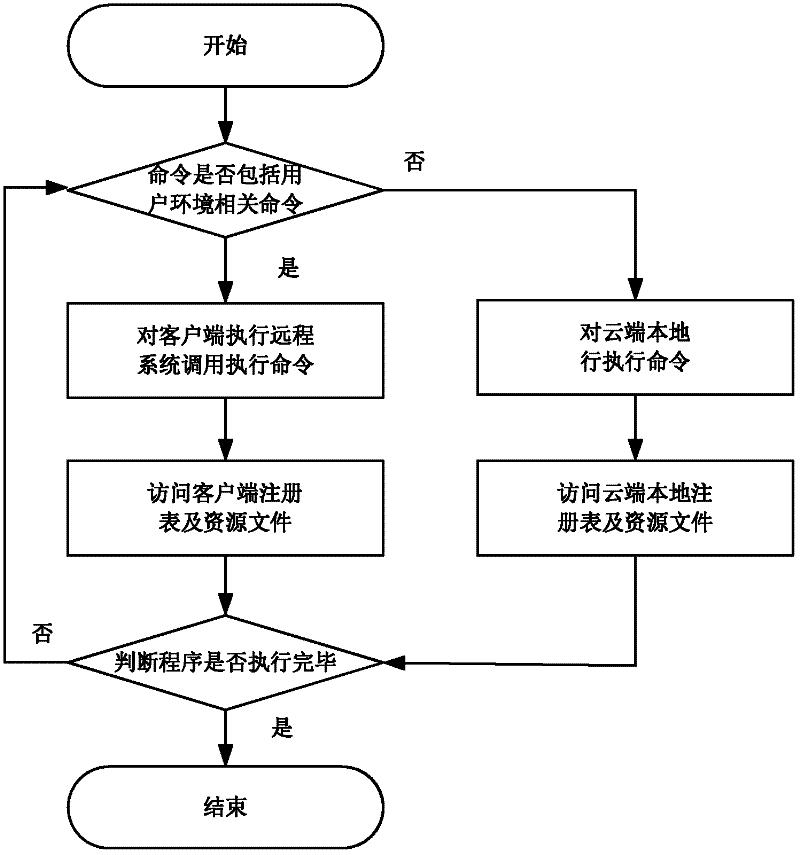
[0025] User environment-related commands: Refers to specific program instructions, such as instructions for processing user input, instructions for reading system information, and instructions for reading user data.
[0026] Cloud analysis: Execute the program on the server side and analyze it to identify the security of the program.
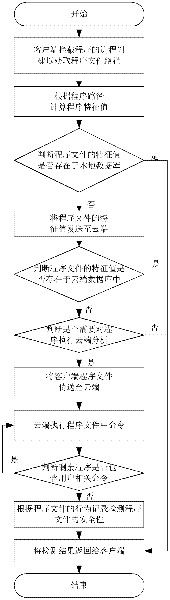
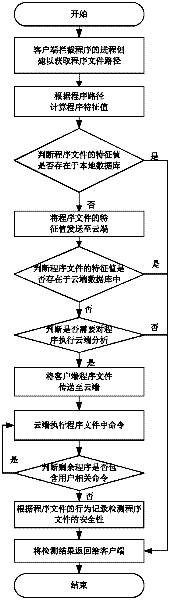
[0027] Such as figure 1 As shown, the active defense method based on cloud computing of the present invention comprises the following steps:
[0028] (1) The client intercepts process creation to obtain the program file path of the process;
[0029] (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com