Safety system and safety protection method for mobile terminal
A technology for mobile terminals and security systems, applied in the field of mobile terminal security systems and security protection, can solve the problems of information leakage, lack of management, and misappropriation of users, and achieve the effect of preventing personal information from being disclosed or stolen, and protecting private information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
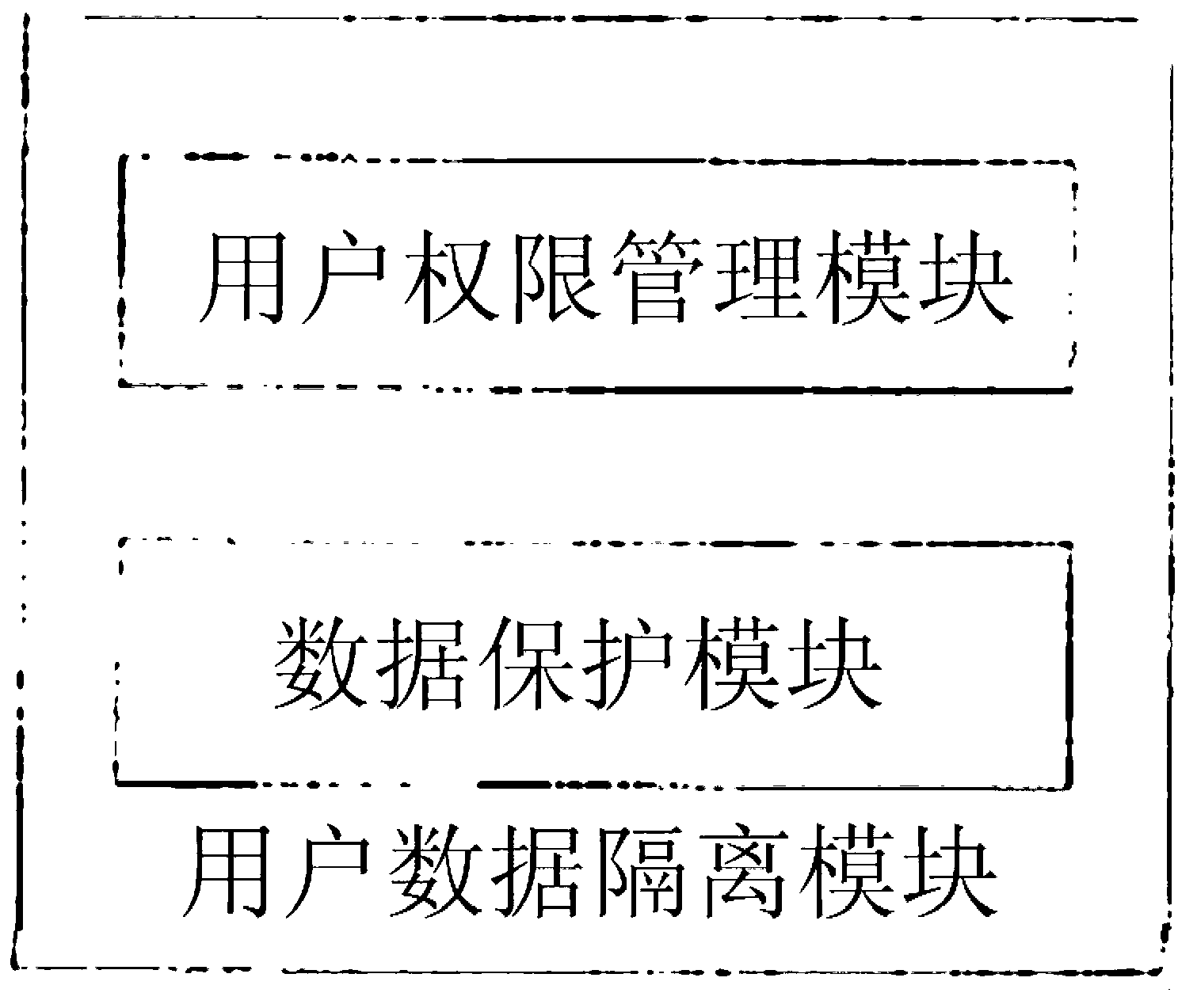
[0029] Such as figure 1 As shown, a mobile terminal security system described in this embodiment includes a user data isolation module;
[0030] The user data isolation module includes a user rights management module and a data protection module for protecting user privacy data;
[0031] The user authority management module is used to enable the user to enter the standby interface of different authority passwords;
[0032] The data protection module is arranged between the application and the database interface, and is used for managing the access authority of the application program to the user data.
