System and method for realizing security storage and access control of data
A technology of data access control and data security storage, which is applied in the field of storage security in information technology, can solve the problems of mixed storage security of different sensitive levels of data, achieve the effect of small impact, improve security, and increase security access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
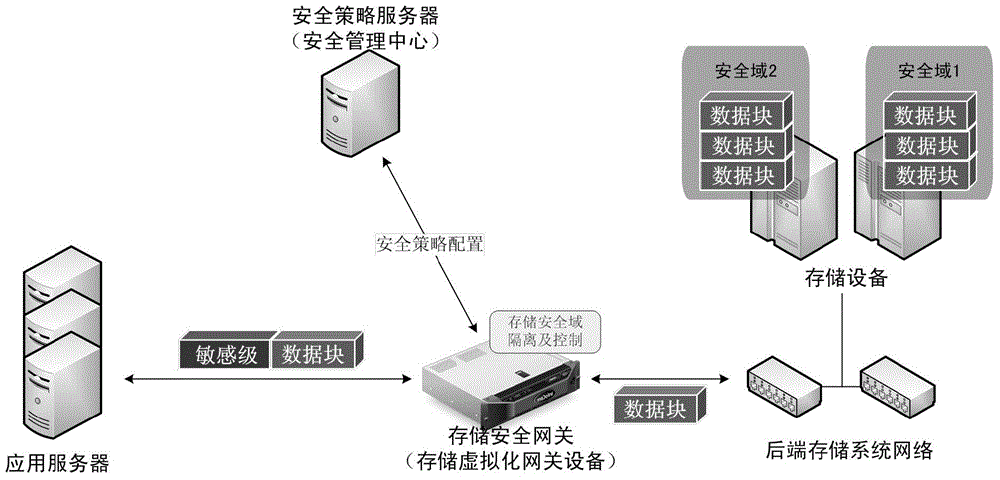
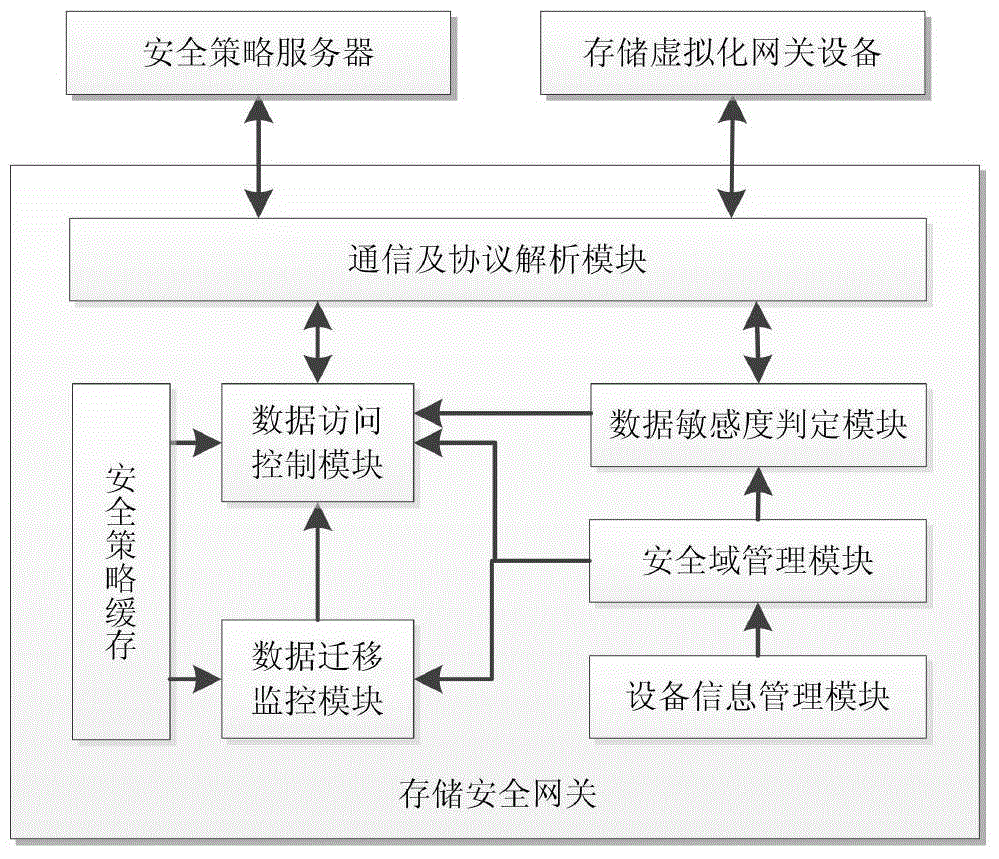
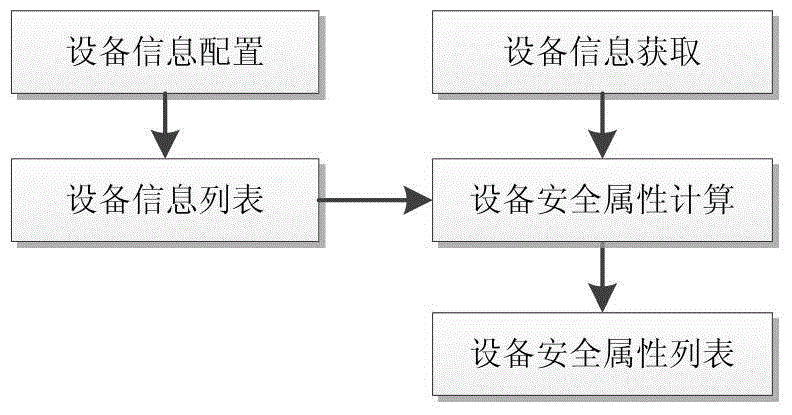
[0065] The present invention mainly adds logical functional components of a storage security gateway between the front-end application server generating data requests and the back-end storage system to realize data security domain division, isolation and access control. The storage security gateway and the storage virtualization gateway can work together, and use the existing virtualization technology to realize the storage of data on the actual physical medium according to the security domain. When a data access request arrives at the storage virtualization gateway, the storage virtualization gateway can invoke the function of the storage security gateway to implement data security domain isolation and access control. Since all data requests to access the back-end storage system will be processed by the storage...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com