Multi-user management method of electronic equipment
A technology of electronic equipment and management methods, applied in branch equipment, telephone communication, electrical components, etc., can solve problems such as obvious forms of protection, information stored on mobile phones cannot be viewed by them, and achieve the effect of protecting privacy information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
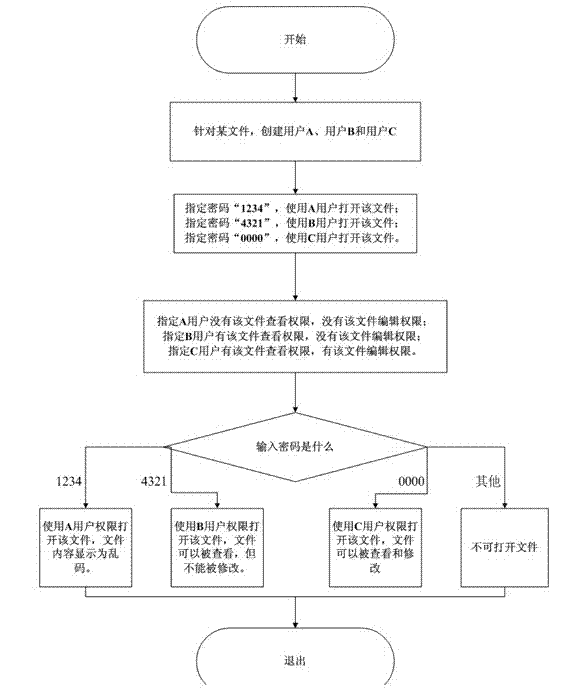
[0011] Such as figure 1 As shown, the multi-user management method for electronic equipment provided by this embodiment performs authentication according to the characters input by the user, including steps S1 for creation and management and S2 for operation execution;
[0012] The steps of S1 for creating and managing include:
[0013] S111 creates permission groups for applications or files; for example, three permission groups are created for the file FILE, which are: GROUP11, GROUP12 and GROUP13;
[0014] S112 sets the functional items included in the authority grouping; those skilled in the art can understand that the application programs and files of the mobile phone include a plurality of functional items, such as the operation of the file FILE including the following functions: viewing function FUNC11, editing function FUNC12, new function FUNC13 There are altogether 4 function items including the delete function FUNC14. This step sets the authority group GROUP11...
Embodiment 2
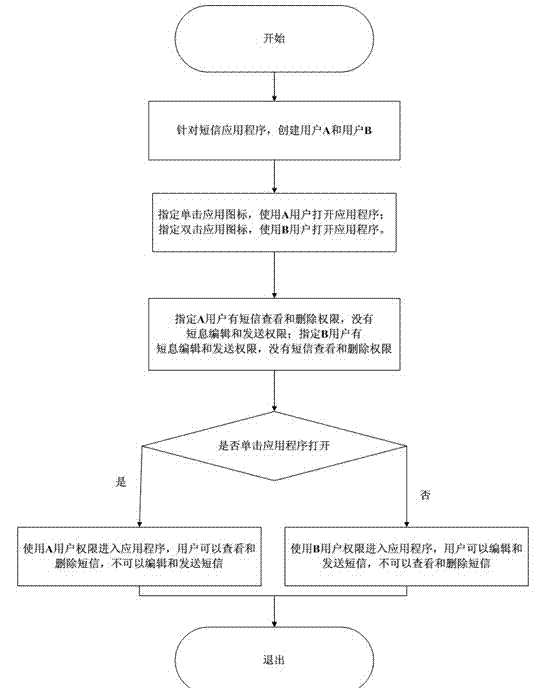
[0034] Such as figure 2 As shown, the multi-user management method for electronic equipment provided in this embodiment performs authentication according to the operation mode, including steps S1 for creation and management and S2 for operation execution;
[0035] The steps of S1 for creating and managing include:
[0036] S211 Create permission groups for applications or files; for example, create three permission groups for SMS application APP, which are: GROUP21 and GROUP22;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com