Multi-source encrypted image retrieval method supporting privacy protection
A technology for encrypting images and protecting privacy. It is used in special data processing applications, instruments, and electrical digital data processing, and can solve problems such as image similarity information leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
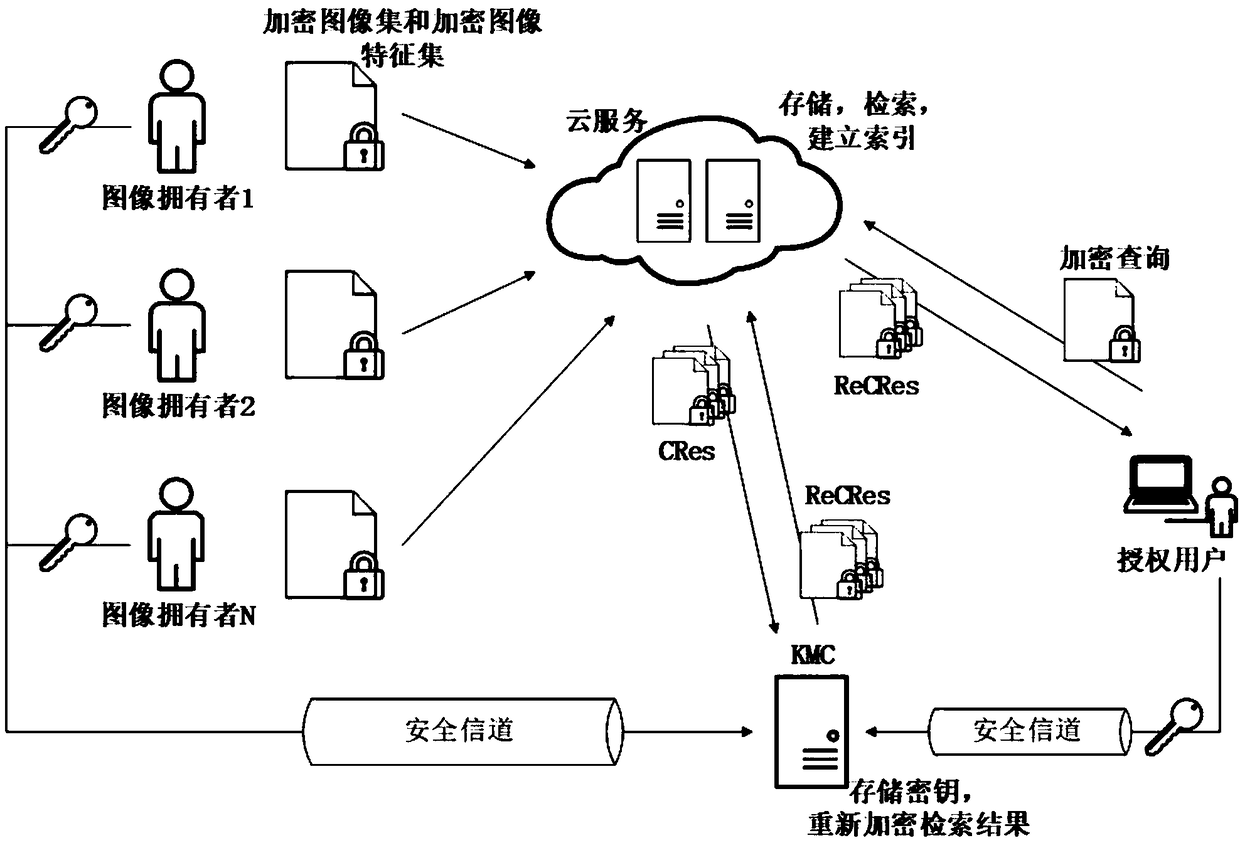
[0061] This embodiment describes the system model during the implementation of a privacy-protected multi-source encrypted image retrieval method of the present invention, such as figure 1 shown.