[0033] Wherein, the mobile terminal security system further includes a user card identification start-up module, which is used for the mobile terminal to judge whether the identification of the user card is correct.
[0034] The database interface is SQLite interface.
[0035] The standby interface of passwords with different authority includes the standby interface of high ...
Embodiment 2
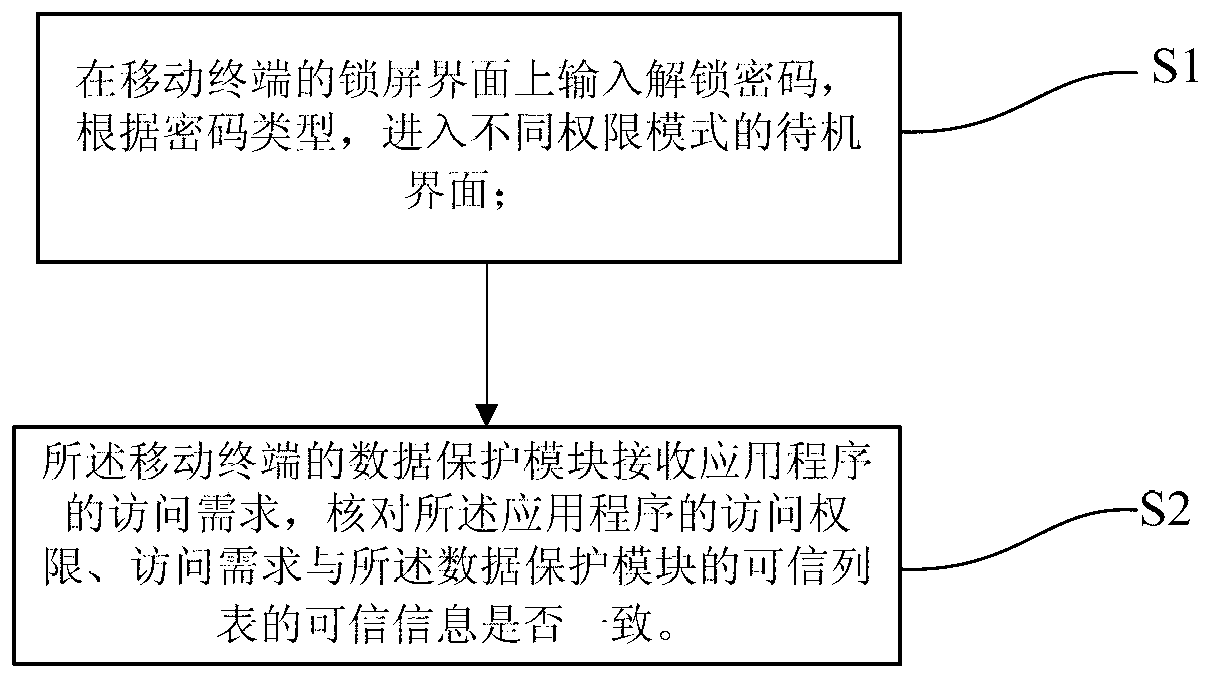
[0042] Such as figure 2 As shown, a mobile terminal security protection method described in this embodiment includes the following steps:
[0043] S1: Enter the unlock password on the lock screen interface of the mobile terminal, and enter the standby interface of different permission modes according to the password type;
[0044] S2: The data protection module of the mobile terminal receives the access requirement of the application program, and checks whether the access right and access requirement of the application program are consistent with the trusted information in the trusted list of the data protection module.
[0045] Wherein, the following steps can also be taken before the above step S1:
[0046] The mobile terminal reads the user card, and the mobile terminal judges that the user card identification is correct, and if so, starts the mobile terminal; otherwise, closes the mobile terminal.
[0047] After entering the standby interface of different permission mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com