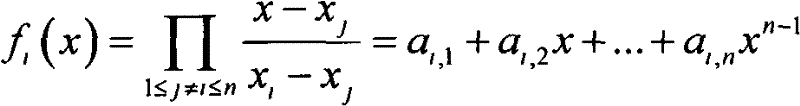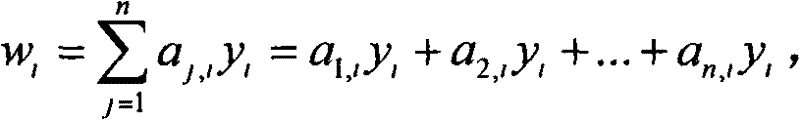Construction method for authorizing listener anonymity set in broadcasting program
A construction method and receiver technology, applied in the direction of broadcasting system control, electrical components, transmission systems, etc., can solve the problems of not being able to obtain any information, not including authorized receiver identity list information, and not intuitively displaying the identity of authorized receivers, etc. , to achieve the effect of solving the privacy protection problem
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] Glossary:
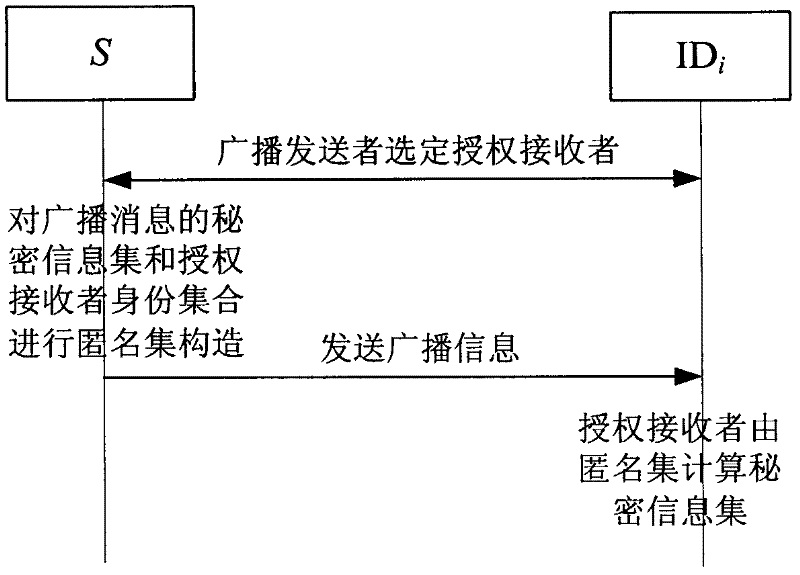
[0018] S: broadcast sender
[0019] n: the number of authorized recipients
[0020] i: integer
[0021] ID i : the identity information of the i-th user, where i=1, 2, ..., n
[0022] L: set of identity information of authorized receivers, L={ID 1 , ID 2 ,...,ID n}
[0023] v i : Authorization recipient ID i The secret information of , where i = 1, 2, ..., n
[0024] V: the set of secret information of each authorized recipient, V={v 1 , v 2 ,...,v n}
[0025] H(x): Hash function, x is an argument
[0026] x i : Interpolation abscissa, that is, the i-th interpolation abscissa of the Lagrangian interpolation function, satisfying x i =H(ID i )
[0027] x: independent variable
[0028] the y i : Interpolation ordinate, that is, the interpolation ordinate corresponding to the i-th interpolation abscissa of the Lagrangian interpolation function
[0029] f i (x): Lagrangian interpolation basis function
[0030] j: integer
[0031] a j,i : ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com