Anti-monitoring method and system for mobile terminal
A technology of mobile terminal and monitoring method, which is applied in the direction of electrical components, wireless communication, security devices, etc., can solve the problems of illegal recording and dissemination of call content, achieve the effect of protecting personal privacy and safety, and improving satisfaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
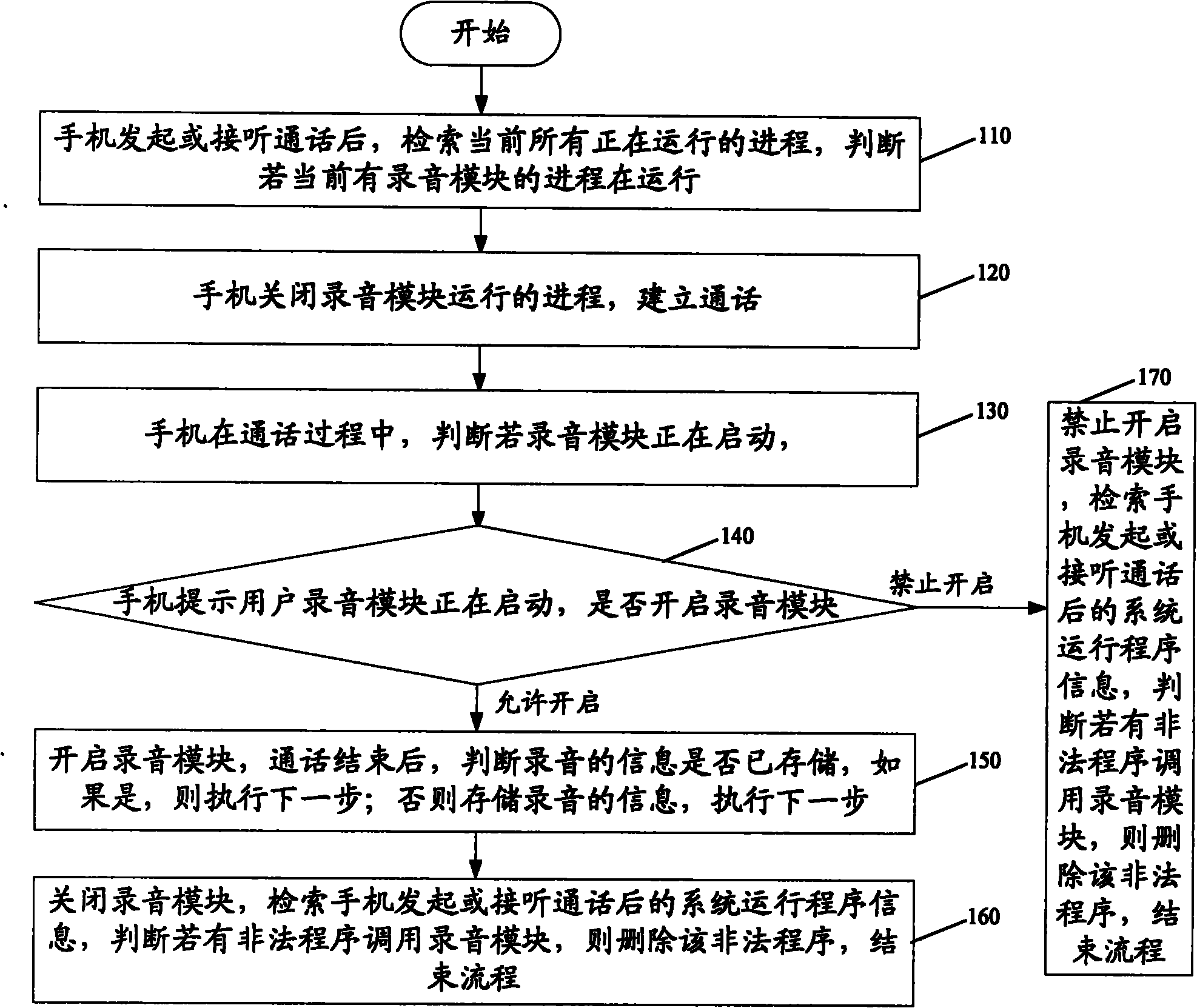
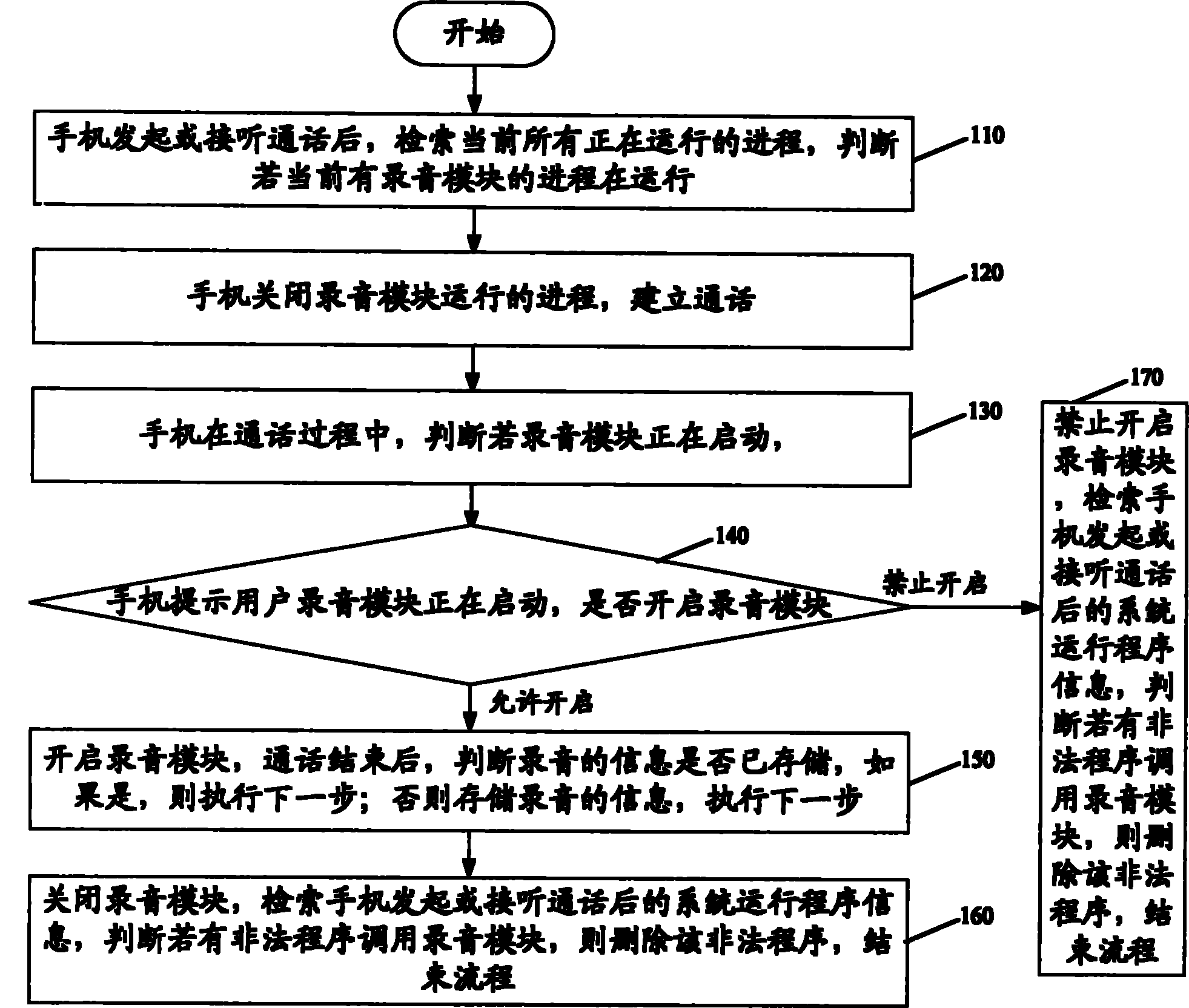
[0017] The current illegal monitoring program mainly calls the recording module of the mobile phone through a Trojan horse program, or the Trojan horse program itself has a recording function, resides in the user's mobile terminal, records voice clips privately during the user's call, and then passes the multimedia message Or Internet upload to listeners. Therefore, if during a mobile phone call, whether the recording module is running or started by monitoring, it is possible to effectively prevent the Trojan horse program from monitoring the call.
