Method for training privacy protection model and privacy protection method and device
A privacy protection and model technology, applied in the field of training privacy protection models, can solve problems such as no defense methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] The solution provided by the present invention will be described below in conjunction with the accompanying drawings.
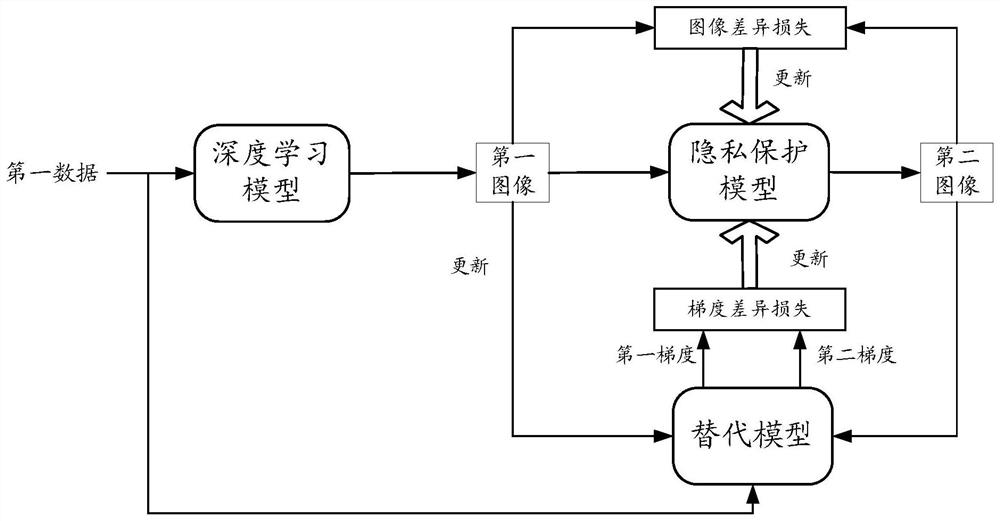
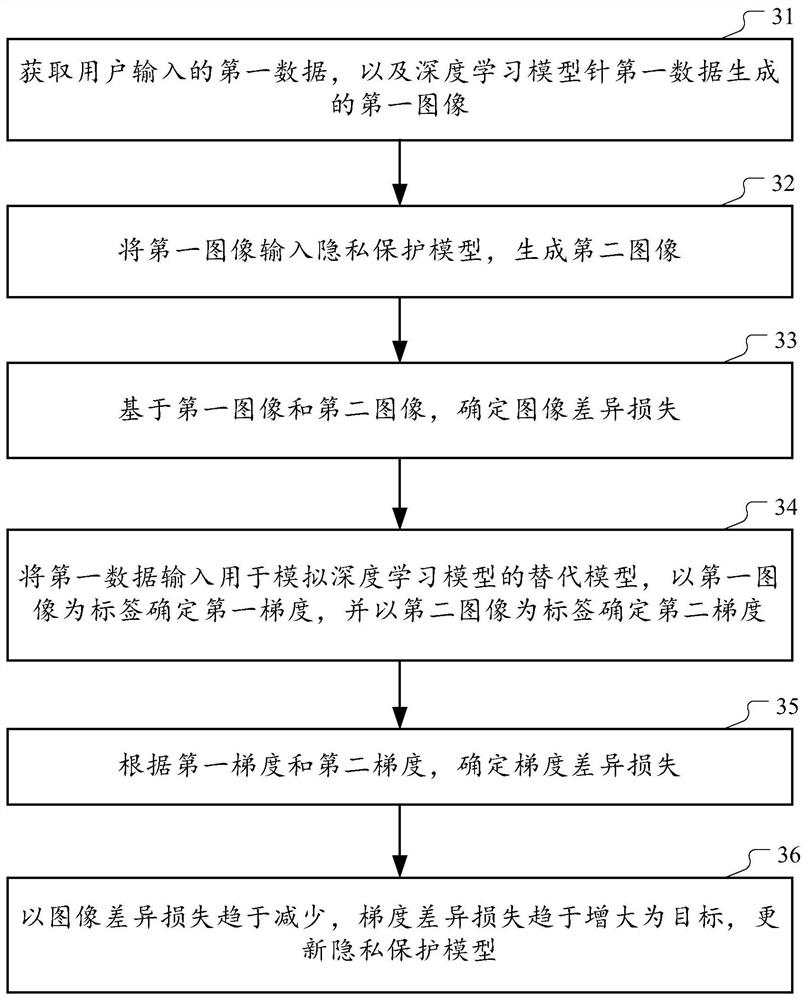
[0075] As mentioned earlier, by accessing the artificial intelligence system multiple times to obtain a large amount of "input-output" data, and then using the input-output pair for model training to obtain a substitute model, it is possible to obtain a substitute model without knowing the structure and weight of the target model. Obtain an alternative model with similar performance to the target model to achieve the purpose of cracking the model.
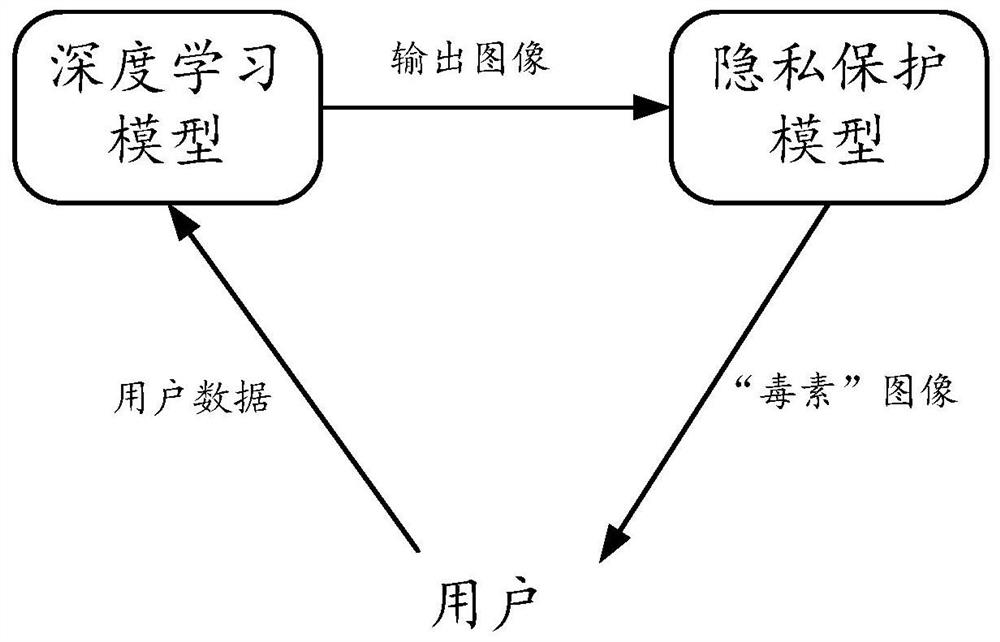
[0076] Considering the above problems, in the embodiments of this specification, a method for training a privacy-preserving model, a privacy-preserving method and a device thereof are proposed. The method and the device thereof can protect the privacy of the deep learning model whose output result is an image. The basic idea is to superimpose "toxin" on the output image of the original model by training a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com