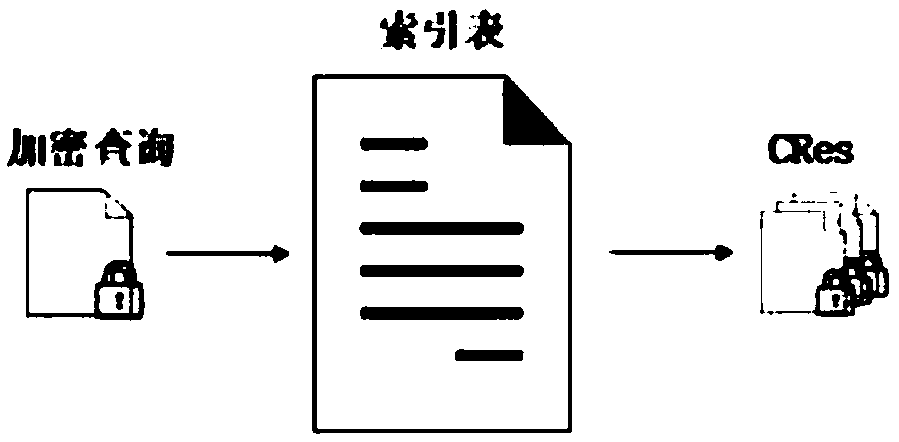
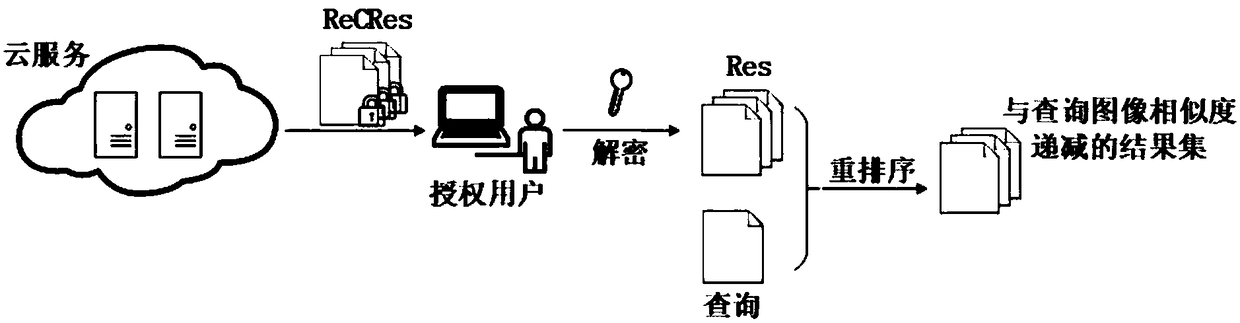
[0062] From figure 1It can be seen that there are multiple image owners, and they respectively outsource the encrypted image set and encrypted image feature set to cloud services for storage and retrieval, and at the same time they will send the image encryption key to KMC for storage through a secure channel; The authorized user will submit an encrypted query to the cloud service, and decrypt the encrypted result set ReCRes returned by the cloud service to obtain the original result set Res. At the same time, the authorized user will send the encrypted image key of this query to KMC; in order to improve the retrieval efficiency, the cloud service will establish a retrieval index based on the encrypted image data outsourced by the image owners. To further protect the privacy inform...
Embodiment 2
[0066] This embodiment describes the image similarity and image retrieval results during the implementation of a multi-source encrypted image retrieval method supporting privacy protection described in the present invention, such as Figure 4 and Figure 5 shown.
[0067] Figure 4 is the percentage of real similar images in the corresponding position range of the result set; Figure 5 is the F1 index of the search result.
[0068] Such as Figure 4 As shown, when using Euclidean distance to measure image similarity, the proportion of real similar images distributed in the first 10% is very large, and along with the increase of the result set range, the distribution percentage of real images is lower; when using the proposed method of the present invention When the distance Dis measures image similarity, the distribution of real similar images in the result set is uniform, and the cloud server cannot judge the similarity information in the image from the result; The F1 in...
Embodiment 3
[0070] This embodiment specifically expounds how the present invention can be used to implement a secure image retrieval outsourcing function and to implement a multi-source image retrieval function based on encrypted images.
[0071] The image owner will encrypt the image according to step 1.1 before outsourcing the image. Suppose the image collection BCollection j One of the images in is (in order to illustrate the image encryption process, it is assumed that the image size is 9×9, in practice it depends on the size of the specific image):
[0072] B ji ={b j1 ,b j2 ,b j3 ,b j4 ,b j5 ,b j6 ,b j7 ,b j8 ,b j9}={30,23,45,236,89,70,66,51,198}
[0073] Image owner j will first generate an image encryption key, assuming the generated key is:
[0074] K j ={k j1 ,k j2 ,k j3 ,k j4 ,k j5 ,k j6 ,k j7 ,k j8 ,k j9}={187,253,56,78,12,45,68,99,100}
[0075] Then the encrypted image can be calculated as:
[0076]
[0077] For all images in the image set, the imag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com