Method for realizing classification management of use right of mobile terminal user
A technology of mobile terminal and implementation method, which is applied in the direction of electronic digital data processing, digital data processing parts, instruments, etc., can solve the problem that wireless mobile business functions cannot be effectively protected, and the scope of protection of personal information is narrow, only readable or not. Read and other issues, to achieve the effect of simple software development, easy programming implementation, protection of private information and business secrets
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The present invention will be further described in detail below with reference to the embodiments of the drawings.
[0015] Implementation example 1
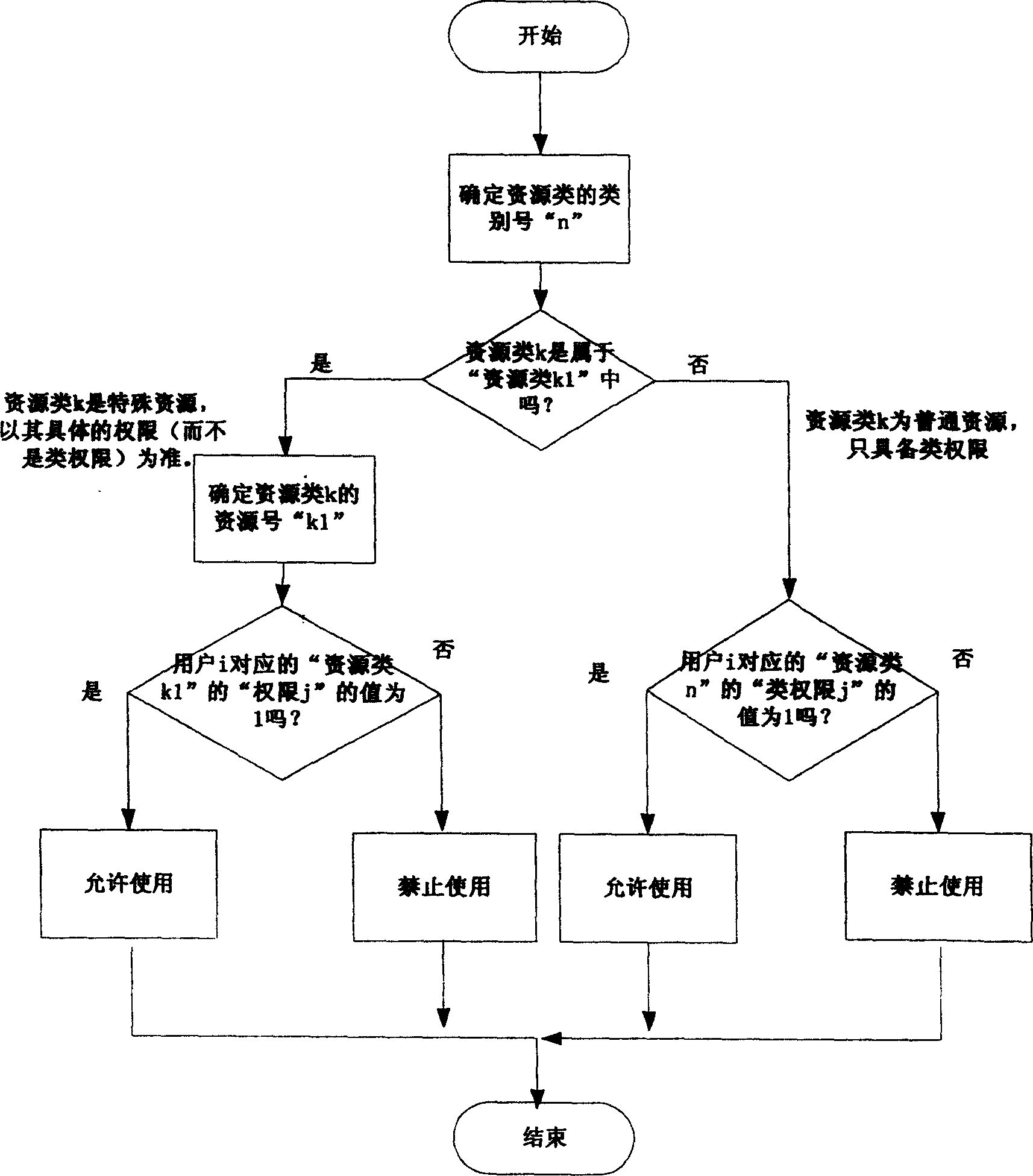
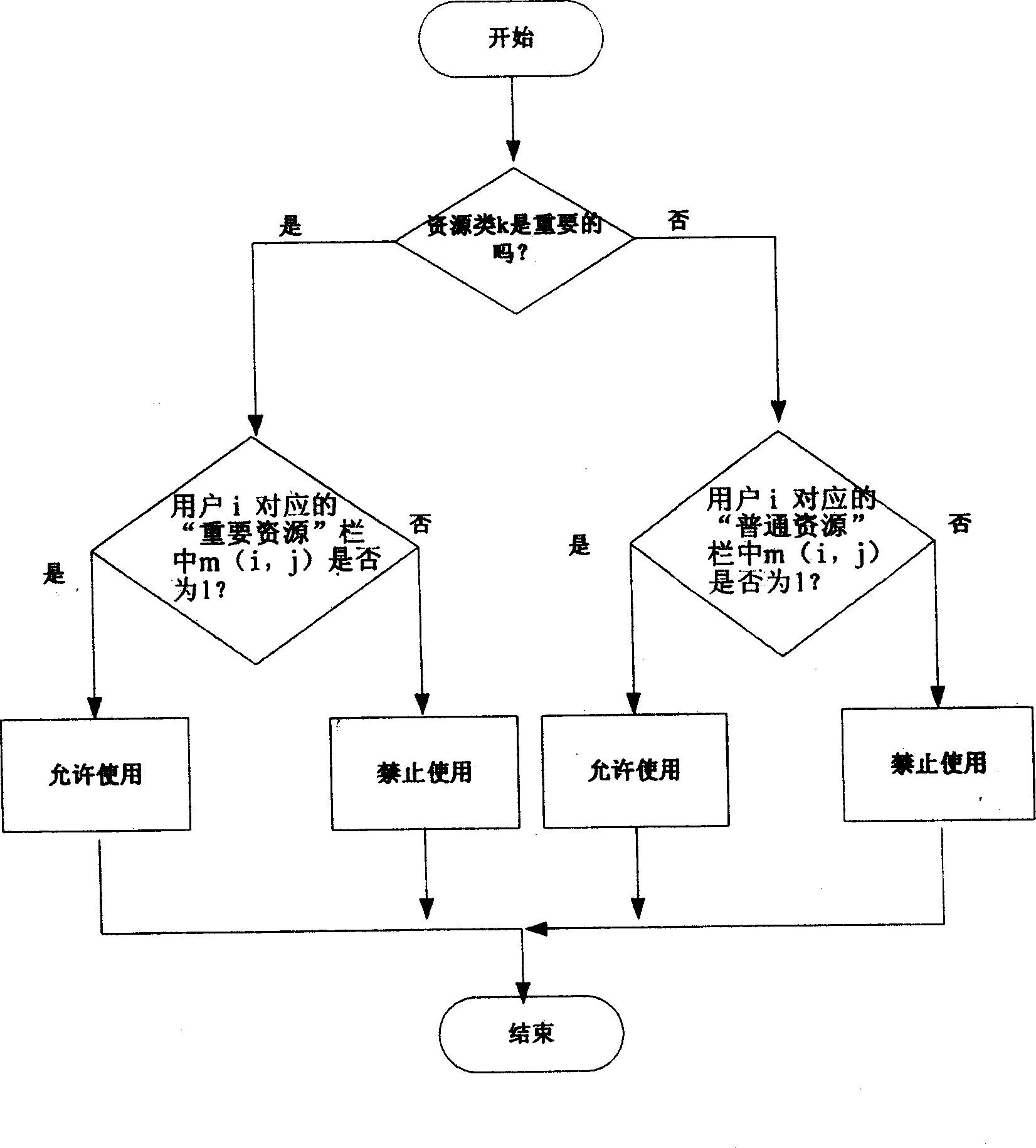
[0016] Mobile terminals classify system resources. Taking general mobile phones as an example, for mobile phones, including high-end and low-end mobile phones and PDAs with different functions, the data or functions used by users are generally divided into the following categories:
[0017] 1) Record: A certain short message, or a certain telephone number in the phone book, or a digital resource in the form of records such as a memo.
[0018] 2) File: It can be a certain document, such as word document, music file such as midi, mp3 and other formats of music file, or video file in dat format, rm format, etc., or executable file such as exe file, or other application files
[0019] 3) Folder: similar to the folder in the PC, such as the entire phone book, such as inbox, outbox, draft box, etc., such as photo albums, etc.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com