Confidential express method and system thereof
A cipher and recipient technology, applied in data processing applications, instruments, calculations, etc., can solve problems such as recipient information leakage, and achieve the effects of ensuring authenticity, strengthening confidentiality, and resolving sign-in disputes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described in detail in conjunction with the following specific embodiments and accompanying drawings. The process, conditions, experimental methods, etc. for implementing the present invention, except for the content specifically mentioned below, are common knowledge and common knowledge in this field, and the present invention has no special limitation content.
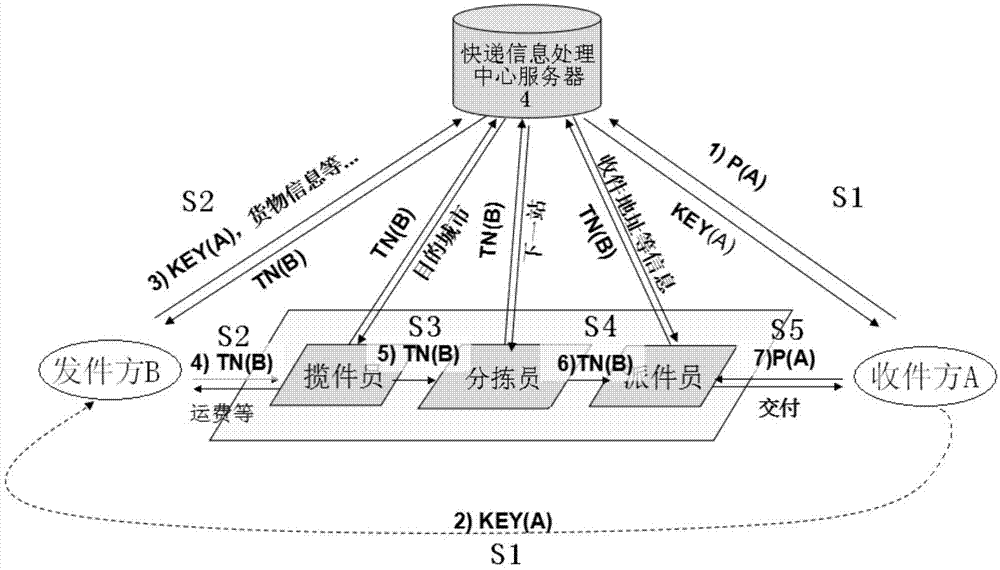
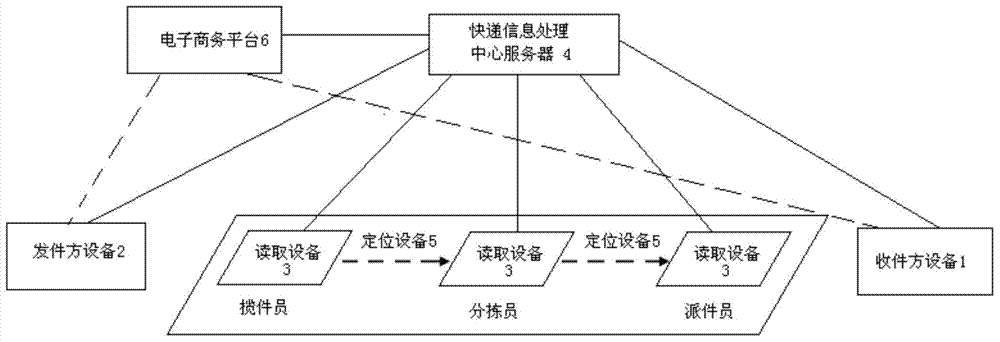
[0024] figure 1 The confidential express delivery method of the present invention is shown. According to the process from sending to receiving, the present invention is mainly divided into sending stage S1, receiving stage S2, transshipment stage S3, dispatching stage S4 and receiving stage S5.
[0025] In the sending phase S1, the receiver stores and encrypts the receiving information in the server of the express information processing center, and the server of the express information processing center generates an encrypted key code KEY (A) and sends it to the receiver. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com