Method and terminal device for protecting privacy information
A terminal device, privacy protection technology, applied in the field of privacy protection, can solve problems such as the inability to fully protect privacy information and the leakage of user privacy information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 3
[0094]The difference between Embodiment 3 and Embodiment 1 is that the special unlocking operation in Embodiment 3 is not a combination of unlocking operations and additional operations, but a special Unlock operation. Specifically, the unlocking operation includes inputting a preset password, inputting a preset gesture, inputting a preset voice, or sliding on the screen. The operation dimension is the operation time, the value of the operation dimension is the operation time length, and the preset threshold is the preset duration. For example, when the unlocking operation is password unlocking, the special unlocking operation is that the time for inputting the password is longer than the preset duration; for gesture unlocking, the special unlocking operation is that the time for inputting the gesture is longer than the preset duration; Preset duration, when unlocking by voice, the special unlocking operation is that the time of inputting the preset voice is longer than the pr...
Embodiment 4
[0113] The difference between Embodiment 4 and Embodiment 1 is that in Embodiment 4, the terminal device does not protect private information by first displaying the second interface when detecting a special unlocking operation, but when detecting a special lock screen operation, the terminal device first Return to the system interface or open the preset interface, and then enter the locked state. The preset interface includes a preset hidden interface or a preset application interface.
[0114] The special screen lock operation includes pressing at least two preset buttons of the terminal device continuously or simultaneously, or the special screen lock operation is pressing the same preset button of the terminal device twice in succession. The preset keys include a physical power key, a physical volume key, a physical function key, or a virtual lock screen key. For example, when the terminal device detects that the physical power button is pressed twice in a row, it first r...
Embodiment 5
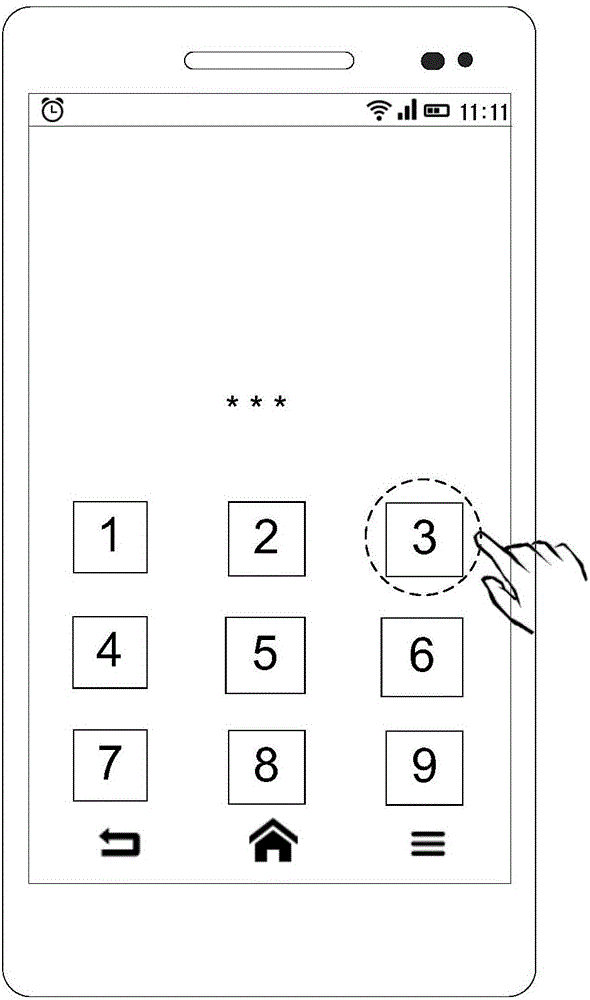
[0132] In Embodiment 5, the receiving the unlock input includes converting the sampled information into a signal by the sensor of the terminal device, and the monitoring the event corresponding to the unlock input includes the processor of the terminal device monitoring whether the event corresponding to the signal is consistent with the preset event match. Taking the input of the preset password "1234" as an example, receiving the first unlock input includes receiving an interrupt signal generated by the user inputting the password "1234", and monitoring the first event corresponding to the first unlock input includes generating an array in response to the interrupt signal, The terminal device matches the generated array with the preset array. After the matching is successful, it detects that the first event corresponding to the first unlock input matches the first preset event, and triggers the first function corresponding to the first preset event. , the first function is u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com