A spatial network query method capable of protecting privacy
A technology of spatial network and query method, applied in the field of privacy protection of spatial network query, to achieve the effect of realizing safe and efficient query processing service
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] The experimental settings are as follows: two servers are used as cloud servers, and the configuration is Intel(R) Xeon(R) CPUL5638@2.00GHz(Dual Processor) and 40.0GB RAM; one PC is used as the data owner, and the configuration is Intel( R) Core(TM) i3-7100 CPU@3.90GHz and 8.0GB RAM. All three hosts run Windows 7 operating system. The two datasets use the real spatial network dataset of urban roads in Austin, USA, containing 526 and 1,148 nodes and 647 and 1,223 edges, respectively. At the same time, we uniformly select 10% nodes from the dataset as the target set. For each dataset, we execute 10 sets of queries using different query nodes and calculate the average query response time.
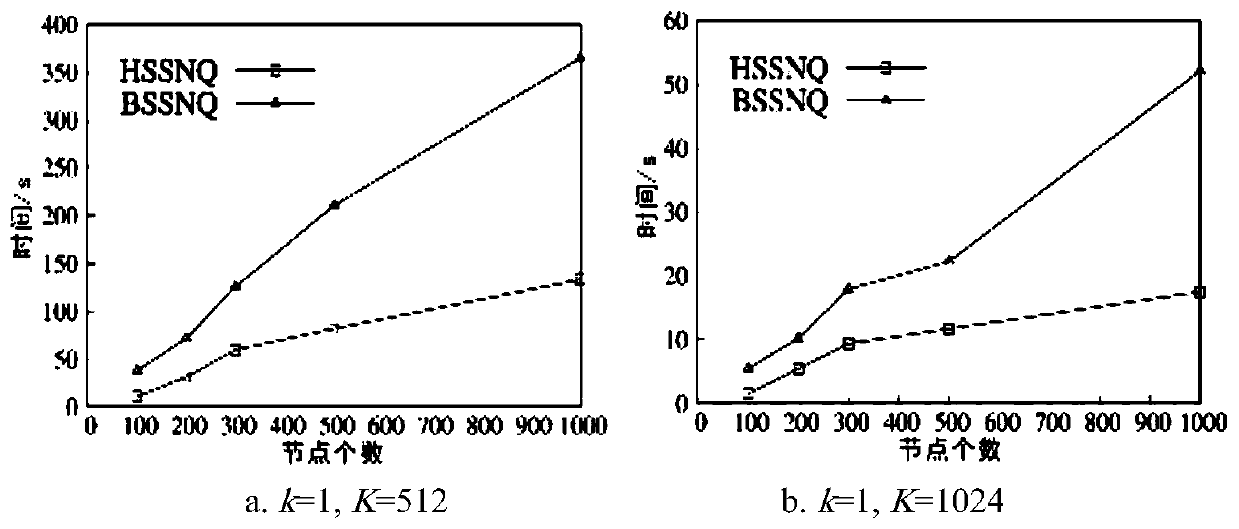
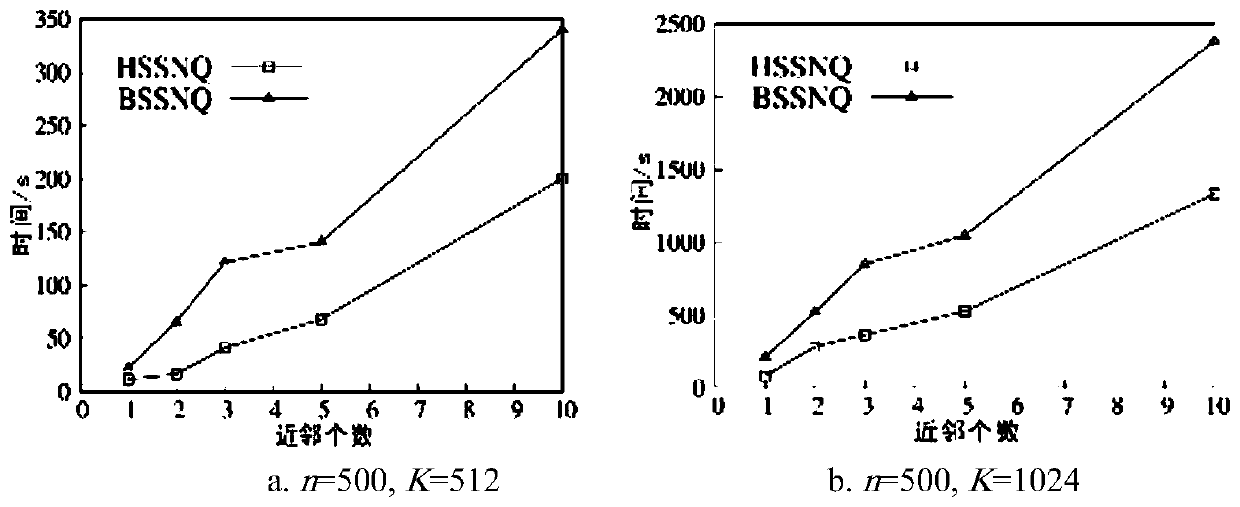
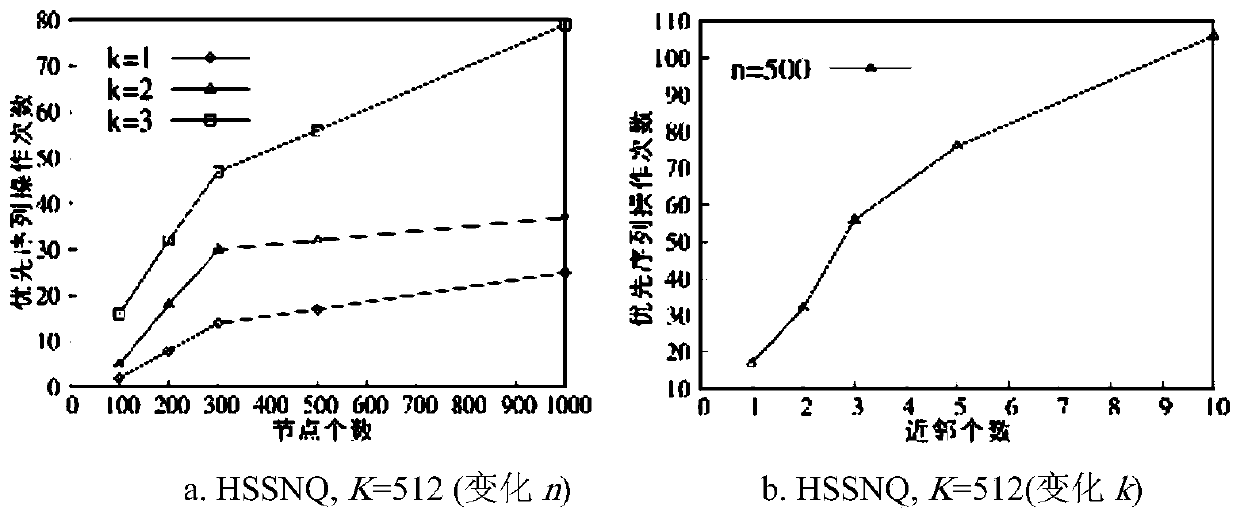
[0047] Next, we comprehensively evaluate the algorithm from three aspects: query response time, number of priority sequence operations, and precomputation time and space costs. The experimental results are as follows:
[0048] When investigating "query response time", the present inv...
Embodiment 2
[0052] The present invention can be applied in the scene of outsourcing space network query. The data owner uses the encrypted space network data construction proposed by the present invention to encrypt the space network, and the authenticated user encrypts the query request q using the privacy protection method generated by the space query request proposed by the present invention, and sends the encrypted query request to Go to the cloud service provider (assuming that the number of neighbors requested is k=2), and initiate an HSSNQ query request. Figure 6 Describes an HSSNQ query instance (k=2), there are 8 objects in this instance, among them, the query point E pk (q), target point E pk (d 1 ),E pk (d 2 ),E pk (d 3 ) and others are nodes on the network, and the value on the edge represents the encrypted edge weight.
[0053] After receiving the query request, the cloud service provider first adds the encrypted query to the preferred sequence, and then uses E pk (d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com