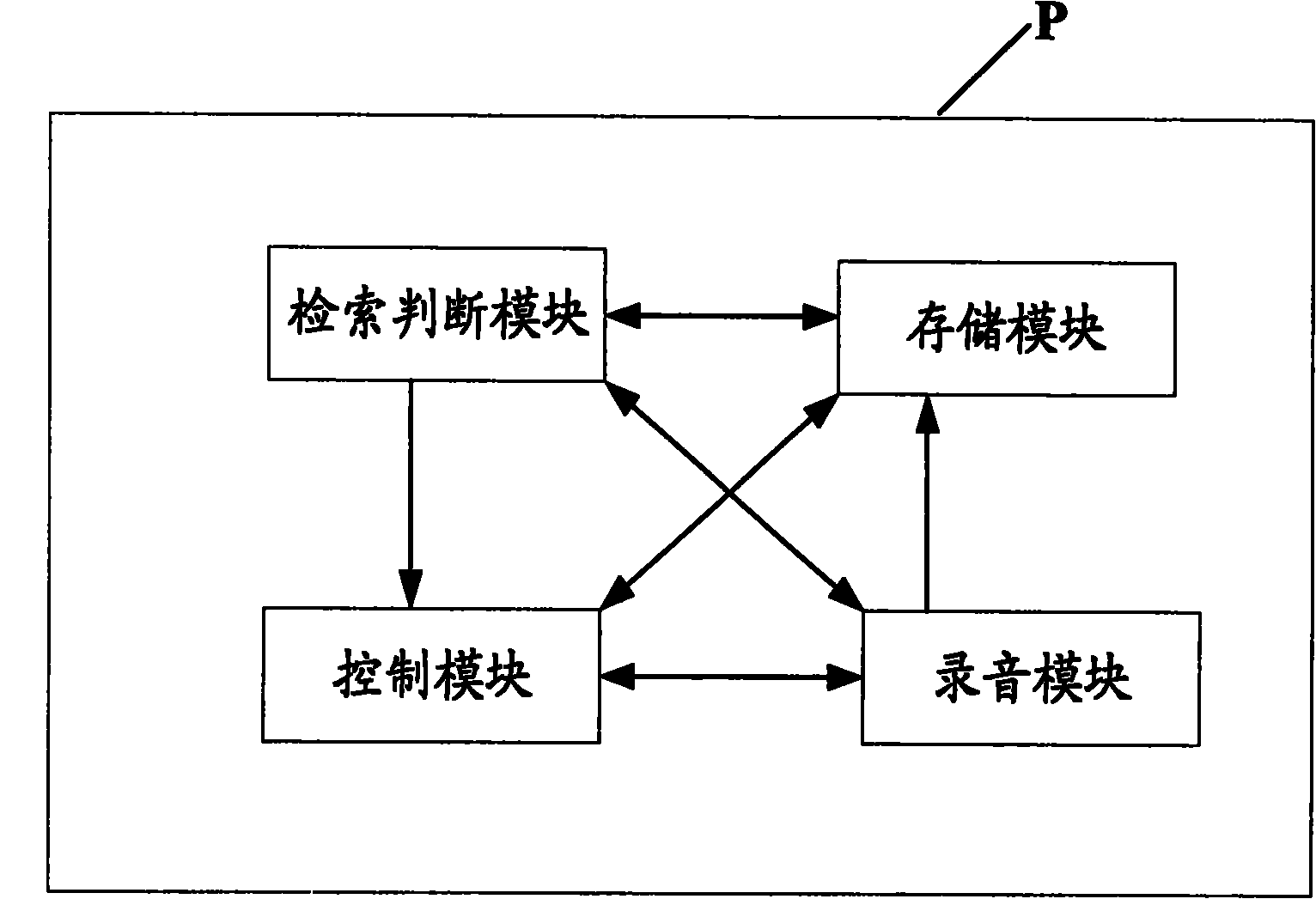
[0018] And the recording module described in the present invention, both can be the recording software that this mobile terminal carries, also can be other software with recording function installed later. As for whether there is a recording function, it can be judged in various ways, such as a pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com